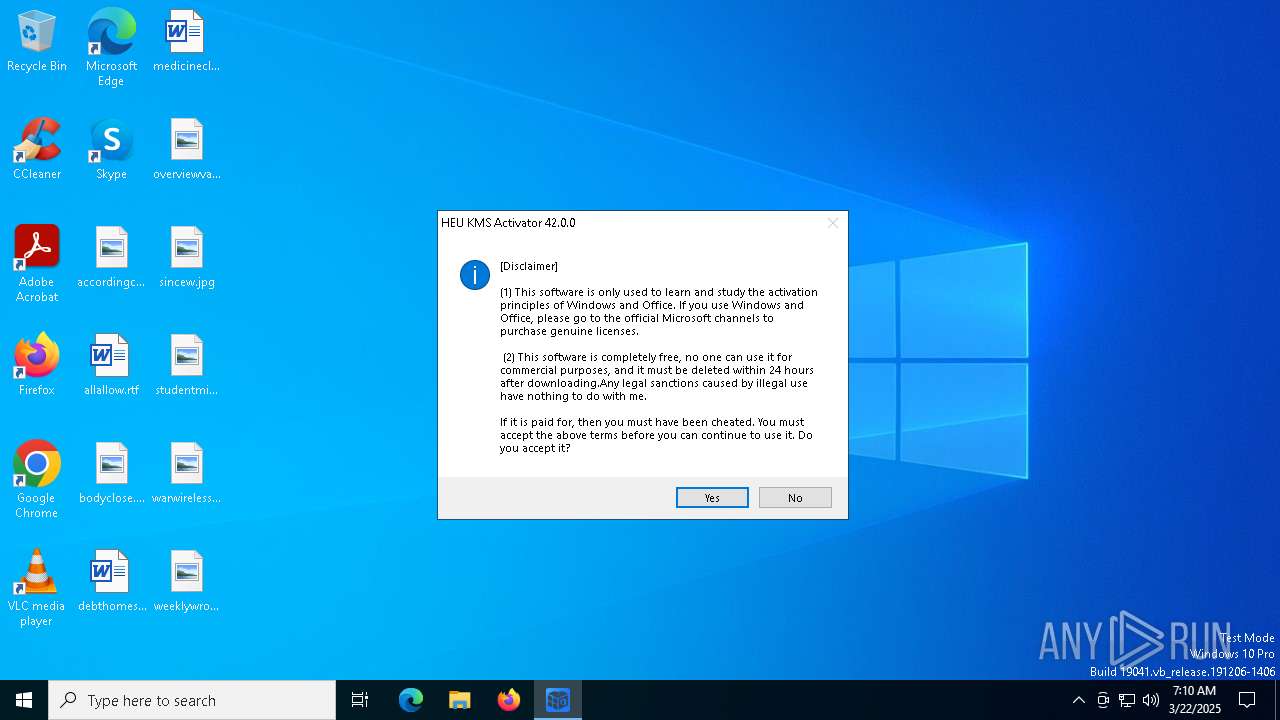
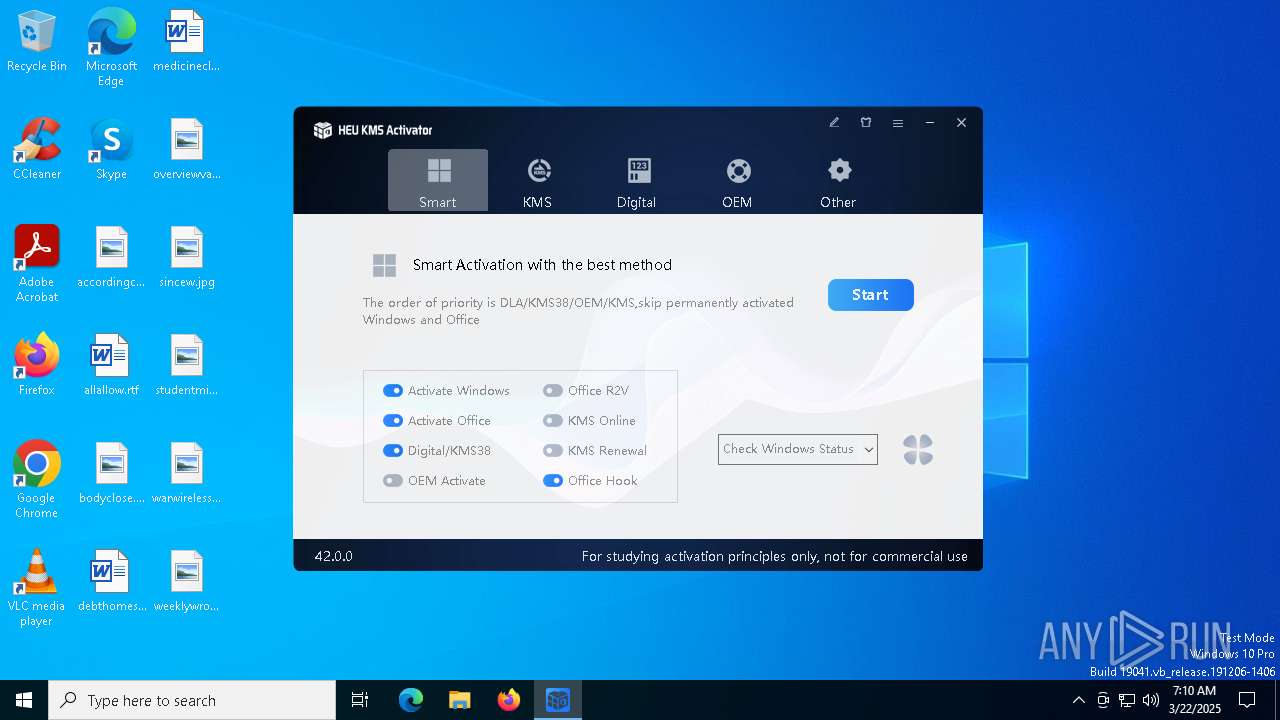
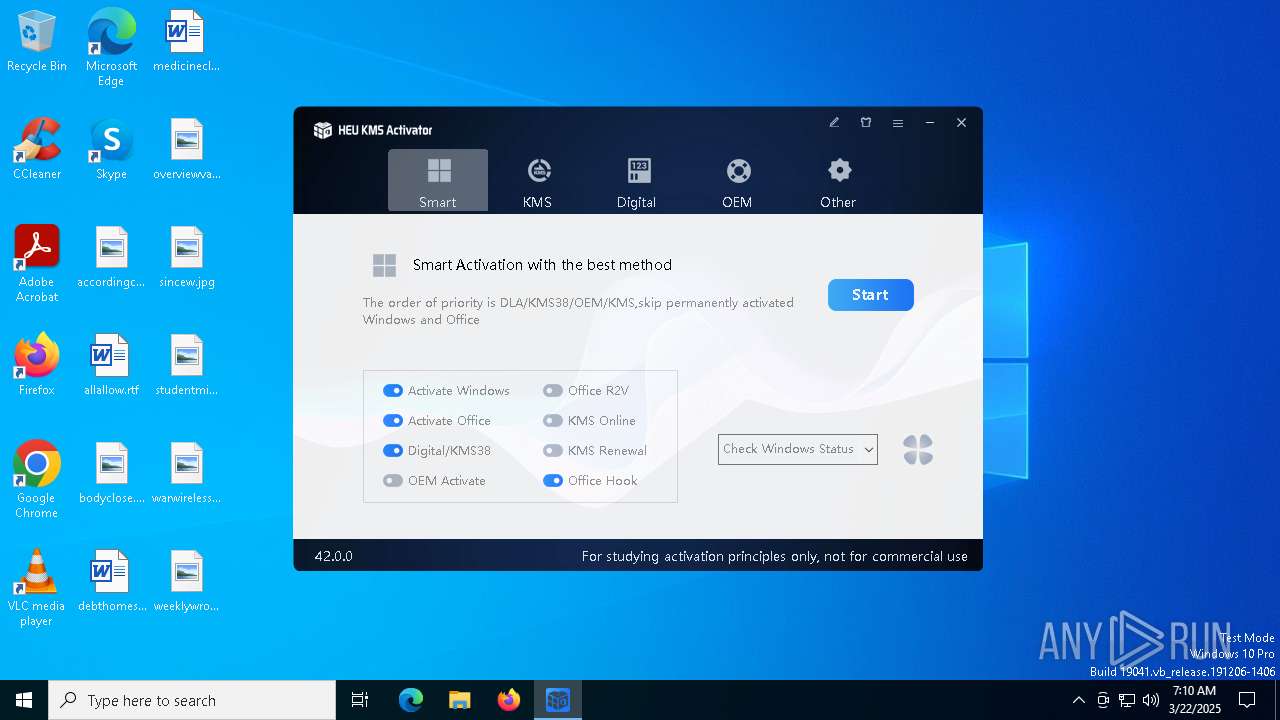
| File name: | HEU KMS Activator 42.exe |
| Full analysis: | https://app.any.run/tasks/b007c8bb-c443-4c69-a756-c4b32d8a39e6 |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2025, 07:09:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 820A4C7E7786AA77B6EB06D1081C9821 |
| SHA1: | 673264E81C920C2E84A219CB4257249523B9E902 |
| SHA256: | 0EBA428EEDC5D77A7BCB424235B5F01C8F71AAFF1CDF31A955CA79BC30CD1FE3 |
| SSDEEP: | 98304:GP/mp7t3T4+B/btosJwIA4hHmZlKH2Tw/Pq83zw0bCjvkMc5qrmpxYLkdZfp9an4:/T9B2Bv |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 5868)
- net.exe (PID: 5668)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- HEU KMS Activator 42.exe (PID: 2980)
Executable content was dropped or overwritten
- HEU KMS Activator 42.exe (PID: 2980)
- 7Z.EXE (PID: 1116)
Drops 7-zip archiver for unpacking
- HEU KMS Activator 42.exe (PID: 2980)
Detected use of alternative data streams (AltDS)
- kms_x64.exe (PID: 5800)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 5608)
- cscript.exe (PID: 5228)
Windows service management via SC.EXE
- sc.exe (PID: 3008)
- sc.exe (PID: 4224)
- sc.exe (PID: 920)
- sc.exe (PID: 4784)
- sc.exe (PID: 4464)
- sc.exe (PID: 1240)
- sc.exe (PID: 2108)
- sc.exe (PID: 6768)
- sc.exe (PID: 4428)
- sc.exe (PID: 6044)
- sc.exe (PID: 4688)
- sc.exe (PID: 4212)
- sc.exe (PID: 1348)
Starts CMD.EXE for commands execution
- kms_x64.exe (PID: 5800)
Starts SC.EXE for service management
- cmd.exe (PID: 780)
- cmd.exe (PID: 5552)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 5436)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 1052)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 5376)
- cmd.exe (PID: 5868)
- cmd.exe (PID: 1280)
- cmd.exe (PID: 472)
Application launched itself
- ClipUp.exe (PID: 6404)
INFO
The process uses AutoIt
- HEU KMS Activator 42.exe (PID: 2980)
The sample compiled with chinese language support
- HEU KMS Activator 42.exe (PID: 2980)
- 7Z.EXE (PID: 1116)
Create files in a temporary directory
- HEU KMS Activator 42.exe (PID: 2980)
- 7Z.EXE (PID: 1116)
- kms_x64.exe (PID: 5800)
- ClipUp.exe (PID: 6736)
Reads mouse settings
- HEU KMS Activator 42.exe (PID: 2980)
- kms_x64.exe (PID: 5800)
Checks supported languages
- HEU KMS Activator 42.exe (PID: 2980)
- 7Z.EXE (PID: 1116)
- kms_x64.exe (PID: 5800)
Reads the computer name
- HEU KMS Activator 42.exe (PID: 2980)
- 7Z.EXE (PID: 1116)
- kms_x64.exe (PID: 5800)
The sample compiled with english language support
- HEU KMS Activator 42.exe (PID: 2980)
Reads security settings of Internet Explorer
- cscript.exe (PID: 5608)
- cscript.exe (PID: 5228)
Reads product name
- kms_x64.exe (PID: 5800)
Reads Environment values
- kms_x64.exe (PID: 5800)
Process checks computer location settings
- kms_x64.exe (PID: 5800)
Creates files in the program directory
- kms_x64.exe (PID: 5800)
- ClipUp.exe (PID: 6736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (44) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.3) |
| .exe | | | Win32 Executable (generic) (7.1) |
| .exe | | | Generic Win/DOS Executable (3.1) |
| .exe | | | DOS Executable Generic (3.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:15 16:28:12+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 633856 |
| InitializedDataSize: | 4678144 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20577 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 42.0.0.0 |
| ProductVersionNumber: | 42.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 42.0.0.0 |
| Comments: | KMS/数字权利/KMS38/OEM激活 |
| FileDescription: | HEU KMS Activator™ |
| ProductVersion: | 42.0.0.0 |
| LegalCopyright: | 知彼而知己 |
| Productname: | HEU KMS Activator |
| CompanyName: | 知彼而知己 |
| OriginalFileName: | HEU_KMS_Activator_v42.0.0 |
| InternalName: | HEU_KMS_Activator_v42.0.0 |
Total processes
197
Monitored processes
61
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | C:\WINDOWS\system32\cmd.exe /c sc query Winmgmt | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ClipUp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | C:\WINDOWS\system32\cmd.exe /c sc query sppsvc | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | sc query ClipSVC | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | C:\WINDOWS\system32\cmd.exe /c C:\WINDOWS\System32\cscript.exe //nologo //Job:WmiQuery "C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\xml\wim.xml?.wsf" SoftwareLicensingService Version | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | C:\WINDOWS\system32\cmd.exe /c set "Path=%SystemRoot%;%SystemRoot%\system32;%SystemRoot%\System32\Wbem;%SystemRoot\System32\WindowsPowerShell\v1.0\" & Powershell Set-WinHomeLocation -GeoId 244 | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | C:\WINDOWS\system32\cmd.exe /c sc query wuauserv | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | "C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\7Z.EXE" x "C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\KMSmini.7z" -y -o"C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds" | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\7Z.EXE | HEU KMS Activator 42.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 19.00 Modules
| |||||||||||||||
Total events
1 516
Read events
1 516
Write events
0
Delete events
0
Modification events
Executable files
5
Suspicious files
8
Text files
88
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2980 | HEU KMS Activator 42.exe | C:\Users\admin\AppData\Local\Temp\autE9D5.tmp | binary | |
MD5:B14108CB199F86AA15351D2E9219412B | SHA256:9BCB98ECEF86ABEE7356CCC4038EDB370BC0CAD07AC15AD6FF73DAB6F90045F5 | |||
| 2980 | HEU KMS Activator 42.exe | C:\Users\admin\AppData\Local\Temp\autEC59.tmp | binary | |
MD5:E25E09DF3DB990F98A165990B2F48B02 | SHA256:52F64C84948068514240283D6C7FA1204E81CA0549CF0159FCACC556A950CD94 | |||
| 2980 | HEU KMS Activator 42.exe | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\7Z.EXE | executable | |
MD5:43141E85E7C36E31B52B22AB94D5E574 | SHA256:EA308C76A2F927B160A143D94072B0DCE232E04B751F0C6432A94E05164E716D | |||
| 1116 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\Office2010OSPP\OSPP.VBS | text | |
MD5:572E9A87757AC96C7677FD1B1B113C55 | SHA256:008CF05944053116A095AD466561D3FD4BE8A7DE79E5ADA7C5DAAB492F730465 | |||
| 1116 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\pic\1-2.bmp | image | |
MD5:F0B50CEB08E0E47410AB0486CFE18E13 | SHA256:1EC1312347FEE5A7CDDDA9D264B536F2A230DE13ACBD024A967FF9BD6D607A5B | |||
| 1116 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\pic\14-1.bmp | image | |
MD5:EA41C4B5B5A96B68758C993A24A80C38 | SHA256:F6E73C93CE3C964A9E8969EFF64BB12BD20685350B6DD8B2EF3D86F803DCBCC9 | |||
| 1116 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\OtherOfficeOSPP\slerror.xml | text | |
MD5:36F7DADFE84E62DA00292D0569C3F523 | SHA256:B3378A3178F3E52094DB20E8A828011CD8882017919522A544BAEF3057BD11D3 | |||
| 2980 | HEU KMS Activator 42.exe | C:\Users\admin\AppData\Local\Temp\splashlogo.jpg | image | |
MD5:2BC3F059E8A844879F91D900FFA6EFFB | SHA256:A222634FD0145551CFBDAAEB101421CDE0037E77A9A33DA407219B99CF0985E1 | |||
| 1116 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\OtherOfficeOSPP\OSPP.VBS | text | |
MD5:885B4DAE3623B427B8F04A7BC88780B9 | SHA256:6BC8E3991DA8C6527B3588E8F95068665918B685299CBB16BA6CC0C484BFE072 | |||
| 1116 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\pic\14-2.bmp | image | |
MD5:047F193F29ED38E689AC53BB6B879C46 | SHA256:FA993936D1682BBCE788E759BD1B2635B987E535ADAB6002792D0C316DF5863C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2284 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2644 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2644 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |