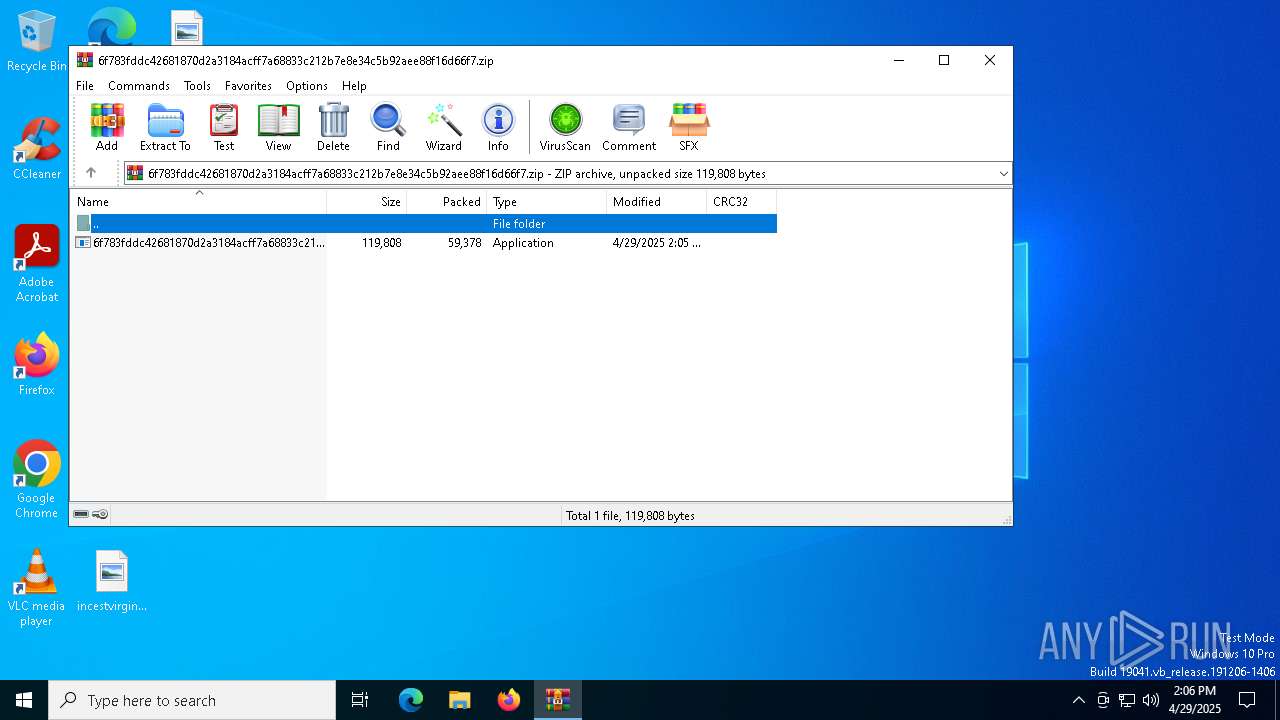
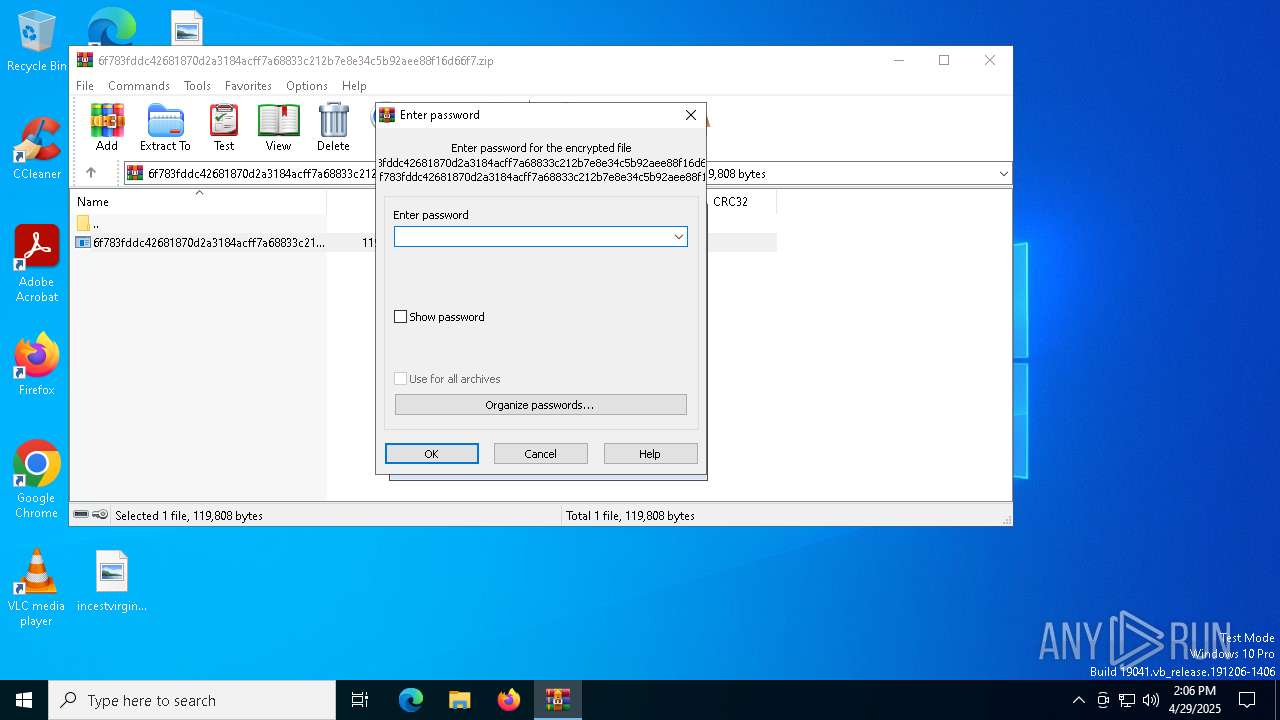
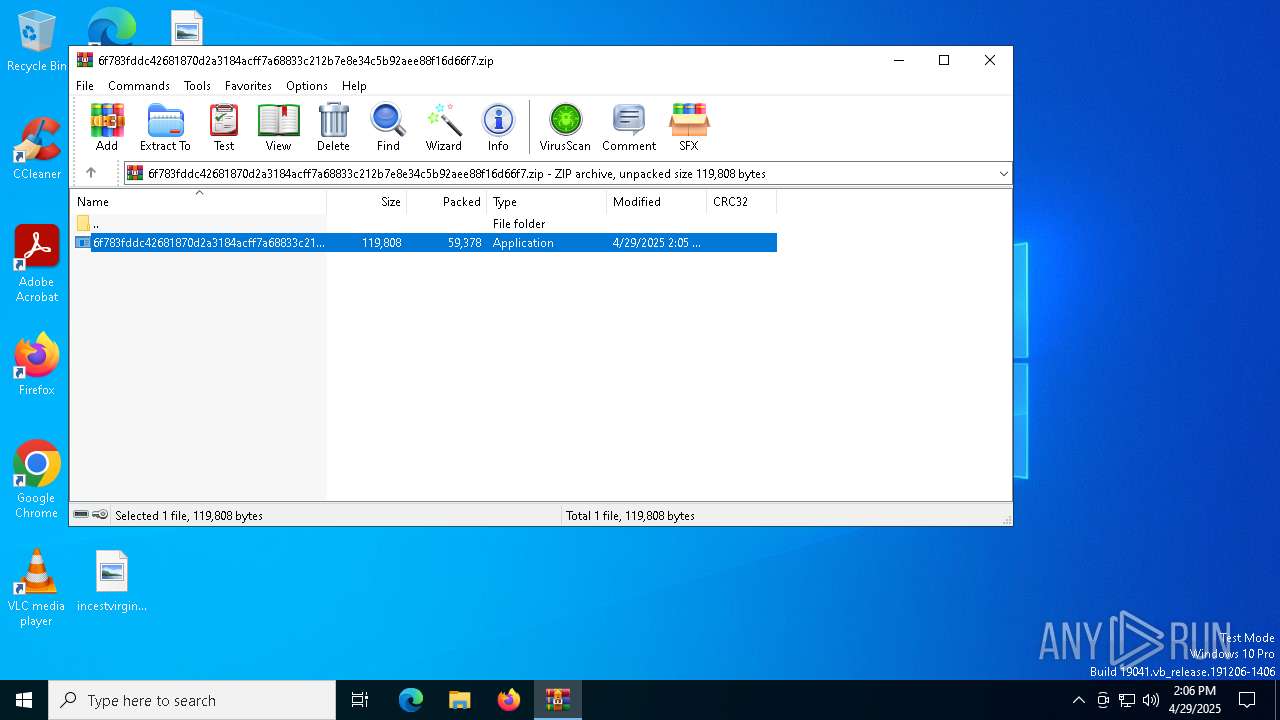
| File name: | 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.zip |
| Full analysis: | https://app.any.run/tasks/6d6e061e-6372-4b8f-9c6d-a8dc437936c6 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 14:06:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
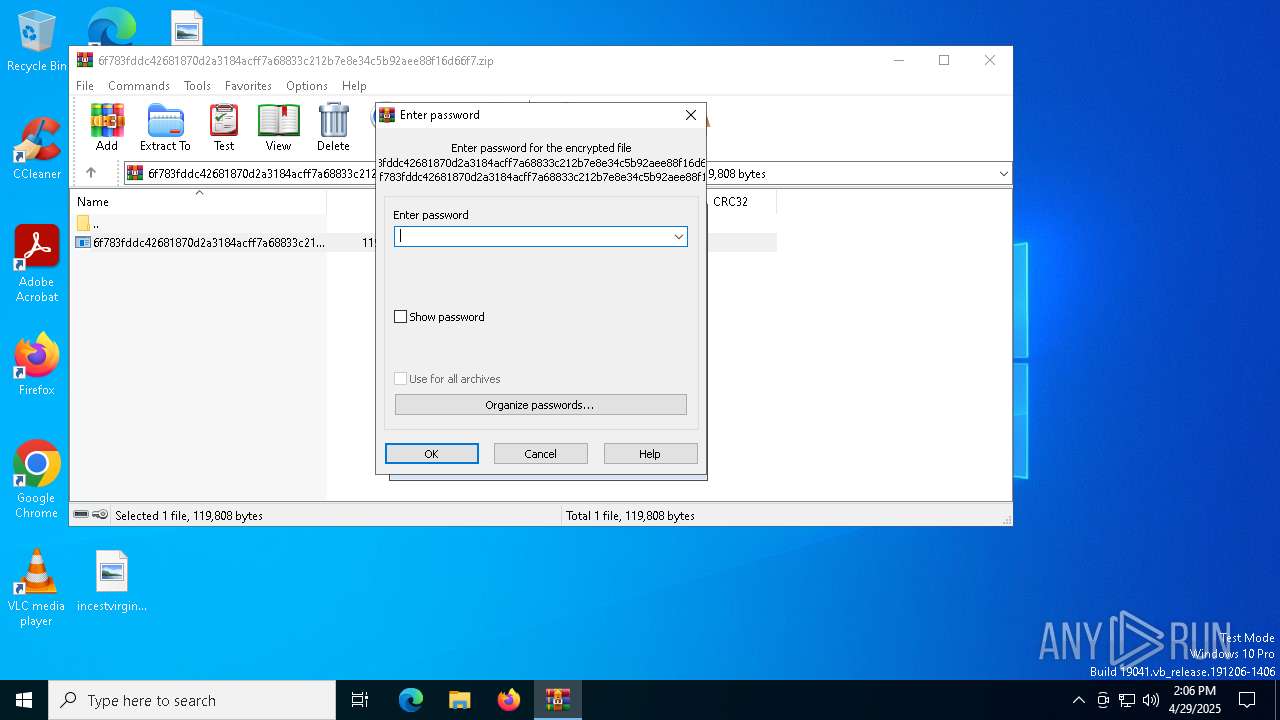
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 34E6ACC183B73270E4A6A6A89307172B |
| SHA1: | 0F9CD5659412A477B87A5A1F22365AFE2861DC7F |
| SHA256: | 0F1AA2CB2FCCA697FFF21C75137A7F1B5E5303D89BAC418EFD70227C92254B8C |
| SSDEEP: | 1536:Z/1ciJq0kTJfY/QrxMjYe64wiNIkX6FOqtCawubrmPnwH0:Z/1cAq0k1YIex6DiNIt9tb3m4H0 |
MALICIOUS
Changes powershell execution policy (Bypass)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 7404)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 904)
Bypass execution policy to execute commands
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6272)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6272)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6272)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6272)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6272)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3300)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 7404)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 904)
Reads the date of Windows installation
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 7404)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 904)
The process executes Powershell scripts
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 7404)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 904)
Starts POWERSHELL.EXE for commands execution
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 7404)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 904)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6272)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7892)
- csc.exe (PID: 7844)
- csc.exe (PID: 5008)
- csc.exe (PID: 6620)
Executable content was dropped or overwritten
- csc.exe (PID: 7844)
- csc.exe (PID: 7892)
- csc.exe (PID: 6620)
- csc.exe (PID: 5008)
Connects to the server without a host name
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6272)
INFO
Checks supported languages
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 7404)
- cvtres.exe (PID: 7864)
- csc.exe (PID: 7892)
- cvtres.exe (PID: 7912)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 904)
- csc.exe (PID: 7844)
- csc.exe (PID: 5008)
- cvtres.exe (PID: 1184)
- csc.exe (PID: 6620)
- identity_helper.exe (PID: 2088)
- cvtres.exe (PID: 3100)
Create files in a temporary directory
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 7404)
- csc.exe (PID: 7844)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 904)
- cvtres.exe (PID: 7864)
- csc.exe (PID: 7892)
- cvtres.exe (PID: 7912)
- csc.exe (PID: 5008)
- csc.exe (PID: 6620)
- cvtres.exe (PID: 3100)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3300)
Process checks computer location settings
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 7404)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 904)
Reads the computer name
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 7404)
- 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe (PID: 904)
Disables trace logs
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6272)
Checks proxy server information
- powershell.exe (PID: 7452)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6272)
Reads the machine GUID from the registry
- csc.exe (PID: 7844)
- csc.exe (PID: 7892)
- csc.exe (PID: 5008)
- csc.exe (PID: 6620)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6272)
Reads the software policy settings
- slui.exe (PID: 7276)
Manual execution by a user
- msedge.exe (PID: 5720)
Application launched itself
- msedge.exe (PID: 5720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:04:29 14:05:32 |
| ZipCRC: | 0xe91043be |
| ZipCompressedSize: | 59378 |
| ZipUncompressedSize: | 119808 |
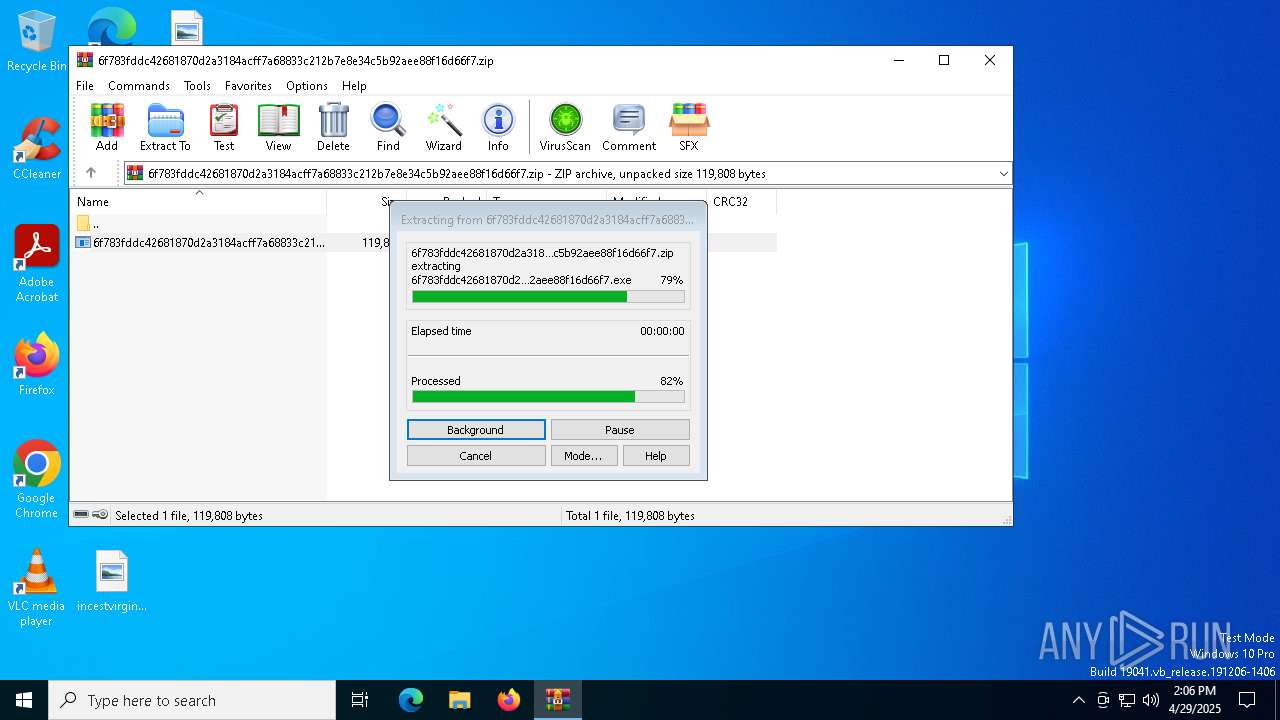
| ZipFileName: | 6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe |
Total processes
187
Monitored processes
54
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4108 --field-trial-handle=2396,i,13773026287809192128,8321551160249197603,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=32 --mojo-platform-channel-handle=6928 --field-trial-handle=2396,i,13773026287809192128,8321551160249197603,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 872 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6976 --field-trial-handle=2396,i,13773026287809192128,8321551160249197603,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 904 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3300.39582\6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3300.39582\6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1184 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES418A.tmp" "c:\Users\admin\AppData\Local\Temp\CSC662BAB5380B04EF6BC31AEBD19A27797.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 1272 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=6356 --field-trial-handle=2396,i,13773026287809192128,8321551160249197603,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1748 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6808 --field-trial-handle=2396,i,13773026287809192128,8321551160249197603,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2088 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6208 --field-trial-handle=2396,i,13773026287809192128,8321551160249197603,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2136 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6796 --field-trial-handle=2396,i,13773026287809192128,8321551160249197603,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2284 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x300,0x304,0x308,0x2f8,0x310,0x7ffc895d5fd8,0x7ffc895d5fe4,0x7ffc895d5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
20 701
Read events
20 637
Write events
46
Delete events
18
Modification events
| (PID) Process: | (3300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\6f783fddc42681870d2a3184acff7a68833c212b7e8e34c5b92aee88f16d66f7.zip | |||
| (PID) Process: | (3300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
Executable files
45
Suspicious files
660
Text files
178
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7912 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES54C.tmp | binary | |
MD5:EC62F22D7E799A03C3230801B901BA5A | SHA256:F059942F4870BF127E48EC5A8EC9BD21182178F9F25822825EB951FA3AC9BB07 | |||
| 7892 | csc.exe | C:\Users\admin\AppData\Local\Temp\livpioza.dll | executable | |
MD5:7040EB99817977D5B05CFA74A3A2267E | SHA256:8C69D4792FBF42AB32686531AAC6E2E1654D78B8767930A4F8C4199BF7D21393 | |||
| 7844 | csc.exe | C:\Users\admin\AppData\Local\Temp\nacpydjm.dll | executable | |
MD5:A7EB5ED6FC8AB4648816EA95CD347326 | SHA256:3E89DCDCA9EA85D652D6C45C35019E6CED81D0BE939D277FC8D70D3BEA9C07CA | |||
| 7844 | csc.exe | C:\Users\admin\AppData\Local\Temp\nacpydjm.out | text | |
MD5:CBEB606D362B3407E2BD4D5727BCCF01 | SHA256:7EE9C9E20585B0717AA029783A619331A2E233509940E967AC9CF097F8CAA03A | |||
| 7452 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_k5x0jlxb.v0n.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7892 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCED583F0C8BC64989ACFA91FE0148460.TMP | binary | |
MD5:E7BCB6E66DA2D70E0E81725678F473E5 | SHA256:49D4E6B12FB3C0227710B80E0484215CBD4CD2CFC8E47350D9863D22E2DD9DEE | |||
| 7844 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC237456E9518E4F1BBDC5D8E99FCC6293.TMP | binary | |
MD5:49FBDBE10620A26E659A854C3F600B4A | SHA256:4FC7F8B1C9C2C8A5B12FD3610310C90AEEB8697F06E92EF7D2E89EC4E2D6EBF9 | |||
| 7452 | powershell.exe | C:\Users\admin\AppData\Local\Temp\nacpydjm.cmdline | text | |
MD5:325E233FA1BA9926BAF2313DCA242855 | SHA256:9C65A0144BF57B8142ED4848964FBDF8660095BBA2900FF021C76DF7515987A3 | |||
| 7864 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES462.tmp | binary | |
MD5:2ABE2F0280CDE4DE66DD5940BCCF7E51 | SHA256:1DC3238412FD770010E80A68C62197562933D7DC96B161568B48509D696341BC | |||
| 7452 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mj0x4ljc.otq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
201
DNS requests
233
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7452 | powershell.exe | GET | 200 | 212.227.245.12:80 | http://212.227.245.12/c.aes | unknown | — | — | unknown |
8120 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8120 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6272 | powershell.exe | GET | 200 | 212.227.245.12:80 | http://212.227.245.12/c.aes | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5256 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |