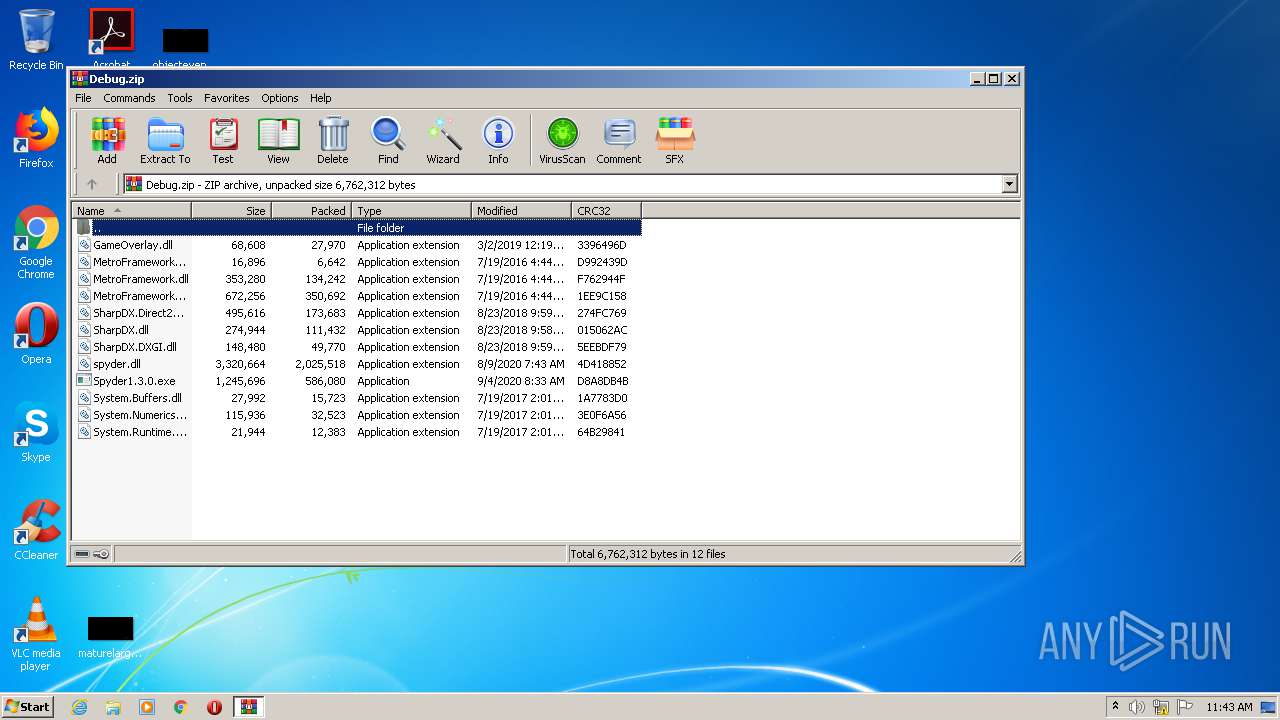
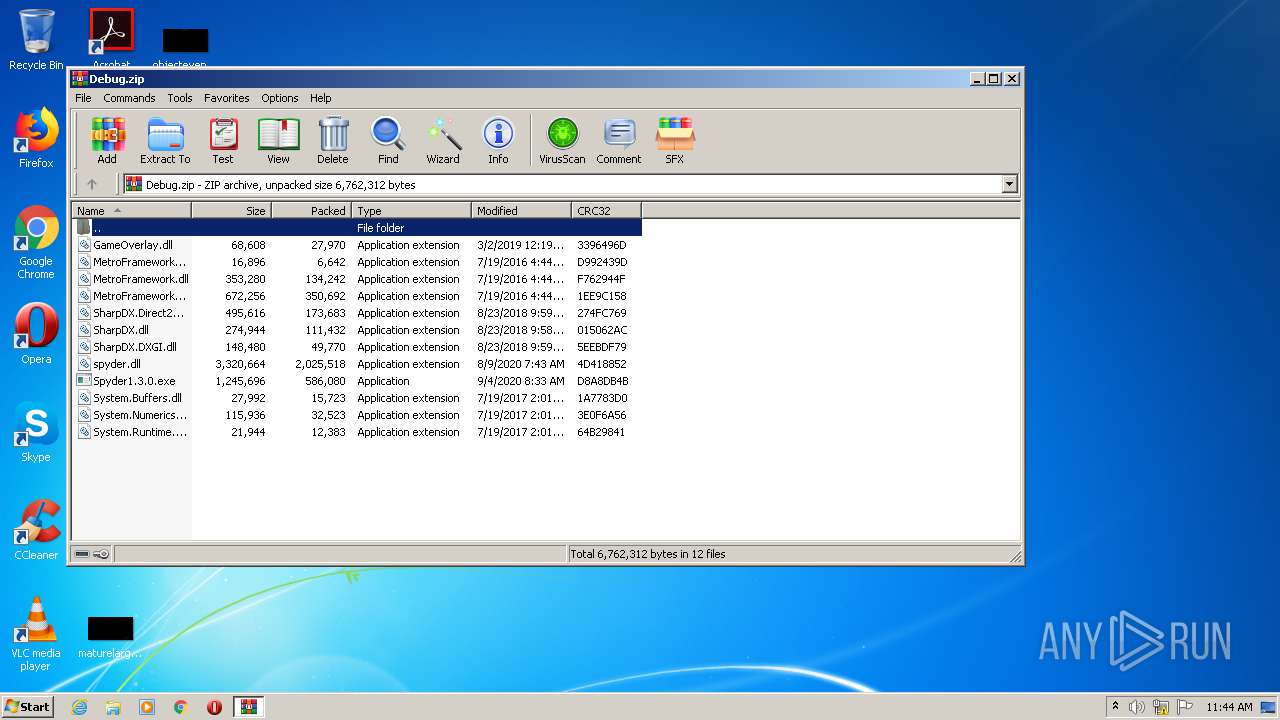
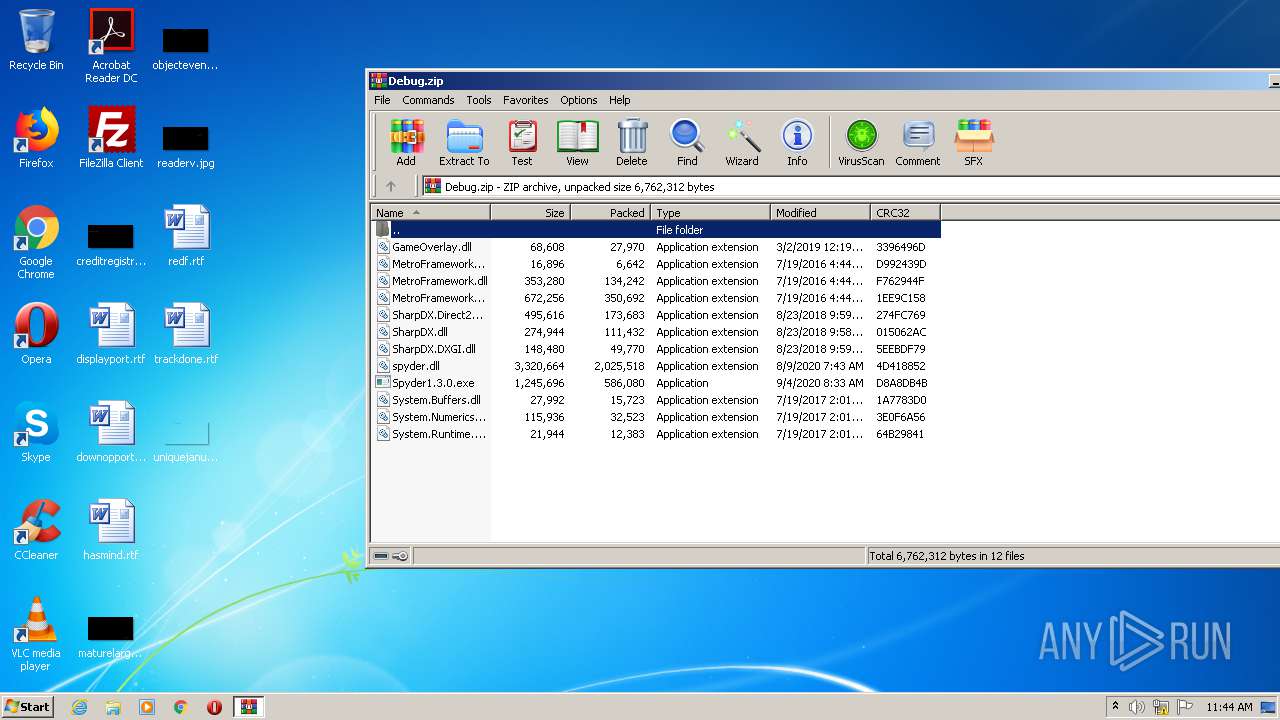
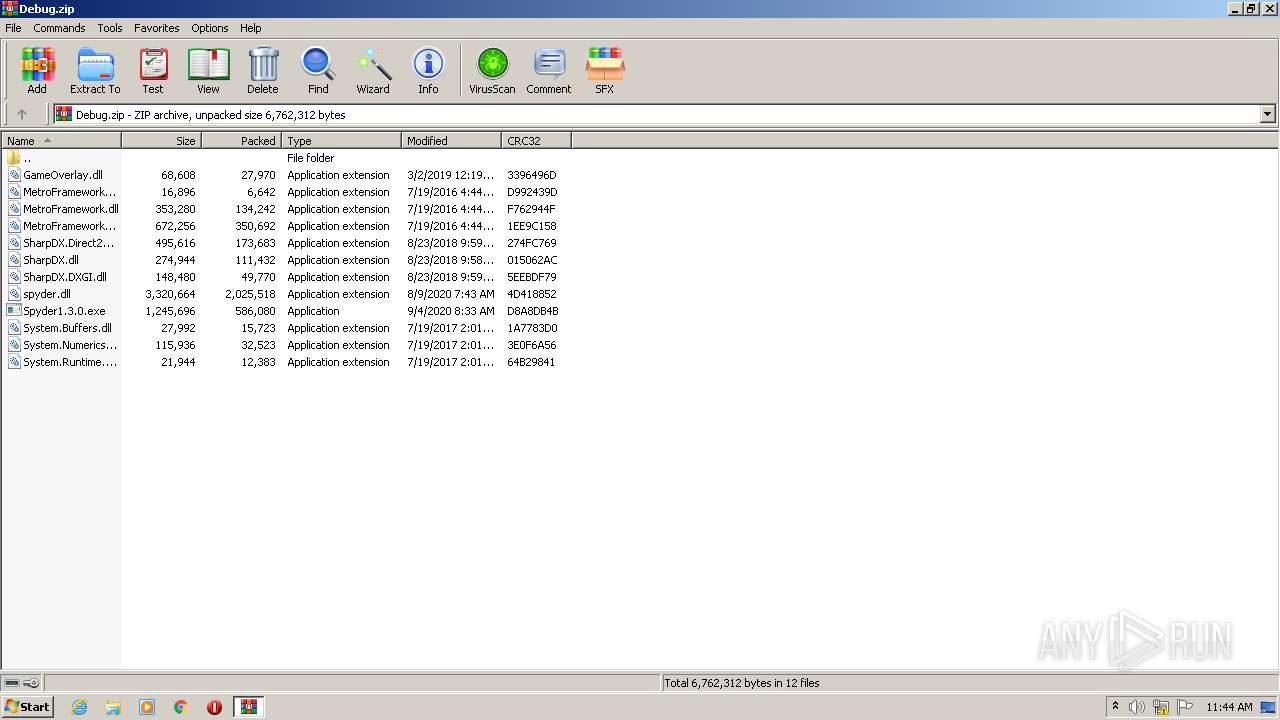
| File name: | Debug.zip |
| Full analysis: | https://app.any.run/tasks/78efb858-98e2-4ee0-9e75-e101e590f7e4 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 11:43:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | BAAE1C69E0B10F25F8AD1C74F663DE8D |
| SHA1: | 820CE12DF752C3C6BEF7F218B6F8FD691E3891D2 |
| SHA256: | 0FB625F48B1210057074B4C2F299B22398070A84D99CD78FE6FA36EA02D44160 |
| SSDEEP: | 98304:+b5Rnf2LXixMr6itVYDPEaxs9mIWJ/lHksQvS:+nJxMr6iED/QmnNlHXQvS |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3448)
Application was dropped or rewritten from another process
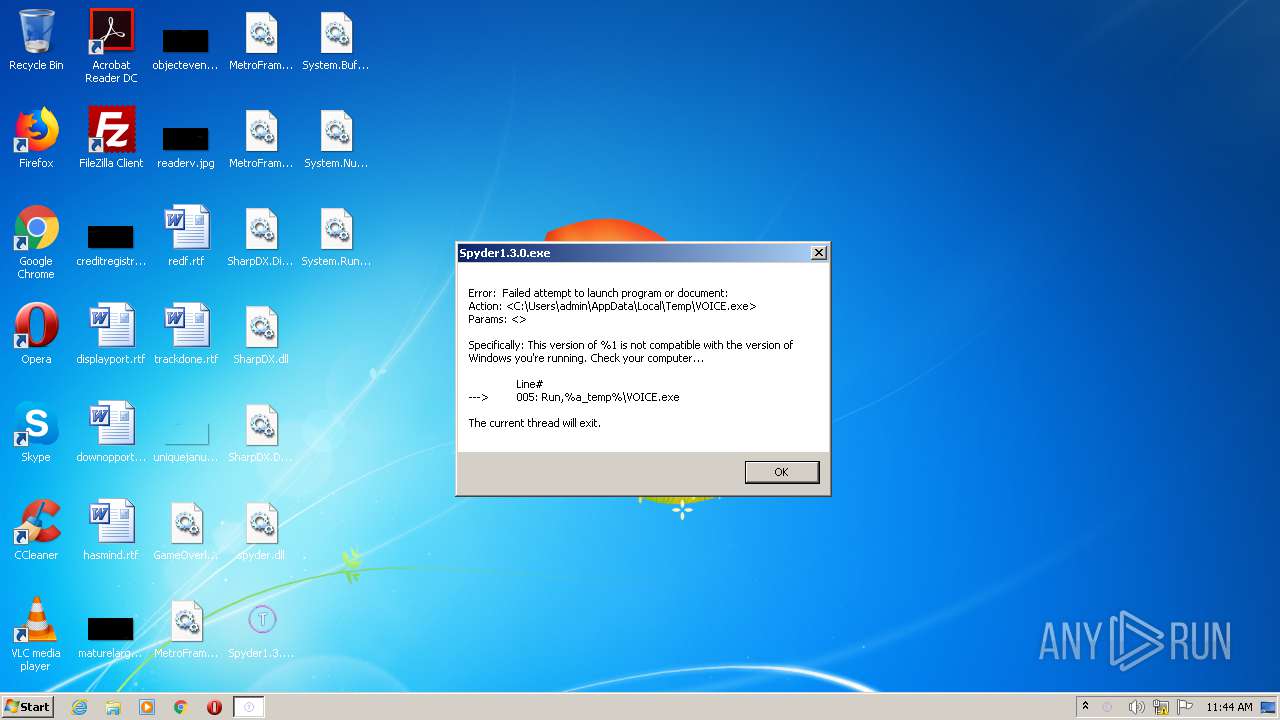
- Spyder1.3.0.exe (PID: 2988)
Drops executable file immediately after starts
- Spyder1.3.0.exe (PID: 2988)
SUSPICIOUS
Drops a file with too old compile date
- WinRAR.exe (PID: 956)
- Spyder1.3.0.exe (PID: 2988)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 956)
- Spyder1.3.0.exe (PID: 2988)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 956)
- Spyder1.3.0.exe (PID: 2988)
Creates files in the user directory
- Spyder1.3.0.exe (PID: 2988)
INFO
Manual execution by user
- Spyder1.3.0.exe (PID: 2988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:03:02 21:19:13 |
| ZipCRC: | 0x3396496d |
| ZipCompressedSize: | 27970 |
| ZipUncompressedSize: | 68608 |
| ZipFileName: | GameOverlay.dll |
Total processes
36
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Debug.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2988 | "C:\Users\admin\Desktop\Spyder1.3.0.exe" | C:\Users\admin\Desktop\Spyder1.3.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.1.32.00 Modules
| |||||||||||||||
| 3448 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
868
Read events
819
Write events
49
Delete events
0
Modification events
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Debug.zip | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Debug | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\AppData\Local\Temp\Debug | |||
Executable files
38
Suspicious files
6
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Debug\GameOverlay.dll | executable | |
MD5:— | SHA256:— | |||
| 956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Debug\spyder.dll | executable | |
MD5:— | SHA256:— | |||
| 956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Debug\Spyder1.3.0.exe | executable | |
MD5:— | SHA256:— | |||
| 956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Debug\SharpDX.dll | executable | |
MD5:C52A44933D17D576D4C97B4CB0545841 | SHA256:A0AF255EA4B09A8CDB995B8C6FD1075E46F098E23C2351C974E6DED9B8B620CF | |||
| 956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Debug\SharpDX.Direct2D1.dll | executable | |
MD5:B992DFABF27B4C32C57D5CC2960CD8E3 | SHA256:9F4B5E240CB42CE903082F81633BBA0C781C1E684FD5903BC3915E3805B5E83E | |||
| 956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Debug\SharpDX.DXGI.dll | executable | |
MD5:D2EDDE626C241549EAB636AA87FB5D38 | SHA256:BC0243134C93C55EA105D0E9C2A43B6030E973290D0A061CF3A61986A2268A88 | |||
| 956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Debug\MetroFramework.dll | executable | |
MD5:34EA7F7D66563F724318E322FF08F4DB | SHA256:C2C12D31B4844E29DE31594FC9632A372A553631DE0A0A04C8AF91668E37CF49 | |||
| 956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Debug\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\spyder.dll | executable | |
MD5:— | SHA256:— | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\GameOverlay.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2988 | Spyder1.3.0.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEBblhnjgcJQ5S9%2FbTvymO98%3D | US | der | 471 b | whitelisted |
2988 | Spyder1.3.0.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEQD5g7jF84adhvw3B5kCUueb | US | der | 280 b | whitelisted |
2988 | Spyder1.3.0.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 313 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2988 | Spyder1.3.0.exe | 162.159.129.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2988 | Spyder1.3.0.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
ocsp.comodoca.com |
| whitelisted |
ocsp.comodoca4.com |
| whitelisted |