| File name: | 328000f8d02f71614704824bc42f33c0N.exe |
| Full analysis: | https://app.any.run/tasks/01778b98-d6db-4aae-9587-e2d2cf5d1533 |
| Verdict: | Malicious activity |
| Analysis date: | July 09, 2024, 08:25:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 328000F8D02F71614704824BC42F33C0 |
| SHA1: | C3FCA145BB2EA19317537BF8DC15AB0D46745D6F |
| SHA256: | 0F5998ABD53DA2B07EAA8681DA8B78C4C67C604E798764AC4E3327D5FA6C4B63 |
| SSDEEP: | 24576:QnWJo7rZhrEHrgrgCyQ94iiTiORKZtB/ksiZdMzPxFh1GuzSgIn0bAPa3Px8dYD:Qn8+gCN4iiTiORiei11C0Wq8dYD |
MALICIOUS
Drops the executable file immediately after the start
- 328000f8d02f71614704824bc42f33c0N.exe (PID: 5932)
XMRIG has been detected (YARA)
- 328000f8d02f71614704824bc42f33c0N.exe (PID: 5932)
SUSPICIOUS
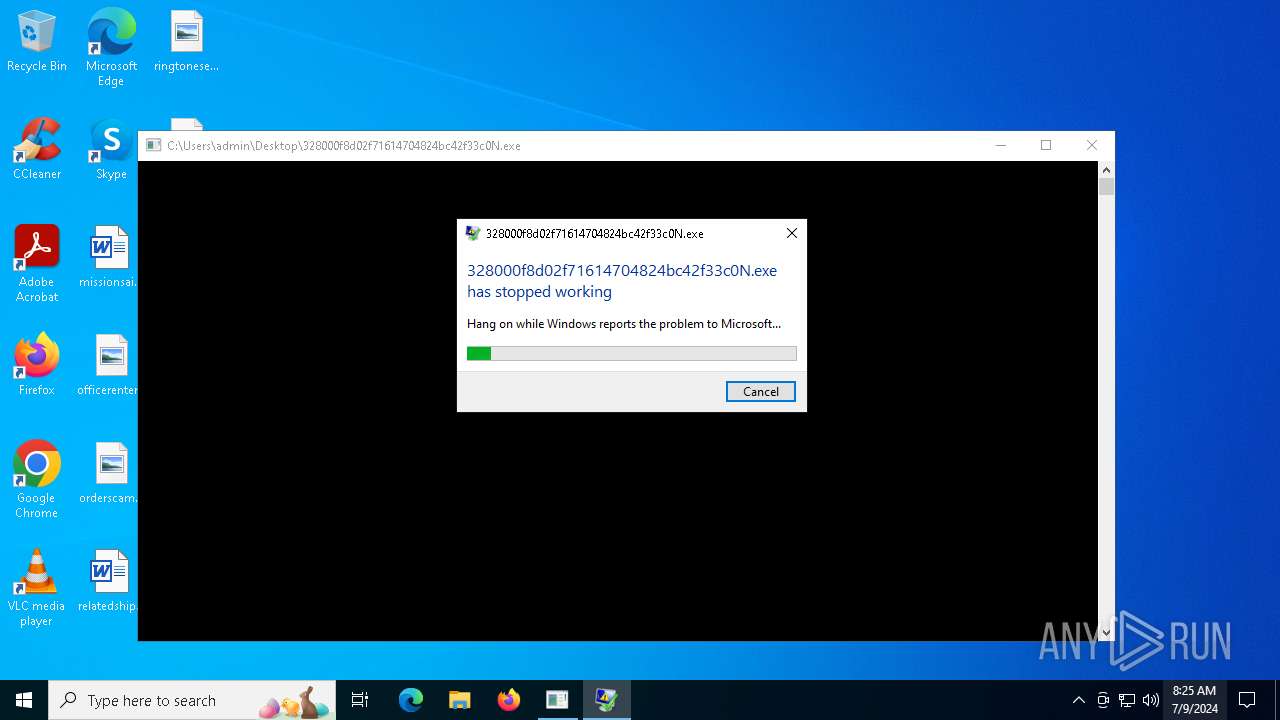
Executes application which crashes
- 328000f8d02f71614704824bc42f33c0N.exe (PID: 5932)
INFO
Checks supported languages
- 328000f8d02f71614704824bc42f33c0N.exe (PID: 5932)
Checks proxy server information
- WerFault.exe (PID: 1496)
Creates files or folders in the user directory
- WerFault.exe (PID: 1496)
Reads the software policy settings
- WerFault.exe (PID: 1496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (53.4) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (35.5) |
| .exe | | | Win32 Executable (generic) (5.8) |
| .exe | | | Generic Win/DOS Executable (2.5) |
| .exe | | | DOS Executable Generic (2.5) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2019:08:29 00:43:41+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.22 |
| CodeSize: | 634368 |
| InitializedDataSize: | 2805760 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9a338 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
128
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1496 | C:\WINDOWS\system32\WerFault.exe -u -p 5932 -s 312 | C:\Windows\System32\WerFault.exe | 328000f8d02f71614704824bc42f33c0N.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 328000f8d02f71614704824bc42f33c0N.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5932 | "C:\Users\admin\Desktop\328000f8d02f71614704824bc42f33c0N.exe" | C:\Users\admin\Desktop\328000f8d02f71614704824bc42f33c0N.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226505 Modules
| |||||||||||||||
Total events
7 655
Read events
7 655
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
1
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1496 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_328000f8d02f7161_1d3596fd16ce4617f5134c9ce9fa11635a5f6b_306ddd82_f0b5a2c5-978c-4340-b643-d4f412bb332a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1496 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERF007.tmp.xml | xml | |
MD5:0541A653B1F2CF23A0AA262BA01D4665 | SHA256:F6C189AFABB1CD2197C1D94CB52632FDD801E130A7324E8BD55457759DEF5CA4 | |||
| 1496 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WEREEDD.tmp.WERInternalMetadata.xml | xml | |
MD5:FD2F941849E4A941622ADF73ADCCE0F0 | SHA256:882F8DF80C0A0ADE51044B4D7A4696BC5587848981A888630369032B5D3652AB | |||
| 1496 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\328000f8d02f71614704824bc42f33c0N.exe.5932.dmp | binary | |
MD5:6EB07BDDB0E70844BE2C554D2DB31F1F | SHA256:BFCEBFD31DF0CD5B817DDA8D8874A82A3A3F761375ED9EB403F62657C177AA1A | |||
| 1496 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WEREDD2.tmp.dmp | dmp | |
MD5:C36CEB62210EAFC043470A07A8953AD9 | SHA256:BA46AC11C54425A7201AAD881EDDB8EC0A73839B76AE5CF3906C2ADFD44126AA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
21
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2056 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
836 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
836 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | POST | 200 | 51.104.15.253:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2056 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1700 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
836 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1496 | WerFault.exe | 20.189.173.21:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2056 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
836 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
836 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2056 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |