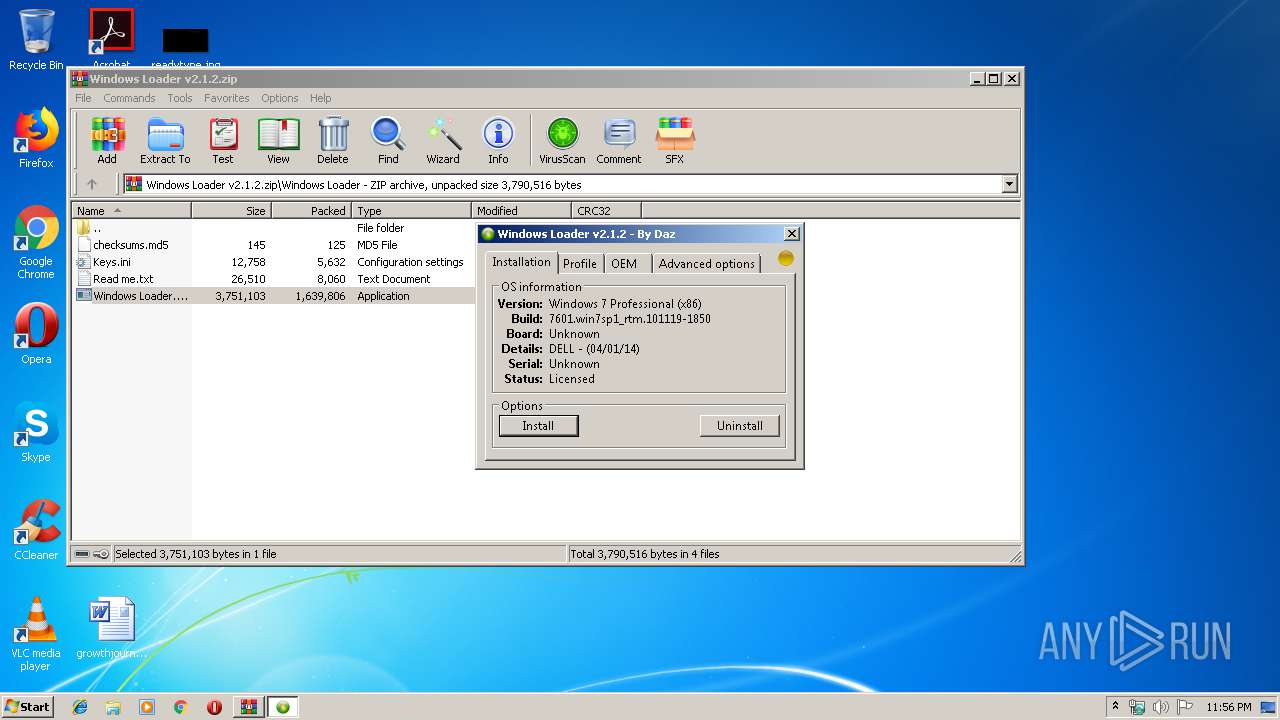
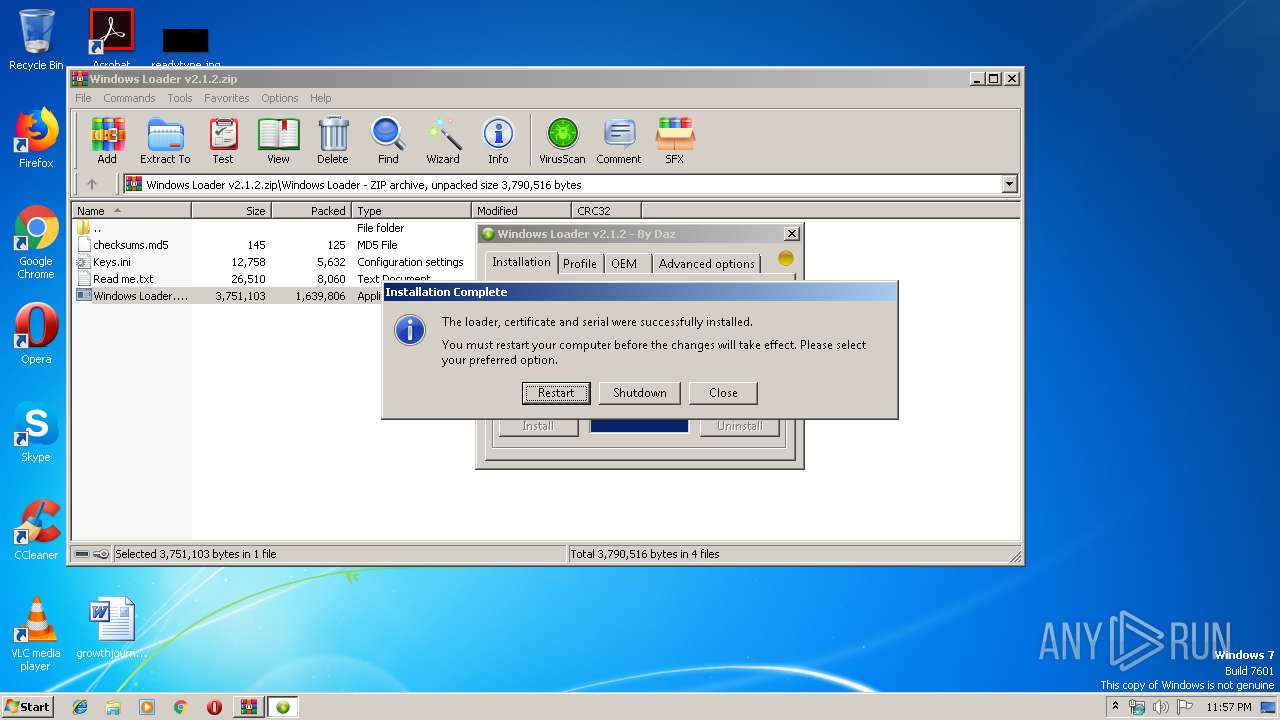
| File name: | Windows Loader v2.1.2.zip |
| Full analysis: | https://app.any.run/tasks/0e12295b-f717-4895-a408-769b5b68e426 |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2019, 23:56:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 429D08DFF15146B6622613CD23574888 |
| SHA1: | 5EB3F62C117D3272EA8439A285378F74D76DD08C |
| SHA256: | 101FF2239CDDFDE32932D3F8C72E831E12DCC9897E625989C2328656245D7B8C |
| SSDEEP: | 24576:09eZhTSc6c2qeYLnrnE5rc3I+Dw34KQgnydHxxkoBMV+Ffa57nScVwo/fOp:Ki4inEVc34fKdHxxt+Yfa8cGYO |
MALICIOUS
Application was dropped or rewritten from another process
- Windows Loader.exe (PID: 3040)
- Windows Loader.exe (PID: 2252)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 3388)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2092)
Starts CMD.EXE for commands execution
- Windows Loader.exe (PID: 2252)
- cmd.exe (PID: 3388)
- cmd.exe (PID: 1880)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 3192)
- cmd.exe (PID: 600)
Executes scripts
- cmd.exe (PID: 4016)
- cmd.exe (PID: 2576)
Low-level read access rights to disk partition
- bootsect.exe (PID: 2076)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2012:03:11 14:33:27 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Windows Loader/ |
Total processes
73
Monitored processes
23
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | takeown /f C:\ldrscan\bootwin | C:\Windows\system32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 600 | cmd.exe /A /C "icacls C:\ldrscan\bootwin /grant *S-1-1-0:(F)" | C:\Windows\system32\cmd.exe | — | Windows Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1036 | compact /u \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963}\SHBRV | C:\Windows\system32\compact.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: File Compress Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1252 | C:\Windows\System32\cscript.exe //nologo C:\Windows\System32\slmgr.vbs -ilc "C:\Dell.XRM-MS" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1880 | cmd.exe /A /C "cmd.exe /c takeown /f C:\ldrscan\bootwin" | C:\Windows\system32\cmd.exe | — | Windows Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2056 | cmd.exe /A /C "C:\bootsect.exe /nt60 SYS /force" | C:\Windows\system32\cmd.exe | — | Windows Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2076 | C:\bootsect.exe /nt60 SYS /force | C:\bootsect.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2092 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Windows Loader v2.1.2.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1073807364 Version: 5.60.0 Modules
| |||||||||||||||
| 2120 | icacls C:\ldrscan\bootwin /grant *S-1-1-0:(F) | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2252 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2092.20107\Windows Loader\Windows Loader.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2092.20107\Windows Loader\Windows Loader.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
570
Read events
557
Write events
13
Delete events
0
Modification events
| (PID) Process: | (2092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2092) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Windows Loader v2.1.2.zip | |||
| (PID) Process: | (2092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
1
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2252 | Windows Loader.exe | C:\bootsect.dat | — | |
MD5:— | SHA256:— | |||
| 2252 | Windows Loader.exe | C:\bootsect.exe | — | |
MD5:— | SHA256:— | |||
| 2076 | bootsect.exe | \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963} | — | |
MD5:— | SHA256:— | |||
| 2252 | Windows Loader.exe | \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963}\SHBRV | binary | |
MD5:— | SHA256:— | |||
| 2252 | Windows Loader.exe | C:\System Volume Information\MountPointManagerRemoteDatabase | binary | |
MD5:— | SHA256:— | |||
| 2092 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2092.20107\Windows Loader\Read me.txt | text | |
MD5:186A6B0290273697C32A07CB51D33F46 | SHA256:2EE83633D242131A20DF453BB25DA1C1490C0EDC712EB489C582AA26CF430D3A | |||
| 2092 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2092.20107\Windows Loader\Keys.ini | text | |
MD5:62BDF0CD5E96CF8035E98498D223508A | SHA256:F8E56CFF7C8C55AD28E5FFB172EB597E4BAC0805F543602D6B4F656F1B32336E | |||
| 2092 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2092.20107\Windows Loader\checksums.md5 | text | |
MD5:2D0AD0E4FDF33B4C94C04065DEDB3FD5 | SHA256:04721392FFF895CDBD037FD52C0D868613A1D0F5F3C5EB4D3632CFDF088A615B | |||
| 2252 | Windows Loader.exe | C:\Dell.XRM-MS | xml | |
MD5:18B1E45BF56F40C3C4BBE65831178216 | SHA256:D072A059D3ED3E75C98B85B41E4319E8D5CFAE0E0C239B62436A3AD34003AB4A | |||
| 2092 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2092.20107\Windows Loader\Windows Loader.exe | executable | |
MD5:2FA16BC885C5A78754BCB2E546FAE368 | SHA256:305E1EAADBD2F953E9A92A53C71DFF2E3A38514E813A3E270E919B103BBE2FFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report