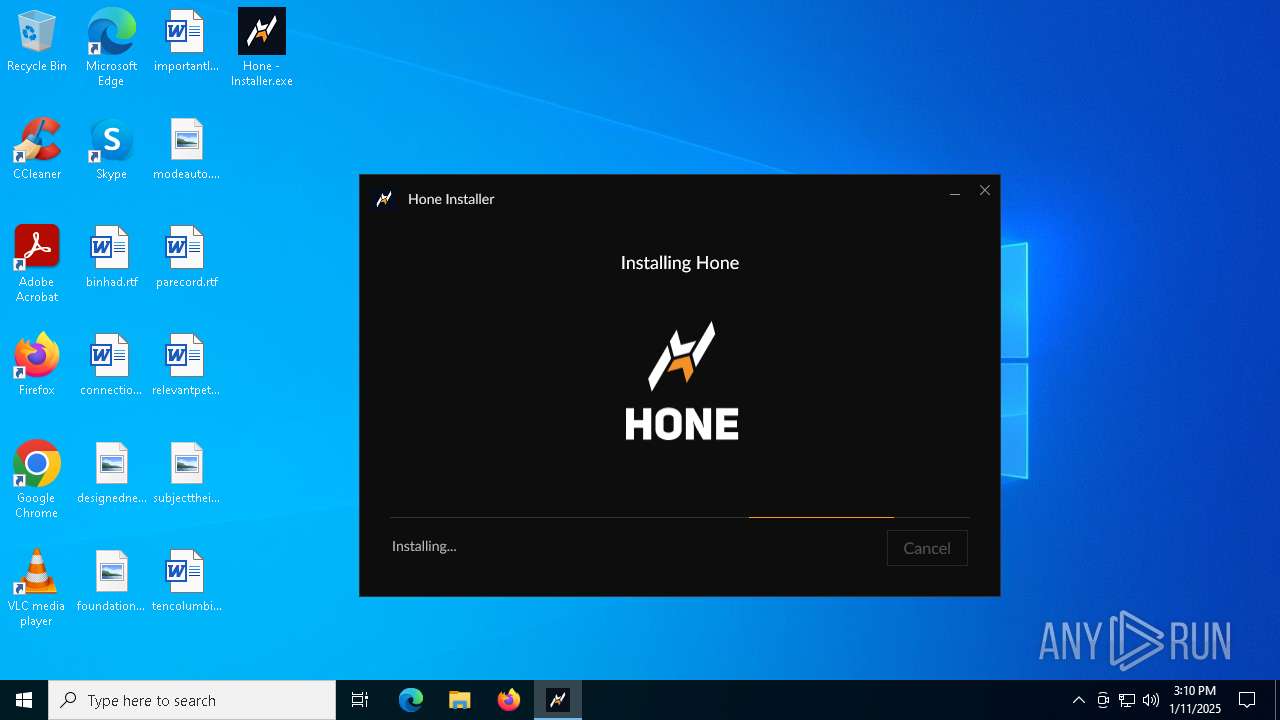
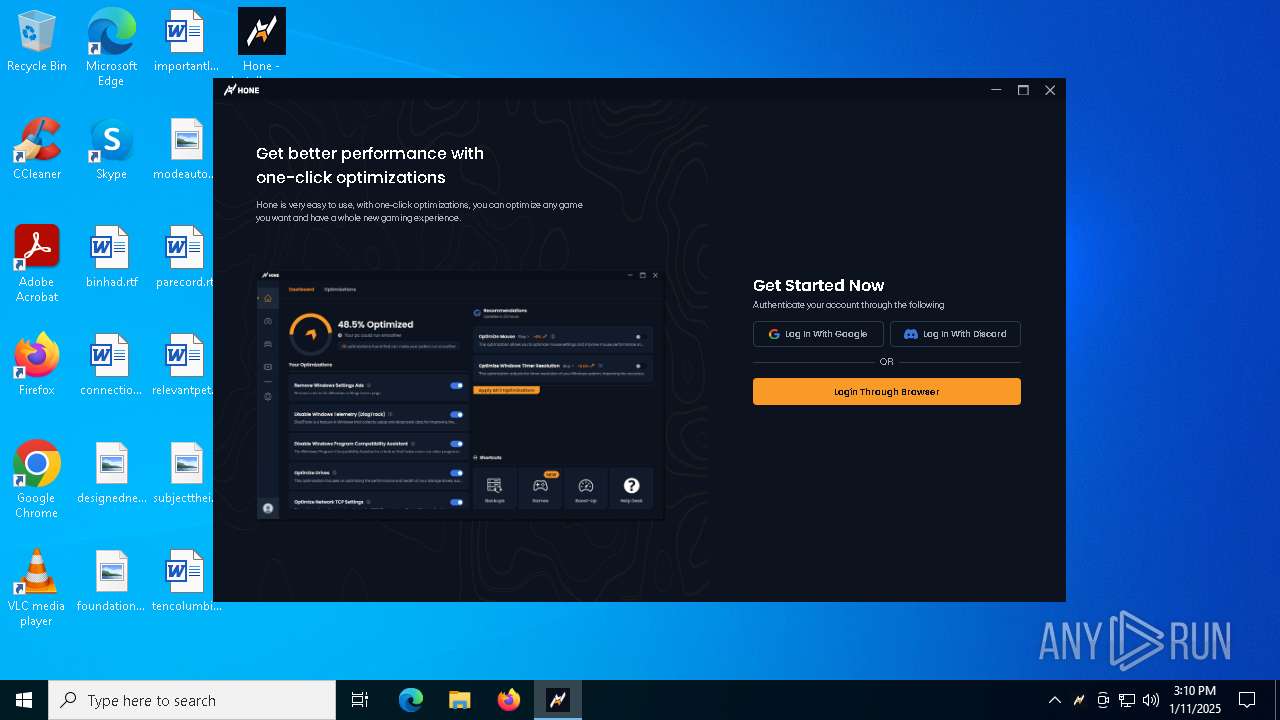
| File name: | Hone - Installer.exe |
| Full analysis: | https://app.any.run/tasks/7c7d4543-f006-46f6-907c-c724e099f6b0 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2025, 15:09:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 933E0F07C831F26DEDBF83C3613D3172 |
| SHA1: | 2D782091EA19A47D67987B04BA1079058474D487 |
| SHA256: | 0FEF9F750B82E6F13DA0938876F7EFF6D1EE9FC7EF6414920AD97F0692C9DCE0 |
| SSDEEP: | 98304:A/RT2uDLTJ/A9nGcRa1xXcVsy3RxeLLCIJgap176MVhBIHckFPFMNA/Pn/PAaq38:pYOvn |
MALICIOUS
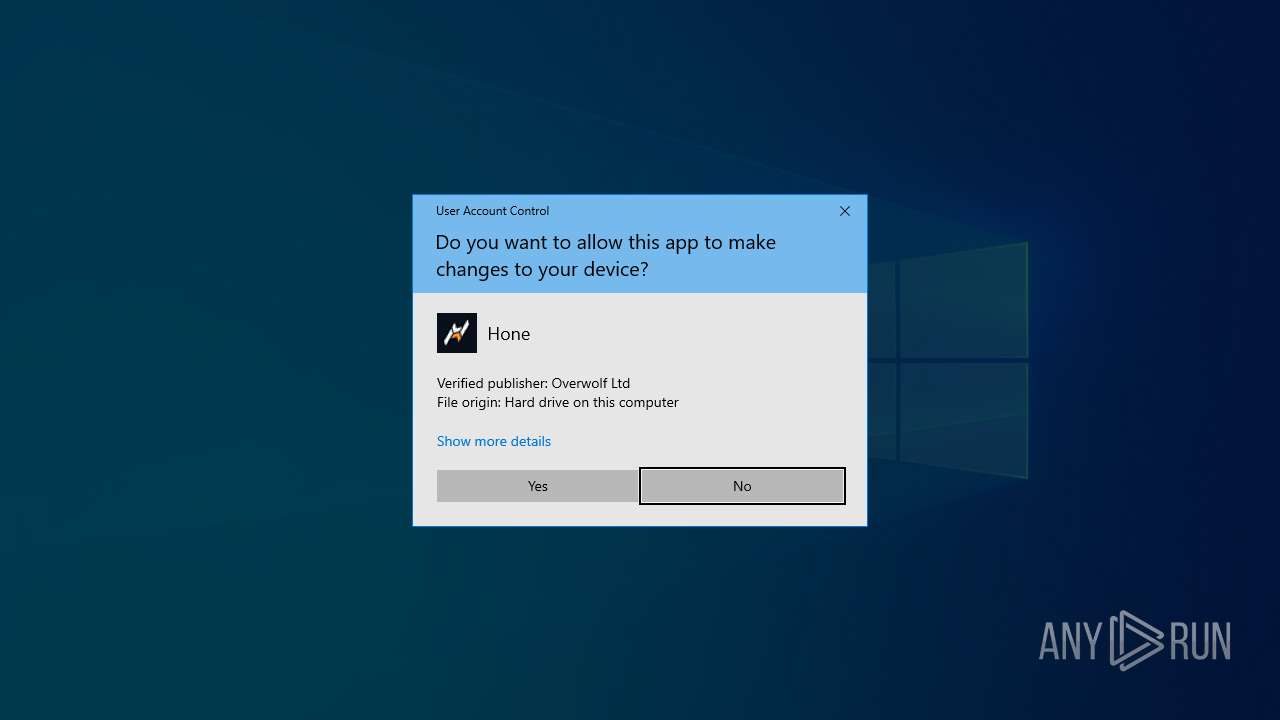
Executing a file with an untrusted certificate
- ow-electron-setup.exe (PID: 6524)
- Hone.exe (PID: 6880)
- Hone.exe (PID: 4864)
- Hone.exe (PID: 4444)
- Hone.exe (PID: 4548)
- Hone.exe (PID: 5628)
- Hone.exe (PID: 4020)
- Hone.exe (PID: 6408)
- HoneStartup.exe (PID: 7148)
- HoneStartup.exe (PID: 1228)
- gamefinder472.exe (PID: 7152)
- gamefinder472.exe (PID: 3560)
- HoneStartup.exe (PID: 2088)
Changes powershell execution policy (Unrestricted)
- Hone.exe (PID: 6880)
Bypass execution policy to execute commands
- powershell.exe (PID: 624)
- powershell.exe (PID: 6544)
- powershell.exe (PID: 5488)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7060)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 3812)
SUSPICIOUS
The process creates files with name similar to system file names
- Hone - Installer.exe (PID: 2072)
- Hone - Installer.exe (PID: 6940)
- ow-electron-setup.exe (PID: 6524)
Drops 7-zip archiver for unpacking
- Hone - Installer.exe (PID: 2072)
- Hone - Installer.exe (PID: 6940)
Executable content was dropped or overwritten
- Hone - Installer.exe (PID: 2072)
- Hone - Installer.exe (PID: 6940)
- ow-electron-setup.exe (PID: 6524)
- Hone.exe (PID: 6408)
Reads security settings of Internet Explorer
- Hone - Installer.exe (PID: 2072)
- Hone - Installer.exe (PID: 6940)
- OWInstaller.exe (PID: 6988)
- Hone.exe (PID: 6880)
Application launched itself
- Hone - Installer.exe (PID: 2072)
- Hone.exe (PID: 6880)
Malware-specific behavior (creating "System.dll" in Temp)
- Hone - Installer.exe (PID: 6940)
- Hone - Installer.exe (PID: 2072)
- ow-electron-setup.exe (PID: 6524)
Reads Internet Explorer settings
- OWInstaller.exe (PID: 6988)
Reads Microsoft Outlook installation path
- OWInstaller.exe (PID: 6988)
Checks Windows Trust Settings
- OWInstaller.exe (PID: 6988)
Reads the date of Windows installation
- OWInstaller.exe (PID: 6988)
Process drops legitimate windows executable
- ow-electron-setup.exe (PID: 6524)
Drops a system driver (possible attempt to evade defenses)
- ow-electron-setup.exe (PID: 6524)
Creates a software uninstall entry
- ow-electron-setup.exe (PID: 6524)
The process drops C-runtime libraries
- ow-electron-setup.exe (PID: 6524)
Starts CMD.EXE for commands execution
- Hone.exe (PID: 6880)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6388)
- cmd.exe (PID: 1616)
- cmd.exe (PID: 2436)
Starts POWERSHELL.EXE for commands execution
- Hone.exe (PID: 6880)
- cmd.exe (PID: 5880)
- cmd.exe (PID: 3640)
- cmd.exe (PID: 7060)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 2484)
- cmd.exe (PID: 3812)
The process hides Powershell's copyright startup banner
- Hone.exe (PID: 6880)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 3812)
- cmd.exe (PID: 7060)
The process bypasses the loading of PowerShell profile settings
- Hone.exe (PID: 6880)
- cmd.exe (PID: 7060)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 3812)
The process executes Powershell scripts
- cmd.exe (PID: 5880)
- cmd.exe (PID: 3640)
- cmd.exe (PID: 7060)
- cmd.exe (PID: 2484)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 3812)
The process hide an interactive prompt from the user
- cmd.exe (PID: 7060)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 3812)
Executes script without checking the security policy
- powershell.exe (PID: 624)
- powershell.exe (PID: 6544)
- powershell.exe (PID: 5488)
INFO
Reads the computer name
- Hone - Installer.exe (PID: 2072)
- Hone - Installer.exe (PID: 6940)
- OWInstaller.exe (PID: 6988)
- ow-electron-setup.exe (PID: 6524)
- Hone.exe (PID: 6880)
- Hone.exe (PID: 4864)
- Hone.exe (PID: 4444)
- HoneStartup.exe (PID: 1228)
- HoneStartup.exe (PID: 2088)
- HoneStartup.exe (PID: 7148)
- Hone.exe (PID: 6408)
- gamefinder472.exe (PID: 3560)
- identity_helper.exe (PID: 5404)
- gamefinder472.exe (PID: 7152)
Process checks computer location settings
- Hone - Installer.exe (PID: 2072)
- OWInstaller.exe (PID: 6988)
- Hone.exe (PID: 6880)
- Hone.exe (PID: 4548)
- Hone.exe (PID: 5628)
- Hone.exe (PID: 4020)
- Hone.exe (PID: 6408)
Checks supported languages
- Hone - Installer.exe (PID: 6940)
- Hone - Installer.exe (PID: 2072)
- OWInstaller.exe (PID: 6988)
- Hone.exe (PID: 4864)
- Hone.exe (PID: 4444)
- Hone.exe (PID: 4548)
- Hone.exe (PID: 6880)
- Hone.exe (PID: 5628)
- Hone.exe (PID: 4020)
- Hone.exe (PID: 6408)
- HoneStartup.exe (PID: 1228)
- HoneStartup.exe (PID: 2088)
- HoneStartup.exe (PID: 7148)
- ow-electron-setup.exe (PID: 6524)
- gamefinder472.exe (PID: 7152)
- identity_helper.exe (PID: 5404)
- gamefinder472.exe (PID: 3560)
Create files in a temporary directory
- Hone - Installer.exe (PID: 2072)
- Hone - Installer.exe (PID: 6940)
- OWInstaller.exe (PID: 6988)
- ow-electron-setup.exe (PID: 6524)
- Hone.exe (PID: 6880)
- Hone.exe (PID: 6408)
The sample compiled with english language support
- Hone - Installer.exe (PID: 6940)
- Hone - Installer.exe (PID: 2072)
- ow-electron-setup.exe (PID: 6524)
- Hone.exe (PID: 6408)
- msedge.exe (PID: 3464)
Checks proxy server information
- Hone - Installer.exe (PID: 6940)
- OWInstaller.exe (PID: 6988)
- Hone.exe (PID: 6880)
Creates files or folders in the user directory
- Hone - Installer.exe (PID: 6940)
- OWInstaller.exe (PID: 6988)
- ow-electron-setup.exe (PID: 6524)
- Hone.exe (PID: 6880)
- Hone.exe (PID: 4444)
- Hone.exe (PID: 6408)
Reads the machine GUID from the registry
- OWInstaller.exe (PID: 6988)
- Hone.exe (PID: 6880)
- gamefinder472.exe (PID: 3560)
- gamefinder472.exe (PID: 7152)
The process uses the downloaded file
- OWInstaller.exe (PID: 6988)
- powershell.exe (PID: 6216)
- powershell.exe (PID: 2280)
- powershell.exe (PID: 5980)
- powershell.exe (PID: 3564)
- powershell.exe (PID: 6056)
Disables trace logs
- OWInstaller.exe (PID: 6988)
Reads Environment values
- OWInstaller.exe (PID: 6988)
- Hone.exe (PID: 6880)
- identity_helper.exe (PID: 5404)
- Hone.exe (PID: 6408)
Reads the software policy settings
- OWInstaller.exe (PID: 6988)
- Hone.exe (PID: 4864)
Creates files in the program directory
- ow-electron-setup.exe (PID: 6524)
- Hone.exe (PID: 6880)
Reads product name
- Hone.exe (PID: 6880)
- Hone.exe (PID: 6408)
Reads CPU info
- Hone.exe (PID: 6880)
Application launched itself
- msedge.exe (PID: 6464)
- msedge.exe (PID: 5528)
Manual execution by a user
- msedge.exe (PID: 5528)
Executable content was dropped or overwritten
- msedge.exe (PID: 3464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.266.0.9 |
| ProductVersionNumber: | 2.266.0.9 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Overwolf Ltd. |
| FileDescription: | Hone |
| FileVersion: | 2.266.0.9 |
| LegalCopyright: | Copyright (C) 2021 Overwolf Ltd. All Rights Reserved. |
| LegalTrademarks: | - |
| ProductName: | Hone |
| ProductVersion: | 2.266.0.9 |
Total processes
249
Monitored processes
114
Malicious processes
6
Suspicious processes
16
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6660 --field-trial-handle=2408,i,9294265890763459403,3932804957510556234,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 236 | reg add "hklm\Software\Classes\hone" /v "URL Protocol" /t REG_SZ /d "" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6800 --field-trial-handle=2408,i,9294265890763459403,3932804957510556234,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 440 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 624 | "C:\WINDOWS\System32\WindowsPowershell\v1.0\powershell.exe" -NoL -NoP -EP Bypass -NonI -C "Set-Location 'C:\Users\admin\AppData\Local\Programs\Hone\resources\assets\hone-resources'; . 'c:\ProgramData\Microsoft\a9d02333-77a9-4262-8293-1752416973eb.ps1'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 768 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3512 --field-trial-handle=2408,i,9294265890763459403,3932804957510556234,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 828 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6232 --field-trial-handle=2408,i,9294265890763459403,3932804957510556234,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5172 --field-trial-handle=2408,i,9294265890763459403,3932804957510556234,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1228 | C:\Users\admin\AppData\Local\Programs\Hone\resources\assets\hone-resources\HoneStartup.exe | C:\Users\admin\AppData\Local\Programs\Hone\resources\assets\hone-resources\HoneStartup.exe | — | Hone.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
50 143
Read events
50 044
Write events
79
Delete events
20
Modification events
| (PID) Process: | (6940) Hone - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6940) Hone - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6940) Hone - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6988) OWInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\OverwolfPersist |
| Operation: | write | Name: | MUIDV2 |
Value: a75ce88d-8997-43db-bac3-0c204641b3d3 | |||
| (PID) Process: | (6988) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\OverwolfPersist |
| Operation: | write | Name: | MUIDV2 |
Value: a75ce88d-8997-43db-bac3-0c204641b3d3 | |||
| (PID) Process: | (6988) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Overwolf |
| Operation: | write | Name: | MUID |
Value: bb926e54-e3ca-40fd-ae90-2764341e7792 | |||
| (PID) Process: | (6988) OWInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\OverwolfElectron |
| Operation: | write | Name: | MUID |
Value: bb926e54-e3ca-40fd-ae90-2764341e7792 | |||
| (PID) Process: | (6988) OWInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6988) OWInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6988) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
90
Suspicious files
733
Text files
257
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2072 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsd53A2.tmp\uac.dll | executable | |
MD5:861F7E800BB28F68927E65719869409C | SHA256:10A0E8CF46038AB3B2C3CF5DCE407B9A043A631CBDE9A5C8BCF0A54B2566C010 | |||
| 2072 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsd53A2.tmp\partner-custom-asset.png | image | |
MD5:BAE604C0326ED9356CFD21E41C7840E2 | SHA256:F242F6BFD1181F07F91756350B4433D8E6D8D04A3F5F71915692E657CFDB7A84 | |||
| 2072 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsd53A2.tmp\Newtonsoft.Json.dll | executable | |
MD5:98CBB64F074DC600B23A2EE1A0F46448 | SHA256:7B44639CBFBC8DDAC8C7A3DE8FFA97A7460BEBB0D54E9FF2E1CCDC3A742C2B13 | |||
| 2072 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsd53A2.tmp\UserInfo.dll | executable | |
MD5:1DD4CA0F4A94155F8D46EC95A20ADA4A | SHA256:A27DC3069793535CB64123C27DCA8748983D133C8FA5AADDEE8CDBC83F16986D | |||
| 2072 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsd53A2.tmp\nsis7z.dll | executable | |
MD5:349B66CC74FA4012D3E3D809E71A89ED | SHA256:8A21A99FEA5967EE2E500FBB8BC220FB55C05D25F1815922D44A1BDB7141D4FB | |||
| 2072 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsd53A2.tmp\log4net.dll | executable | |
MD5:F15C8A9E2876568B3910189B2D493706 | SHA256:AE9C8073C3357C490F5D1C64101362918357C568F6B9380A60B09A4A4C1FF309 | |||
| 2072 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsd53A2.tmp\CommandLine.dll | executable | |
MD5:210472E9E333D3329072C9EA3EF06326 | SHA256:569307401B949368527B128155B4E16B349803EC7D65C1052CC23C7B7A1336D8 | |||
| 2072 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsd53A2.tmp\nsProcess.dll | executable | |
MD5:10E47E822B85D2A12FA4727001612182 | SHA256:D530589A90918334B8E08D7355630892DD62F41333D948A860735D5BECFCB391 | |||
| 2072 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsd53A2.tmp\app\game_detection_database.json | binary | |
MD5:336D26D3E0AB31E8DC102EA86C48FA26 | SHA256:F30B571B8BB396AA0BCA9AA9B80638416EC638DE5C4788BC281AC67D3D54CCAF | |||
| 2072 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsd53A2.tmp\OverWolf.Client.CommonUtils.dll | executable | |
MD5:DA655A4D82DBBA4C0F442429047E1A7E | SHA256:A935C85EB5DE3333E9883D8B6BE6176D775B524FB13EC1D13D9F8705ECD80601 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
64
TCP/UDP connections
149
DNS requests
143
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6988 | OWInstaller.exe | GET | 200 | 172.217.18.110:80 | http://www.google-analytics.com/__utm.gif?utmwv=4.7.2&utmn=407571616&utmhn=&utmcs=UTF-8&utmsr=-&utmsc=-&utmul=-&utmje=0&utmfl=-&utmdt=&utmhid=81069139&utmr=/&utmp=/&utmac=UA-80584726-1&utmcc=__utma%3D0.1567748313.1736608176.1736608176.1736608176.2%3B%2B__utmz%3D0.1736608176.1.1.utmcsr%3D%28direct%29%7Cutmccn%3D%7Cutmcmd%3D%3B&utme=5%28Funnel2%2AInstaller%20Launched%2A%29%28%29&gaq=1&utmt=event | unknown | — | — | whitelisted |
6988 | OWInstaller.exe | GET | 200 | 172.217.18.110:80 | http://www.google-analytics.com/__utm.gif?utmwv=4.7.2&utmn=710735890&utmhn=&utmcs=UTF-8&utmsr=-&utmsc=-&utmul=-&utmje=0&utmfl=-&utmdt=&utmhid=758396338&utmr=/&utmp=/&utmac=UA-18298709-8&utmcc=__utma%3D0.1567748313.1736608176.1736608176.1736608176.2%3B%2B__utmz%3D0.1736608176.1.1.utmcsr%3D%28direct%29%7Cutmccn%3D%7Cutmcmd%3D%3B&utme=5%28Funnel2%2AInstaller%20Launched%2A%29%28%29&gaq=1&utmt=event | unknown | — | — | whitelisted |
6988 | OWInstaller.exe | GET | 200 | 18.66.145.213:80 | http://ocsp.rootca3.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRkNawYMzz%2BjKSfYbTyFR0AXuhs6QQUq7bb1waeN6wwhgeRcMecxBmxeMACEwdzEm3iwvr9LEetiLFWbgGCBG0%3D | unknown | — | — | unknown |
6988 | OWInstaller.exe | GET | 200 | 216.58.206.67:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQD4ZvdMc2VaVBBsza0qVaGi | unknown | — | — | whitelisted |
6988 | OWInstaller.exe | GET | 200 | 18.66.145.213:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | — | — | unknown |
5872 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6988 | OWInstaller.exe | GET | 200 | 216.58.206.67:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQC43tOywHj%2BZRL%2FyfPgB5LY | unknown | — | — | whitelisted |
5004 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6988 | OWInstaller.exe | GET | 200 | 172.217.18.110:80 | http://www.google-analytics.com/__utm.gif?utmwv=4.7.2&utmn=213022174&utmhn=&utmcs=UTF-8&utmsr=-&utmsc=-&utmul=-&utmje=0&utmfl=-&utmdt=&utmhid=366667753&utmr=/&utmp=/&utmac=UA-18298709-8&utmcc=__utma%3D0.1567748313.1736608176.1736608176.1736608176.2%3B%2B__utmz%3D0.1736608176.1.1.utmcsr%3D%28direct%29%7Cutmccn%3D%7Cutmcmd%3D%3B&utme=5%28Funnel2%2AInstalled%20Successfully%2A%29%28%29&gaq=1&utmt=event | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2356 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2356 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.34:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
analyticsnew.overwolf.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6940 | Hone - Installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
4548 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
4548 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6 ETPRO signatures available at the full report