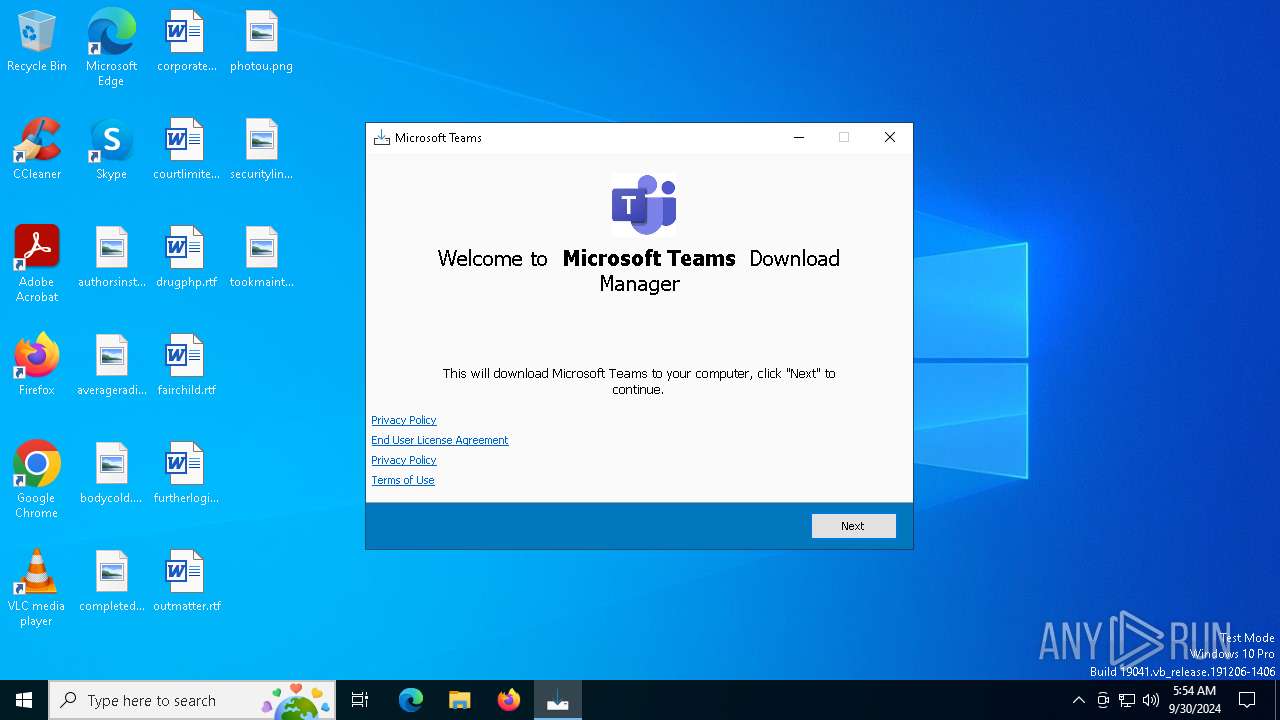
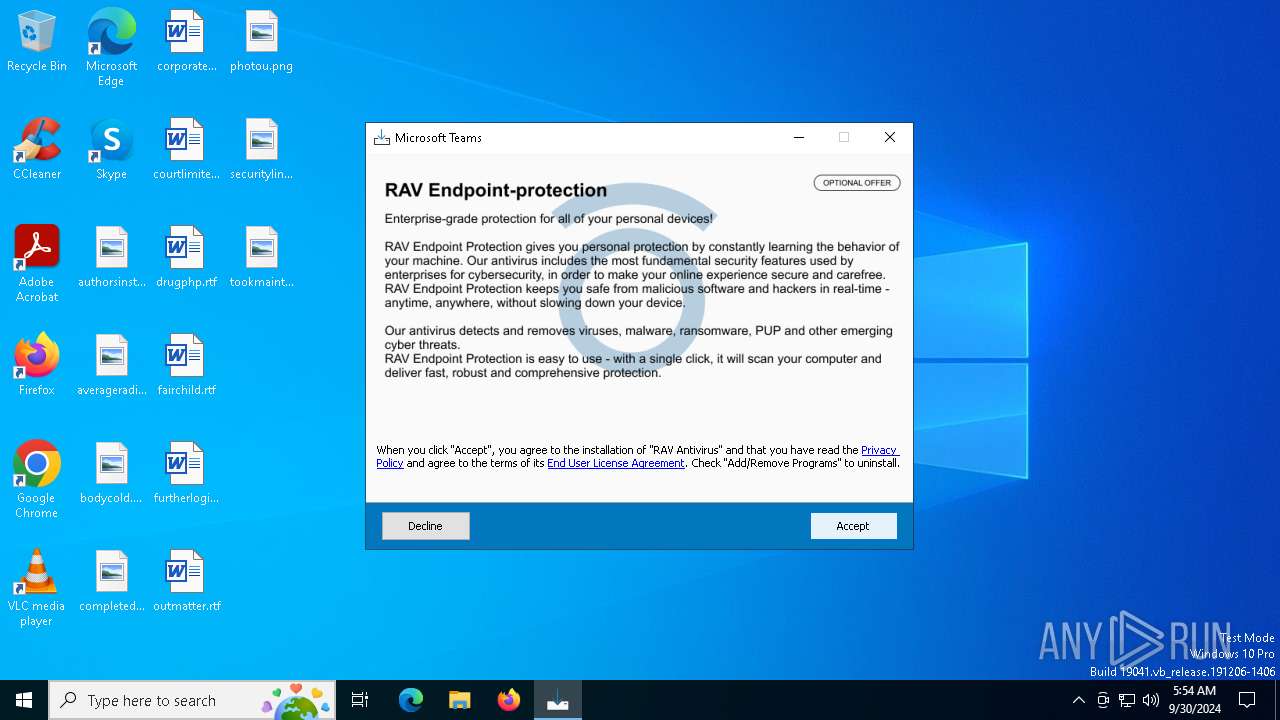
| File name: | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.exe |
| Full analysis: | https://app.any.run/tasks/7b00f107-3d3d-4b84-9270-ddf6f77329ad |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2024, 05:54:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6766745AD3B385FC232E44D92DD29541 |
| SHA1: | D46D57D2CBC6C26E1202082C6C1867EB9C3DFCE7 |
| SHA256: | 0F8DDF8788968309F3E65DD0F2547E8C7B13C7AE2AFABA17AE2E3E4EDD8120C8 |
| SSDEEP: | 49152:37HecD4dnbibBl3QMKQMFCo2nChOlLLEDobS/KzEeIQ5aDMbgSWjN9wA1F5bNMEx:r+cD4dnsQ3oo2kOlLTbSi0Q5aMNWvf1k |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- UnifiedStub-installer.exe (PID: 6664)
- microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp (PID: 3832)
- 5hddlerq.exe (PID: 5280)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 6664)
Executes as Windows Service
- rsSyncSvc.exe (PID: 2376)
- rsWSC.exe (PID: 2532)
- rsClientSvc.exe (PID: 240)
- rsEngineSvc.exe (PID: 4648)
Executable content was dropped or overwritten
- component0.exe (PID: 1072)
- microsoft-teams-24231.512.3106.6573-installer_GREH-c1.exe (PID: 2868)
- 5hddlerq.exe (PID: 5280)
- UnifiedStub-installer.exe (PID: 6664)
- microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp (PID: 3832)
- microsoft-teams-24231.512.3106.6573-installer_GREH-c1.exe (PID: 4840)
Drops 7-zip archiver for unpacking
- UnifiedStub-installer.exe (PID: 6664)
The process drops C-runtime libraries
- UnifiedStub-installer.exe (PID: 6664)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 6664)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 6664)
Reads security settings of Internet Explorer
- microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp (PID: 2808)
INFO
Create files in a temporary directory
- microsoft-teams-24231.512.3106.6573-installer_GREH-c1.exe (PID: 4840)
Checks supported languages
- microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp (PID: 2808)
- microsoft-teams-24231.512.3106.6573-installer_GREH-c1.exe (PID: 4840)
Reads the computer name
- microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp (PID: 2808)
Process checks computer location settings
- microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp (PID: 2808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
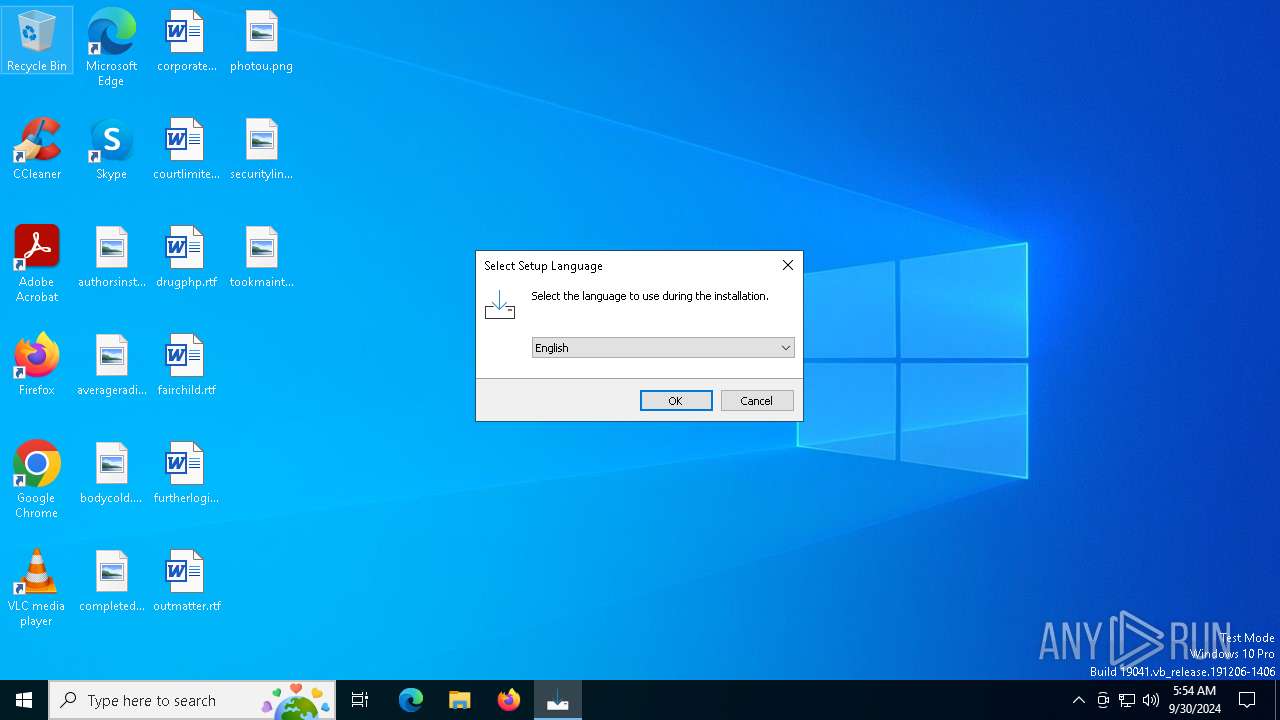
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.40.1.8969 |
| ProductVersionNumber: | 2.40.1.8969 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Softonic International SA |
| FileVersion: | 2.40.1.8969 |
| LegalCopyright: | ©2023 Softonic International SA |
| OriginalFileName: | |
| ProductName: | Softonic International SA |
| ProductVersion: | 3.1.5.7 |
Total processes
157
Monitored processes
29
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\ReasonLabs\EPP\rsClientSvc.exe" | C:\Program Files\ReasonLabs\EPP\rsClientSvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Reason Software Company Inc. Integrity Level: SYSTEM Description: Reason Client Service Version: 5.40.0 Modules
| |||||||||||||||
| 512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wevtutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\AppData\Local\Temp\is-T11ER.tmp\component0.exe" -ip:"dui=bb926e54-e3ca-40fd-ae90-2764341e7792&dit=20240930055425&is_silent=true&oc=ZB_RAV_Cross_Solo_Soft&p=fa70&a=100&b=&se=true" -i | C:\Users\admin\AppData\Local\Temp\is-T11ER.tmp\component0.exe | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp | ||||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: rsStubActivator Version: 1.6.1.0 Modules
| |||||||||||||||
| 1256 | "C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe" -i -bn:ReasonLabs -pn:EPP -lpn:rav_antivirus -url:https://update.reasonsecurity.com/v2/live -dt:10 | C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe | — | UnifiedStub-installer.exe | |||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: Reason Security Synchronize Service Exit code: 0 Version: 1.8.5.0 Modules
| |||||||||||||||
| 1344 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | "C:\WINDOWS\system32\rundll32.exe" setupapi.dll,InstallHinfSection DefaultInstall 128 C:\Program Files\ReasonLabs\EPP\x64\rsKernelEngine.inf | C:\Windows\System32\rundll32.exe | — | UnifiedStub-installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fltMC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1772 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wevtutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2128 | "C:\WINDOWS\system32\wevtutil.exe" im C:\Program Files\ReasonLabs\EPP\x64\rsKernelEngineEvents.xml | C:\Windows\System32\wevtutil.exe | — | UnifiedStub-installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Eventing Command Line Utility Exit code: 87 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 221
Read events
22 068
Write events
110
Delete events
43
Modification events
| (PID) Process: | (1072) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1072) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1072) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1072) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1072) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1072) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1072) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1072) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1072) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1072) component0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\component0_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
494
Suspicious files
88
Text files
29
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4840 | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.exe | C:\Users\admin\AppData\Local\Temp\is-8QCK3.tmp\microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp | executable | |
MD5:86BC259E1FFB8E8DC057D5BE74F631DD | SHA256:829DCCEA375271A0AB90E2A1F6C213690EE3B7535C107D98DE4FF394C005CEB1 | |||
| 3832 | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp | C:\Users\admin\AppData\Local\Temp\is-T11ER.tmp\Y.png | image | |
MD5:C199687E52F7393C941A143B45D78207 | SHA256:0EB767424750B6F8C22AE5EBB105C5C37B3A047EED986FFA6DEBA53EFDC2142E | |||
| 3832 | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp | C:\Users\admin\AppData\Local\Temp\is-T11ER.tmp\image.jpg | image | |
MD5:52B1F009D53EEDFBD908065B2B103C5A | SHA256:BE226FE7A2530E3412A361C54976B1AD58322B112F7F5C5B98FF8C1F62941118 | |||
| 3832 | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp | C:\Users\admin\AppData\Local\Temp\is-T11ER.tmp\100.png | image | |
MD5:4167C79312B27C8002CBEEA023FE8CB5 | SHA256:C3BF350627B842BED55E6A72AB53DA15719B4F33C267A6A132CB99FF6AFE3CD8 | |||
| 2868 | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.exe | C:\Users\admin\AppData\Local\Temp\is-S80FO.tmp\microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp | executable | |
MD5:86BC259E1FFB8E8DC057D5BE74F631DD | SHA256:829DCCEA375271A0AB90E2A1F6C213690EE3B7535C107D98DE4FF394C005CEB1 | |||
| 3832 | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp | C:\Users\admin\AppData\Local\Temp\is-T11ER.tmp\N.png | image | |
MD5:1A01027365500D86730A737EB32CBF2A | SHA256:D79A97538B93179012A5EBEBDE873EDC18E30A0287953800F7AA7EA4F25724E1 | |||
| 3832 | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp | C:\Users\admin\AppData\Local\Temp\is-T11ER.tmp\microsoft-teams-24231.512.3106.6573-installer.exe | executable | |
MD5:147D1BEDDBBE5043ABD79D4F6AA0D20B | SHA256:40514E96A27593344604590AC962745B1533F8128D95D1562FF36A60E37698FD | |||
| 3832 | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp | C:\Users\admin\AppData\Local\Temp\is-T11ER.tmp\component0.exe | executable | |
MD5:069A3054CD2E7A3EA3013E1555A70CFC | SHA256:2D0B6AAE644C5FDECCC158E81706281BB0BF595EAE4494D244F547EDEBA4DBD6 | |||
| 5280 | 5hddlerq.exe | C:\Users\admin\AppData\Local\Temp\7zS0A4E0BEF\da-DK\UnifiedStub.resources.dll | executable | |
MD5:C7D53FBA41BBD98B09ADC6370530187D | SHA256:0973897156246245DAFC537D4023FD899E29F65F9AFCCC0049F41BC08138F5F5 | |||
| 3832 | microsoft-teams-24231.512.3106.6573-installer_GREH-c1.tmp | C:\Users\admin\AppData\Local\Temp\is-T11ER.tmp\is-VQG49.tmp | image | |
MD5:52B1F009D53EEDFBD908065B2B103C5A | SHA256:BE226FE7A2530E3412A361C54976B1AD58322B112F7F5C5B98FF8C1F62941118 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
67
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1944 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1944 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6664 | UnifiedStub-installer.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAEllBL0tvuy4gAAAAAAAQ%3D | unknown | — | — | whitelisted |
6664 | UnifiedStub-installer.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBQ0NE46krjtIffEj0l00lckKsLufgQUJEWZoXeQKnzDyoOwbmQWhCr4LGcCEzMAAXxhE9usAbRsOHIAAAABfGE%3D | unknown | — | — | whitelisted |
6664 | UnifiedStub-installer.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ID%20Verified%20CS%20AOC%20CA%2002.crl | unknown | — | — | whitelisted |
5760 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6664 | UnifiedStub-installer.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTDHsfuqfubd3pihvq4mgQVWgHWNwQUyH7SaoUqG8oZmAQHJ89QEE9oqKICEzMAAAAHh6M0o3uljhwAAAAAAAc%3D | unknown | — | — | whitelisted |
6664 | UnifiedStub-installer.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Public%20RSA%20Timestamping%20CA%202020.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7108 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1768 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
d25qho5rs4tpl0.cloudfront.net |
| whitelisted |
images.sftcdn.net |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
Process | Message |
|---|---|
rsEngineSvc.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ReasonLabs\EPP\x64\SQLite.Interop.dll"...
|