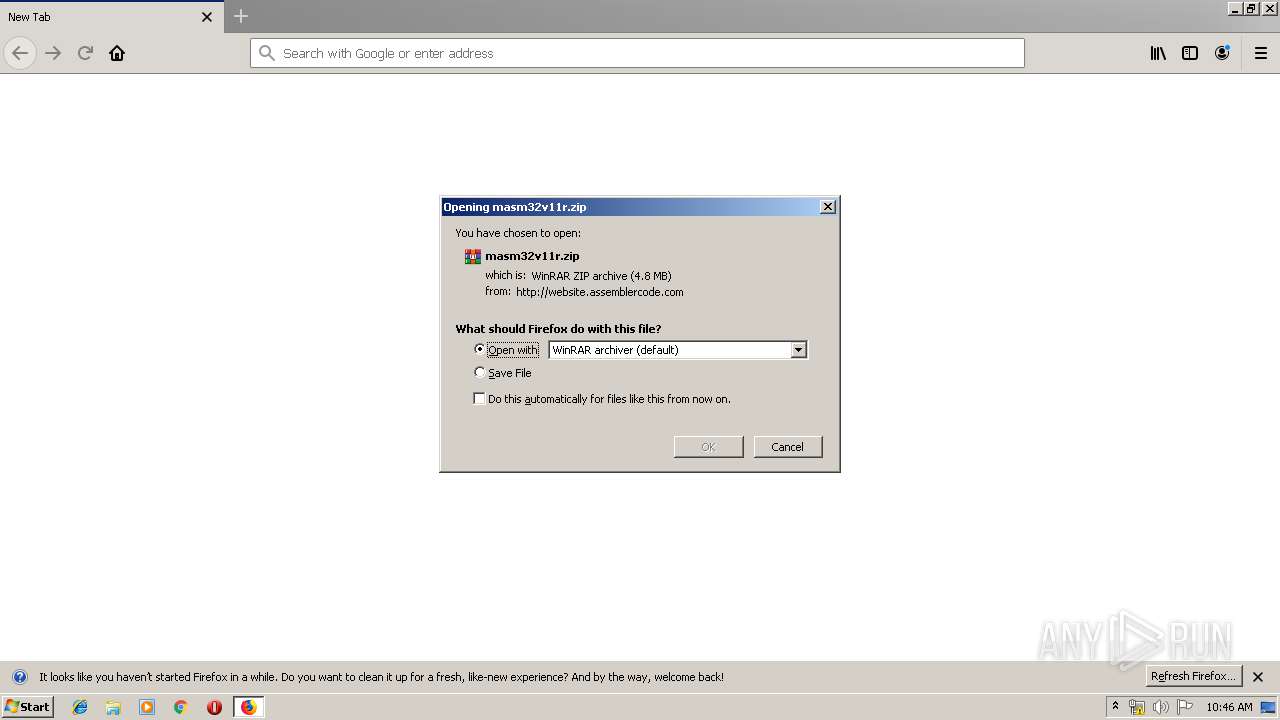
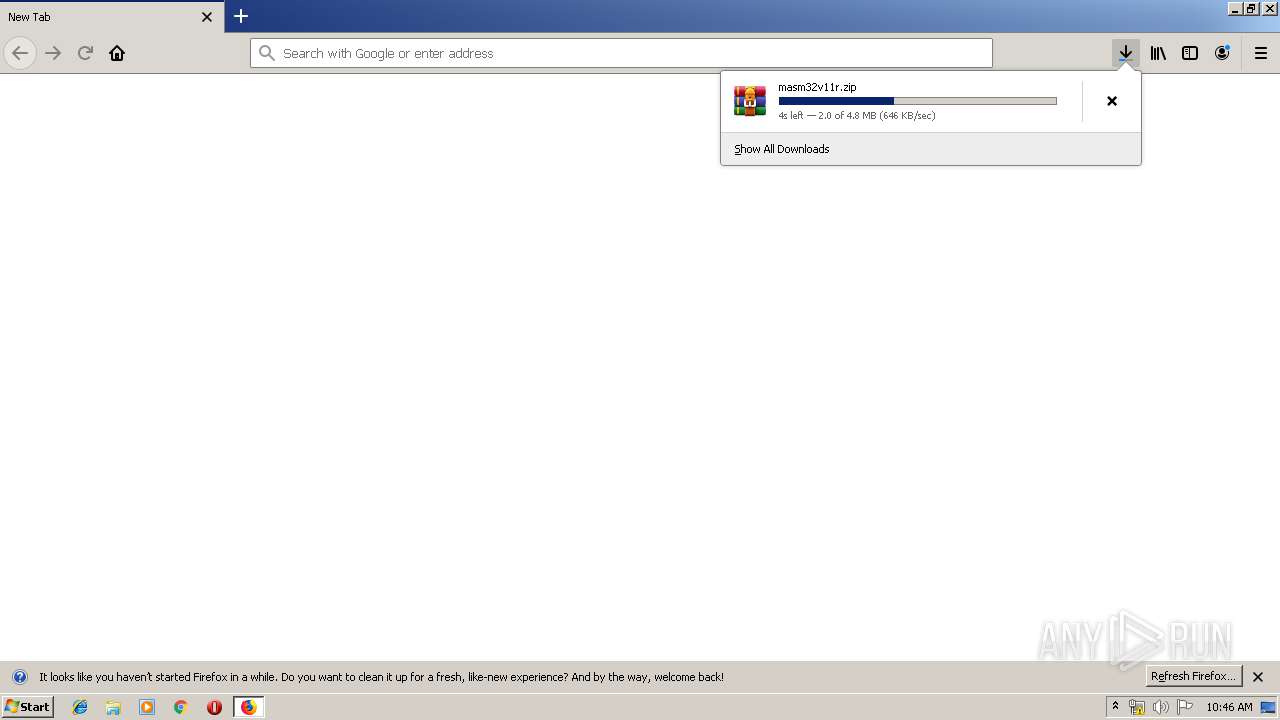
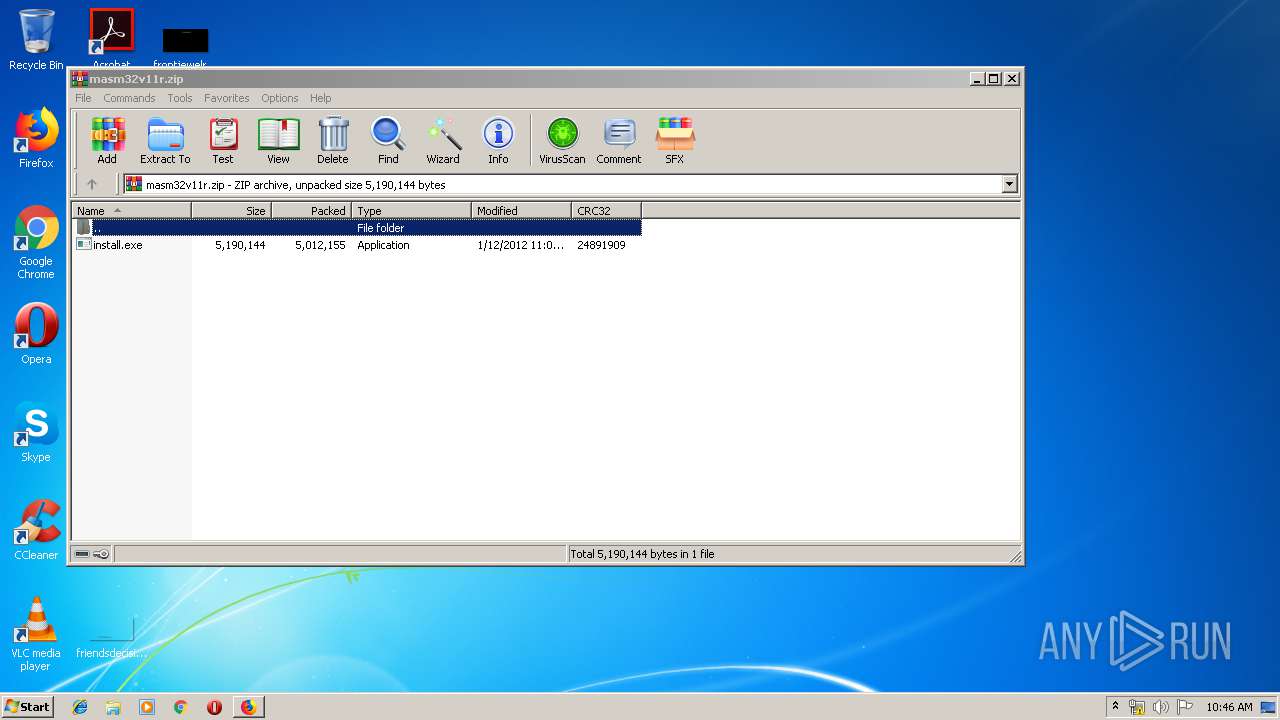
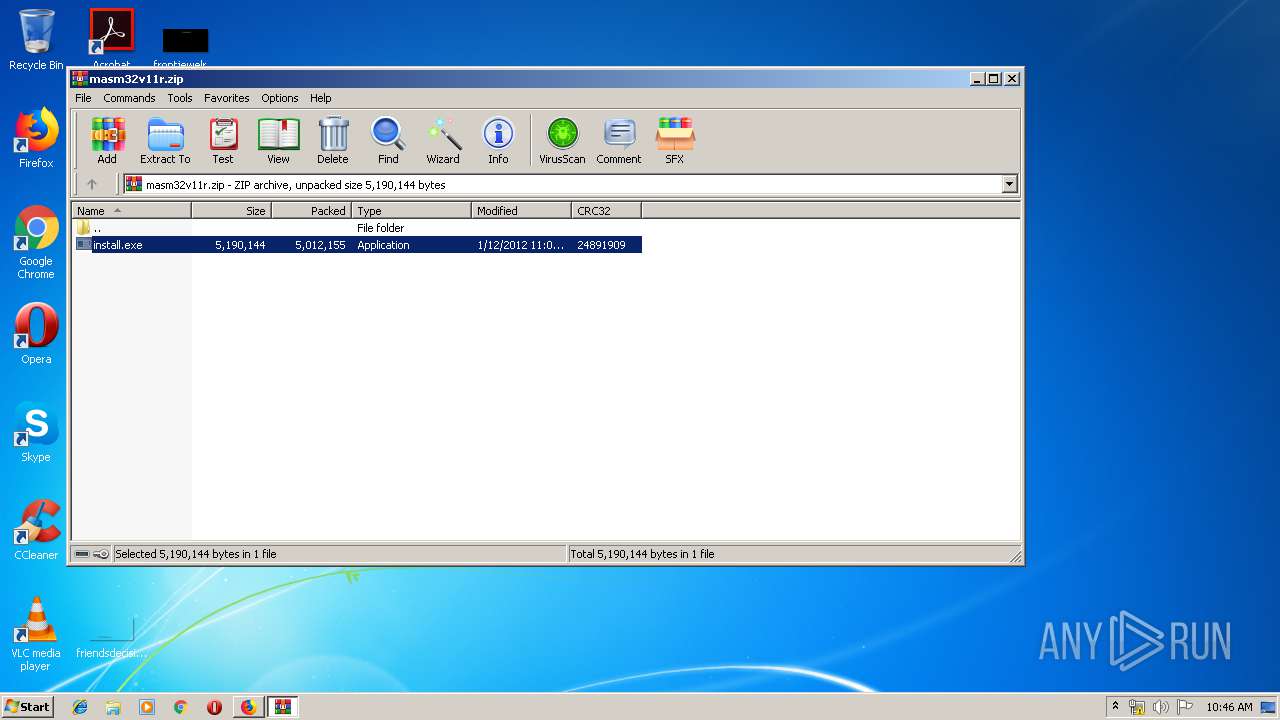
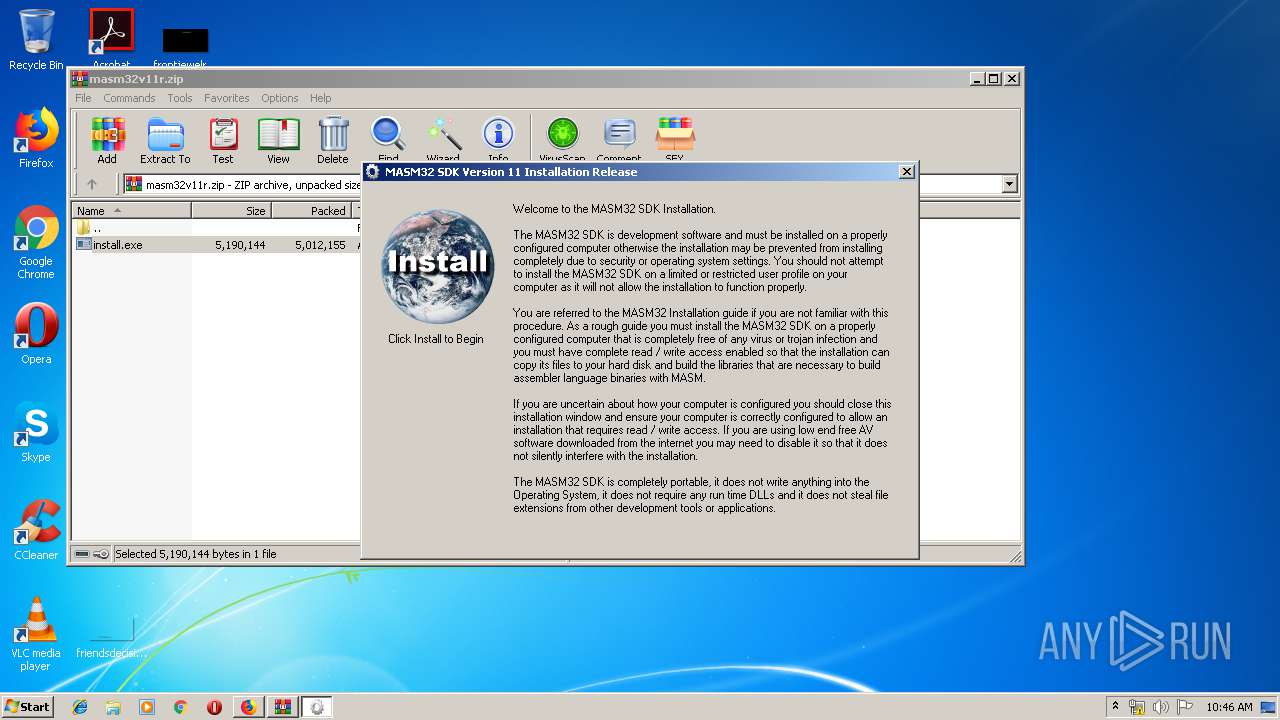
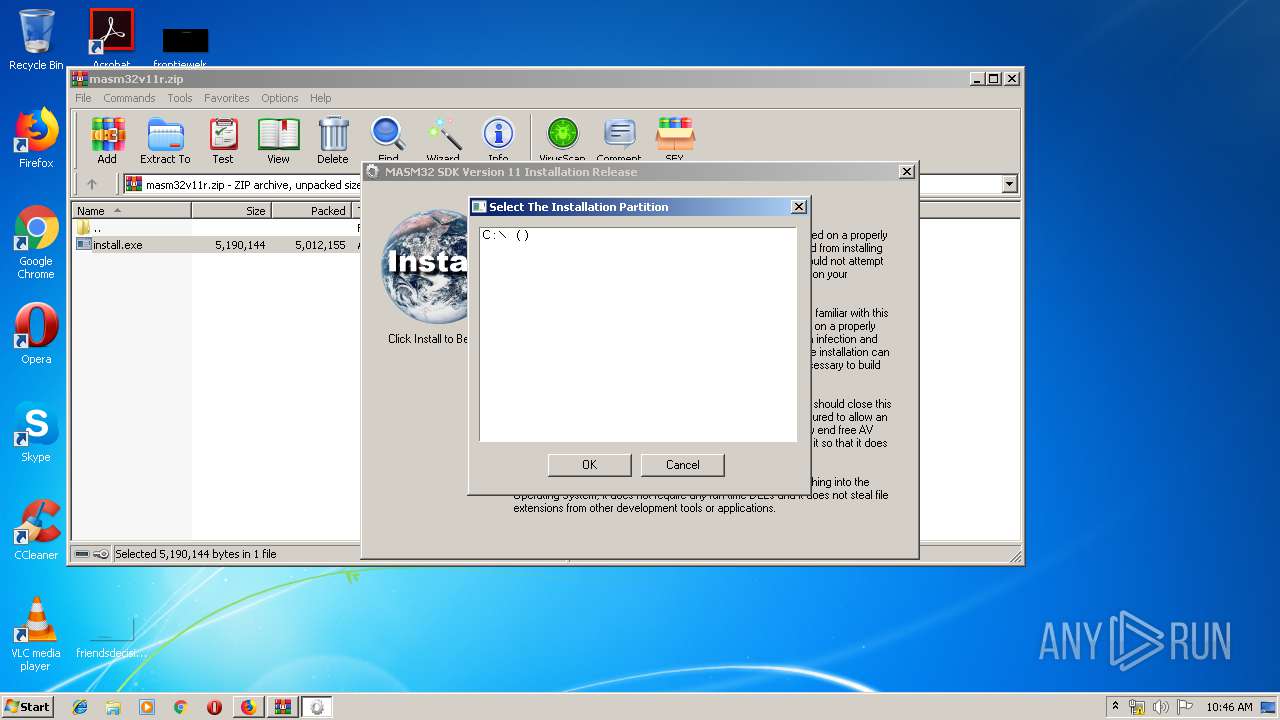
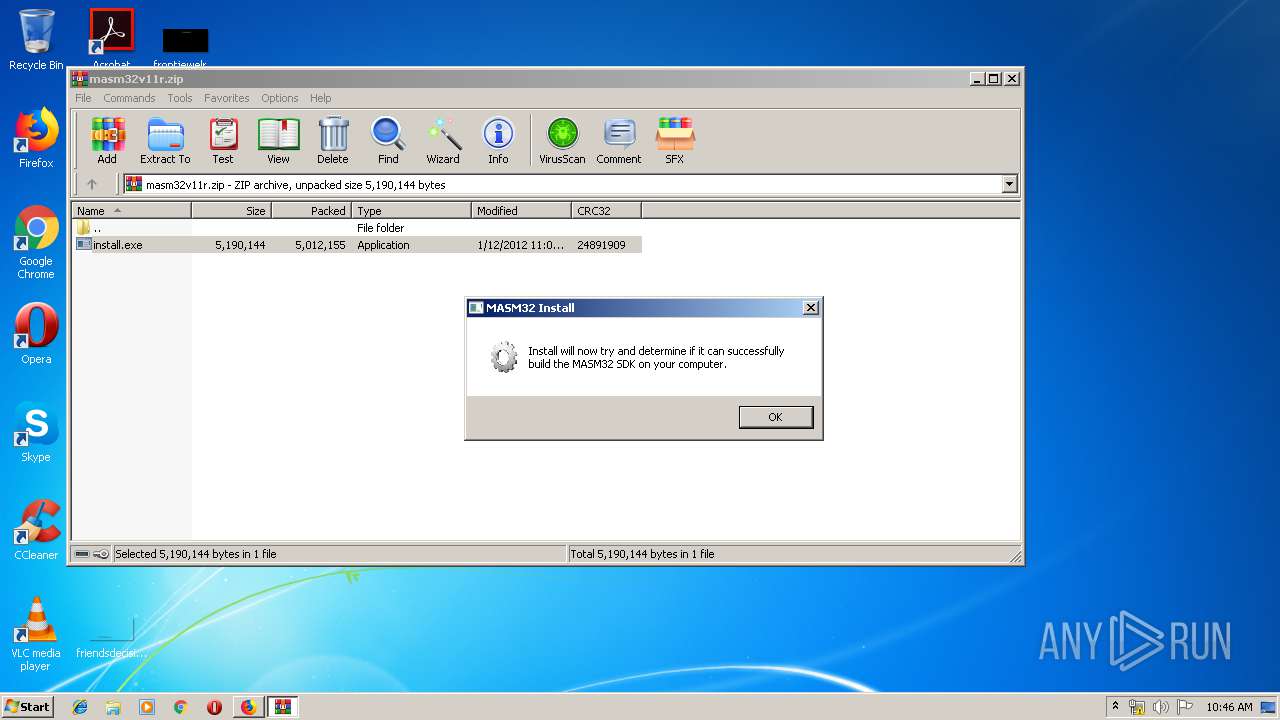
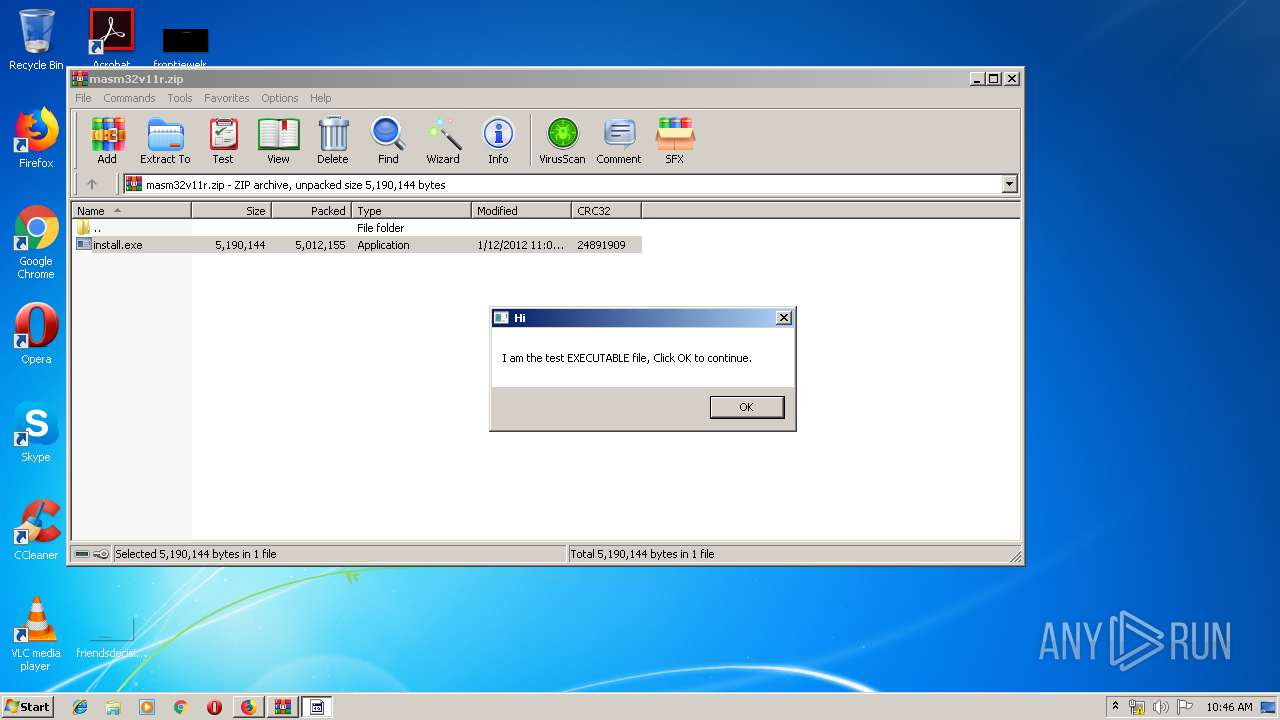
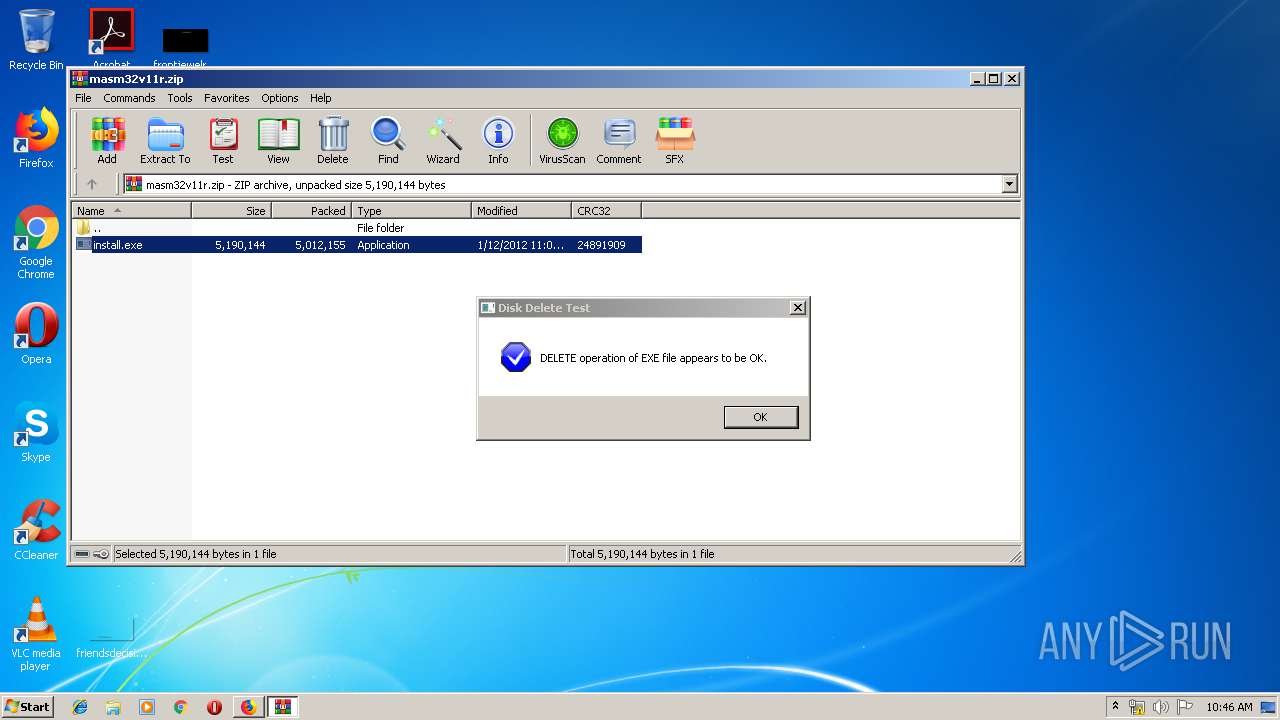
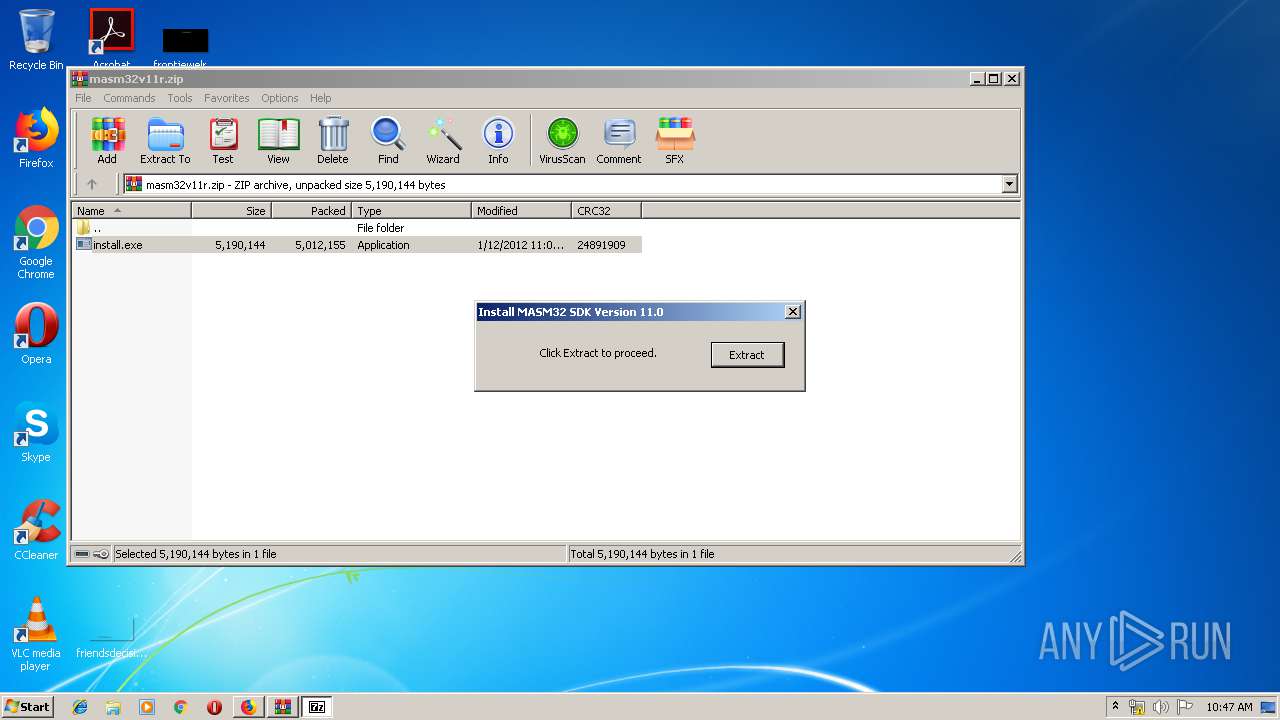
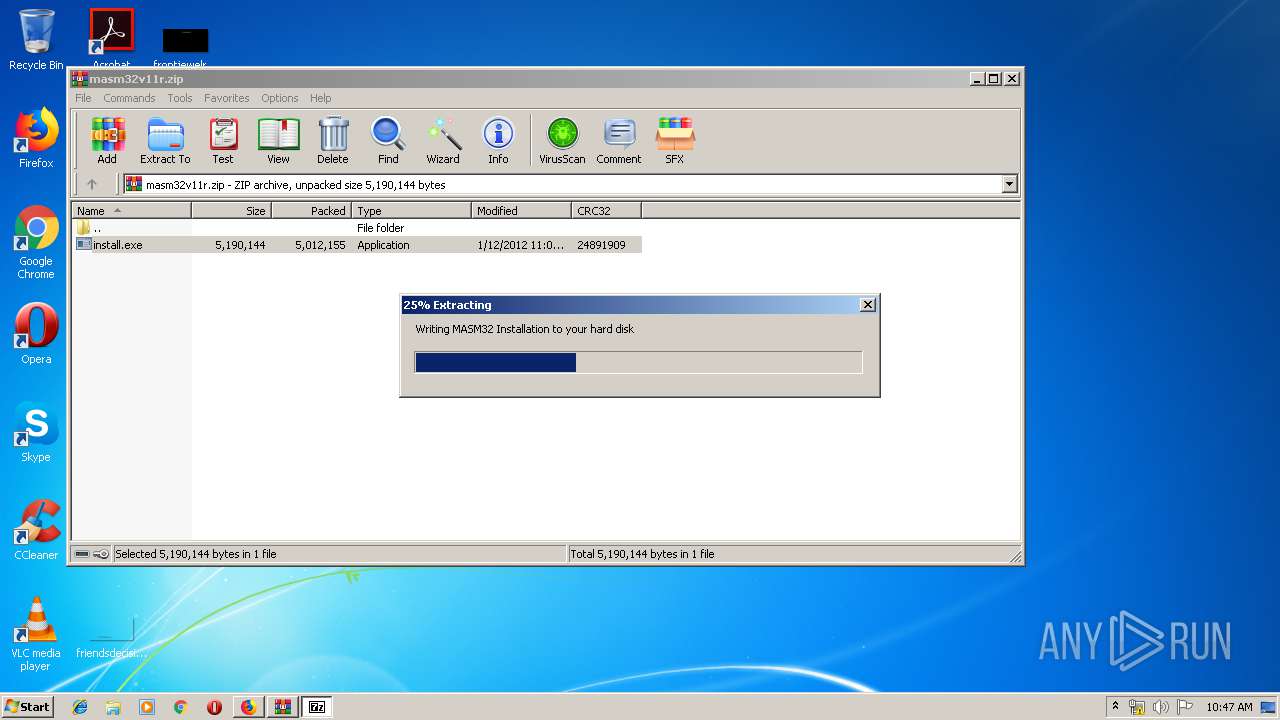
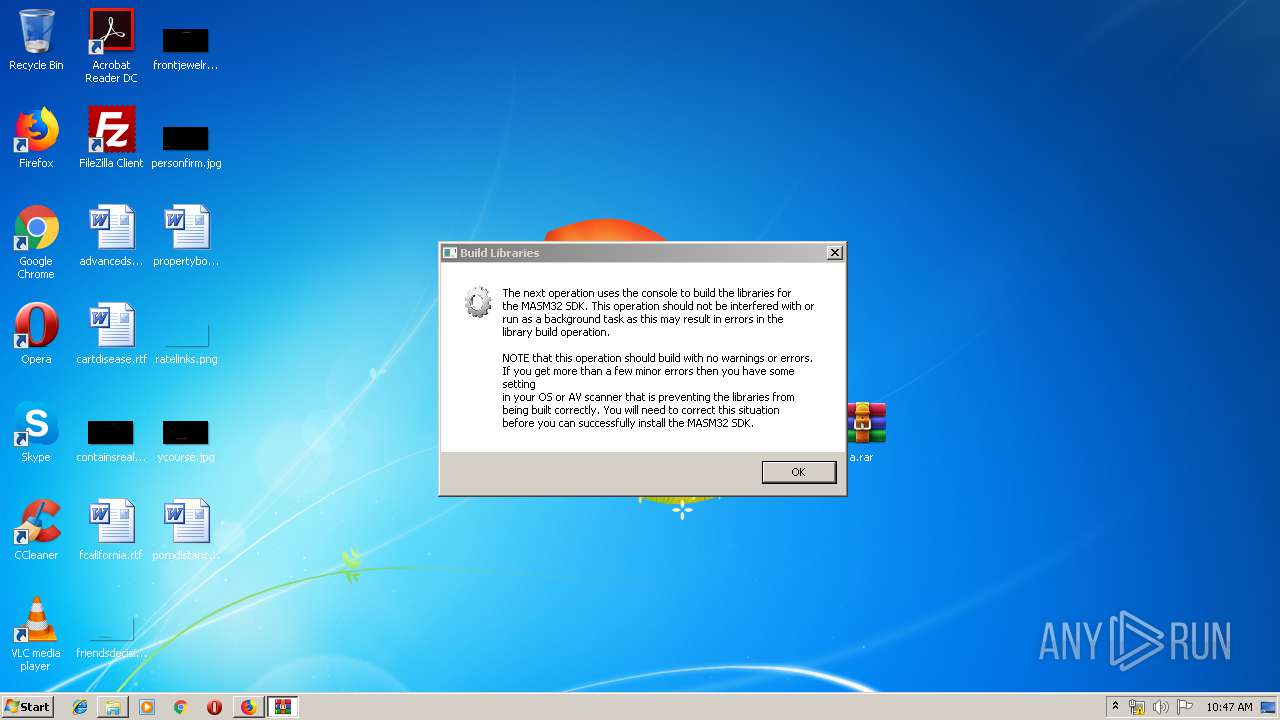
| URL: | http://website.assemblercode.com/masm32/masm32v11r.zip |
| Full analysis: | https://app.any.run/tasks/a03bedf6-e011-41e9-9949-a0156380175b |
| Verdict: | Malicious activity |
| Analysis date: | July 23, 2019, 09:46:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 804CC19D00DB89E520EB91272A4446B1 |
| SHA1: | 9226B0097072BDDC3D5E665A317A655C86EE5C80 |
| SHA256: | 0F95C22C104A423522A2A3E5CE83D1680493BBD233C3C2315E0DC09E40B3E310 |
| SSDEEP: | 3:N1KJA2SWyaAtIza1qrU:CO2BA6O1qU |
MALICIOUS
Application was dropped or rewritten from another process
- masm32ci.exe (PID: 3724)
- tstexe.exe (PID: 3296)
- install.exe (PID: 3196)
- install.exe (PID: 2304)
Loads dropped or rewritten executable
- Link.exe (PID: 1704)
- Link.exe (PID: 2296)
- Link.exe (PID: 1472)
- Link.exe (PID: 3808)
- Link.exe (PID: 1764)
- Link.exe (PID: 3308)
- Link.exe (PID: 2024)
- Link.exe (PID: 608)
- Link.exe (PID: 4052)
- Link.exe (PID: 2316)
- Link.exe (PID: 2160)
- Link.exe (PID: 2856)
- Link.exe (PID: 3676)
- Link.exe (PID: 3116)
- Link.exe (PID: 4036)
- Link.exe (PID: 3636)
- Link.exe (PID: 1752)
- Link.exe (PID: 3356)
- Link.exe (PID: 1640)
- Link.exe (PID: 3308)
- Link.exe (PID: 3976)
- Link.exe (PID: 3036)
- Link.exe (PID: 4020)
- Link.exe (PID: 2296)
- Link.exe (PID: 3488)
- Link.exe (PID: 2484)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1736)
- install.exe (PID: 2304)
- Link.exe (PID: 3308)
- masm32ci.exe (PID: 3724)
Application launched itself
- Link.exe (PID: 2024)
Starts CMD.EXE for commands execution
- install.exe (PID: 2304)
INFO
Application launched itself
- firefox.exe (PID: 3760)
Creates files in the user directory
- firefox.exe (PID: 3760)
Reads CPU info
- firefox.exe (PID: 3760)
Manual execution by user
- explorer.exe (PID: 3112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
111
Monitored processes
69
Malicious processes
1
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
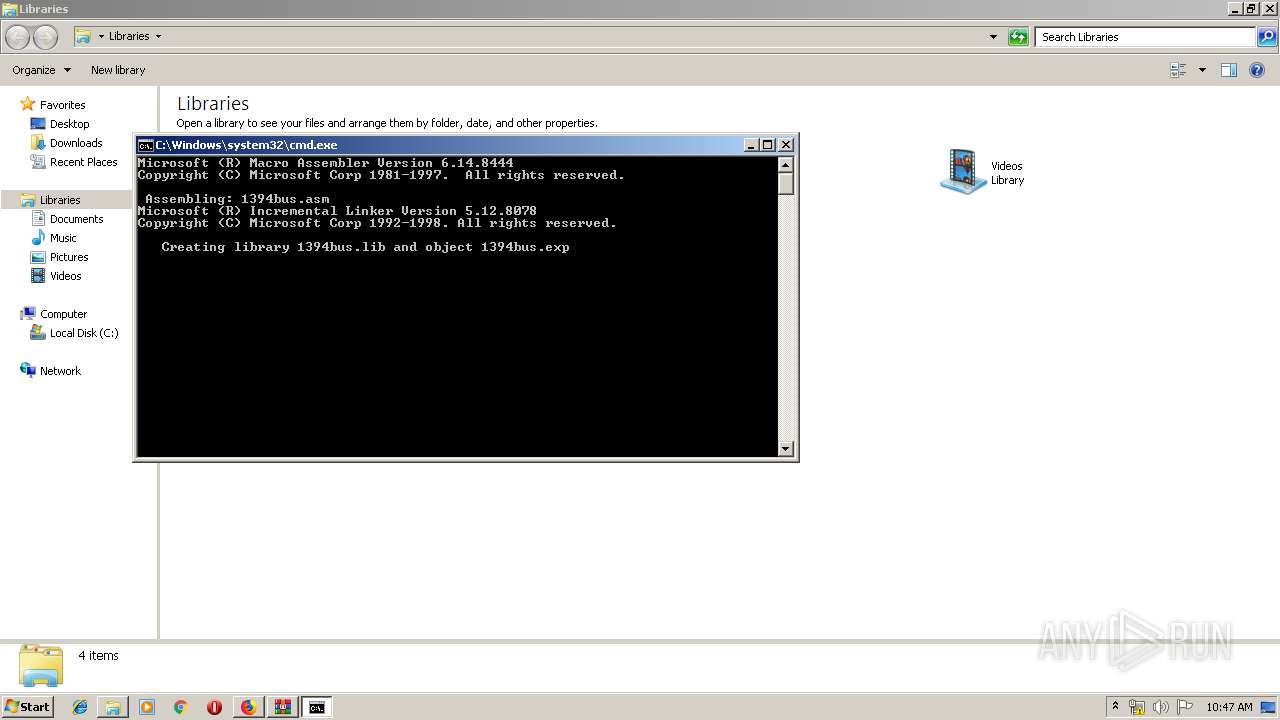
| 540 | \masm32\bin\ml /c /coff acpisim.asm | C:\masm32\bin\ml.exe | — | inc2l.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 608 | "C:\masm32\bin\Link.exe" /lib @"C:\Users\admin\AppData\Local\Temp\lahB198.tmp" | C:\masm32\bin\Link.exe | — | Link.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) Incremental Linker Exit code: 0 Version: 5.012.8078.0 Modules
| |||||||||||||||
| 1324 | \masm32\bin\ml /c /coff advapip.asm | C:\masm32\bin\ml.exe | — | inc2l.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1440 | \masm32\bin\ml /c /coff authz.asm | C:\masm32\bin\ml.exe | — | inc2l.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 1472 | "C:\masm32\bin\Link.exe" /lib @"C:\Users\admin\AppData\Local\Temp\lahC1B5.tmp" | C:\masm32\bin\Link.exe | — | Link.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) Incremental Linker Exit code: 0 Version: 5.012.8078.0 Modules
| |||||||||||||||
| 1636 | \masm32\bin\ml /c /coff asycfilt.asm | C:\masm32\bin\ml.exe | — | inc2l.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1640 | \masm32\bin\Link /SUBSYSTEM:WINDOWS /DLL /DEF:asycfilt.def asycfilt.obj | C:\masm32\bin\Link.exe | — | inc2l.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) Incremental Linker Exit code: 0 Version: 5.012.8078.0 Modules
| |||||||||||||||
| 1668 | inc2l authz.inc | C:\masm32\include\inc2l.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 1704 | "C:\masm32\bin\Link.exe" /lib @"C:\Users\admin\AppData\Local\Temp\lahC3A9.tmp" | C:\masm32\bin\Link.exe | — | Link.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) Incremental Linker Exit code: 0 Version: 5.012.8078.0 Modules
| |||||||||||||||
| 1708 | inc2l advapip.inc | C:\masm32\include\inc2l.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 609
Read events
1 589
Write events
20
Delete events
0
Modification events
| (PID) Process: | (3760) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 0000000000000000 | |||
| (PID) Process: | (3760) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3760) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000078000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3760) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3760) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3760) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (1736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1736) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\masm32v11r.zip | |||
Executable files
60
Suspicious files
74
Text files
1 810
Unknown types
105
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3760 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3760 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3760 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\pluginreg.dat.tmp | — | |
MD5:— | SHA256:— | |||
| 3760 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3760 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3760 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3760 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3760 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3760 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | — | |
MD5:— | SHA256:— | |||
| 3760 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
20
DNS requests
45
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3760 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3760 | firefox.exe | POST | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 471 b | whitelisted |
3760 | firefox.exe | POST | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 471 b | whitelisted |
3760 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3760 | firefox.exe | GET | 200 | 65.254.250.106:80 | http://website.assemblercode.com/masm32/masm32v11r.zip | US | compressed | 4.78 Mb | malicious |
3760 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3760 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3760 | firefox.exe | GET | 200 | 2.16.186.112:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3760 | firefox.exe | 2.16.186.112:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
3760 | firefox.exe | 65.254.250.106:80 | website.assemblercode.com | The Endurance International Group, Inc. | US | malicious |
3760 | firefox.exe | 54.186.90.148:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3760 | firefox.exe | 99.86.1.62:443 | snippets.cdn.mozilla.net | AT&T Services, Inc. | US | unknown |
3760 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3760 | firefox.exe | 35.160.103.71:443 | push.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3760 | firefox.exe | 172.217.22.106:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3760 | firefox.exe | 54.190.222.97:443 | search.services.mozilla.com | Amazon.com, Inc. | US | malicious |
3760 | firefox.exe | 172.217.16.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3760 | firefox.exe | 172.217.22.46:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
website.assemblercode.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
location.services.mozilla.com |
| whitelisted |
locprod1-elb-eu-west-1.prod.mozaws.net |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
drcwo519tnci7.cloudfront.net |
| shared |