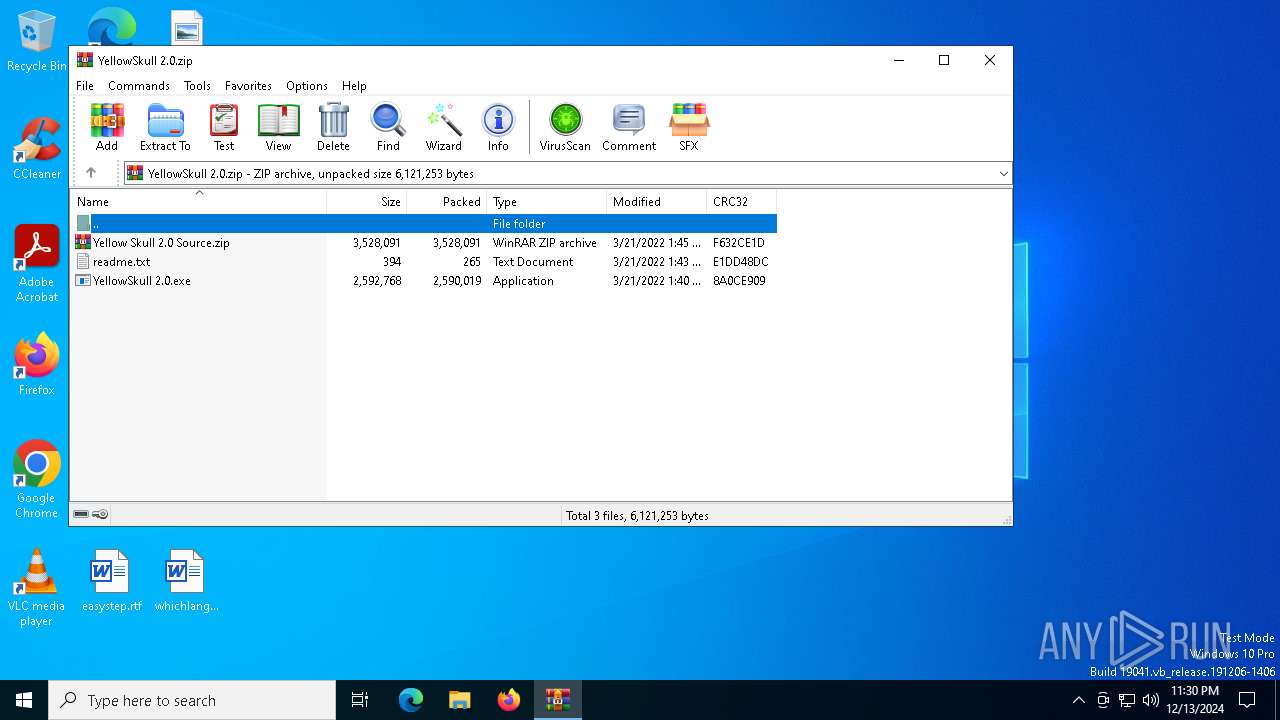
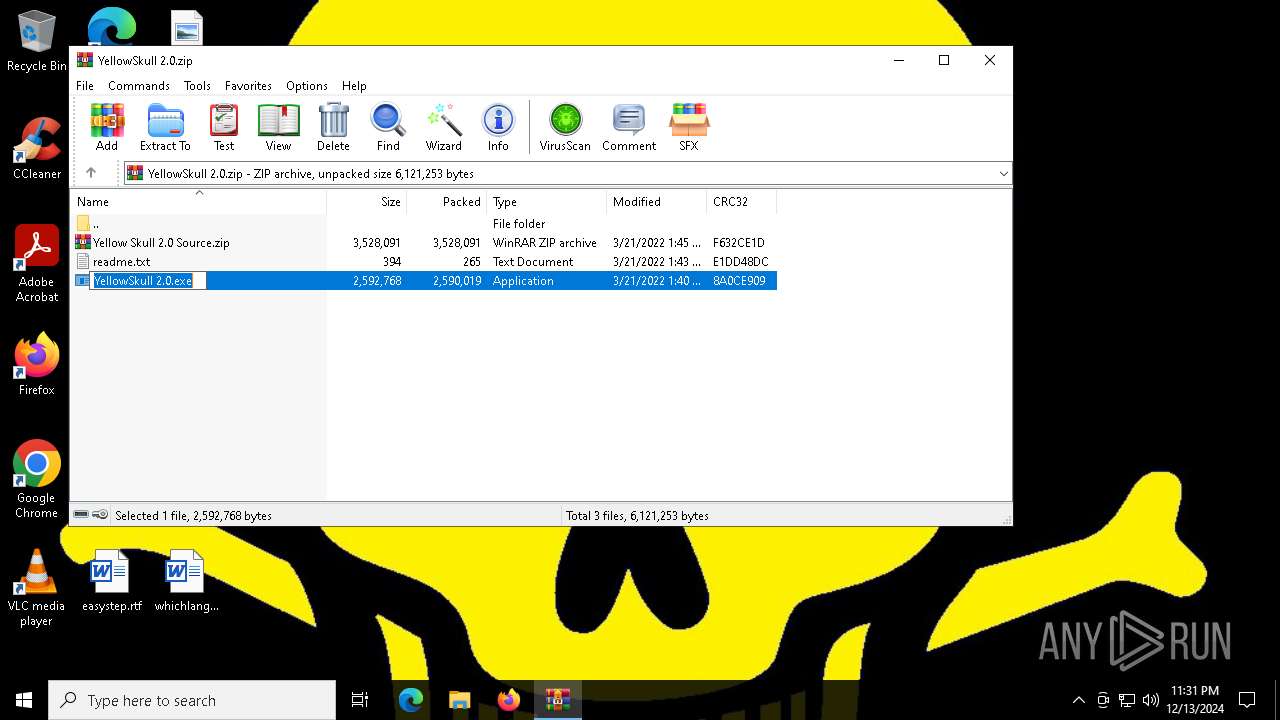
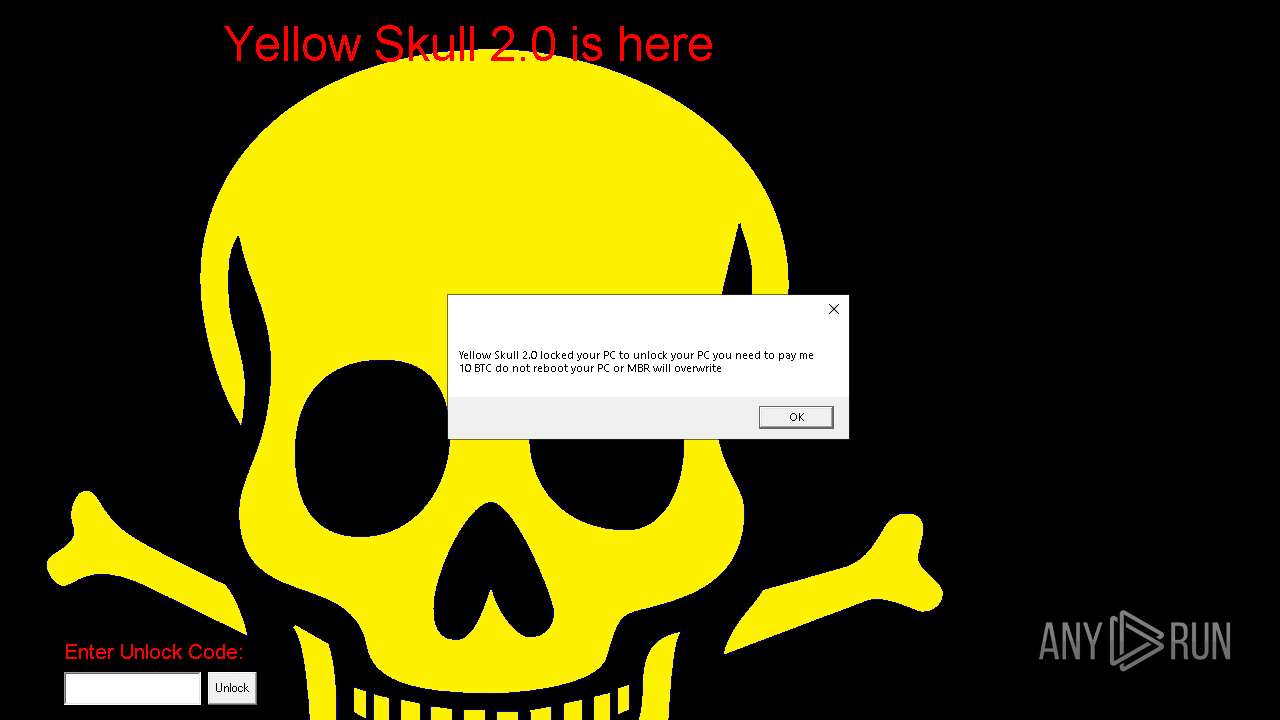
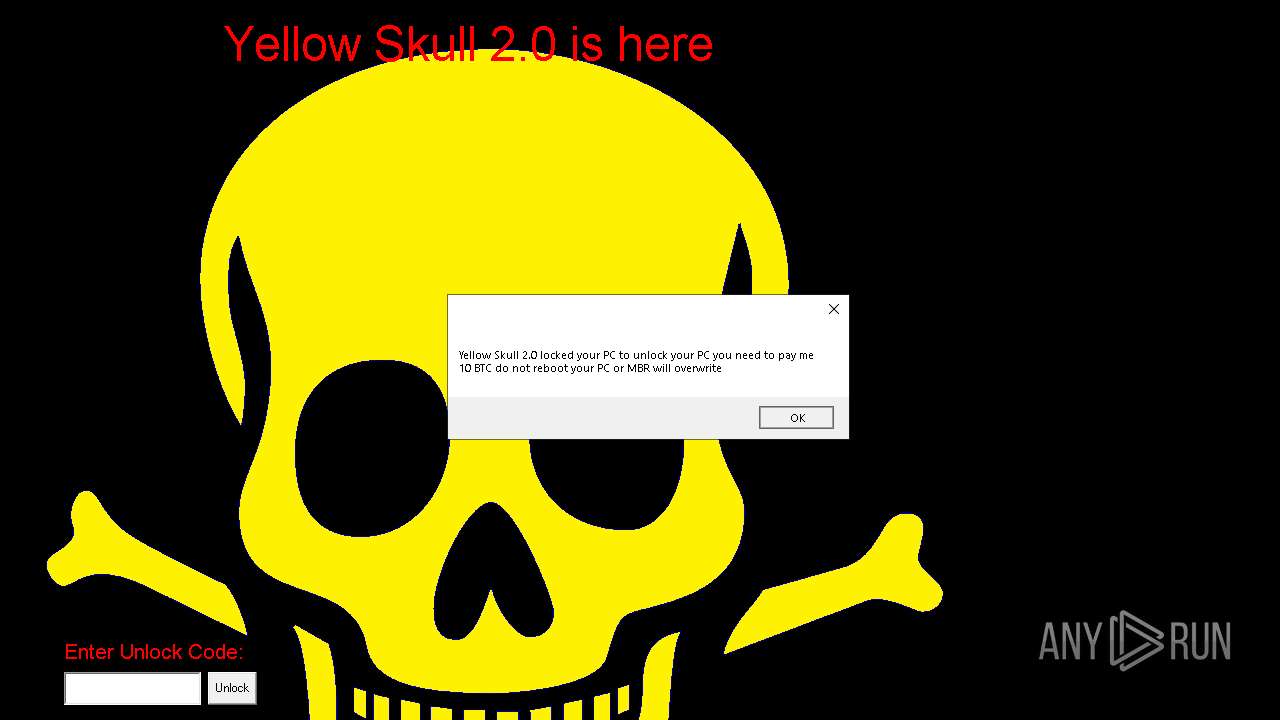
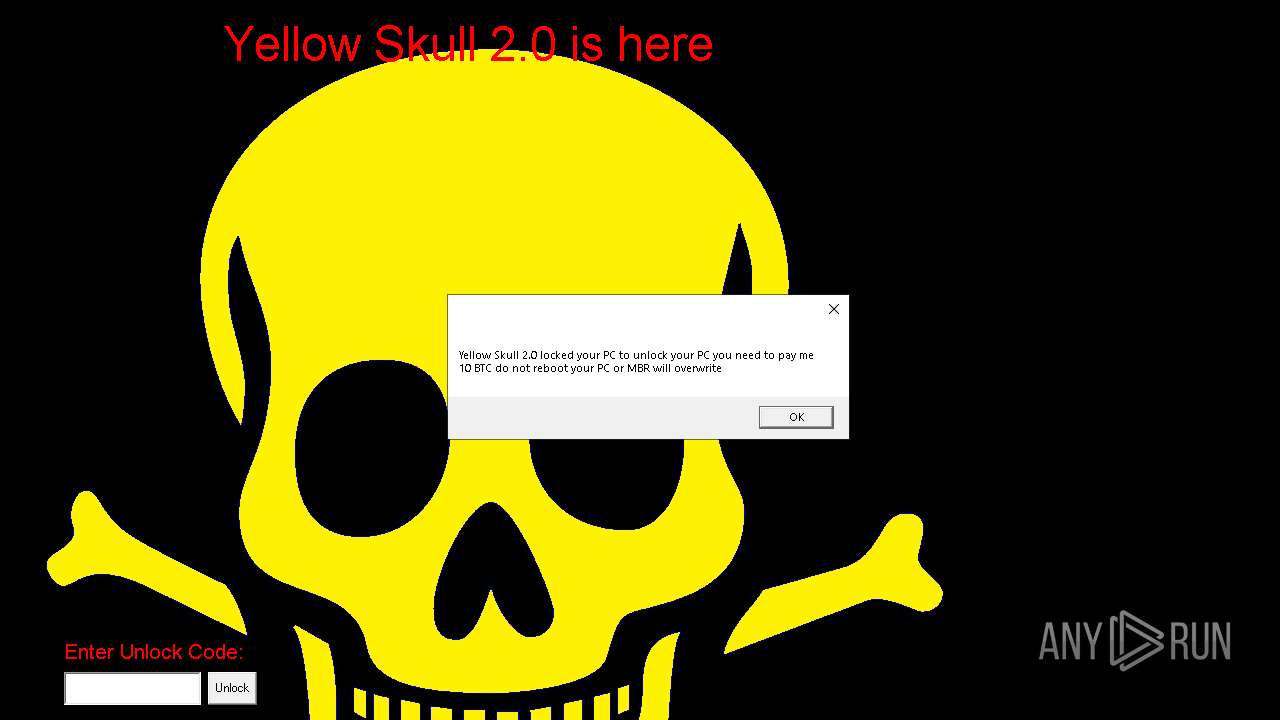
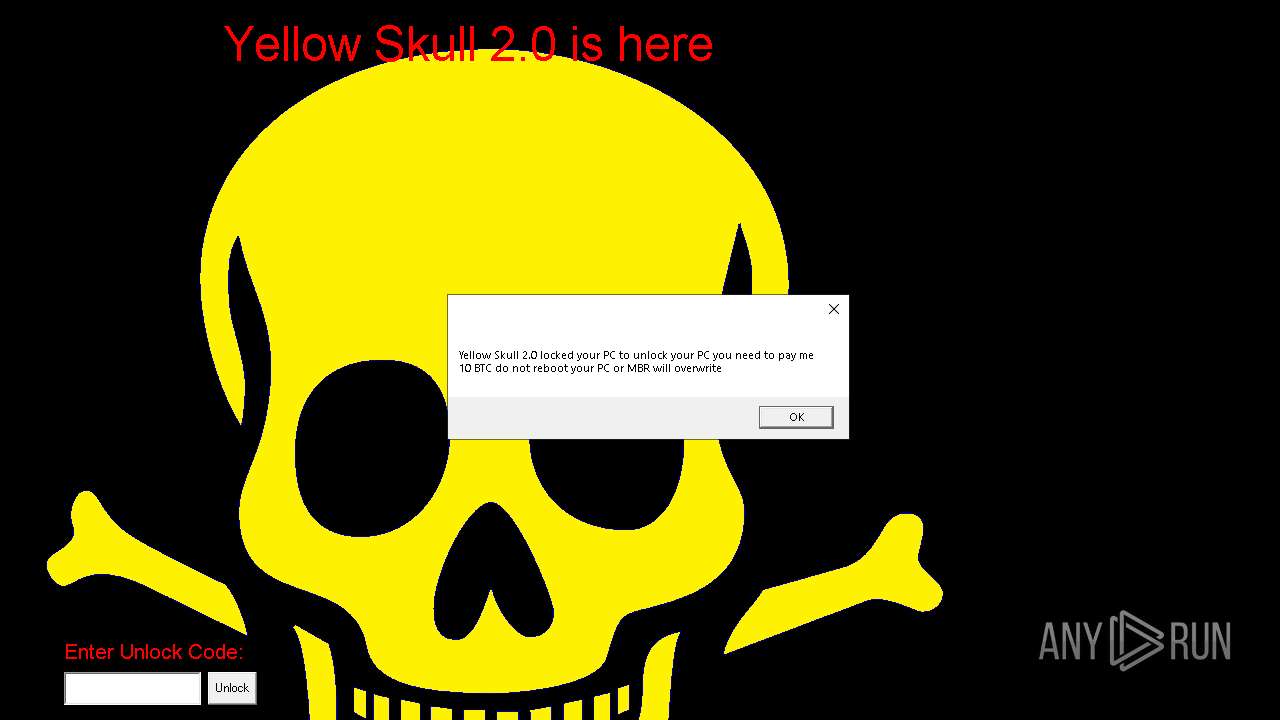
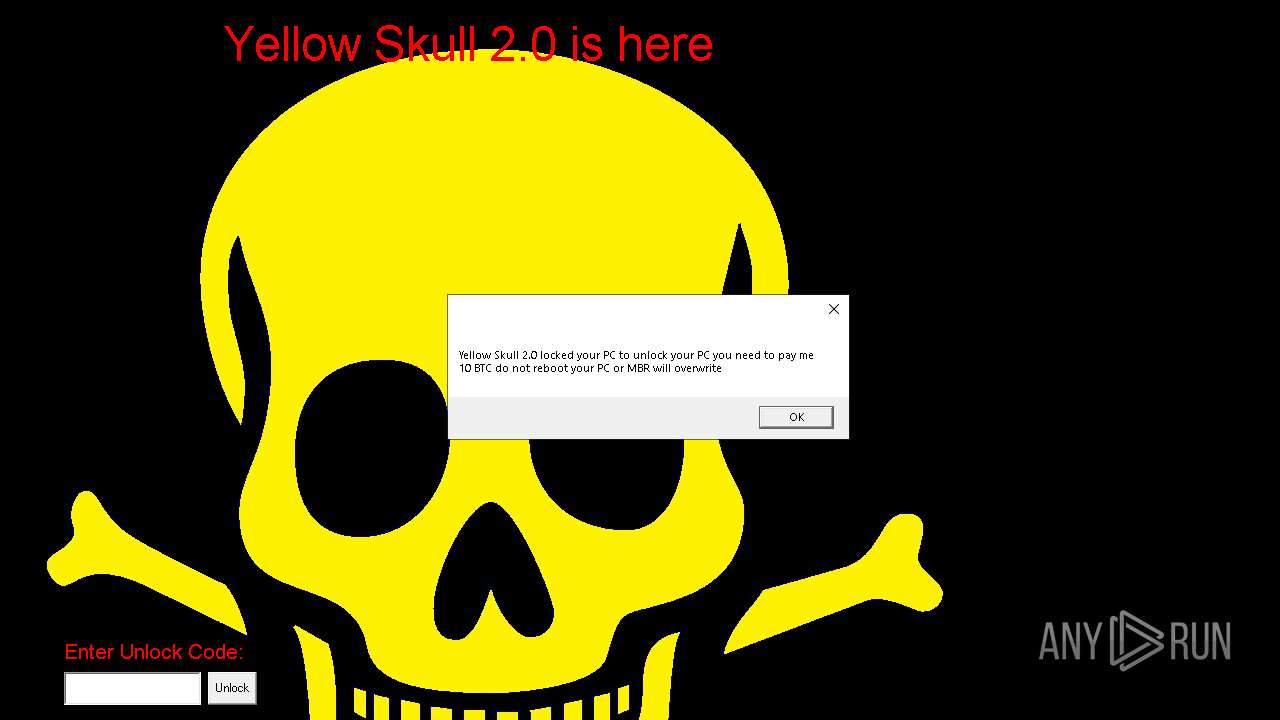
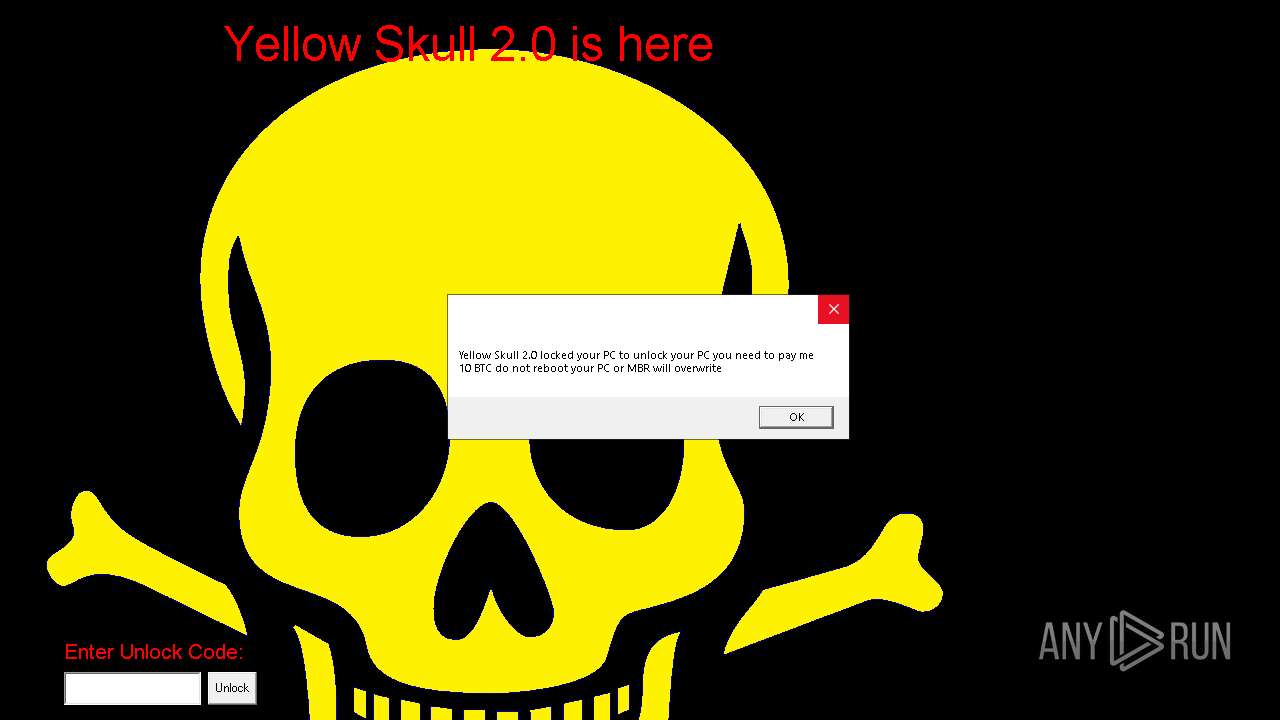
| File name: | YellowSkull 2.0.zip |
| Full analysis: | https://app.any.run/tasks/76df820f-44f1-49e7-9ffb-81dde495c8a2 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 23:30:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D700D6CCBBEA18C0FE32775A65F13280 |
| SHA1: | 7C159DD708EFD29B1404F1B7FB8D4E3D4C0D1CFD |
| SHA256: | 0FDCD8EF8BE7B2BC8B2AA44CA2DFE251E8850B0BE1E0EC563BD3736D2F05A09D |
| SSDEEP: | 98304:sX1++uBsOBDE0JPblL8CQhiXikAazRXOfZv4gXrQzy1SvaV1Vvc759u:81+5dDtJDlLVXztRG5Xro1Cn0e |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6360)
Disables the LogOff the Start menu
- reg.exe (PID: 7136)
UAC/LUA settings modification
- reg.exe (PID: 2792)
Changes the autorun value in the registry
- reg.exe (PID: 4624)
SUSPICIOUS
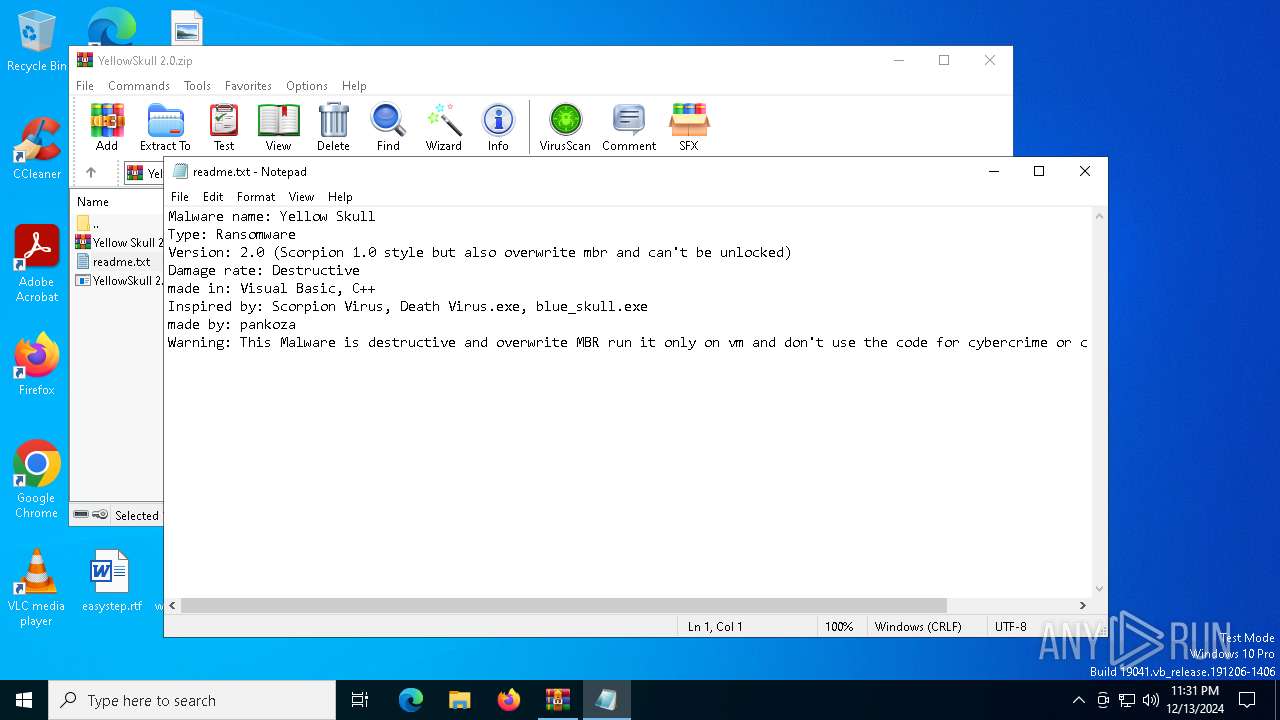
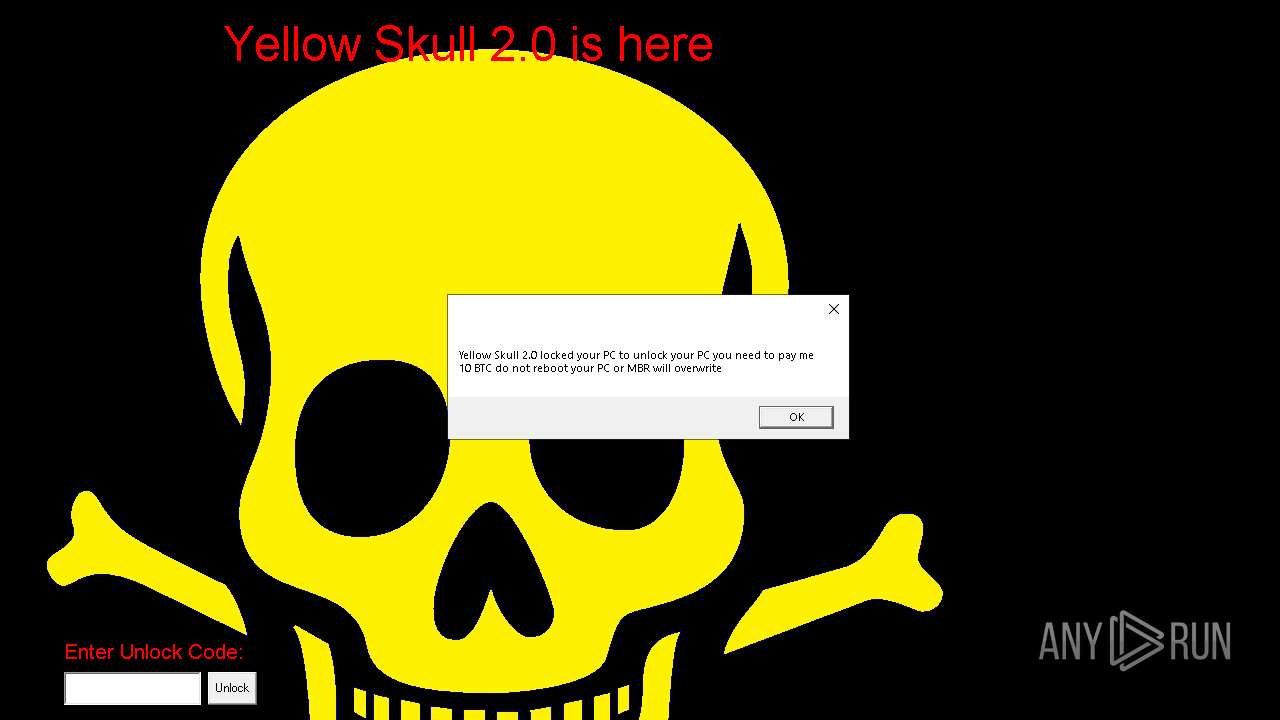
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 6360)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6360)
- YellowSkull 2.0.exe (PID: 1540)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6076)
Executable content was dropped or overwritten
- YellowSkull 2.0.exe (PID: 1540)
- cmd.exe (PID: 6076)
Executing commands from a ".bat" file
- YellowSkull 2.0.exe (PID: 1540)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6076)
Creates file in the systems drive root
- cmd.exe (PID: 6076)
The executable file from the user directory is run by the CMD process
- bg.exe (PID: 900)
- YSkullLock.exe (PID: 3296)
Starts CMD.EXE for commands execution
- YellowSkull 2.0.exe (PID: 1540)
Changes the desktop background image
- reg.exe (PID: 396)
The process executes VB scripts
- cmd.exe (PID: 6076)
INFO
The sample compiled with german language support
- WinRAR.exe (PID: 6360)
The sample compiled with english language support
- YellowSkull 2.0.exe (PID: 1540)
- WinRAR.exe (PID: 6360)
Reads the computer name
- YellowSkull 2.0.exe (PID: 1540)
- YSkullLock.exe (PID: 3296)
- bg.exe (PID: 900)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7044)
The process uses the downloaded file
- WinRAR.exe (PID: 6360)
- YellowSkull 2.0.exe (PID: 1540)
- cmd.exe (PID: 6076)
Checks supported languages
- YellowSkull 2.0.exe (PID: 1540)
- bg.exe (PID: 900)
- YSkullLock.exe (PID: 3296)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6360)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6360)
Process checks computer location settings
- YellowSkull 2.0.exe (PID: 1540)
Create files in a temporary directory
- YellowSkull 2.0.exe (PID: 1540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:03:21 14:40:32 |
| ZipCRC: | 0x8a0ce909 |
| ZipCompressedSize: | 2590019 |
| ZipUncompressedSize: | 2592768 |
| ZipFileName: | YellowSkull 2.0.exe |
Total processes
180
Monitored processes
54
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | reg add "HKEY_CURRENT_USER\Control Panel\Desktop" /v Wallpaper /t REG_SZ /d c:\yellowskull.bmp /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableChangePassword /t REG_DWORD /d 1 /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | reg add HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System /v HideFastUserSwitching /t REG_DWORD /d 1 /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | bg.exe | C:\Users\admin\AppData\Local\Temp\E245.tmp\bg.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1144 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1540 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.49636\YellowSkull 2.0.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.49636\YellowSkull 2.0.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1804 | reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v ConsentPromptBehaviorAdmin /t REG_DWORD /d 0 /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2212 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 898
Read events
6 879
Write events
19
Delete events
0
Modification events
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\YellowSkull 2.0.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
| (PID) Process: | (396) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: c:\yellowskull.bmp | |||
Executable files
5
Suspicious files
2
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1540 | YellowSkull 2.0.exe | C:\Users\admin\AppData\Local\Temp\E245.tmp\bg.exe | executable | |
MD5:12CF508E9058E3E67CF8A736557C2749 | SHA256:B3670EC42931E2DEA3E03053EDA32240D8B6DB15BF89D0C74E23E99ECB0AAF49 | |||
| 1540 | YellowSkull 2.0.exe | C:\Users\admin\AppData\Local\Temp\E245.tmp\YSkullLock.exe | executable | |
MD5:2191C3A14B53531E82726B17DD331CEF | SHA256:3B2ABD3773E4678100F197F53A886EC833FD2E26AA9A94D780A2D22BEFDF7D44 | |||
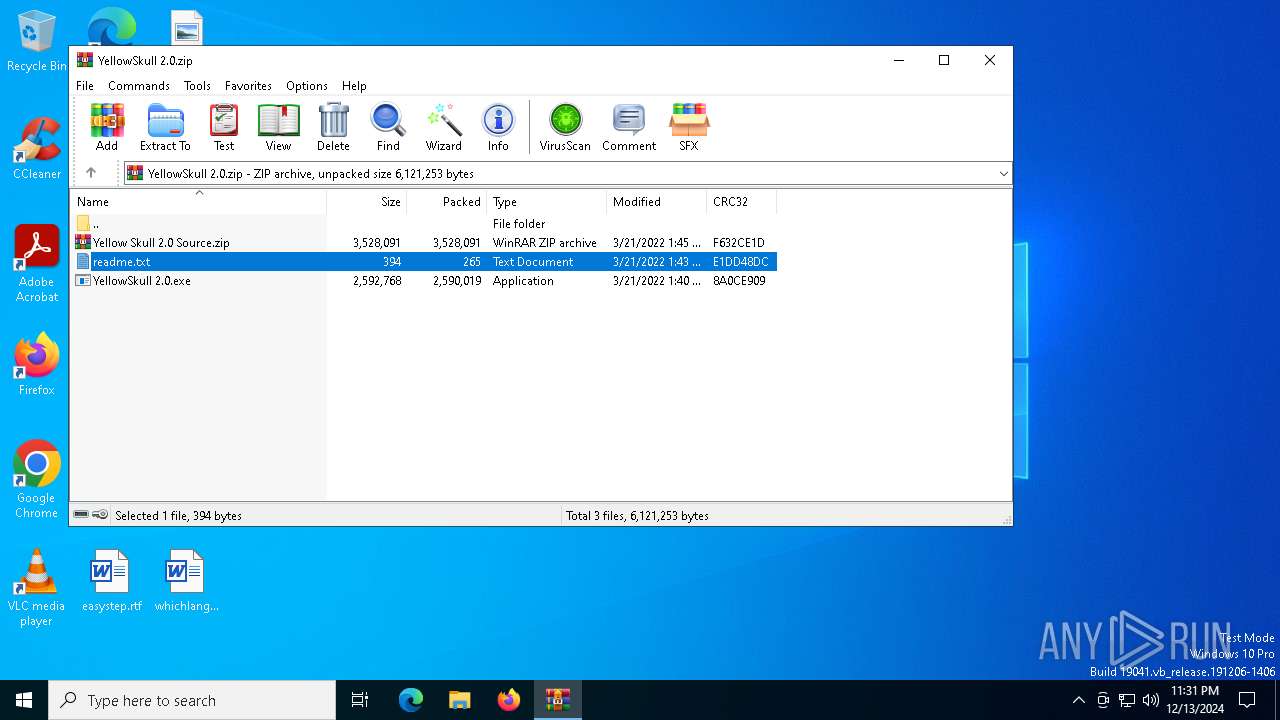
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.49636\readme.txt | text | |
MD5:A2A8F6716FE5889F704616038368DE82 | SHA256:3C26F7E09E30073AE5609073A7B711089F03A0731BC6616B8366496DA67FDF88 | |||
| 1540 | YellowSkull 2.0.exe | C:\Users\admin\AppData\Local\Temp\E245.tmp\YellowSkull2.bat | text | |
MD5:4671D5895D88BC19645CAB0FC7CA398A | SHA256:DD8AA9F7955674A7A1B5B222D7C1809C583C705DAE8BF476CDD42EFCC0AFABB5 | |||
| 1540 | YellowSkull 2.0.exe | C:\Users\admin\AppData\Local\Temp\E245.tmp\bg.cpp | text | |
MD5:A4F885352ED45CF37331BD01EC5B838A | SHA256:7032FD15B3B95CC3F0637BB8F8463E0848B5C2767C1CF4109EC34D7E2861322C | |||
| 1540 | YellowSkull 2.0.exe | C:\Users\admin\AppData\Local\Temp\E245.tmp\YellowSkull.bmp | image | |
MD5:11BCDA64D254AD8DC591B41F8FCEB04D | SHA256:84C5DAD2D4CEC5B636C1FAE6F1E1482ADA9F62363DCF269B4A86F6070D5B50FC | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6360.47402\readme.txt | text | |
MD5:A2A8F6716FE5889F704616038368DE82 | SHA256:3C26F7E09E30073AE5609073A7B711089F03A0731BC6616B8366496DA67FDF88 | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.49636\YellowSkull 2.0.exe | executable | |
MD5:660E26001A8891E78135A09D3EC2623F | SHA256:1811C7B5DDCC6637A782BF32DB70B60BD0BF3EC2B3498716591F718CDA25FD14 | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.49636\Yellow Skull 2.0 Source.zip | compressed | |
MD5:461366366B36A48ECCAF3CE181862CB7 | SHA256:7243123D7A3CE88D732AAB8CDEEE468D2ADC2700AC5BE304C91A984AA13611E1 | |||
| 1540 | YellowSkull 2.0.exe | C:\Users\admin\AppData\Local\Temp\E245.tmp\bg.wav | wav | |
MD5:832B350B50A07906C630A2B8819FD209 | SHA256:94E1CECF8ED740EA45C87927DE31005C3B2F9DB261AAE04FE56A81E337D1E8DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
32
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6312 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6312 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7128 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7128 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 23.212.110.178:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 184.30.17.189:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |