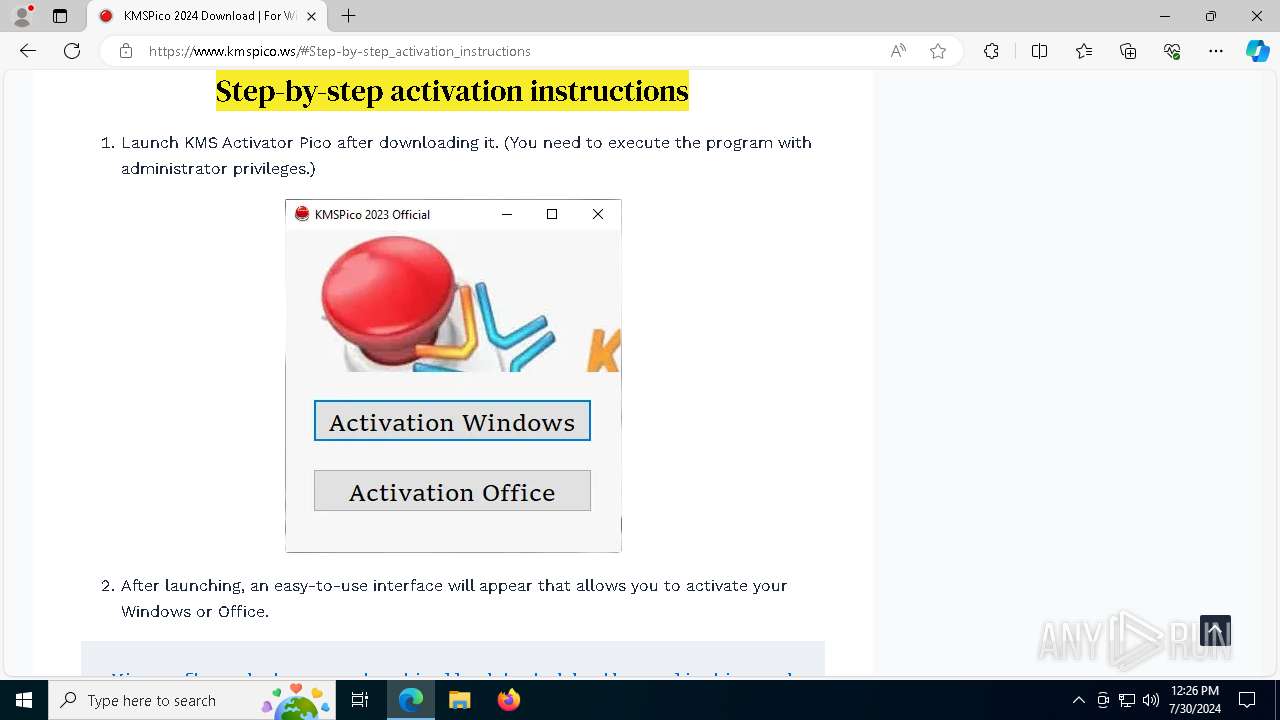
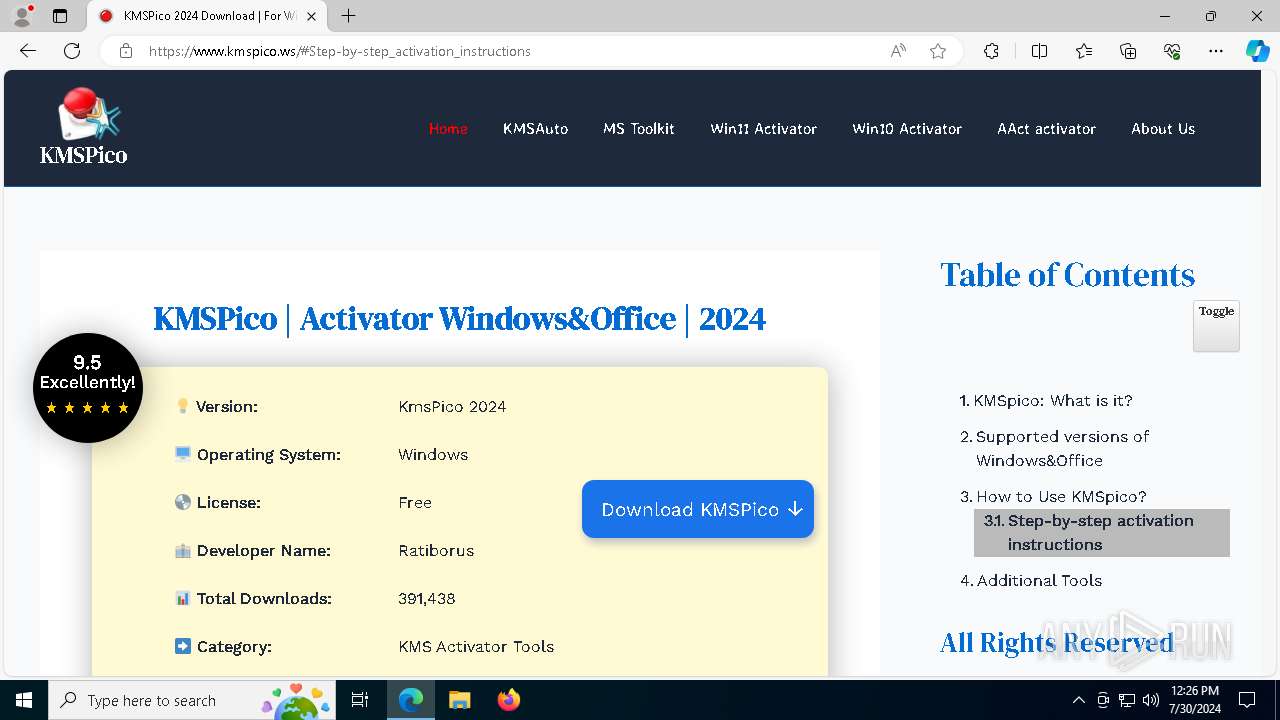
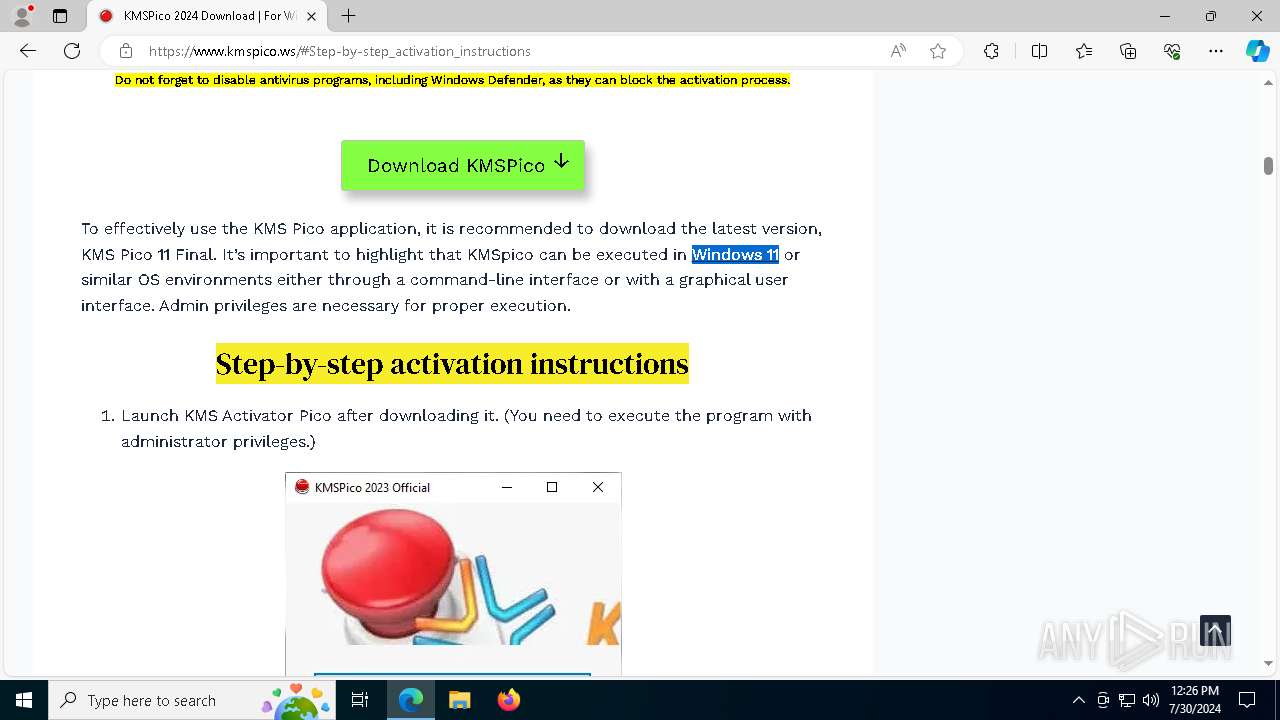
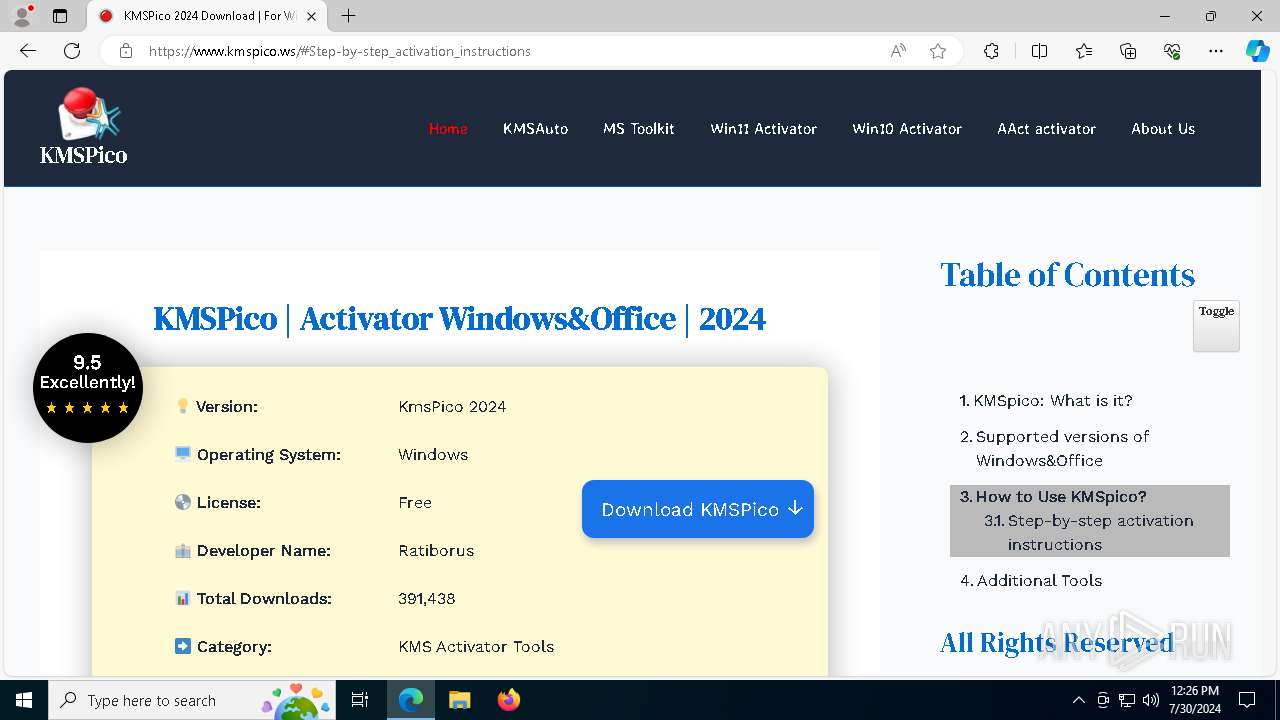
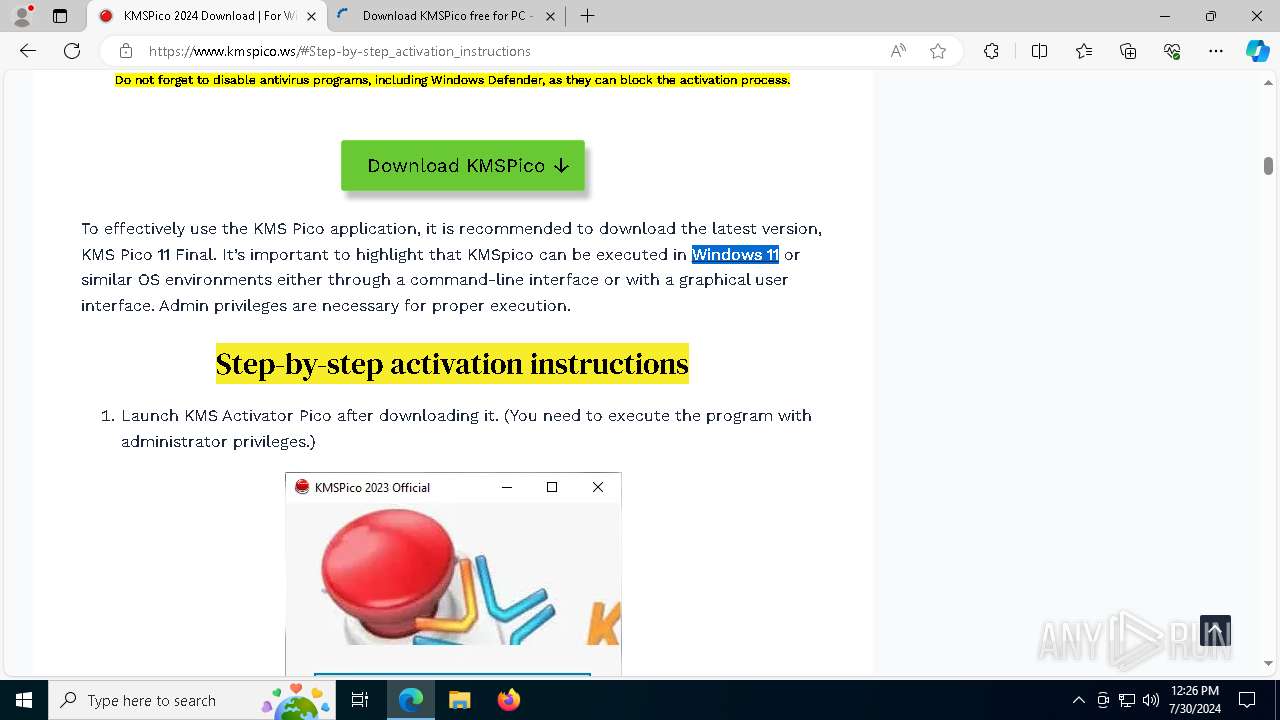
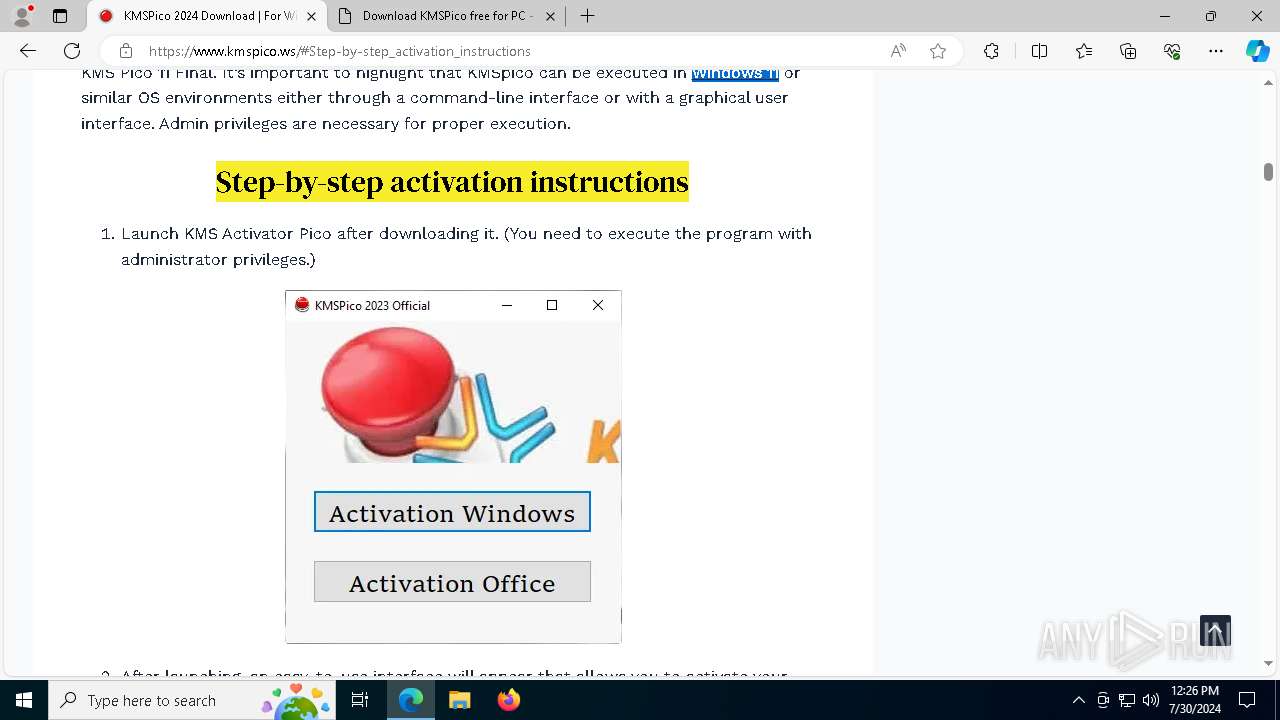
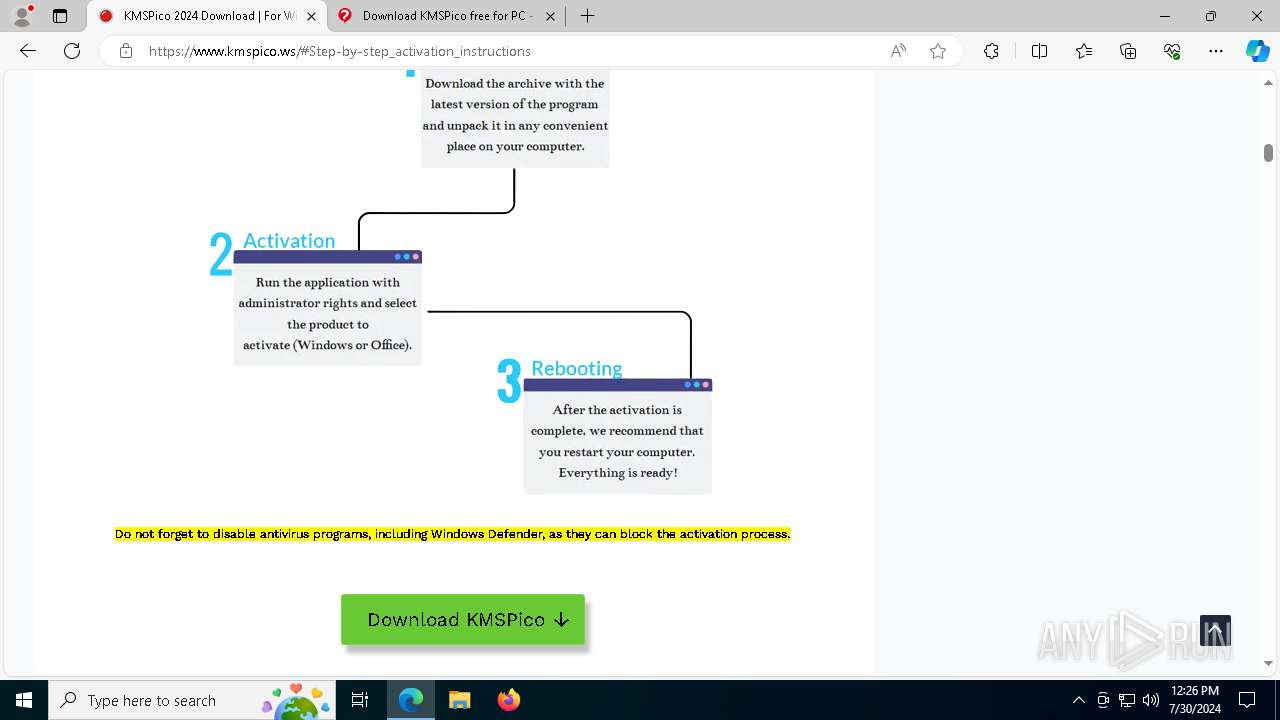
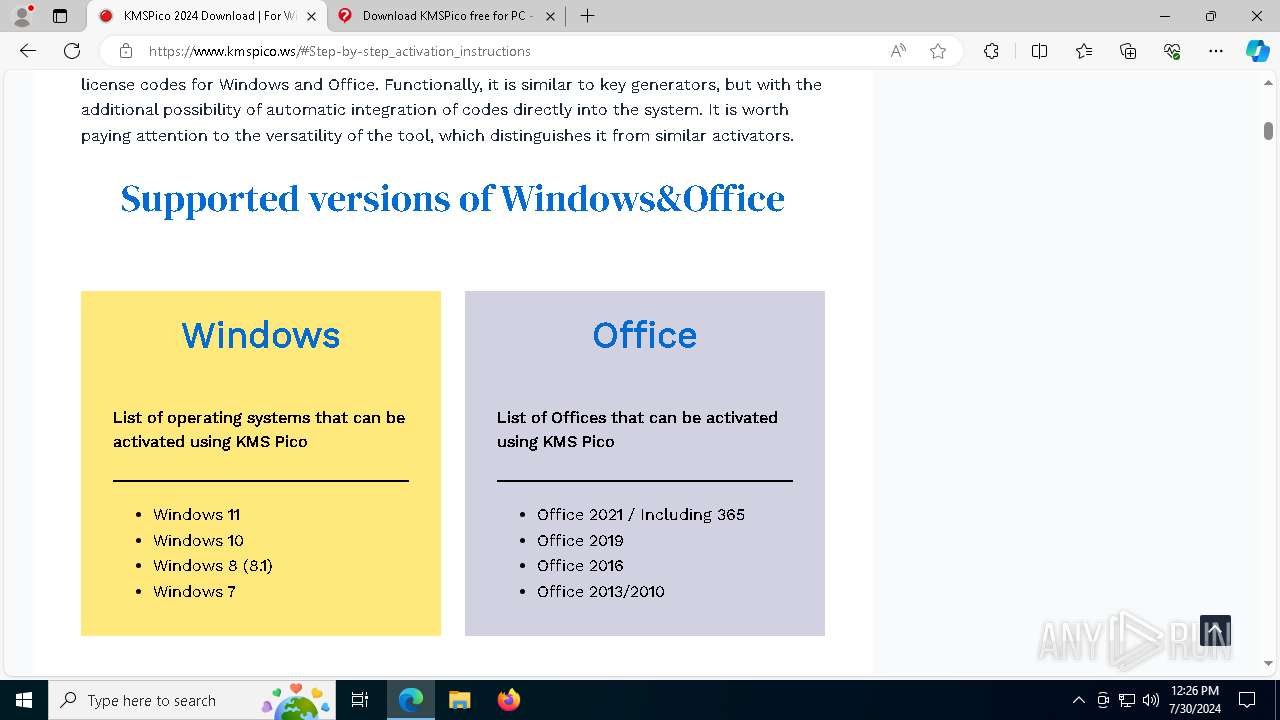
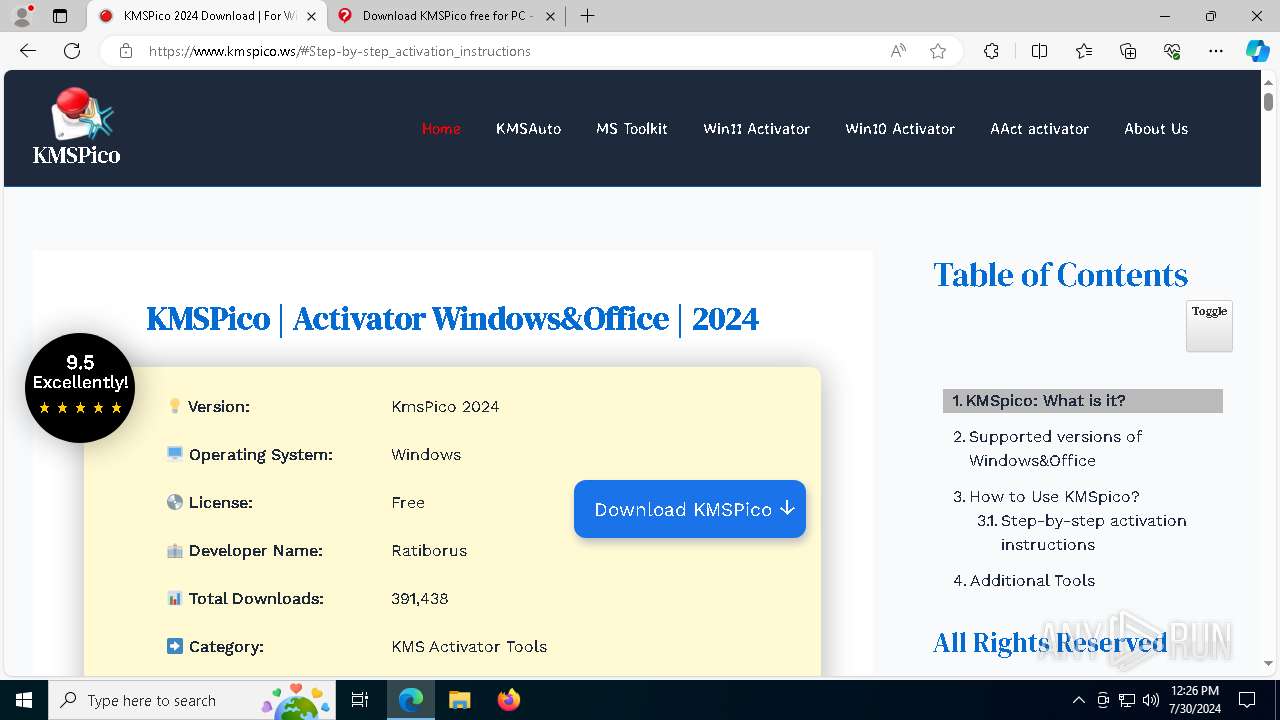
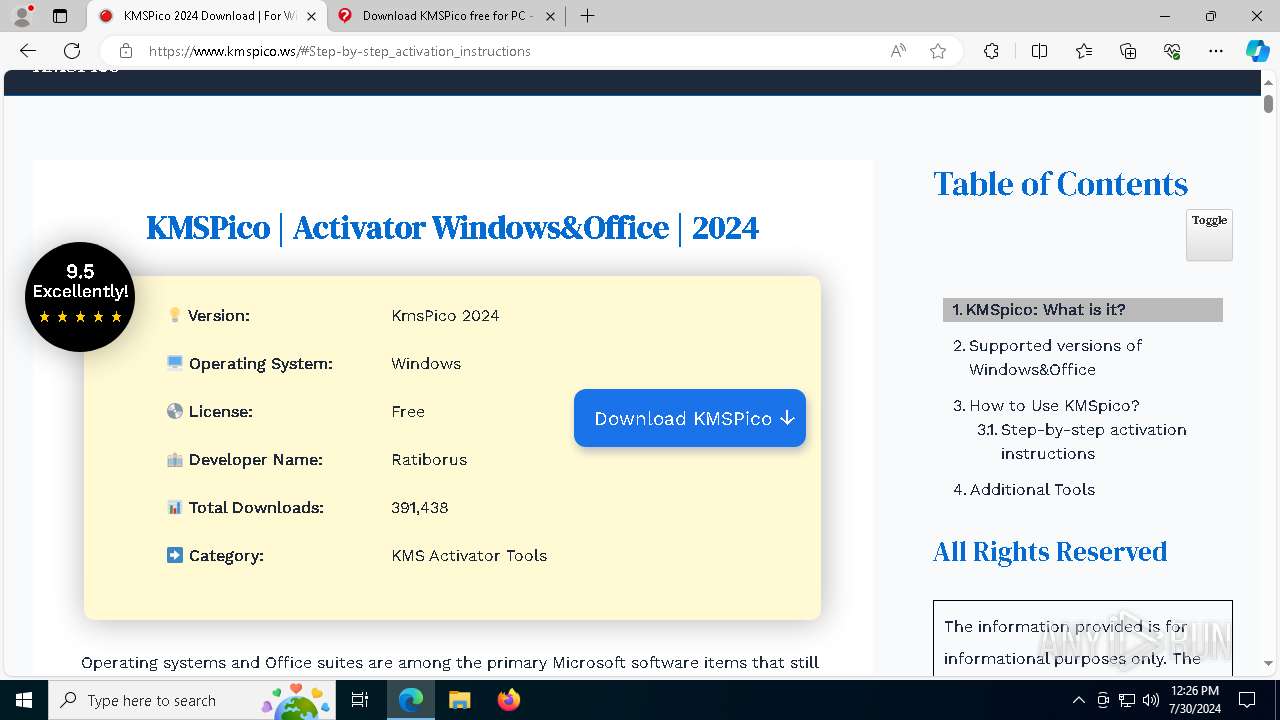
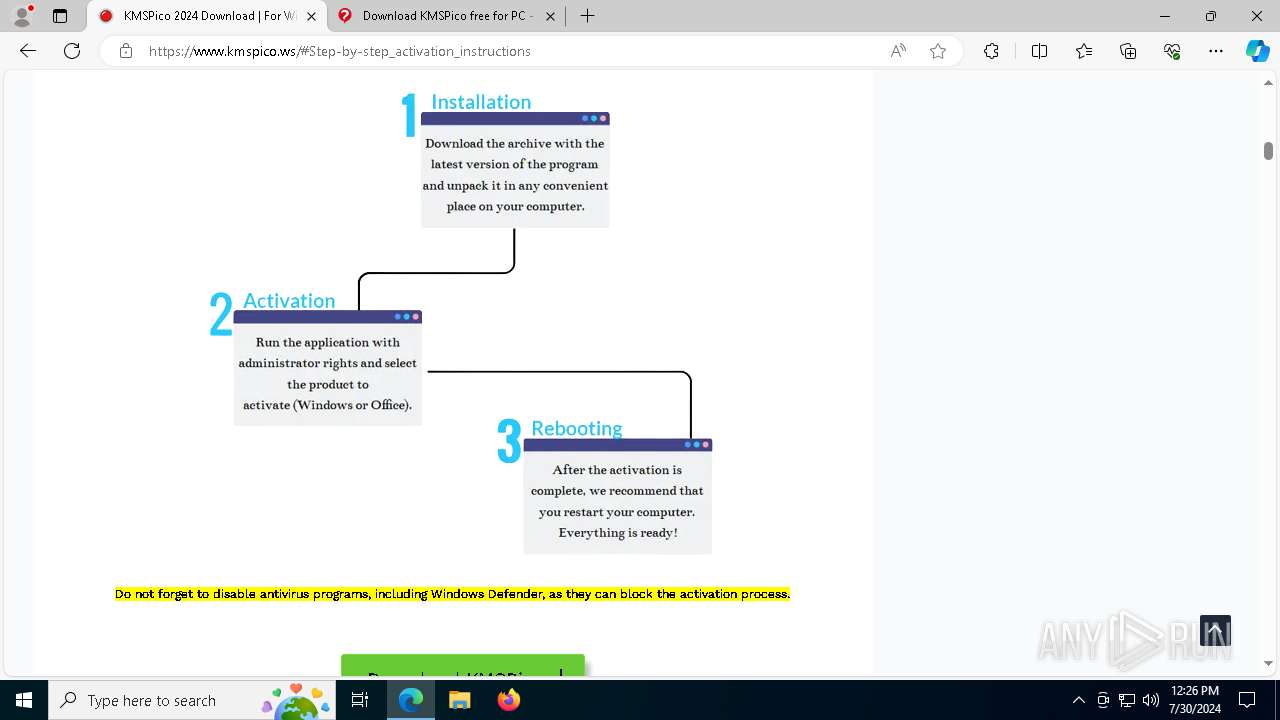
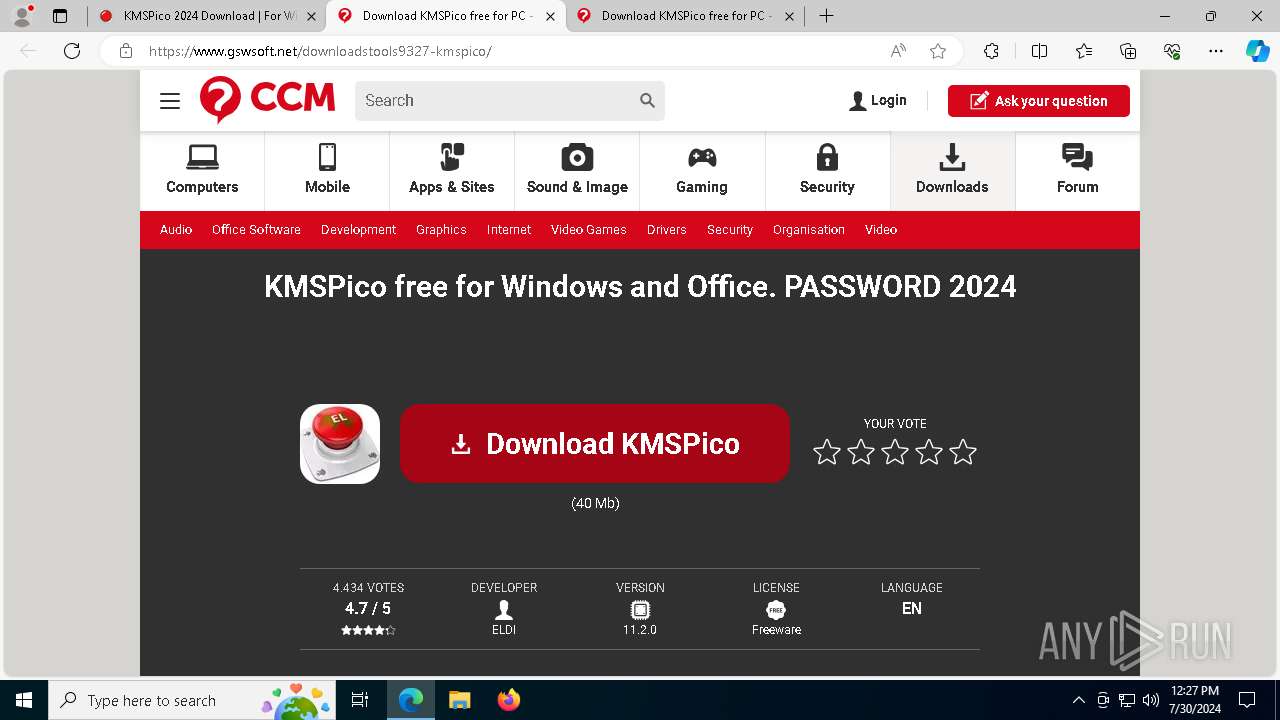
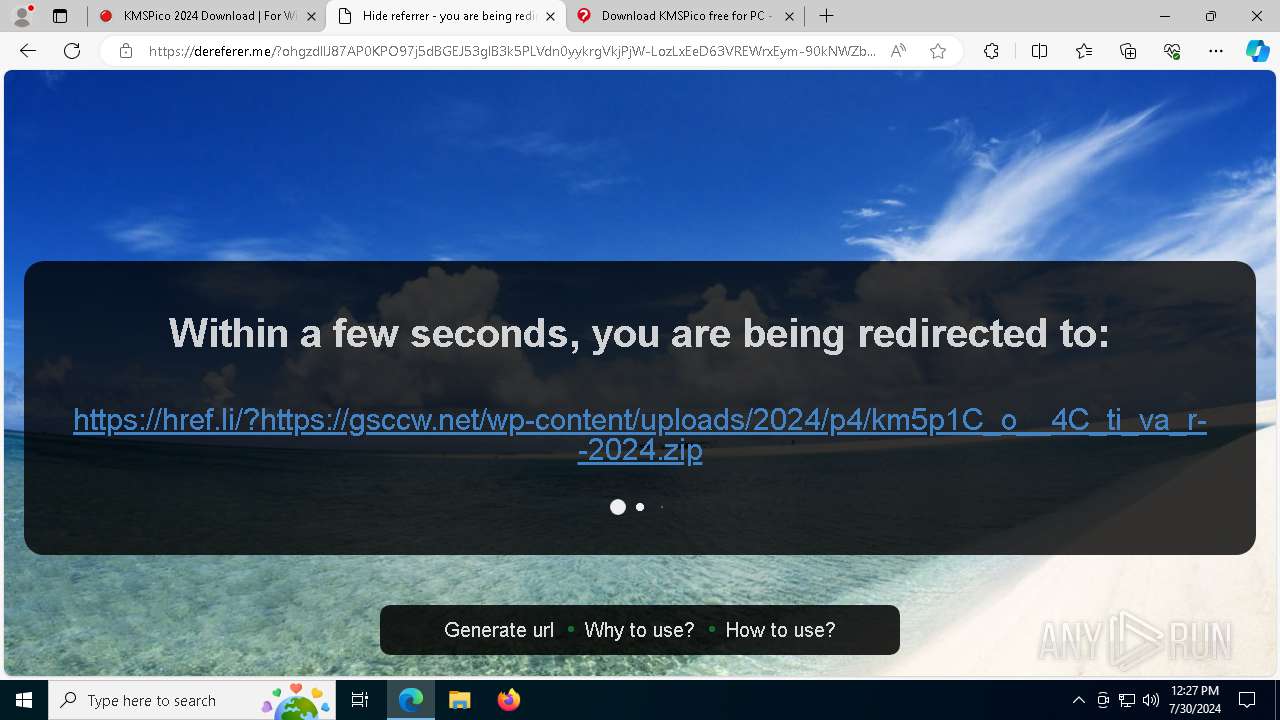
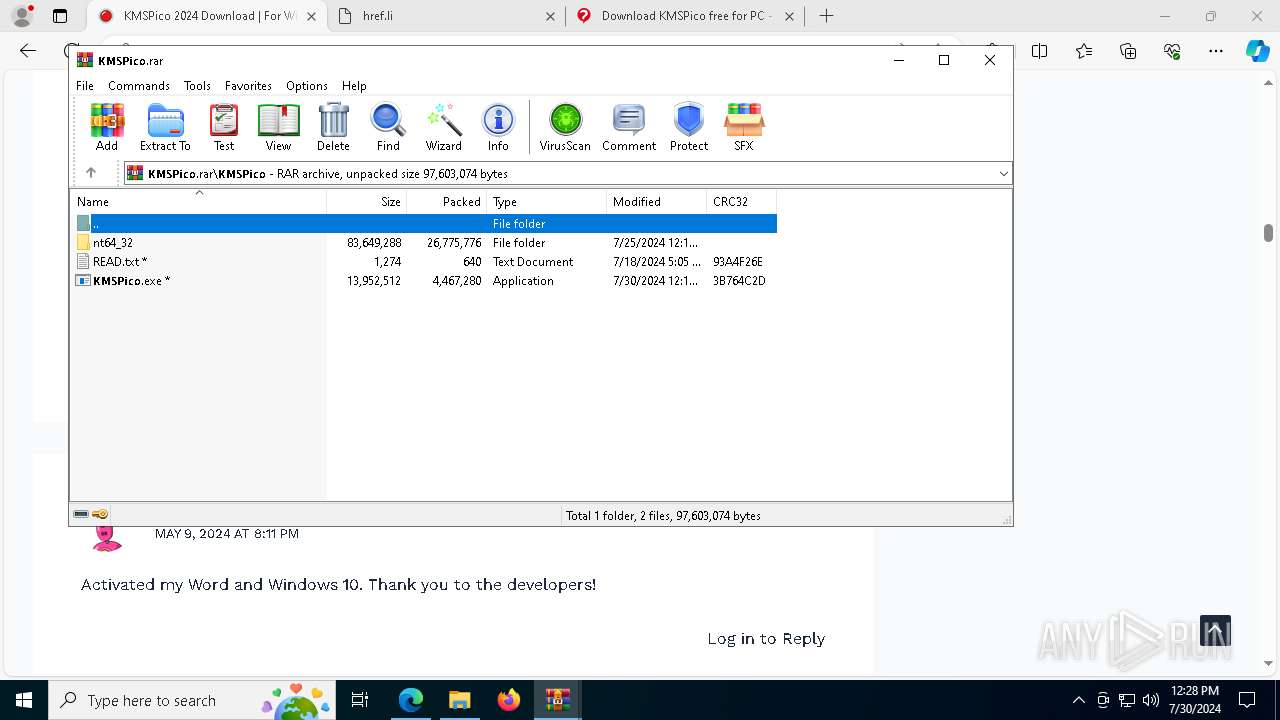
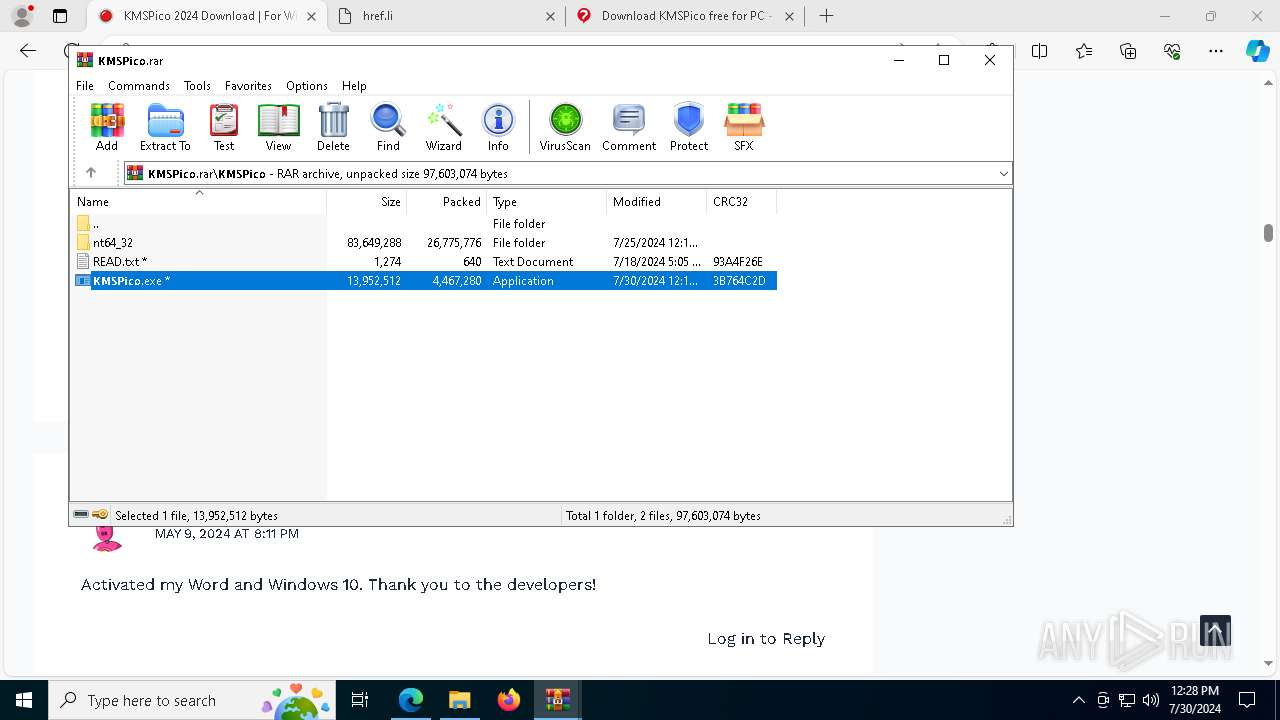
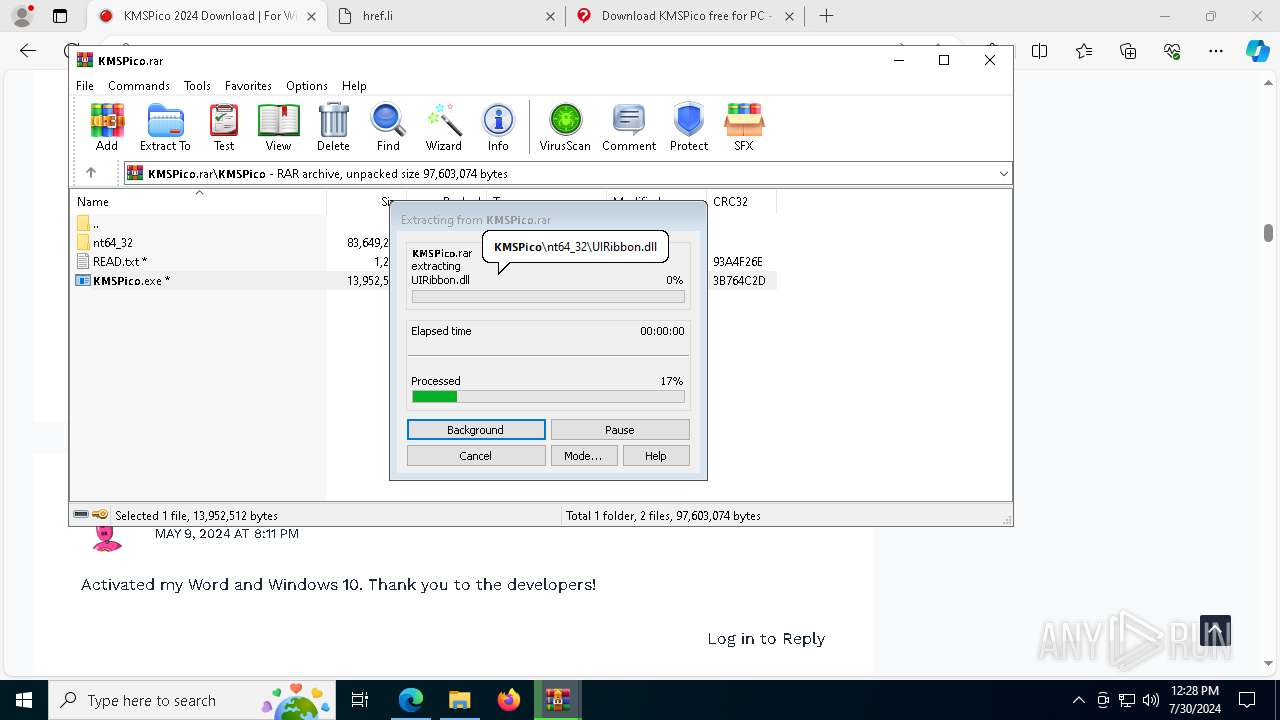
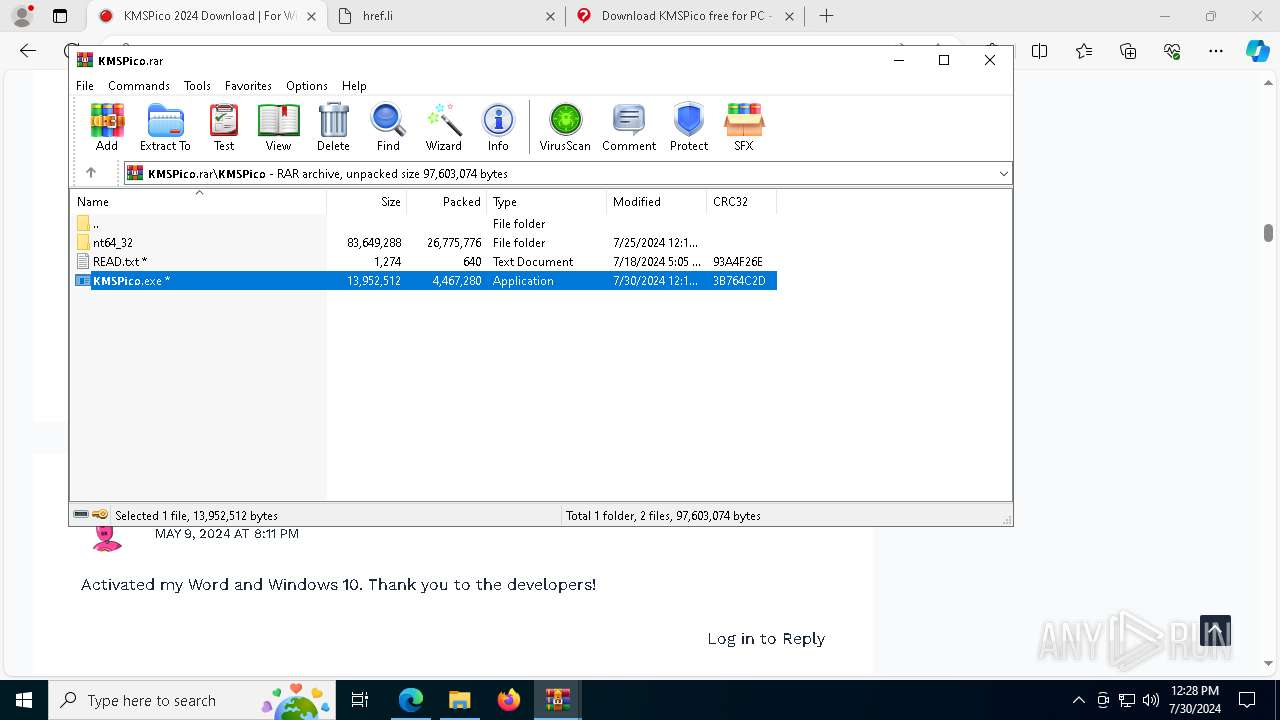
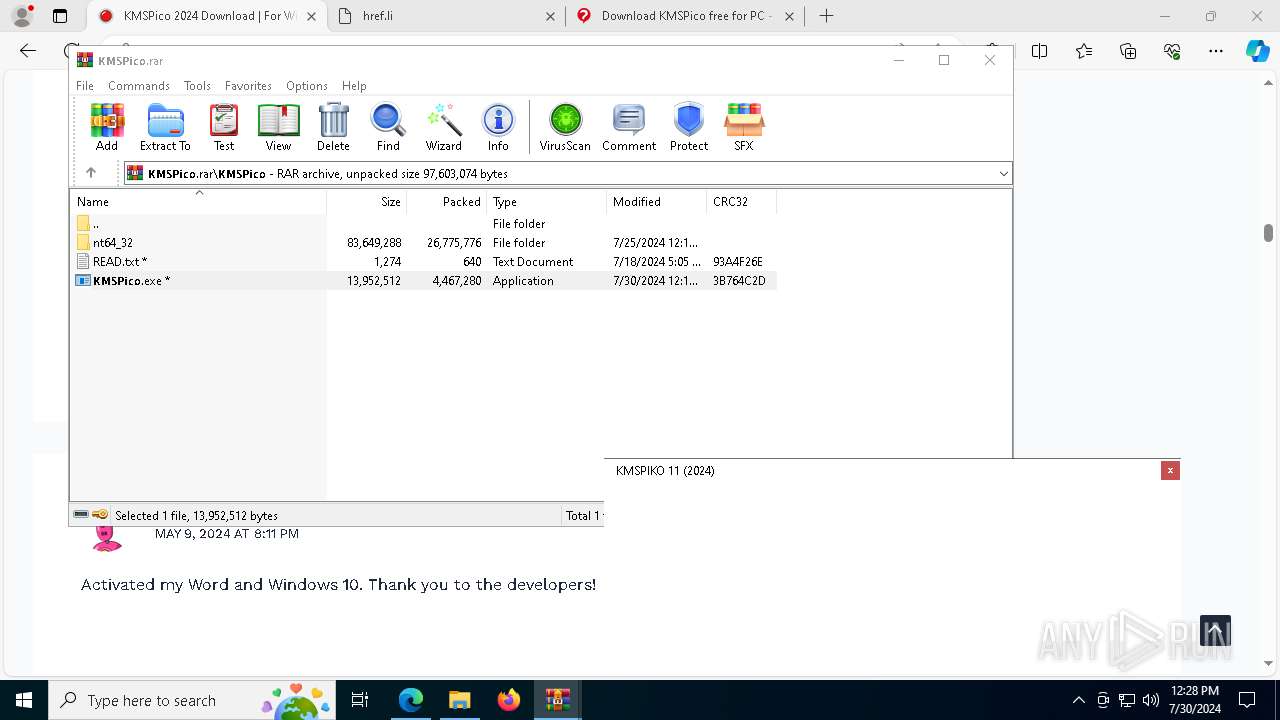
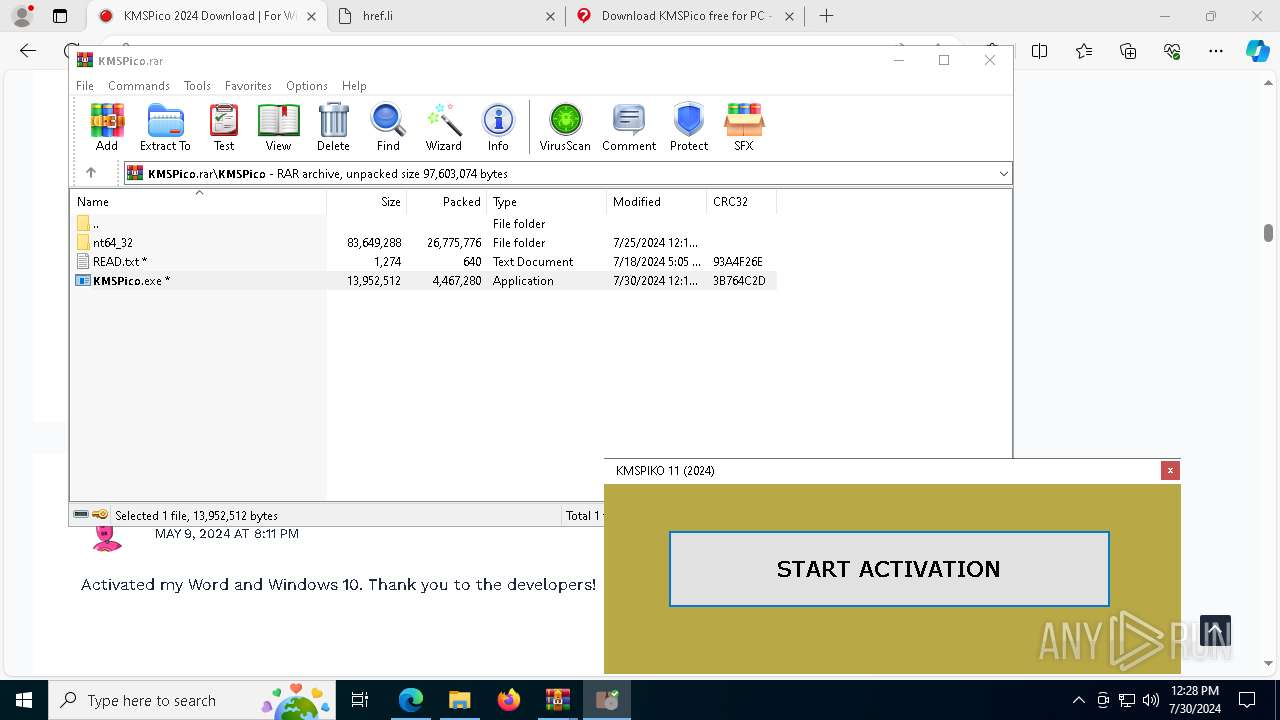
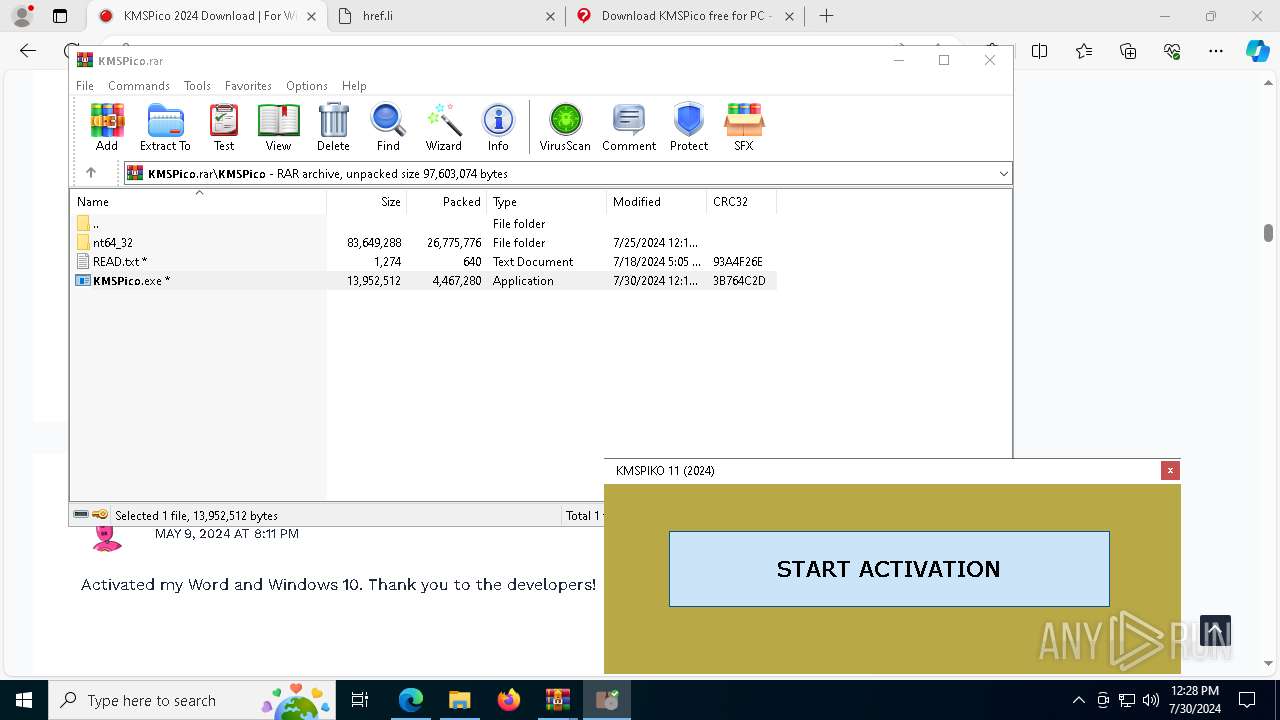
| URL: | https://www.kmspico.ws/ |
| Full analysis: | https://app.any.run/tasks/6f0bf8a7-d5da-4ef8-84cb-7398e5e757a0 |
| Verdict: | Malicious activity |
| Analysis date: | July 30, 2024, 12:25:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | AC72507AE9119BA80B4CB1E6A9C3F704 |
| SHA1: | F6B0CA696A7136CB5940FCF06D8AE5B58049B10E |
| SHA256: | 0FF8D1710E480C1AD2A9A6436360CD9D4BE00A2F7D842A78173DB267115F9694 |
| SSDEEP: | 3:N8DSLOt:2OLS |
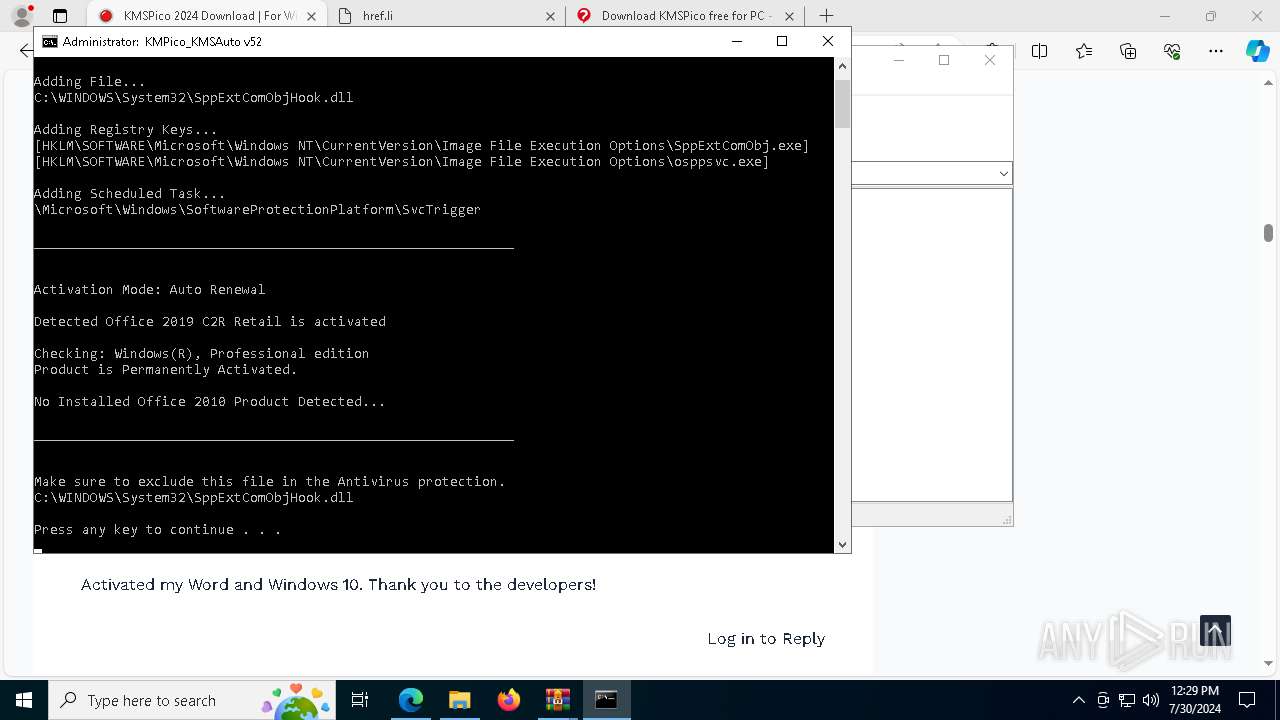
MALICIOUS
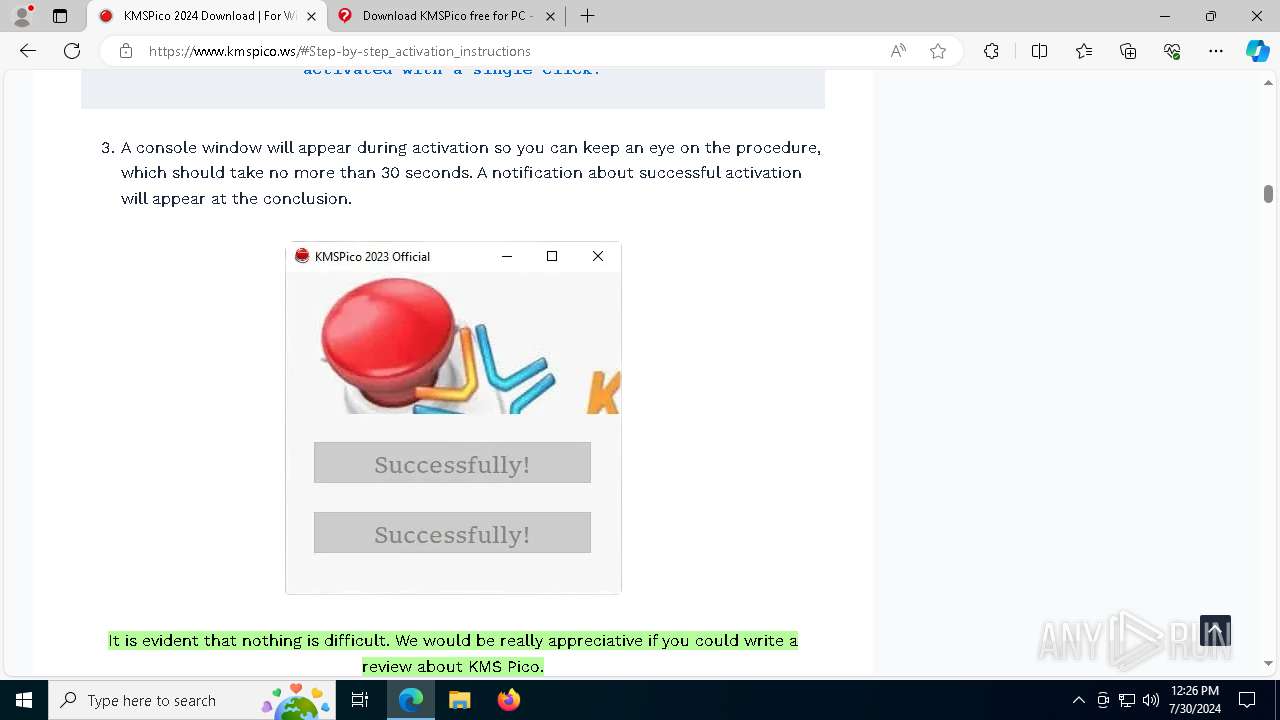
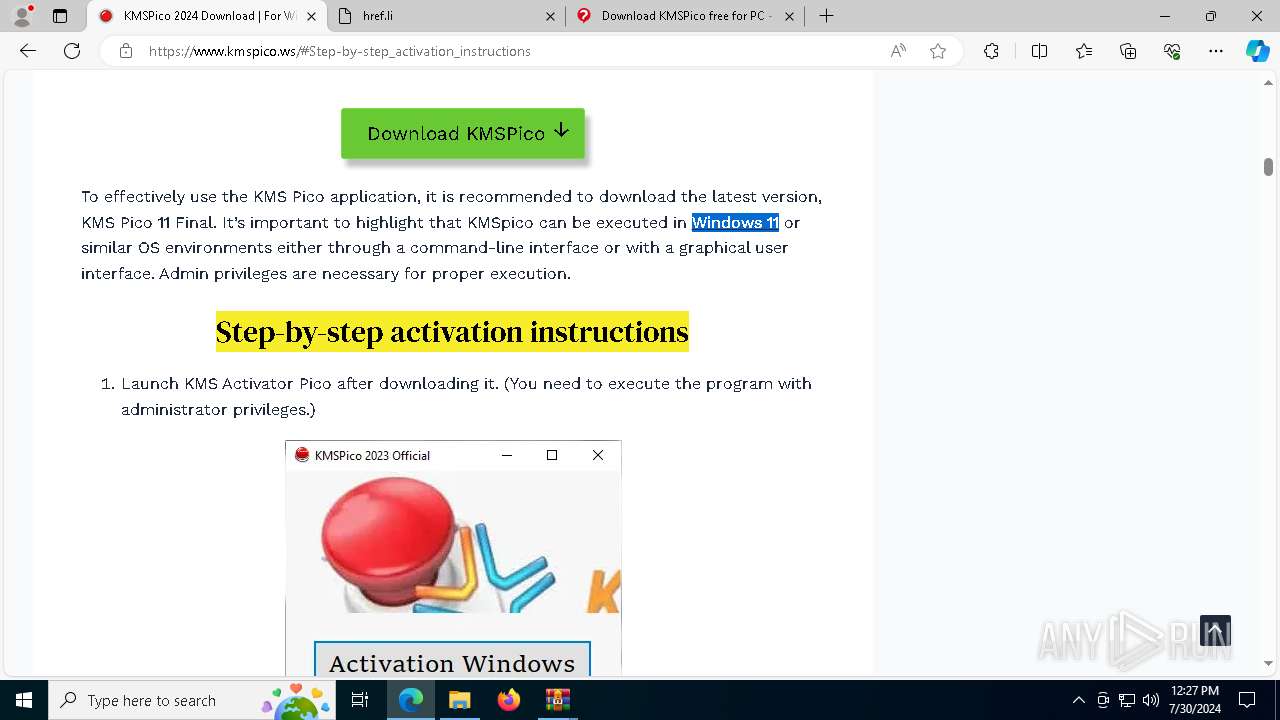
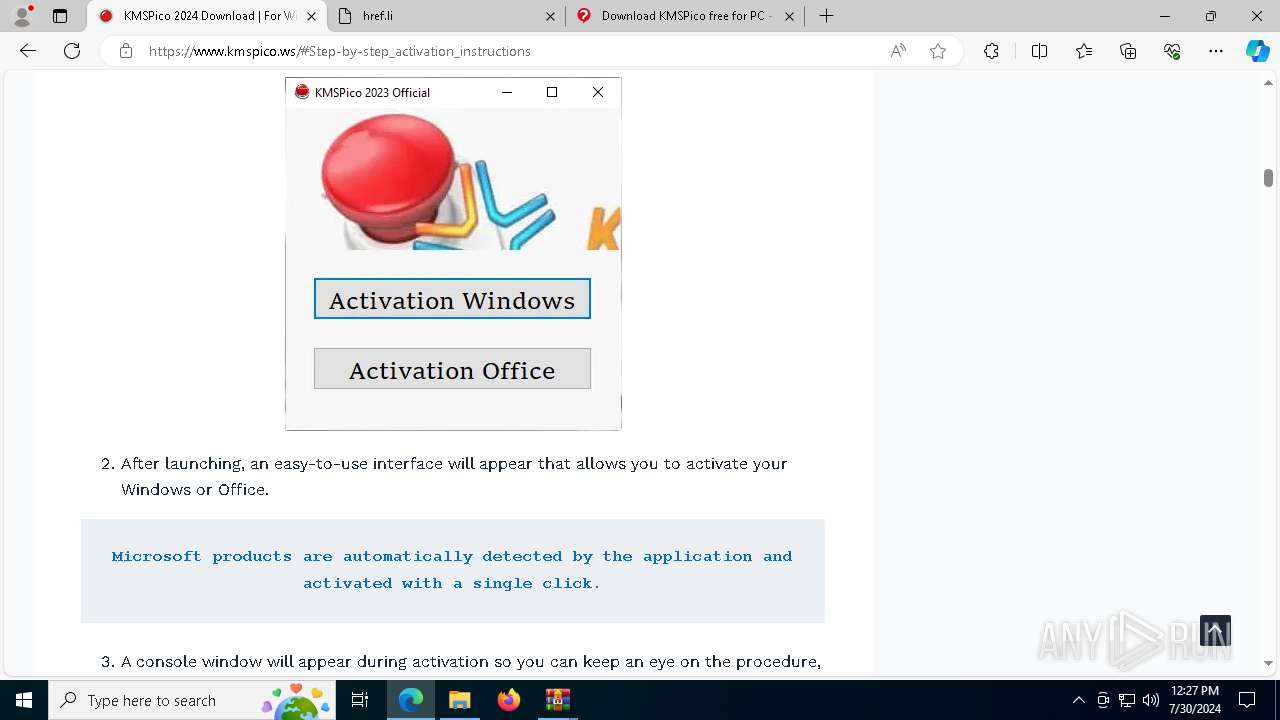
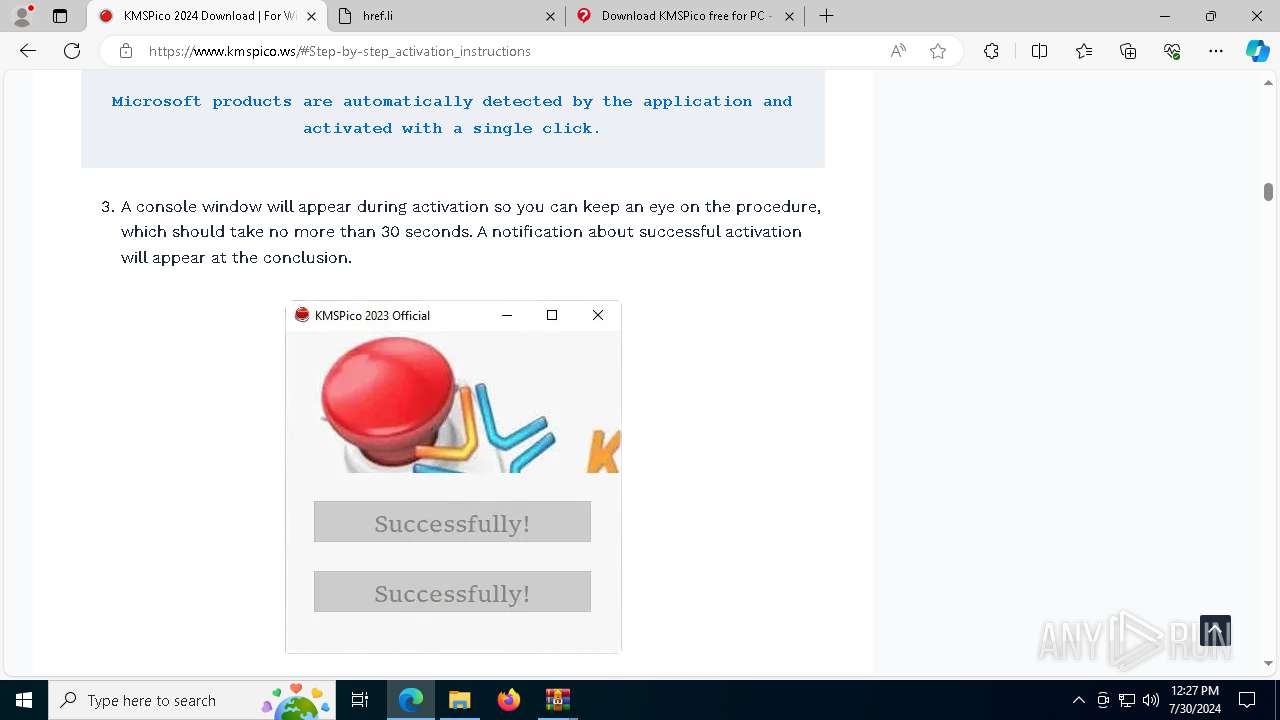
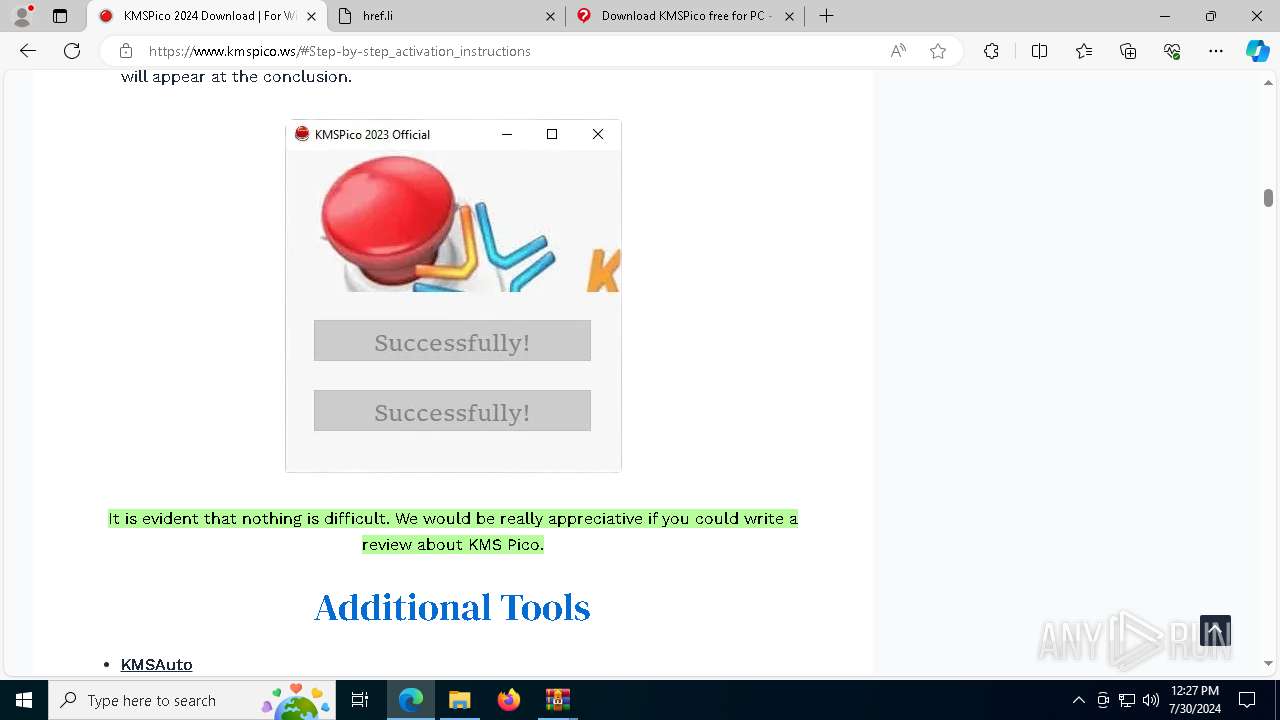
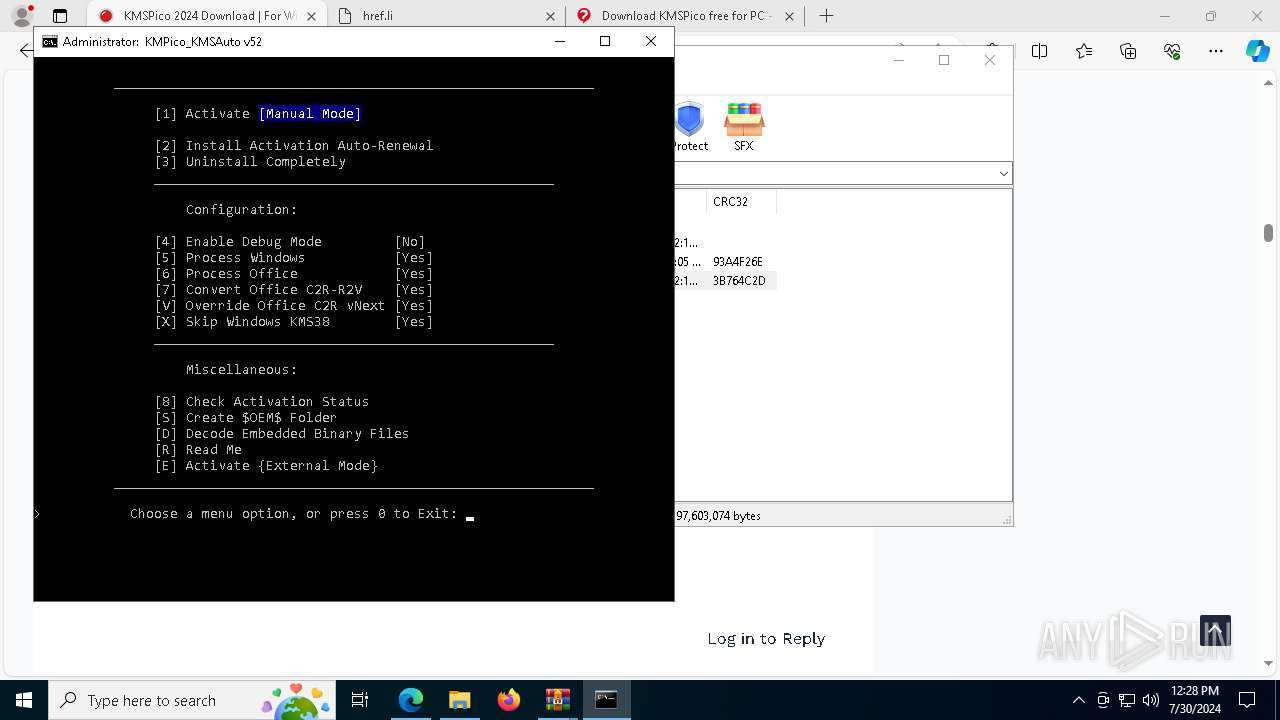
Drops the executable file immediately after the start
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
- powershell.exe (PID: 2944)
- csc.exe (PID: 5028)
Registers / Runs the DLL via REGSVR32.EXE
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7956)
Starts NET.EXE for service management
- net.exe (PID: 2944)
- cmd.exe (PID: 7956)
- net.exe (PID: 7732)
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 7956)
SUSPICIOUS
Application launched itself
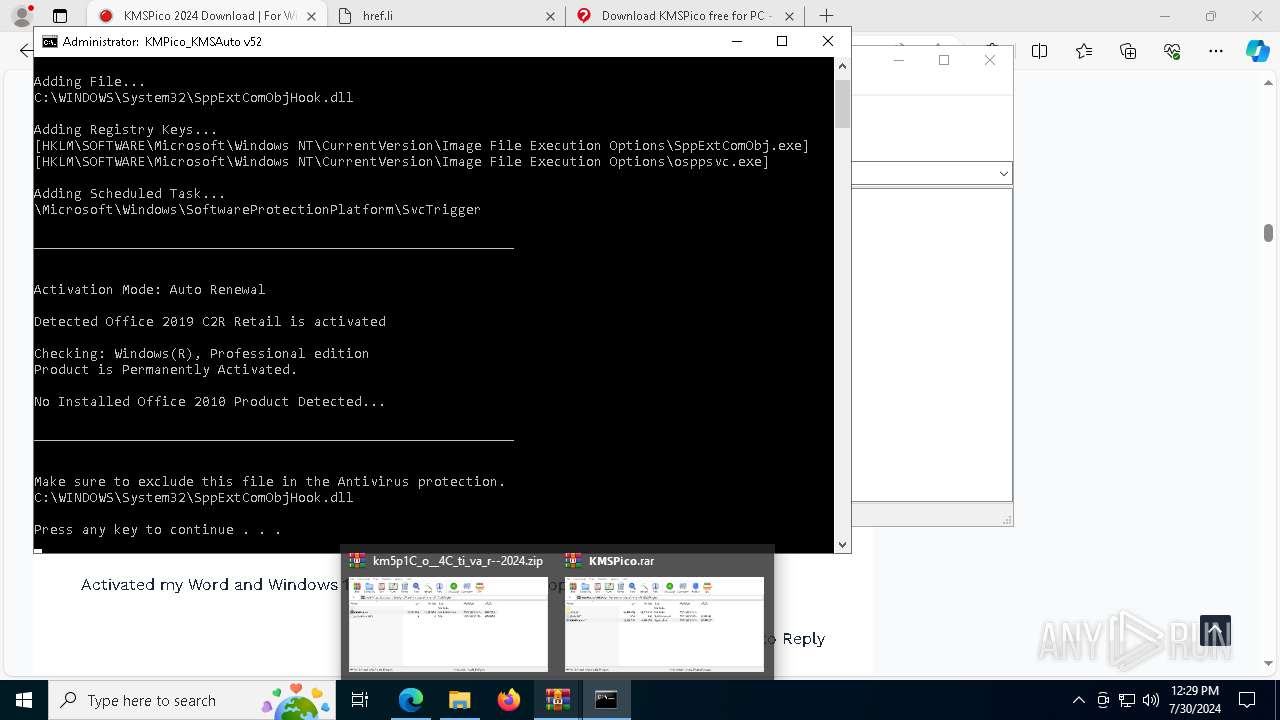
- WinRAR.exe (PID: 1336)
- cmd.exe (PID: 7956)
Reads security settings of Internet Explorer
- cookie_exporter.exe (PID: 6064)
- WinRAR.exe (PID: 1336)
- WinRAR.exe (PID: 6448)
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6448)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6448)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6448)
Executes application which crashes
- regsvr32.exe (PID: 8076)
Reads the date of Windows installation
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
Executable content was dropped or overwritten
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
- csc.exe (PID: 5028)
- powershell.exe (PID: 2944)
Executing commands from a ".bat" file
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7956)
Starts CMD.EXE for commands execution
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
- cmd.exe (PID: 7956)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7956)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7956)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 1924)
Hides command output
- cmd.exe (PID: 1012)
- cmd.exe (PID: 7964)
- cmd.exe (PID: 1108)
- cmd.exe (PID: 4840)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 700)
- cmd.exe (PID: 524)
- cmd.exe (PID: 7616)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 6512)
- cmd.exe (PID: 6040)
- cmd.exe (PID: 6484)
- cmd.exe (PID: 3820)
- cmd.exe (PID: 3780)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 4040)
- cmd.exe (PID: 8036)
- cmd.exe (PID: 6592)
- cmd.exe (PID: 5628)
- cmd.exe (PID: 812)
- cmd.exe (PID: 644)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 4196)
Starts SC.EXE for service management
- cmd.exe (PID: 7956)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7956)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 7956)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 7956)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2944)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2944)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 2944)
Lists all scheduled tasks
- schtasks.exe (PID: 5000)
- schtasks.exe (PID: 5660)
- schtasks.exe (PID: 2088)
- schtasks.exe (PID: 3276)
- schtasks.exe (PID: 5304)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7956)
Modifies existing scheduled task
- schtasks.exe (PID: 3628)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 4840)
- cmd.exe (PID: 7956)
- cmd.exe (PID: 2068)
- cmd.exe (PID: 436)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7956)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 512)
INFO
Application launched itself
- msedge.exe (PID: 2188)
Checks supported languages
- identity_helper.exe (PID: 4152)
- cookie_exporter.exe (PID: 6064)
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
- mode.com (PID: 5800)
- mode.com (PID: 5800)
- csc.exe (PID: 5028)
- cvtres.exe (PID: 1976)
Reads the computer name
- identity_helper.exe (PID: 4152)
- cookie_exporter.exe (PID: 6064)
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
Reads Microsoft Office registry keys
- msedge.exe (PID: 2188)
- reg.exe (PID: 3400)
- reg.exe (PID: 7616)
- reg.exe (PID: 6820)
- reg.exe (PID: 5528)
- reg.exe (PID: 1468)
- reg.exe (PID: 5736)
- reg.exe (PID: 6916)
- reg.exe (PID: 3200)
- reg.exe (PID: 8036)
- reg.exe (PID: 6916)
- reg.exe (PID: 1356)
- reg.exe (PID: 1924)
- reg.exe (PID: 7712)
- reg.exe (PID: 5556)
- reg.exe (PID: 5860)
- reg.exe (PID: 7400)
- reg.exe (PID: 5800)
- reg.exe (PID: 3200)
- reg.exe (PID: 5592)
- reg.exe (PID: 4660)
- reg.exe (PID: 3108)
- reg.exe (PID: 7964)
- reg.exe (PID: 436)
- reg.exe (PID: 2476)
- reg.exe (PID: 6632)
- reg.exe (PID: 5956)
- reg.exe (PID: 5868)
- reg.exe (PID: 5668)
- reg.exe (PID: 6916)
- reg.exe (PID: 8036)
- reg.exe (PID: 1976)
The process uses the downloaded file
- msedge.exe (PID: 3804)
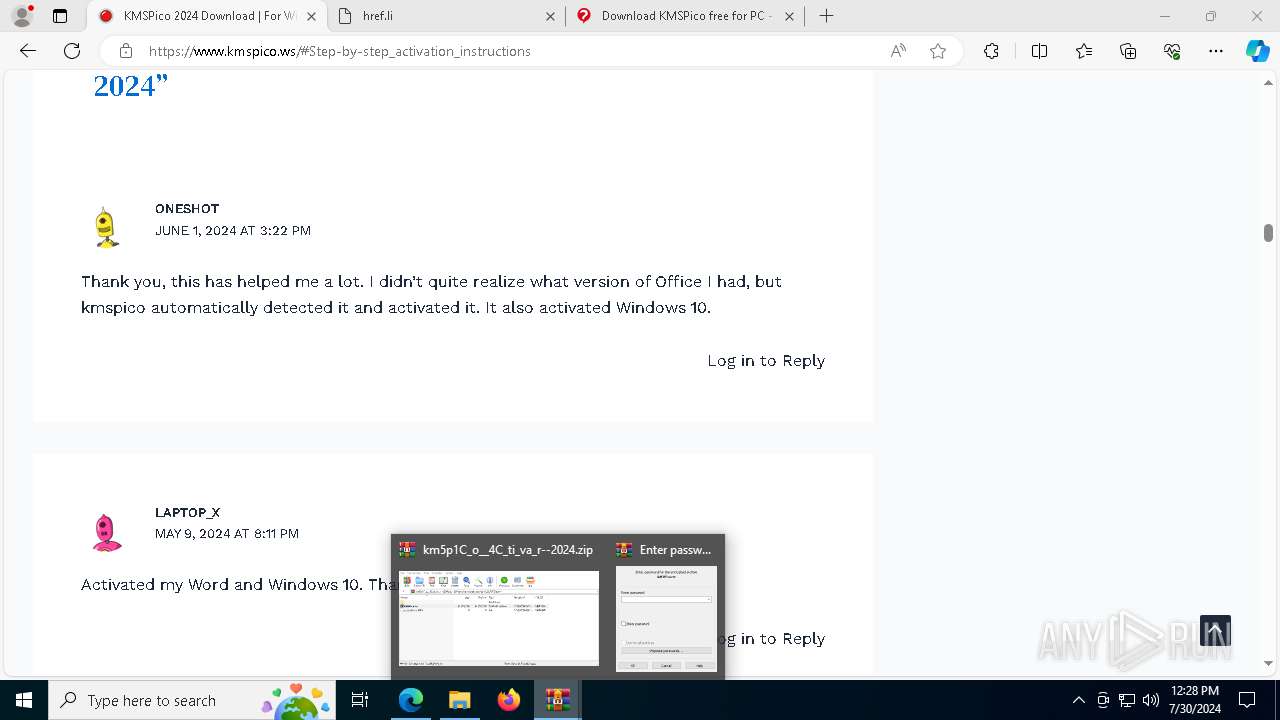
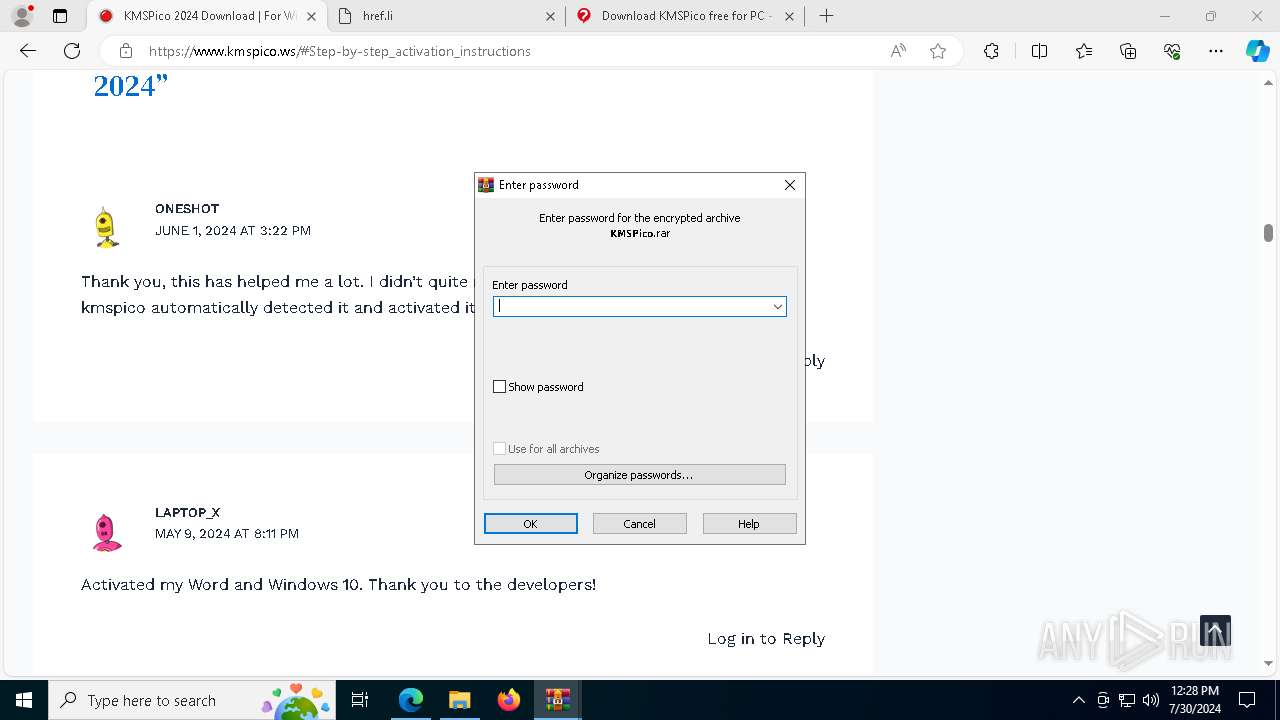
- WinRAR.exe (PID: 1336)
Manual execution by a user
- WinRAR.exe (PID: 1336)
Reads Environment values
- cookie_exporter.exe (PID: 6064)
- identity_helper.exe (PID: 4152)
Checks proxy server information
- cookie_exporter.exe (PID: 6064)
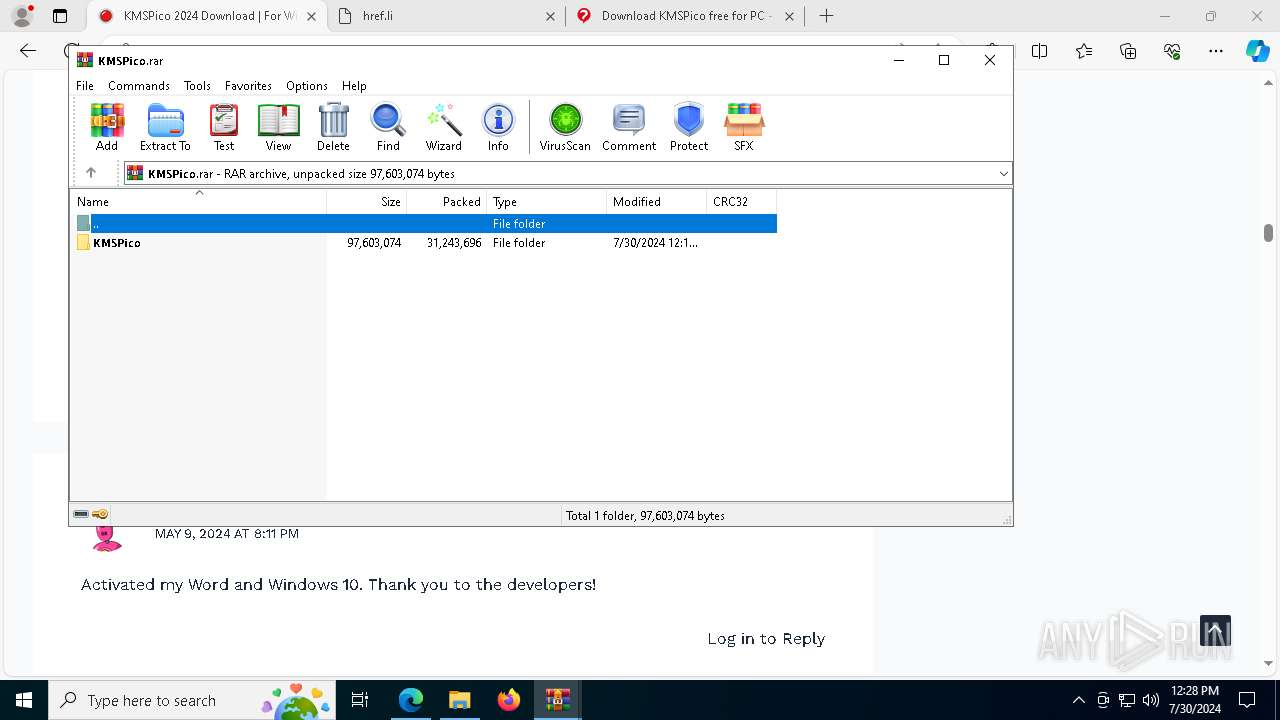
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6448)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6448)
Create files in a temporary directory
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6524)
- WMIC.exe (PID: 4068)
- WMIC.exe (PID: 3400)
- WMIC.exe (PID: 7276)
- WMIC.exe (PID: 7652)
- WMIC.exe (PID: 4632)
- WMIC.exe (PID: 3780)
- WMIC.exe (PID: 5464)
- WMIC.exe (PID: 7964)
- WMIC.exe (PID: 524)
- WMIC.exe (PID: 1028)
- WMIC.exe (PID: 8168)
- WMIC.exe (PID: 4840)
- WMIC.exe (PID: 2912)
- WMIC.exe (PID: 7400)
- WMIC.exe (PID: 5556)
- WMIC.exe (PID: 5700)
- WMIC.exe (PID: 320)
- WMIC.exe (PID: 756)
- WMIC.exe (PID: 7824)
- WMIC.exe (PID: 3664)
- WMIC.exe (PID: 1356)
- WMIC.exe (PID: 700)
- WMIC.exe (PID: 7968)
- WMIC.exe (PID: 6640)
- WMIC.exe (PID: 4108)
- WMIC.exe (PID: 8036)
- WMIC.exe (PID: 6820)
- WMIC.exe (PID: 464)
- WMIC.exe (PID: 3400)
- WMIC.exe (PID: 5876)
- WMIC.exe (PID: 2068)
- WMIC.exe (PID: 5376)
- WMIC.exe (PID: 6044)
Creates files or folders in the user directory
- WerFault.exe (PID: 8040)
Process checks computer location settings
- 𝗞𝗠𝗦𝗣𝗶𝗰𝗼.exe (PID: 5528)
Checks operating system version
- cmd.exe (PID: 7956)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2944)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 2944)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 2944)
Reads the machine GUID from the registry
- csc.exe (PID: 5028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
758
Monitored processes
606
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | findstr /I /C:"VisioProRetail" "C:\WINDOWS\Temp\c2rchk.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | findstr /I /C:"VisioPro2021Retail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | find /i "Office 15" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | wmic path SoftwareLicensingProduct where "ApplicationID='55c92734-d682-4d71-983e-d6ec3f16059f' and Description like '%KMSCLIENT%' and PartialProductKey is not NULL" get Name /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe" /f /v KMS_RenewalInterval /t REG_DWORD /d 10080 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | reg query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\msoxmled.exe" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | reg query HKLM\SOFTWARE\Microsoft\Office\ClickToRun /v InstallPath | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | findstr /I /C:"VisioPro2021Volume" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | find /i "Office24Professional2019R_OEM" "C:\WINDOWS\Temp\crvRetail.txt" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | C:\WINDOWS\system32\cmd.exe /c wmic path SoftwareLicensingProduct where "ApplicationID='55c92734-d682-4d71-983e-d6ec3f16059f' and Description like '%KMSCLIENT%' " get ID /value | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
73 317
Read events
73 085
Write events
222
Delete events
10
Modification events
| (PID) Process: | (6740) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (6740) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (6740) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (6740) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (6740) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (6740) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31122043 | |||
| (PID) Process: | (6740) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6740) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6740) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6740) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
31
Suspicious files
280
Text files
158
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1c08b2.TMP | — | |
MD5:— | SHA256:— | |||
| 2188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1c08c2.TMP | — | |
MD5:— | SHA256:— | |||
| 2188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1c08c2.TMP | — | |
MD5:— | SHA256:— | |||
| 2188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1c08e1.TMP | — | |
MD5:— | SHA256:— | |||
| 2188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1c08e1.TMP | — | |
MD5:— | SHA256:— | |||
| 2188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
161
DNS requests
130
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
8184 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2548 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7336 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cea6d764-36bf-4144-a357-ec91013ddbf5?P1=1722620948&P2=404&P3=2&P4=EXe9knOhoTwNPX%2fJRSRg8FhlaTN%2fufaBvZWyYnLXM5Qoqr7XuJmTCnTkbFGoeIyrCHrQAkqaNRUKYGtkYhx2%2bQ%3d%3d | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7336 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cea6d764-36bf-4144-a357-ec91013ddbf5?P1=1722620948&P2=404&P3=2&P4=EXe9knOhoTwNPX%2fJRSRg8FhlaTN%2fufaBvZWyYnLXM5Qoqr7XuJmTCnTkbFGoeIyrCHrQAkqaNRUKYGtkYhx2%2bQ%3d%3d | unknown | — | — | whitelisted |
7336 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cea6d764-36bf-4144-a357-ec91013ddbf5?P1=1722620948&P2=404&P3=2&P4=EXe9knOhoTwNPX%2fJRSRg8FhlaTN%2fufaBvZWyYnLXM5Qoqr7XuJmTCnTkbFGoeIyrCHrQAkqaNRUKYGtkYhx2%2bQ%3d%3d | unknown | — | — | whitelisted |
7336 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cea6d764-36bf-4144-a357-ec91013ddbf5?P1=1722620948&P2=404&P3=2&P4=EXe9knOhoTwNPX%2fJRSRg8FhlaTN%2fufaBvZWyYnLXM5Qoqr7XuJmTCnTkbFGoeIyrCHrQAkqaNRUKYGtkYhx2%2bQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3688 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1340 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
132 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.152:443 | www.bing.com | Akamai International B.V. | DE | unknown |
2668 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2188 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
www.kmspico.ws |
| malicious |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
4 ETPRO signatures available at the full report