| URL: | https://www.deepcool.com/products/Cooling/cpuaircoolers/AK500-DIGITAL-CPU-Cooler-With-Status-Display-1700-AM5/2023/17236.shtml#Downloads |
| Full analysis: | https://app.any.run/tasks/b859d738-2b72-4e11-9e79-716c11926082 |
| Verdict: | Malicious activity |
| Analysis date: | October 24, 2024, 14:26:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 8B4693DA7934B7FEED85F8155FF3F2FA |
| SHA1: | B230FD19AFF37E61CA7A244C7B71F66922BDE406 |
| SHA256: | 0F09234610D02DB9B6EE5DB367B2B34221D905104F9FB539BD81781D1A1DCA1B |
| SSDEEP: | 3:N8DSLVGRJLKOXaQGRWXCxWKKJwQ/gxRB7IfRz41cpS/WddUSEuRIczgn:2OLeJLKRRWXSYJtYpoVpSebLEuRlg |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
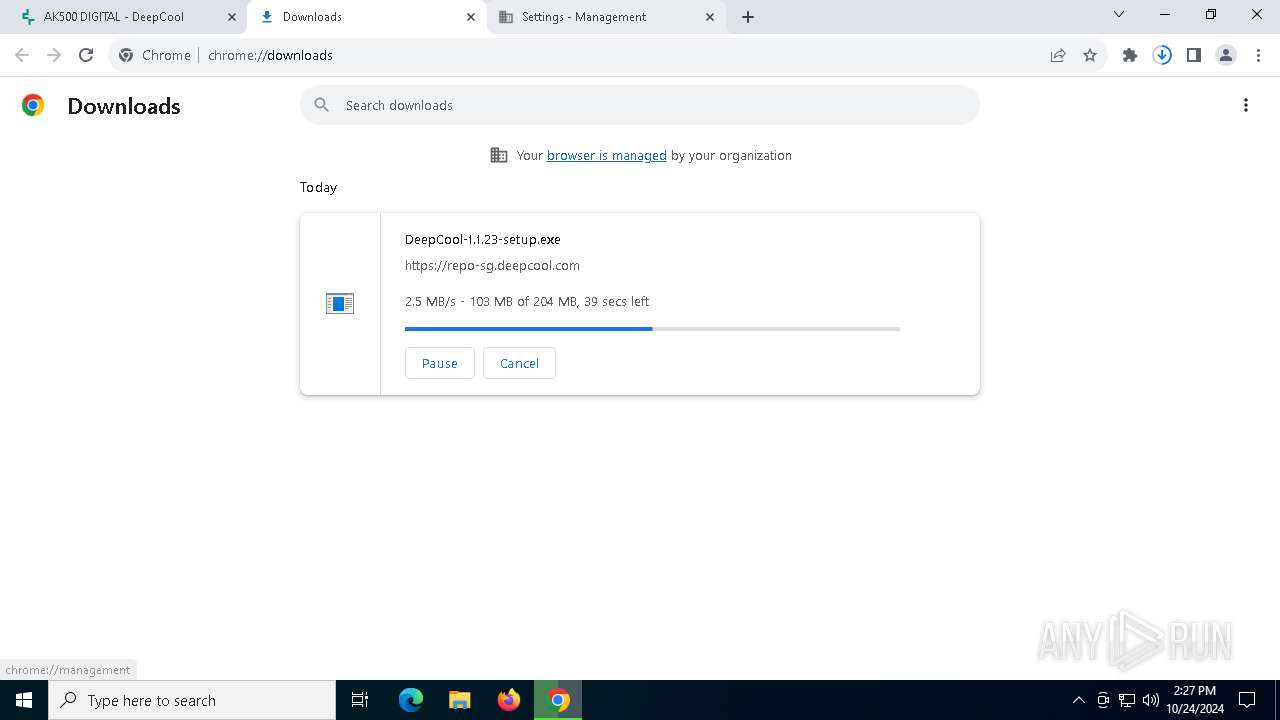
- DeepCool-1.1.23-setup.exe (PID: 7108)
Executable content was dropped or overwritten
- DeepCool-1.1.23-setup.exe (PID: 7108)
- vc_redist.x64.exe (PID: 1552)
- vc_redist.x64.exe (PID: 7936)
- Dism.exe (PID: 5068)
- deep_service.exe (PID: 1376)
- DeepCool.exe (PID: 5580)
Process drops legitimate windows executable
- DeepCool-1.1.23-setup.exe (PID: 7108)
- vc_redist.x64.exe (PID: 7936)
Drops 7-zip archiver for unpacking
- DeepCool-1.1.23-setup.exe (PID: 7108)
The process drops C-runtime libraries
- DeepCool-1.1.23-setup.exe (PID: 7108)
Starts a Microsoft application from unusual location
- vc_redist.x64.exe (PID: 1552)
- DismHost.exe (PID: 6844)
Executes as Windows Service
- nssm.exe (PID: 7832)
Drops a system driver (possible attempt to evade defenses)
- deep_service.exe (PID: 1376)
Application launched itself
- DeepCool.exe (PID: 5580)
Connects to unusual port
- DeepCool.exe (PID: 5580)
INFO
Connects to unusual port
- chrome.exe (PID: 5240)
Executable content was dropped or overwritten
- chrome.exe (PID: 6872)
- chrome.exe (PID: 6428)
Manual execution by a user
- Taskmgr.exe (PID: 6220)
- Taskmgr.exe (PID: 3732)
- DeepCool.exe (PID: 5580)
Application launched itself
- chrome.exe (PID: 6428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
208
Monitored processes
64
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2224 --field-trial-handle=1872,i,2274840481589774455,18345790393843062418,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 624 | "C:\DeepCool\DeepCool.exe" --type=utility --utility-sub-type=video_capture.mojom.VideoCaptureService --lang=en-US --service-sandbox-type=none --no-sandbox --user-data-dir="C:\Users\admin\AppData\Roaming\DeepCool" --mojo-platform-channel-handle=3356 --field-trial-handle=2108,i,3066757566757228367,13873755217400149029,131072 --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:8 | C:\DeepCool\DeepCool.exe | — | DeepCool.exe | |||||||||||
User: admin Company: cn.deepcool.com Integrity Level: MEDIUM Description: DeepCool Exit code: 0 Version: 1.1.23 Modules
| |||||||||||||||
| 632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5640 --field-trial-handle=1872,i,2274840481589774455,18345790393843062418,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1244 | C:\DeepCool\resources\service\x86\nssm.exe remove "Deep Cool Helper Service" confirm | C:\DeepCool\resources\service\x86\nssm.exe | — | DeepCool-1.1.23-setup.exe | |||||||||||
User: admin Integrity Level: HIGH Description: The non-sucking service manager Exit code: 3 Version: 2.24 Modules
| |||||||||||||||
| 1376 | "C:\DeepCool\resources\service\x64\deep_service.exe" | C:\DeepCool\resources\service\x64\deep_service.exe | nssm.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Modules
| |||||||||||||||
| 1552 | "C:\WINDOWS\Temp\{25EC74EF-5C0F-4CAB-81C4-424071FED588}\.cr\vc_redist.x64.exe" -burn.clean.room="C:\DeepCool\resources\VCRuntime\vc_redist.x64.exe" -burn.filehandle.attached=572 -burn.filehandle.self=568 /install /quiet /norestart | C:\Windows\Temp\{25EC74EF-5C0F-4CAB-81C4-424071FED588}\.cr\vc_redist.x64.exe | vc_redist.x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2019 Redistributable (x64) - 14.29.30153 Exit code: 1638 Version: 14.29.30153.0 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1868 --field-trial-handle=1872,i,2274840481589774455,18345790393843062418,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1748 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | C:\DeepCool\resources\service\x86\nssm.exe set "Deep Cool Helper Service" DisplayName "Deep Cool Helper Service" | C:\DeepCool\resources\service\x86\nssm.exe | — | DeepCool-1.1.23-setup.exe | |||||||||||
User: admin Integrity Level: HIGH Description: The non-sucking service manager Exit code: 0 Version: 2.24 Modules
| |||||||||||||||
Total events
17 165
Read events
17 094
Write events
44
Delete events
27
Modification events
| (PID) Process: | (6428) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6428) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6428) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6428) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6428) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7832) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000004F1388F22026DB01 | |||
| (PID) Process: | (6428) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
| (PID) Process: | (6428) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C2I |
Value: 1 | |||
| (PID) Process: | (6428) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7I |
Value: 1 | |||
| (PID) Process: | (6428) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1S |
Value: 1 | |||
Executable files
384
Suspicious files
154
Text files
277
Unknown types
150
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6428 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF8c107.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF8c107.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF8c107.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF8c0f7.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF8c107.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
120
DNS requests
84
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2364 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7116 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4904 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acccxbt6wwsvpxzpob4hojndwkqq_4.10.2830.0/oimompecagnajdejgnnjijobebaeigek_4.10.2830.0_win64_dldxogwi36sxwpr57ta4lg57z4.crx3 | unknown | — | — | whitelisted |
4904 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acccxbt6wwsvpxzpob4hojndwkqq_4.10.2830.0/oimompecagnajdejgnnjijobebaeigek_4.10.2830.0_win64_dldxogwi36sxwpr57ta4lg57z4.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
864 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6944 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6428 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5240 | chrome.exe | 142.250.110.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
5240 | chrome.exe | 8.210.90.60:443 | www.deepcool.com | Alibaba US Technology Co., Ltd. | HK | whitelisted |
5240 | chrome.exe | 151.101.194.208:443 | cdn.deepcool.com | FASTLY | US | whitelisted |
5240 | chrome.exe | 172.217.16.206:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.deepcool.com |
| whitelisted |
accounts.google.com |
| whitelisted |
cdn.deepcool.com |
| whitelisted |
global.deepcool.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
pro.ip-api.com |
| shared |
connect.facebook.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5240 | chrome.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
5240 | chrome.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
Process | Message |
|---|---|
Dism.exe | PID=5068 TID=6868 Connecting to the provider located at C:\WINDOWS\system32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
Dism.exe | PID=5068 TID=6868 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=5068 TID=6868 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5068 TID=6868 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5068 TID=6868 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5068 TID=6868 Loading Provider from location C:\WINDOWS\system32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
DismHost.exe | PID=6844 TID=6784 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=6844 TID=6784 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=6844 TID=6784 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=5068 TID=6868 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |