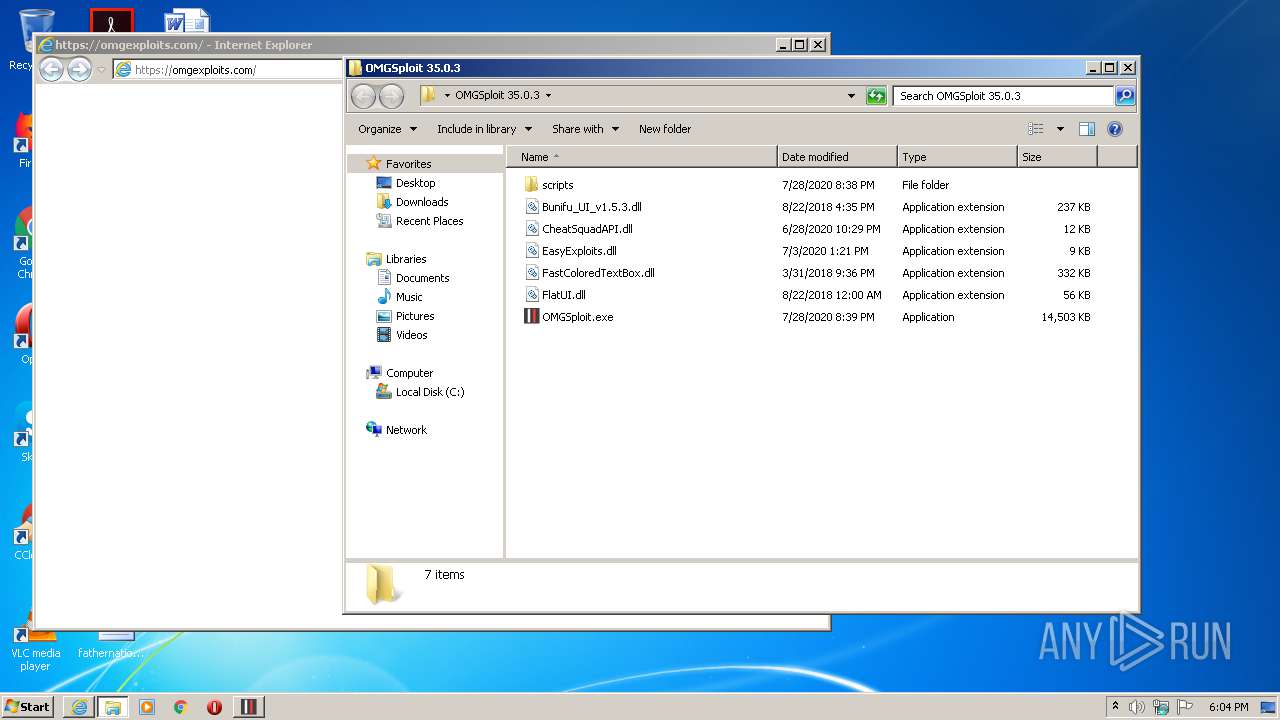
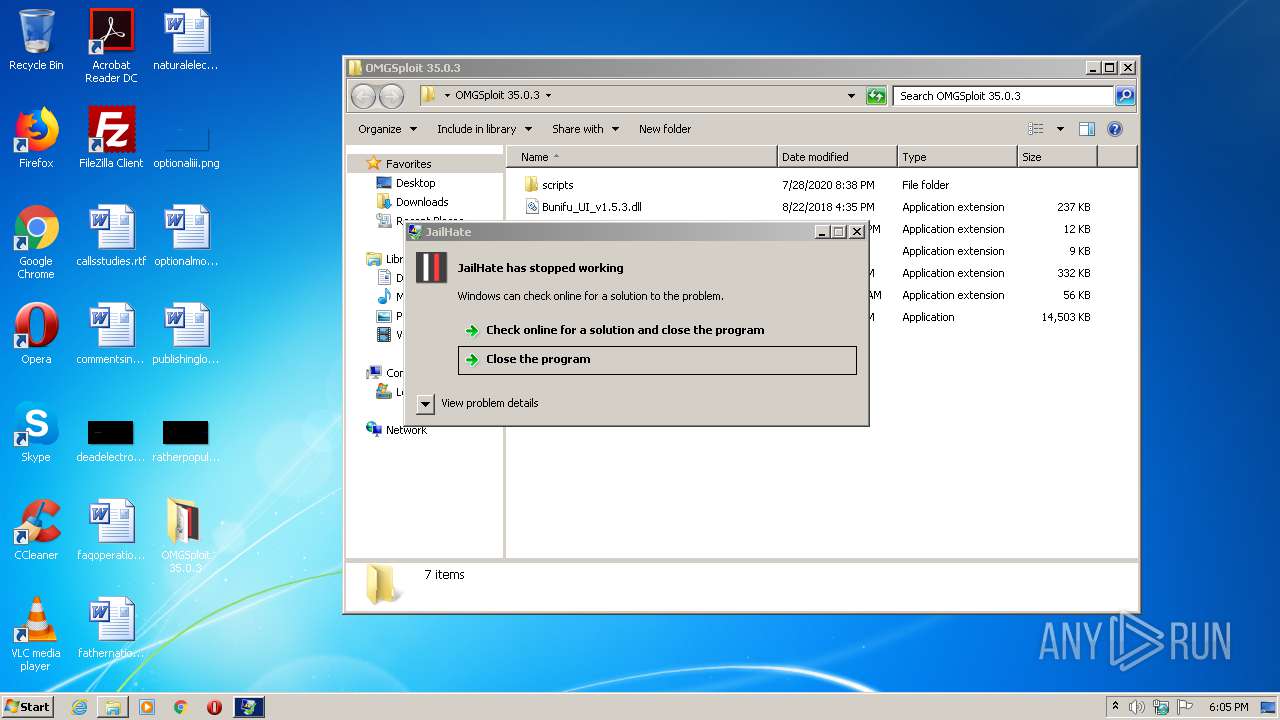
| File name: | OMGSploit 35.0.3.zip |
| Full analysis: | https://app.any.run/tasks/df9efe87-2871-45c8-b706-3431162e0f94 |
| Verdict: | Malicious activity |
| Analysis date: | September 24, 2020, 17:04:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | D64CC41D4E17B36A9D07E11A15DBB8B3 |
| SHA1: | E17BDC41574152E7AC9B9503095AB93089D11A27 |
| SHA256: | 0F973C04BAE1E9737B8D677586A8789AFDF96220C0951E37EDDA7C19A342C511 |
| SSDEEP: | 393216:f10q2JKZqiVz6ehzJaX32qvbBDAH7lSy9:NV2JigyVMmylEpSy9 |
MALICIOUS
No malicious indicators.SUSPICIOUS
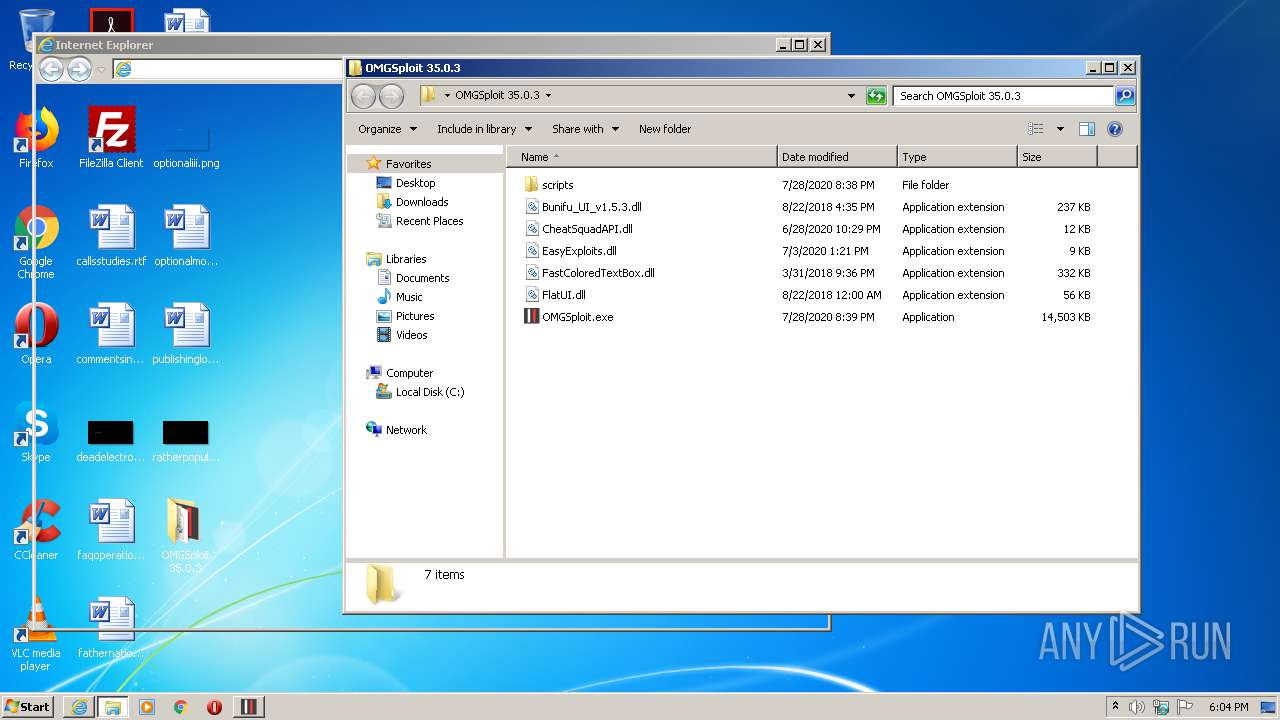
Starts Internet Explorer
- OMGSploit.exe (PID: 4048)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3924)
Reads internet explorer settings
- iexplore.exe (PID: 700)
Manual execution by user
- OMGSploit.exe (PID: 4048)
Reads Internet Cache Settings
- iexplore.exe (PID: 3924)
- iexplore.exe (PID: 700)
Application launched itself
- iexplore.exe (PID: 3924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:07:28 21:39:13 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | OMGSploit 35.0.3/ |
Total processes
43
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3924 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2508 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\OMGSploit 35.0.3.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
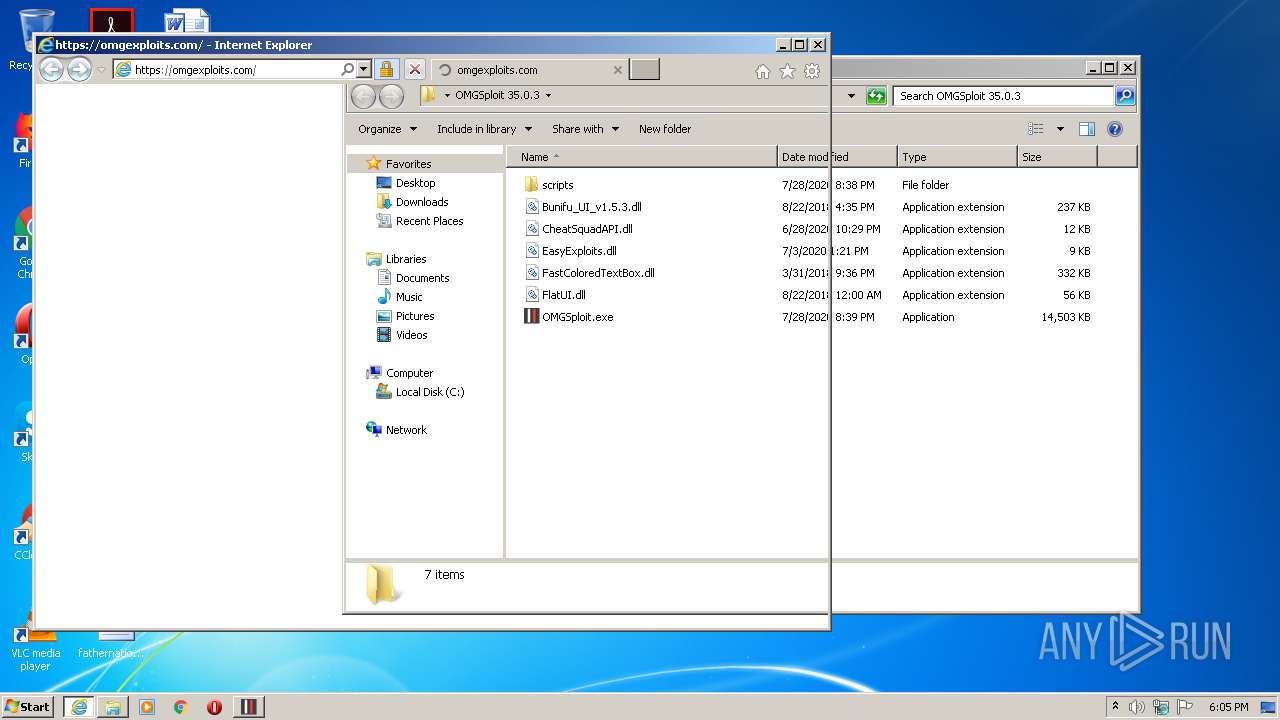
| 3924 | "C:\Program Files\Internet Explorer\iexplore.exe" https://omgexploits.com/ | C:\Program Files\Internet Explorer\iexplore.exe | OMGSploit.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
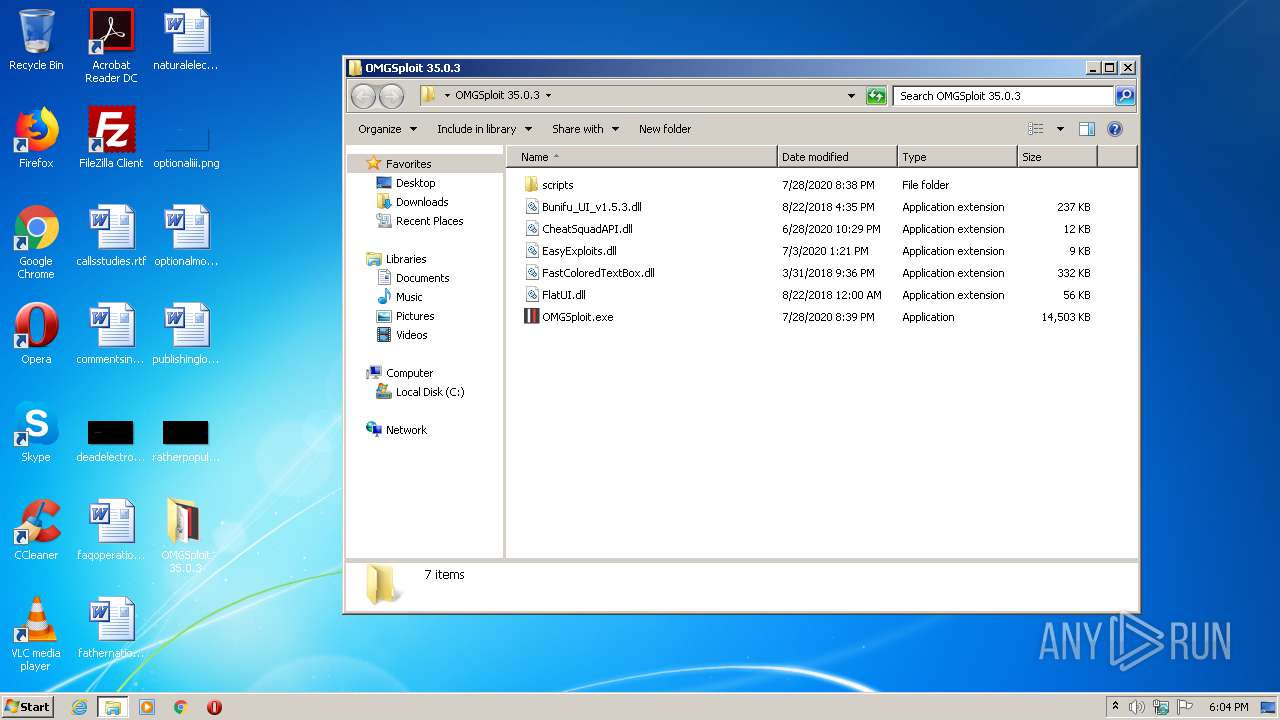
| 4048 | "C:\Users\admin\Desktop\OMGSploit 35.0.3\OMGSploit.exe" | C:\Users\admin\Desktop\OMGSploit 35.0.3\OMGSploit.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: JailHate Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
793
Read events
692
Write events
97
Delete events
4
Modification events
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\OMGSploit 35.0.3.zip | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
0
Suspicious files
47
Text files
13
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2508.40750\OMGSploit 35.0.3\Bunifu_UI_v1.5.3.dll | — | |
MD5:— | SHA256:— | |||
| 2508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2508.40750\OMGSploit 35.0.3\CheatSquadAPI.dll | — | |
MD5:— | SHA256:— | |||
| 2508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2508.40750\OMGSploit 35.0.3\EasyExploits.dll | — | |
MD5:— | SHA256:— | |||
| 2508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2508.40750\OMGSploit 35.0.3\FastColoredTextBox.dll | — | |
MD5:— | SHA256:— | |||
| 2508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2508.40750\OMGSploit 35.0.3\FlatUI.dll | — | |
MD5:— | SHA256:— | |||
| 2508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2508.40750\OMGSploit 35.0.3\OMGSploit.exe | — | |
MD5:— | SHA256:— | |||
| 700 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab52BA.tmp | — | |
MD5:— | SHA256:— | |||
| 700 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar52BB.tmp | — | |
MD5:— | SHA256:— | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
41
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
700 | iexplore.exe | GET | — | 8.241.122.126:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | — | — | whitelisted |
700 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
700 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
700 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCmw8k59ISJiAgAAAAAVgXp | US | der | 472 b | whitelisted |
700 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
700 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDqXuNQ97mPtAIAAAAAektt | US | der | 472 b | whitelisted |
700 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
700 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDqXuNQ97mPtAIAAAAAektt | US | der | 472 b | whitelisted |
700 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCmw8k59ISJiAgAAAAAVgXp | US | der | 472 b | whitelisted |
700 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQDJzHdWtGaEjwP4azdkLZou | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
700 | iexplore.exe | 94.31.29.128:443 | p363420.mycdn.co | netDNA | GB | malicious |
— | — | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
700 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
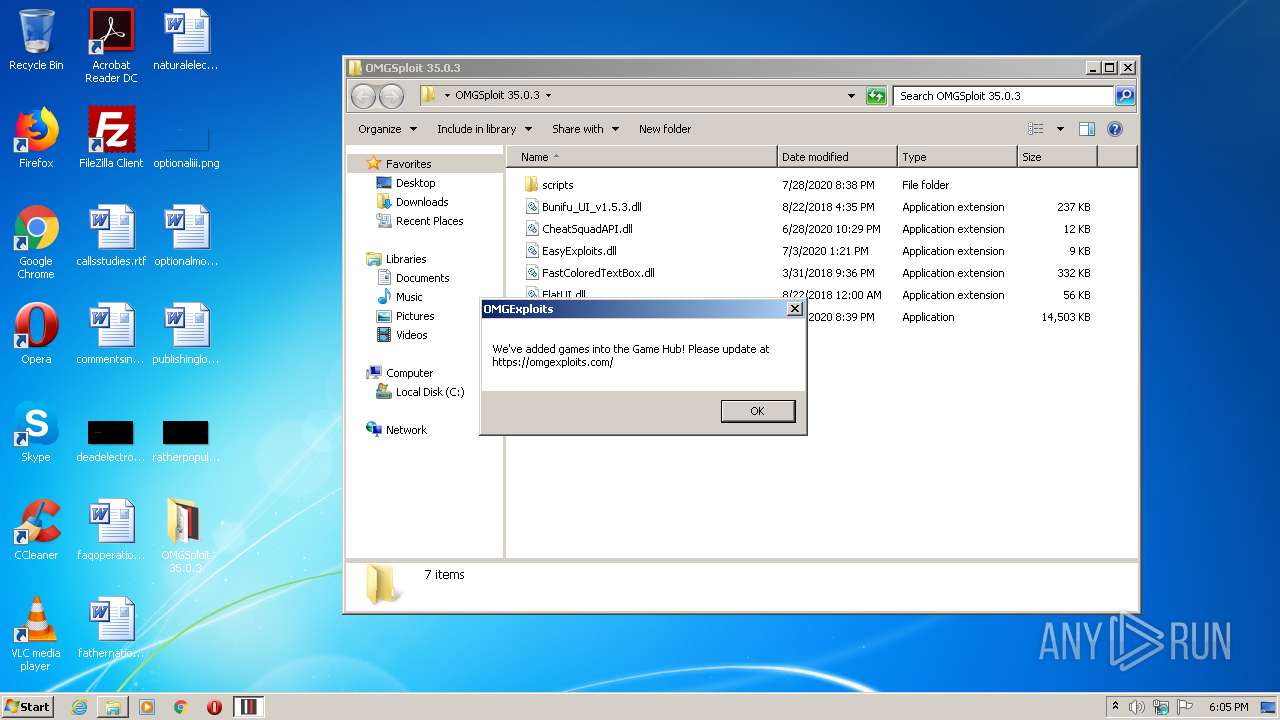
700 | iexplore.exe | 199.188.201.16:443 | omgexploits.com | Namecheap, Inc. | US | malicious |
3924 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
700 | iexplore.exe | 173.192.101.24:443 | p363420.clksite.com | SoftLayer Technologies Inc. | US | suspicious |
700 | iexplore.exe | 172.217.21.226:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
700 | iexplore.exe | 8.241.122.126:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
700 | iexplore.exe | 216.58.207.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
700 | iexplore.exe | 172.217.22.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
omgexploits.com |
| malicious |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
p363420.clksite.com |
| suspicious |
pagead2.googlesyndication.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |