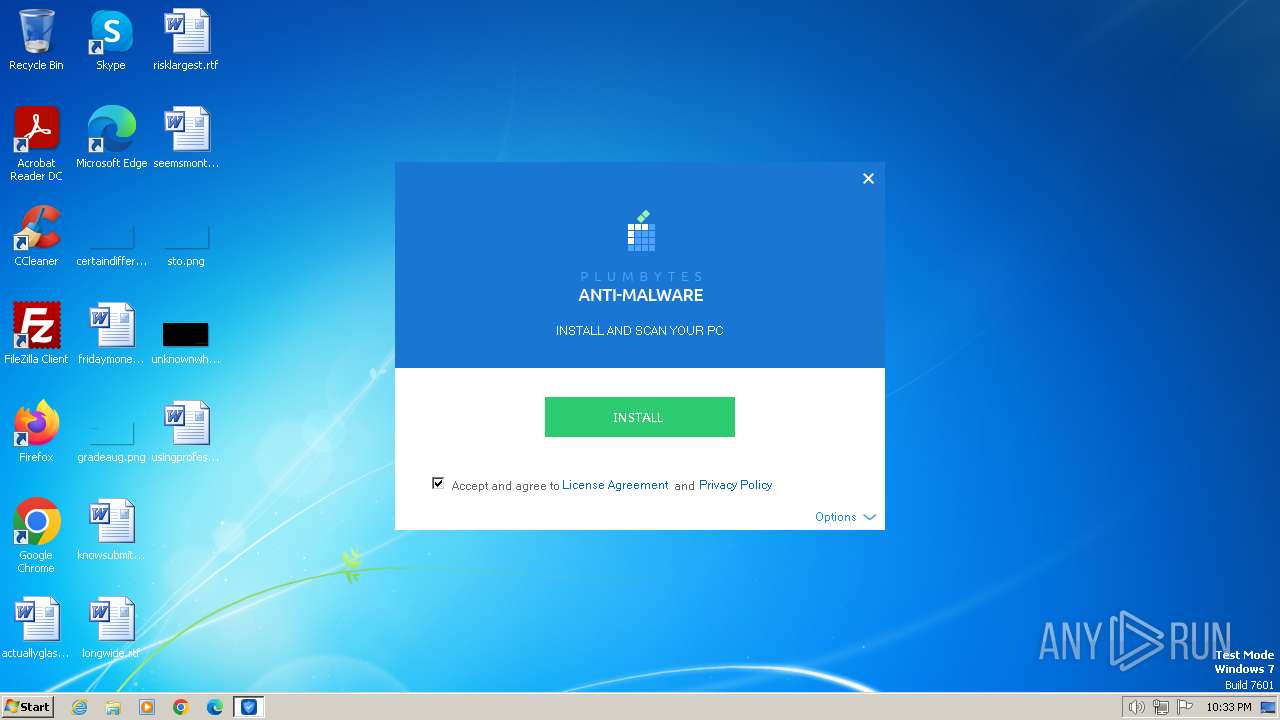
| File name: | antimalwaresetup.exe |
| Full analysis: | https://app.any.run/tasks/8af6095b-6a34-4c37-b7dc-db4df65cb0e5 |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2024, 22:33:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | BFF8D0BAAAFF0E3957C0F474DB79775F |
| SHA1: | 455B90DA5B9FE0577A887DB6D5FDB8EFB09BD9D1 |
| SHA256: | 0F444E679344F8F25BFE8CF16A46FA48CC530E605FDF2D1A5E4A7B60DF75CC75 |
| SSDEEP: | 6144:3hkqLCSglf/uK9/dpzrtKfUPdof923n6wJn4U5q:3hC9WwNReidoAXrn55q |
MALICIOUS
Drops the executable file immediately after the start
- antimalwaresetup.exe (PID: 2840)
SUSPICIOUS
Checks Windows Trust Settings
- Plumbytes.Installer.exe (PID: 3228)
- antimalwaresetup.exe (PID: 2840)
Reads the Internet Settings
- antimalwaresetup.exe (PID: 2840)
- Plumbytes.Installer.exe (PID: 3228)
Reads settings of System Certificates
- Plumbytes.Installer.exe (PID: 3228)
- antimalwaresetup.exe (PID: 2840)
Reads security settings of Internet Explorer
- antimalwaresetup.exe (PID: 2840)
- Plumbytes.Installer.exe (PID: 3228)
Executable content was dropped or overwritten
- antimalwaresetup.exe (PID: 2840)
INFO
Checks supported languages
- antimalwaresetup.exe (PID: 2840)
- Plumbytes.Installer.exe (PID: 3228)
Create files in a temporary directory
- antimalwaresetup.exe (PID: 2840)
Checks proxy server information
- antimalwaresetup.exe (PID: 2840)
Reads the machine GUID from the registry
- Plumbytes.Installer.exe (PID: 3228)
- antimalwaresetup.exe (PID: 2840)
Reads the software policy settings
- Plumbytes.Installer.exe (PID: 3228)
- antimalwaresetup.exe (PID: 2840)
Reads the computer name
- Plumbytes.Installer.exe (PID: 3228)
- antimalwaresetup.exe (PID: 2840)
Creates files or folders in the user directory
- antimalwaresetup.exe (PID: 2840)
Creates files in the program directory
- Plumbytes.Installer.exe (PID: 3228)
Reads Environment values
- Plumbytes.Installer.exe (PID: 3228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:11:21 16:25:29+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 26112 |
| InitializedDataSize: | 188928 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x33ec |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | ASCII |
| CompanyName: | Plumbytes Software |
| FileDescription: | Plumbytes Anti-Malware |
| FileVersion: | 1.0.0.1 |
| LegalCopyright: | Copyright Plumbytes Software |
| ProductName: | Plumbytes Anti-Malware |
Total processes
45
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2840 | "C:\Users\admin\AppData\Local\Temp\antimalwaresetup.exe" | C:\Users\admin\AppData\Local\Temp\antimalwaresetup.exe | explorer.exe | ||||||||||||
User: admin Company: Plumbytes Software Integrity Level: HIGH Description: Plumbytes Anti-Malware Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 3228 | "C:\Users\admin\AppData\Local\Temp\pbinstall_files\Plumbytes.Installer.exe" | C:\Users\admin\AppData\Local\Temp\pbinstall_files\Plumbytes.Installer.exe | antimalwaresetup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Plumbytes.Installer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3652 | "C:\Users\admin\AppData\Local\Temp\antimalwaresetup.exe" | C:\Users\admin\AppData\Local\Temp\antimalwaresetup.exe | — | explorer.exe | |||||||||||
User: admin Company: Plumbytes Software Integrity Level: MEDIUM Description: Plumbytes Anti-Malware Exit code: 3221226540 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
12 526
Read events
12 453
Write events
64
Delete events
9
Modification events
| (PID) Process: | (2840) antimalwaresetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2840) antimalwaresetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (2840) antimalwaresetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (2840) antimalwaresetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (2840) antimalwaresetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (2840) antimalwaresetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2840) antimalwaresetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2840) antimalwaresetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2840) antimalwaresetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2840) antimalwaresetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
2
Suspicious files
1
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2840 | antimalwaresetup.exe | C:\Users\admin\AppData\Local\Temp\pbinstall_files\Plumbytes.Installer.exe.config | xml | |
MD5:A220996D08C67307039441454B928E7E | SHA256:8A2A1E2D20CC82C0BAC44DAFC02CB27B5FC795E1BCB0FF6740F50A0BAEE4F4D4 | |||
| 2840 | antimalwaresetup.exe | C:\Users\admin\AppData\Local\Temp\nsjF1A4.tmp\INetC.dll | executable | |
MD5:640BFF73A5F8E37B202D911E4749B2E9 | SHA256:C1E568E25EC111184DEB1B87CFDA4BFEC529B1ABEAB39B66539D998012F33502 | |||
| 2840 | antimalwaresetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:CB623DCD678B1CF22E16E0A296461362 | SHA256:F7FAD7BBA7376F0FE6680AC0A81A00EEA4F39E765DF1BA387C8FF613799C45C8 | |||
| 2840 | antimalwaresetup.exe | C:\Users\admin\AppData\Local\Temp\pbinstall_files\Plumbytes.Installer.exe | executable | |
MD5:F2F977D2606108E26DB2966D28000D7E | SHA256:4C62CA5B34B3018C43C225B263F1D0AB2EAF9B23E9784BF26BB265802225124B | |||
| 2840 | antimalwaresetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | der | |
MD5:E6B562FABB3D6DD97E04B93E8B592CF6 | SHA256:DCD2036E03E48EE6CD2ACEFD7523FFD5570DC26A107804BC945A586B1ADBBC75 | |||
| 2840 | antimalwaresetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:88D030F7DDB46462EC18EBB3550FD96F | SHA256:BF1528561A009C7286CF64BB3947FC54C5601C5433032E2EF0B8695F82A2A654 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
19
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2840 | antimalwaresetup.exe | GET | 304 | 184.24.77.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8771f4e6f85bff9e | unknown | — | — | unknown |
2840 | antimalwaresetup.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a414549a770d7263 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2840 | antimalwaresetup.exe | 104.40.92.107:443 | plumbytes2.azurewebsites.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2840 | antimalwaresetup.exe | 184.24.77.172:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2840 | antimalwaresetup.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3228 | Plumbytes.Installer.exe | 104.40.92.107:443 | plumbytes2.azurewebsites.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
plumbytes2.azurewebsites.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Plumbytes.Installer.exe | System.Net.WebException: The remote server returned an error: (403) Forbidden.
at System.Net.WebClient.UploadValues(Uri address, String method, NameValueCollection data)
at System.Net.WebClient.UploadValues(String address, NameValueCollection data)
at Plumbytes.Services.PlumbytesService.Post(String url, NameValueCollection nvc)
at Plumbytes.Services.PlumbytesService.Event(String EventType, SystemInfo systemInfo, String Data, Boolean IsError)
|