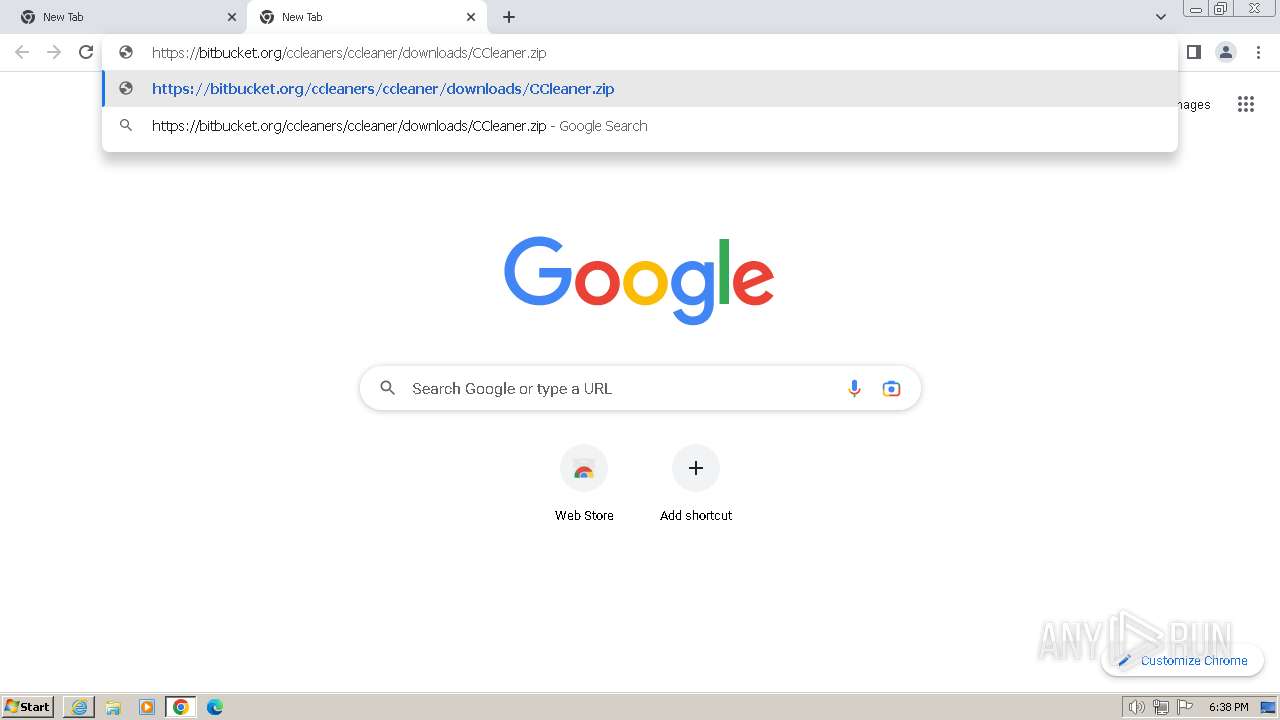
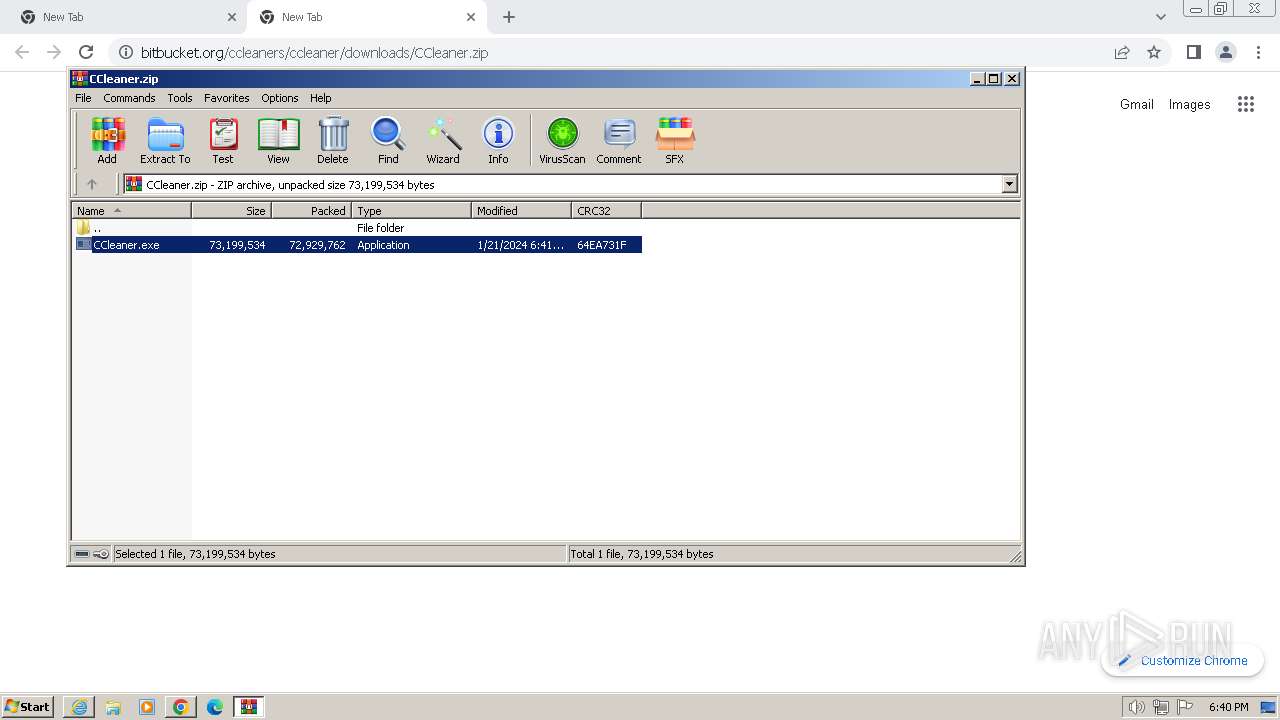
| URL: | https://bitbucket.org/ccleaners/ccleaner/downloads/CCleaner.zip |
| Full analysis: | https://app.any.run/tasks/28ce629e-ed17-4535-8cb1-3a0af3741fe7 |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2024, 18:37:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 371E3EBBF2628043FFFA1E69B4798738 |
| SHA1: | B39561B646B3A81D10C1B0FBC6AB86633323FB05 |
| SHA256: | 0F8A9A8E4832700467095EE4F0B86F8A37248404B93631599EECC9856F8D1E34 |
| SSDEEP: | 3:N8J+RoCJUTaJLJ4KRF:2J+rFhf |
MALICIOUS
Drops the executable file immediately after the start
- CCleaner.exe (PID: 2508)
Steals credentials from Web Browsers
- CCleaner.exe (PID: 2508)
- taskhost.exe (PID: 4064)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 2508)
SUSPICIOUS
Reads the Internet Settings
- CCleaner.exe (PID: 1812)
- CCleaner.exe (PID: 2508)
- taskhost.exe (PID: 4064)
Application launched itself
- CCleaner.exe (PID: 1812)
Reads Internet Explorer settings
- CCleaner.exe (PID: 2508)
Checks Windows Trust Settings
- CCleaner.exe (PID: 2508)
Executable content was dropped or overwritten
- CCleaner.exe (PID: 2508)
Reads security settings of Internet Explorer
- CCleaner.exe (PID: 2508)
Reads settings of System Certificates
- CCleaner.exe (PID: 2508)
Executes as Windows Service
- taskhost.exe (PID: 4064)
Reads browser cookies
- CCleaner.exe (PID: 2508)
Searches for installed software
- CCleaner.exe (PID: 2508)
INFO
Application launched itself
- iexplore.exe (PID: 2044)
- chrome.exe (PID: 1316)
Reads the computer name
- CCleaner.exe (PID: 1812)
- CCleaner.exe (PID: 2508)
- CCleanerBugReport.exe (PID: 316)
Manual execution by a user
- chrome.exe (PID: 1316)
Checks supported languages
- CCleaner.exe (PID: 1812)
- CCleaner.exe (PID: 2508)
- CCleanerBugReport.exe (PID: 316)
- wa_3rd_party_host_32.exe (PID: 3448)
The process uses the downloaded file
- chrome.exe (PID: 3660)
- WinRAR.exe (PID: 3804)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3804)
- chrome.exe (PID: 3372)
Reads Environment values
- CCleaner.exe (PID: 1812)
- CCleaner.exe (PID: 2508)
Reads the machine GUID from the registry
- CCleaner.exe (PID: 2508)
- CCleanerBugReport.exe (PID: 316)
Reads CPU info
- CCleaner.exe (PID: 2508)
- CCleanerBugReport.exe (PID: 316)
Reads product name
- CCleaner.exe (PID: 2508)
Create files in a temporary directory
- CCleaner.exe (PID: 2508)
Creates files or folders in the user directory
- CCleaner.exe (PID: 2508)
- taskhost.exe (PID: 4064)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3804)
- chrome.exe (PID: 3372)
Checks proxy server information
- CCleaner.exe (PID: 2508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
77
Monitored processes
34
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2044 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 316 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3804.41028\x86\CCleanerBugReport.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3804.41028\x86\CCleanerBugReport.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Piriform Software Integrity Level: MEDIUM Description: CCleaner Bug Report Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=3656 --field-trial-handle=1172,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1196 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3352 --field-trial-handle=1172,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1812 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3804.36043\CCleaner.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3804.36043\CCleaner.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 1880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2108 --field-trial-handle=1172,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e298b38,0x6e298b48,0x6e298b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://bitbucket.org/ccleaners/ccleaner/downloads/CCleaner.zip" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1112 --field-trial-handle=1172,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
30 154
Read events
29 766
Write events
331
Delete events
57
Modification events
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
316
Suspicious files
141
Text files
74
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C31B2498754E340573F1336DE607D619 | binary | |
MD5:B54F58D139201BB3A3909916DA6630C2 | SHA256:0F74ECFDE363B2DB5A7A5291D76A7CE15DAC938EE55EDEADCB4254FBF5DA3C69 | |||
| 1316 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFe1de4.TMP | — | |
MD5:— | SHA256:— | |||
| 1316 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:93C502C08F33B5884BD3D49DDEE0610C | SHA256:6A0C43D1AE4CE21D52CC2E42E26D421E308AF1D9722CE32E136BA8C841C33E35 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:509DD68B3F1B9DE153B413A7DF9F92DD | SHA256:6FAAC50DA3A987AEA44F7DA55C01AC3AB245512C46DF4D88249A1195F9190E2D | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:9ECFB5FBBD3AE270A4054CC1B2155E20 | SHA256:E3D4138CF82ADB452F509A85119B081C307AB29560A4D27A644D2238495F3F08 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:4E5EEEF781875B0149643A0D7360BFA3 | SHA256:FBA12918E5AA8BDD3ED2D4C3E9614E794703356236825924CCD7F88E59AC4865 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D03E46CD585BBE111C712E6577BC5F07_95A4562DEA3FE449C14A6BEBAD97C213 | binary | |
MD5:ACE7AF22F7795BB897C03CD0E723DCF3 | SHA256:52F7D54F0B7BBFAE852F2928ABB9946324217B699FEDCE75E8737B4C0095AAA1 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:BC62B7EF2A63881E6E61BCD98E02D200 | SHA256:807FDCE9E42A1789265C9AE2FFCB97EE298413CA3B6BEB17216E6CA1CFDF8423 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
75
TCP/UDP connections
60
DNS requests
62
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2044 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
2044 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2044 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 5.55 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 9.99 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 9.63 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 10.1 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 45.1 Kb | unknown |
296 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?16e53a13f7f2d96f | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
296 | iexplore.exe | 104.192.141.1:443 | bitbucket.org | AMAZON-02 | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
296 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
296 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
296 | iexplore.exe | 52.216.179.235:443 | bbuseruploads.s3.amazonaws.com | AMAZON-02 | US | unknown |
296 | iexplore.exe | 18.239.15.192:80 | o.ss2.us | — | US | unknown |
296 | iexplore.exe | 52.84.193.90:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | unknown |
296 | iexplore.exe | 18.238.246.206:80 | ocsp.r2m01.amazontrust.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bitbucket.org |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
bbuseruploads.s3.amazonaws.com |
| shared |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m01.amazontrust.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
Threats
Process | Message |
|---|---|
CCleaner.exe | [2024-01-22 18:41:22.260] [error ] [settings ] [ 2508: 2836] [000000: 0] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | [2024-01-22 18:41:22.260] [error ] [ini_access ] [ 2508: 2836] [000000: 0] Incorrect ini_accessor configuration! Fixing relative input path to avoid recursion. Input was: Setup
|
CCleaner.exe | Failed to open log file 'C:\Users\admin\AppData\Local\Temp\Rar$EXa3804.36043' |
CCleaner.exe | [2024-01-22 18:41:22.573] [error ] [lil ] [ 2508: 2836] [000000: 0] ~/ZIeepDOOIKB77M+twVIhby3C3qK2j6Oz+zmOa0CQcL9uBZwmdU5goHtryC7RQ==
|
CCleaner.exe | [2024-01-22 18:41:22.573] [error ] [LifBurger ] [ 2508: 2836] [000000: 0] Failed to send burger event
Exception: Event Manager: Using of uninitialized Global event manager
|
CCleaner.exe | [2024-01-22 18:41:22.573] [error ] [lil ] [ 2508: 2836] [000000: 0] ~sroNZ9z+MoTE+7IlsQUVhZu1Fn+Z32qTzquhKapLScyxsV9kjtI+goH/ryG7Swjm54gqYJnJObvA76slsDdu1a2QHmed5waIwuqqEIoOQtWBhh5h2P4ShpKz9njwWBmV6ecjUL/XL4bP7rRisgJMgtf0XzPcm2rHgavmbP5LD4X99F8z3Jtqx4Gr5mz+Sw+F/fRfM9ybaseBq+Zs/ksPhf30XzPcm2rHgavmbP5LD4X9lxB3mYFq19m79nzuWx+V7/RXIdU=
|
CCleaner.exe | [2024-01-22 18:41:22.573] [error ] [LifBurger ] [ 2508: 2836] [000000: 0] Failed to send burger event
Exception: Event Manager: Using of uninitialized Global event manager
|
CCleaner.exe | [2024-01-22 18:41:22.573] [error ] [lil ] [ 2508: 2836] [000000: 0] ~/ZEHcJnLPo7O5fxsmApGybiwX2eTmy2C1augJbIOD9KvvQt23M8jisSr4Q/kN3rWuKYMT53fJ47P14c8ri9O0byIM3yf2ia79e6rPII5Ttf5kSdyz4N604+48HzqWHPmnrgacpLeOMnN4qVr1EsPhf30XzPcm2rHgavmbP5LD4X99F8z3Jtqx4Gr5mz+Sw+F/fRfM9ybaseBq+Zs/ksPhf30XzPcm2rHgavmbP4oQMG47l8jhIt615G79nzsSweX9A==
|
CCleaner.exe | [2024-01-22 18:41:22.573] [error ] [lil ] [ 2508: 2836] [000000: 0] ~tbUNZdz+MoTE+7IlsQUVhZu1Fn+Z32qTzquhKapLScyxsV9kjtI+goH/ryG7Swjm54gqYJnJObvA76slsDdu1a2QHmed5waIwuqqEIoOQtWBhh5h2P4ShpKz9njwWBmV6ecjUL/XL4bP7rRisgJMgtf0XzPcm2rHgavmbP5LD4X99F8z3Jtqx4Gr5mz+Sw+F/fRfM9ybaseBq+Zs/ksPhf30XzPcm2rHgavmbP5LD4X9lxB3mYFq19m79nzuWx+V7/RXIdU=
|
CCleaner.exe | [2024-01-22 18:41:22.573] [error ] [lil ] [ 2508: 2836] [000000: 0] ~/ZEHcJnLPo7O5fxsmApGybiwX2eTmy2C1augJbIOD9KvvQt23M8jisSr4Q/kN3rWuKYMT53fJ47P14c8ri9O0byIM3yf2ia79e6rPII5Ttf5kSdyz4N604+48HzqWHPmnrgacpLeOMnN4qVr1EsPhf30XzPcm2rHgavmbP5LD4X99F8z3Jtqx4Gr5mz+Sw+F/fRfM9ybaseBq+Zs/ksPhf30XzPcm2rHgavmbP4oQMG47l8jhIt615G79nzsSweX9A==
|