| File name: | Systeme.exe |
| Full analysis: | https://app.any.run/tasks/fffaa2f4-2603-4bbc-bdd1-15ec001340b5 |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2024, 09:26:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 7254BC46F8C6EF326A56B2B9CE745D7E |
| SHA1: | 6DC2B9DFF4EE9DDAE1A0DE72D8052EF355D8357B |
| SHA256: | 0FE8C87EDCD0880ADB34D1686514FA286D029B4EB87590F86F34C8C3F2DF9FDE |
| SSDEEP: | 12288:HsRC0dvzZjLLZ72OVjbiRIEUdLL1D1l14KAIFJADnRte6U8C0RecxvVGAyrW:MRC0dvzZjnZ7BNbiRIE831D1l1jAgqDD |
MALICIOUS
No malicious indicators.SUSPICIOUS
There is functionality for communication over UDP network (YARA)
- Systeme.exe (PID: 5748)
- Systeme.exe (PID: 5512)
Reads security settings of Internet Explorer
- Systeme.exe (PID: 5748)
Executable content was dropped or overwritten
- InstallFramework.exe (PID: 6916)
- Systeme.exe (PID: 5748)
Connects to unusual port
- Systeme.exe (PID: 5748)
- Systeme.exe (PID: 5512)
Connects to FTP
- Systeme.exe (PID: 5748)
Starts itself from another location
- Systeme.exe (PID: 5748)
INFO
Checks supported languages
- Systeme.exe (PID: 5748)
Reads the computer name
- Systeme.exe (PID: 5748)
Checks proxy server information
- Systeme.exe (PID: 5748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (46.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (41) |
| .exe | | | Win32 Executable (generic) (6.6) |
| .exe | | | Generic Win/DOS Executable (2.9) |
| .exe | | | DOS Executable Generic (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:03:22 08:39:05+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 73728 |
| InitializedDataSize: | 188416 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1222e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.16 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | French |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.00Qb |
| Version: | 1.00Qb |
| LegalCopyright: | - |
| WDVersion: | 16 |
| ProductName: | Acad |
| ProductVersion: | 1.00Qb |
Total processes
131
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5512 | C:\ProgramData\Systeme\Systeme.exe | C:\ProgramData\Systeme\Systeme.exe | Systeme.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.00Qb Modules
| |||||||||||||||
| 5748 | "C:\Users\admin\AppData\Local\Temp\Systeme.exe" | C:\Users\admin\AppData\Local\Temp\Systeme.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.00Qb Modules
| |||||||||||||||
| 6916 | "C:\Users\admin\AppData\Local\Temp\InstallFramework.exe" /REP="C:\Users\admin\AppData\Local\Temp\" /SILENT | C:\Users\admin\AppData\Local\Temp\InstallFramework.exe | Systeme.exe | ||||||||||||
User: admin Company: PC SOFT Integrity Level: MEDIUM Description: PC SOFT - Executable auto-extractible Exit code: 0 Version: 15.00Aa Modules
| |||||||||||||||
Total events
1 108
Read events
1 103
Write events
5
Delete events
0
Modification events
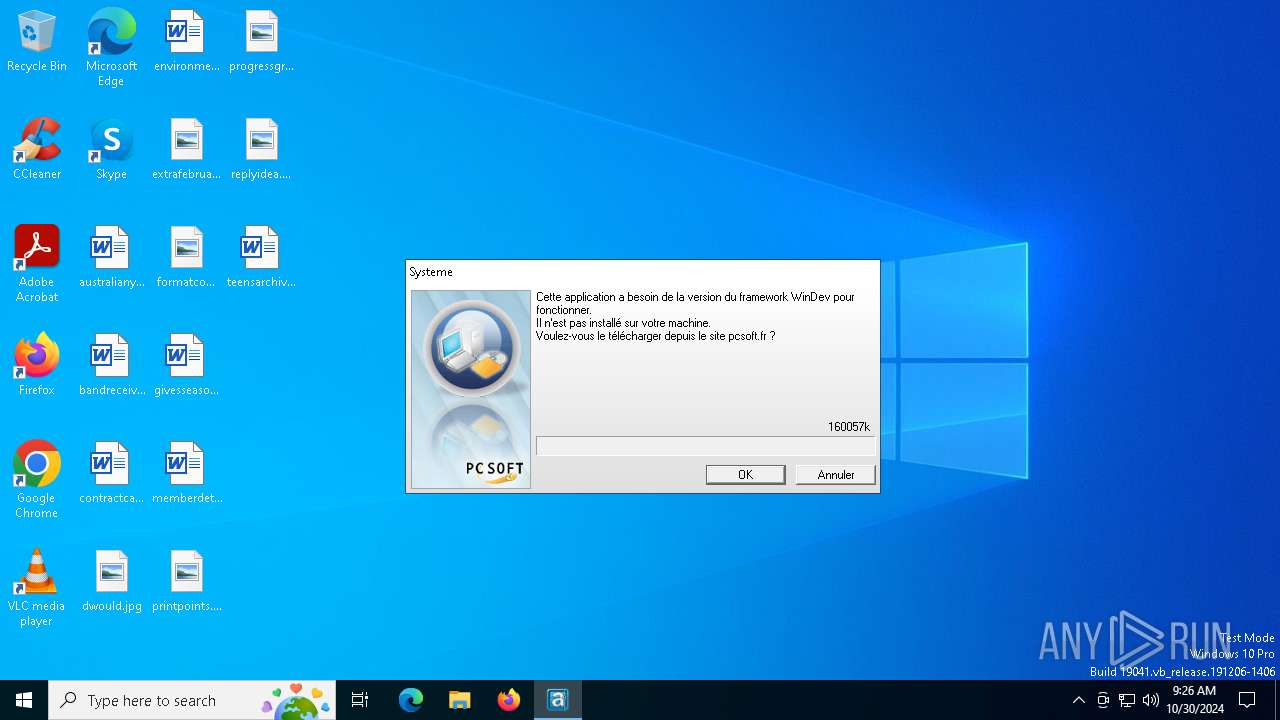
| (PID) Process: | (5748) Systeme.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\PC SOFT\WinDev\16.0\APPLI\Systeme |
| Operation: | write | Name: | LAST_FRAMEWORK |
Value: 160057k | |||
| (PID) Process: | (5748) Systeme.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5748) Systeme.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5748) Systeme.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5748) Systeme.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Poisson18 |
Value: C:\ProgramData\Systeme\Systeme.exe | |||
Executable files
47
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6916 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\wd160com.dll | executable | |
MD5:4D225127B75B51B44B830859560A9EF6 | SHA256:8DE8B4FEB26470463F13BFB48AAAD601702B9963DCB36354A056763570E7B9F3 | |||
| 6916 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\wd160ce.dll | executable | |
MD5:2DDF6672A67C7E33F2B215AF8CFAE4BC | SHA256:445225C9BD489BCC17B39FD3A5AC35FDB0B2F1149CB682CAB712C6018F5C6D4D | |||
| 6916 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\wd160cpl.dll | executable | |
MD5:E963C9984D3B2DBD75940BF47A6C4B9F | SHA256:60D5778E349EFDE5C2E8B87491B39B78CCAB495BCD502022698251CC81A59B22 | |||
| 6916 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\wd160agt.dll | executable | |
MD5:CE48B94ECFBE8C34B29D559B4CF3FC73 | SHA256:4A0B0B2EA41044CC9062A1DC076B3149A6C3EA2ED11653F131F4CBB2139DB3DC | |||
| 5748 | Systeme.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\InstallFramework_160057k[1].exe | executable | |
MD5:4152937F33475D31249CE919C323AFA3 | SHA256:BE986D474F493ED6098760AAA958E86499F495E352242CE022FFF81B434F930F | |||
| 6916 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\wd160barc.dll | executable | |
MD5:F7B37B4A7077A65C9C00129F81DB429E | SHA256:917786738AD36FFBC20152EADB75A7702C6213155DBA3AD5DD87DAE10396C6F8 | |||
| 6916 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\wd160hf.dll | executable | |
MD5:78A4482B551B7A68D0655772F0C750B8 | SHA256:91DE274BDA06509F62B23261E3437988694987B938CB441B8FAAD3AF2183851A | |||
| 6916 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\wd160db.dll | executable | |
MD5:FF71B65D39FCB54CF5BDEC1E38833BC4 | SHA256:E22E591167FC5FFC4D5D18C1ADCD08F78B234FE5D906C78FA8583A8C5DADACD7 | |||
| 6916 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\wd160gpu.dll | executable | |
MD5:E03380FDFEA5121AF207174414CAB5A9 | SHA256:475DF80DD8C2E7094E553B7753AA95A1E8294B0C12C322397329AB56A87B74D3 | |||
| 6916 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\wd160etat.dll | executable | |
MD5:68BBACFC966C59E7DF74EF90003BB836 | SHA256:83A82ED17E0DB8B537AD9C45967E8D28B22533C0AC7B2B3819386465BE28F43B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
46
DNS requests
25
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.18.97.123:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5736 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5512 | Systeme.exe | GET | 200 | 212.129.20.209:80 | http://www.monip.org/ | unknown | — | — | unknown |
4516 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4432 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4432 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
632 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.209.173:443 | — | Akamai International B.V. | GB | unknown |
5748 | Systeme.exe | 51.89.20.151:21 | framework.pcsoft.fr | OVH SAS | GB | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5748 | Systeme.exe | 51.89.20.151:50705 | framework.pcsoft.fr | OVH SAS | GB | whitelisted |
5748 | Systeme.exe | 51.89.20.151:50445 | framework.pcsoft.fr | OVH SAS | GB | whitelisted |
6944 | svchost.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
framework.pcsoft.fr |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
www.monip.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5748 | Systeme.exe | Misc activity | ET INFO .exe File requested over FTP |
5748 | Systeme.exe | Misc activity | ET HUNTING PE EXE Download over raw TCP |