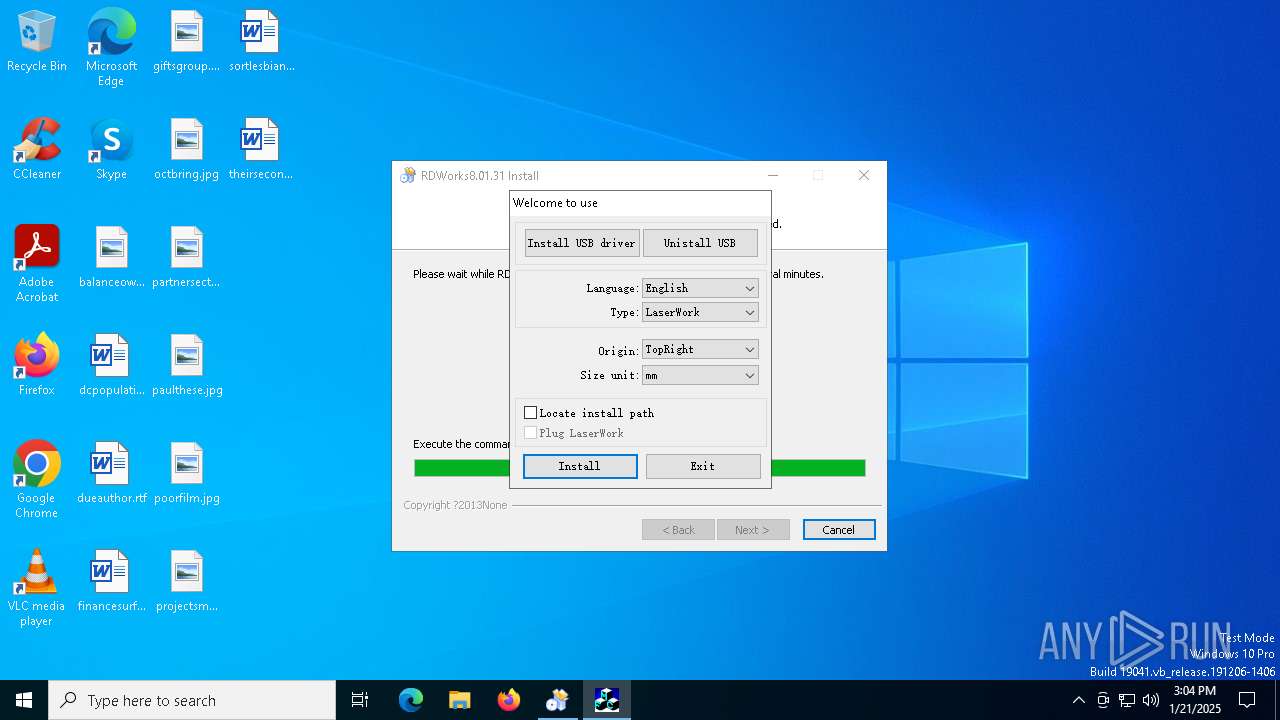
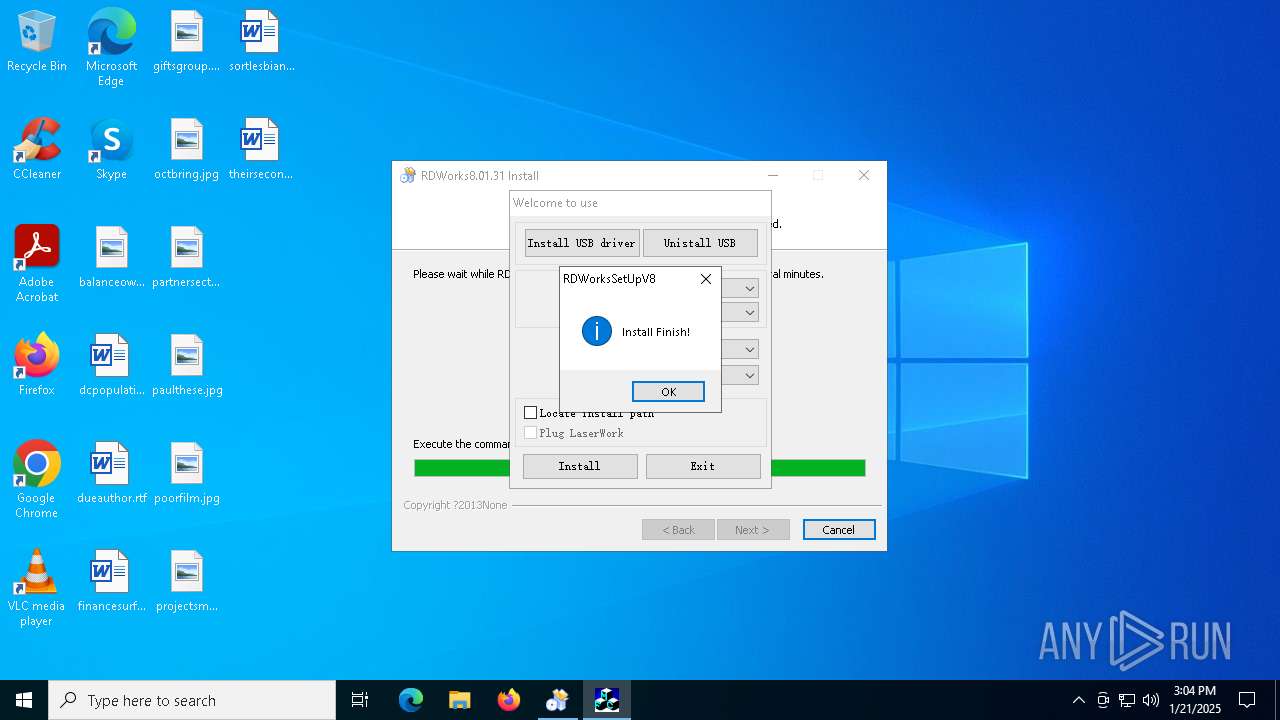
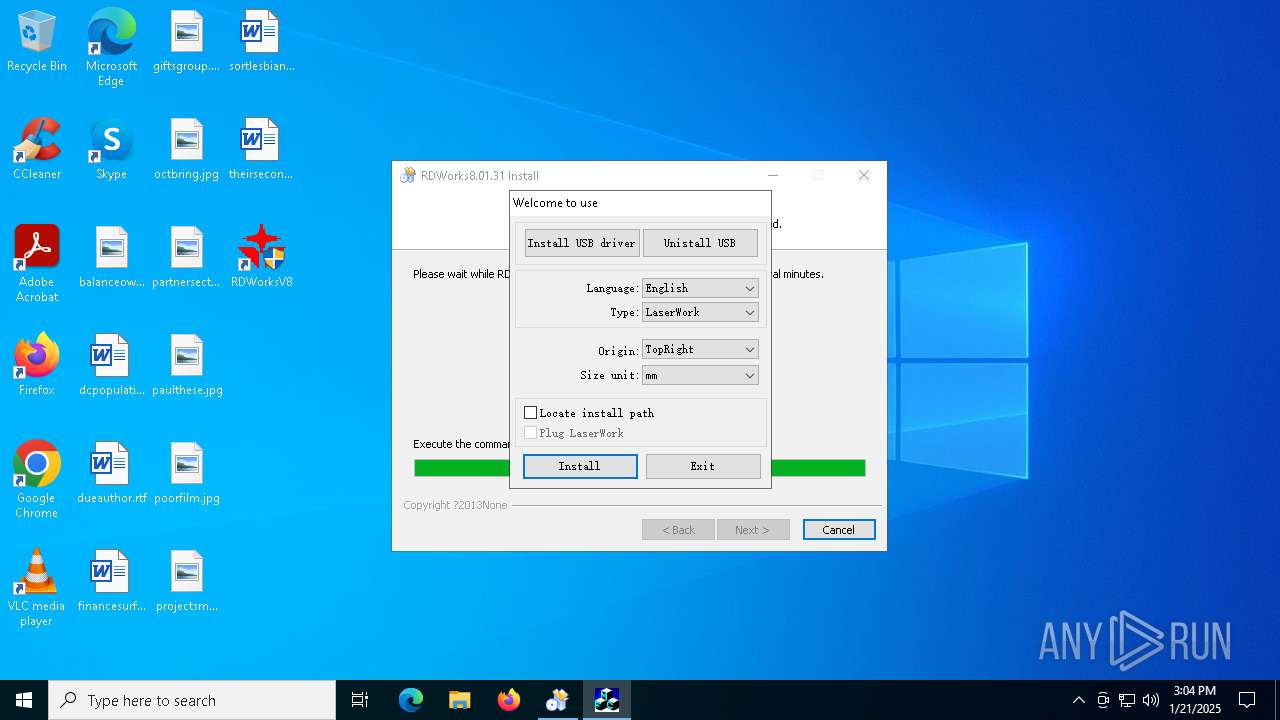
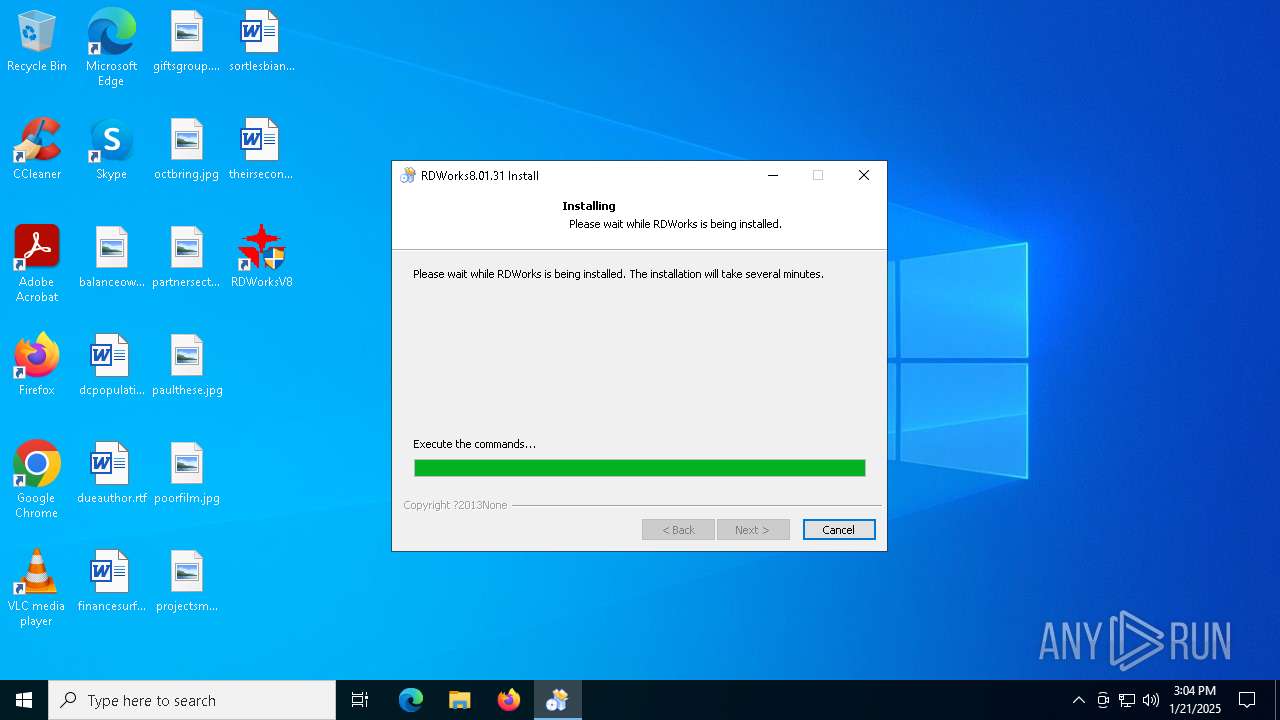
| File name: | G0874 RDWorksV8Setup8.01.31-180607.exe |
| Full analysis: | https://app.any.run/tasks/7769e0a2-f04d-4e2e-9099-a868940586ff |
| Verdict: | Malicious activity |
| Analysis date: | January 21, 2025, 15:03:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 43375C9A0556412DA4A4B8E8549579F3 |
| SHA1: | 0E0D3D9E0B779DD4382D2F08612C6691B10DAD67 |
| SHA256: | 0F26EDDDC1155F5DF0CDB1590976F58204C915479E47A9A5842463D7C8B72B5B |
| SSDEEP: | 98304:B+fgEyE1HyE0FvGmTwZiHD8/bj1G4i8nzPAzB4HDNBU1icDIXXhn5WylGllNQdc7:rGiSu8dp+VVoB6gS5nr |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
- RDWorksSetUpV8.exe (PID: 7056)
Executable content was dropped or overwritten
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
- RDWorksSetUpV8.exe (PID: 7056)
Drops a system driver (possible attempt to evade defenses)
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
There is functionality for taking screenshot (YARA)
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
Creates a software uninstall entry
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
Reads security settings of Internet Explorer
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
Starts CMD.EXE for commands execution
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
Creates file in the systems drive root
- RDWorksSetUpV8.exe (PID: 7056)
INFO
Reads the computer name
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
- RDWorksSetUpV8.exe (PID: 7056)
The sample compiled with english language support
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
- RDWorksSetUpV8.exe (PID: 7056)
The sample compiled with arabic language support
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
The sample compiled with chinese language support
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
- RDWorksSetUpV8.exe (PID: 7056)
Process checks computer location settings
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
Checks supported languages
- RDWorksSetUpV8.exe (PID: 7056)
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
The process uses the downloaded file
- G0874 RDWorksV8Setup8.01.31-180607.exe (PID: 6564)
Manual execution by a user
- RDWorksV8.exe (PID: 6692)
- RDWorksV8.exe (PID: 6768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (31.9) |
|---|---|---|
| .scr | | | Windows screen saver (29.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (14.8) |
| .exe | | | Win32 Executable (generic) (10.1) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 148992 |
| InitializedDataSize: | 41984 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25468 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.1.31.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | - |
| CompanyName: | None |
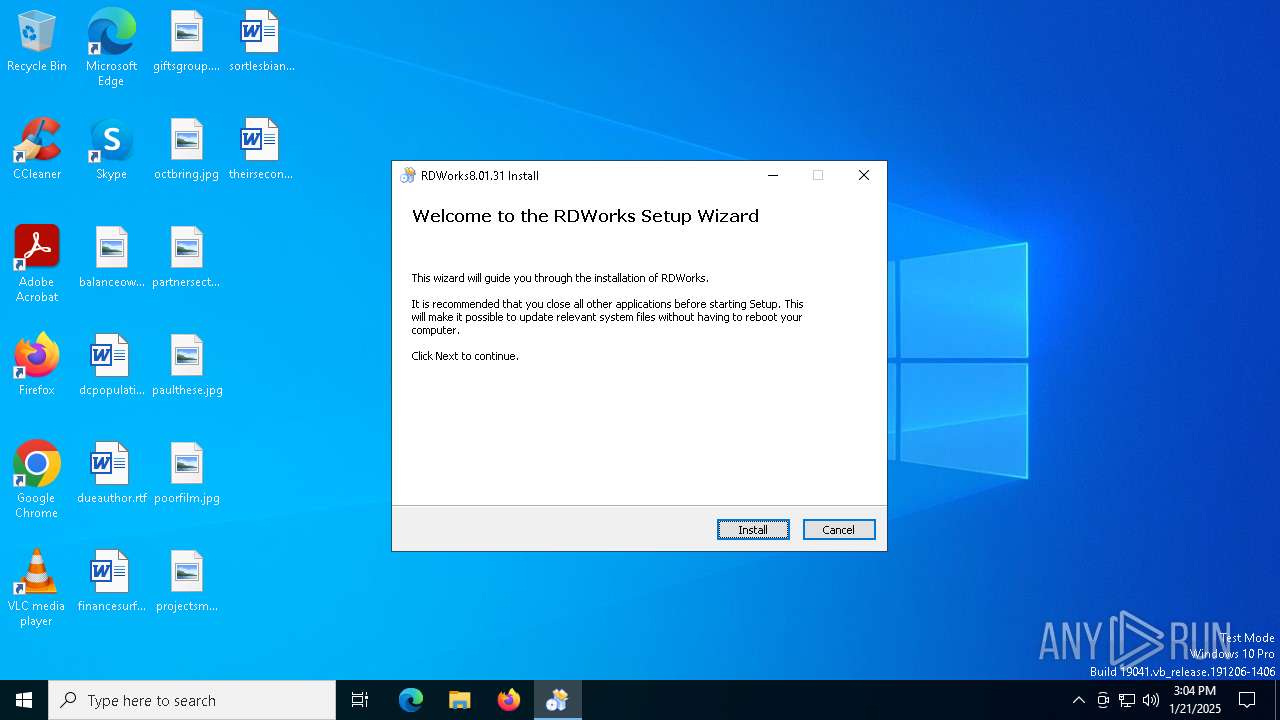
| FileDescription: | RDWorks 8.01.31 Installation |
| FileVersion: | 8.01.31 |
| LegalCopyright: | None |
Total processes
218
Monitored processes
87
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | "C:\Windows\System32\cmd.exe" "/c copy Lang\LGP_chs.ini c:\newpr\com\LGP_chs.ini" | C:\Windows\SysWOW64\cmd.exe | — | G0874 RDWorksV8Setup8.01.31-180607.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | "C:\Windows\System32\cmd.exe" "/c copy Lang\Lang_cht.ini c:\newpr\laserwork\Lang_cht.ini" | C:\Windows\SysWOW64\cmd.exe | — | G0874 RDWorksV8Setup8.01.31-180607.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | "C:\Windows\System32\cmd.exe" "/c copy Lang\Preview_cht.ini c:\newpr\com\Preview_cht.ini" | C:\Windows\SysWOW64\cmd.exe | — | G0874 RDWorksV8Setup8.01.31-180607.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2408 | "C:\Windows\System32\cmd.exe" "/c copy Lang\Lang_eng.ini c:\newpr\laserwork\Lang_eng.ini" | C:\Windows\SysWOW64\cmd.exe | — | G0874 RDWorksV8Setup8.01.31-180607.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2828 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3172 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 267
Read events
3 249
Write events
18
Delete events
0
Modification events
| (PID) Process: | (6564) G0874 RDWorksV8Setup8.01.31-180607.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RDWorks 8.01.31 |
| Operation: | write | Name: | DisplayName |
Value: RDWorks 8.01.31 | |||
| (PID) Process: | (6564) G0874 RDWorksV8Setup8.01.31-180607.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RDWorks 8.01.31 |
| Operation: | write | Name: | DisplayVersion |
Value: 8.01.31 | |||
| (PID) Process: | (6564) G0874 RDWorksV8Setup8.01.31-180607.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RDWorks 8.01.31 |
| Operation: | write | Name: | VersionMajor |
Value: 8 | |||
| (PID) Process: | (6564) G0874 RDWorksV8Setup8.01.31-180607.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RDWorks 8.01.31 |
| Operation: | write | Name: | VersionMinor |
Value: 1 | |||
| (PID) Process: | (6564) G0874 RDWorksV8Setup8.01.31-180607.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RDWorks 8.01.31 |
| Operation: | write | Name: | Publisher |
Value: None | |||
| (PID) Process: | (6564) G0874 RDWorksV8Setup8.01.31-180607.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RDWorks 8.01.31 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\newpr\Uninstall.exe | |||
| (PID) Process: | (6564) G0874 RDWorksV8Setup8.01.31-180607.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RDWorks 8.01.31 |
| Operation: | write | Name: | UninstallString |
Value: C:\newpr\Uninstall.exe | |||
| (PID) Process: | (6564) G0874 RDWorksV8Setup8.01.31-180607.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RDWorks 8.01.31 |
| Operation: | write | Name: | InstallLocation |
Value: C:\newpr\ | |||
| (PID) Process: | (6564) G0874 RDWorksV8Setup8.01.31-180607.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RDWorks 8.01.31 |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (6564) G0874 RDWorksV8Setup8.01.31-180607.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\RDWorks 8.01.31 |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
Executable files
130
Suspicious files
135
Text files
119
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6564 | G0874 RDWorksV8Setup8.01.31-180607.exe | C:\Users\admin\AppData\Local\Temp\$inst\temp_0.tmp | — | |
MD5:— | SHA256:— | |||
| 6564 | G0874 RDWorksV8Setup8.01.31-180607.exe | C:\newpr\driver\ftd2xx.h | text | |
MD5:F8A1E29135D11D97B428AC2EAA96E649 | SHA256:20ABFF3908C202C78F1CAC05CFC0900D5DA12A8CBA0EA54B2B7DFA5BE678A493 | |||
| 6564 | G0874 RDWorksV8Setup8.01.31-180607.exe | C:\newpr\driver\dpinst.xml | xml | |
MD5:E8DA2059C139D3D4CB8A9520EC594DAA | SHA256:7FCD043C4E8B5AAC218CEB659D5BACBCA46B5FA671D33DDD2E4B44C2D5B3DEDD | |||
| 6564 | G0874 RDWorksV8Setup8.01.31-180607.exe | C:\newpr\driver\ftdibus.cat | binary | |
MD5:2BA8C9F11297024B1FD1B3184D0A89AC | SHA256:8E7BA03AC35E5DE07467DD629CDB6675B5F6251C11AC238B79BAF8683D2A1E19 | |||
| 6564 | G0874 RDWorksV8Setup8.01.31-180607.exe | C:\newpr\driver\UnInst32.exe | executable | |
MD5:620B7067B6A22CEE35234DB5C1E75262 | SHA256:9F6311C613E5E739A0C945F76D370FF7468BAEE7AF0673B240FA4CE3FA20D69F | |||
| 6564 | G0874 RDWorksV8Setup8.01.31-180607.exe | C:\newpr\driver\DPInst32.exe | executable | |
MD5:79A58A1D039ECD08ABF6223460D6B557 | SHA256:FEFC6F5992A1896E40F5A9DCABC38A172AB88CE156F95201D59BE2F7524C9B96 | |||
| 6564 | G0874 RDWorksV8Setup8.01.31-180607.exe | C:\newpr\driver\DPInst64.exe | executable | |
MD5:31A683C31C4E6E3E3E410B2A59542C3F | SHA256:3E3DD480ACA5746113D3AD482393095D1AD3F96DD57262D0E637419E3AB19030 | |||
| 6564 | G0874 RDWorksV8Setup8.01.31-180607.exe | C:\newpr\driver\ftdiport.cat | binary | |
MD5:70CDA61115376F5ACA40565191DBEB95 | SHA256:B41D6B213FD4CEDE6FCA34966484047B21E74BCC84EA87A0D39B47691269B06B | |||
| 6564 | G0874 RDWorksV8Setup8.01.31-180607.exe | C:\Users\admin\AppData\Local\Temp\$inst\2.tmp | compressed | |
MD5:8708699D2C73BED30A0A08D80F96D6D7 | SHA256:A32E0A83001D2C5D41649063217923DAC167809CAB50EC5784078E41C9EC0F0F | |||
| 6564 | G0874 RDWorksV8Setup8.01.31-180607.exe | C:\newpr\driver\amd64\ftbusui.dll | executable | |
MD5:653CDCA6BE222085FEFEE8B2B94D42F2 | SHA256:F4F60010C4EE5BD0FDE9D28E9B3F3626FBCFF5B05040CDCD60FE98D2E8CE2E76 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.113:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1792 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1792 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3208 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.242.9:443 | go.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
1076 | svchost.exe | 2.23.242.9:443 | go.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.113:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |