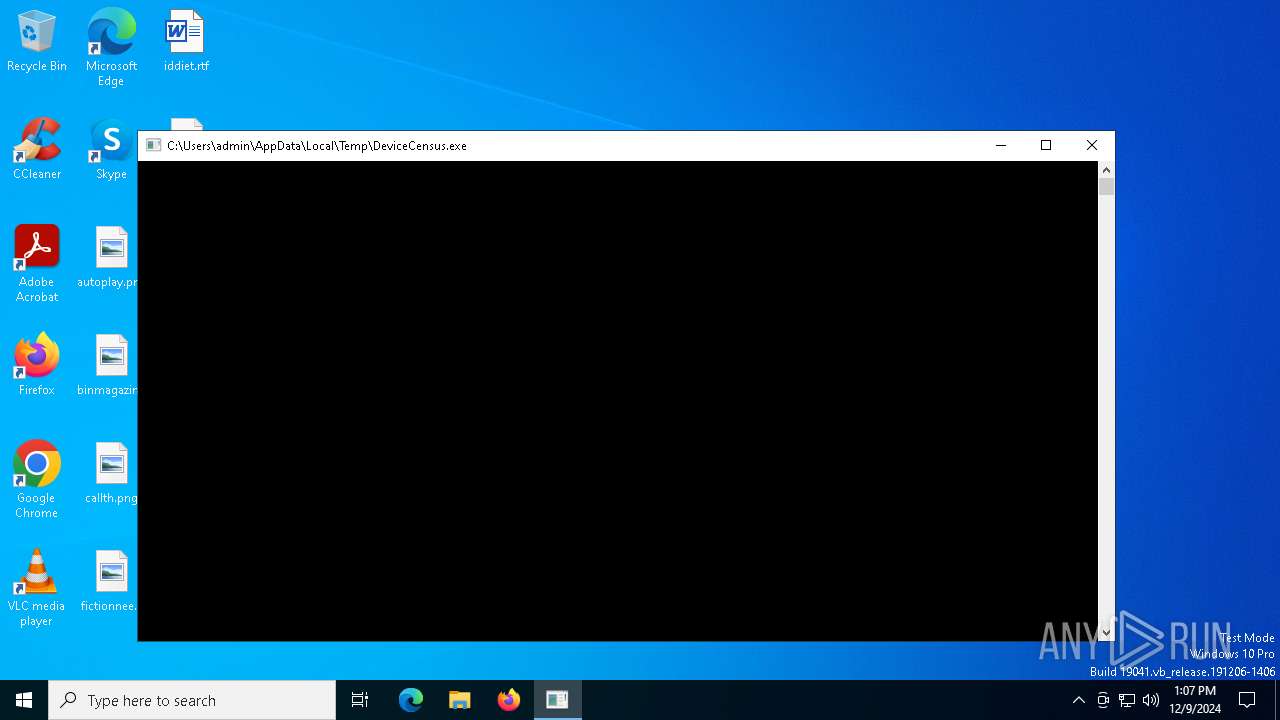
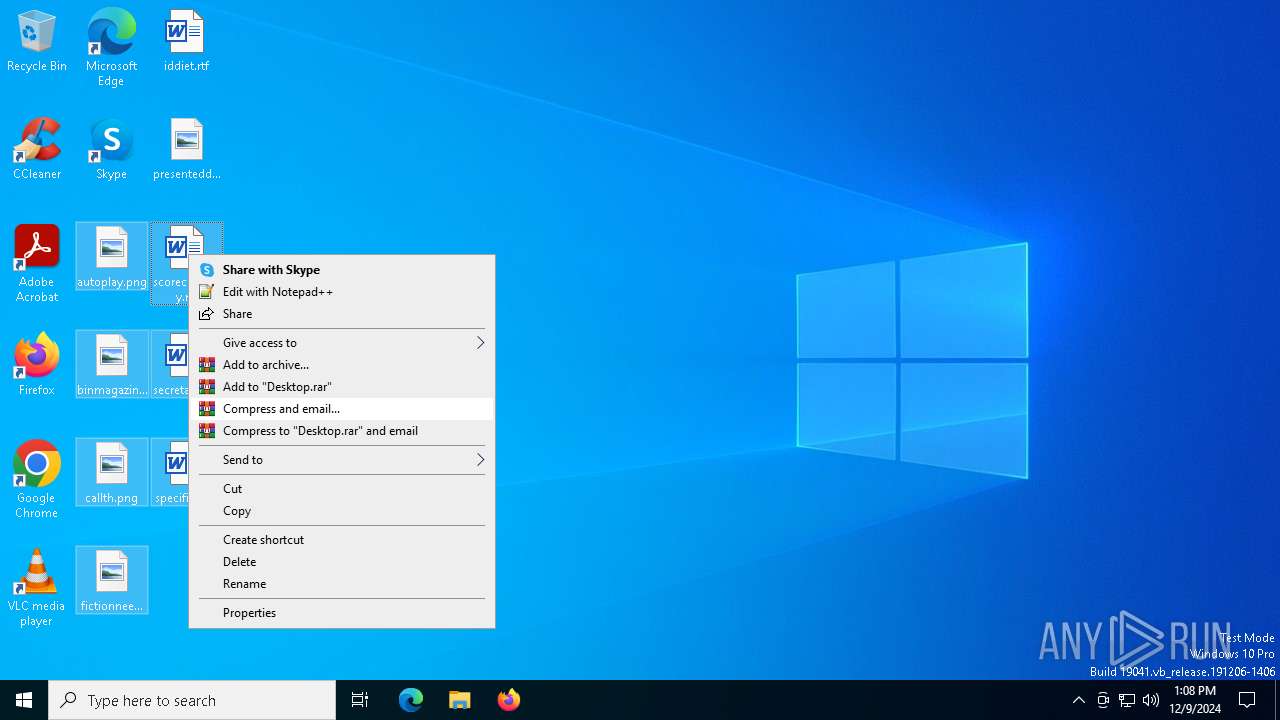
| File name: | DeviceCensus.exe |
| Full analysis: | https://app.any.run/tasks/fec78a3d-9847-4b6e-9a02-17fdbbd9bb07 |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2024, 13:07:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | F7056495A79374C7A06CAB943CEC9422 |
| SHA1: | 153962531DECB14F1C685B763433AA07DD1CC3E2 |
| SHA256: | 0EC01B252EC583A9848AD5E47890FDDA60AA584A425C5EF20466D57F665709D7 |
| SSDEEP: | 768:8y1griticJJgMl0iOegM9PGZLo/+nj2/7YI+WDK+:8e4itj+iOLCPGZLc+nKTh+WO+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- DeviceCensus.exe (PID: 4652)
Starts a Microsoft application from unusual location
- DeviceCensus.exe (PID: 4652)
Reads the date of Windows installation
- DeviceCensus.exe (PID: 4652)
Reads the BIOS version
- DeviceCensus.exe (PID: 4652)
INFO
Reads the machine GUID from the registry
- DeviceCensus.exe (PID: 4652)
Checks supported languages
- DeviceCensus.exe (PID: 4652)
Reads the computer name
- DeviceCensus.exe (PID: 4652)
Manual execution by a user
- WinRAR.exe (PID: 4164)
- WinRAR.exe (PID: 3732)
Reads Environment values
- DeviceCensus.exe (PID: 4652)
Checks proxy server information
- DeviceCensus.exe (PID: 4652)
Reads CPU info
- DeviceCensus.exe (PID: 4652)
Reads the time zone
- DeviceCensus.exe (PID: 4652)
Creates files or folders in the user directory
- DeviceCensus.exe (PID: 4652)
Process checks computer location settings
- DeviceCensus.exe (PID: 4652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2096:05:22 02:17:09+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.13 |
| CodeSize: | 9216 |
| InitializedDataSize: | 18432 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x27e0 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 10 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 10.0.17763.1016 |
| ProductVersionNumber: | 10.0.17763.1016 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Device Census |
| FileVersion: | 10.0.17763.1016 (WinBuild.160101.0800) |
| InternalName: | DeviceCensus |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | DeviceCensus.exe |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 10.0.17763.1016 |
Total processes
130
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3560 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | DeviceCensus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
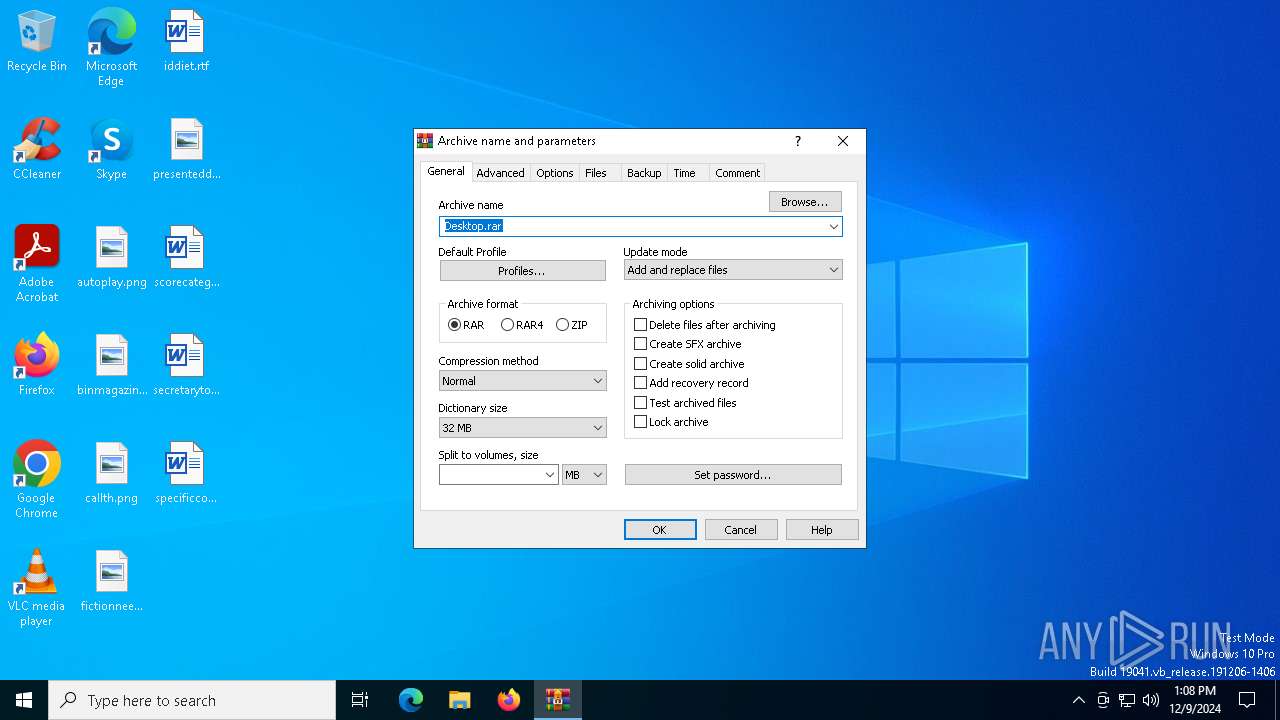
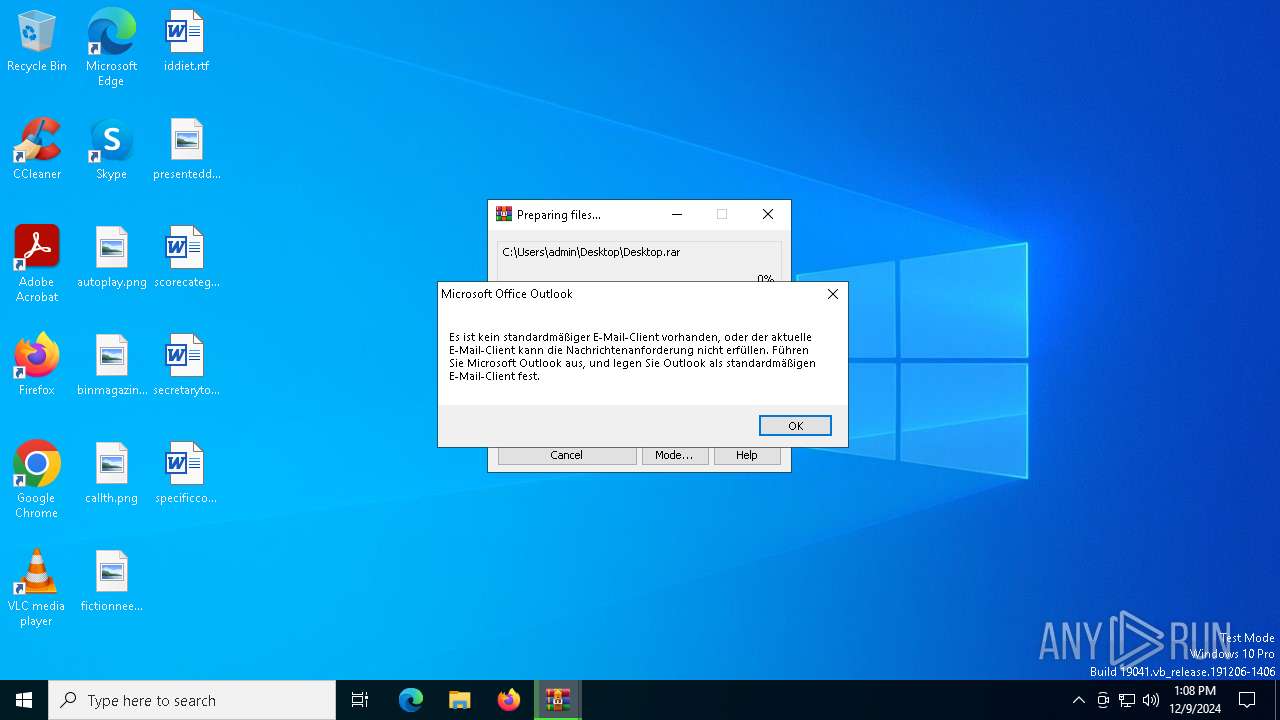
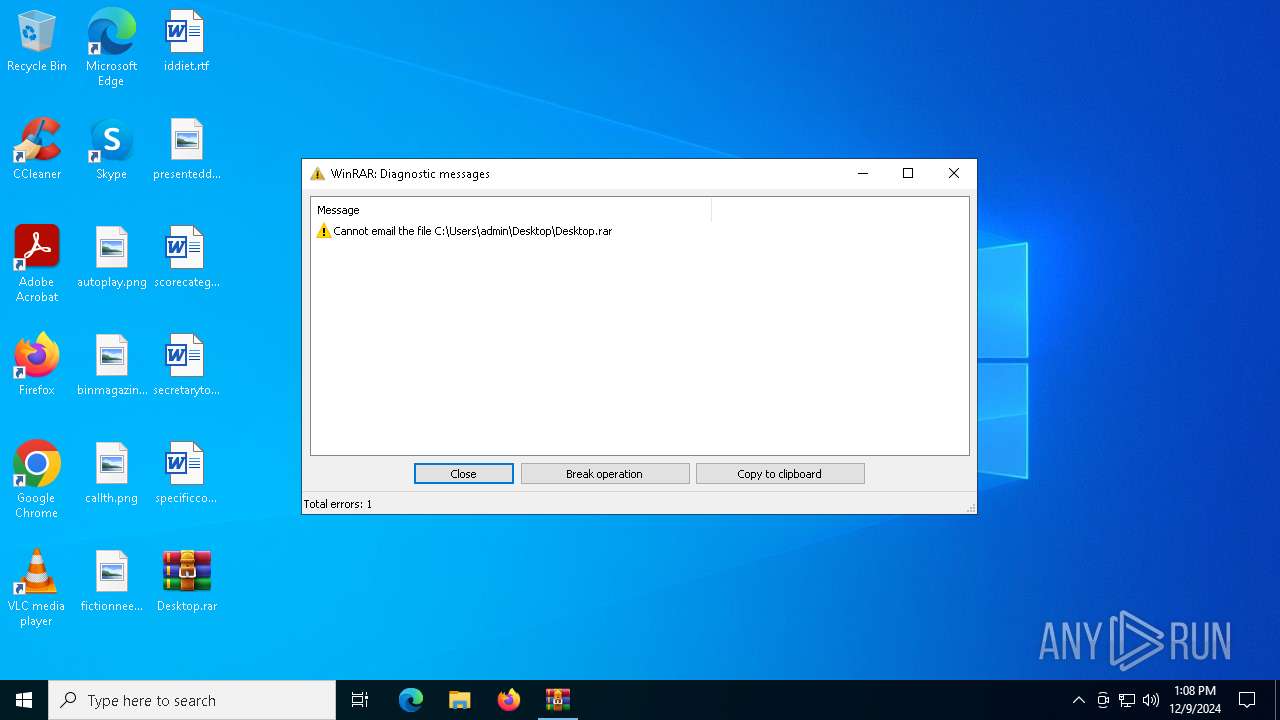
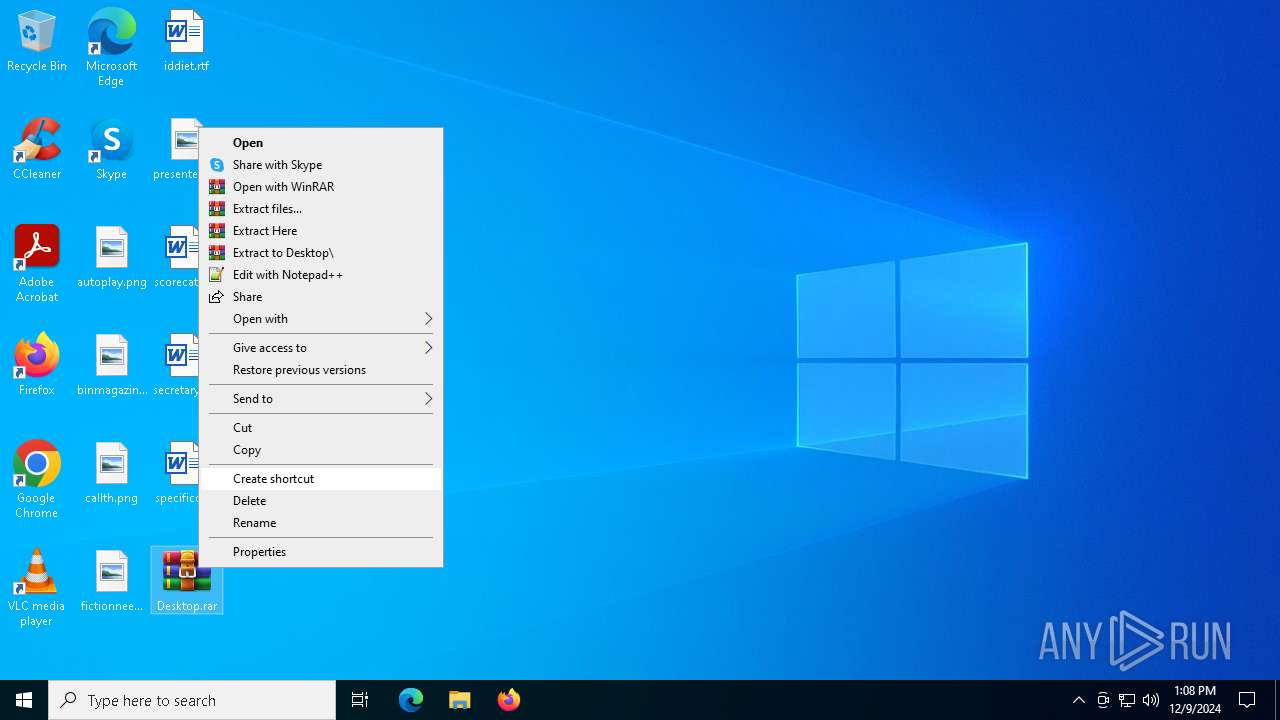
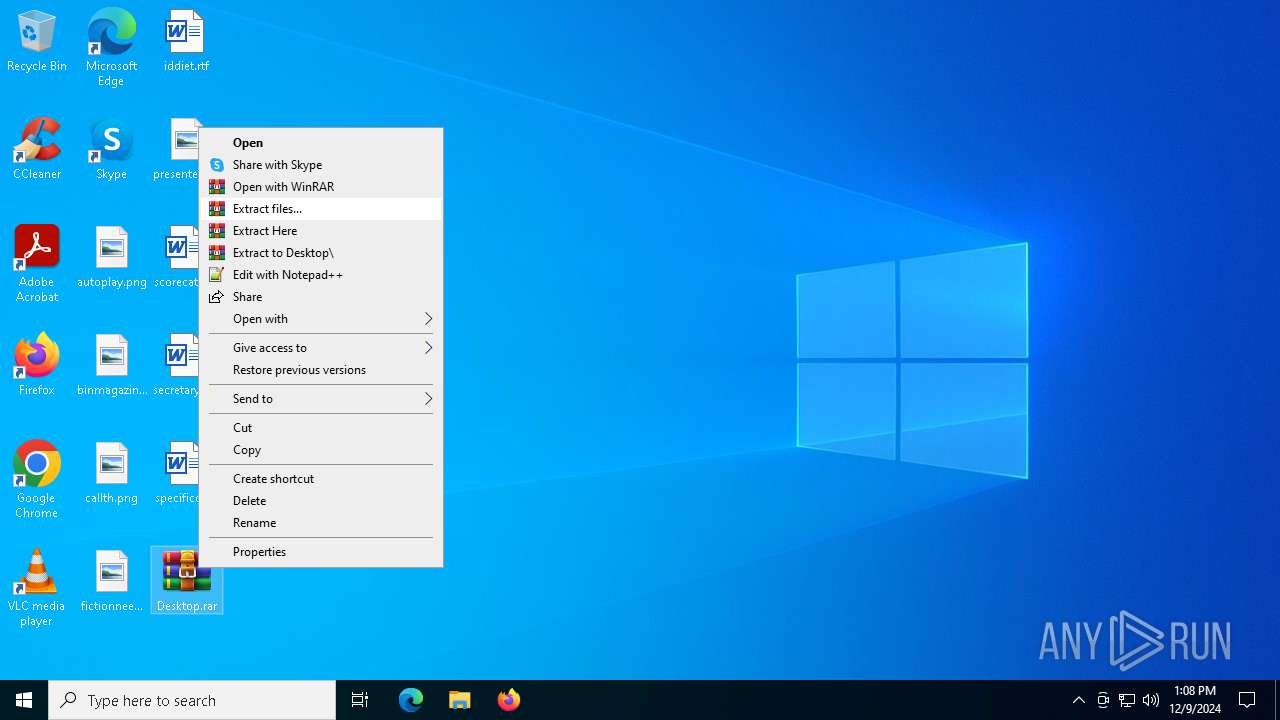
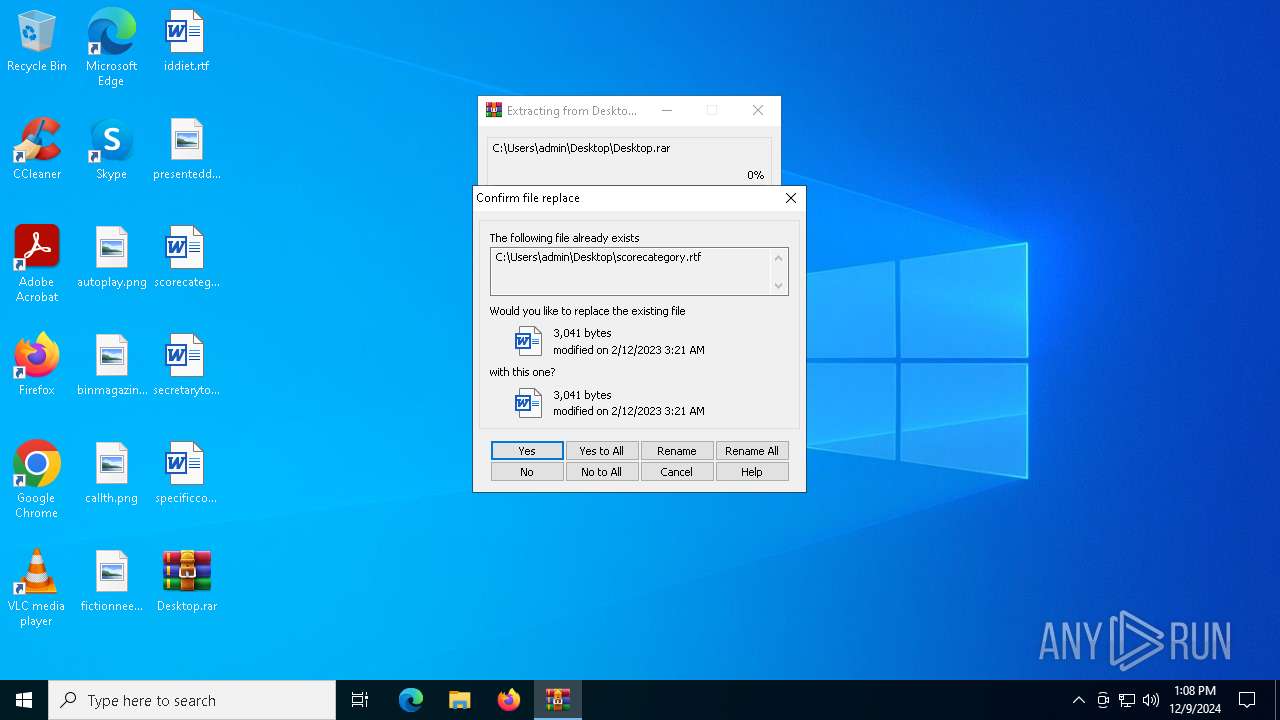
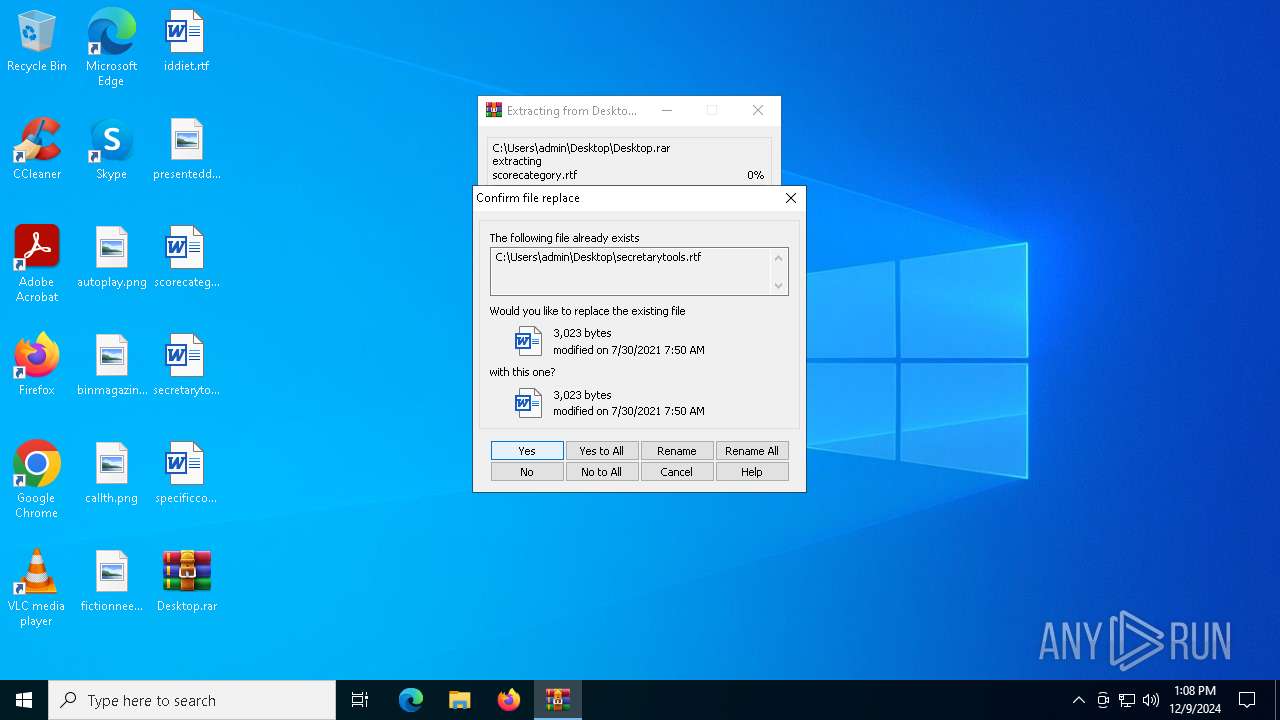
| 3732 | "C:\Program Files\WinRAR\WinRAR.exe" a -ieml. -ep1 -scul -r0 -iext -- . C:\Users\admin\Desktop\scorecategory.rtf C:\Users\admin\Desktop\secretarytools.rtf C:\Users\admin\Desktop\specificconsumer.rtf C:\Users\admin\Desktop\autoplay.png C:\Users\admin\Desktop\binmagazine.jpg C:\Users\admin\Desktop\callth.png C:\Users\admin\Desktop\fictionneed.jpg | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 2 Version: 5.91.0 Modules
| |||||||||||||||
| 4164 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Desktop.rar" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4652 | "C:\Users\admin\AppData\Local\Temp\DeviceCensus.exe" | C:\Users\admin\AppData\Local\Temp\DeviceCensus.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Device Census Exit code: 0 Version: 10.0.17763.1016 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6948 | C:\WINDOWS\system32\DllHost.exe /Processid:{AA65DD7C-83AC-48C0-A6FD-9B61FEBF8800} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 568
Read events
17 508
Write events
60
Delete events
0
Modification events
| (PID) Process: | (6948) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\DeliveryOptimization\Config |
| Operation: | write | Name: | DownloadMode_BackCompat |
Value: 0 | |||
| (PID) Process: | (6948) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\DeliveryOptimization\Config |
| Operation: | write | Name: | DODownloadMode |
Value: 0 | |||
| (PID) Process: | (4652) DeviceCensus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UpdatePolicy\Settings |
| Operation: | write | Name: | PausedQualityStatus |
Value: 0 | |||
| (PID) Process: | (4652) DeviceCensus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UpdatePolicy\Settings |
| Operation: | write | Name: | PausedFeatureStatus |
Value: 0 | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ArcName |
| Operation: | write | Name: | 0 |
Value: Desktop.rar | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
0
Suspicious files
8
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4164 | WinRAR.exe | C:\Users\admin\Desktop\scorecategory.rtf | text | |
MD5:5537F0A7F86E680D98DAB66141D941E7 | SHA256:146FE175D0582AF73E6D9FE0EFBE619159B6E2CC22E50C57DE708F9F92B3344E | |||
| 4652 | DeviceCensus.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:F0CF5B1794ECA7CD73F9C020DAAB8EF2 | SHA256:2AF00EDCE7EF3266897E52DC81E8DE3B7A079028C0F1F96EAFF9E38AD342F617 | |||
| 4164 | WinRAR.exe | C:\Users\admin\Desktop\specificconsumer.rtf | text | |
MD5:32A8BE9153EDBA18D9780D762FF23506 | SHA256:F2CB2F7D053BB51F9CDFA42FB2E50BA90ED3F48BCBA0AAD9A746A143373CE5D2 | |||
| 4652 | DeviceCensus.exe | C:\Users\admin\AppData\Local\D3DSCache\637f029a71589346\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 4652 | DeviceCensus.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:F7E9F3EF7EEEAB6255A89FB32015717F | SHA256:6DB23E45DBF4022CBFA9151B0122551C8F1FFFB7C9A9148F68BCE5D7FBB8E9D2 | |||
| 6948 | dllhost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Microsoft\Windows\DeliveryOptimization\Logs\domgmt.20241209_130750_267.etl | binary | |
MD5:E19C9CD81A6C6835AD09F209AF8F2838 | SHA256:BD188FD6B52897F4F1780053F8CA12644951443F46F4AFB0B9E1DDF3ABBD0709 | |||
| 4652 | DeviceCensus.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:F6F53CD09A41E968C363419B279D3112 | SHA256:6D2BB01CC7A9BADE2113B219CAC1BDA86B2733196B7E1BD0C807CE1E396B1892 | |||
| 4652 | DeviceCensus.exe | C:\Users\admin\AppData\Local\D3DSCache\637f029a71589346\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.val | binary | |
MD5:389B1B6CFF9A5CBAB35F7BAB1C8573F4 | SHA256:FD2AB0D35B7D33D4910E082611C6C0C267FA5DFB5E8E4432C91737B93FA34741 | |||
| 4164 | WinRAR.exe | C:\Users\admin\Desktop\autoplay.png | image | |
MD5:652BD40B1FDCF2964D218E98B8E3A460 | SHA256:B20F8CD986A4A519123EA56D7936167C4FD294EF85929D3A663931B211D6CDC2 | |||
| 4164 | WinRAR.exe | C:\Users\admin\Desktop\callth.png | image | |
MD5:872B4D47C431245D85A2019E7308AB7F | SHA256:A9E08BDD619D2139372E5551E80ADE0FFF2487678F6AF1A4CB0459172D74F4FB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
27
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4652 | DeviceCensus.exe | GET | 200 | 2.16.164.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4652 | DeviceCensus.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7096 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7096 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6204 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4652 | DeviceCensus.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4652 | DeviceCensus.exe | 2.16.164.99:80 | — | Akamai International B.V. | NL | unknown |
4652 | DeviceCensus.exe | 95.101.149.131:80 | — | Akamai International B.V. | NL | unknown |
5064 | SearchApp.exe | 2.23.209.193:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1176 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |