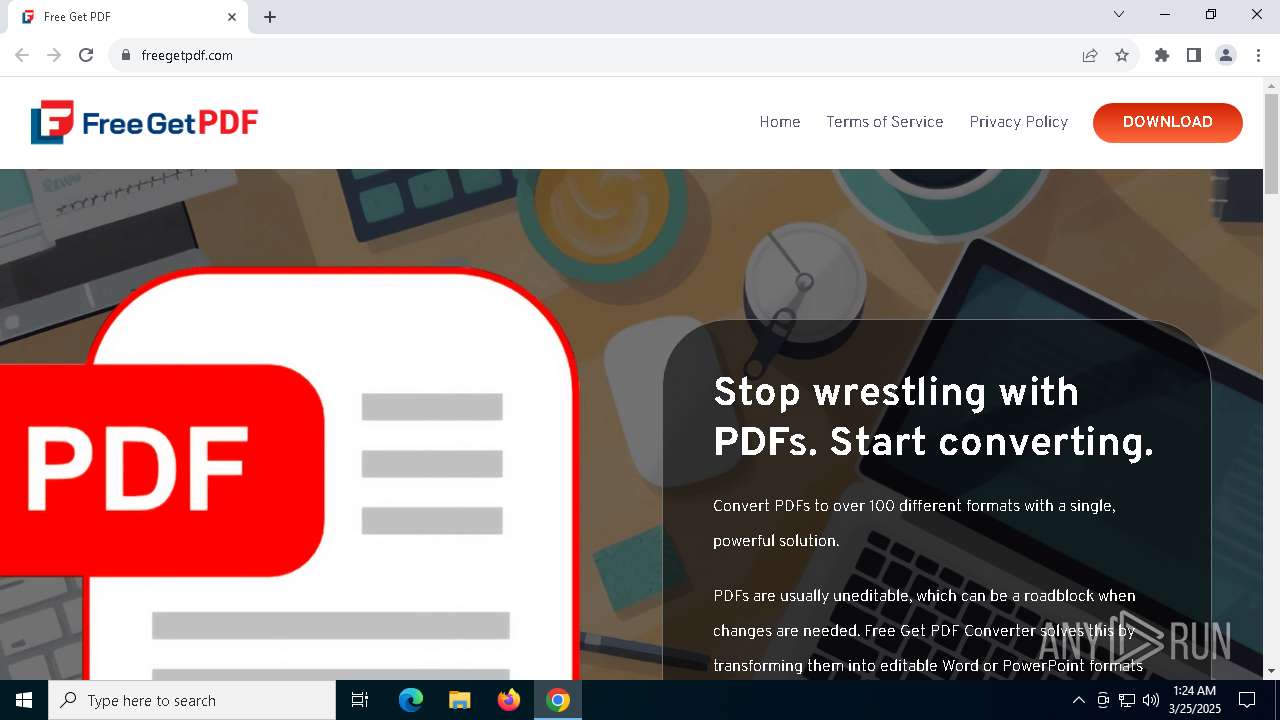
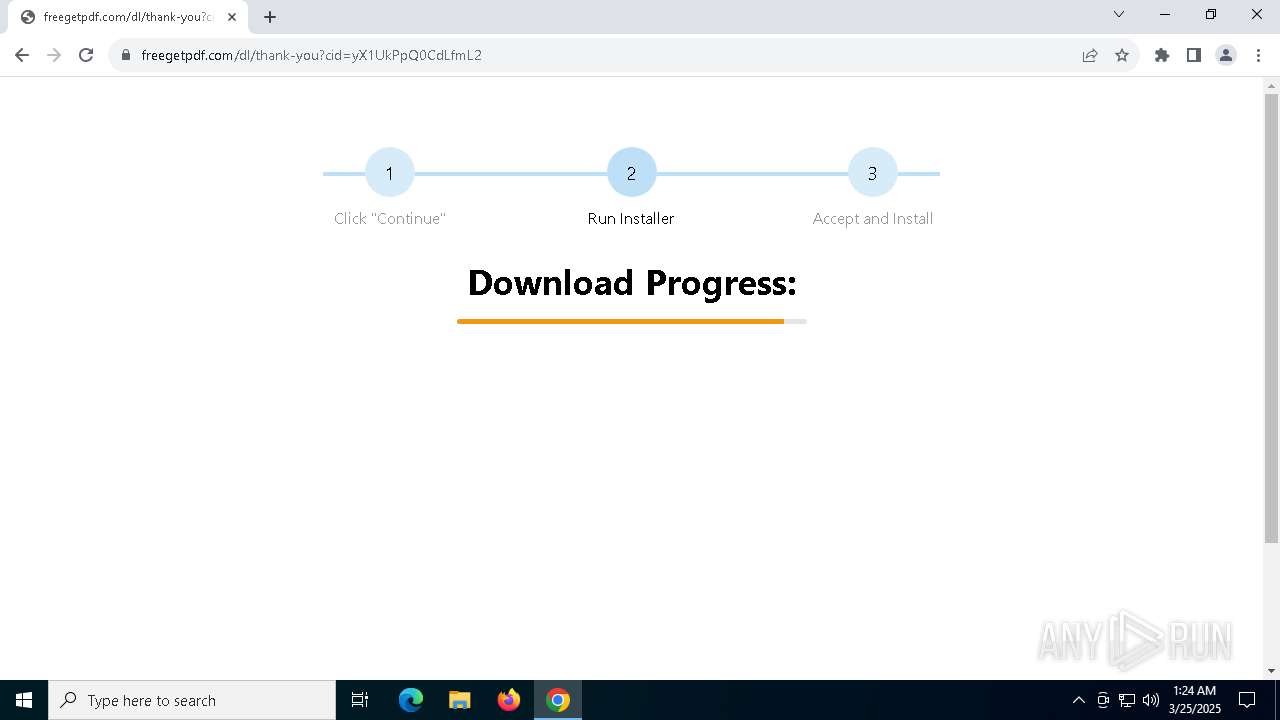
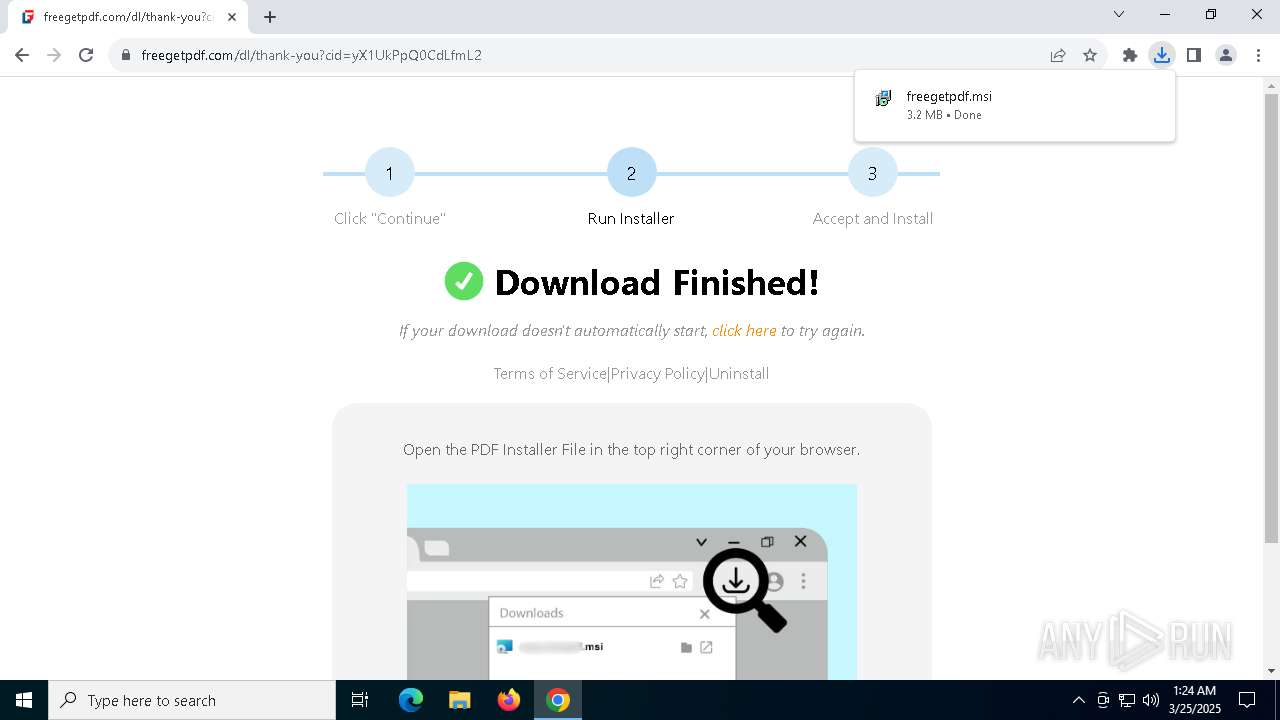
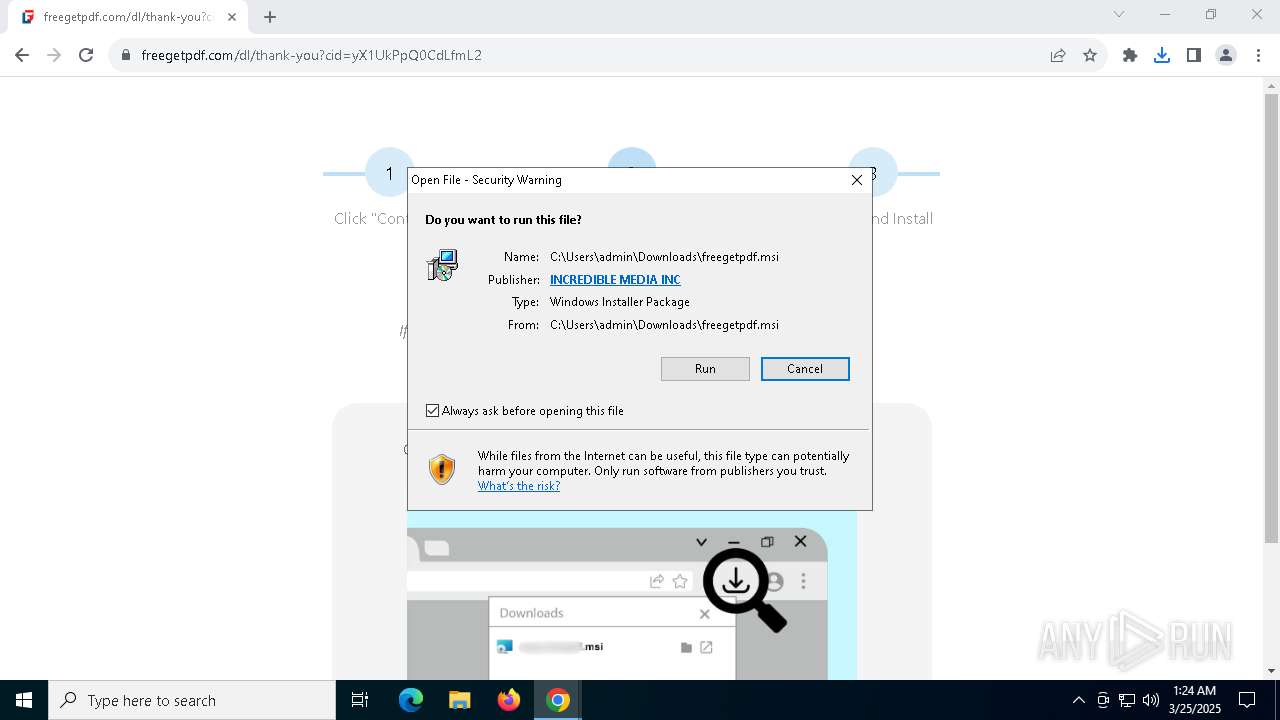
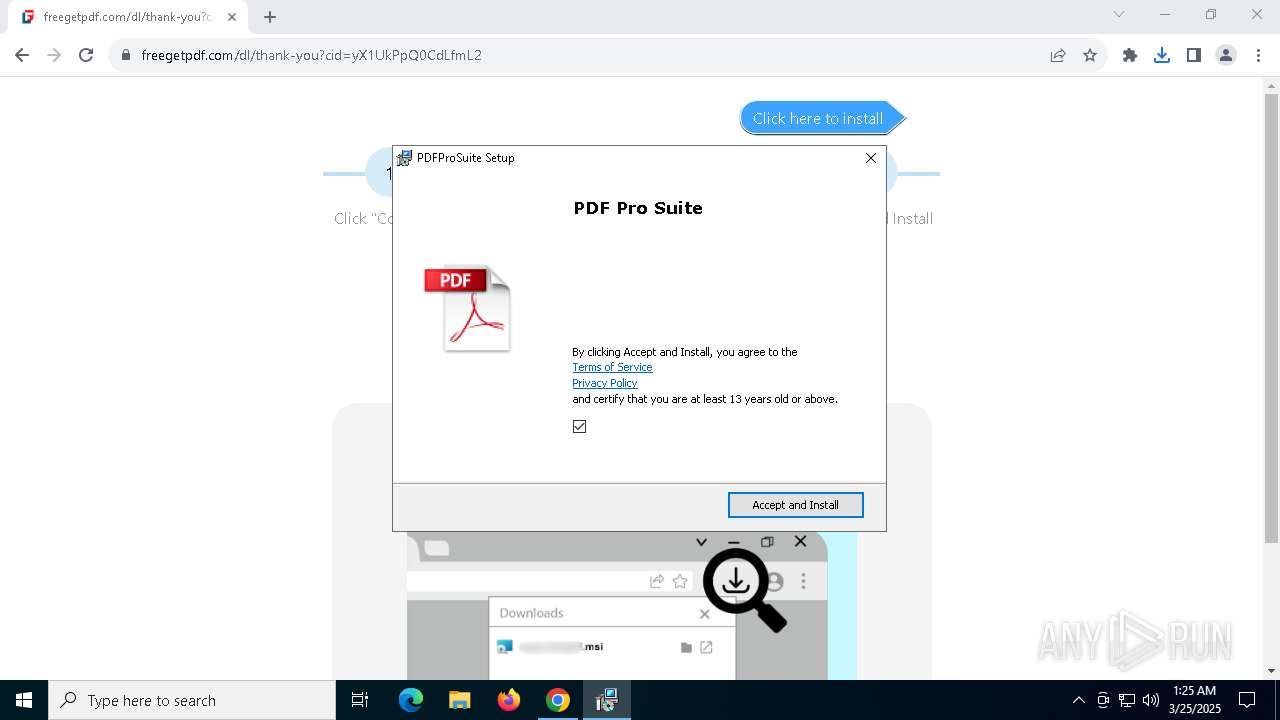
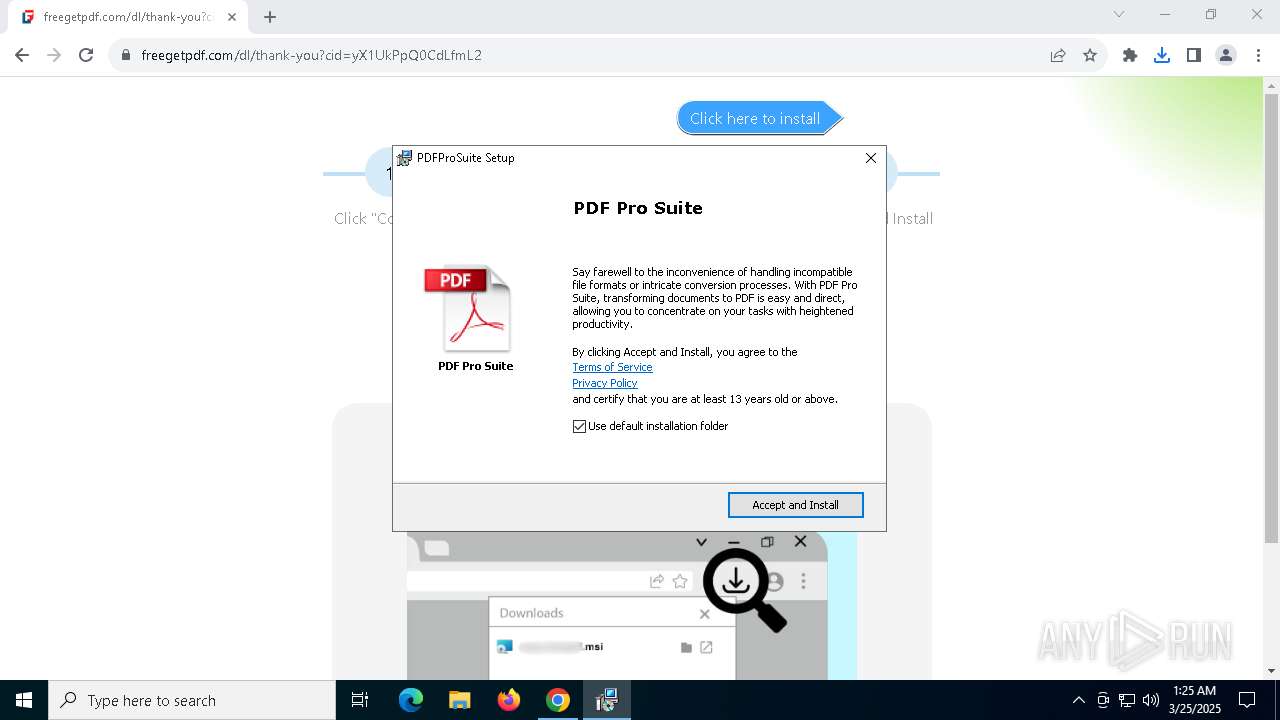
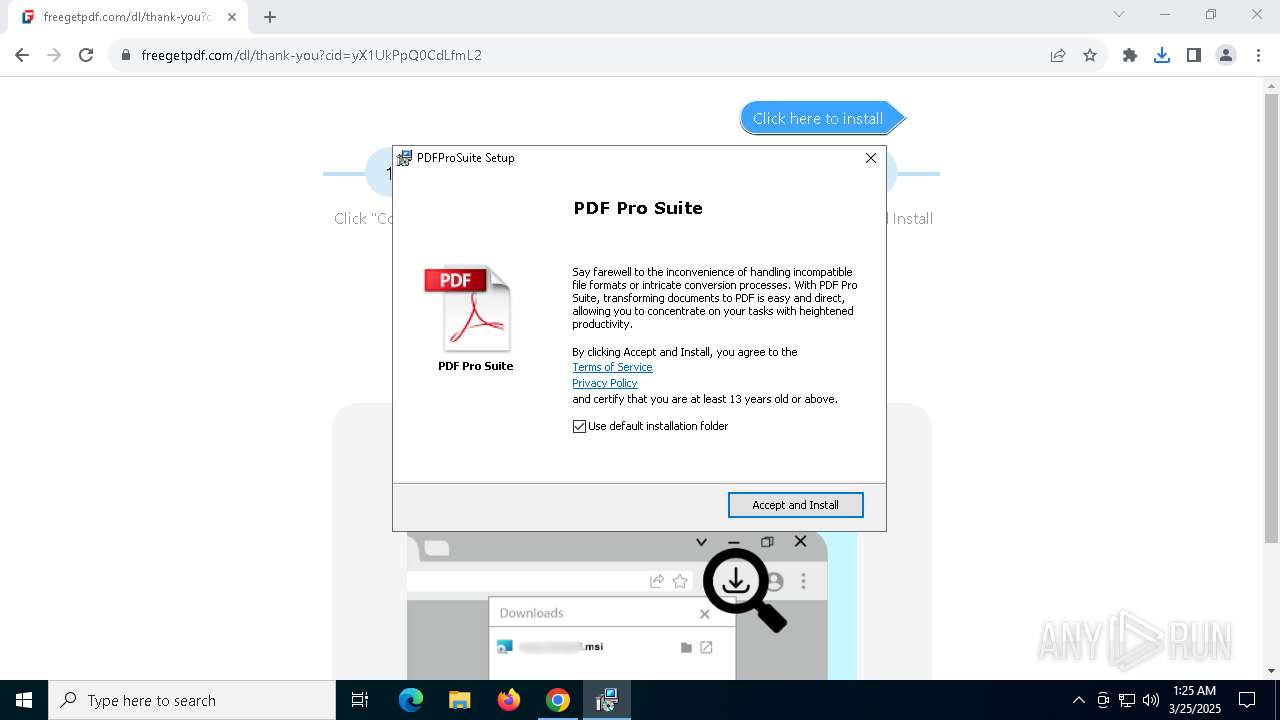
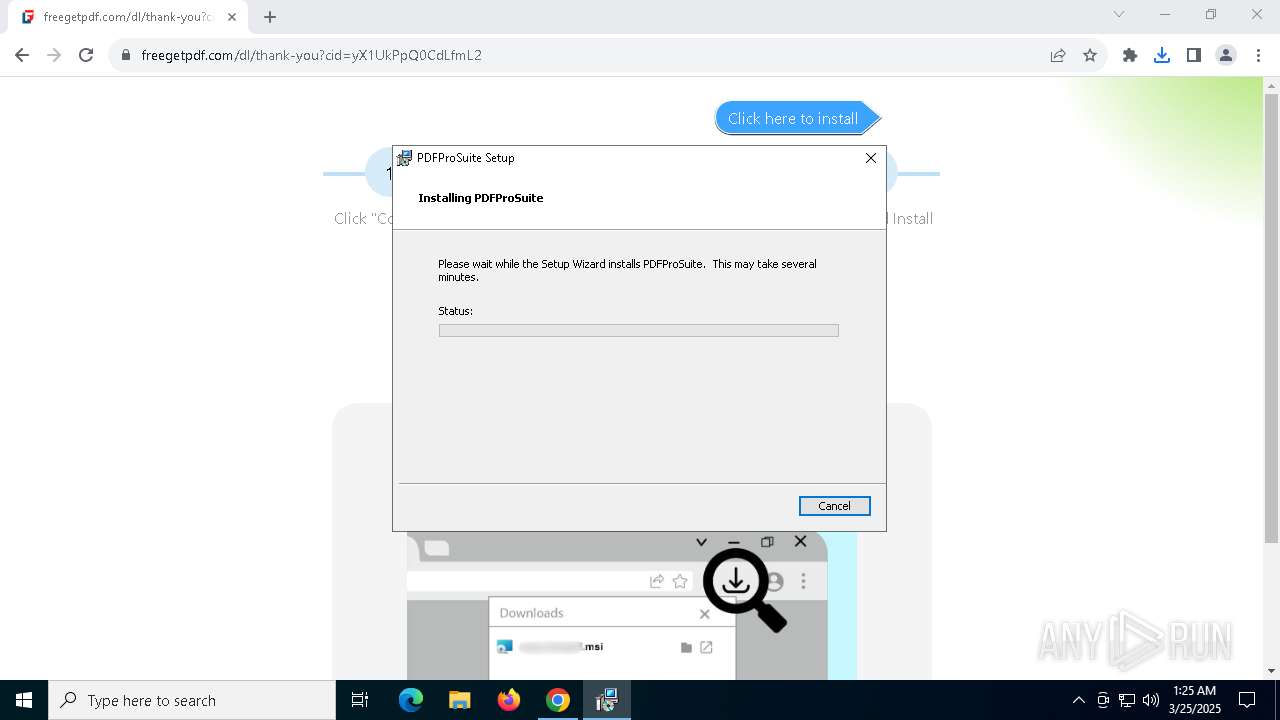
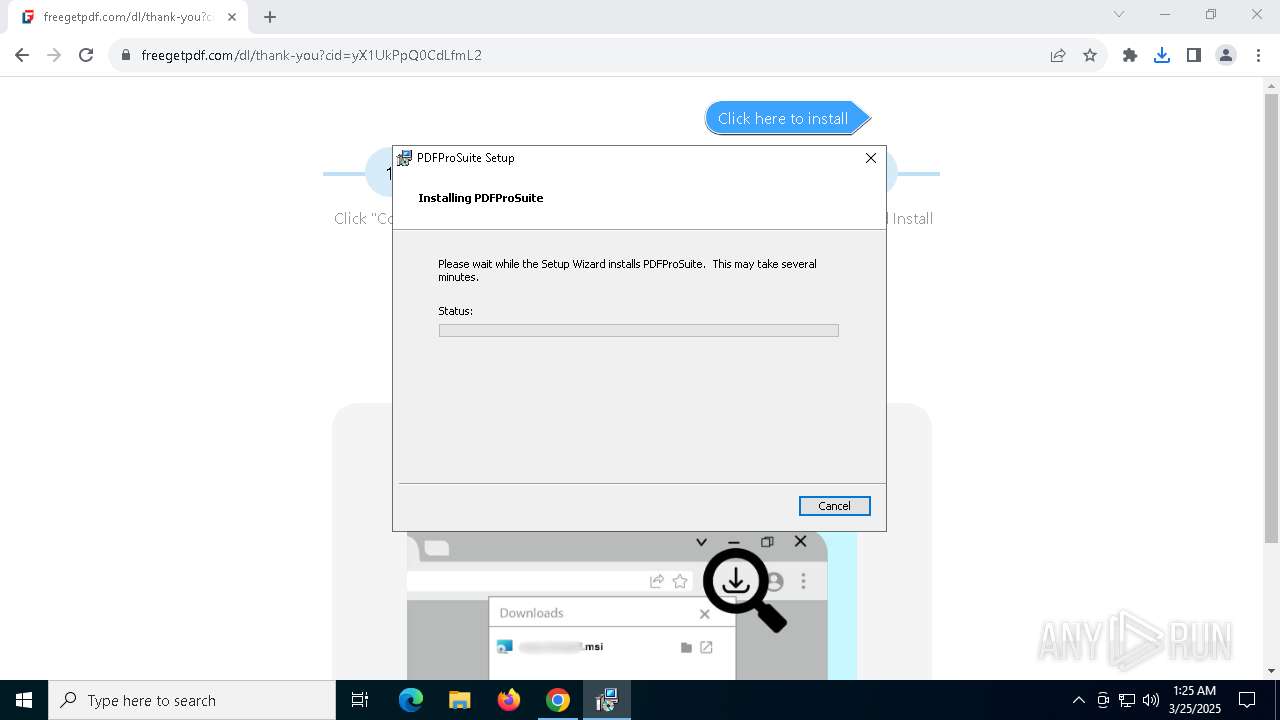
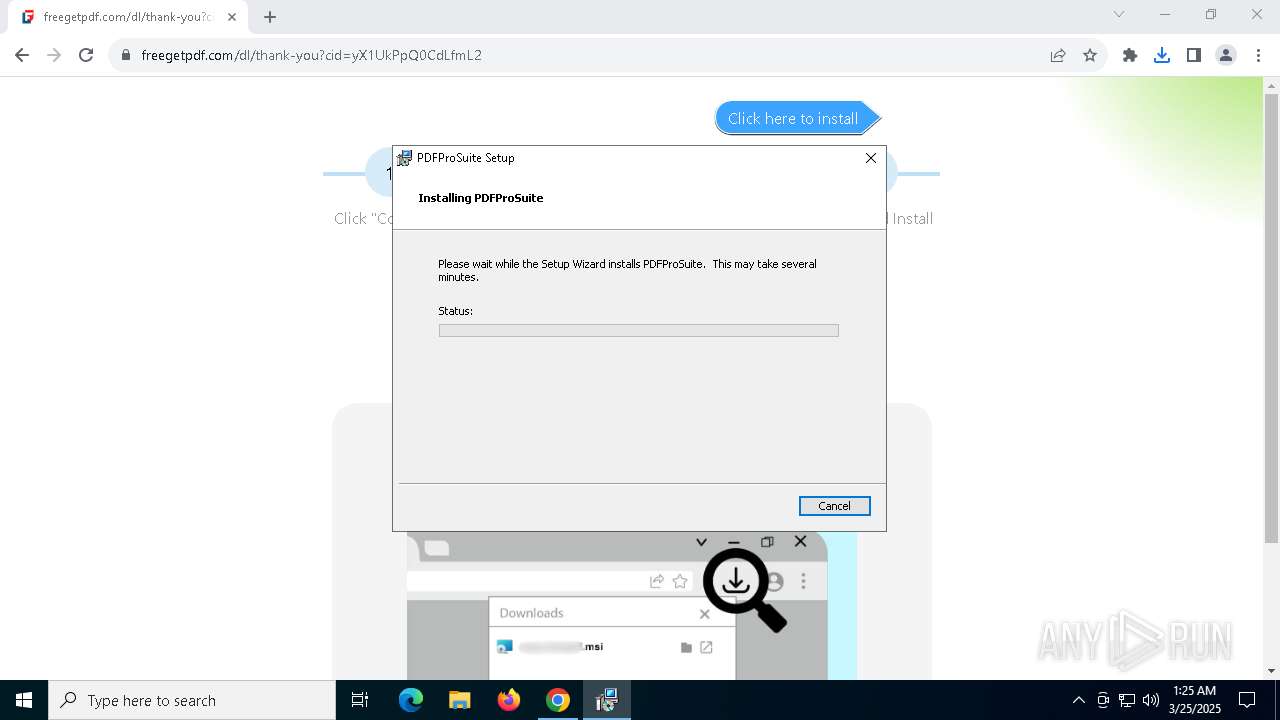
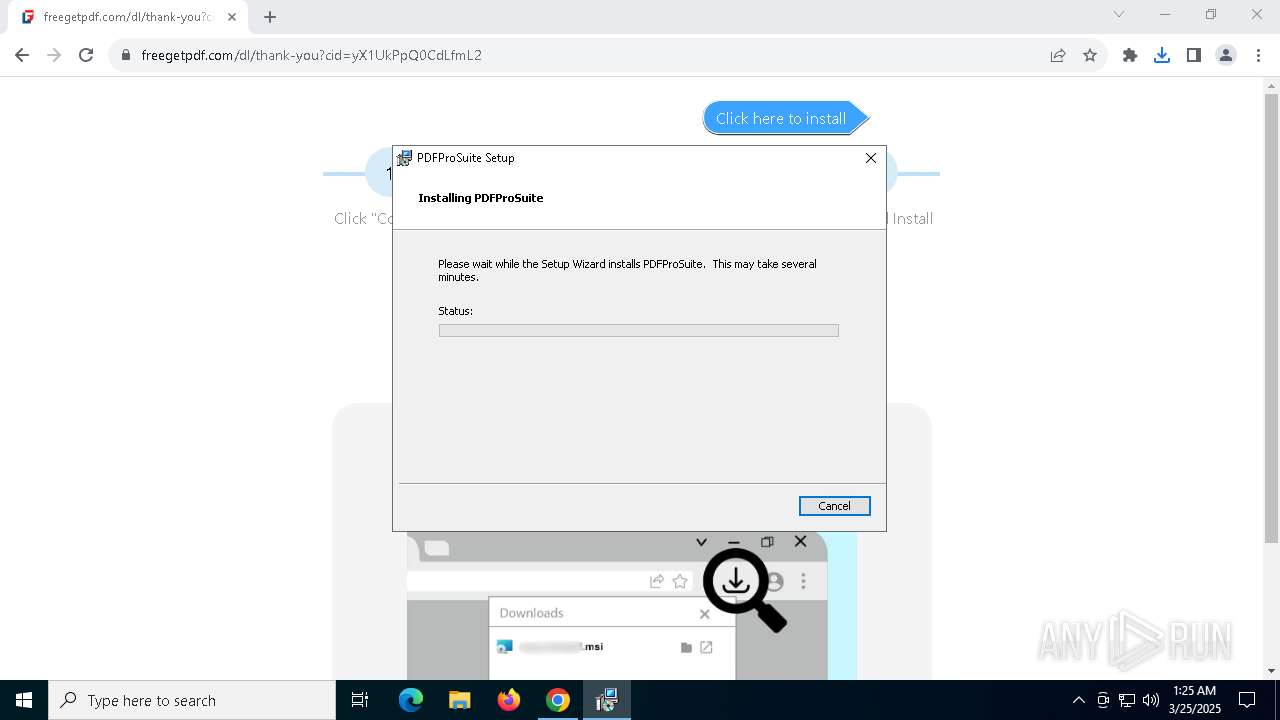
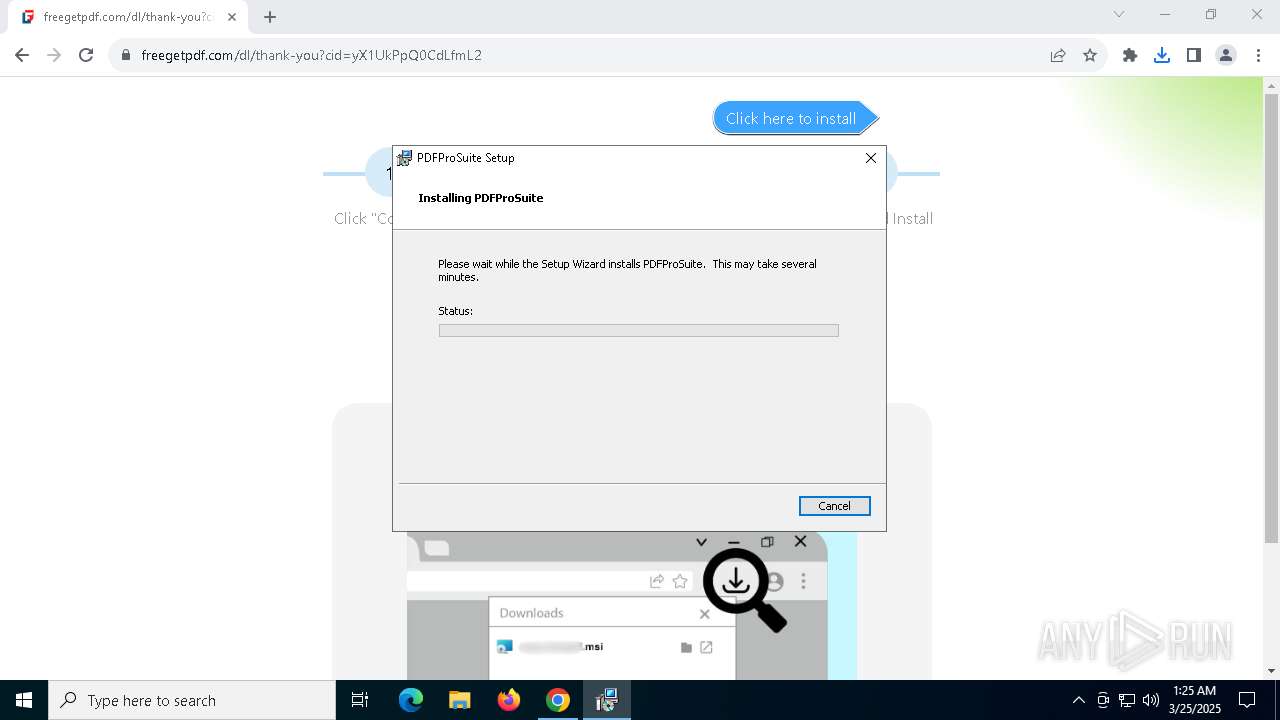
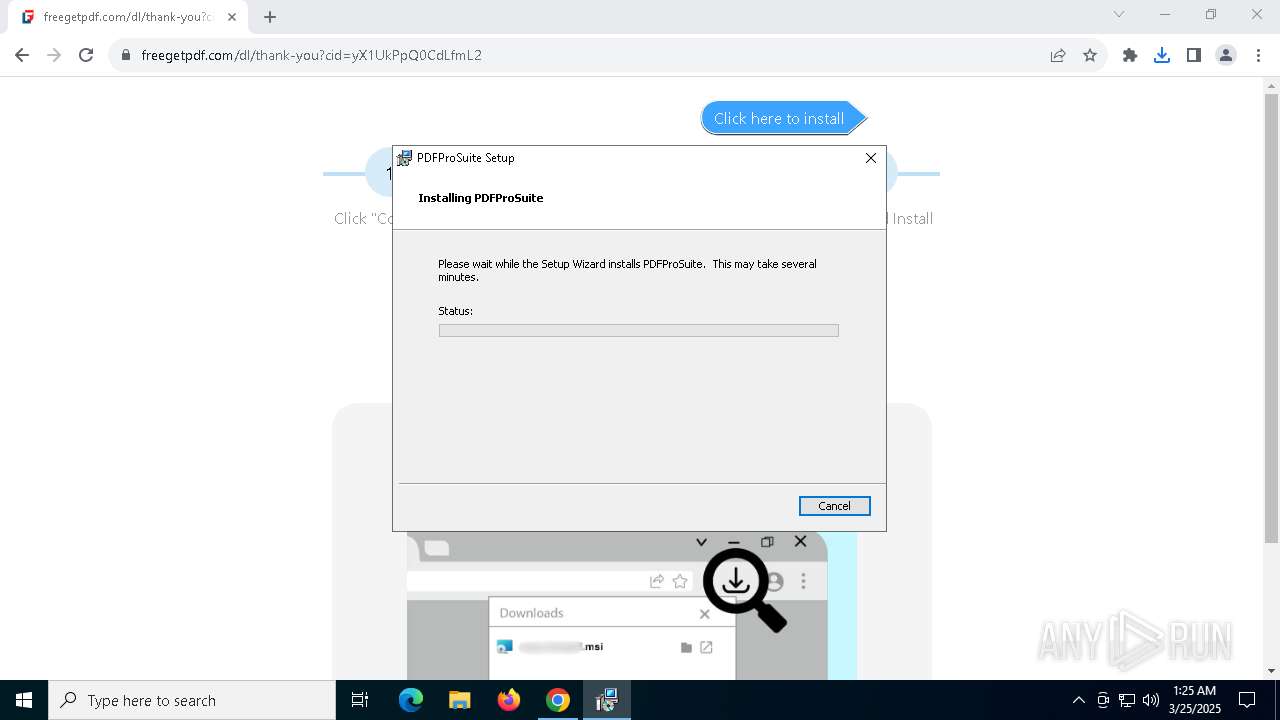
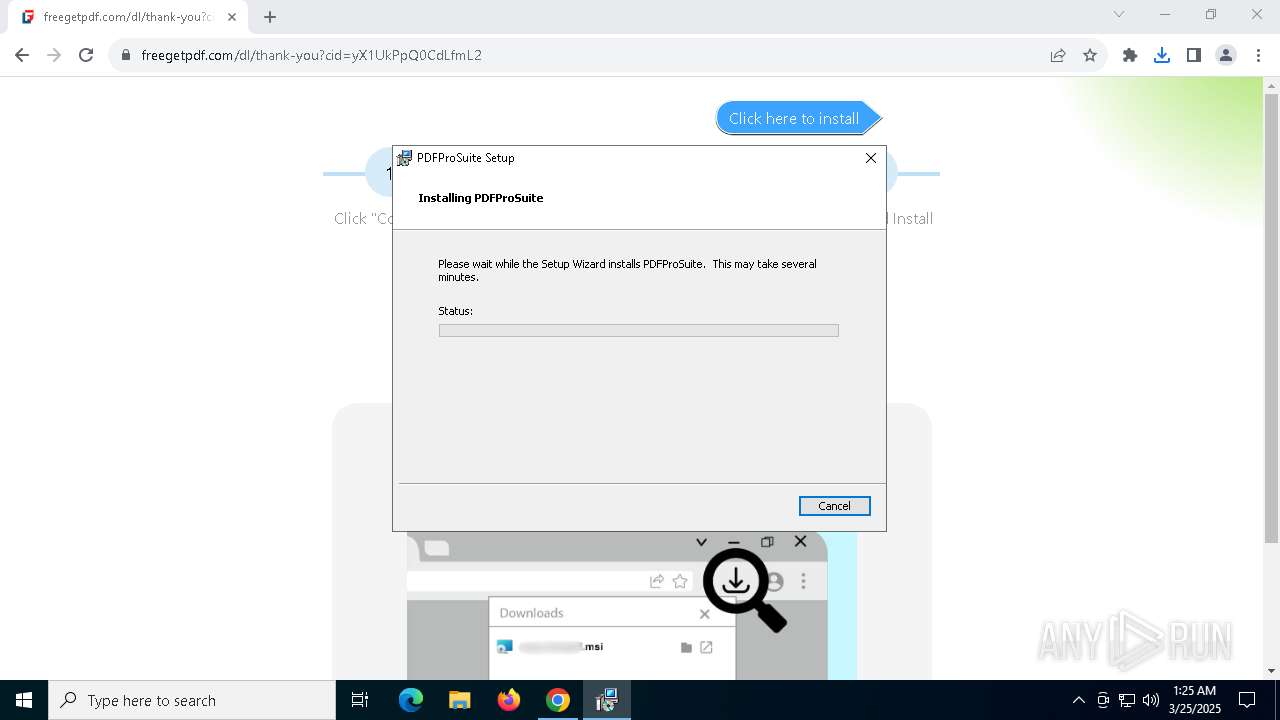
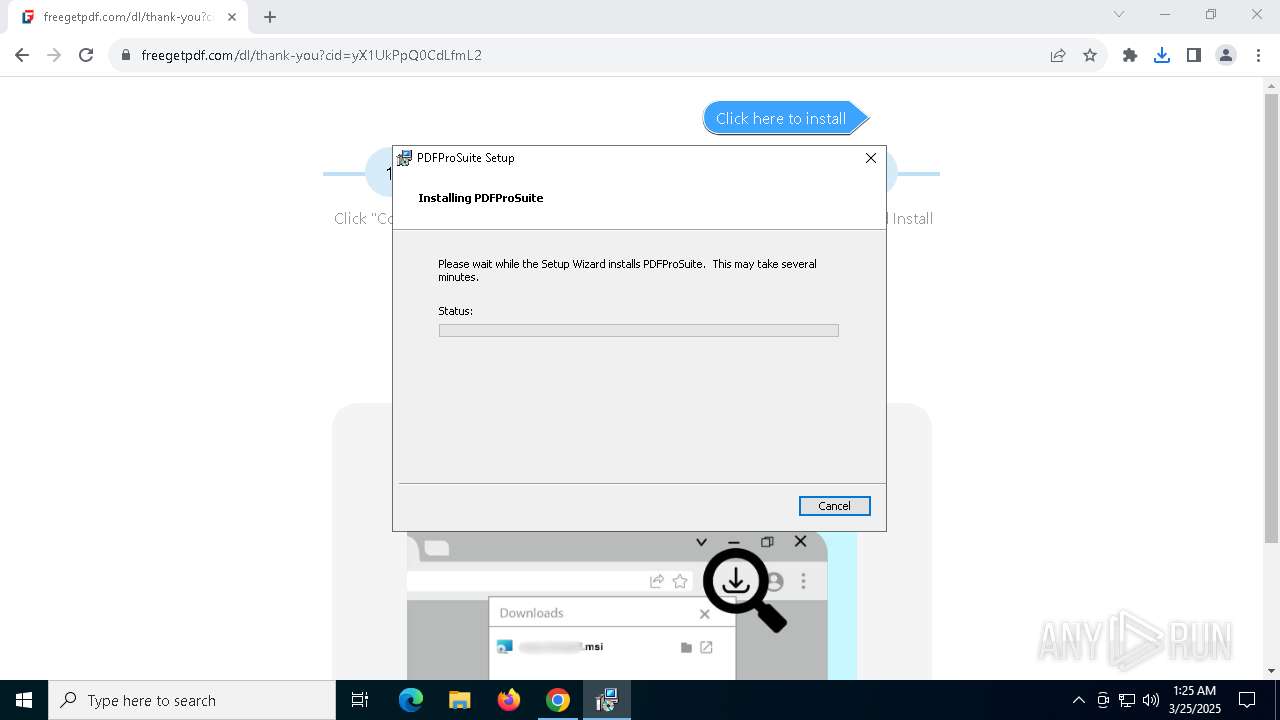
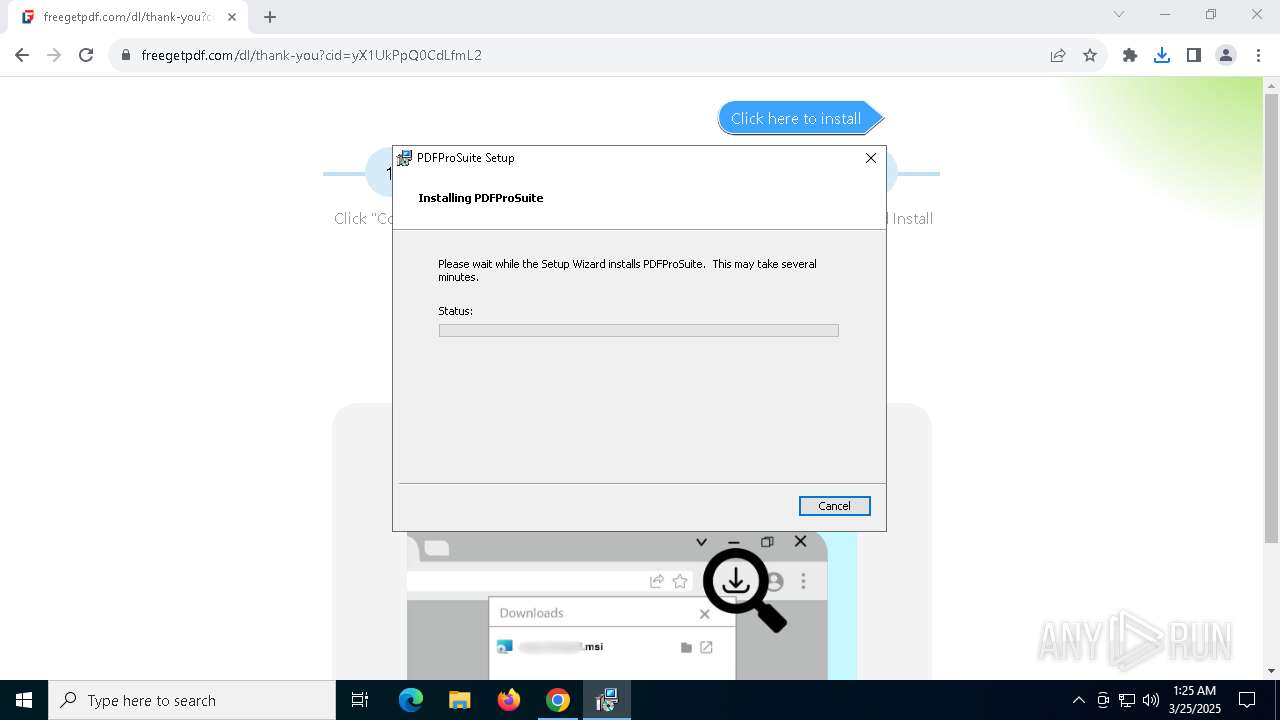
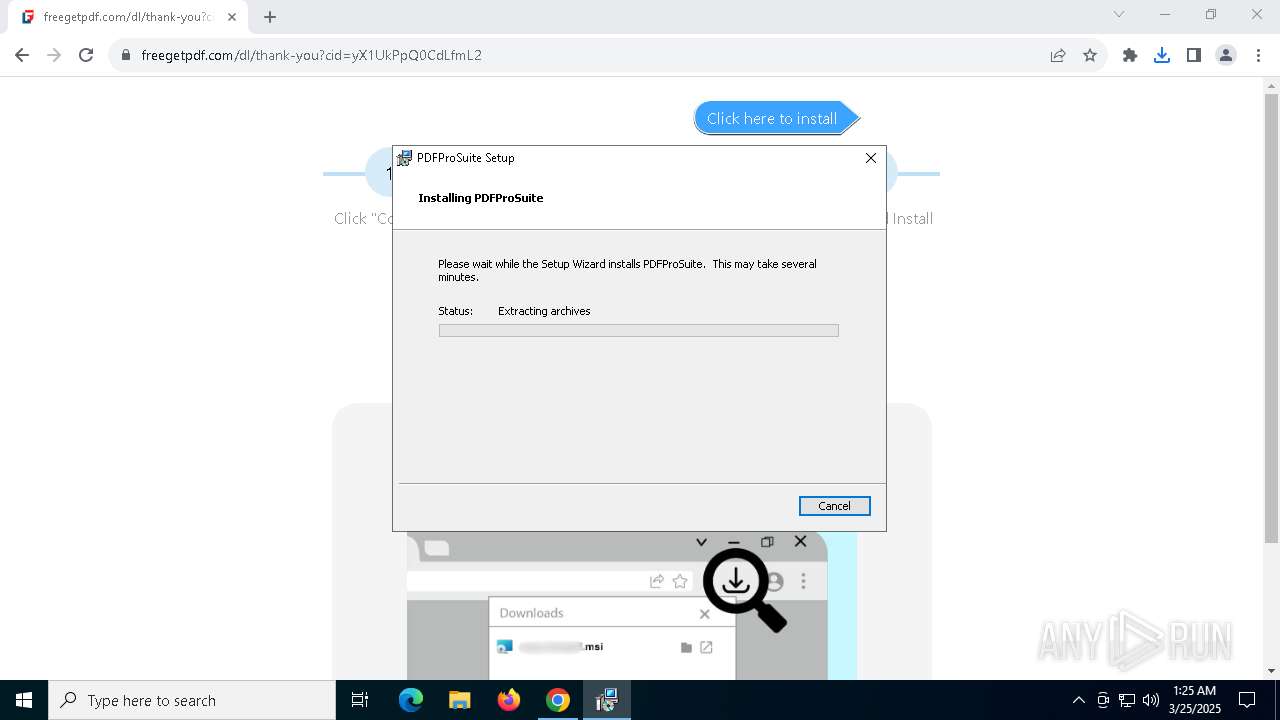
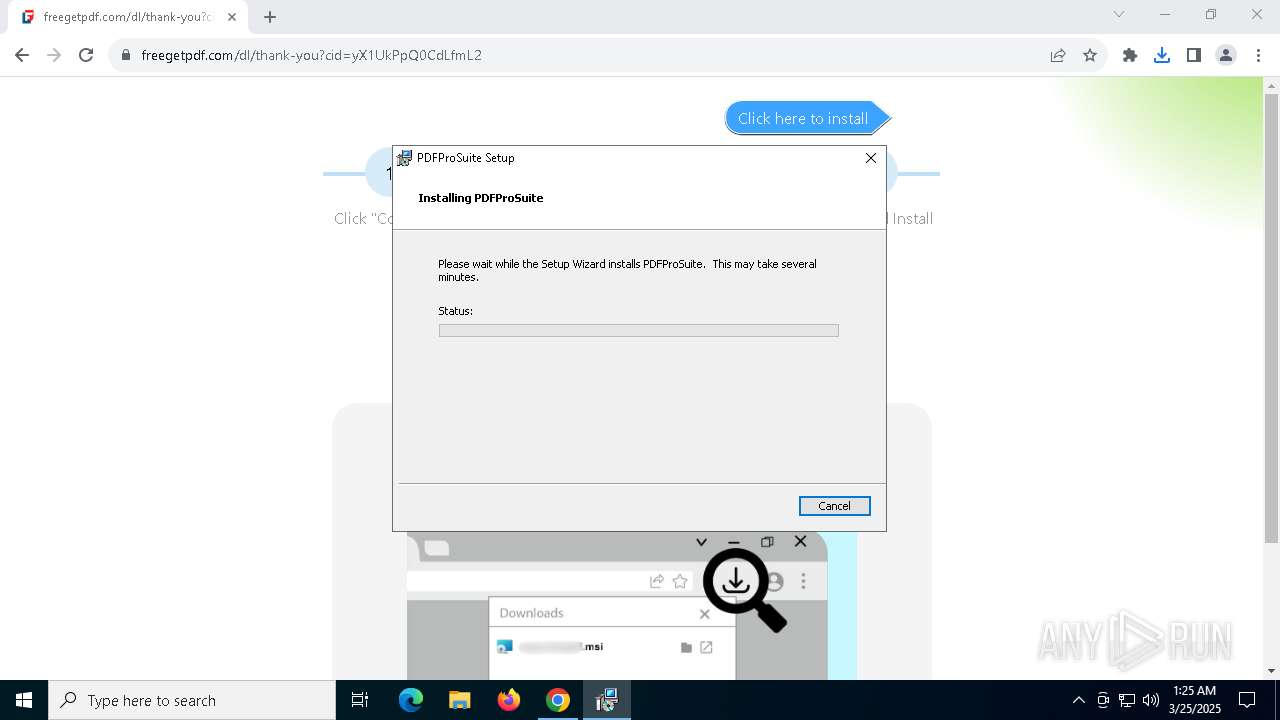
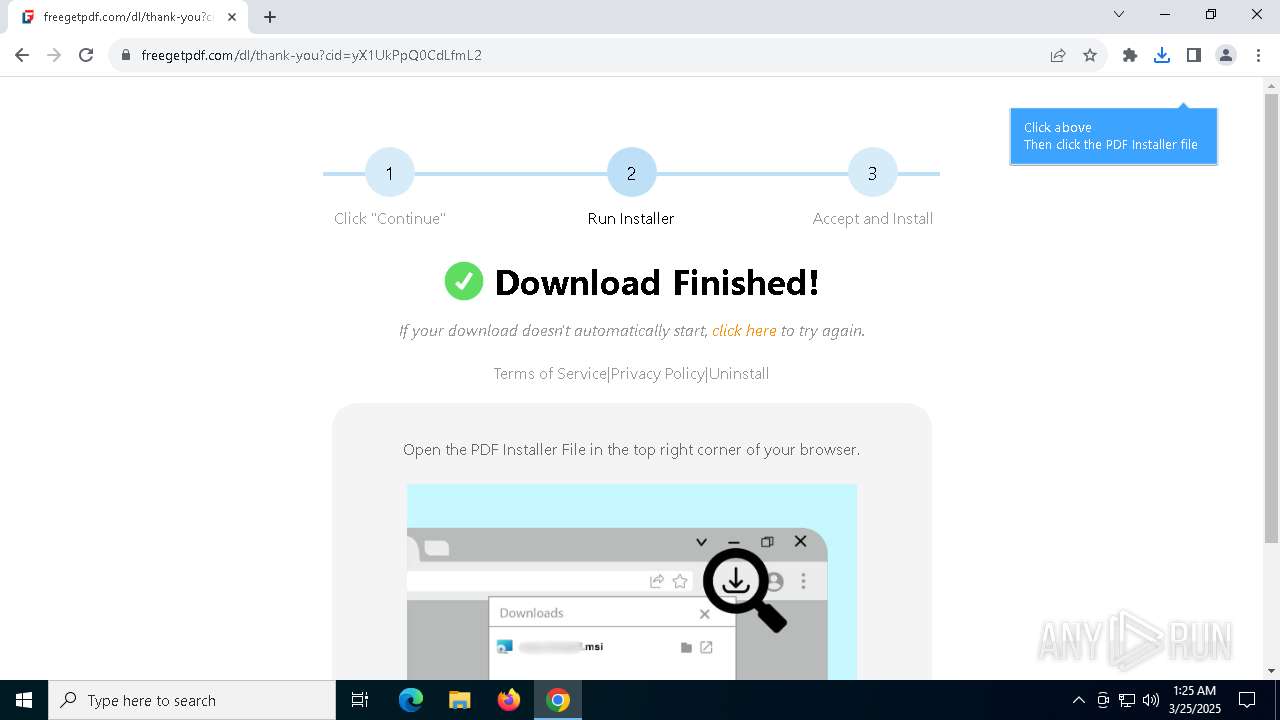
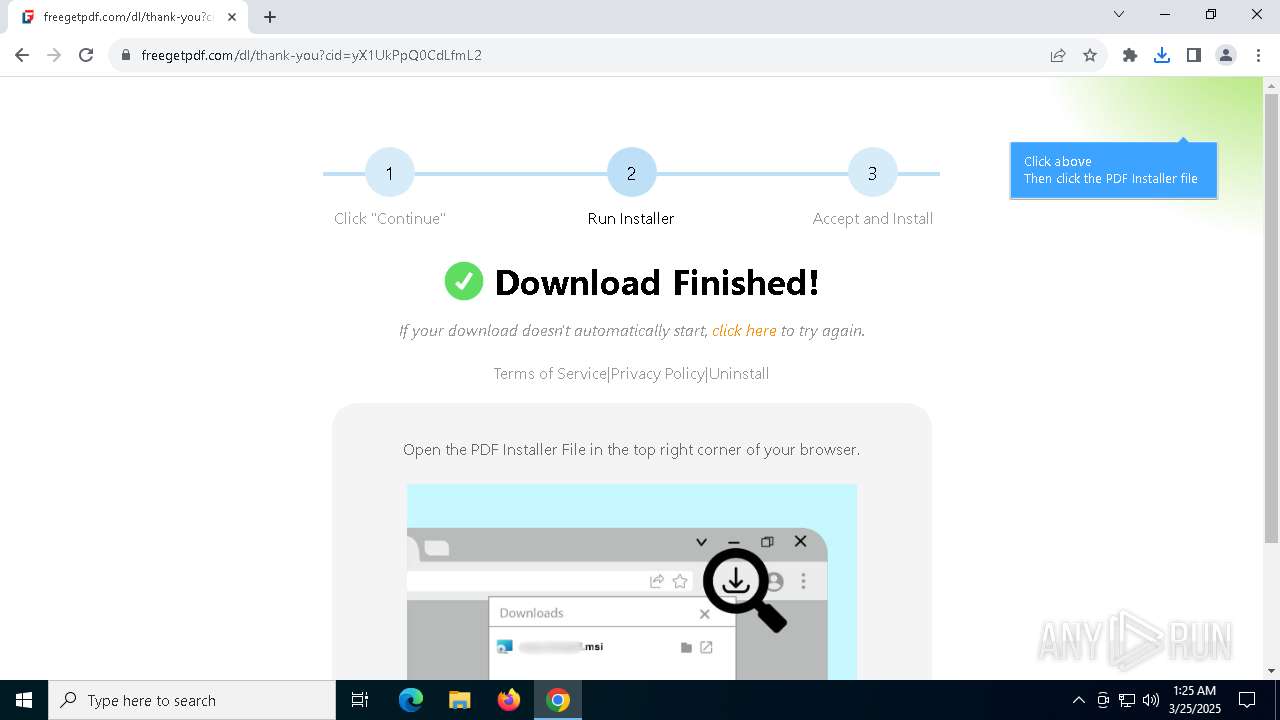
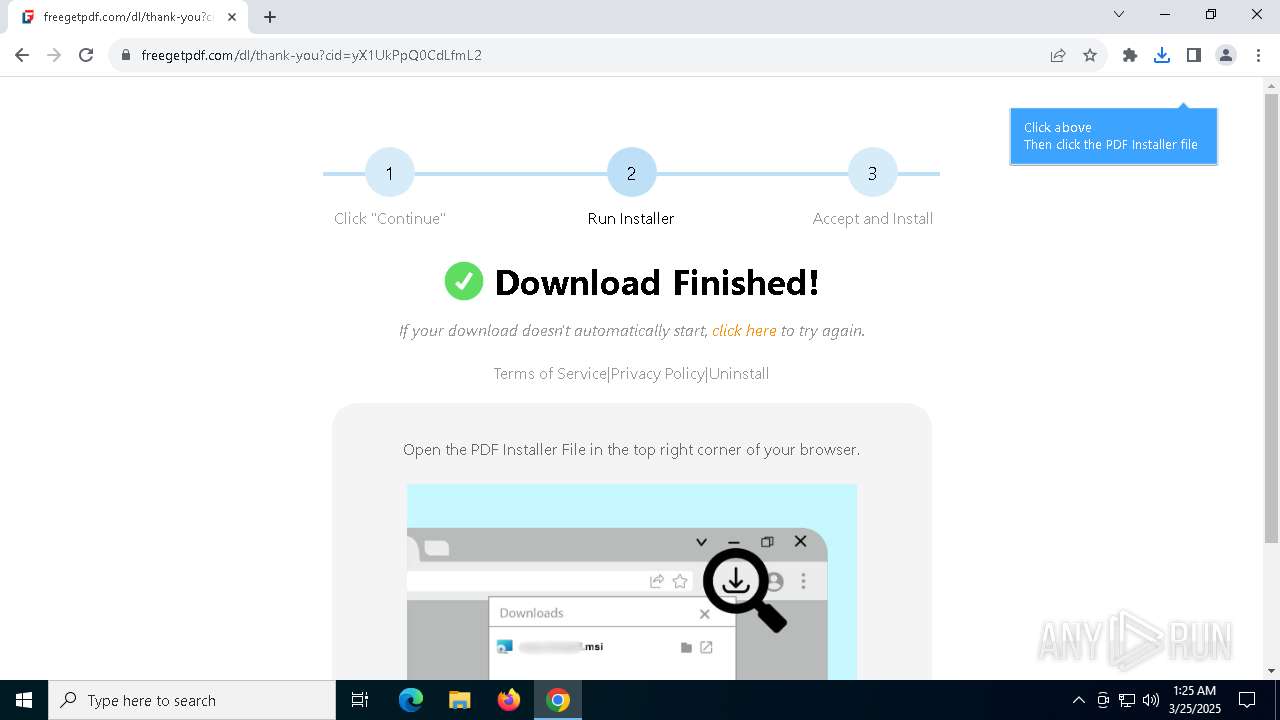
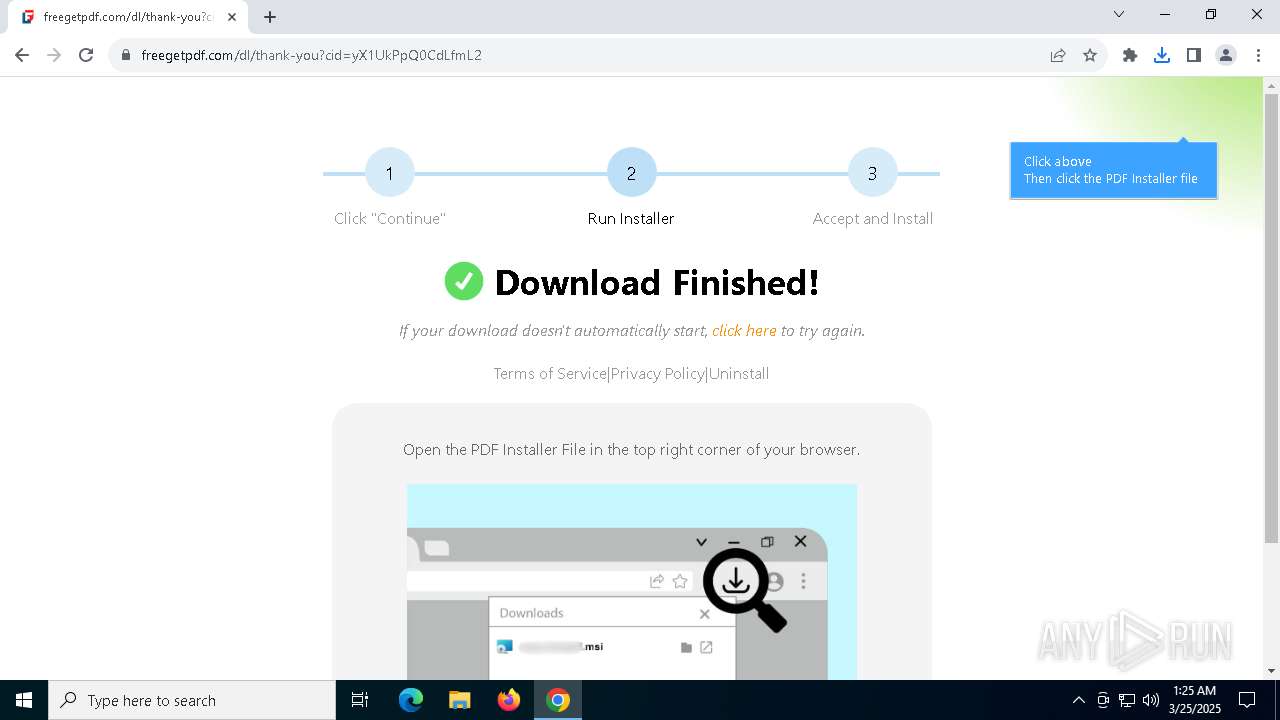
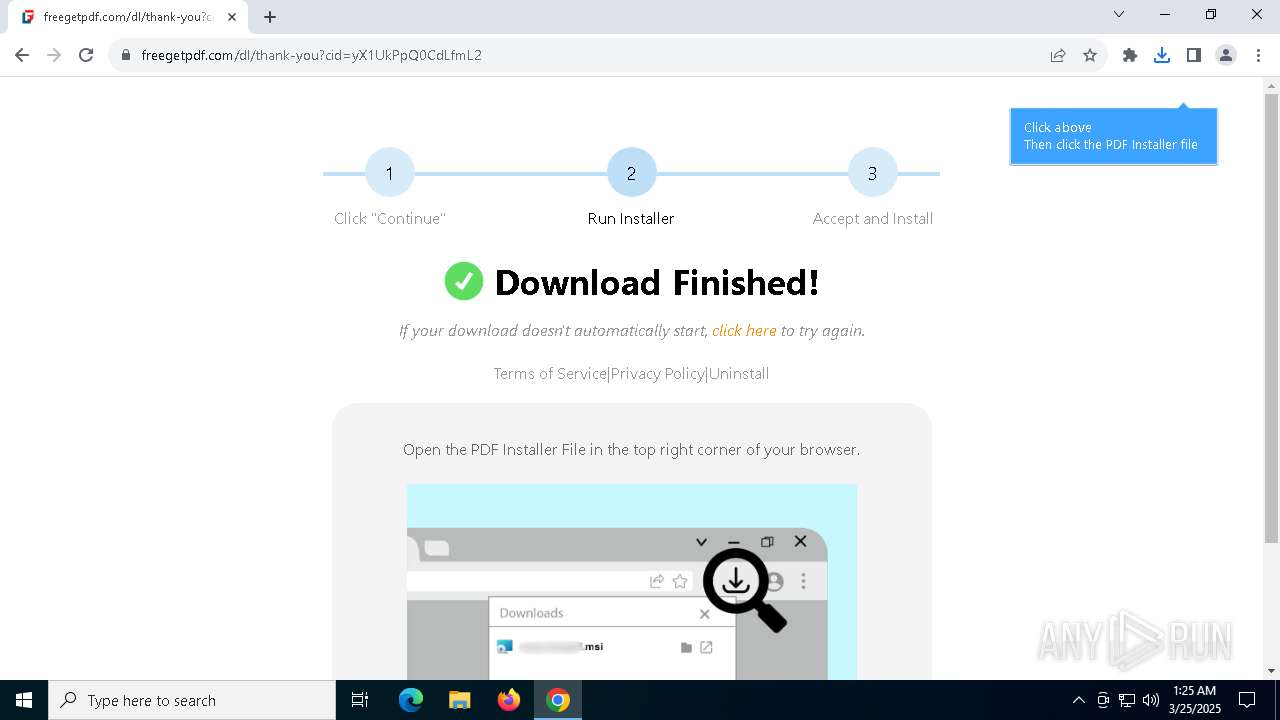
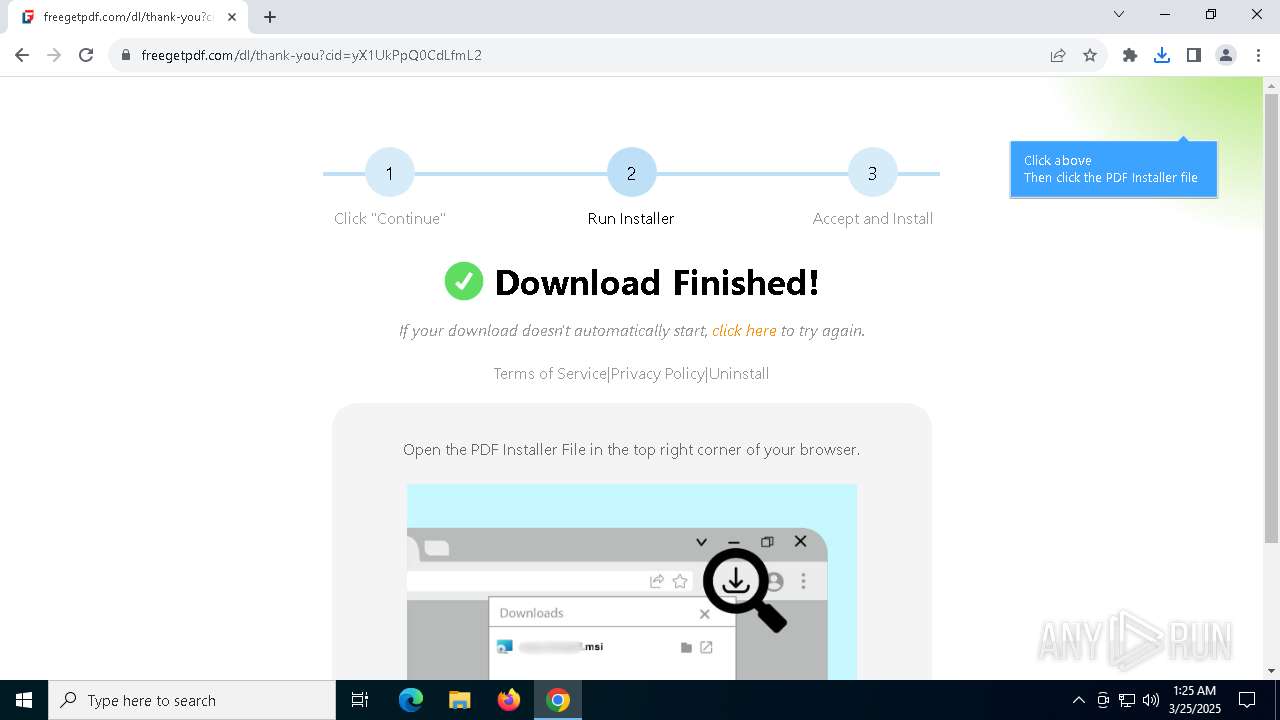
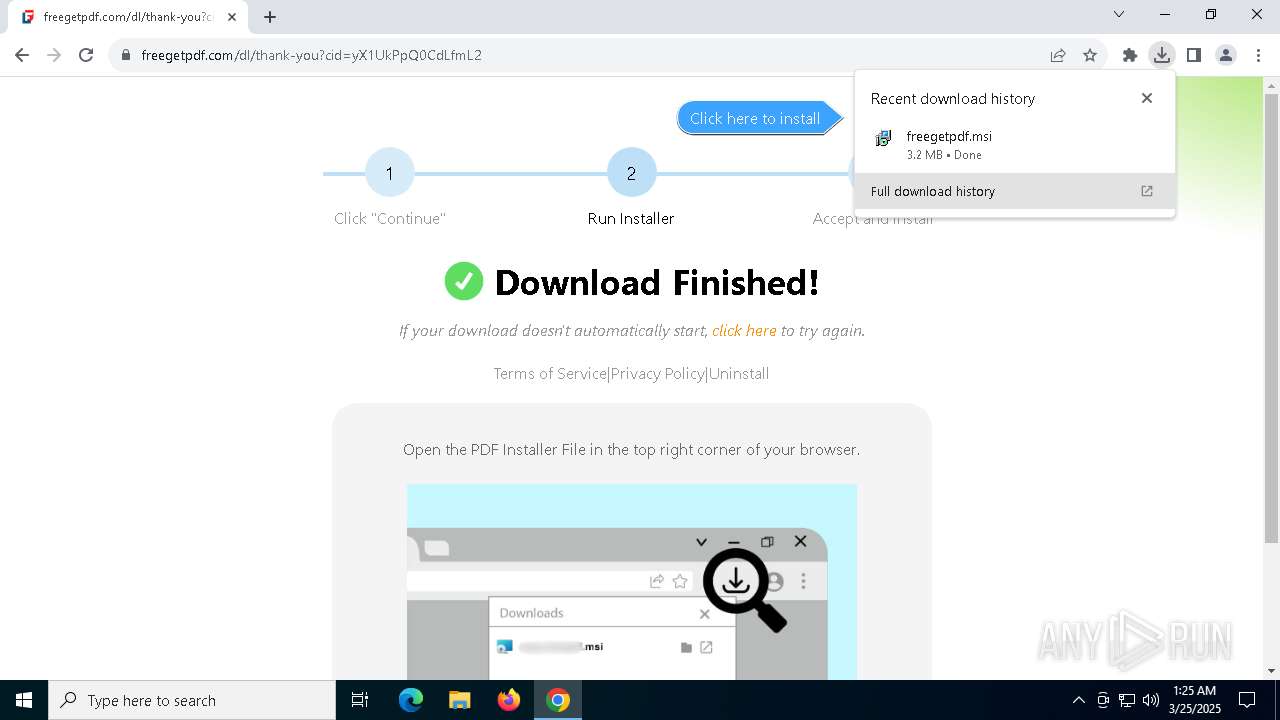
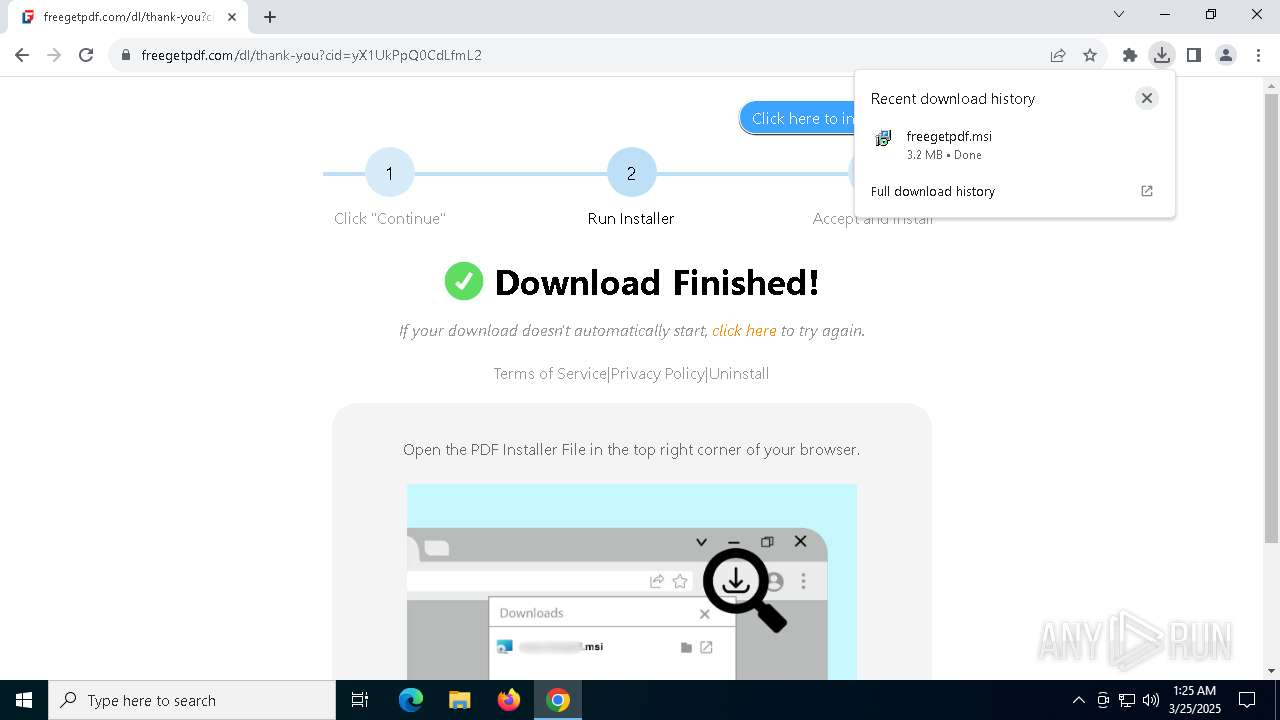
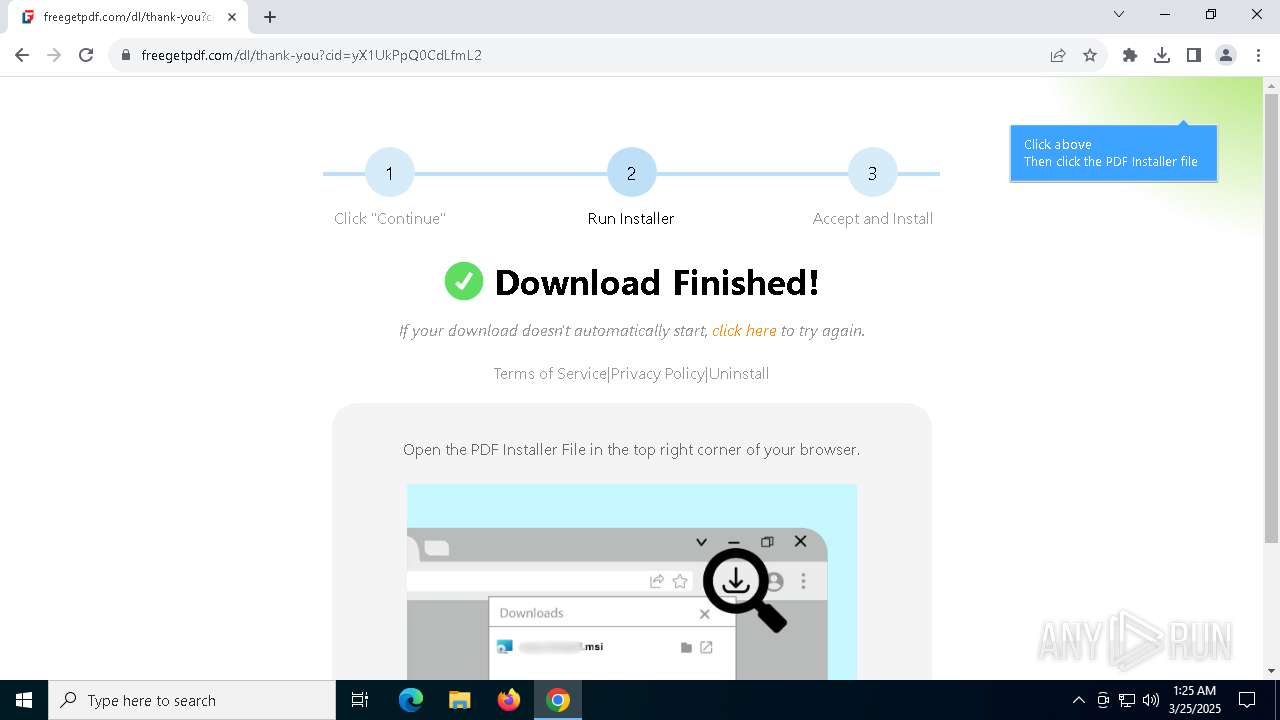
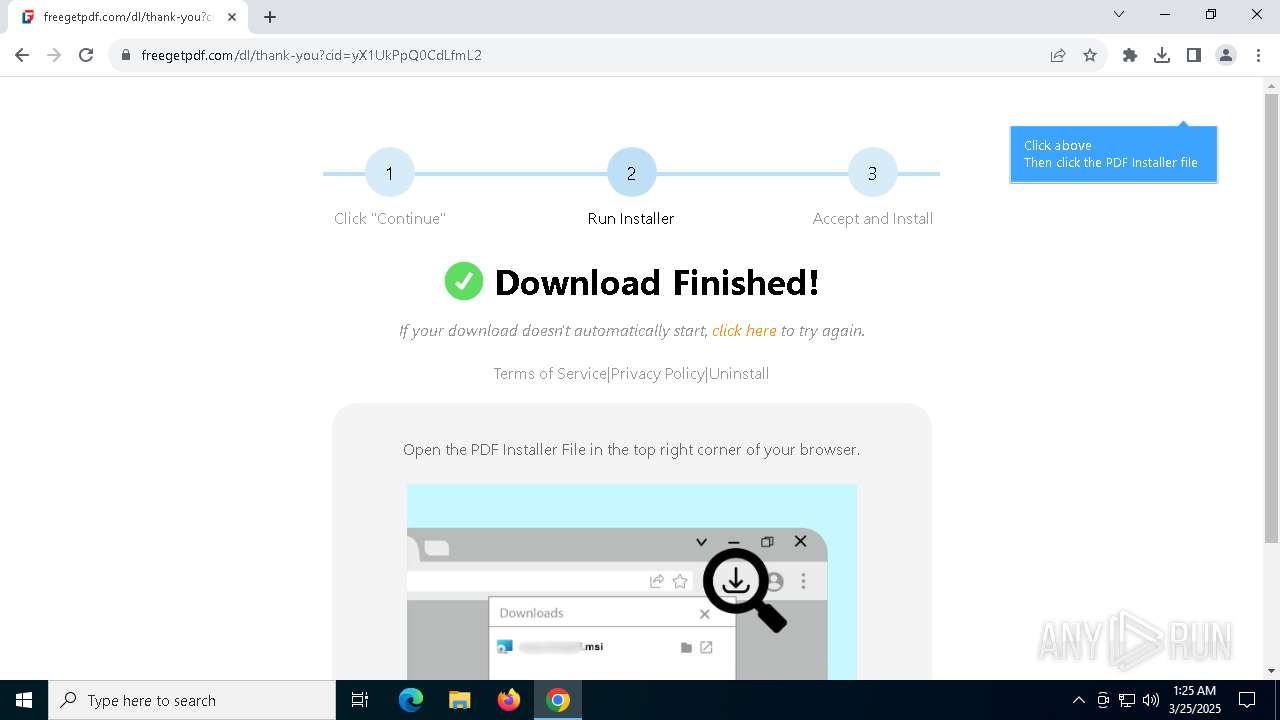
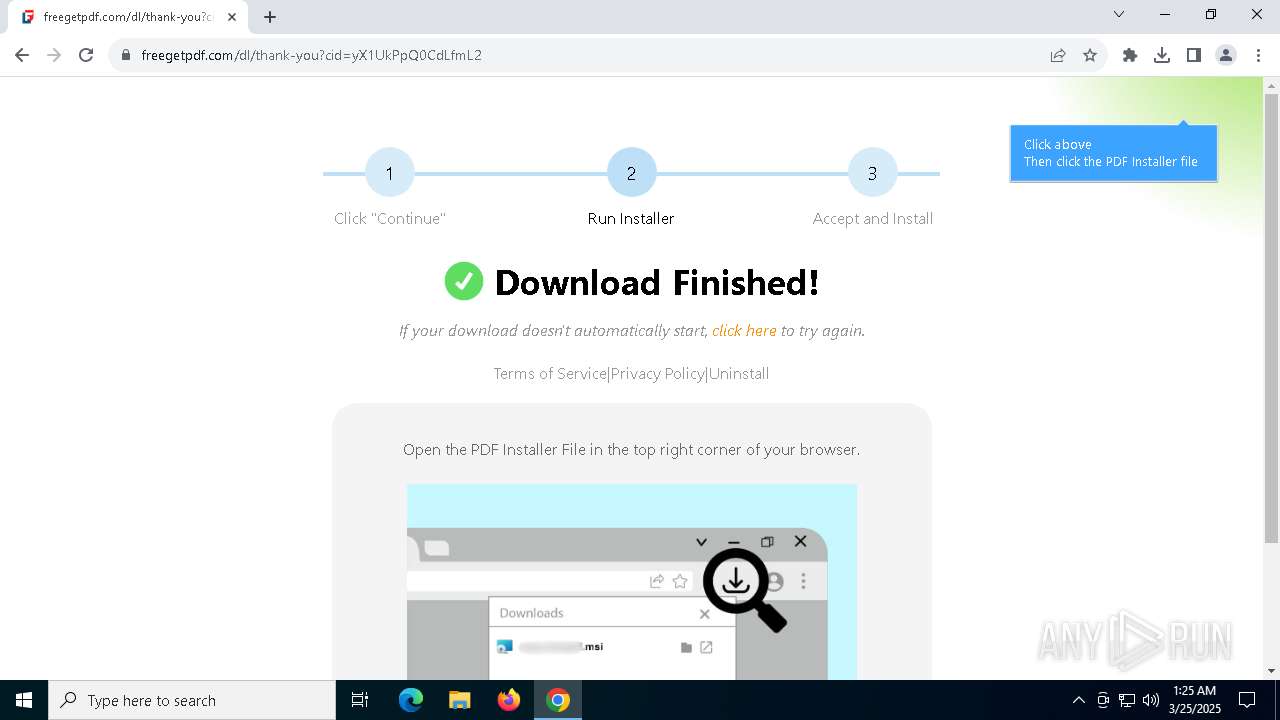
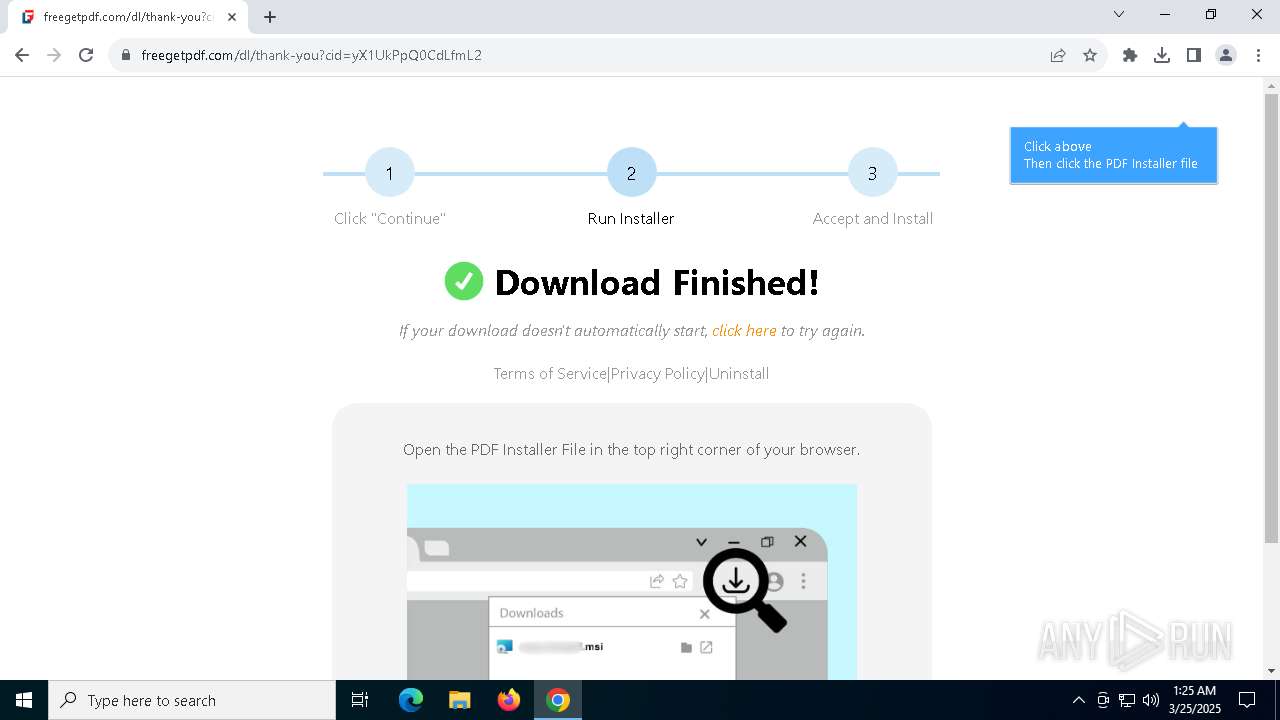
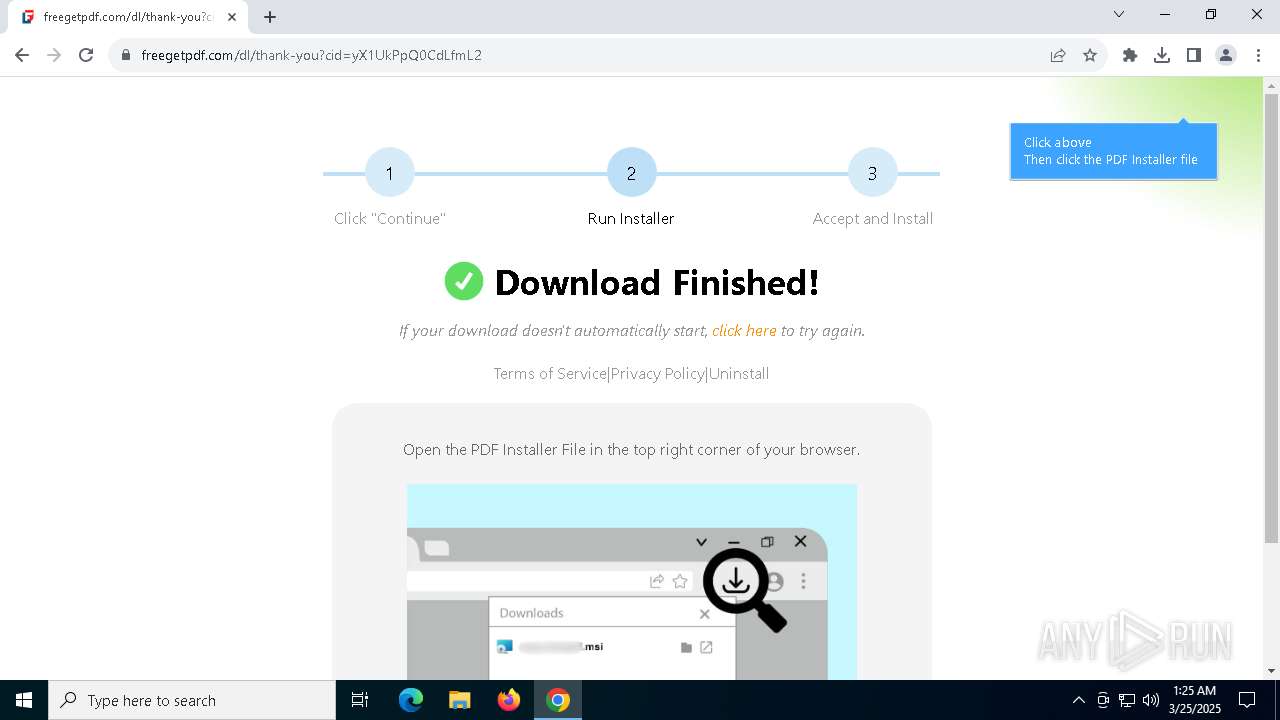
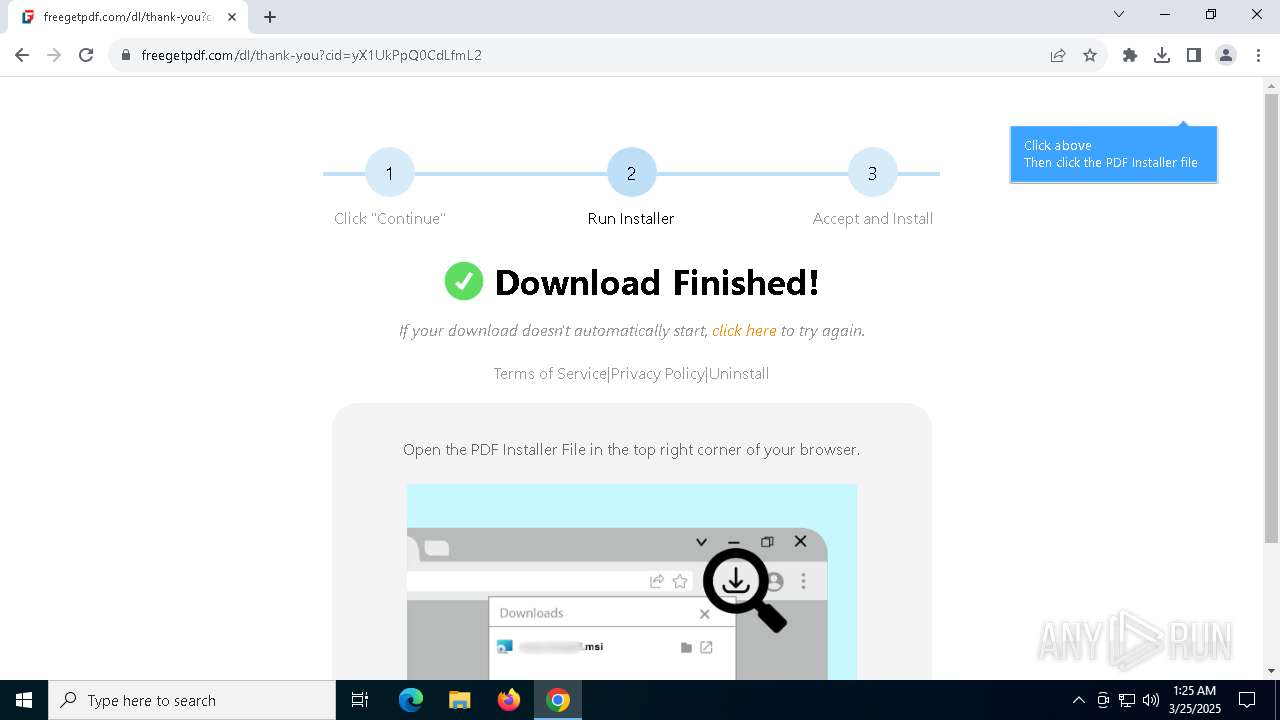
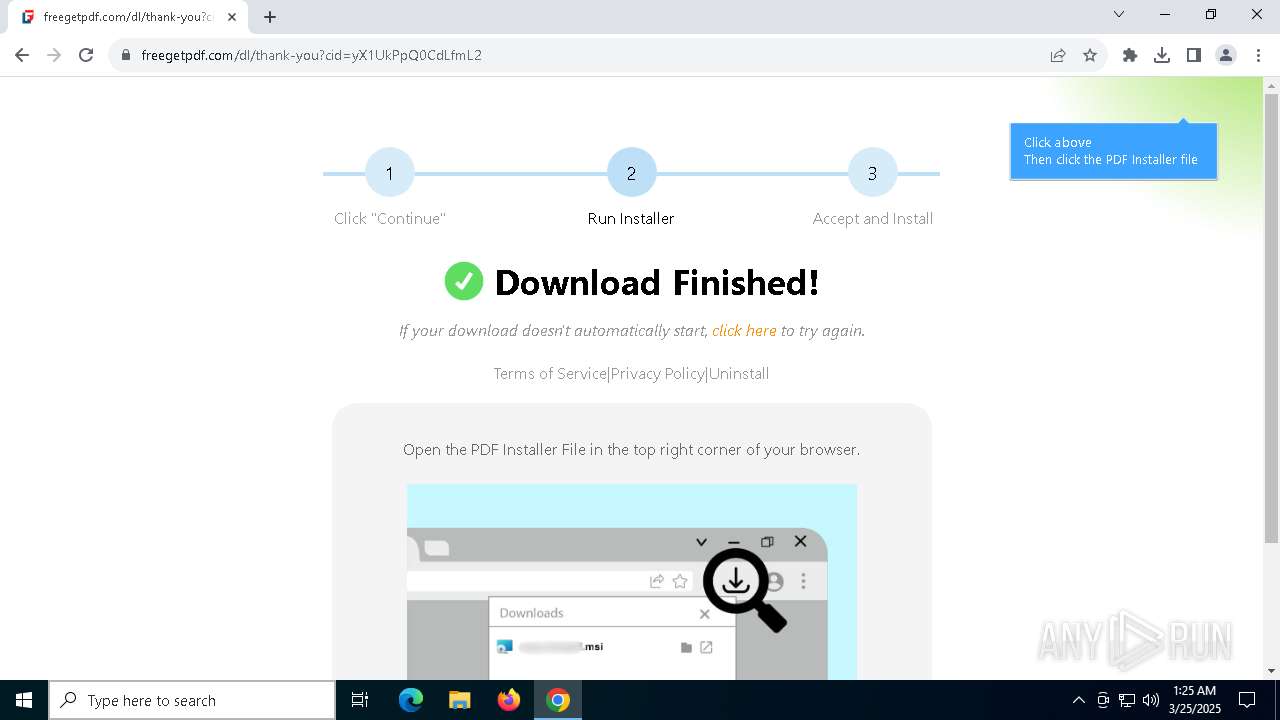
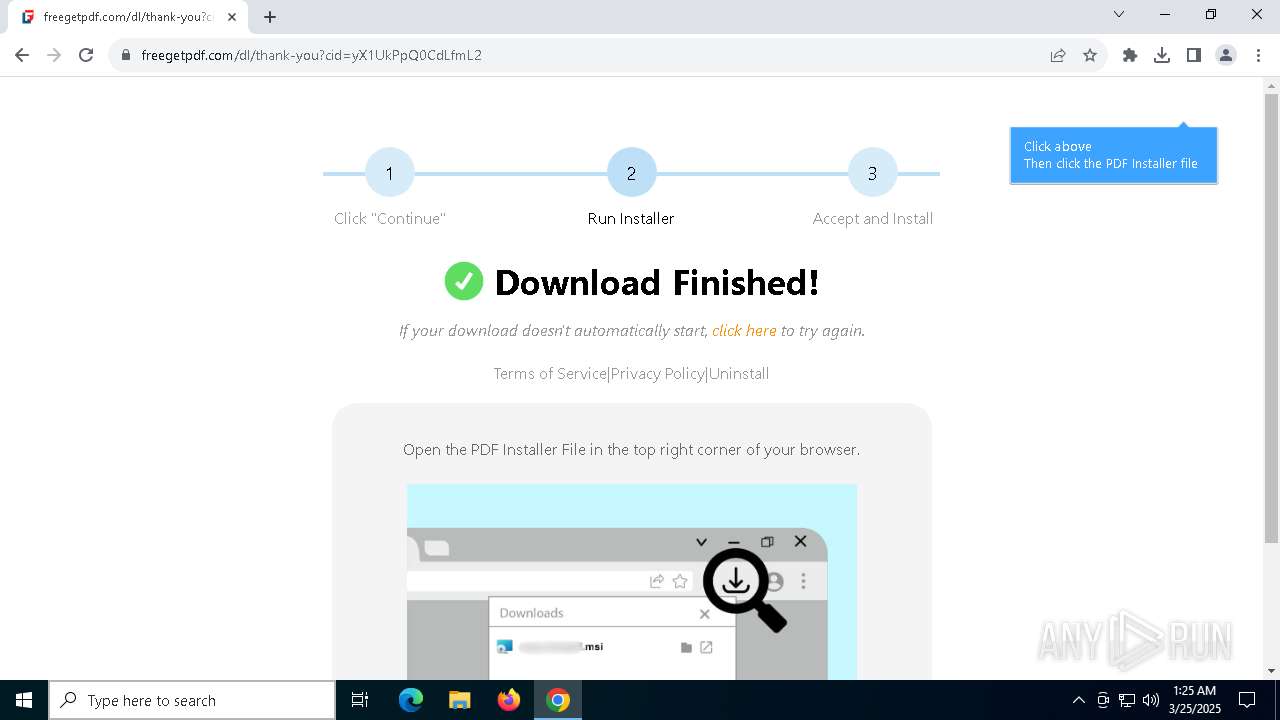
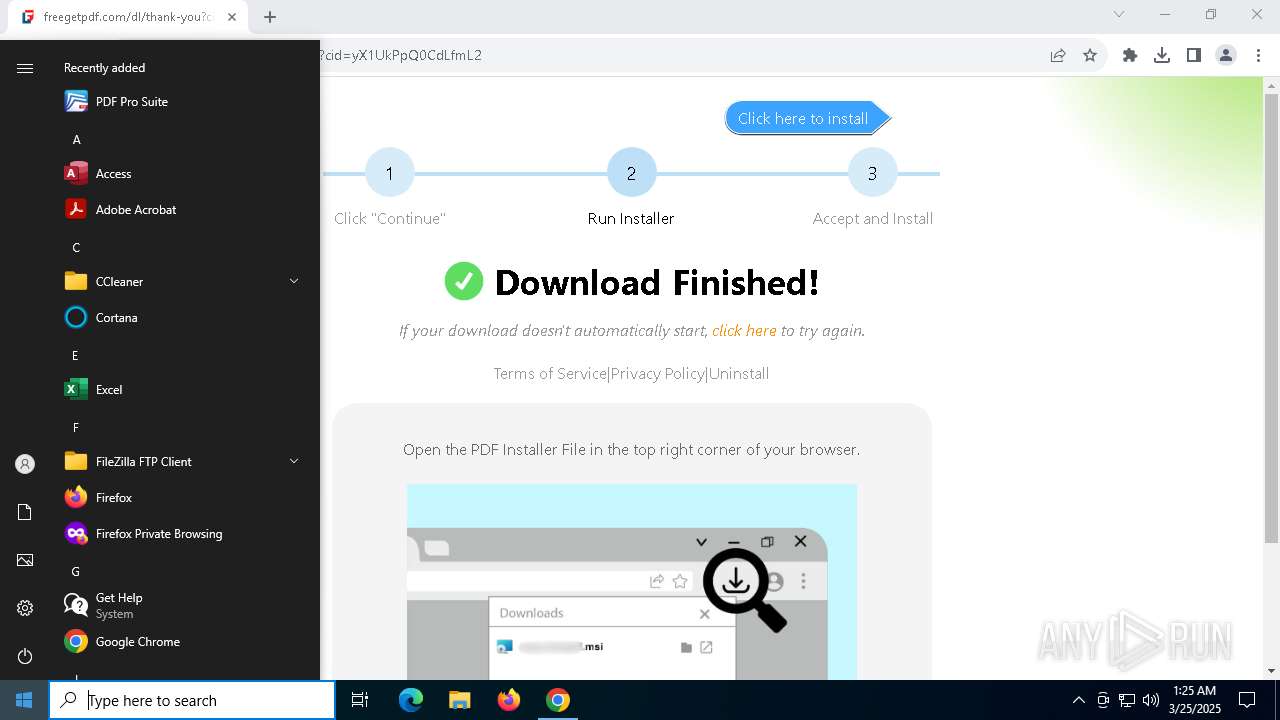
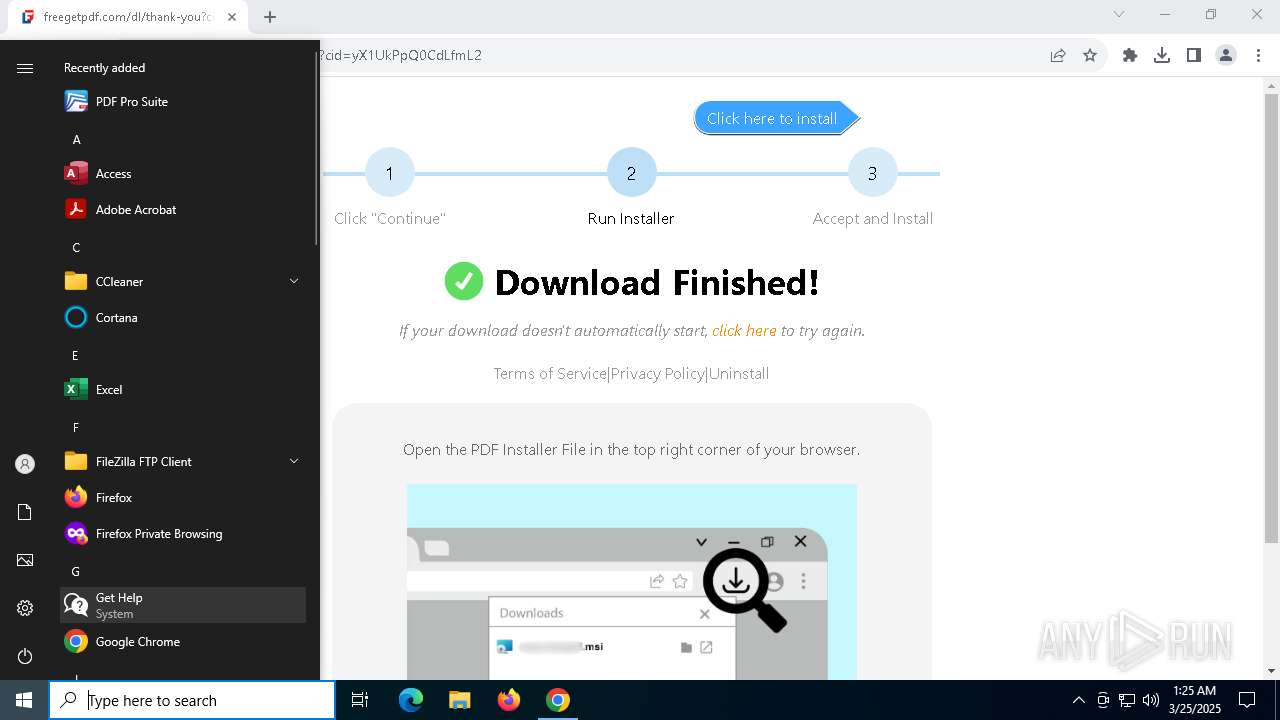
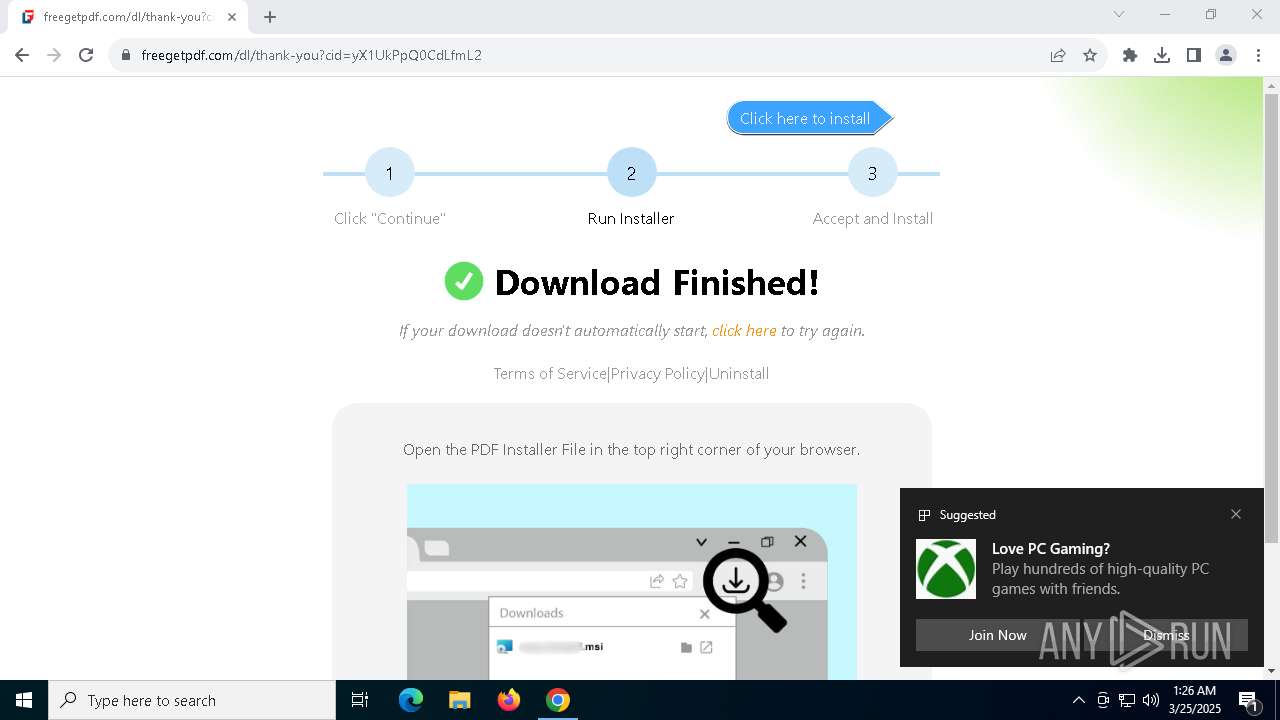
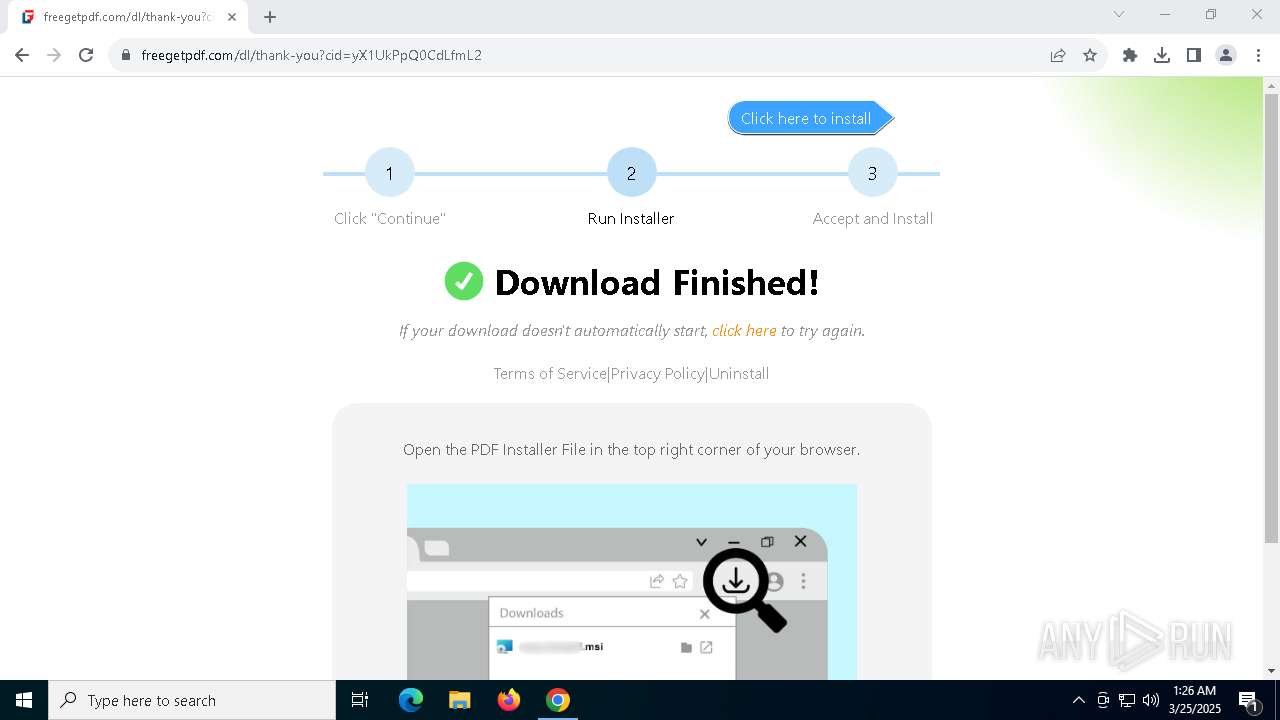
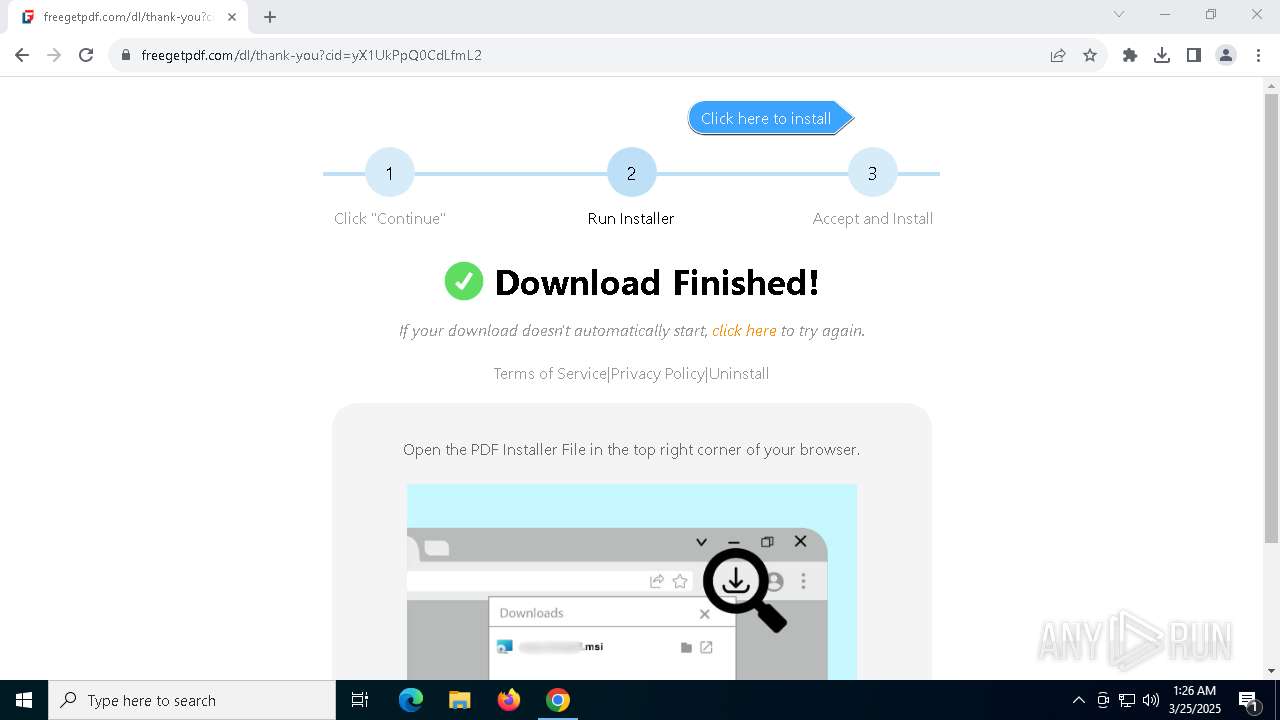
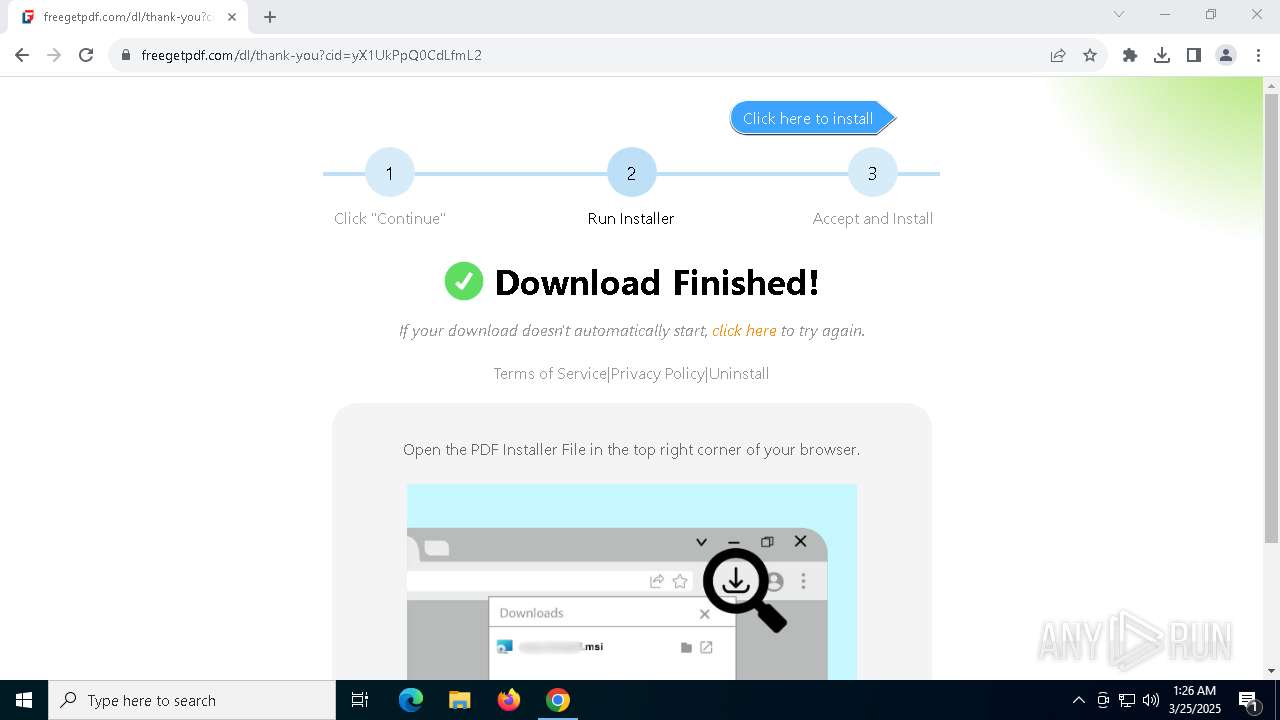
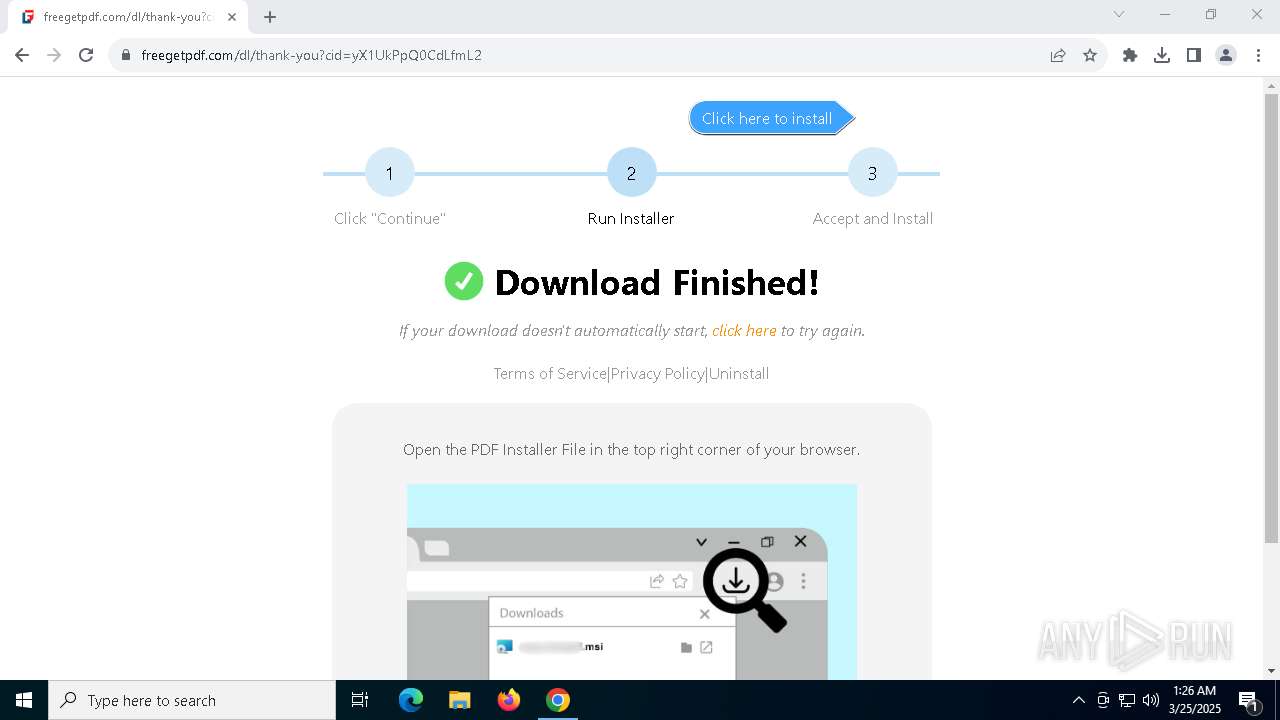
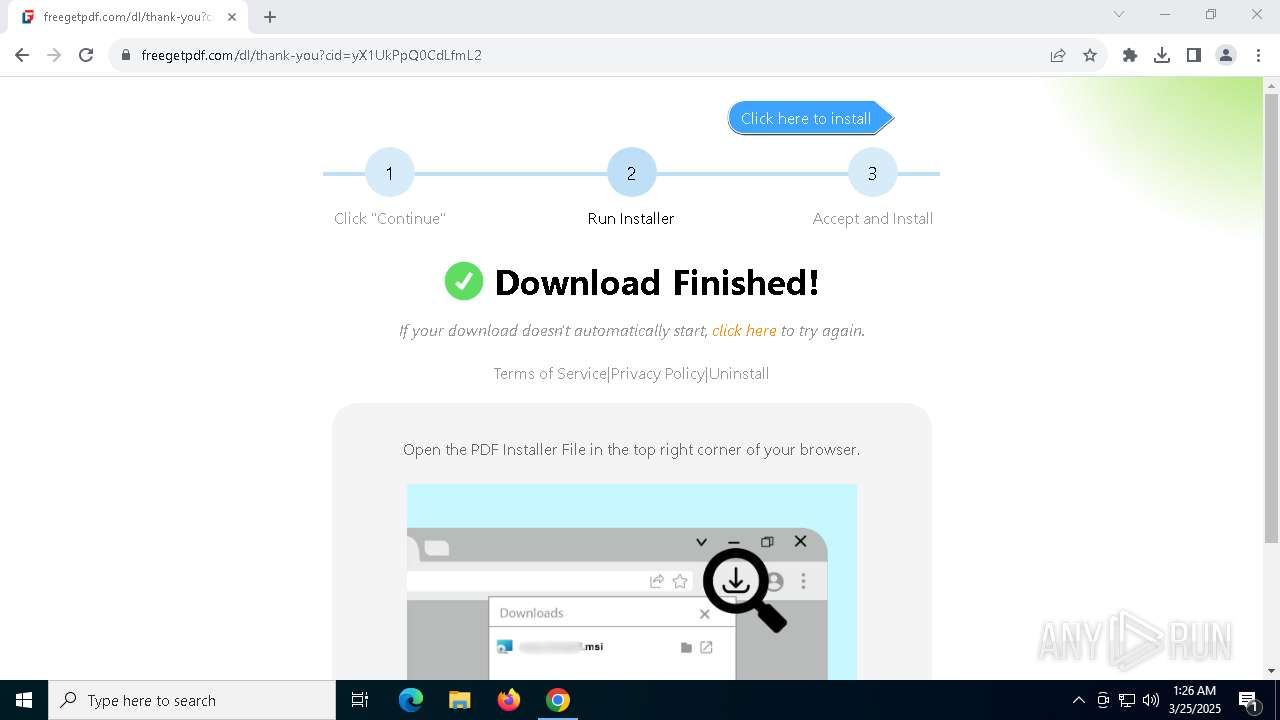
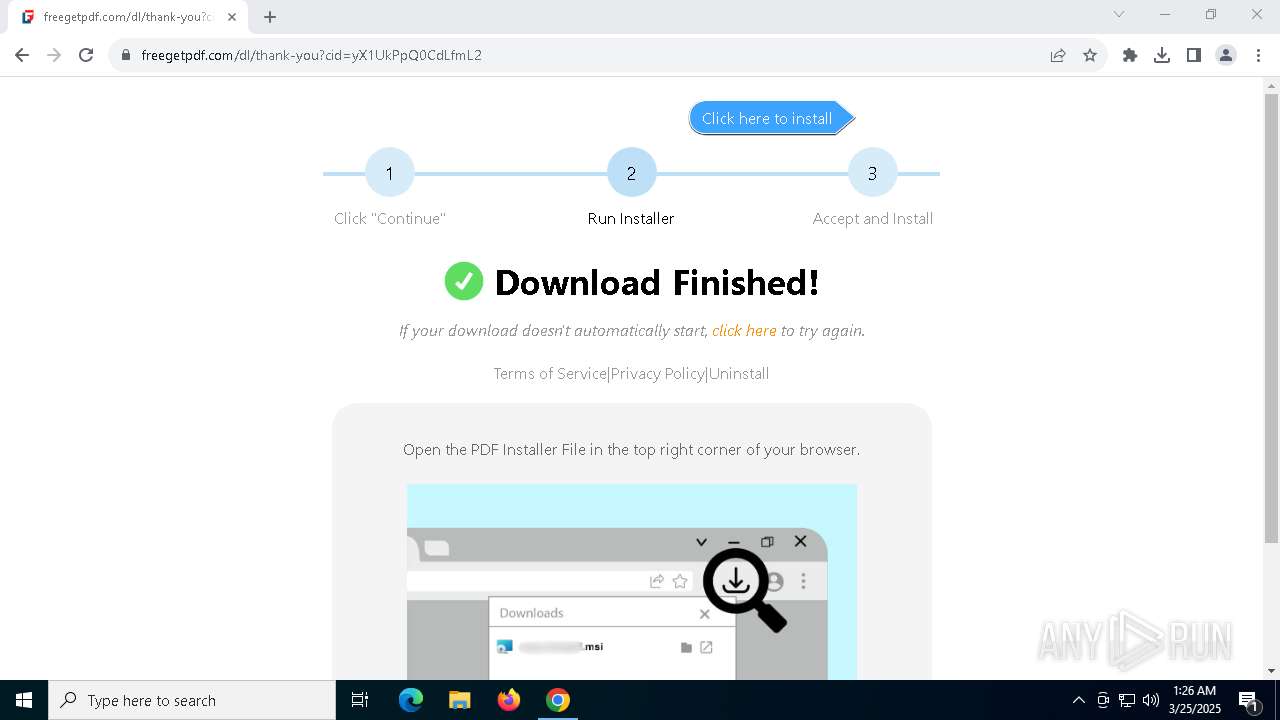
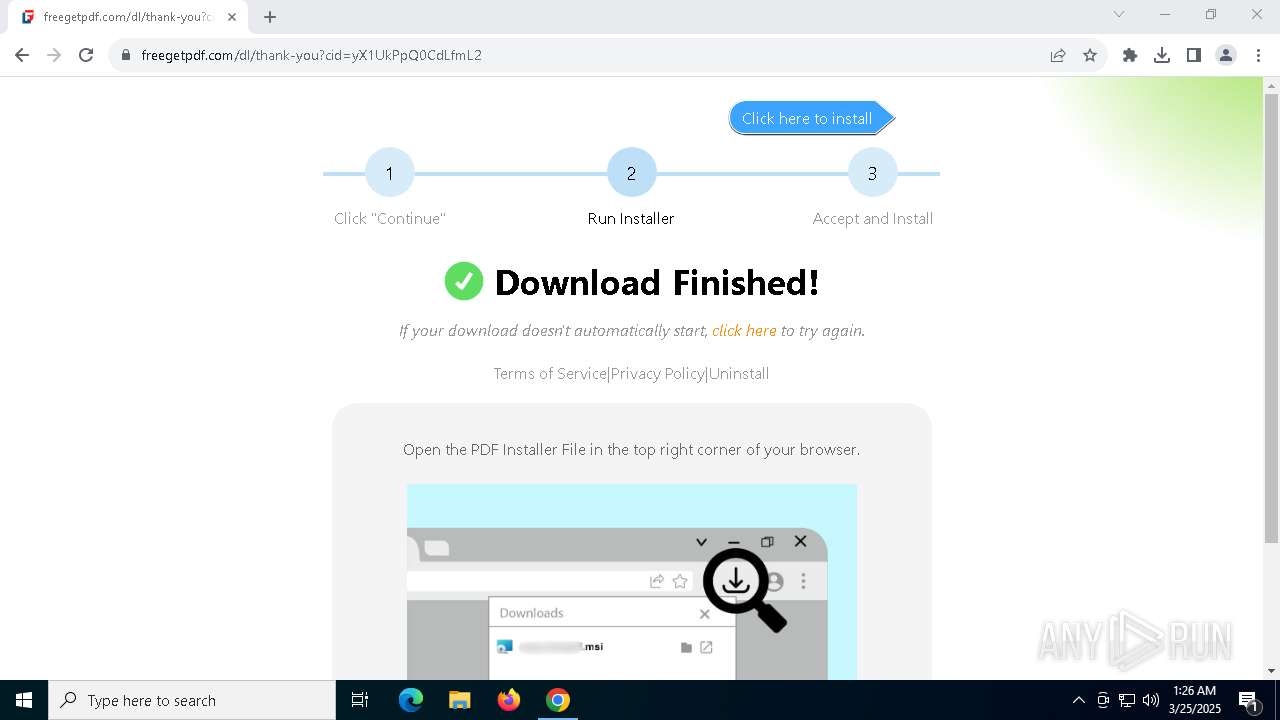
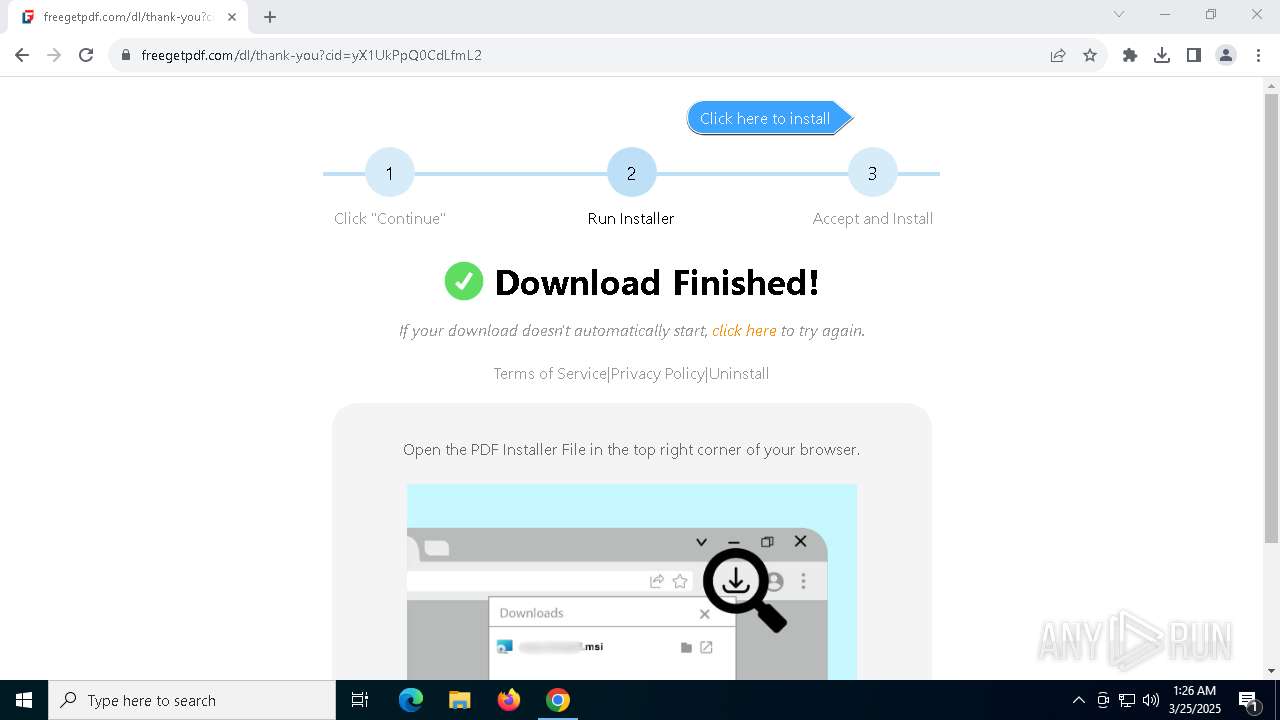
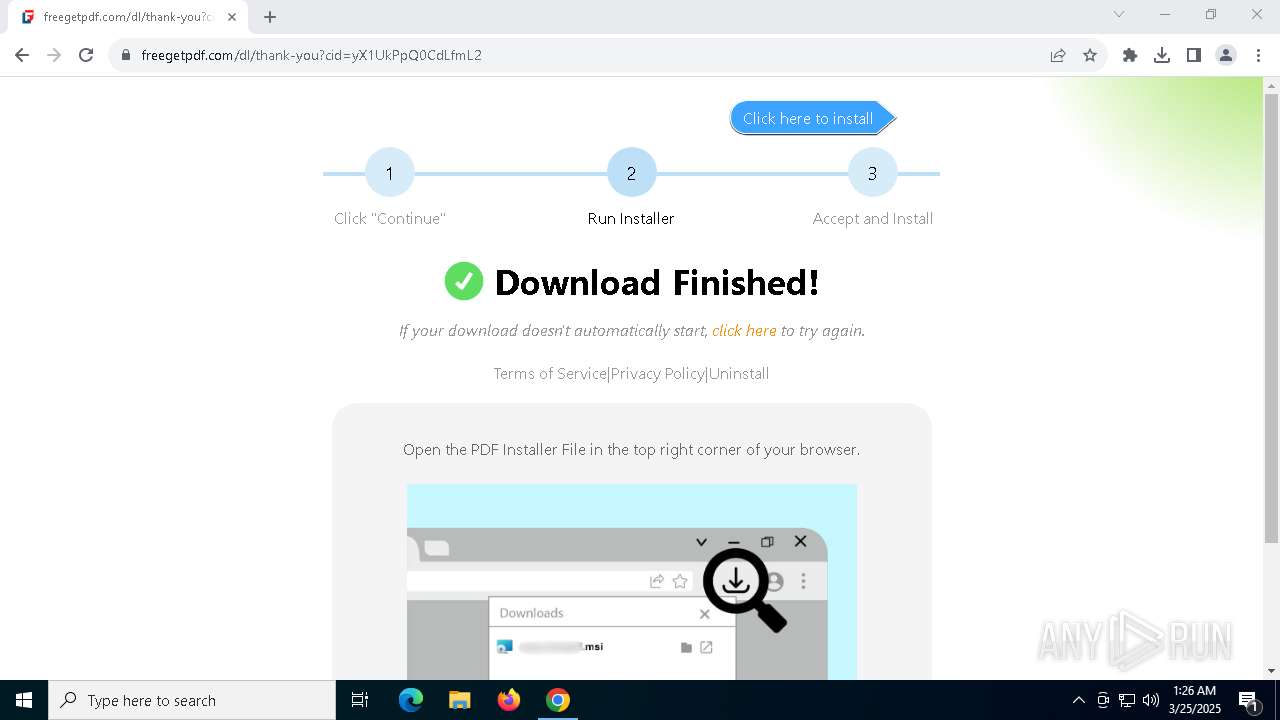
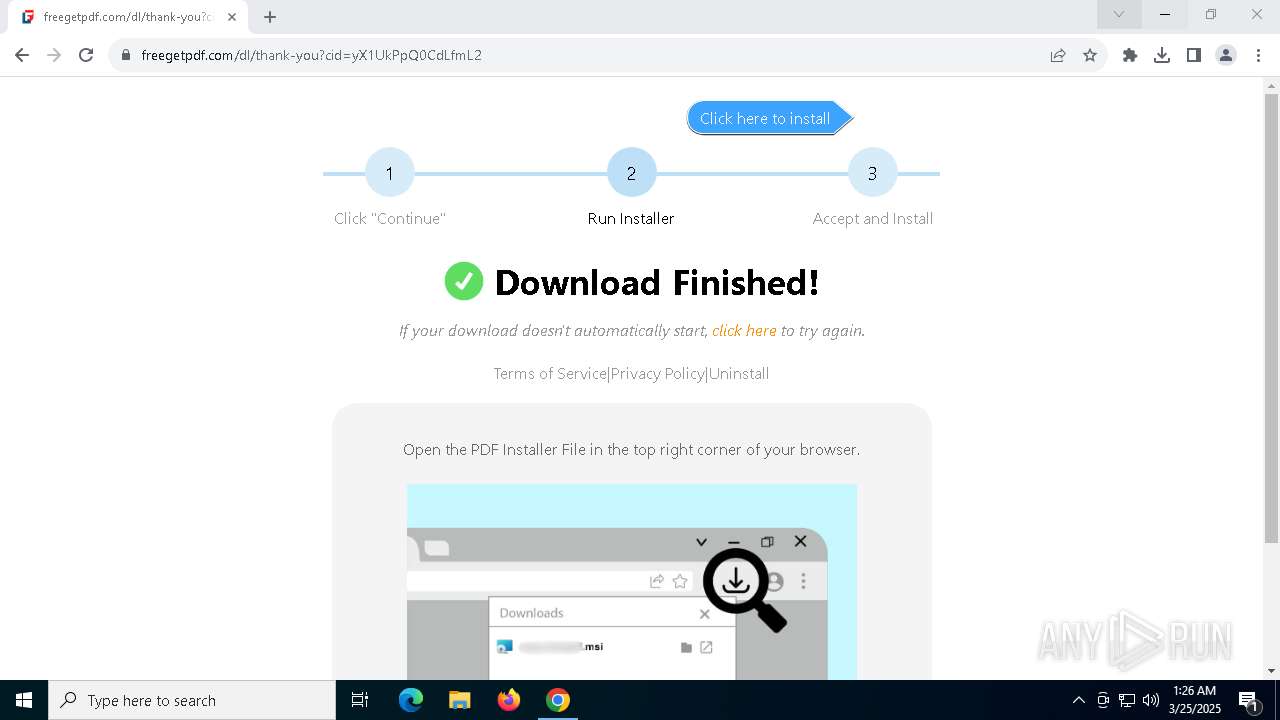
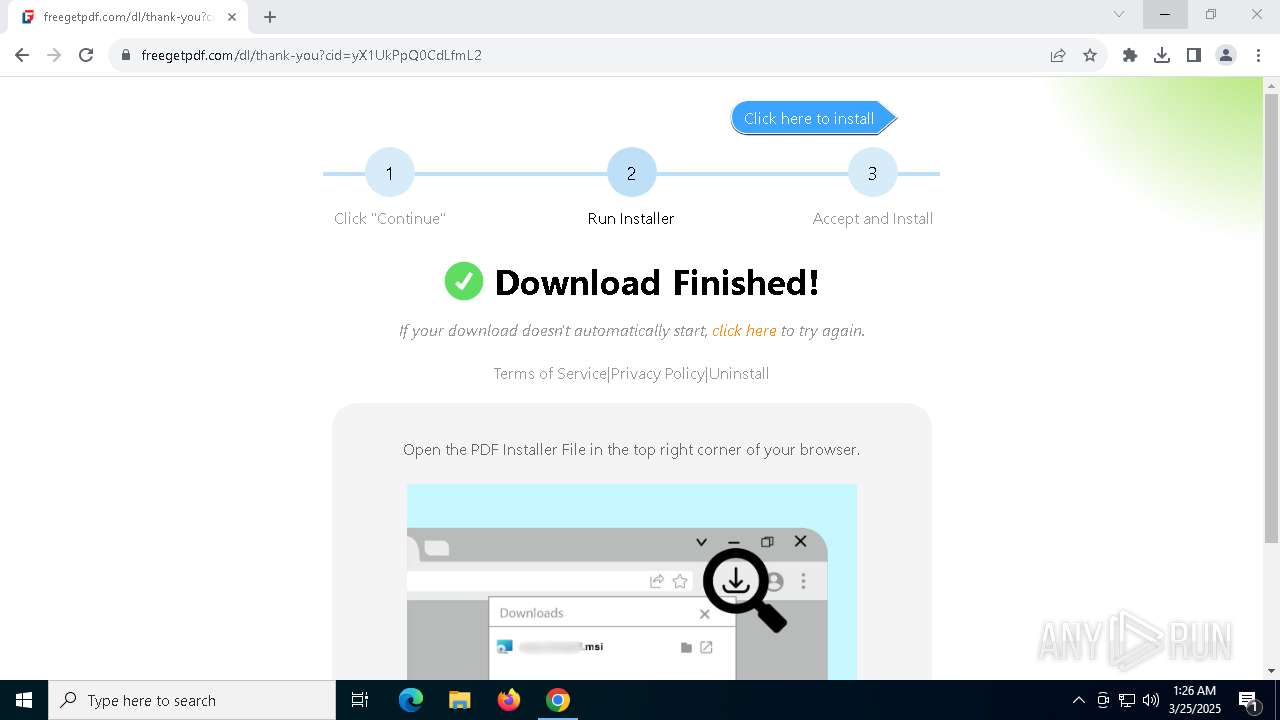
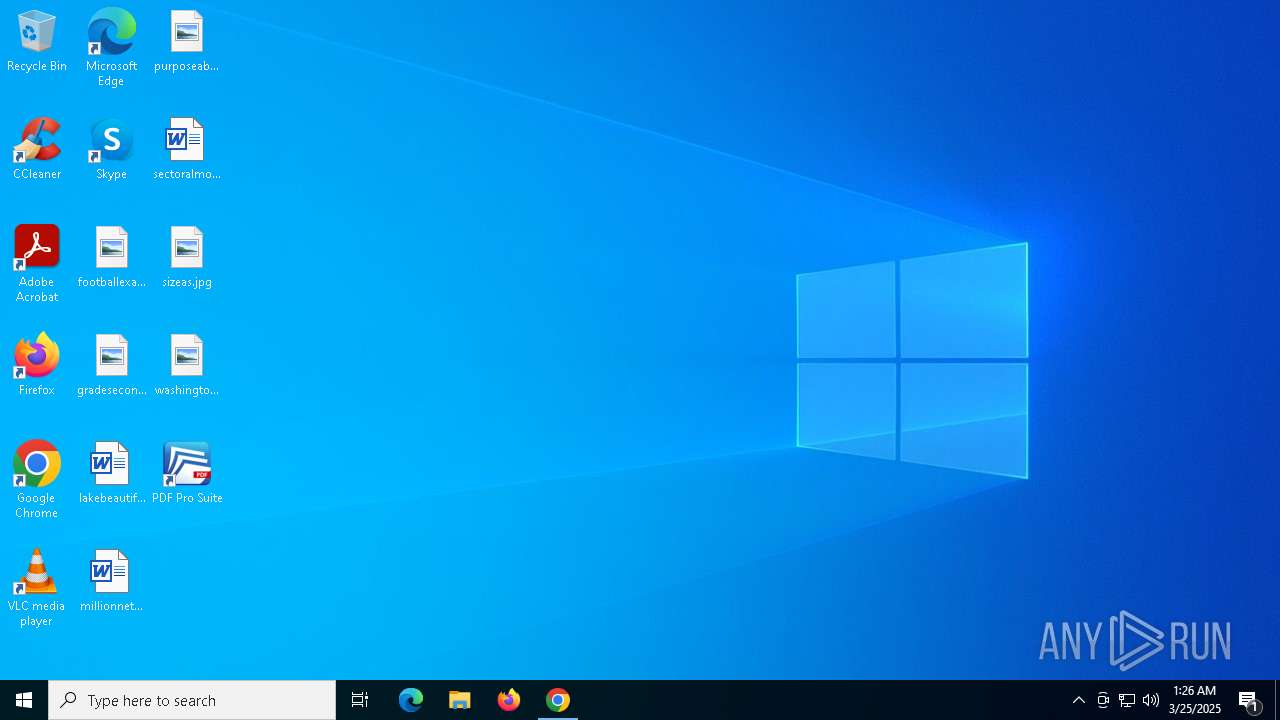
| URL: | https://freegetpdf.com/ |
| Full analysis: | https://app.any.run/tasks/aa0d2ac5-ff27-4265-8135-a70afcf37f8b |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 01:24:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E5DB5CBDF2AF2012E52DD183D4735548 |
| SHA1: | 2AB79BE580594E2C45C95A2312F8C28C1E2DEDAE |
| SHA256: | 1009FFA8506BEE3436A90F674AE879DE778589404F10828D26D99CB925166C42 |
| SSDEEP: | 3:N82ARrXGK3n:22ANGGn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 5680)
Detects AdvancedInstaller (YARA)
- msiexec.exe (PID: 4108)
- msiexec.exe (PID: 7360)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7360)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5228)
- MSI8D61.tmp (PID: 840)
- msiexec.exe (PID: 1056)
- ShellExperienceHost.exe (PID: 4464)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 1056)
Node.exe was dropped
- msiexec.exe (PID: 5228)
INFO
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 2140)
- msiexec.exe (PID: 7360)
- msiexec.exe (PID: 5228)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 5548)
- BackgroundTransferHost.exe (PID: 3100)
- BackgroundTransferHost.exe (PID: 2140)
- BackgroundTransferHost.exe (PID: 856)
- BackgroundTransferHost.exe (PID: 4436)
- msiexec.exe (PID: 4108)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 2140)
- msiexec.exe (PID: 5228)
- slui.exe (PID: 4572)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 2140)
- msiexec.exe (PID: 4108)
- msiexec.exe (PID: 7360)
- msiexec.exe (PID: 5228)
- slui.exe (PID: 8168)
- slui.exe (PID: 4572)
Executable content was dropped or overwritten
- chrome.exe (PID: 7392)
- msiexec.exe (PID: 4108)
- msiexec.exe (PID: 7360)
- chrome.exe (PID: 1764)
Autorun file from Downloads
- chrome.exe (PID: 7760)
- chrome.exe (PID: 7392)
Reads Microsoft Office registry keys
- chrome.exe (PID: 7392)
Application launched itself
- chrome.exe (PID: 7392)
Checks supported languages
- msiexec.exe (PID: 7360)
- msiexec.exe (PID: 1056)
- msiexec.exe (PID: 5228)
- MSI8D61.tmp (PID: 840)
- pdfprosuite.exe (PID: 7144)
- pdfprosuite.exe (PID: 2316)
- ShellExperienceHost.exe (PID: 4464)
- pdfprosuite.exe (PID: 4200)
Reads the computer name
- msiexec.exe (PID: 7360)
- msiexec.exe (PID: 1056)
- msiexec.exe (PID: 5228)
- MSI8D61.tmp (PID: 840)
- ShellExperienceHost.exe (PID: 4464)
The sample compiled with english language support
- msiexec.exe (PID: 4108)
- msiexec.exe (PID: 7360)
- msiexec.exe (PID: 5228)
- chrome.exe (PID: 1764)
Manages system restore points
- SrTasks.exe (PID: 5392)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7360)
- msiexec.exe (PID: 5228)
Reads Environment values
- msiexec.exe (PID: 5228)
- msiexec.exe (PID: 1056)
- pdfprosuite.exe (PID: 7144)
- pdfprosuite.exe (PID: 2316)
- pdfprosuite.exe (PID: 4200)
Creates a software uninstall entry
- msiexec.exe (PID: 7360)
Starts application with an unusual extension
- msiexec.exe (PID: 7360)
Process checks computer location settings
- msiexec.exe (PID: 1056)
- MSI8D61.tmp (PID: 840)
Reads product name
- pdfprosuite.exe (PID: 7144)
- pdfprosuite.exe (PID: 2316)
- pdfprosuite.exe (PID: 4200)
Manual execution by a user
- cmd.exe (PID: 2656)
- cmd.exe (PID: 132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
194
Monitored processes
50
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\WINDOWS\system32\cmd.exe" /c "start /min /d "C:\Users\admin\AppData\Local\PDFProSuite\" PDFProSuite ." | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3104 --field-trial-handle=1840,i,4176337598687587244,13470699741281501532,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3136 --field-trial-handle=1840,i,4176337598687587244,13470699741281501532,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
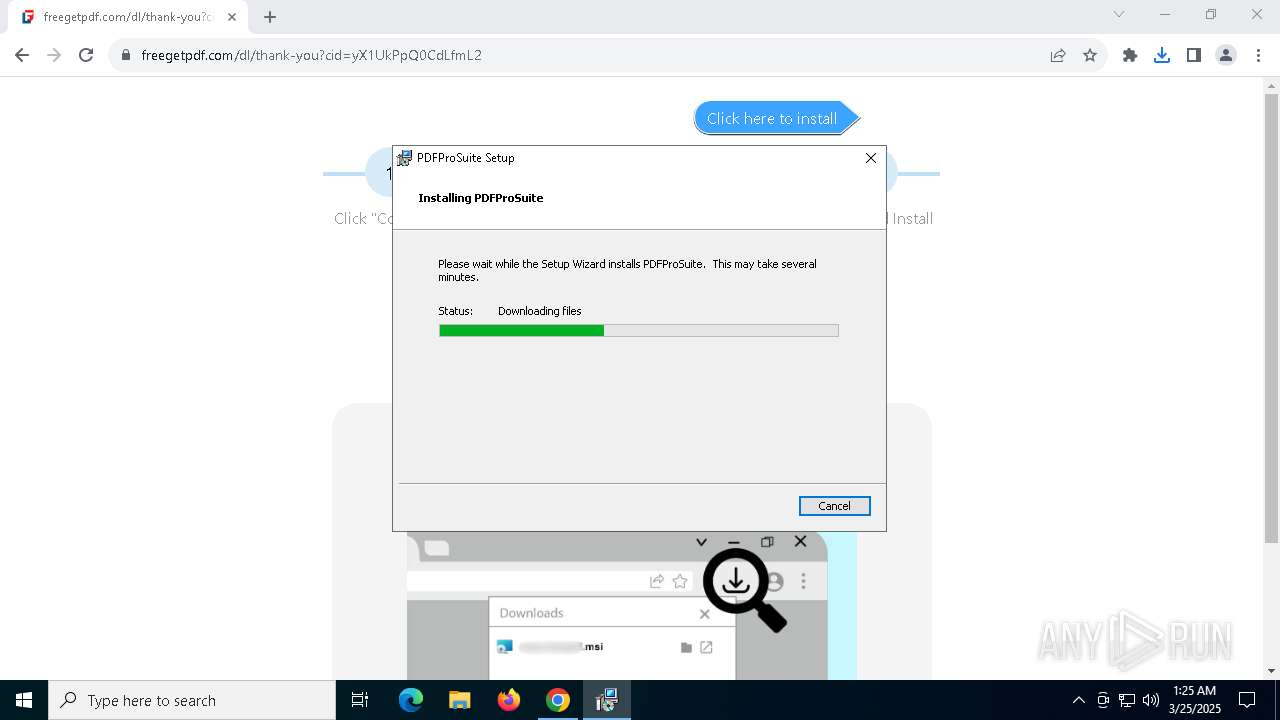
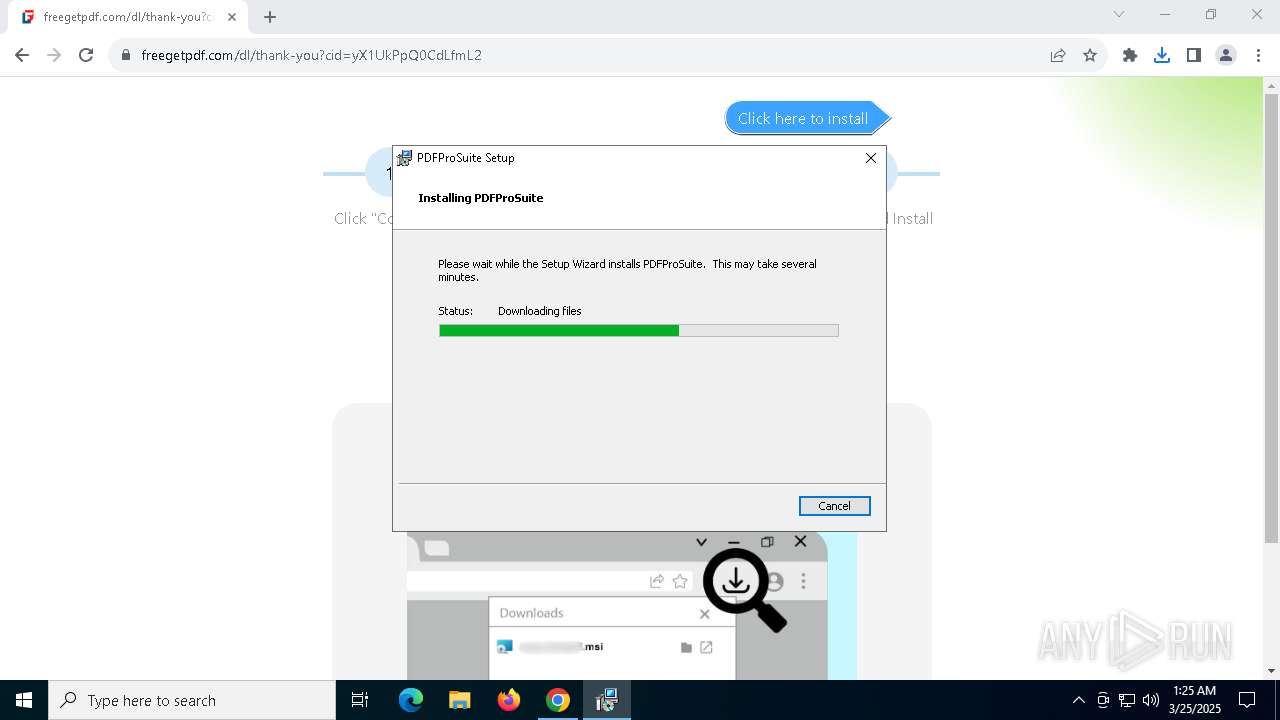
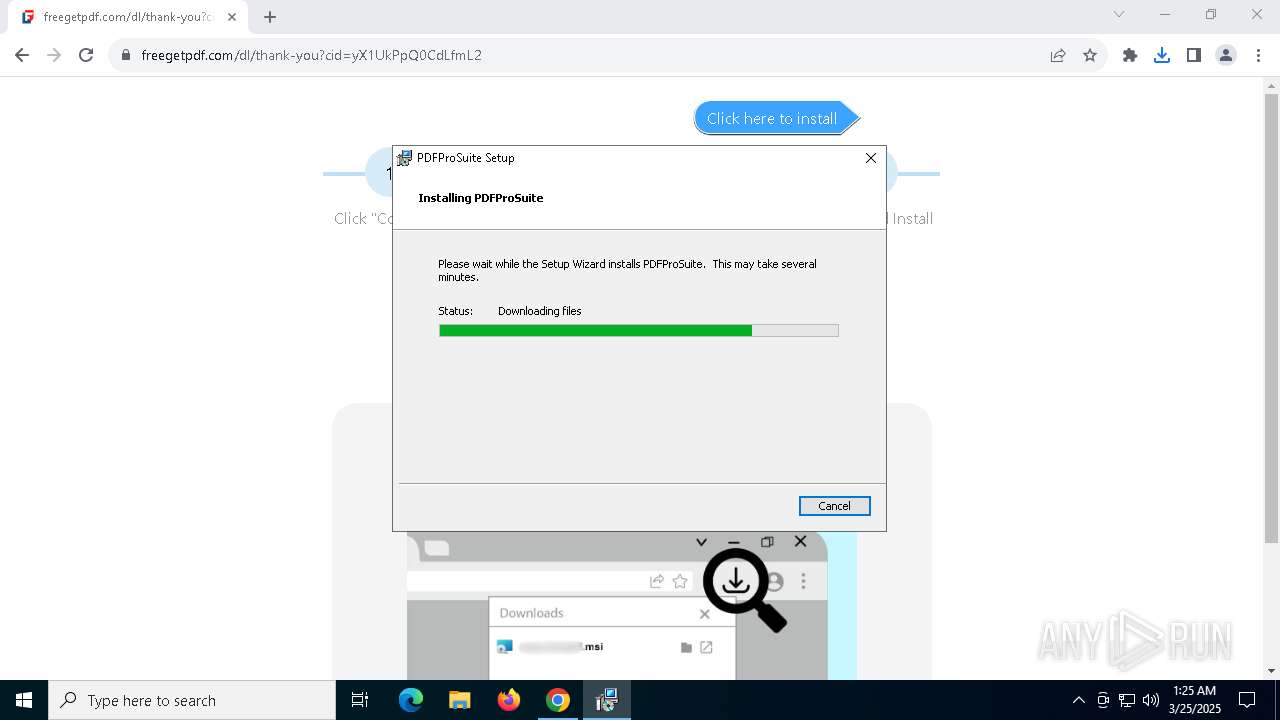
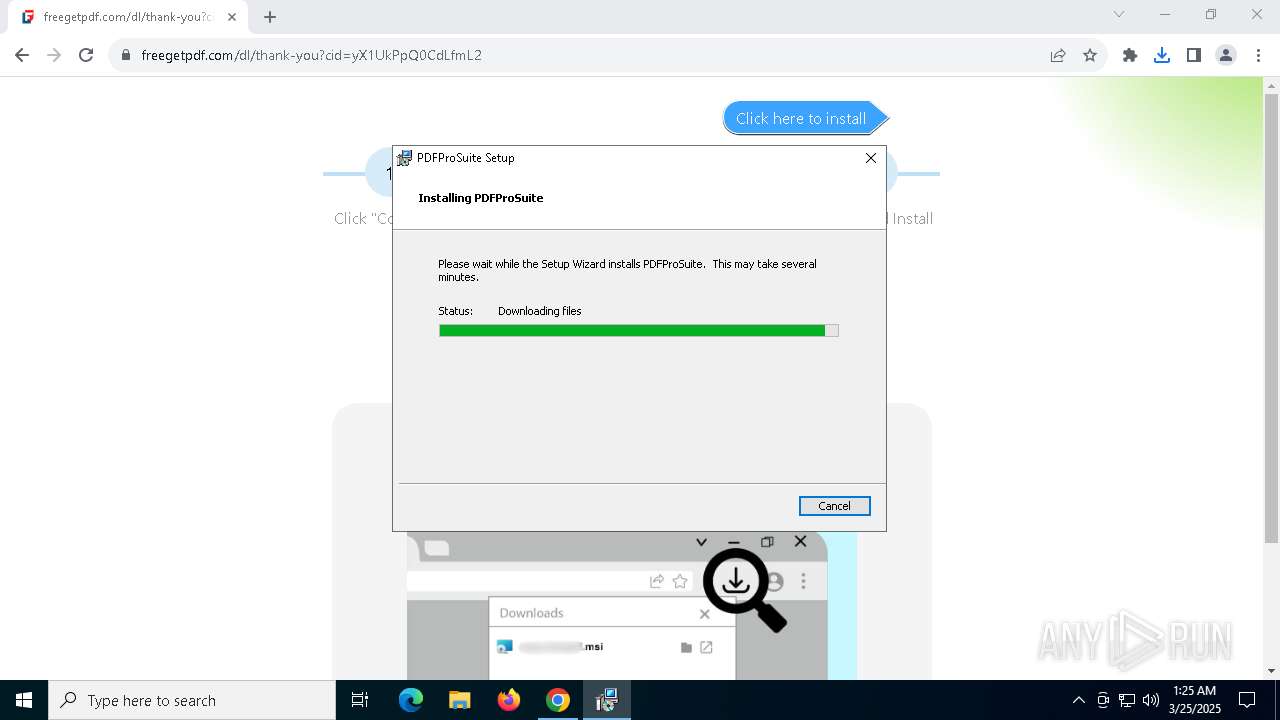
| 840 | "C:\WINDOWS\Installer\MSI8D61.tmp" /DontWait /HideWindow /dir "C:\Users\admin\AppData\Local\PDFProSuite\" pdfprosuite.exe . | C:\Windows\Installer\MSI8D61.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Caphyon LTD Integrity Level: MEDIUM Description: File that launches another file Exit code: 0 Version: 21.9.0.0 Modules
| |||||||||||||||
| 856 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6196 --field-trial-handle=1840,i,4176337598687587244,13470699741281501532,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1056 | C:\Windows\syswow64\MsiExec.exe -Embedding 454A565DA9F470B62DBD0FEB865042BD C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4668 --field-trial-handle=1840,i,4176337598687587244,13470699741281501532,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | pdfprosuite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
31 309
Read events
30 960
Write events
325
Delete events
24
Modification events
| (PID) Process: | (7392) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7392) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7392) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7392) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7392) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5548) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5548) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5548) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2140) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2140) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
33
Suspicious files
483
Text files
39
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c4f8.TMP | — | |
MD5:— | SHA256:— | |||
| 7392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c4f8.TMP | — | |
MD5:— | SHA256:— | |||
| 7392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c4f8.TMP | — | |
MD5:— | SHA256:— | |||
| 7392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c4f8.TMP | — | |
MD5:— | SHA256:— | |||
| 7392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c507.TMP | — | |
MD5:— | SHA256:— | |||
| 7392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
81
DNS requests
69
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7392 | chrome.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDACP4PKUmHSg8coXrA%3D%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7392 | chrome.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/codesigningrootr45/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEQCBTkI%2BxI6x4NL94uMAHTSA | unknown | — | — | whitelisted |
2140 | BackgroundTransferHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
736 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
736 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7812 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adelf34uy3ecewv6y7hgg42lbcpq_2025.3.23.1/jflhchccmppkfebkiaminageehmchikm_2025.03.23.01_all_lr6l24f3pyyo6ycnpoc5lsae6u.crx3 | unknown | — | — | whitelisted |
5228 | msiexec.exe | GET | 200 | 18.245.38.41:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | whitelisted |
5228 | msiexec.exe | GET | 200 | 18.173.208.27:80 | http://ocsp.r2m03.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQqHI%2BsdmapawQncL1rpCEZZ8gTSAQUVdkYX9IczAHhWLS%2Bq9lVQgHXLgICEA%2BjuCOT1x259UHHR62v01I%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
7612 | chrome.exe | 74.125.206.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
7392 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7612 | chrome.exe | 13.33.187.39:443 | freegetpdf.com | — | US | unknown |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
freegetpdf.com |
| unknown |
accounts.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |