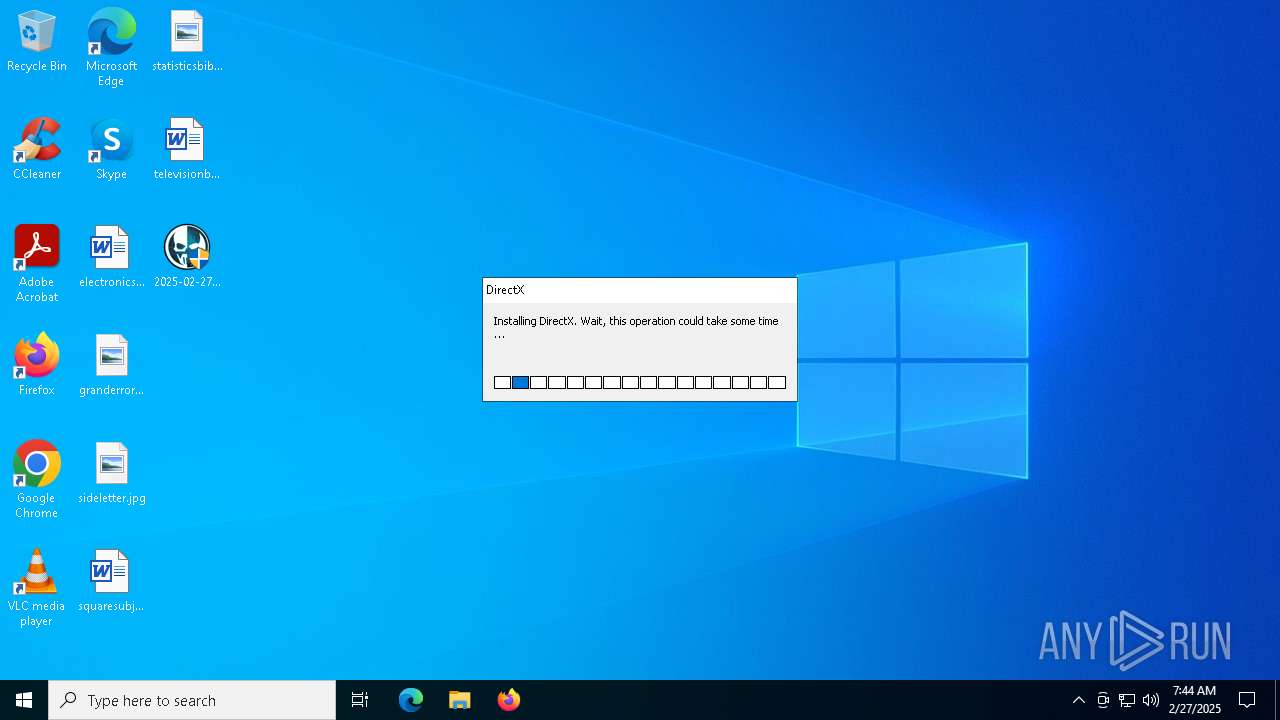
| File name: | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid |
| Full analysis: | https://app.any.run/tasks/2f393195-f564-47f5-b3f8-ec97e7a52102 |
| Verdict: | Malicious activity |
| Analysis date: | February 27, 2025, 07:43:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 5EDE1711FDD104FD06CF464610F324C3 |
| SHA1: | C8F27A8B69EE96E98DA554A638B822C10CAAC045 |
| SHA256: | 0FEC22408E1A754C0709B1A0686D511F0E960E24F920BA25AE0180D8BC27C99E |
| SSDEEP: | 98304:fzKHLlk7b5kRBak9/wNqxhqd2pvDa+1qUSfOIocFR68gfmhPPzHiFwYE9sDRhqJy:UBTEc2h2 |
MALICIOUS
Executing a file with an untrusted certificate
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 4120)
- DXSETUP.exe (PID: 1188)
Connects to the CnC server
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
SUSPICIOUS
Process drops legitimate windows executable
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
- DXSETUP.exe (PID: 1188)
Executable content was dropped or overwritten
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
- DXSETUP.exe (PID: 1188)
Starts a Microsoft application from unusual location
- DXSETUP.exe (PID: 1188)
Executes as Windows Service
- VSSVC.exe (PID: 900)
Reads security settings of Internet Explorer
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
- DXSETUP.exe (PID: 1188)
- Installer.exe (PID: 5084)
Searches for installed software
- dllhost.exe (PID: 6272)
- Installer.exe (PID: 5084)
Contacting a server suspected of hosting an CnC
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
There is functionality for taking screenshot (YARA)
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
Checks Windows Trust Settings
- DXSETUP.exe (PID: 1188)
- Installer.exe (PID: 5084)
Creates/Modifies COM task schedule object
- DXSETUP.exe (PID: 1188)
Adds/modifies Windows certificates
- Installer.exe (PID: 5084)
INFO
The sample compiled with english language support
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
- DXSETUP.exe (PID: 1188)
Checks supported languages
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
- DXSETUP.exe (PID: 1188)
- Installer.exe (PID: 5084)
Reads the computer name
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
- DXSETUP.exe (PID: 1188)
- Installer.exe (PID: 5084)
Create files in a temporary directory
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
- DXSETUP.exe (PID: 1188)
Checks proxy server information
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
- DXSETUP.exe (PID: 1188)
- Installer.exe (PID: 5084)
- slui.exe (PID: 4452)
Creates files in the program directory
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
UPX packer has been detected
- 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe (PID: 1812)
Reads the machine GUID from the registry
- DXSETUP.exe (PID: 1188)
- Installer.exe (PID: 5084)
Manages system restore points
- SrTasks.exe (PID: 6656)
Reads the software policy settings
- DXSETUP.exe (PID: 1188)
- Installer.exe (PID: 5084)
- slui.exe (PID: 4452)
Disables trace logs
- Installer.exe (PID: 5084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:09:28 01:37:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 851968 |
| InitializedDataSize: | 3665920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8d103 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.81.0 |
| ProductVersionNumber: | 2.0.81.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | DevAge, Vestris Inc. & Contributors |
| FileDescription: | - |
| FileVersion: | 2.0.81.0 |
| InternalName: | - |
| LegalCopyright: | Copyright (c) DevAge, Vestris Inc. & Contributors |
| LegalTrademarks: | All Rights Reserved |
| OLESelfRegister: | - |
| OriginalFileName: | - |
| PrivateBuild: | - |
| ProductName: | dotNetInstaller |
| ProductVersion: | 2.0.81.0 |
| SpecialBuild: | - |
Total processes
134
Monitored processes
9
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 900 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\DXRedist\DXSETUP.exe /silent | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\DXRedist\DXSETUP.exe | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft DirectX Setup Exit code: 0 Version: 4.9.0.0904 Modules
| |||||||||||||||
| 1812 | "C:\Users\admin\Desktop\2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe" | C:\Users\admin\Desktop\2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | explorer.exe | ||||||||||||
User: admin Company: DevAge, Vestris Inc. & Contributors Integrity Level: HIGH Exit code: 0 Version: 2.0.81.0 Modules
| |||||||||||||||
| 4120 | "C:\Users\admin\Desktop\2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe" | C:\Users\admin\Desktop\2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | — | explorer.exe | |||||||||||
User: admin Company: DevAge, Vestris Inc. & Contributors Integrity Level: MEDIUM Exit code: 3221226540 Version: 2.0.81.0 Modules
| |||||||||||||||
| 4452 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5084 | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\InstallLauncher\Installer.exe | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\InstallLauncher\Installer.exe | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | ||||||||||||
User: admin Company: Ubisoft Integrity Level: HIGH Description: Installer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6272 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6656 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 172
Read events
15 936
Write events
209
Delete events
27
Modification events
| (PID) Process: | (1812) 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1812) 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1812) 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1188) DXSETUP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\DirectX |
| Operation: | write | Name: | command |
Value: 0 | |||
| (PID) Process: | (1188) DXSETUP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\DirectX |
| Operation: | write | Name: | DXSetup |
Value: 0 | |||
| (PID) Process: | (1188) DXSETUP.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000C18F6763EB88DB01A40400003C080000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6272) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000C18F6763EB88DB0180180000D81A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6272) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000089E4B363EB88DB0180180000D81A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6272) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000089E4B363EB88DB0180180000D81A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6272) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000004598B863EB88DB0180180000D81A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
34
Suspicious files
38
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | C:\Users\admin\AppData\Local\Temp\DVCFB6.tmp | image | |
MD5:1A2FDECE59714CD7A59B2354B8402C67 | SHA256:0912175D9A556EB372E836D2675EE591A1F0D971C63E4D22DDBC245C7B5C954C | |||
| 1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\DXRedist\Jun2010_D3DCompiler_43_x86.cab | compressed | |
MD5:F7F554AA613ECCF065575B8C69717EF7 | SHA256:417EEBD5B19F45C67C94C2D2BA8B774C0FC6D958B896D7B1AC12CF5A0EA06E0E | |||
| 1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\DXRedist\Jun2010_XAudio_x86.cab | compressed | |
MD5:9D2DA3B1055120AF7C2995896F5D51ED | SHA256:7B4332207563BEBA1103744B6DB5399AD150E9E6838F9D5A71497E7EB3645EBF | |||
| 1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\DXRedist\APR2007_xinput_x86.cab | compressed | |
MD5:C234DF417C9B12E2D31C7FD1E17E4786 | SHA256:2ACEA6C8B9F6F7F89EC51365A1E49FBD0D8C42C53418BD0783DBF3F74A744E6D | |||
| 1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\DXRedist\dxdllreg_x86.cab | compressed | |
MD5:A025C67403DC2C2BCD709AA9435FAEB1 | SHA256:8AD77A4D9C76F65CD62337588F847CC1E0CA6CA9735937F3A781F7395E9566A1 | |||
| 1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\DXRedist\dsetup32.dll | executable | |
MD5:0F58CCD58A29827B5D406874360E4C08 | SHA256:642D9E7DB6D4FC15129F011DCE2EA087BF7F7FB015AECECF82BF84FF6634A6FB | |||
| 1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\DXRedist\DSETUP.dll | executable | |
MD5:9E0711BED229B60A853BCC5D10DEAAFC | SHA256:DEF6F245762BE36CF18B435BA8B7EBC224B9C21D1A1DB606A8E8FAFDAA97BBA0 | |||
| 1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\DXRedist\Jun2010_d3dx9_43_x86.cab | compressed | |
MD5:7749862C307E527366B6868326DB8198 | SHA256:FCC6CF0966B4853D6FA3D32AB299CDE5A9824FEAECB0D4F34EA452FB9FD1C867 | |||
| 1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\DXRedist\dxupdate.cab | compressed | |
MD5:8ADF5A3C4BD187052BFA92B34220F4E7 | SHA256:13393A91201E69E70A9F68D21428453FFF3951535DEC88F879270269CFE54D6F | |||
| 1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | C:\Users\admin\AppData\Local\Temp\{BCBA8581-F6C1-40C5-BEEB-74402F51DC3D}\InstallLauncher\config.ini | binary | |
MD5:B7AC82425E76F541DD1D0A9FFD311B2F | SHA256:A8D826D794FCC2D9E3C39394EEA0BA887F78293B76EC0C7BC763B61B50AD42EF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
36
DNS requests
16
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | GET | 403 | 96.126.123.244:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | GET | 403 | 96.126.123.244:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
1188 | DXSETUP.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/CSPCA.crl | unknown | — | — | whitelisted |
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | GET | 403 | 96.126.123.244:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
5084 | Installer.exe | GET | 404 | 172.64.149.23:80 | http://crl.usertrust.com/AddTrustExternalCARoot.crl | unknown | — | — | whitelisted |
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | GET | 403 | 96.126.123.244:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
5084 | Installer.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | unknown | — | — | whitelisted |
5084 | Installer.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | unknown | — | — | whitelisted |
5084 | Installer.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEC58h8wOk0pS%2FpT9HLfNNK8%3D | unknown | — | — | whitelisted |
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | GET | 403 | 96.126.123.244:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | 96.126.123.244:80 | www.aieov.com | Linode, LLC | US | malicious |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1188 | DXSETUP.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5084 | Installer.exe | 104.18.38.233:80 | ocsp.usertrust.com | CLOUDFLARENET | — | whitelisted |
5084 | Installer.exe | 172.64.149.23:80 | ocsp.usertrust.com | CLOUDFLARENET | US | whitelisted |
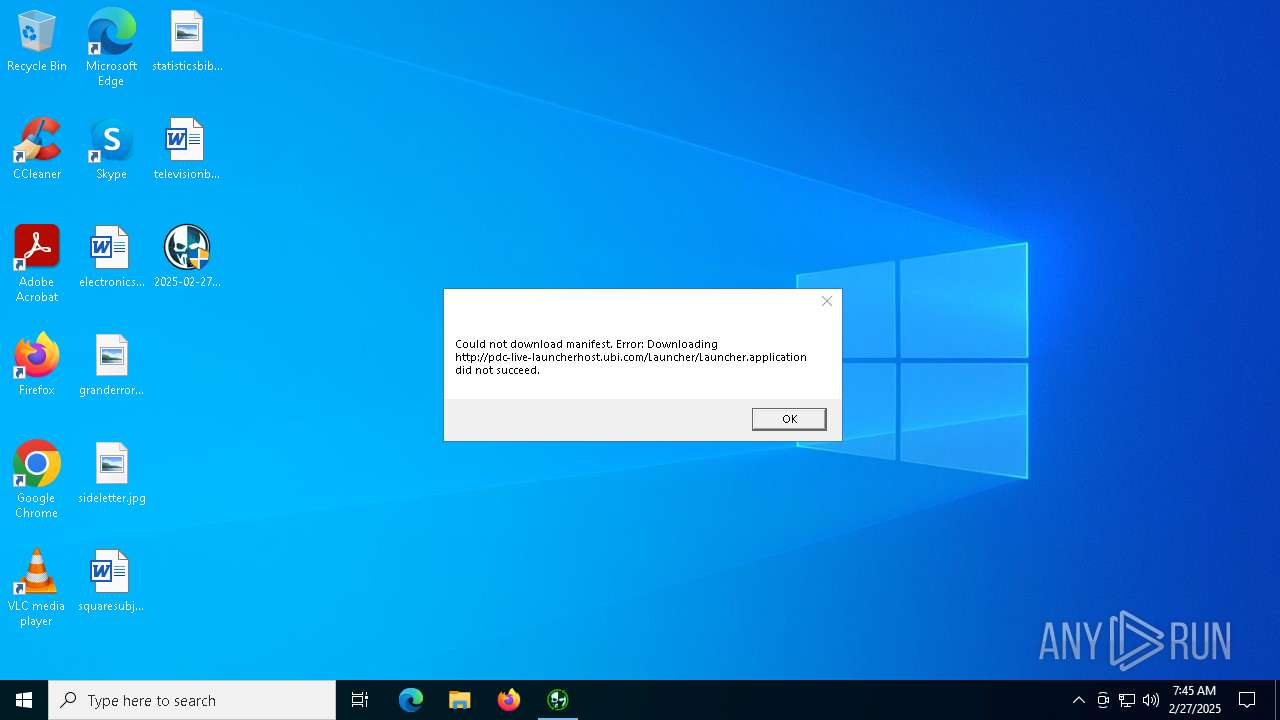
5084 | Installer.exe | 195.22.144.89:80 | pdc-live-launcherhost.ubi.com | Ubisoft International SAS | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
5isohu.com |
| whitelisted |
www.aieov.com |
| malicious |
crl.microsoft.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
crl.usertrust.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
pdc-live-launcherhost.ubi.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
1812 | 2025-02-27_5ede1711fdd104fd06cf464610f324c3_floxif_icedid.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
5084 | Installer.exe | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |