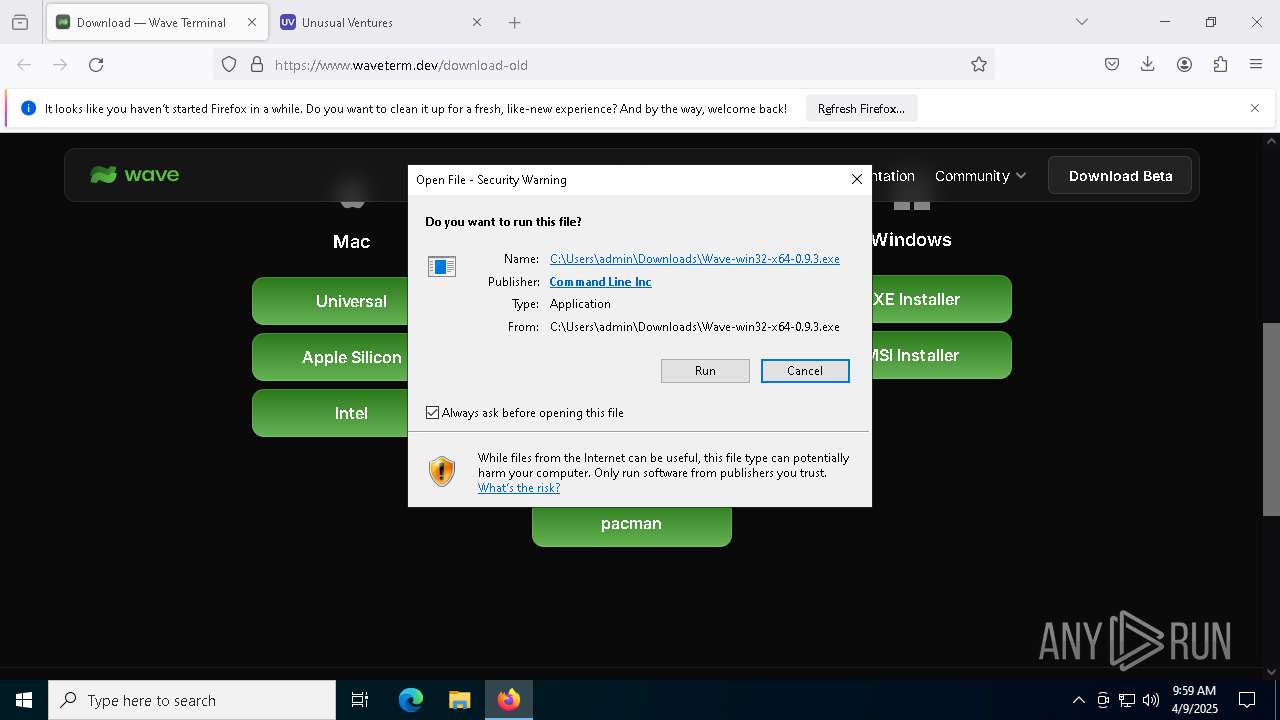
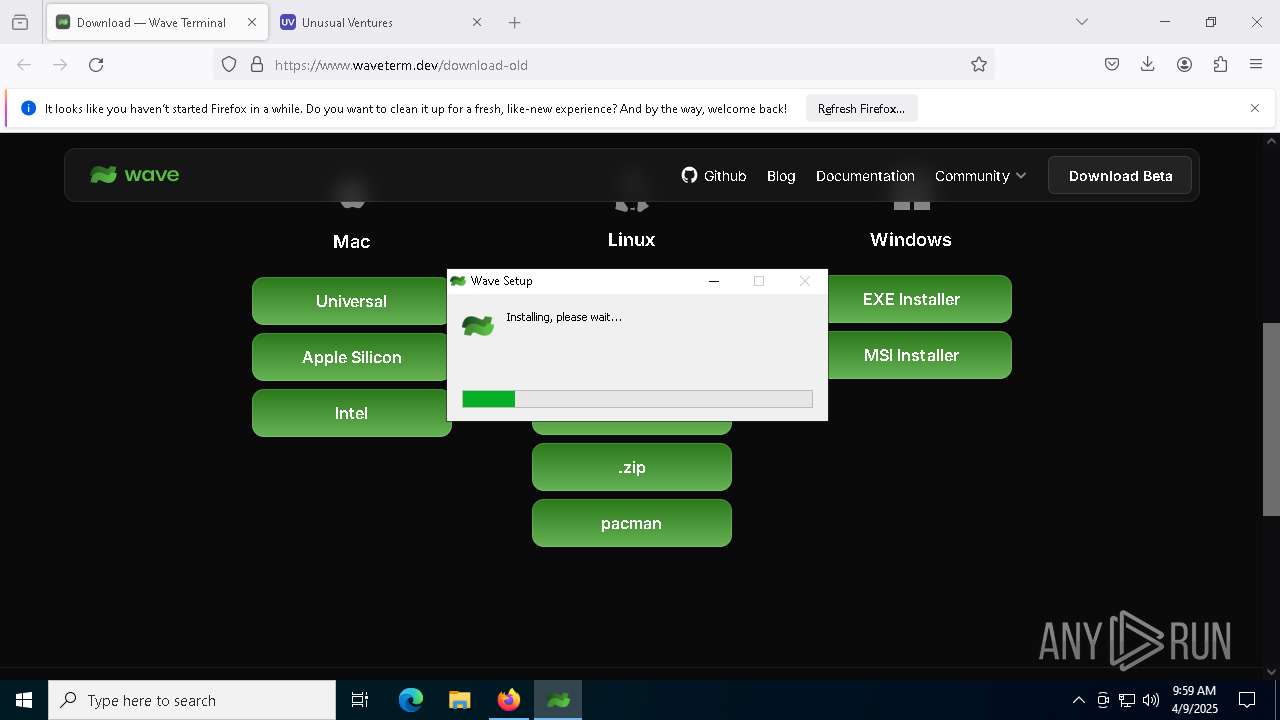
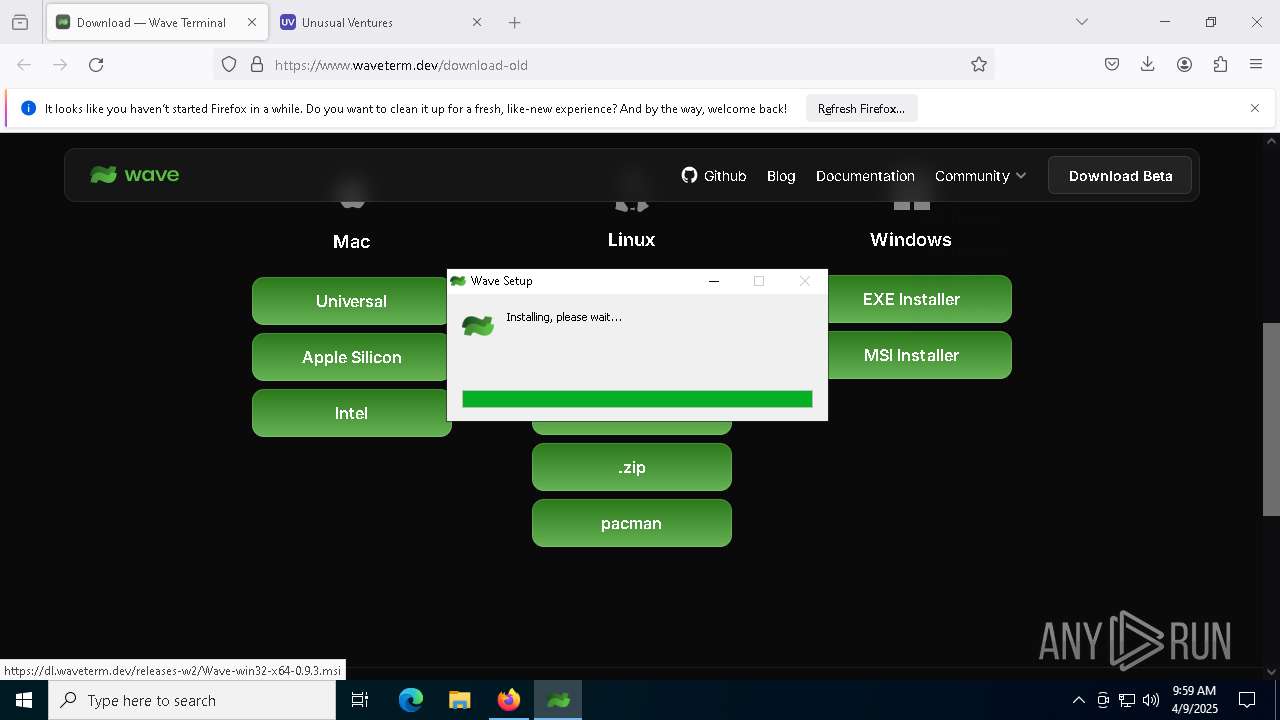
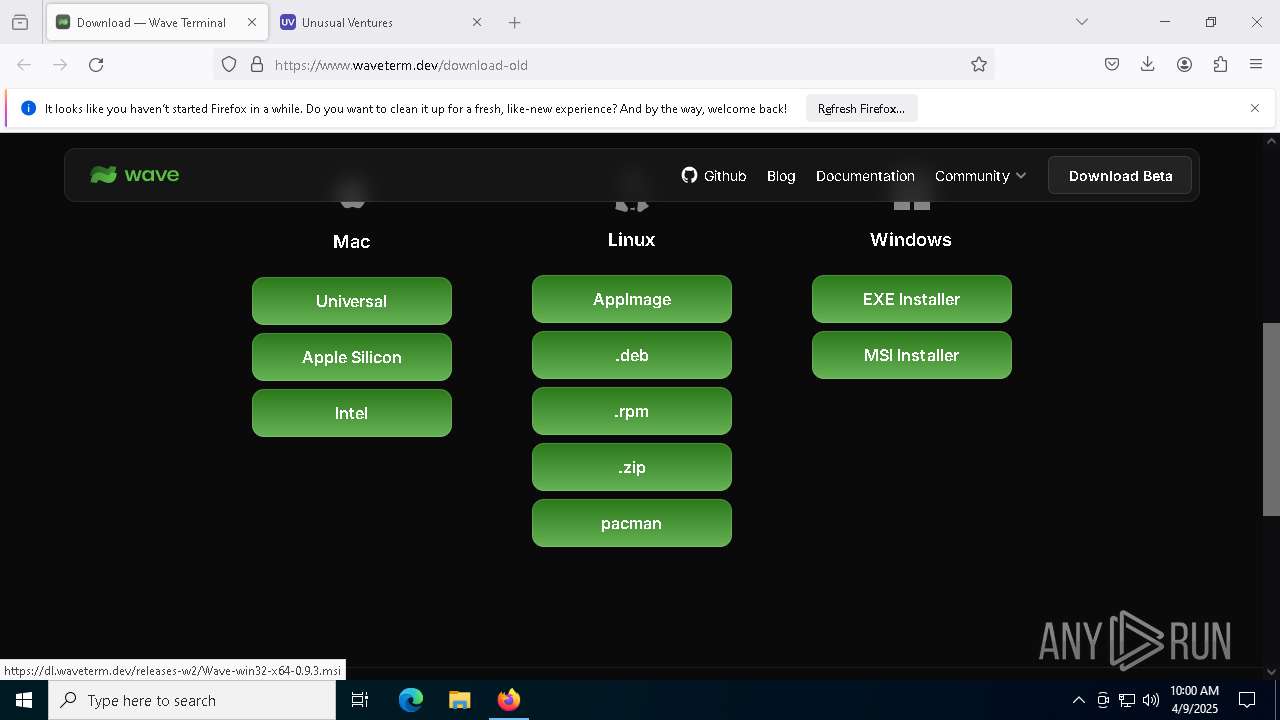
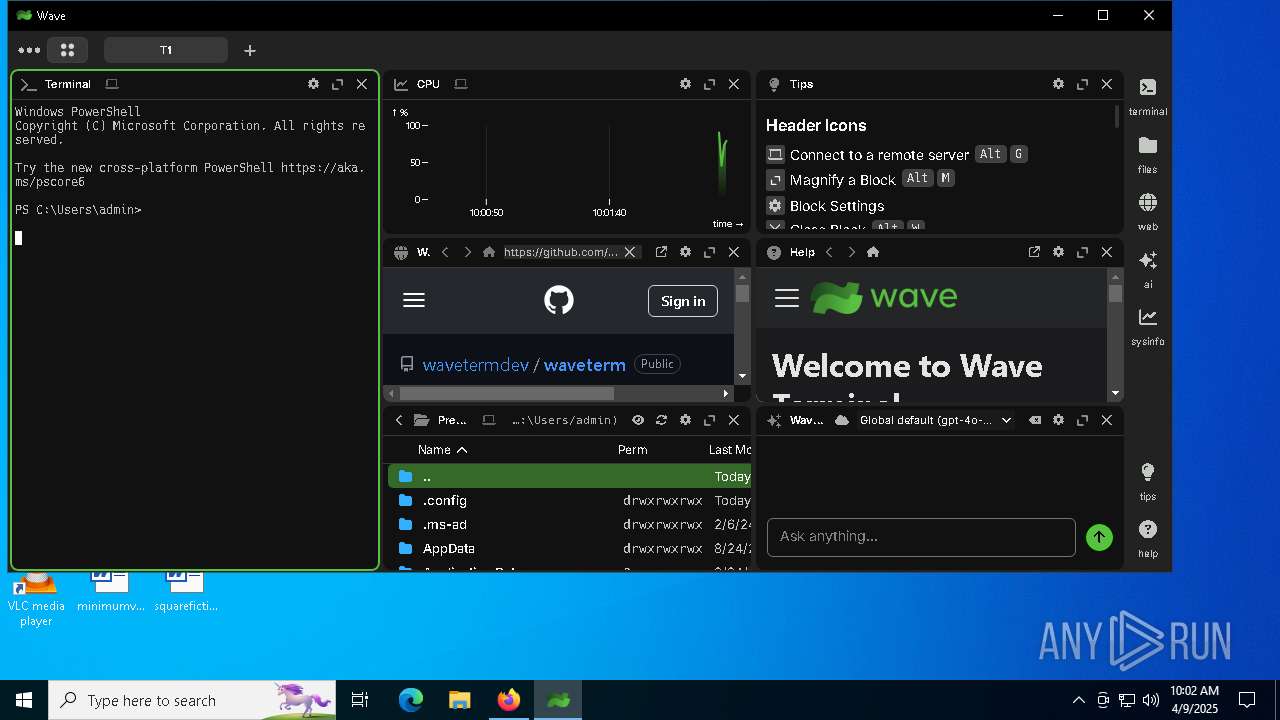
| URL: | https://www.waveterm.dev/download-old |
| Full analysis: | https://app.any.run/tasks/007103cd-2aef-4732-9400-35ab917fe9dc |
| Verdict: | Malicious activity |
| Analysis date: | April 09, 2025, 09:58:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 534B1E1074CD97D3B9B64FD3B9553A0E |
| SHA1: | A11B327926B1036B4F64C6F2E29012E9D4195C46 |
| SHA256: | 0FA8DAEDC8BBDED930B0C124656749327A5FB4B683B6EBABBF1C2D5F09490CF5 |
| SSDEEP: | 3:N8DSLAym6KJBn:2OLNCP |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 5408)
Changes powershell execution policy (Bypass)
- wavesrv.x64.exe (PID: 8092)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
- old-uninstaller.exe (PID: 8212)
The process creates files with name similar to system file names
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
- old-uninstaller.exe (PID: 8212)
Executable content was dropped or overwritten
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- wavesrv.x64.exe (PID: 8092)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
- old-uninstaller.exe (PID: 8212)
- wavesrv.x64.exe (PID: 6252)
- wavesrv.x64.exe (PID: 8300)
Starts CMD.EXE for commands execution
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- Wave.exe (PID: 1300)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
- old-uninstaller.exe (PID: 8212)
Get information on the list of running processes
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- cmd.exe (PID: 5544)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
- cmd.exe (PID: 9176)
- old-uninstaller.exe (PID: 8212)
- cmd.exe (PID: 7856)
- cmd.exe (PID: 924)
Drops 7-zip archiver for unpacking
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
Process drops legitimate windows executable
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- old-uninstaller.exe (PID: 8212)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
There is functionality for taking screenshot (YARA)
- Wave-win32-x64-0.9.3.exe (PID: 6800)
Reads security settings of Internet Explorer
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- ShellExperienceHost.exe (PID: 8660)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
Application launched itself
- Wave.exe (PID: 1300)
- Wave.exe (PID: 5304)
- Wave.exe (PID: 8280)
Creates a software uninstall entry
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
The process executes Powershell scripts
- wavesrv.x64.exe (PID: 8092)
Starts POWERSHELL.EXE for commands execution
- wavesrv.x64.exe (PID: 8092)
- cmd.exe (PID: 8264)
Hides command output
- cmd.exe (PID: 8264)
Starts application with an unusual extension
- cmd.exe (PID: 8264)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 8264)
The process hide an interactive prompt from the user
- cmd.exe (PID: 8264)
Searches for installed software
- Wave-win32-x64-0.11.2.exe (PID: 8820)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4016)
INFO
Application launched itself
- firefox.exe (PID: 6640)
- firefox.exe (PID: 6036)
Executable content was dropped or overwritten
- firefox.exe (PID: 6036)
Reads the software policy settings
- slui.exe (PID: 4428)
- wavesrv.x64.exe (PID: 8092)
- slui.exe (PID: 6004)
- wavesrv.x64.exe (PID: 8300)
Autorun file from Downloads
- firefox.exe (PID: 6036)
Checks supported languages
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- wavesrv.x64.exe (PID: 8092)
- Wave.exe (PID: 6256)
- Wave.exe (PID: 3760)
- Wave.exe (PID: 4040)
- Wave.exe (PID: 1300)
- Wave.exe (PID: 236)
- Wave.exe (PID: 5036)
- Wave.exe (PID: 8172)
- Wave.exe (PID: 7720)
- Wave.exe (PID: 3304)
- chcp.com (PID: 8316)
- ShellExperienceHost.exe (PID: 8660)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
- old-uninstaller.exe (PID: 8212)
- Wave.exe (PID: 5304)
- wavesrv.x64.exe (PID: 6252)
- Wave.exe (PID: 2904)
- Wave.exe (PID: 2316)
- Wave.exe (PID: 6876)
- Wave.exe (PID: 5868)
- Wave.exe (PID: 8280)
- wavesrv.x64.exe (PID: 8300)
- Wave.exe (PID: 4164)
- Wave.exe (PID: 6564)
- Wave.exe (PID: 4068)
- Wave.exe (PID: 5064)
- Wave.exe (PID: 6080)
- Wave.exe (PID: 6800)
- pwsh.exe (PID: 6148)
- Wave.exe (PID: 664)
- Wave.exe (PID: 5036)
- wsh.exe (PID: 3796)
- wsh.exe (PID: 8988)
The sample compiled with english language support
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- old-uninstaller.exe (PID: 8212)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
Reads the computer name
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- Wave.exe (PID: 3760)
- Wave.exe (PID: 1300)
- Wave.exe (PID: 6256)
- wavesrv.x64.exe (PID: 8092)
- ShellExperienceHost.exe (PID: 8660)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
- Wave.exe (PID: 5304)
- Wave.exe (PID: 2904)
- Wave.exe (PID: 2316)
- Wave.exe (PID: 8280)
- Wave.exe (PID: 5036)
- Wave.exe (PID: 4164)
- wavesrv.x64.exe (PID: 8300)
- wsh.exe (PID: 3796)
- pwsh.exe (PID: 6148)
Create files in a temporary directory
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- Wave.exe (PID: 1300)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
- old-uninstaller.exe (PID: 8212)
- Wave.exe (PID: 5304)
- Wave.exe (PID: 8280)
Creates files or folders in the user directory
- Wave-win32-x64-0.9.3.exe (PID: 6800)
- wavesrv.x64.exe (PID: 8092)
- Wave.exe (PID: 6256)
- Wave.exe (PID: 1300)
- wavesrv.x64.exe (PID: 6252)
- Wave.exe (PID: 5304)
- Wave.exe (PID: 2904)
- Wave.exe (PID: 8280)
- Wave-win32-x64-0.11.2.exe (PID: 8820)
- wavesrv.x64.exe (PID: 8300)
- Wave.exe (PID: 4164)
Process checks computer location settings
- Wave.exe (PID: 1300)
- Wave.exe (PID: 4040)
- Wave.exe (PID: 5036)
- Wave.exe (PID: 8172)
- Wave.exe (PID: 7720)
- Wave.exe (PID: 236)
- Wave.exe (PID: 3304)
- Wave.exe (PID: 5304)
- Wave.exe (PID: 6876)
- Wave.exe (PID: 5868)
- Wave.exe (PID: 8280)
- Wave.exe (PID: 4068)
- Wave.exe (PID: 5064)
- Wave.exe (PID: 6080)
- Wave.exe (PID: 6564)
- Wave.exe (PID: 6800)
- Wave.exe (PID: 664)
- pwsh.exe (PID: 6148)
Manual execution by a user
- Wave.exe (PID: 1300)
- Wave.exe (PID: 5304)
- Wave.exe (PID: 8280)
Reads product name
- Wave.exe (PID: 1300)
- Wave.exe (PID: 5304)
- Wave.exe (PID: 8280)
Reads Environment values
- Wave.exe (PID: 1300)
- Wave.exe (PID: 5304)
- Wave.exe (PID: 8280)
Reads the machine GUID from the registry
- Wave.exe (PID: 1300)
- wavesrv.x64.exe (PID: 8092)
- Wave.exe (PID: 5304)
- Wave.exe (PID: 8280)
- wavesrv.x64.exe (PID: 8300)
Drops encrypted JS script (Microsoft Script Encoder)
- wavesrv.x64.exe (PID: 8092)
- wavesrv.x64.exe (PID: 8300)
Checks proxy server information
- Wave.exe (PID: 1300)
- slui.exe (PID: 6004)
- Wave.exe (PID: 5304)
- Wave.exe (PID: 8280)
Application based on Golang
- wavesrv.x64.exe (PID: 8092)
Detects GO elliptic curve encryption (YARA)
- wavesrv.x64.exe (PID: 8092)
Checks current location (POWERSHELL)
- powershell.exe (PID: 5408)
Changes the display of characters in the console
- cmd.exe (PID: 8264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
221
Monitored processes
80
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Users\admin\AppData\Local\Programs\waveterm\Wave.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\Wave" --app-path="C:\Users\admin\AppData\Local\Programs\waveterm\resources\app.asar" --enable-sandbox --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3572,i,8650699057520707047,5879924895801712616,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=3544 /prefetch:1 | C:\Users\admin\AppData\Local\Programs\waveterm\Wave.exe | — | Wave.exe | |||||||||||
User: admin Company: Command Line Inc Integrity Level: LOW Description: Open-Source AI-Native Terminal Built for Seamless Workflows Exit code: 0 Version: 0.9.3 Modules
| |||||||||||||||
| 664 | "C:\Users\admin\AppData\Local\Programs\waveterm\Wave.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\Wave" --app-path="C:\Users\admin\AppData\Local\Programs\waveterm\resources\app.asar" --enable-sandbox --enable-blink-features --disable-blink-features --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --field-trial-handle=3924,i,2236255096315619488,9656426897110430988,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=4032 /prefetch:1 | C:\Users\admin\AppData\Local\Programs\waveterm\Wave.exe | — | Wave.exe | |||||||||||
User: admin Company: Command Line Inc Integrity Level: LOW Description: Wave Exit code: 0 Version: 0.11.2 Modules
| |||||||||||||||
| 924 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | "C:\WINDOWS\system32\cmd.exe" /c tasklist /FI "USERNAME eq %USERNAME%" /FI "IMAGENAME eq Wave.exe" /FO csv | "C:\WINDOWS\system32\find.exe" "Wave.exe" | C:\Windows\SysWOW64\cmd.exe | — | old-uninstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | "C:\Users\admin\AppData\Local\Programs\waveterm\Wave.exe" | C:\Users\admin\AppData\Local\Programs\waveterm\Wave.exe | — | explorer.exe | |||||||||||
User: admin Company: Command Line Inc Integrity Level: MEDIUM Description: Open-Source AI-Native Terminal Built for Seamless Workflows Exit code: 0 Version: 0.9.3 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6048 -parentBuildID 20240213221259 -prefsHandle 4820 -prefMapHandle 5176 -prefsLen 36970 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {0e549fe1-c4de-4932-89ba-48e168689027} 6036 "\\.\pipe\gecko-crash-server-pipe.6036" 12e77589710 rdd | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1452 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2316 | "C:\Users\admin\AppData\Local\Programs\waveterm\Wave.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\Wave" --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1888,i,2229720691238047758,1988960371223948045,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=1876 /prefetch:2 | C:\Users\admin\AppData\Local\Programs\waveterm\Wave.exe | — | Wave.exe | |||||||||||
User: admin Company: Command Line Inc Integrity Level: LOW Description: Open-Source AI-Native Terminal Built for Seamless Workflows Exit code: 0 Version: 0.9.3 Modules
| |||||||||||||||
| 2416 | tasklist /FI "USERNAME eq admin" /FI "IMAGENAME eq Wave.exe" /FO csv | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
57 188
Read events
57 103
Write events
29
Delete events
56
Modification events
| (PID) Process: | (6036) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6036) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6800) Wave-win32-x64-0.9.3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\acb9179c-3638-5f0d-8173-399943676f25 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Programs\waveterm | |||
| (PID) Process: | (6800) Wave-win32-x64-0.9.3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\acb9179c-3638-5f0d-8173-399943676f25 |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (6800) Wave-win32-x64-0.9.3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\acb9179c-3638-5f0d-8173-399943676f25 |
| Operation: | write | Name: | ShortcutName |
Value: Wave | |||
| (PID) Process: | (6800) Wave-win32-x64-0.9.3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\acb9179c-3638-5f0d-8173-399943676f25 |
| Operation: | write | Name: | DisplayName |
Value: Wave 0.9.3 | |||
| (PID) Process: | (6800) Wave-win32-x64-0.9.3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\acb9179c-3638-5f0d-8173-399943676f25 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\waveterm\Uninstall Wave.exe" /currentuser | |||
| (PID) Process: | (6800) Wave-win32-x64-0.9.3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\acb9179c-3638-5f0d-8173-399943676f25 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\waveterm\Uninstall Wave.exe" /currentuser /S | |||
| (PID) Process: | (6800) Wave-win32-x64-0.9.3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\acb9179c-3638-5f0d-8173-399943676f25 |
| Operation: | write | Name: | DisplayVersion |
Value: 0.9.3 | |||
| (PID) Process: | (6800) Wave-win32-x64-0.9.3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\acb9179c-3638-5f0d-8173-399943676f25 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Local\Programs\waveterm\Wave.exe,0 | |||
Executable files
69
Suspicious files
988
Text files
322
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6036 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6036 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6036 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 6036 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6036 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6036 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6036 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db | binary | |
MD5:652A058986ED4C4827D5671C2C5AE672 | SHA256:0A967B0E5B6B8767941661041FBCD6F6A950358B3A7CDB055886D600ADE7C590 | |||
| 6036 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db-journal | binary | |
MD5:D57575F4A63D3678D0C62B97F9A0A134 | SHA256:3E05E53F85F0C25388BD242077982F87E9A41DB8F2267218B09D623B4610A11B | |||
| 6036 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 6036 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
202
DNS requests
243
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6036 | firefox.exe | POST | 200 | 2.16.206.148:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6036 | firefox.exe | POST | 200 | 2.16.206.148:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6036 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
6036 | firefox.exe | POST | 200 | 2.16.206.148:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6036 | firefox.exe | POST | 200 | 2.16.206.148:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6036 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
6036 | firefox.exe | POST | 200 | 18.245.65.219:80 | http://ocsp.r2m03.amazontrust.com/ | unknown | — | — | whitelisted |
6036 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
6036 | firefox.exe | POST | 200 | 2.16.206.148:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6036 | firefox.exe | POST | 200 | 2.16.206.148:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6036 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
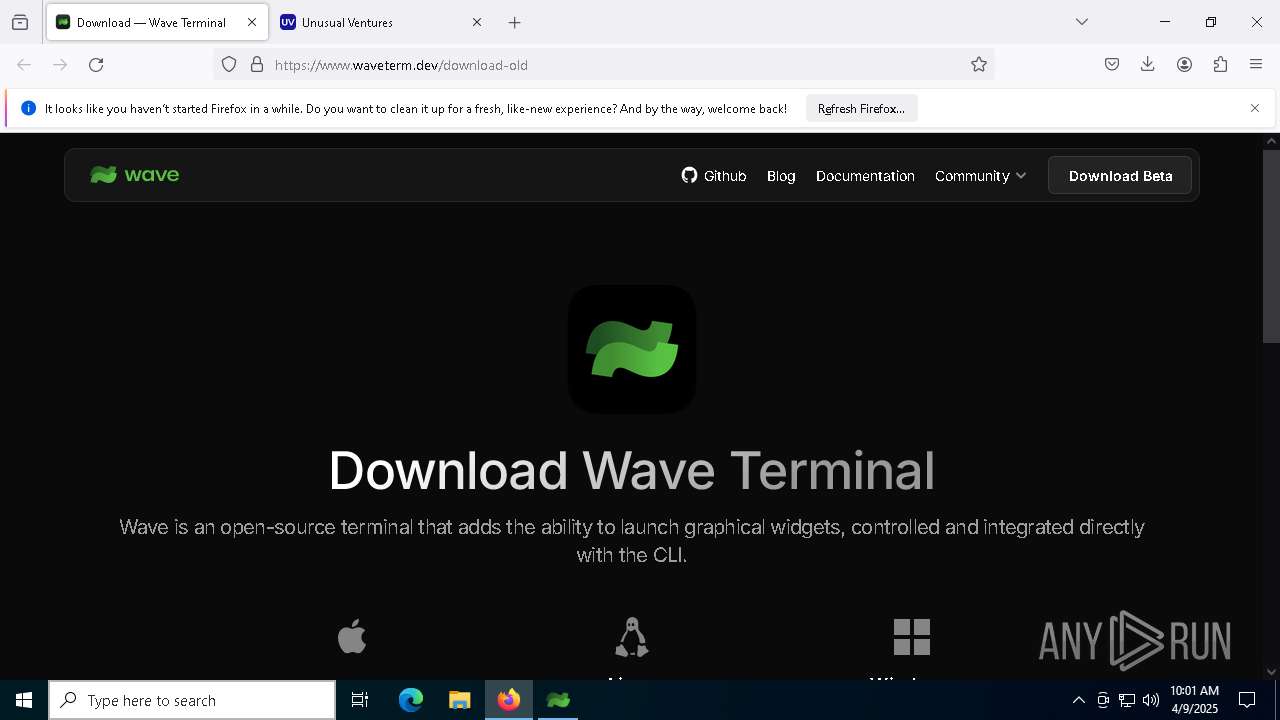
6036 | firefox.exe | 52.223.52.2:443 | www.waveterm.dev | AMAZON-02 | US | unknown |
6036 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
6036 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
6036 | firefox.exe | 142.250.186.42:443 | safebrowsing.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.waveterm.dev |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
sites.framer.app |
| unknown |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Framer web builder (.framer .app) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Framer web builder (.framer .app) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud development environments (csb .app) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud development environments (csb .app) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud development environments (csb .app) |
6036 | firefox.exe | Not Suspicious Traffic | INFO [ANY.RUN] CodeSandbox domain observed in TLS SNI |