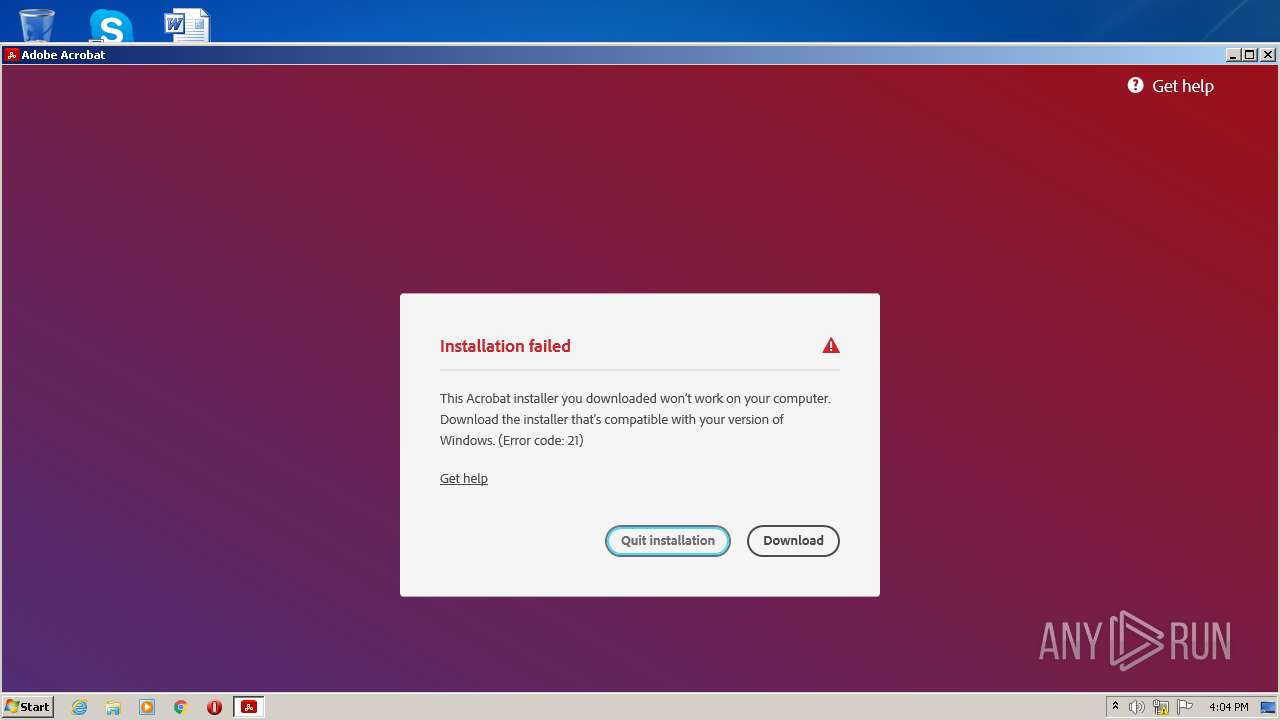
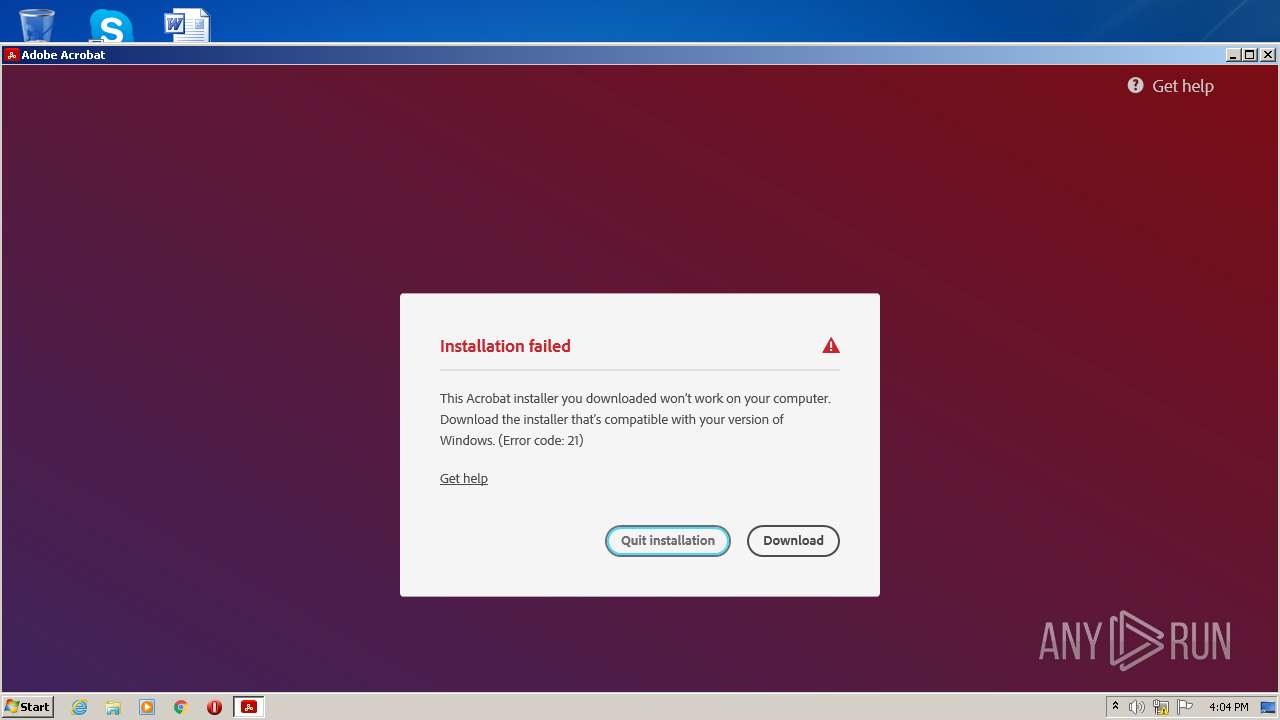
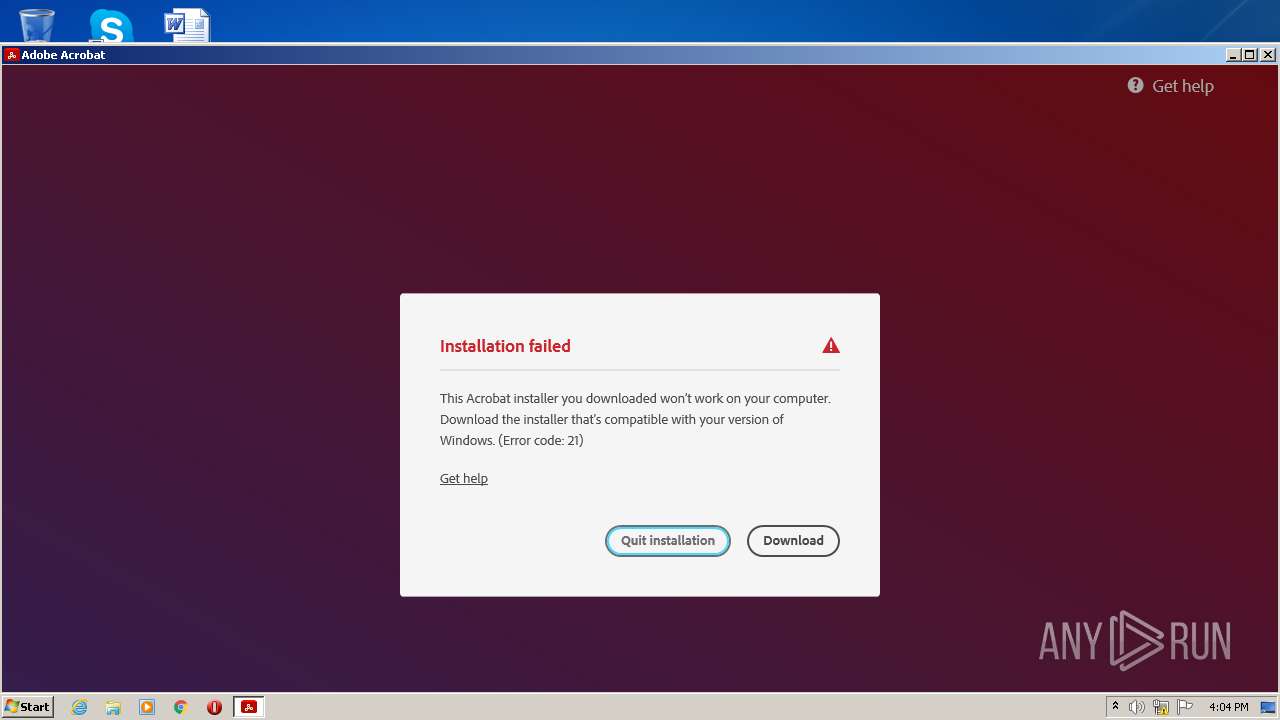
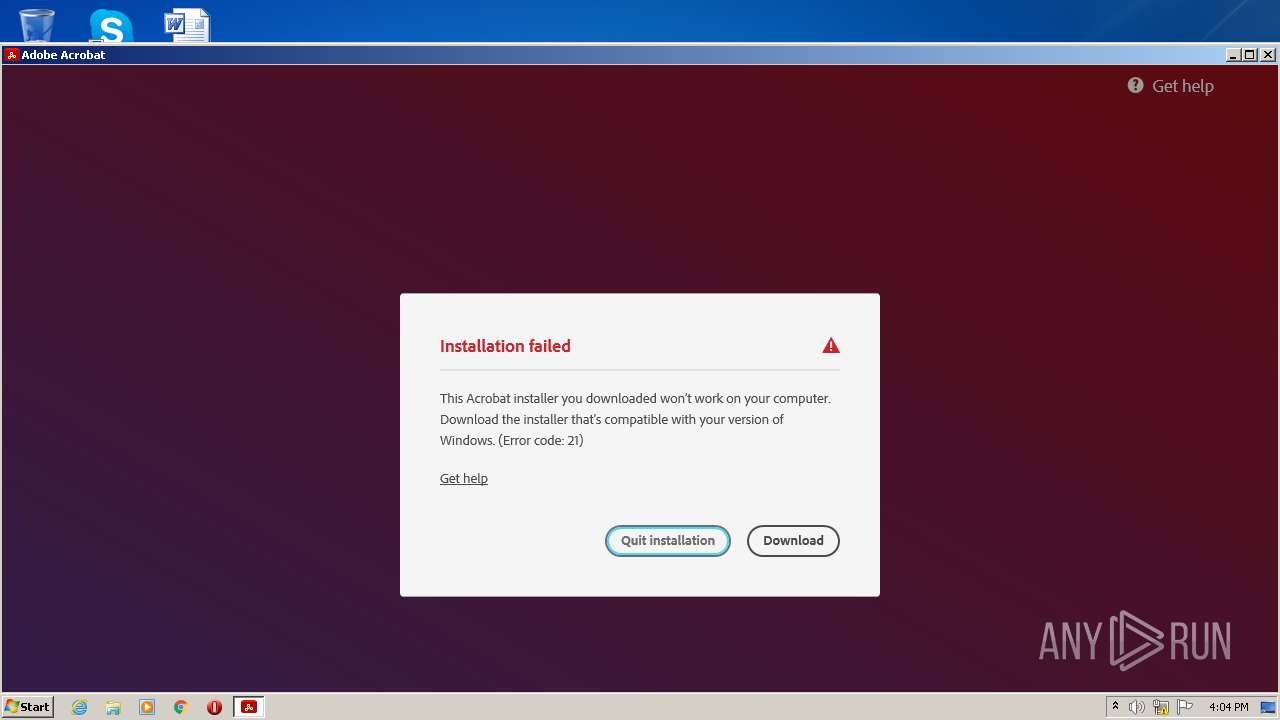
| File name: | Acrobat_Set-Up.exe |
| Full analysis: | https://app.any.run/tasks/8aaf2251-3685-47e0-ab9e-6392ade90e1a |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2023, 16:03:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | B92AA9934227DF899414B84EB4EF9109 |
| SHA1: | DB1FA7DA67D1326687D5DD7ABB4BAA944B3C1B8E |
| SHA256: | 0EB5B05BF2E74D1153974BCC64BBE10FD7393B7879503CBCF016E840EED515B9 |
| SSDEEP: | 49152:t51Z7F25DNGy3g9lRC8mk62yFjqGAuf75pqjf8jJPfs/kfwMflf0hchZgtyeU:t515F2W+8ClgduD59fVfwM/am |
MALICIOUS
LAPLASCLIPPER detected by memory dumps
- Acrobat_Set-Up.exe (PID: 2660)
SUSPICIOUS
Reads settings of System Certificates
- Acrobat_Set-Up.exe (PID: 2660)
Reads the Internet Settings
- Acrobat_Set-Up.exe (PID: 2660)
Reads Microsoft Outlook installation path
- Acrobat_Set-Up.exe (PID: 2660)
Reads Internet Explorer settings
- Acrobat_Set-Up.exe (PID: 2660)
Reads security settings of Internet Explorer
- Acrobat_Set-Up.exe (PID: 2660)
Checks Windows Trust Settings
- Acrobat_Set-Up.exe (PID: 2660)
INFO
Reads CPU info
- Acrobat_Set-Up.exe (PID: 2660)
Checks supported languages
- Acrobat_Set-Up.exe (PID: 2660)
The process checks LSA protection
- Acrobat_Set-Up.exe (PID: 2660)
Reads the computer name
- Acrobat_Set-Up.exe (PID: 2660)
Reads the machine GUID from the registry
- Acrobat_Set-Up.exe (PID: 2660)
Create files in a temporary directory
- Acrobat_Set-Up.exe (PID: 2660)
Creates files or folders in the user directory
- Acrobat_Set-Up.exe (PID: 2660)
Checks proxy server information
- Acrobat_Set-Up.exe (PID: 2660)
Process checks are UAC notifies on
- Acrobat_Set-Up.exe (PID: 2660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| ProductVersion: | 2.11.0.30 |
|---|---|
| ProductName: | Adobe Installer |
| OriginalFileName: | Adobe Installer |
| LegalCopyright: | © 2015-2023 Adobe. All rights reserved. |
| InternalName: | Adobe Installer |
| FileVersion: | 2.11.0.30 |
| FileDescription: | Adobe Installer |
| CompanyName: | Adobe Inc. |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Dynamic link library |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 2.11.0.30 |
| FileVersionNumber: | 2.11.0.30 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x938650 |
| UninitializedDataSize: | 6766592 |
| InitializedDataSize: | 45056 |
| CodeSize: | 2899968 |
| LinkerVersion: | 14.33 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2023:02:27 07:58:01+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 27-Feb-2023 07:58:01 |
| Detected languages: |
|
| CompanyName: | Adobe Inc. |
| FileDescription: | Adobe Installer |
| FileVersion: | 2.11.0.30 |
| InternalName: | Adobe Installer |
| LegalCopyright: | © 2015-2023 Adobe. All rights reserved. |
| OriginalFilename: | Adobe Installer |
| ProductName: | Adobe Installer |
| ProductVersion: | 2.11.0.30 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 27-Feb-2023 07:58:01 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00674000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00675000 | 0x002C4000 | 0x002C3A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.90065 |
.rsrc | 0x00939000 | 0x0000B000 | 0x0000AC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.82055 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.14505 | 1907 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 2.43487 | 16936 | UNKNOWN | English - United States | RT_ICON |
3 | 2.47851 | 9640 | UNKNOWN | English - United States | RT_ICON |
4 | 2.63372 | 4264 | UNKNOWN | English - United States | RT_ICON |
5 | 2.70876 | 2440 | UNKNOWN | English - United States | RT_ICON |
6 | 2.77188 | 1128 | UNKNOWN | English - United States | RT_ICON |
101 | 2.75765 | 90 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 7.33828 | 716 | UNKNOWN | English - United States | XML |
121 | 7.10177 | 426 | UNKNOWN | English - United States | RT_HTML |
122 | 0 | 939559 | UNKNOWN | English - United States | CSS |
Imports
KERNEL32.DLL |
WS2_32.dll |
urlmon.dll |
Total processes
36
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2660 | "C:\Users\admin\AppData\Local\Temp\Acrobat_Set-Up.exe" | C:\Users\admin\AppData\Local\Temp\Acrobat_Set-Up.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Installer Exit code: 0 Version: 2.11.0.30 Modules
| |||||||||||||||
Total events
7 346
Read events
7 274
Write events
72
Delete events
0
Modification events
| (PID) Process: | (2660) Acrobat_Set-Up.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2660) Acrobat_Set-Up.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2660) Acrobat_Set-Up.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2660) Acrobat_Set-Up.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2660) Acrobat_Set-Up.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2660) Acrobat_Set-Up.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2660) Acrobat_Set-Up.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2660) Acrobat_Set-Up.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2660) Acrobat_Set-Up.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{FCC67766-6201-4AD1-A6B8-2F4553C93D47} |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
| (PID) Process: | (2660) Acrobat_Set-Up.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{FCC67766-6201-4AD1-A6B8-2F4553C93D47} |
| Operation: | write | Name: | WpadDecisionTime |
Value: 6874D9F8D75CD901 | |||
Executable files
0
Suspicious files
8
Text files
10
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2660 | Acrobat_Set-Up.exe | C:\Users\admin\AppData\Roaming\com.adobe.dunamis\f65a88c9-12b3-4201-a633-87cf11b91fa8\v1\0\meta_events\0e3e6052-4431-4f46-b20d-6ccab5ee4d19 | — | |
MD5:— | SHA256:— | |||
| 2660 | Acrobat_Set-Up.exe | C:\Users\admin\AppData\Roaming\com.adobe.dunamis\f65a88c9-12b3-4201-a633-87cf11b91fa8\v1\0\anon_events\7ce3dfeb-d4a6-4852-899a-d59b9cfab26e | — | |
MD5:— | SHA256:— | |||
| 2660 | Acrobat_Set-Up.exe | C:\Users\admin\AppData\Local\Adobe\OOBE\temp_lbs_wid | text | |
MD5:— | SHA256:— | |||
| 2660 | Acrobat_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\Adobe\com.adobe.dunamis\dunamis-2023-03-22_16-03-55.log | text | |
MD5:— | SHA256:— | |||
| 2660 | Acrobat_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\{F3DB6F74-8EE4-472B-B821-8B0954A9BBF6}\CCDInstaller.js | binary | |
MD5:18D4529E99A898E41B49178111EDC235 | SHA256:13C952C9DAB374EE2EF3DE41F2AB5F9D1B488F94F5400498E69BB18BC68BC00B | |||
| 2660 | Acrobat_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\{F3DB6F74-8EE4-472B-B821-8B0954A9BBF6}\index.html | html | |
MD5:A28AB17B18FF254173DFEEF03245EFD0 | SHA256:886C0AB69E6E9D9D5B5909451640EA587ACCFCDF11B8369CAD8542D1626AC375 | |||
| 2660 | Acrobat_Set-Up.exe | C:\Users\admin\AppData\Roaming\com.adobe.dunamis\f65a88c9-12b3-4201-a633-87cf11b91fa8\v1\0\anon_events\manifest | binary | |
MD5:335ECF8B087703C67A4831976CDD382C | SHA256:A0C08679CC6D6592ABCE004BB4CEC199AECDE68678E9B9A634C01DA37D58A7DD | |||
| 2660 | Acrobat_Set-Up.exe | C:\Users\admin\AppData\Roaming\com.adobe.dunamis\f65a88c9-12b3-4201-a633-87cf11b91fa8\v1\0\meta_events\manifest | binary | |
MD5:335ECF8B087703C67A4831976CDD382C | SHA256:A0C08679CC6D6592ABCE004BB4CEC199AECDE68678E9B9A634C01DA37D58A7DD | |||
| 2660 | Acrobat_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\dat1152.tmp | woff | |
MD5:D070306A9062178AFDFA98FCC06D2525 | SHA256:8F5CCDFD3DA9185D4AD262EC386EBB64B3EB6C0521EC5BD1662CEC04E1E0F895 | |||
| 2660 | Acrobat_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\dat1182.tmp | woff | |
MD5:E204643042591AEEC2043C5EAE255099 | SHA256:7F58F56A7A353F8FC78EC2757394A7C7F28165E6BBF2A37D6A6E48E845874F3E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
7
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2660 | Acrobat_Set-Up.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/DigiCertGlobalRootCA.crl | US | der | 779 b | whitelisted |
2660 | Acrobat_Set-Up.exe | GET | — | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | — | — | whitelisted |
2660 | Acrobat_Set-Up.exe | GET | — | 8.248.141.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8804322f625d53d5 | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2660 | Acrobat_Set-Up.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2660 | Acrobat_Set-Up.exe | 8.248.141.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
2660 | Acrobat_Set-Up.exe | 8.248.119.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
2660 | Acrobat_Set-Up.exe | 13.32.99.120:443 | client.messaging.adobe.com | AMAZON-02 | US | suspicious |
— | — | 13.32.99.75:443 | client.messaging.adobe.com | AMAZON-02 | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
client.messaging.adobe.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |