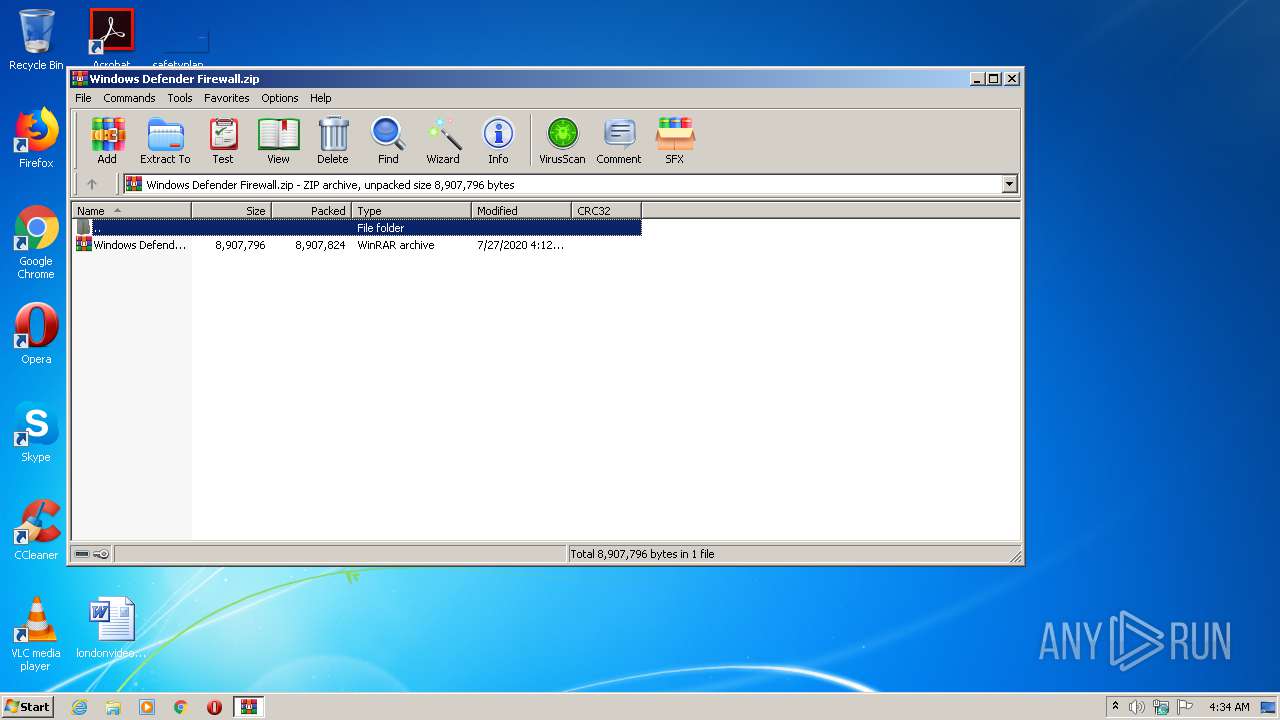
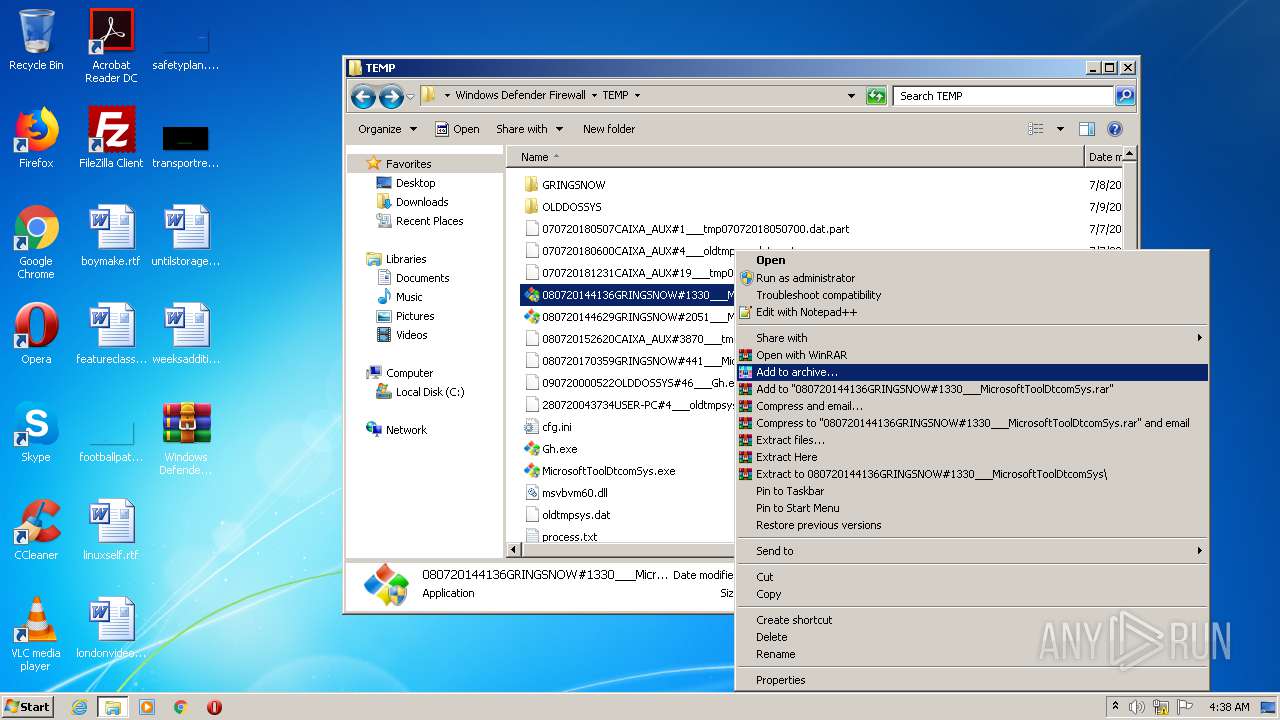
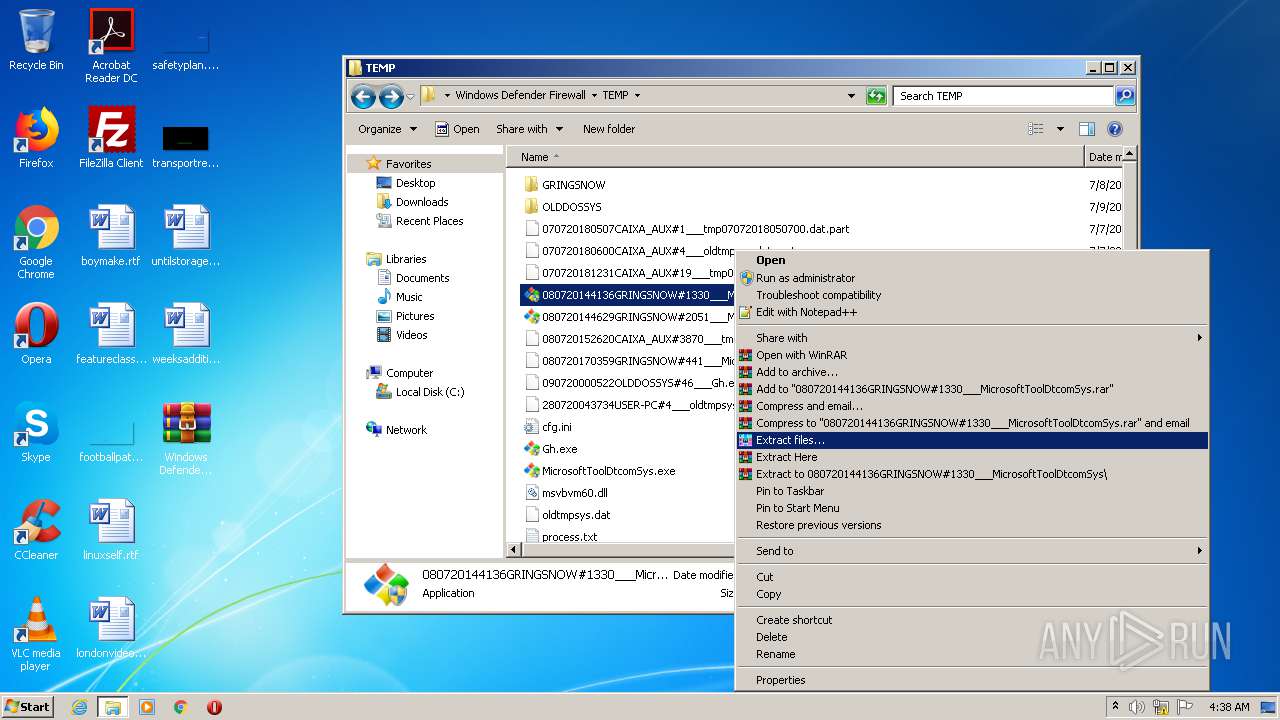
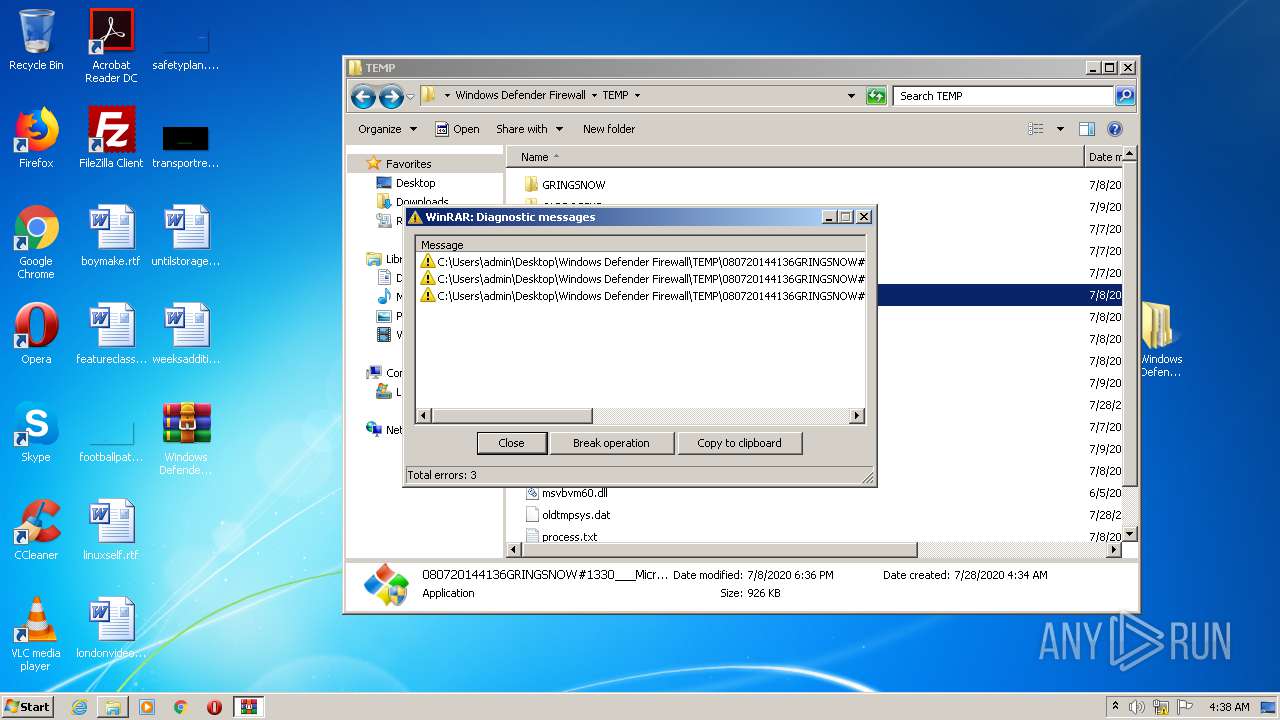
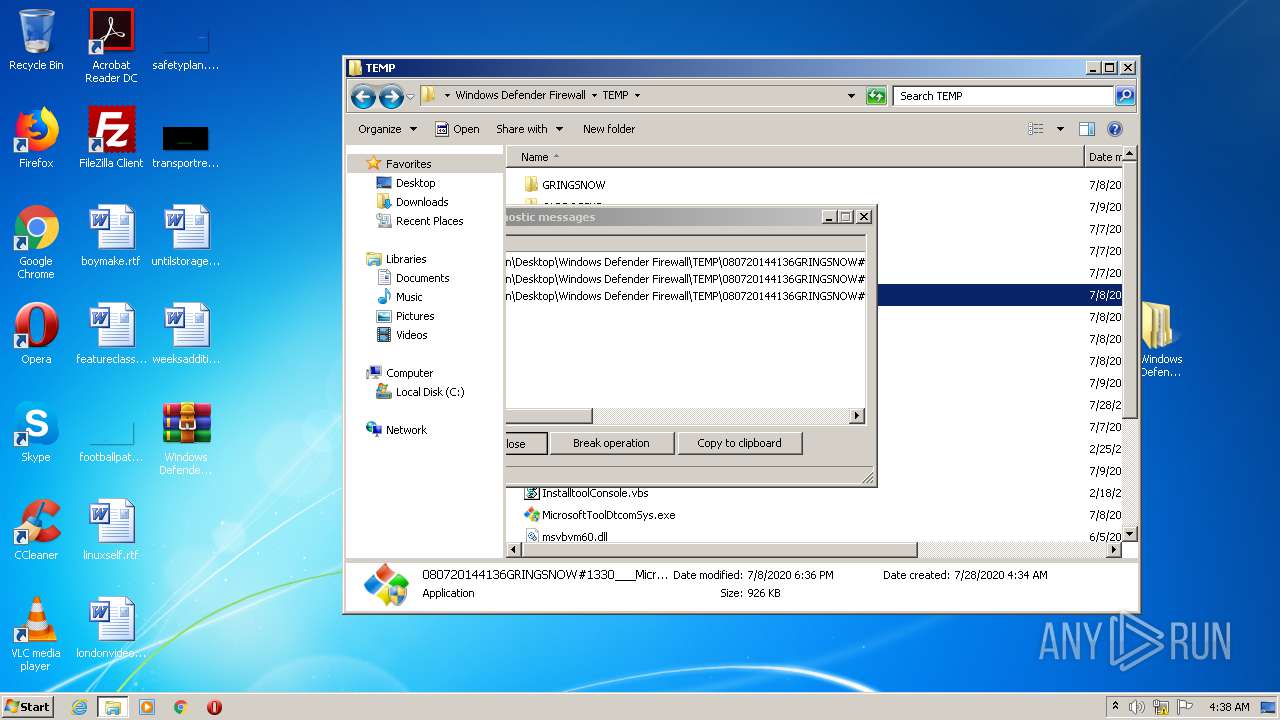
| File name: | Windows Defender Firewall.zip |
| Full analysis: | https://app.any.run/tasks/eeeee913-7127-4034-ba67-dd282290b61e |
| Verdict: | Malicious activity |
| Analysis date: | July 28, 2020, 03:33:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | D9B7216F78AF077F444DF24E4DEE9201 |
| SHA1: | FF433707EB12260271A38C15178FC214C1E70421 |
| SHA256: | 0FBDC48E3F5204F1C4A767416C2C0153F428AC0EDDF8685DC511D7103345038A |
| SSDEEP: | 196608:j0ZPZvKviZ+EyNCgEAyRFLIUHP2n7e1LCr+nmoAJAdGa:j0ZPZCvtrgLIMOnqgr+yK |
MALICIOUS
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2836)
- schtasks.exe (PID: 2136)
- schtasks.exe (PID: 3440)
- schtasks.exe (PID: 4092)
- schtasks.exe (PID: 1572)
- Microsoft0leSystemmcas.exe (PID: 272)
- schtasks.exe (PID: 2376)
- schtasks.exe (PID: 1084)
- schtasks.exe (PID: 1760)
- schtasks.exe (PID: 1668)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3172)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 956)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 3172)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 956)
Application was dropped or rewritten from another process
- Gh.exe (PID: 1080)
- Gh.exe (PID: 1680)
- Rar.exe (PID: 332)
- Winlog0nUser.exe (PID: 2512)
- Microsoft0leSystemmcas.exe (PID: 2716)
- SNDCAB.exe (PID: 3176)
- MicrosoftToolDtcomSys.exe (PID: 2824)
- MicrosoftToolDtcomSys.exe (PID: 3884)
- Rar.exe (PID: 656)
- Microsoft0leSystemmcas.exe (PID: 272)
- dtcomsys.exe (PID: 2864)
- Winlog0nUser.exe (PID: 564)
- 080720144629GRINGSNOW#2051___MicrosoftToolDtcomSys.exe (PID: 2592)
- Winlog0nUserKD.exe (PID: 1132)
- MicrosoftToolDtcomSys.exe (PID: 1728)
- MicrosoftToolDtcomSys.exe (PID: 1680)
- 080720144629GRINGSNOW#2051___MicrosoftToolDtcomSys.exe (PID: 3396)
- 080720144136GRINGSNOW#1330___MicrosoftToolDtcomSys.exe (PID: 1896)
- Rar.exe (PID: 2280)
- Winlog0nUser.exe (PID: 3380)
- Microsoft0leSystemmcas.exe (PID: 1688)
- dtcomsys.exe (PID: 2488)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2560)
- SearchProtocolHost.exe (PID: 3524)
- Microsoft0leSystemmcas.exe (PID: 2716)
- Winlog0nUser.exe (PID: 2512)
- SNDCAB.exe (PID: 3176)
- regsvr32.exe (PID: 3384)
- Winlog0nUser.exe (PID: 564)
- Microsoft0leSystemmcas.exe (PID: 272)
- dtcomsys.exe (PID: 2864)
- Winlog0nUser.exe (PID: 3708)
- Winlog0nUserKD.exe (PID: 1132)
- regsvr32.exe (PID: 964)
- Microsoft0leSystemmcas.exe (PID: 1688)
- dtcomsys.exe (PID: 2488)
- Winlog0nUser.exe (PID: 3380)
Changes the autorun value in the registry
- reg.exe (PID: 1756)
- reg.exe (PID: 2384)
- reg.exe (PID: 312)
- reg.exe (PID: 3884)
- reg.exe (PID: 3004)
- reg.exe (PID: 3572)
- reg.exe (PID: 3840)
- reg.exe (PID: 2272)
- reg.exe (PID: 900)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2516)
- Gh.exe (PID: 1680)
- MicrosoftToolDtcomSys.exe (PID: 3884)
- xcopy.exe (PID: 2600)
- Rar.exe (PID: 656)
- MicrosoftToolDtcomSys.exe (PID: 1680)
- Rar.exe (PID: 332)
- xcopy.exe (PID: 2924)
- cmd.exe (PID: 3172)
- 080720144629GRINGSNOW#2051___MicrosoftToolDtcomSys.exe (PID: 3396)
- 080720144136GRINGSNOW#1330___MicrosoftToolDtcomSys.exe (PID: 1896)
- WinRAR.exe (PID: 4028)
- Rar.exe (PID: 2280)
Application launched itself
- WinRAR.exe (PID: 2812)
Executes scripts
- Gh.exe (PID: 1680)
- MicrosoftToolDtcomSys.exe (PID: 3884)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 2396)
- MicrosoftToolDtcomSys.exe (PID: 1680)
- cmd.exe (PID: 956)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3172)
- cmd.exe (PID: 2916)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 2044)
- cmd.exe (PID: 956)
- cmd.exe (PID: 3844)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3172)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 956)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3172)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 956)
Starts CMD.EXE for commands execution
- Winlog0nUser.exe (PID: 2512)
- WScript.exe (PID: 2776)
- WScript.exe (PID: 1488)
- Winlog0nUser.exe (PID: 564)
- WScript.exe (PID: 852)
- Winlog0nUser.exe (PID: 3708)
- Winlog0nUserKD.exe (PID: 1132)
- WScript.exe (PID: 2320)
- WScript.exe (PID: 624)
- Winlog0nUser.exe (PID: 3380)
- WScript.exe (PID: 3320)
Creates files in the Windows directory
- cmd.exe (PID: 3172)
INFO
Manual execution by user
- Gh.exe (PID: 1680)
- Gh.exe (PID: 1080)
- MicrosoftToolDtcomSys.exe (PID: 2824)
- MicrosoftToolDtcomSys.exe (PID: 3884)
- Winlog0nUser.exe (PID: 3708)
- 080720144629GRINGSNOW#2051___MicrosoftToolDtcomSys.exe (PID: 2592)
- 080720144629GRINGSNOW#2051___MicrosoftToolDtcomSys.exe (PID: 3396)
- Winlog0nUserKD.exe (PID: 1132)
- MicrosoftToolDtcomSys.exe (PID: 1728)
- MicrosoftToolDtcomSys.exe (PID: 1680)
- 080720144136GRINGSNOW#1330___MicrosoftToolDtcomSys.exe (PID: 1896)
- WinRAR.exe (PID: 4028)
- WinRAR.exe (PID: 2424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
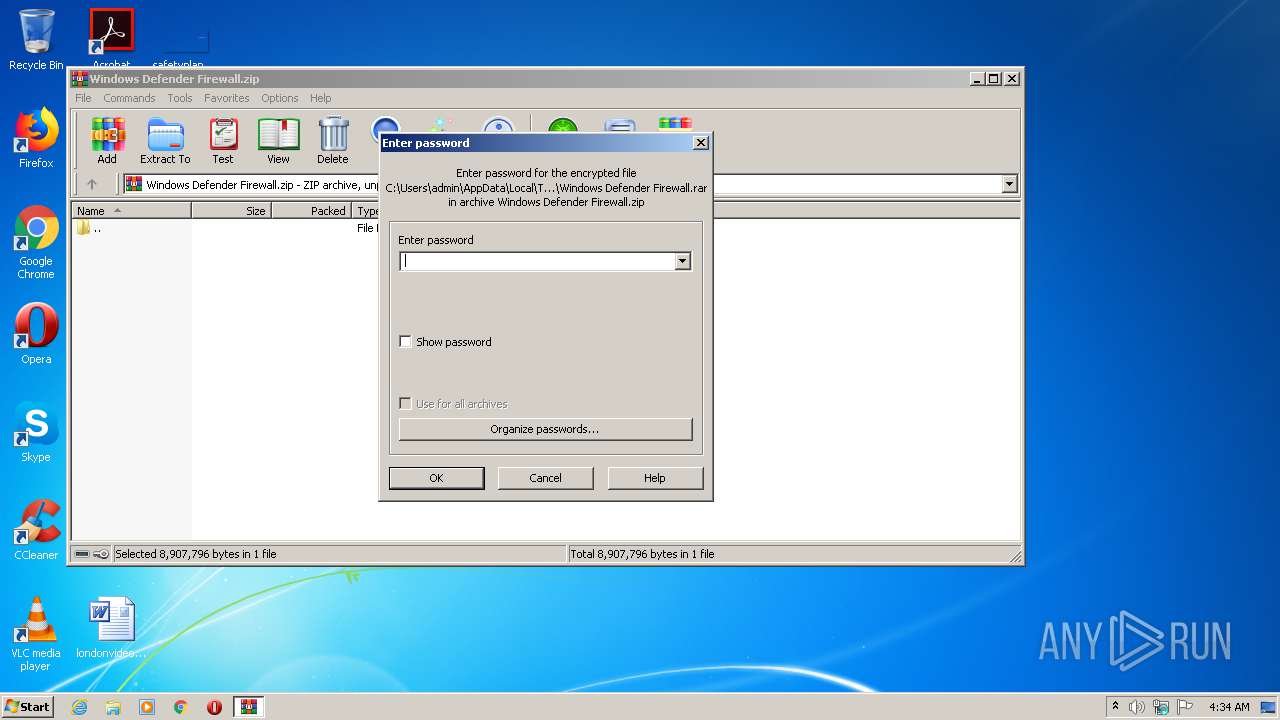
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2020:07:27 12:12:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 8907824 |
| ZipUncompressedSize: | 8907796 |
| ZipFileName: | Windows Defender Firewall.rar |
Total processes
237
Monitored processes
132
Malicious processes
18
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | cmd /c del tmp*.dat | C:\Windows\system32\cmd.exe | — | Winlog0nUser.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 180 | taskkill /im Microsoft0leSystemmcas.exe /f | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | Microsoft0leSystemmcas.exe | C:\Intel\Drv\Microsoft0leSystemmcas.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windoows System Exit code: 1 Version: 6.03.7799 Modules
| |||||||||||||||
| 312 | reg add HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /f /v MicrosoftUptadeTool /d "C:\Intel\Drv\Microsoft0leSystemmcas.exe" | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 320 | cmd /c del tmp*.dat | C:\Windows\system32\cmd.exe | — | Winlog0nUser.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
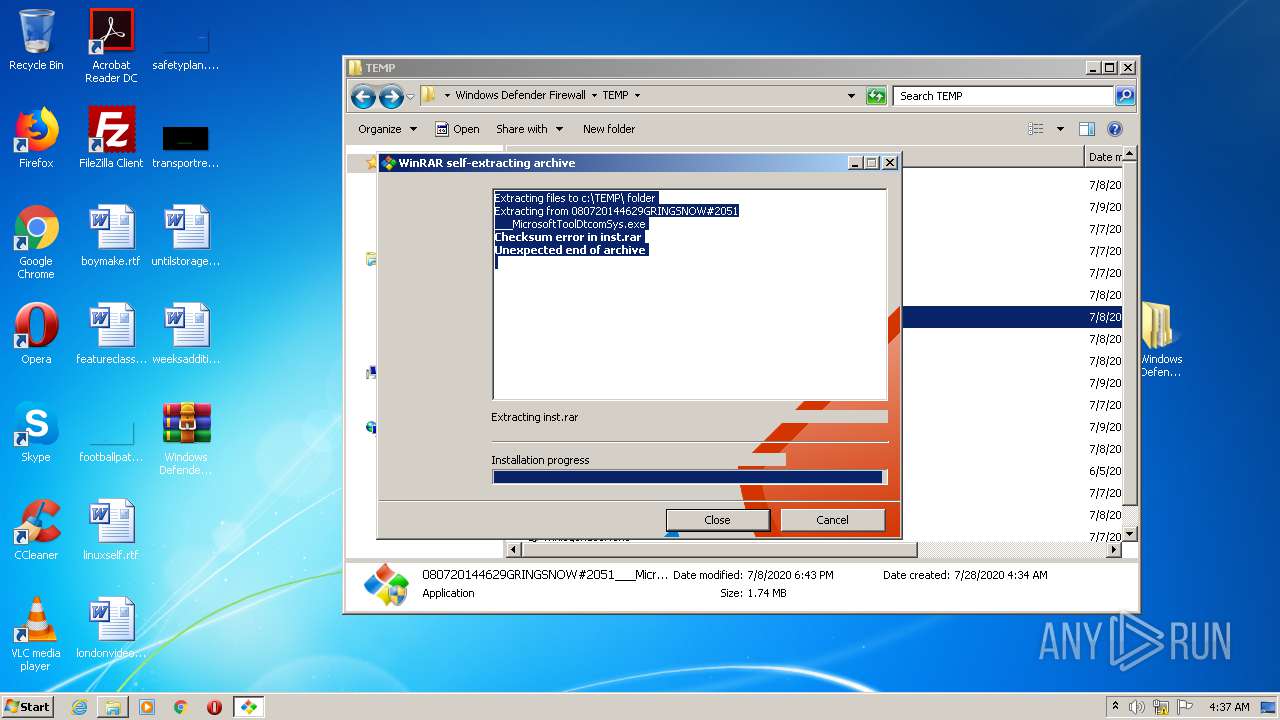
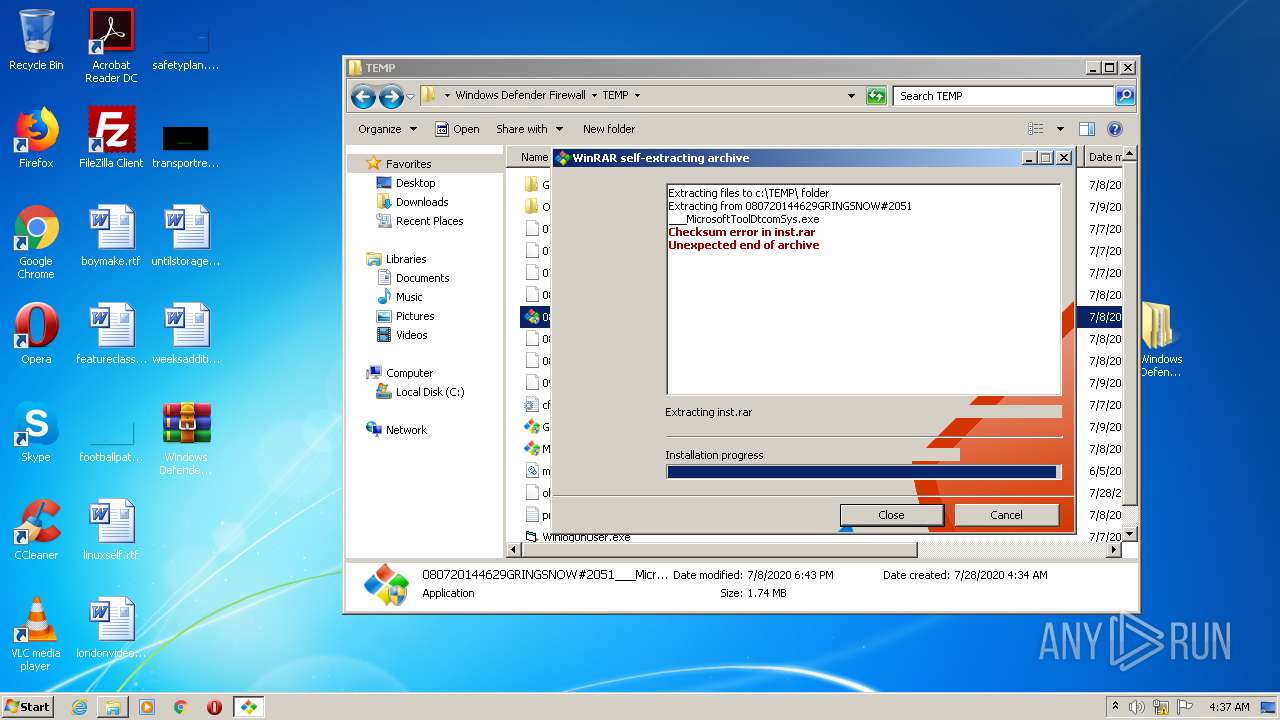
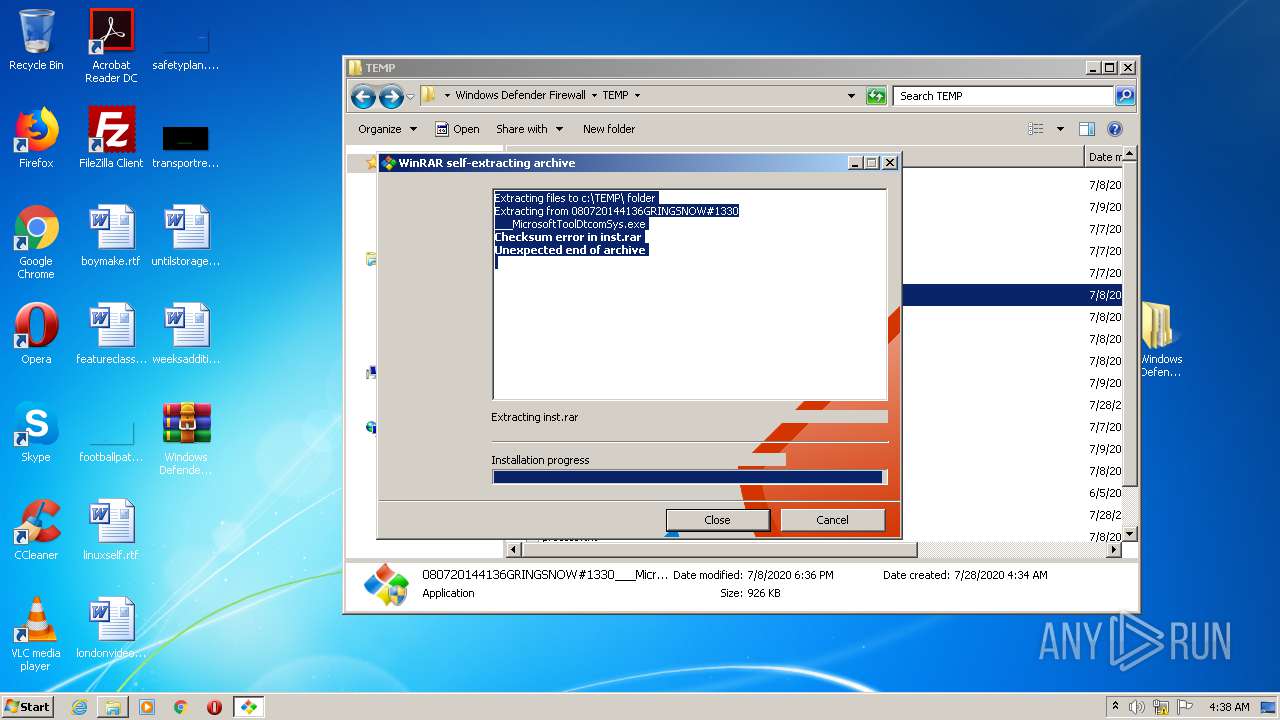
| 332 | rar x -y inst.rar C:\Intel\Drv\ | c:\TEMP\Rar.exe | cmd.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: Command line RAR Exit code: 0 Version: 5.60.1 Modules
| |||||||||||||||
| 544 | cmd /c del tmp*.dat | C:\Windows\system32\cmd.exe | — | Winlog0nUser.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 564 | winlog0nUser.exe | C:\Intel\Drv\Winlog0nUser.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Company Integrity Level: HIGH Exit code: 1 Version: 1.00.0064 Modules
| |||||||||||||||
| 624 | "C:\Windows\System32\WScript.exe" "C:\temp\InstalltoolConsole.vbs" | C:\Windows\System32\WScript.exe | — | Gh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 656 | rar x -y inst.rar C:\Intel\Drv\ | c:\TEMP\Rar.exe | cmd.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: Command line RAR Exit code: 0 Version: 5.60.1 Modules
| |||||||||||||||
Total events
2 672
Read events
2 475
Write events
191
Delete events
6
Modification events
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Windows Defender Firewall.zip | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2516) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
28
Suspicious files
3
Text files
95
Unknown types
0
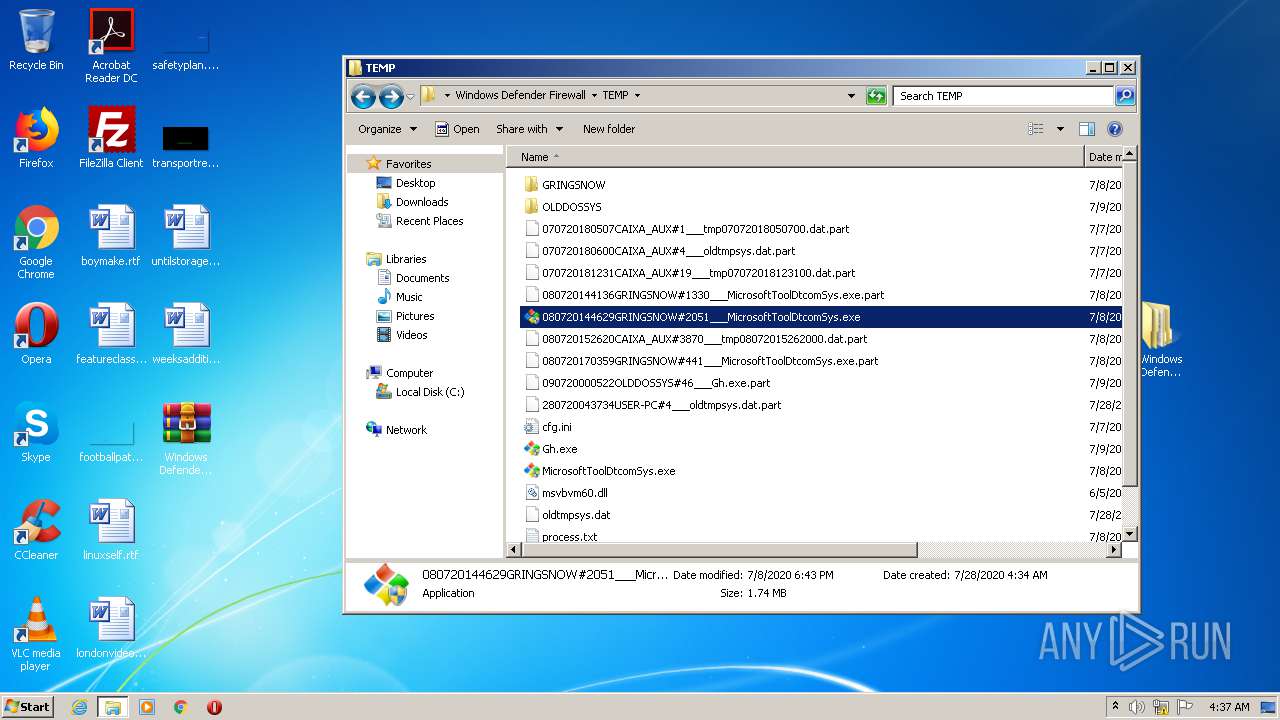
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2812.8926\Windows Defender Firewall.rar | — | |
MD5:— | SHA256:— | |||
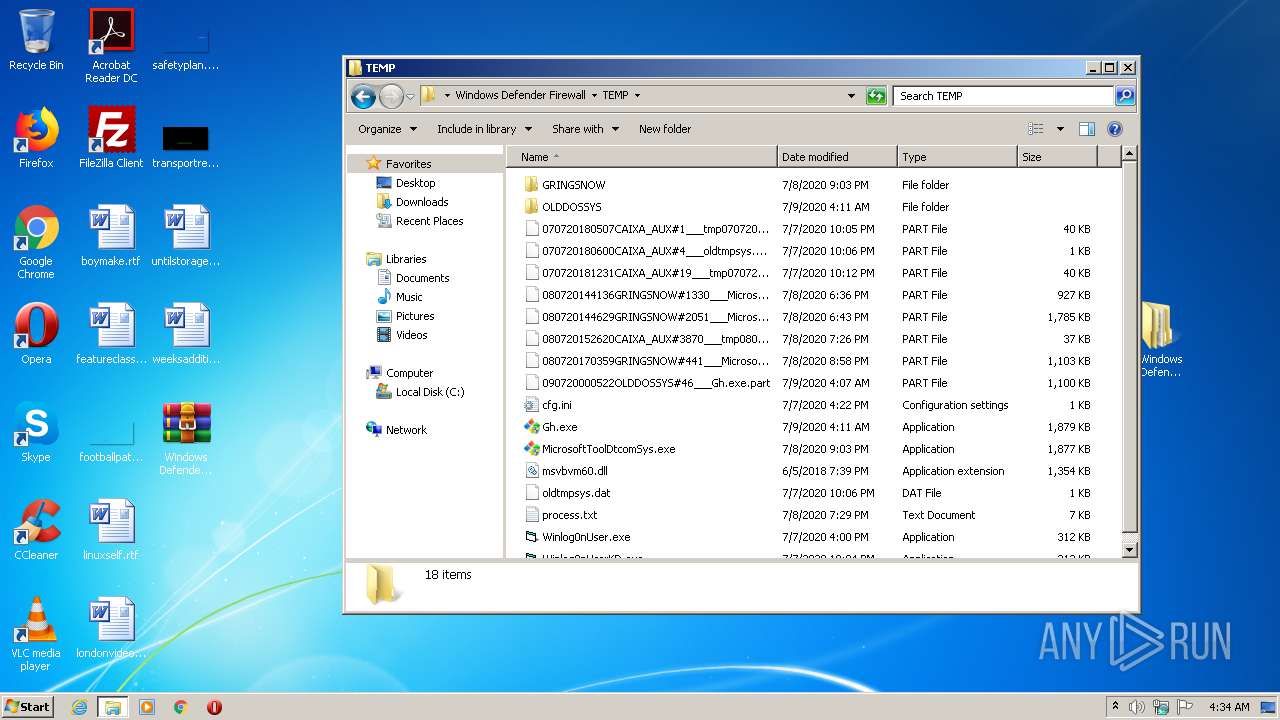
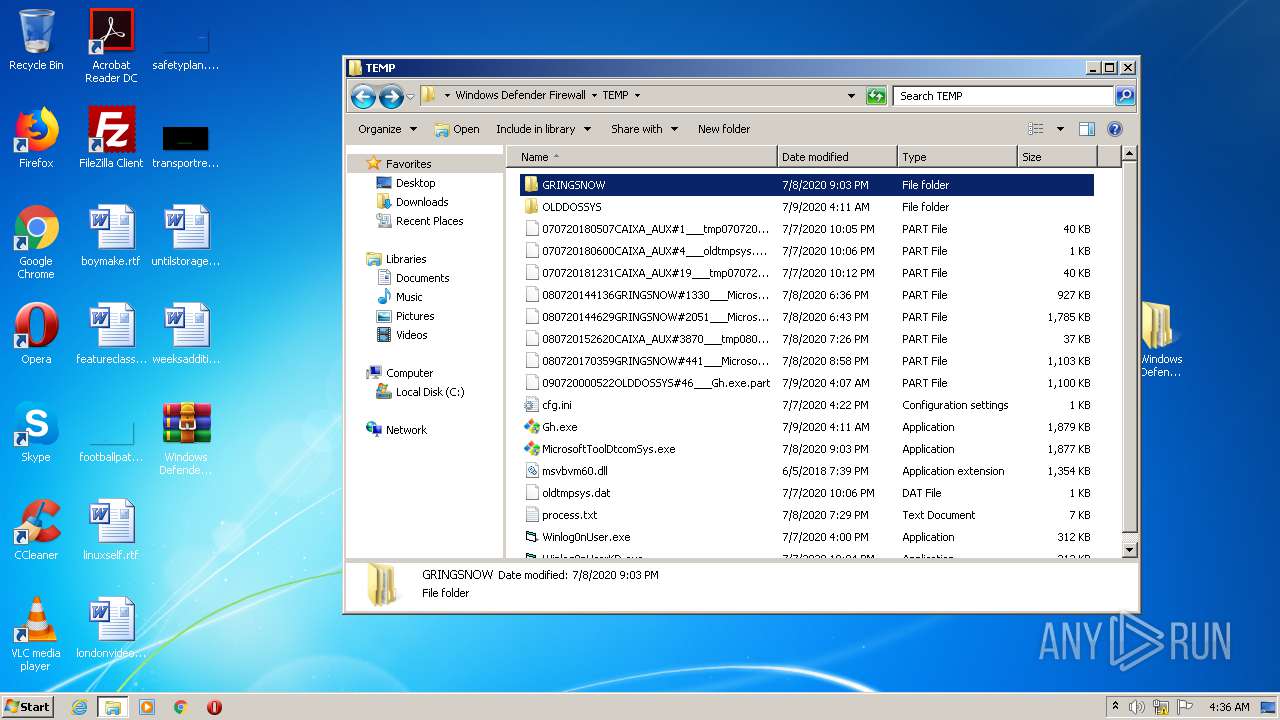
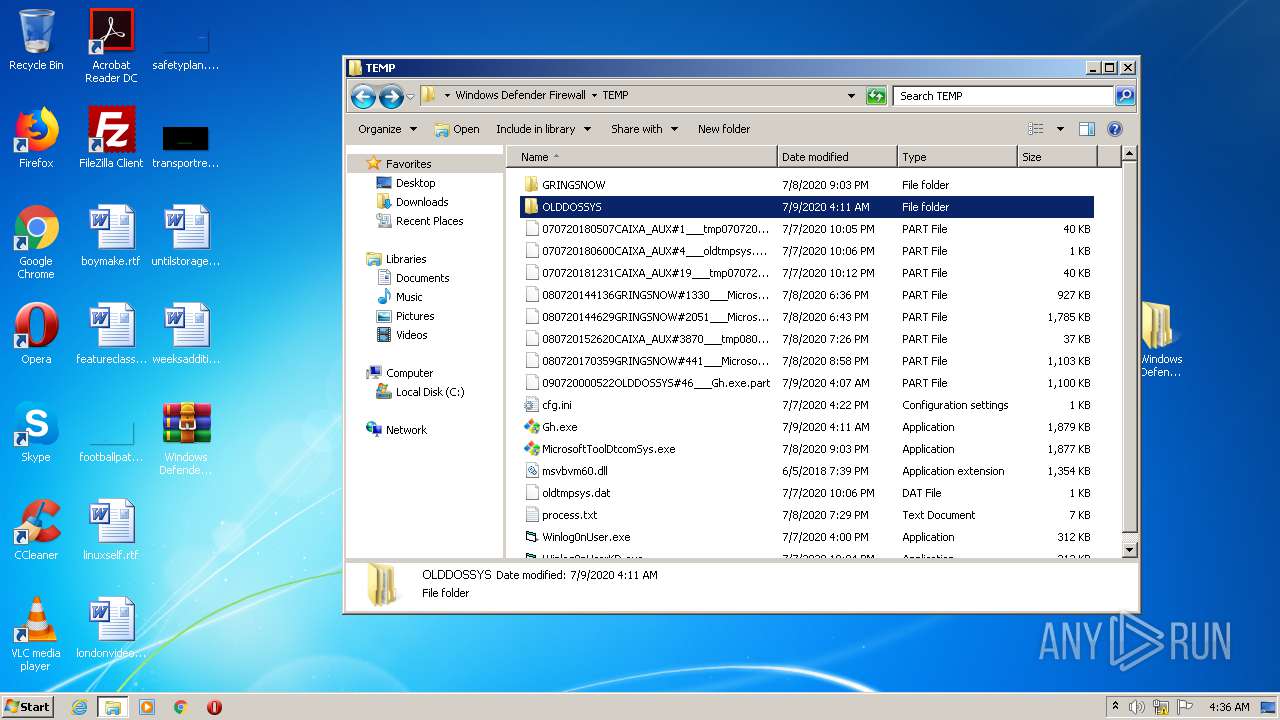
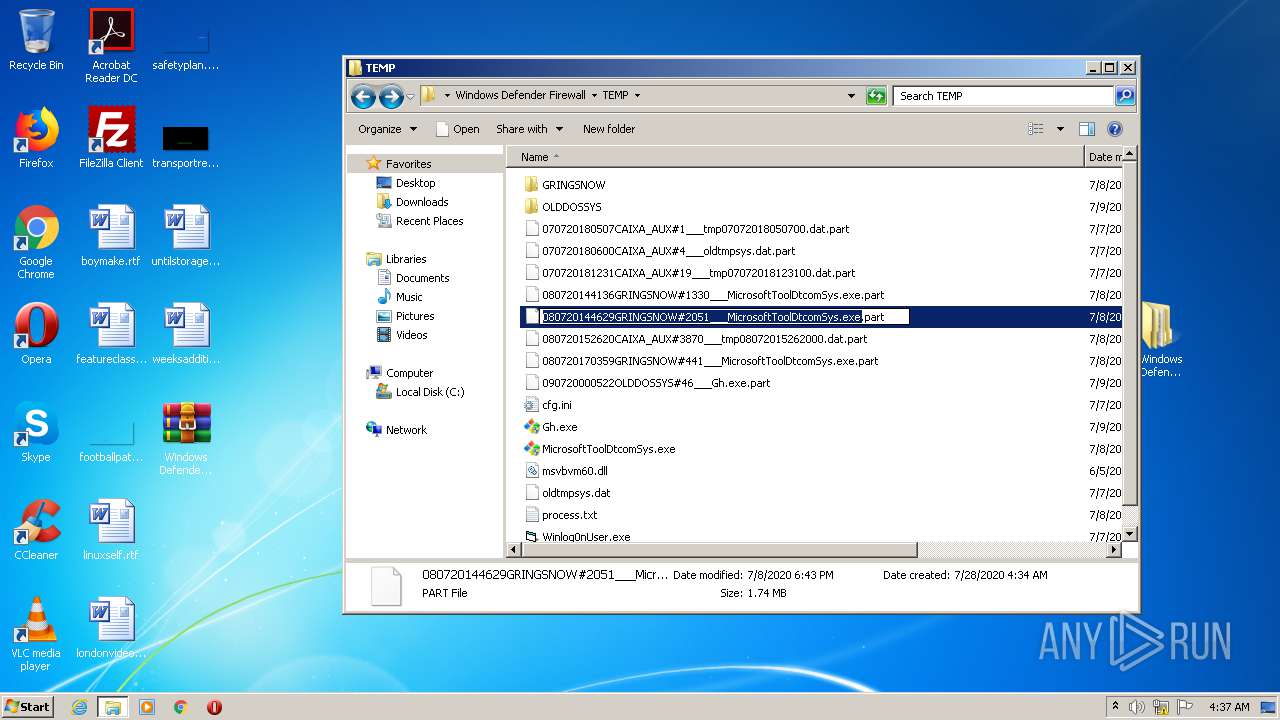
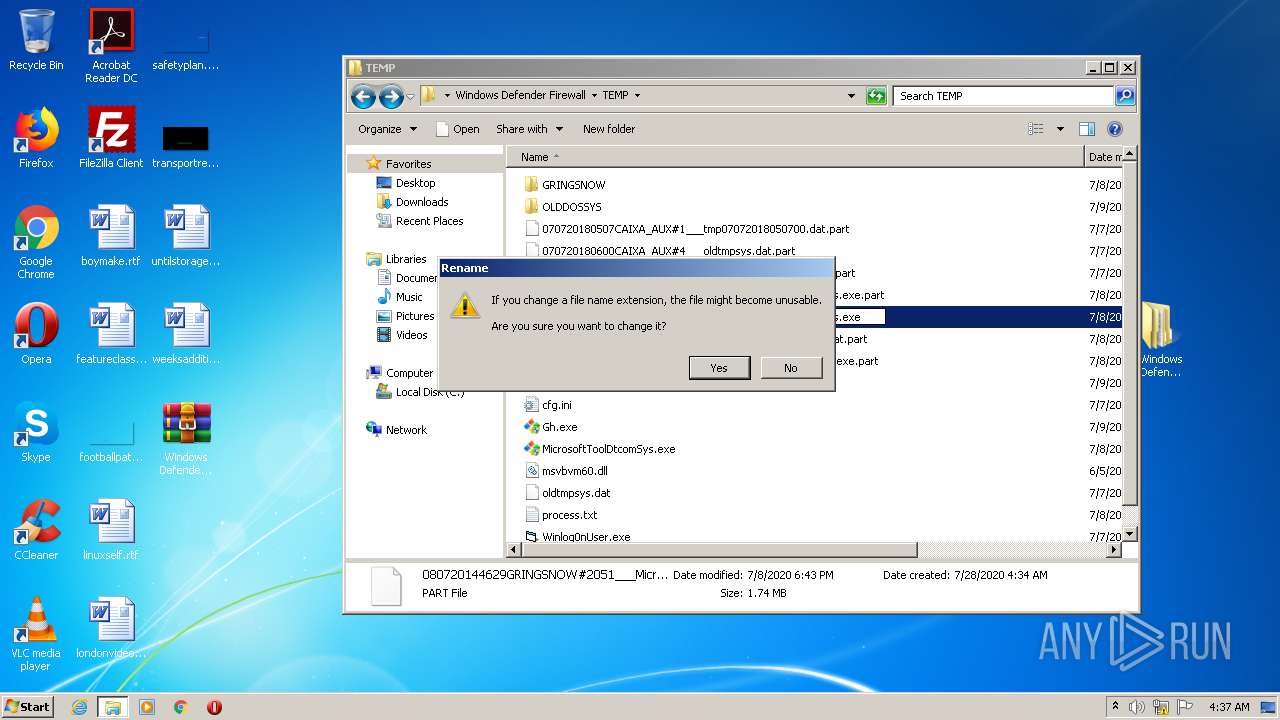
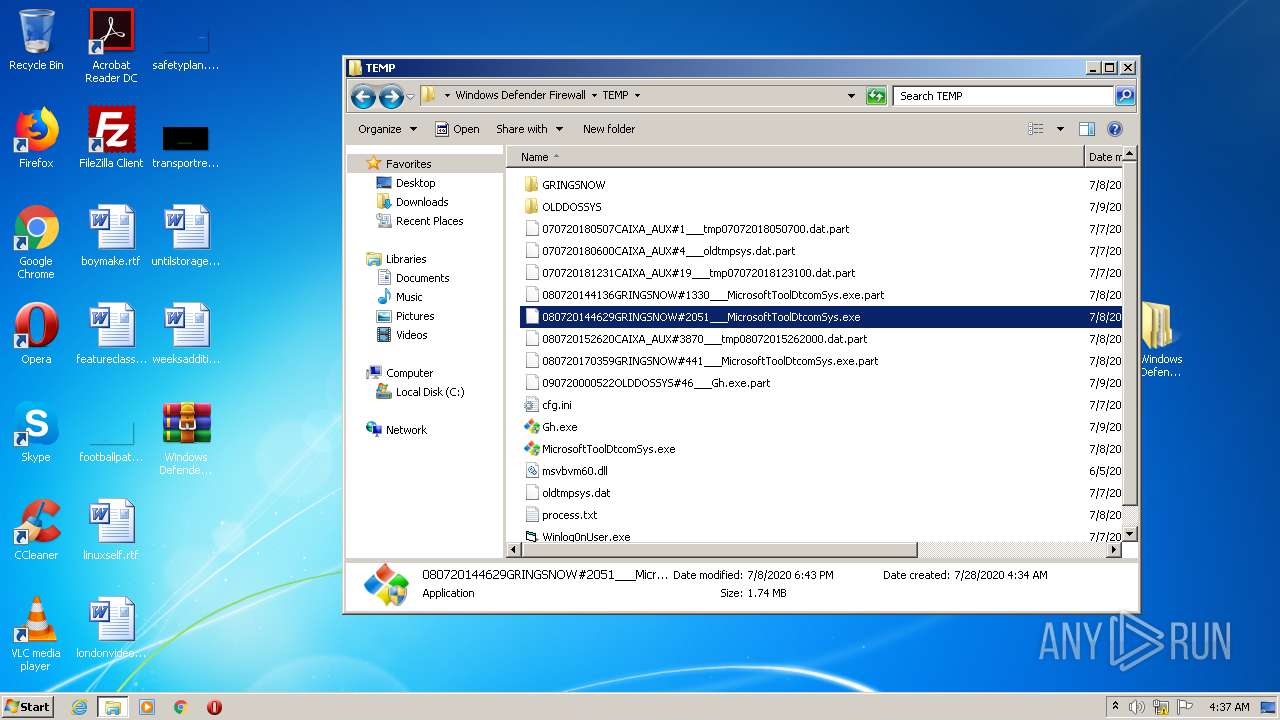
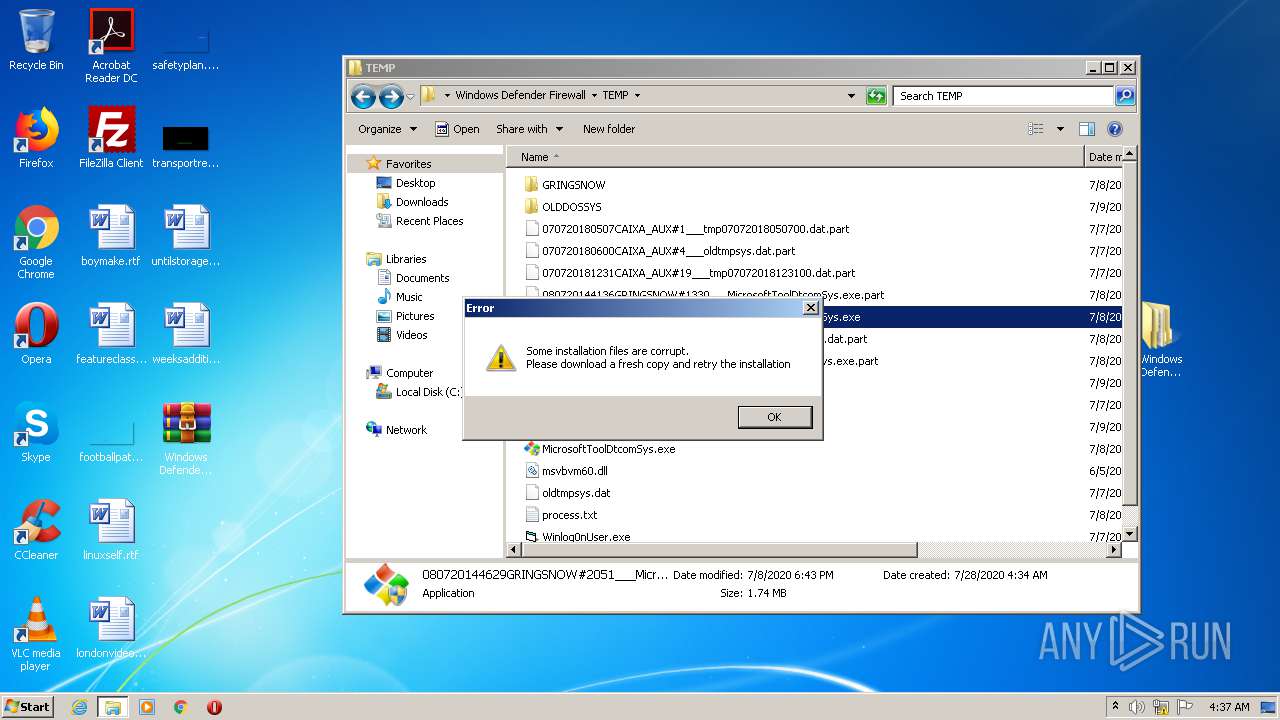
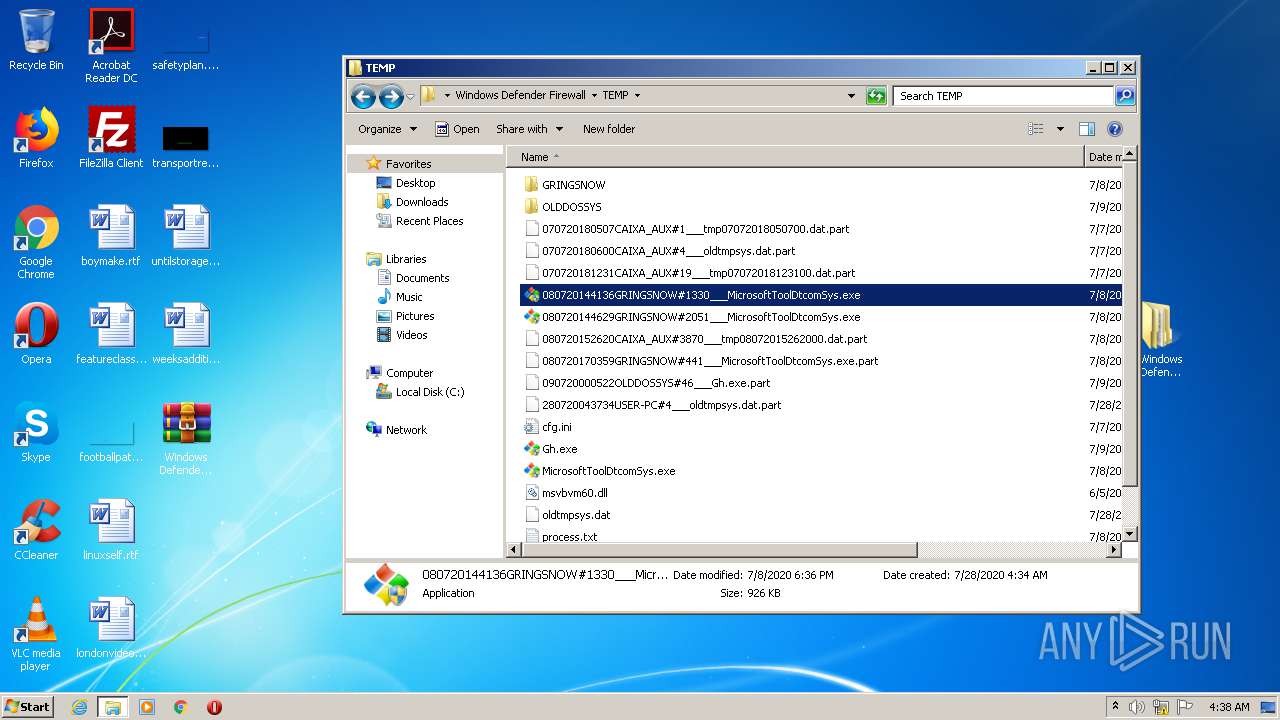
| 2516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2516.10233\Windows Defender Firewall\TEMP\080720144629GRINGSNOW#2051___MicrosoftToolDtcomSys.exe.part | — | |
MD5:— | SHA256:— | |||
| 2516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2516.10233\Windows Defender Firewall\TEMP\080720152620CAIXA_AUX#3870___tmp08072015262000.dat.part | — | |
MD5:— | SHA256:— | |||
| 2516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2516.10233\Windows Defender Firewall\TEMP\080720170359GRINGSNOW#441___MicrosoftToolDtcomSys.exe.part | — | |
MD5:— | SHA256:— | |||
| 2516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2516.10233\Windows Defender Firewall\TEMP\090720000522OLDDOSSYS#46___Gh.exe.part | — | |
MD5:— | SHA256:— | |||
| 2516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2516.10233\Windows Defender Firewall\TEMP\cfg.ini | — | |
MD5:— | SHA256:— | |||
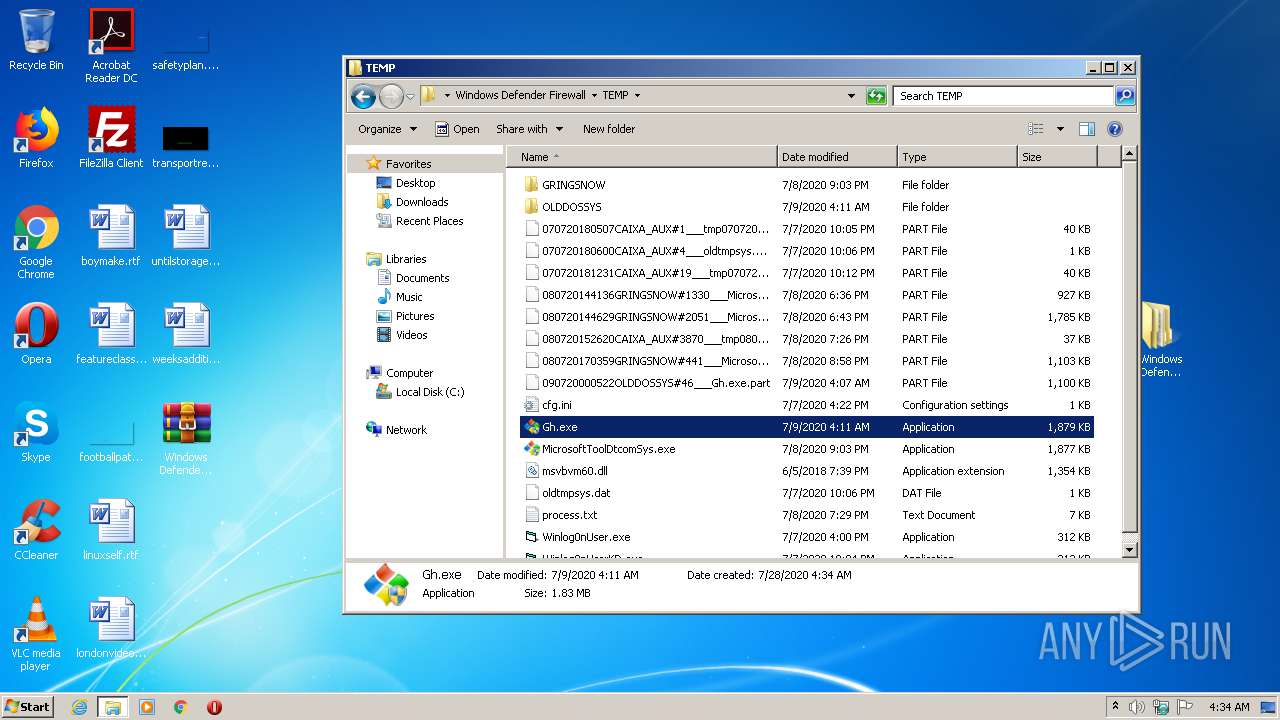
| 2516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2516.10233\Windows Defender Firewall\TEMP\Gh.exe | — | |
MD5:— | SHA256:— | |||
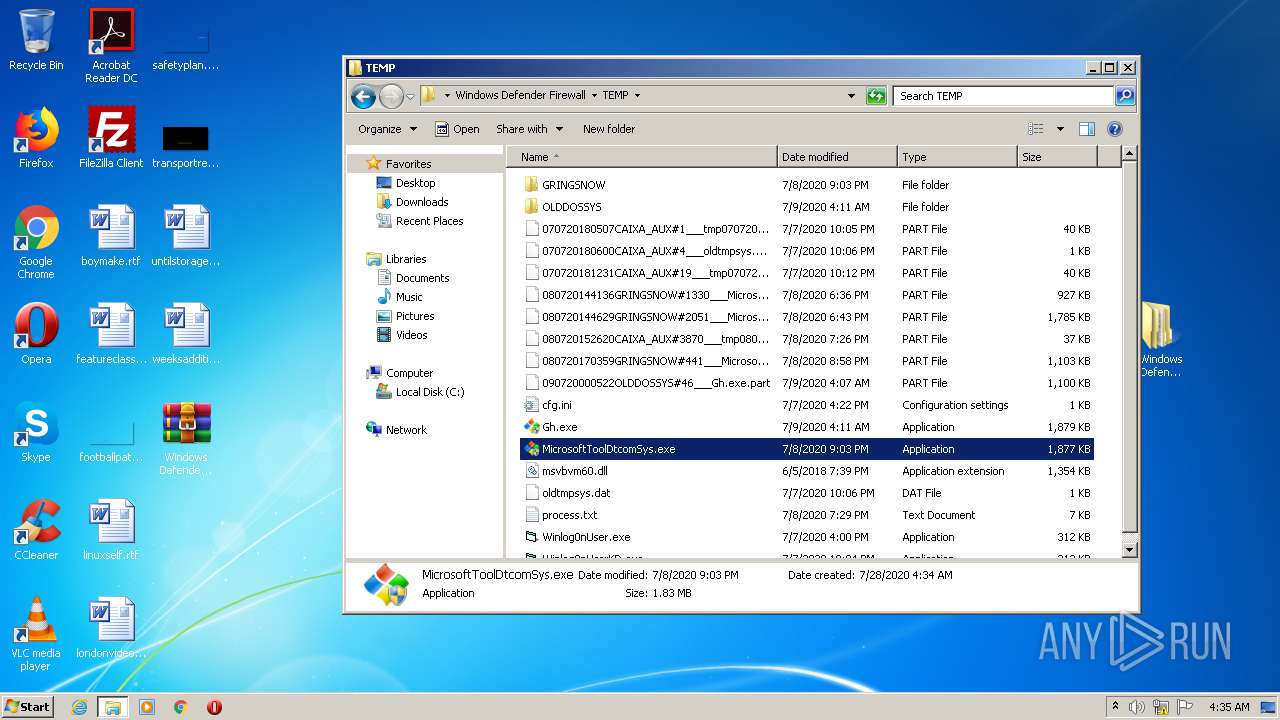
| 2516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2516.10233\Windows Defender Firewall\TEMP\MicrosoftToolDtcomSys.exe | — | |
MD5:— | SHA256:— | |||
| 2516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2516.10233\Windows Defender Firewall\TEMP\msvbvm60.dll | — | |
MD5:— | SHA256:— | |||
| 2516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2516.10233\Windows Defender Firewall\TEMP\oldtmpsys.dat | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
35
DNS requests
5
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2512 | Winlog0nUser.exe | 193.29.57.84:10003 | prdxboss1.chickenkiller.com | — | — | malicious |
2512 | Winlog0nUser.exe | 177.12.49.235:10003 | box.h4ck.me | Predlink Rede de Telecomunicções Ltda | BR | unknown |
564 | Winlog0nUser.exe | 177.12.49.235:20003 | box.h4ck.me | Predlink Rede de Telecomunicções Ltda | BR | unknown |
3708 | Winlog0nUser.exe | 177.12.49.235:20003 | box.h4ck.me | Predlink Rede de Telecomunicções Ltda | BR | unknown |
1132 | Winlog0nUserKD.exe | 193.29.57.84:10003 | prdxboss1.chickenkiller.com | — | — | malicious |
1132 | Winlog0nUserKD.exe | 177.12.49.235:10003 | box.h4ck.me | Predlink Rede de Telecomunicções Ltda | BR | unknown |
3380 | Winlog0nUser.exe | 177.12.49.235:20003 | box.h4ck.me | Predlink Rede de Telecomunicções Ltda | BR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
prdxboss1.chickenkiller.com |
| malicious |
box.h4ck.me |
| unknown |
enois.mooo.com |
| unknown |
sysmaster.mooo.com |
| suspicious |
olddossys.mooo.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |