| File name: | setup.msi |
| Full analysis: | https://app.any.run/tasks/9727689d-93ec-4eb7-b52b-1b06a6026c54 |
| Verdict: | Malicious activity |
| Analysis date: | June 23, 2025, 12:15:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {D11D1A01-F475-44D2-BE71-0120E9530948}, Number of Words: 10, Subject: Kroqoul Civil Tools, Author: Werqos Livina, Name of Creating Application: Kroqoul Civil Tools, Template: x64;1033, Comments: This installer database contains the logic and data required to install Kroqoul Civil Tools., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Sun Jun 22 21:28:53 2025, Last Saved Time/Date: Sun Jun 22 21:28:53 2025, Last Printed: Sun Jun 22 21:28:53 2025, Number of Pages: 450 |
| MD5: | EC36175FDADA97232B695634192DD62E |
| SHA1: | 137B9DEAE5E7822353CE4A2C2D576063C4C69C23 |
| SHA256: | 0ED50D27280D82FC40EFFA6C72CE38B2FAE60476A242F95F379FD5C13D537CA2 |
| SSDEEP: | 393216:2gShndyL/8/aDzj9U82/PVoATjN2h0objZMdmYxIg2AZkijr:6dij9RcVoATjN2h0objZB2Iflw |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6224)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1564)
Process drops python dynamic module
- msiexec.exe (PID: 6224)
Process drops legitimate windows executable
- msiexec.exe (PID: 6224)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 6224)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 6224)
The executable file from the user directory is run by the CMD process
- 7z.exe (PID: 5708)
- openvpn.exe (PID: 3740)
The process drops C-runtime libraries
- msiexec.exe (PID: 6224)
Executing commands from a ".bat" file
- msiexec.exe (PID: 6224)
There is functionality for taking screenshot (YARA)
- taskcoach.exe (PID: 4036)
INFO
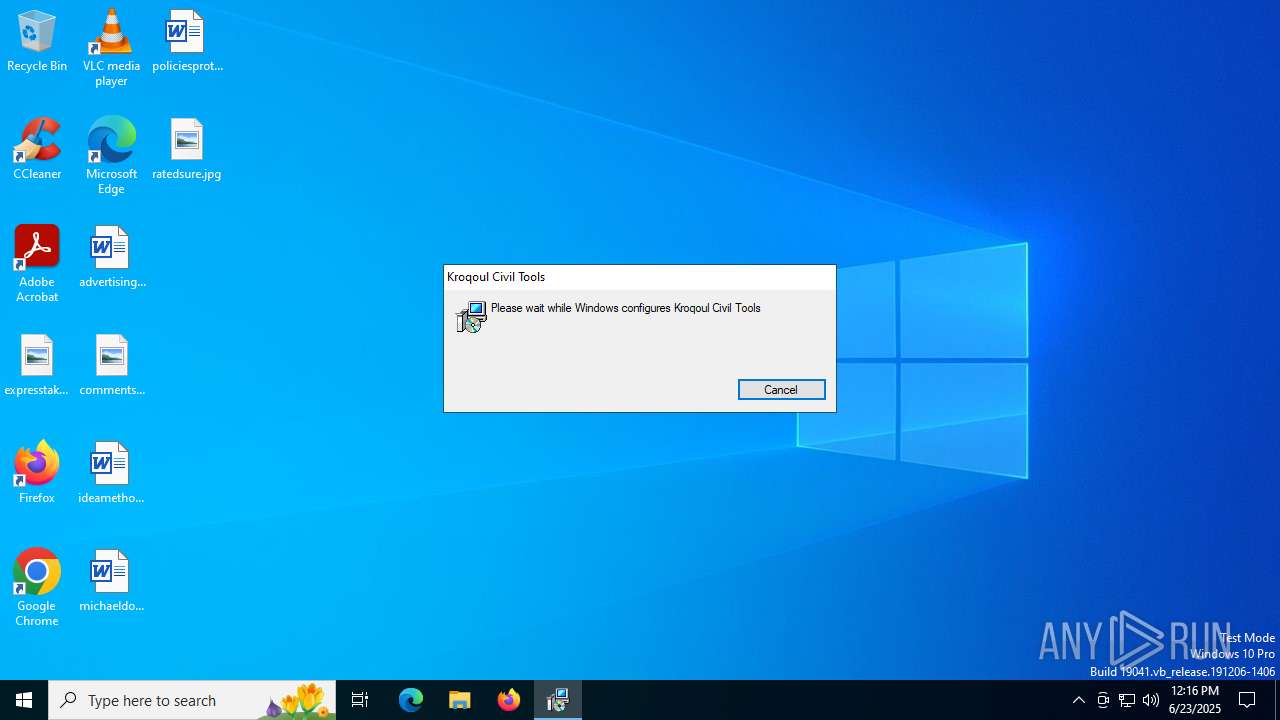
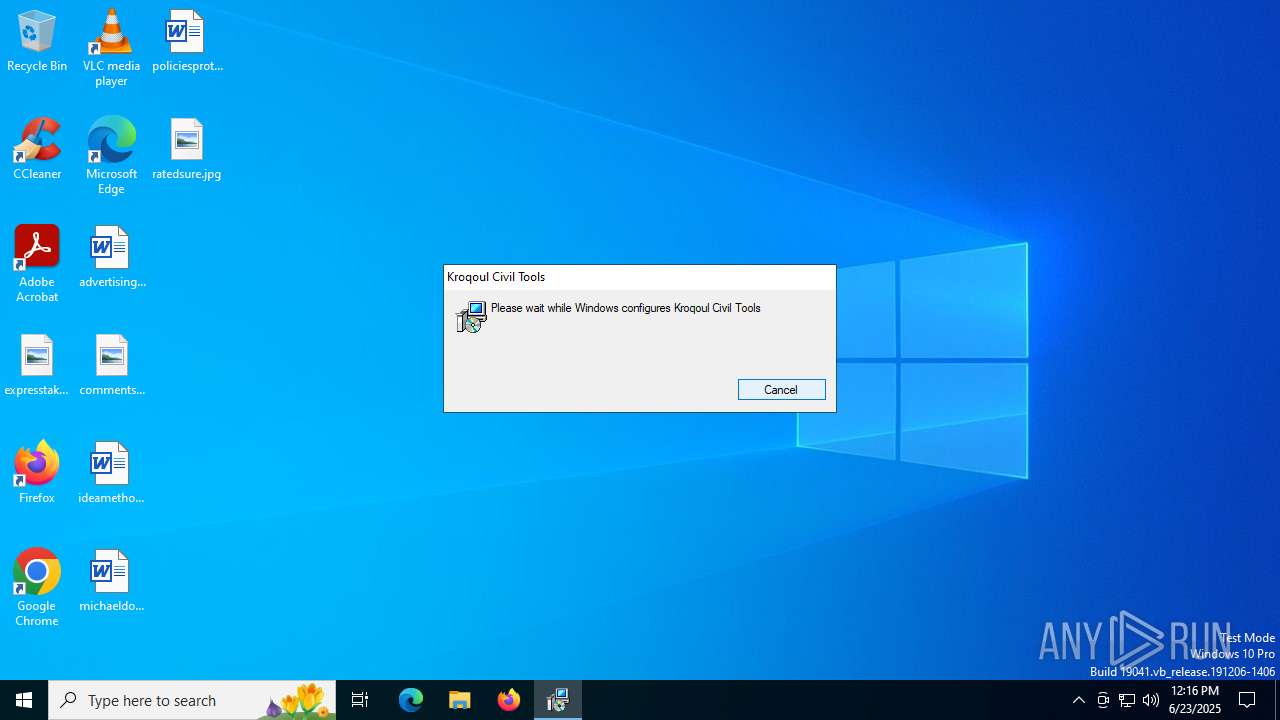
An automatically generated document
- msiexec.exe (PID: 2760)
Reads the computer name
- msiexec.exe (PID: 6224)
- msiexec.exe (PID: 1564)
- 7z.exe (PID: 5708)
- taskcoach.exe (PID: 4036)
Checks supported languages
- msiexec.exe (PID: 1564)
- msiexec.exe (PID: 6224)
- taskcoach.exe (PID: 4036)
- 7z.exe (PID: 5708)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6224)
Reads the machine GUID from the registry
- msiexec.exe (PID: 1564)
- taskcoach.exe (PID: 4036)
Checks proxy server information
- msiexec.exe (PID: 1564)
- slui.exe (PID: 5896)
- taskcoach.exe (PID: 4036)
The sample compiled with english language support
- msiexec.exe (PID: 6224)
Creates files or folders in the user directory
- msiexec.exe (PID: 1564)
- msiexec.exe (PID: 6224)
- taskcoach.exe (PID: 4036)
Reads Environment values
- msiexec.exe (PID: 1564)
Reads the software policy settings
- msiexec.exe (PID: 1564)
- slui.exe (PID: 5896)
Creates a software uninstall entry
- msiexec.exe (PID: 6224)
Create files in a temporary directory
- taskcoach.exe (PID: 4036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {D11D1A01-F475-44D2-BE71-0120E9530948} |
| Words: | 10 |
| Subject: | Kroqoul Civil Tools |
| Author: | Werqos Livina |
| LastModifiedBy: | - |
| Software: | Kroqoul Civil Tools |
| Template: | x64;1033 |
| Comments: | This installer database contains the logic and data required to install Kroqoul Civil Tools. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2025:06:22 21:28:53 |
| ModifyDate: | 2025:06:22 21:28:53 |
| LastPrinted: | 2025:06:22 21:28:53 |
| Pages: | 450 |
Total processes
146
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1564 | C:\Windows\syswow64\MsiExec.exe -Embedding C214334F788206E85276C94AC12EE98F | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2760 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\setup.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3740 | "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\\openvpn.exe" 0 | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\openvpn.exe | — | cmd.exe | |||||||||||
User: admin Company: The OpenVPN Project Integrity Level: MEDIUM Description: OpenVPN Daemon Exit code: 3221225781 Version: 2.6.11.0 Modules
| |||||||||||||||
| 4036 | "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\taskcoach.exe" | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\taskcoach.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Your friendly task manager Version: 1.4.6 Modules
| |||||||||||||||
| 5708 | "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\\7z.exe" x "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\\xlicense.dat" -o"C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\" -y -p0 | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\7z.exe | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 2 Version: 24.09 Modules
| |||||||||||||||
| 5896 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6224 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6636 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6940 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\xupdate.bat" "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\" 0" | C:\Windows\System32\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225781 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 897
Read events
3 569
Write events
319
Delete events
9
Modification events
| (PID) Process: | (6224) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 50180000FF078D9C38E4DB01 | |||
| (PID) Process: | (6224) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 02EBB2DBDB8D981AE4143CB0F9E74B50A8D259942B8CB0F9D039A020757528E3 | |||
| (PID) Process: | (6224) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1564) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1564) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1564) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6224) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\EE517F264941A23449C811419D3E65FF |
| Operation: | write | Name: | ACC62E45E452308468EDC41BAD281F1D |
Value: C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\ | |||
| (PID) Process: | (6224) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\825033A6A7F99AF4ABD0055DFD47DE0D |
| Operation: | write | Name: | ACC62E45E452308468EDC41BAD281F1D |
Value: 21:\Software\Werqos Livina\Kroqoul Civil Tools\Version | |||
| (PID) Process: | (6224) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\083E538AEB4D6AA4CAE0D26CFEF6E4C3 |
| Operation: | write | Name: | ACC62E45E452308468EDC41BAD281F1D |
Value: C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\_socket.pyd | |||
| (PID) Process: | (6224) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\9101AFDFAB2B2564B88347A4A121C144 |
| Operation: | write | Name: | ACC62E45E452308468EDC41BAD281F1D |
Value: C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\gdiplus.dll | |||
Executable files
119
Suspicious files
166
Text files
102
Unknown types
100
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6224 | msiexec.exe | C:\Windows\Installer\17786c.msi | — | |
MD5:— | SHA256:— | |||
| 6224 | msiexec.exe | C:\Windows\Installer\MSI7A7F.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 1564 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3554D6D68D8291652D7FDC994BCEF253 | binary | |
MD5:861F51E2F26927F32BB9E85F23F81BD6 | SHA256:185184A2A9DDAD0550CB535F1E50A5EA8F33B7E34022300D276F734A1675F4E9 | |||
| 6224 | msiexec.exe | C:\Windows\Installer\MSI7B9A.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 1564 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3554D6D68D8291652D7FDC994BCEF253 | binary | |
MD5:BC758025E898E1BE4F2A1EF2AC14B959 | SHA256:56DD102D139C2C6D5C3550792BD0F4538C0C0109CB64D75844F8DB59A8C1CD9C | |||
| 6224 | msiexec.exe | C:\Windows\Temp\~DF8711425B4F12E8D2.TMP | binary | |
MD5:9D1C7884C6A1DABF82E92914575B4DA1 | SHA256:64DAF413CA90B999AD806A2A1CD375B5E9319B2AD25C65B7A5E3ACA3AE3DC4D0 | |||
| 6224 | msiexec.exe | C:\Windows\Installer\MSI7C19.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 6224 | msiexec.exe | C:\Windows\Installer\MSI92C1.tmp | binary | |
MD5:F4F297CC9BC143D28537EAD3AA43383E | SHA256:F8359B4436E5864BA4878C51D1499E64C8AF01CE37F43545B50AB7D4A574842B | |||
| 6224 | msiexec.exe | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\_socket.pyd | executable | |
MD5:07789A8C23BCEBE32F8BFD4CE4AF5FFB | SHA256:235CC97584C3D31E5F3146121F64699D30CF372A86868EA755A9A0AFA6C56144 | |||
| 6224 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:9D1C7884C6A1DABF82E92914575B4DA1 | SHA256:64DAF413CA90B999AD806A2A1CD375B5E9319B2AD25C65B7A5E3ACA3AE3DC4D0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
31
DNS requests
23
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1200 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1564 | msiexec.exe | GET | 200 | 104.18.21.213:80 | http://r10.c.lencr.org/52.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4036 | taskcoach.exe | GET | 301 | 51.158.149.82:80 | http://taskcoach.org/version.txt | unknown | — | — | unknown |
4036 | taskcoach.exe | GET | 301 | 51.158.149.82:80 | http://taskcoach.org/messages.txt | unknown | — | — | unknown |
4960 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4960 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5348 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1200 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1200 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1564 | msiexec.exe | 169.150.247.37:443 | salsawynwood.com | — | GB | unknown |
1564 | msiexec.exe | 104.18.21.213:80 | r10.c.lencr.org | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
salsawynwood.com |
| unknown |
r10.c.lencr.org |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4036 | taskcoach.exe | Attempted Information Leak | ET INFO Python-urllib/ Suspicious User Agent |
4036 | taskcoach.exe | Attempted Information Leak | ET INFO Python-urllib/ Suspicious User Agent |
Process | Message |
|---|---|
taskcoach.exe | 12:16:29 PM: ..\..\src\msw\menu.cpp(487): 'InsertMenuItem()' failed with error 0x00000057 (the parameter is incorrect.).
|
taskcoach.exe | 12:16:29 PM: ..\..\src\msw\menu.cpp(487): 'InsertMenuItem()' failed with error 0x00000057 (the parameter is incorrect.).
|
taskcoach.exe | 12:16:29 PM: ..\..\src\msw\menu.cpp(487): 'InsertMenuItem()' failed with error 0x00000057 (the parameter is incorrect.).
|