| File name: | 32dd776765476810f31febf445dcd096 |
| Full analysis: | https://app.any.run/tasks/6d8c46ad-00b4-4960-984d-a212abcb43c2 |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2023, 04:38:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, PECompact2 compressed |
| MD5: | 32DD776765476810F31FEBF445DCD096 |
| SHA1: | ABE06E8B87C47BD667A33F48F435275633FF10FE |
| SHA256: | 0EBD2A7571FCC8CCD6A521263D56B4ED710EBC9A137303C735BCF17843B4B832 |
| SSDEEP: | 196608:BfgDDfLMYXqEev3cob+R4bg3W7U/YsSI3OZnAAYFYNyUT0A6dRfK:uPVFev3Pb+IsWNsSI2aaNy6sdRfK |
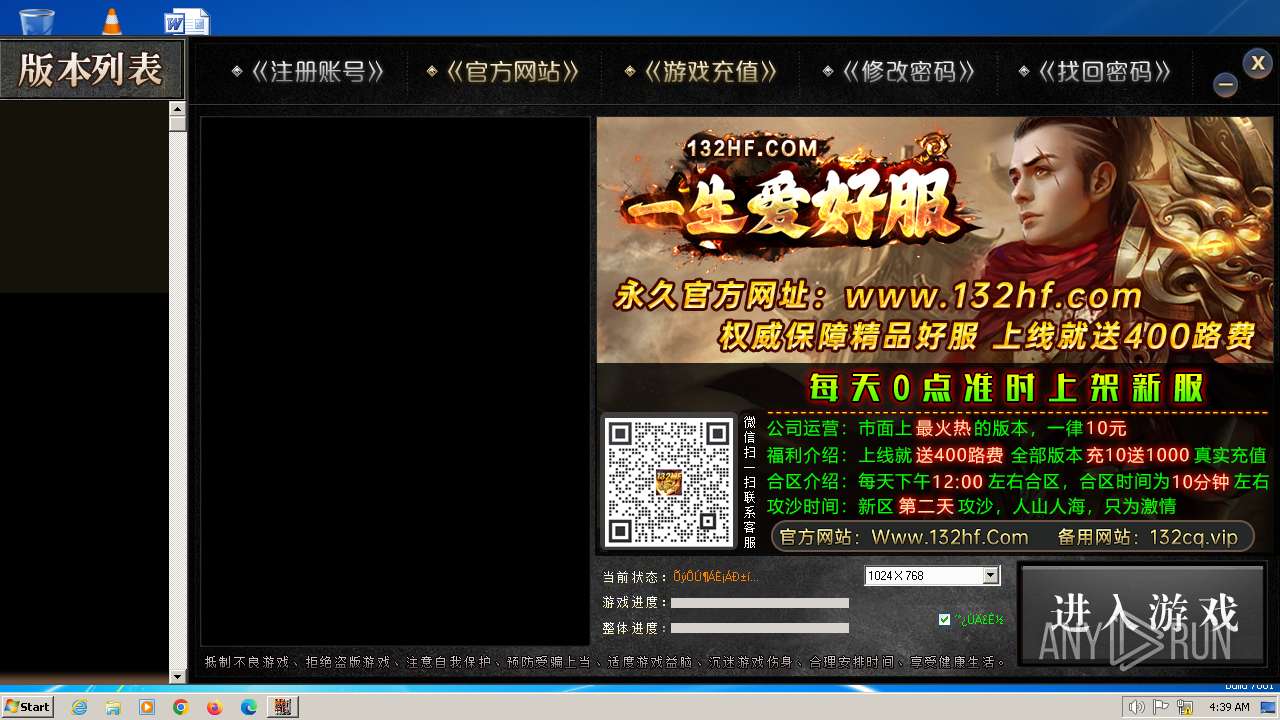
MALICIOUS
Drops the executable file immediately after the start
- mscorsvw.exe (PID: 2840)
- mscorsvw.exe (PID: 2180)
- mscorsvw.exe (PID: 1852)
- mscorsvw.exe (PID: 1776)
- mscorsvw.exe (PID: 1368)
- mscorsvw.exe (PID: 2532)
Creates a writable file in the system directory
- taskhost.exe (PID: 2096)
SUSPICIOUS
Process drops legitimate windows executable
- mscorsvw.exe (PID: 2840)
- mscorsvw.exe (PID: 2180)
- mscorsvw.exe (PID: 1852)
- mscorsvw.exe (PID: 2532)
- mscorsvw.exe (PID: 1776)
- mscorsvw.exe (PID: 1368)
Reads the Internet Settings
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
Connects to unusual port
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
Executes as Windows Service
- taskhost.exe (PID: 2096)
Reads Internet Explorer settings
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
Reads Microsoft Outlook installation path
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
Starts CMD.EXE for commands execution
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
INFO
Manual execution by a user
- mscorsvw.exe (PID: 1564)
- mscorsvw.exe (PID: 2840)
- mscorsvw.exe (PID: 2308)
- mscorsvw.exe (PID: 2740)
- mscorsvw.exe (PID: 1360)
- mscorsvw.exe (PID: 1456)
- mscorsvw.exe (PID: 608)
- mscorsvw.exe (PID: 1852)
- mscorsvw.exe (PID: 2988)
- mscorsvw.exe (PID: 3044)
- mscorsvw.exe (PID: 2532)
- mscorsvw.exe (PID: 2980)
- mscorsvw.exe (PID: 1928)
- mscorsvw.exe (PID: 2164)
- mscorsvw.exe (PID: 2252)
- mscorsvw.exe (PID: 1776)
- mscorsvw.exe (PID: 1884)
- mscorsvw.exe (PID: 1120)
- mscorsvw.exe (PID: 1368)
- mscorsvw.exe (PID: 2180)
- 32dd776765476810f31febf445dcd096.exe (PID: 2460)
Checks supported languages
- mscorsvw.exe (PID: 1564)
- mscorsvw.exe (PID: 2308)
- mscorsvw.exe (PID: 2980)
- mscorsvw.exe (PID: 2180)
- mscorsvw.exe (PID: 1360)
- mscorsvw.exe (PID: 1456)
- mscorsvw.exe (PID: 608)
- mscorsvw.exe (PID: 2988)
- mscorsvw.exe (PID: 1852)
- mscorsvw.exe (PID: 3044)
- mscorsvw.exe (PID: 2532)
- mscorsvw.exe (PID: 1928)
- mscorsvw.exe (PID: 2252)
- mscorsvw.exe (PID: 1776)
- mscorsvw.exe (PID: 2740)
- mscorsvw.exe (PID: 1884)
- mscorsvw.exe (PID: 1120)
- mscorsvw.exe (PID: 1368)
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
- mscorsvw.exe (PID: 2164)
- mscorsvw.exe (PID: 2840)
Reads the computer name
- mscorsvw.exe (PID: 1564)
- mscorsvw.exe (PID: 2840)
- mscorsvw.exe (PID: 2308)
- mscorsvw.exe (PID: 2740)
- mscorsvw.exe (PID: 2980)
- mscorsvw.exe (PID: 1360)
- mscorsvw.exe (PID: 2180)
- mscorsvw.exe (PID: 1456)
- mscorsvw.exe (PID: 1852)
- mscorsvw.exe (PID: 608)
- mscorsvw.exe (PID: 2988)
- mscorsvw.exe (PID: 3044)
- mscorsvw.exe (PID: 2532)
- mscorsvw.exe (PID: 1928)
- mscorsvw.exe (PID: 2252)
- mscorsvw.exe (PID: 2164)
- mscorsvw.exe (PID: 1776)
- mscorsvw.exe (PID: 1884)
- mscorsvw.exe (PID: 1120)
- mscorsvw.exe (PID: 1368)
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
Reads the machine GUID from the registry
- mscorsvw.exe (PID: 1564)
- mscorsvw.exe (PID: 2840)
- mscorsvw.exe (PID: 2308)
- mscorsvw.exe (PID: 1360)
- mscorsvw.exe (PID: 2980)
- mscorsvw.exe (PID: 2180)
- mscorsvw.exe (PID: 1456)
- mscorsvw.exe (PID: 608)
- mscorsvw.exe (PID: 1852)
- mscorsvw.exe (PID: 2988)
- mscorsvw.exe (PID: 3044)
- mscorsvw.exe (PID: 2532)
- mscorsvw.exe (PID: 2740)
- mscorsvw.exe (PID: 2164)
- mscorsvw.exe (PID: 1776)
- mscorsvw.exe (PID: 1884)
- mscorsvw.exe (PID: 1120)
- mscorsvw.exe (PID: 2252)
- mscorsvw.exe (PID: 1368)
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
- mscorsvw.exe (PID: 1928)
Create files in a temporary directory
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
Checks proxy server information
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
Creates files or folders in the user directory
- 32dd776765476810f31febf445dcd096.exe (PID: 2760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:26 16:43:32+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 1257472 |
| InitializedDataSize: | 25063424 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
273
Monitored processes
26
Malicious processes
1
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 608 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 258 -InterruptEvent 280 -NGENProcess 23c -Pipe 314 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | — | mscorsvw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 608 | cmd /c del "C:\Users\admin\AppData\Local\Temp\*.dll" | C:\Windows\SysWOW64\cmd.exe | — | 32dd776765476810f31febf445dcd096.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1120 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 23c -InterruptEvent 194 -NGENProcess 278 -Pipe 284 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | — | mscorsvw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1304 | cmd /c del "C:\Users\admin\AppData\Local\Temp\*d776765476810f31febf445dcd096.exe" | C:\Windows\SysWOW64\cmd.exe | — | 32dd776765476810f31febf445dcd096.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1360 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 288 -InterruptEvent 268 -NGENProcess 23c -Pipe 240 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | — | mscorsvw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1368 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 194 -InterruptEvent 28c -NGENProcess 2a0 -Pipe 2cc -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | — | mscorsvw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1456 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 284 -InterruptEvent 258 -NGENProcess 288 -Pipe 2e4 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | — | mscorsvw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1564 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 23c -InterruptEvent 240 -NGENProcess 258 -Pipe 25c -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | — | mscorsvw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1776 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 22c -InterruptEvent 27c -NGENProcess 23c -Pipe 2bc -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | — | mscorsvw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1852 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 280 -InterruptEvent 27c -NGENProcess 270 -Pipe 260 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | — | mscorsvw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
2 805
Read events
2 793
Write events
12
Delete events
0
Modification events
| (PID) Process: | (2760) 32dd776765476810f31febf445dcd096.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2760) 32dd776765476810f31febf445dcd096.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2760) 32dd776765476810f31febf445dcd096.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2760) 32dd776765476810f31febf445dcd096.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2760) 32dd776765476810f31febf445dcd096.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2760) 32dd776765476810f31febf445dcd096.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000C5000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2760) 32dd776765476810f31febf445dcd096.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2760) 32dd776765476810f31febf445dcd096.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
12
Suspicious files
21
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1852 | mscorsvw.exe | C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Web.Mobile\bba235befc5106f3f07e0930960d5a71\System.Web.Mobile.ni.dll.aux.tmp | binary | |
MD5:F01E86CC073989C35C338E9AB628EE0B | SHA256:4D6D0E59AB2C2C35658F567B1D71AFE423A66BC7F14BF7B93D744BE32F397A2A | |||
| 1852 | mscorsvw.exe | C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Web.Mobile\bba235befc5106f3f07e0930960d5a71\System.Web.Mobile.ni.dll.aux | binary | |
MD5:F01E86CC073989C35C338E9AB628EE0B | SHA256:4D6D0E59AB2C2C35658F567B1D71AFE423A66BC7F14BF7B93D744BE32F397A2A | |||
| 1852 | mscorsvw.exe | C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Web.Mobile\bba235befc5106f3f07e0930960d5a71\System.Web.Mobile.ni.dll | executable | |
MD5:291F3B0B110581D444F3ABE244B367DC | SHA256:A11B6BCA2FDFF73259D030EDB5D8CFA4839A96FFAA473F56ECAA818544A9A573 | |||
| 2180 | mscorsvw.exe | C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Web.dc83ace6#\1e6861aeb297c08ccefa17d23416d1b3\System.Web.Extensions.Design.ni.dll.aux.tmp | pgc | |
MD5:BECD4EFC5391D24CB2F5ED7C3E9B3157 | SHA256:BB29AEF3828B505E4CEF64319A5D5A0CCBA7E1E4A901D0FE8FE5280EBF766578 | |||
| 1368 | mscorsvw.exe | C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Wind0de890be#\d3767569dd31e72906224c47d8a3eee0\System.Windows.Forms.DataVisualization.ni.dll | executable | |
MD5:A4014D0E085880F9CA7169A4D551E62F | SHA256:CF8A1E4052F1D6E52D62389A5E5EC2A7A0D4E43F0B3B43CA1D55B6F8C0B34D1C | |||
| 2180 | mscorsvw.exe | C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Web.dc83ace6#\1e6861aeb297c08ccefa17d23416d1b3\System.Web.Extensions.Design.ni.dll.aux | binary | |
MD5:BECD4EFC5391D24CB2F5ED7C3E9B3157 | SHA256:BB29AEF3828B505E4CEF64319A5D5A0CCBA7E1E4A901D0FE8FE5280EBF766578 | |||
| 1776 | mscorsvw.exe | C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Wind412bbddf#\f499b26506a9e3448df012895f28c137\System.Windows.Controls.Ribbon.ni.dll | executable | |
MD5:6FFC09184CCFB42832B9391BB931E543 | SHA256:0D6EB12F5EBB827C6C93BC1696F710FB25439B84C7389C421A5366C1B39B7890 | |||
| 2532 | mscorsvw.exe | C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Web.Routing\57f2eb187fbbfe1f1ab405edafb08a29\System.Web.Routing.ni.dll.aux.tmp | binary | |
MD5:E9B4F3678C7D4F9D6D9624666F66F160 | SHA256:7594DD39B7F2585E5E33589BA73E36E684749BF46174BB29306CA3FEEBFCC3AC | |||
| 1776 | mscorsvw.exe | C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Wind412bbddf#\f499b26506a9e3448df012895f28c137\System.Windows.Controls.Ribbon.ni.dll.aux.tmp | binary | |
MD5:0376147C030686BF9B27C10A6C007351 | SHA256:E4EF6CC2C2284040CDCEC4BC6DA6B20FCCE2D508509C47450CD76F9AB00E6355 | |||
| 2532 | mscorsvw.exe | C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Web.Routing\57f2eb187fbbfe1f1ab405edafb08a29\System.Web.Routing.ni.dll.aux | binary | |
MD5:E9B4F3678C7D4F9D6D9624666F66F160 | SHA256:7594DD39B7F2585E5E33589BA73E36E684749BF46174BB29306CA3FEEBFCC3AC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
16
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2760 | 32dd776765476810f31febf445dcd096.exe | GET | 200 | 188.114.96.3:80 | http://www.htdlq.com/bmd.txt | unknown | text | 1.22 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1220 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
352 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2760 | 32dd776765476810f31febf445dcd096.exe | 188.114.96.3:80 | www.htdlq.com | CLOUDFLARENET | NL | unknown |
2760 | 32dd776765476810f31febf445dcd096.exe | 154.222.224.99:7000 | a.0qsf.com | STARCLOUD GLOBAL PTE., LTD. | SC | unknown |
2760 | 32dd776765476810f31febf445dcd096.exe | 140.210.19.174:2699 | — | CHINATELECOM JiangSu YangZhou IDC networkdescr: YangZhouJiangsu Province, P.R.China. | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.htdlq.com |
| unknown |
a.0qsf.com |
| unknown |