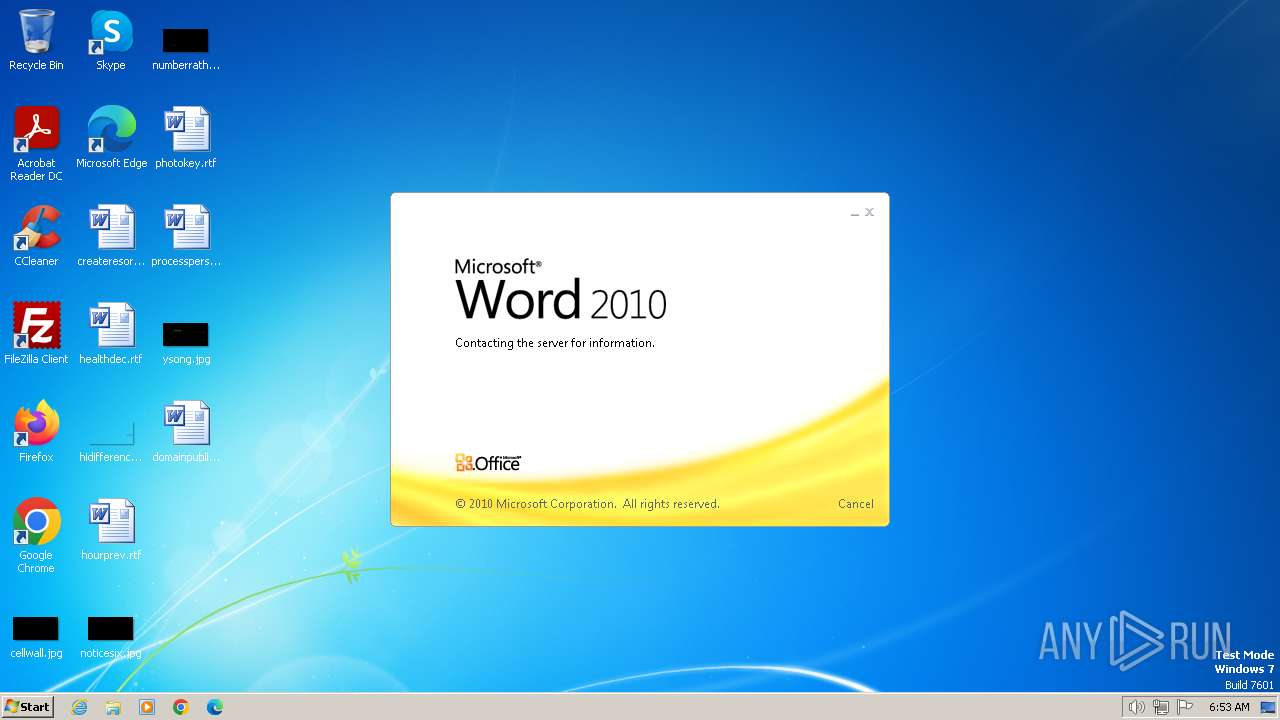
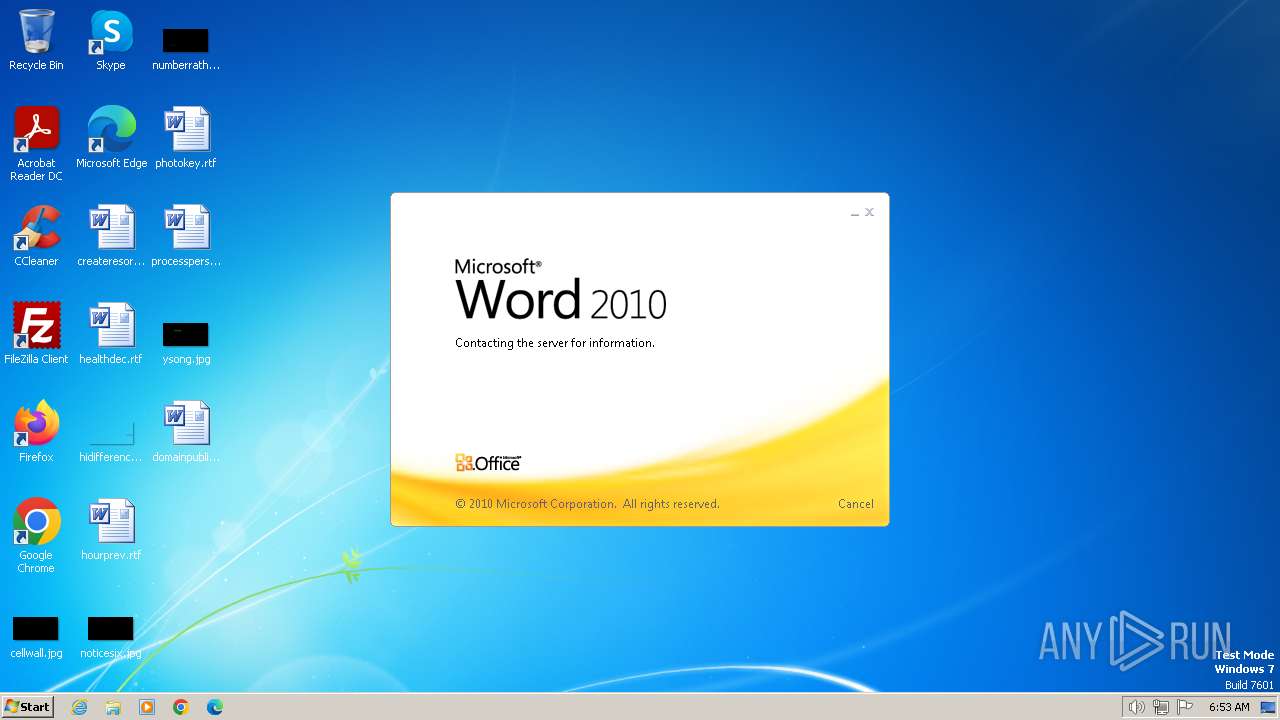
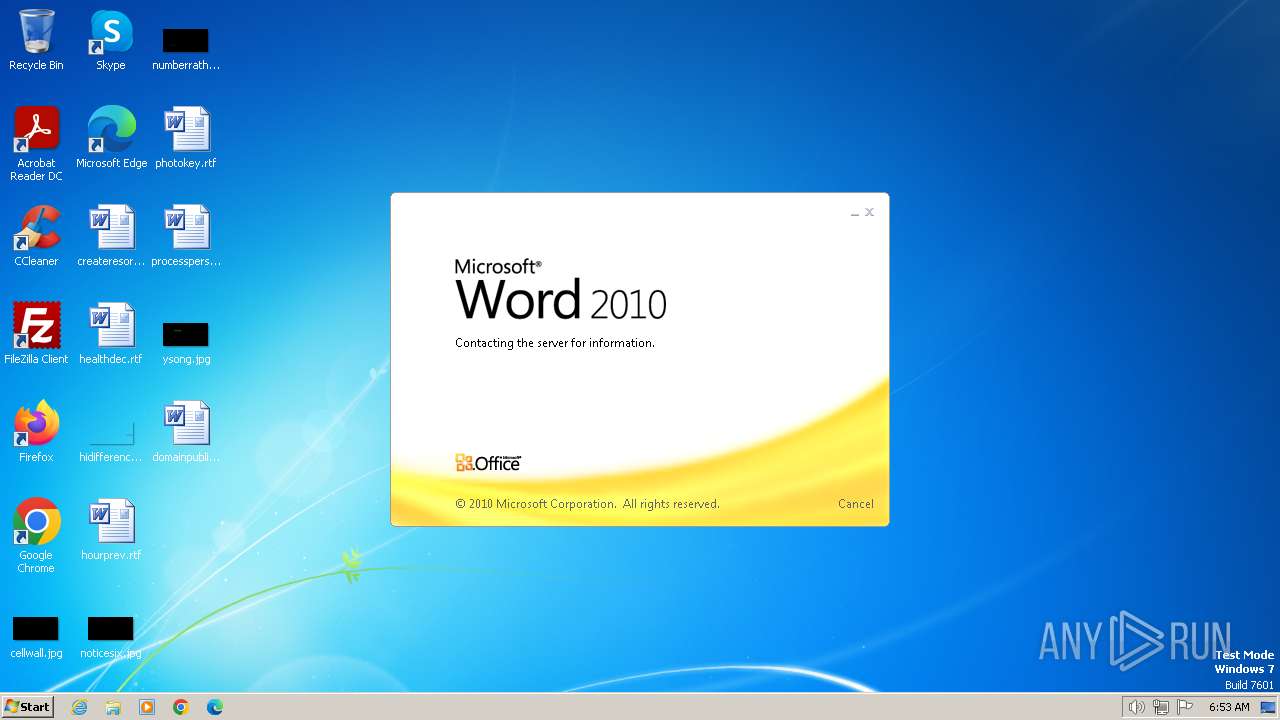
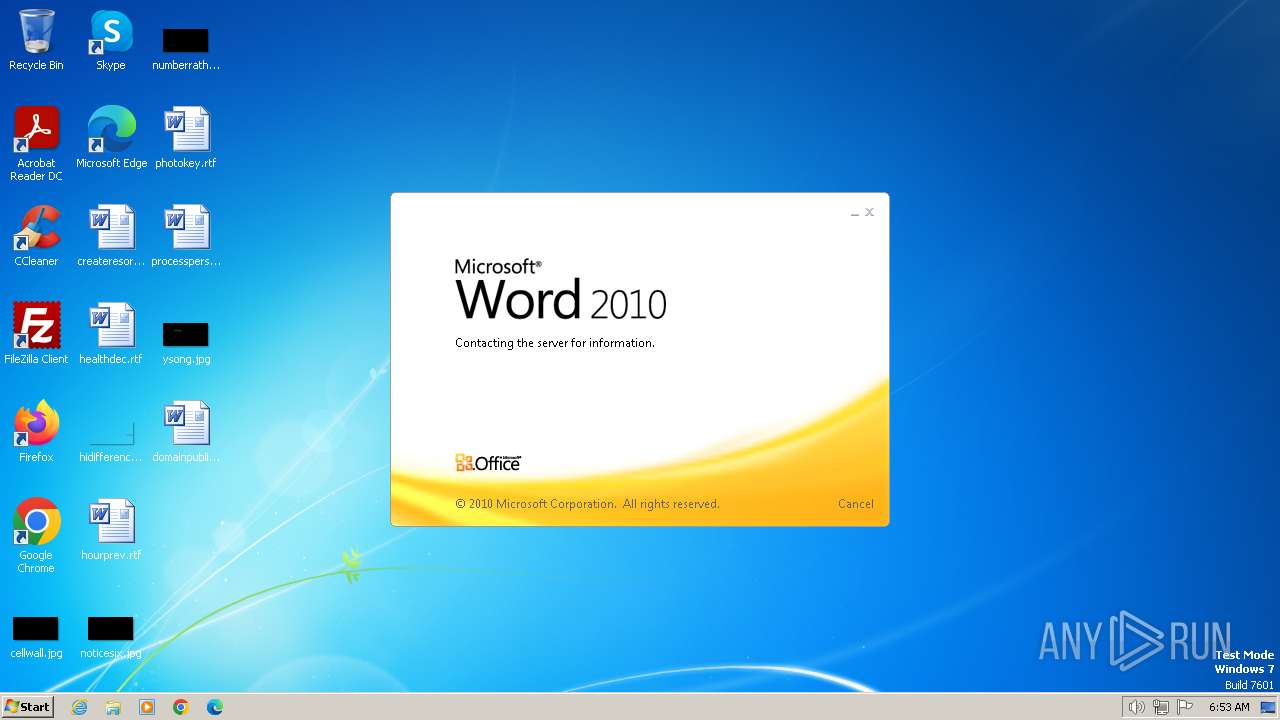
| File name: | DETAILS INFORMATION.docx |
| Full analysis: | https://app.any.run/tasks/1e28df13-345e-4545-bdfa-88a113b0b57e |
| Verdict: | Malicious activity |
| Analysis date: | April 18, 2024, 05:50:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | BB683A0E1B197CAB5DCE152E9355983F |
| SHA1: | 48DAB24779ECF13E3C130107E950514E46046C11 |
| SHA256: | 0EAB45741C6D3ABDB145B7C928D045DC77CF3DEF915D017ABC388C2C38DA8137 |
| SSDEEP: | 24576:NFHbaBI/wnSXQwTMQwT22n51B6iX6nhNLhKmQwTAZ:NFHbaBI/wnSXQwTMQwT22fB6iX6nhNLQ |
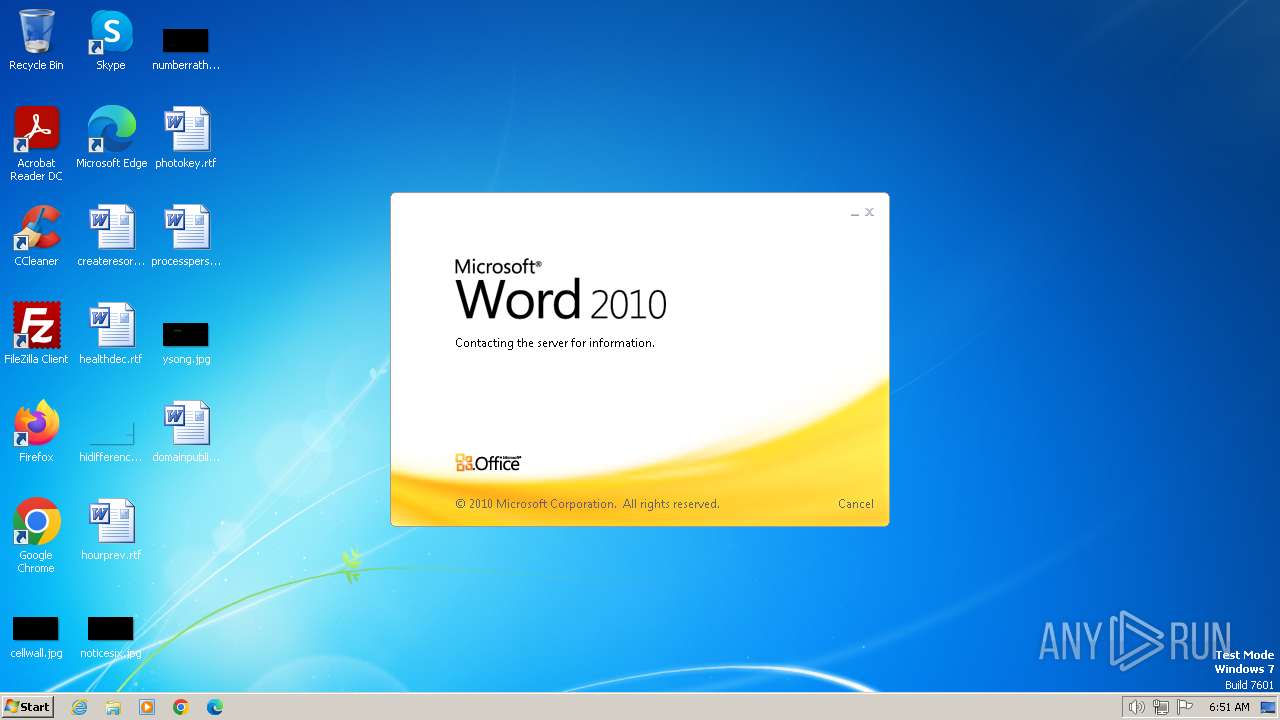
MALICIOUS
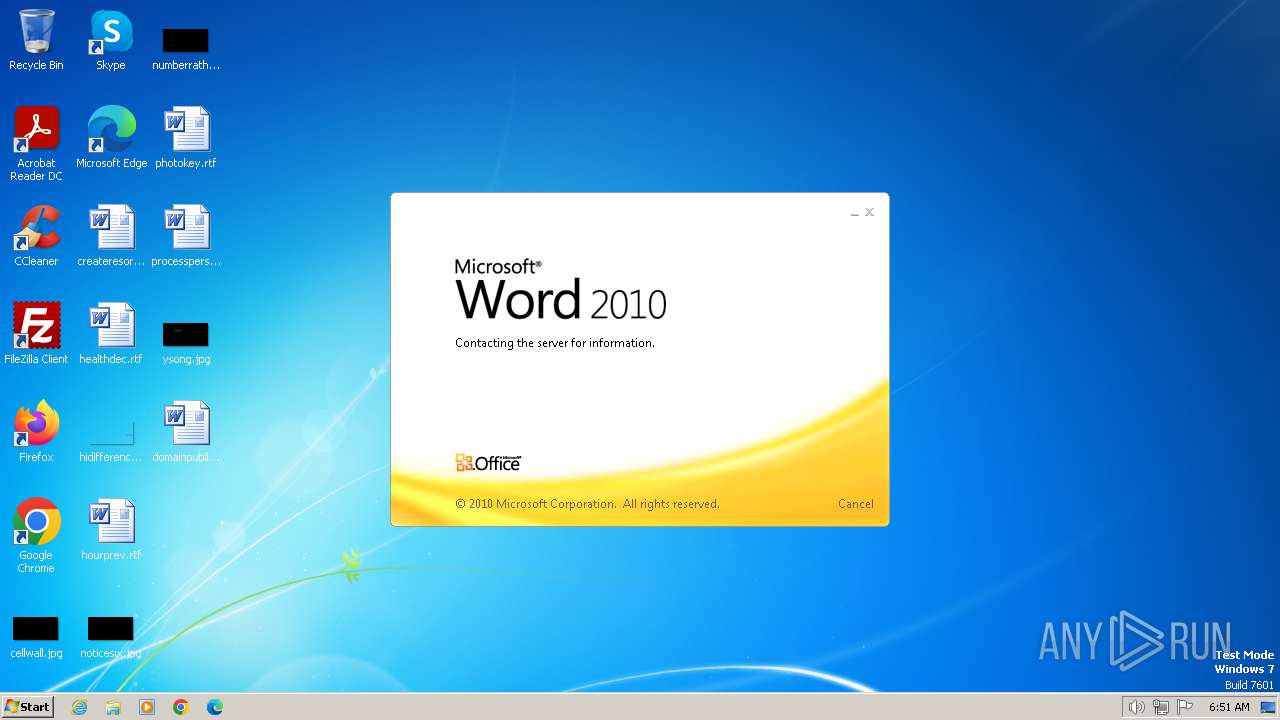
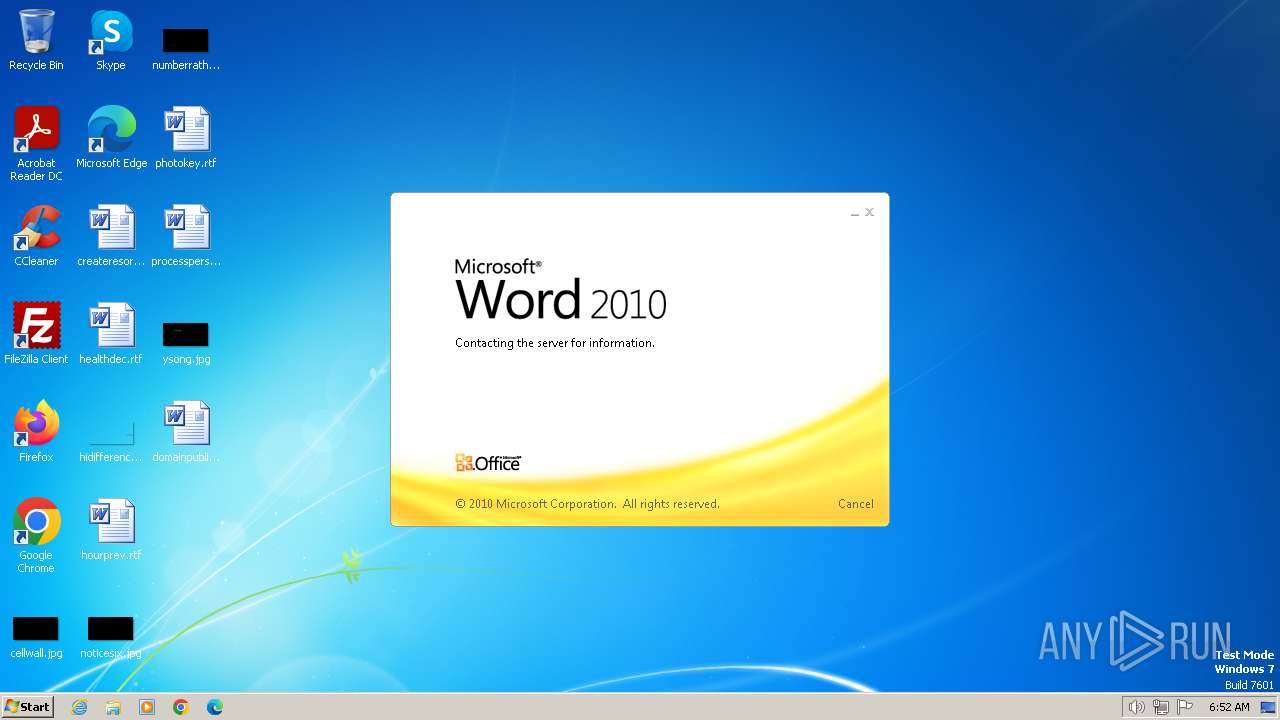
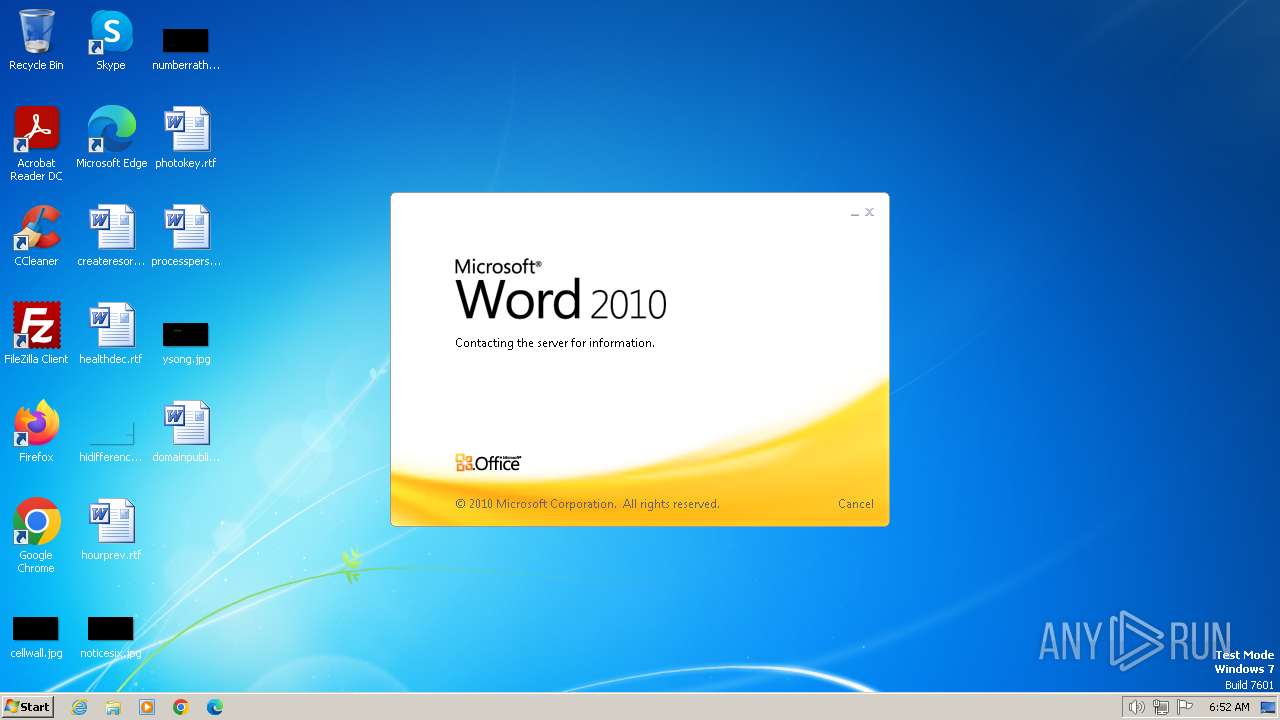
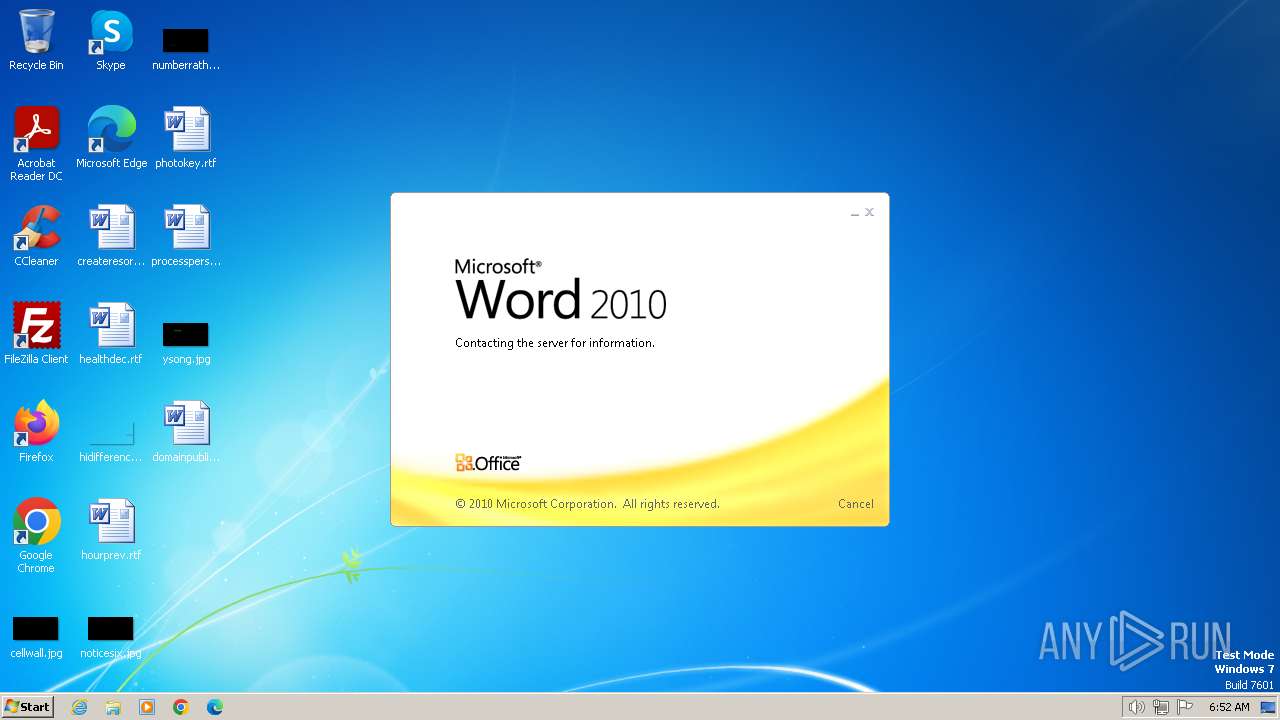
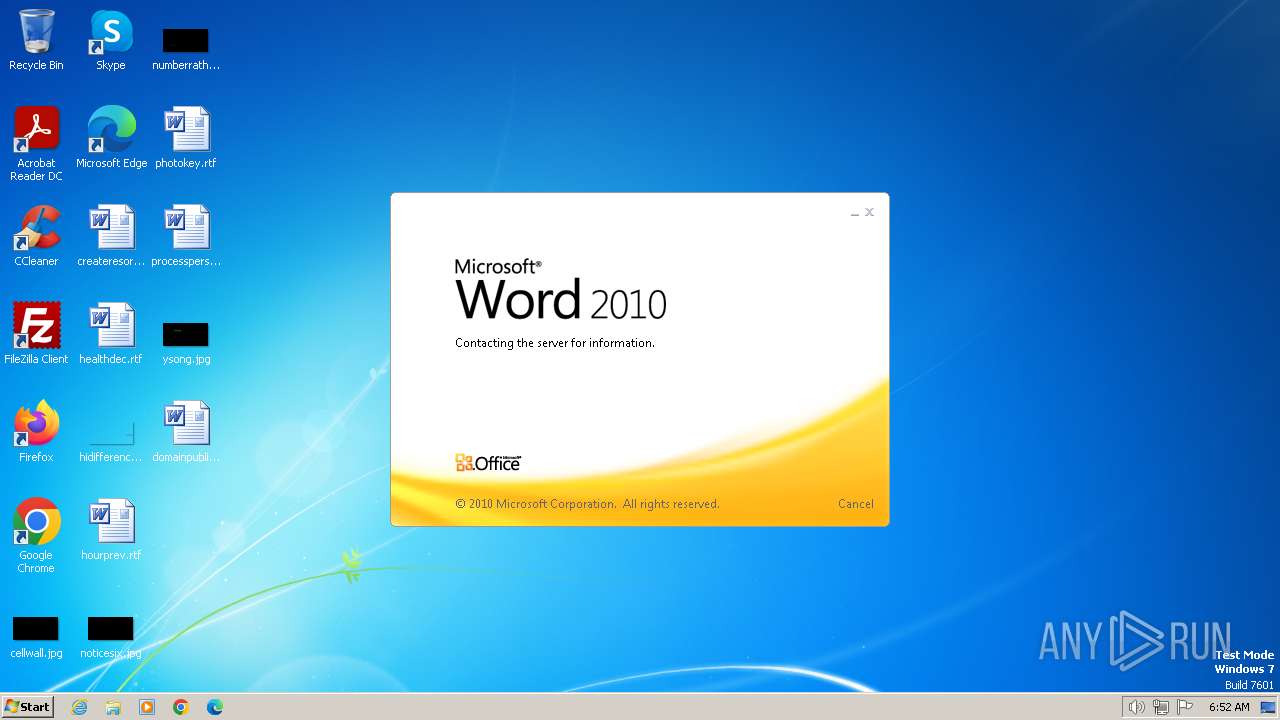
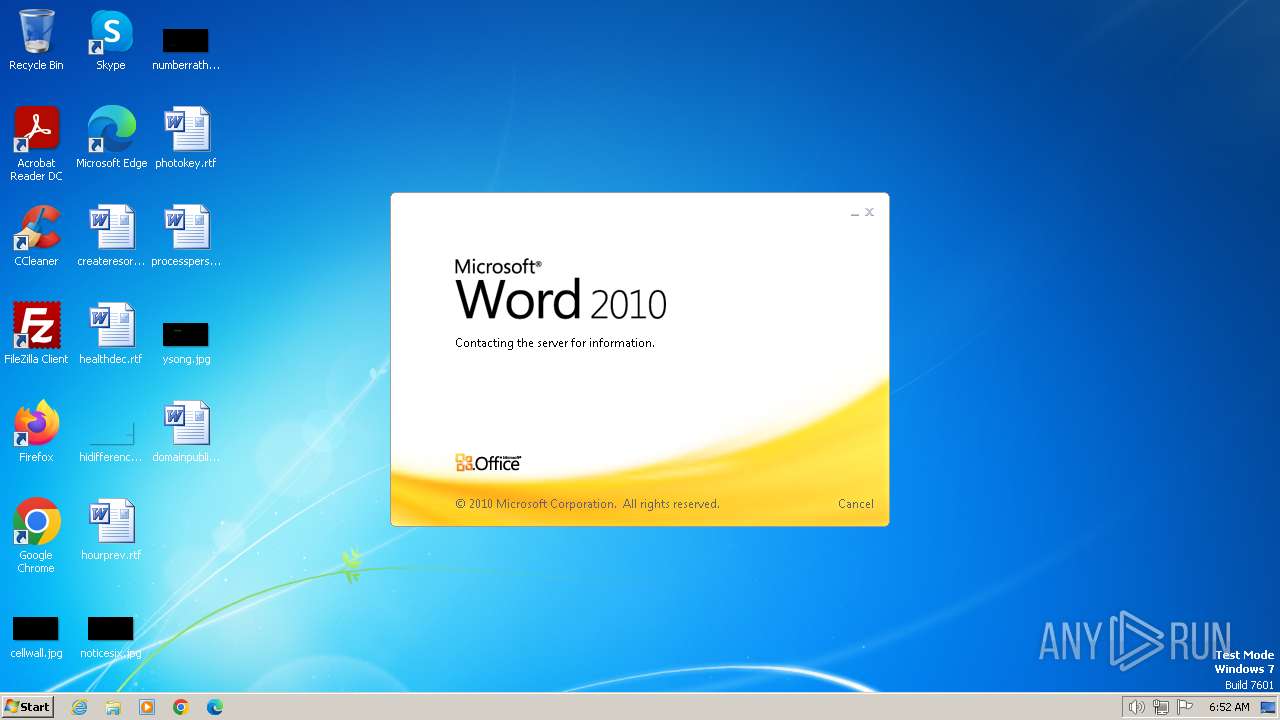
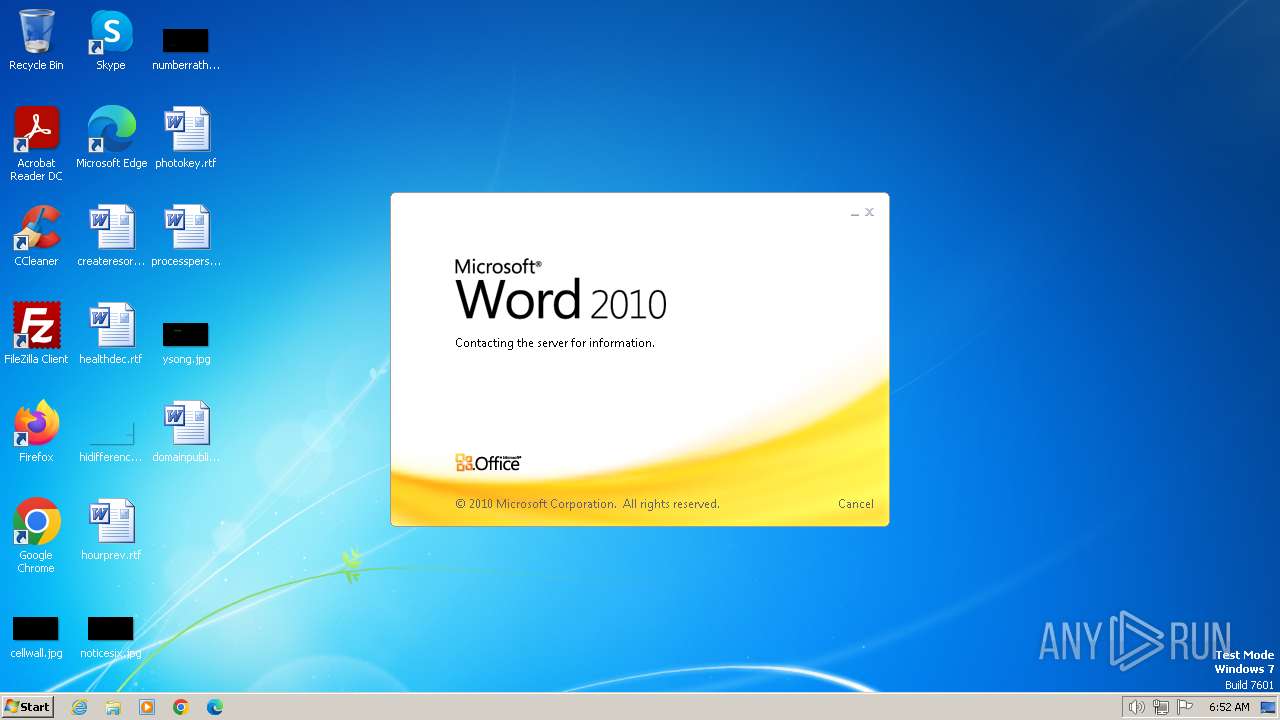
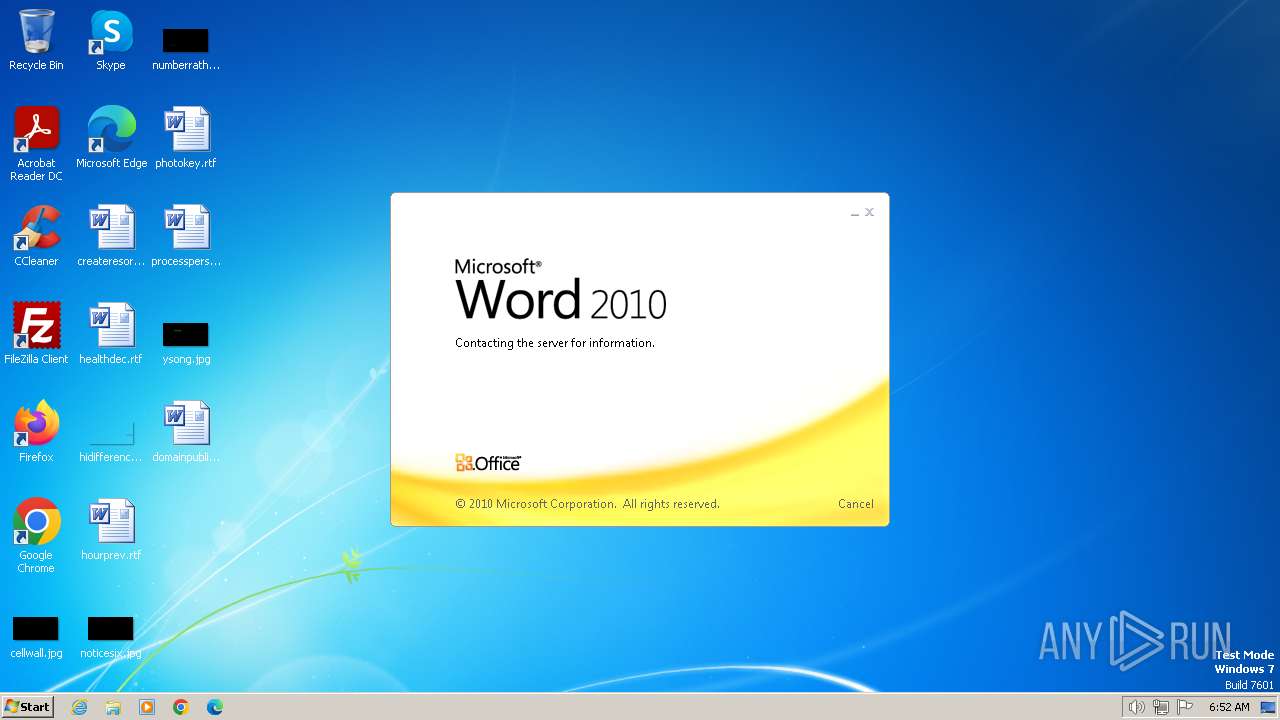
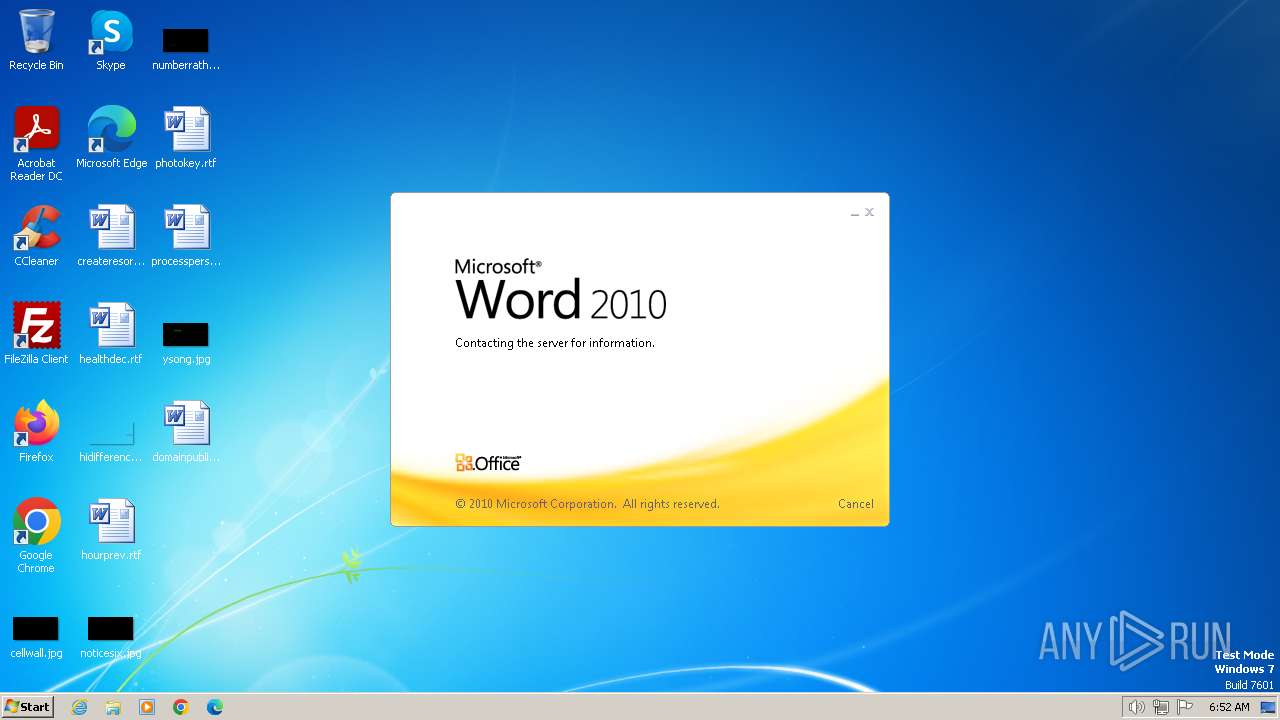
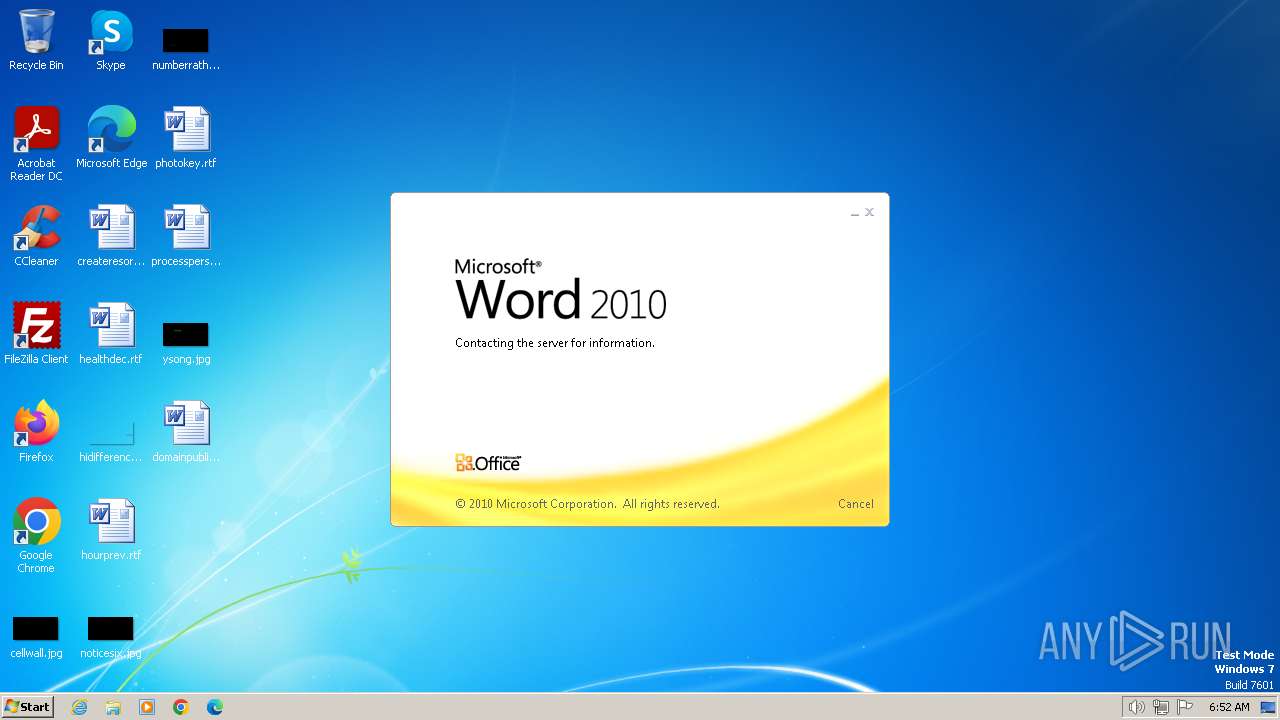
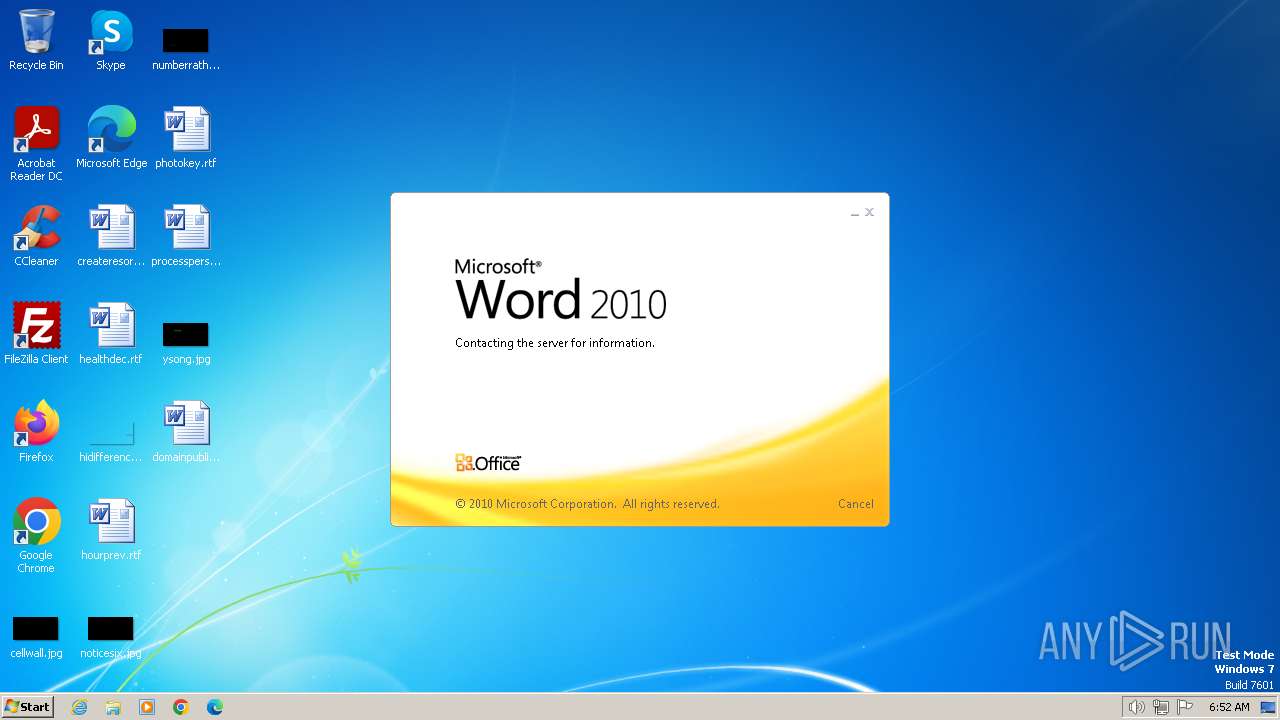
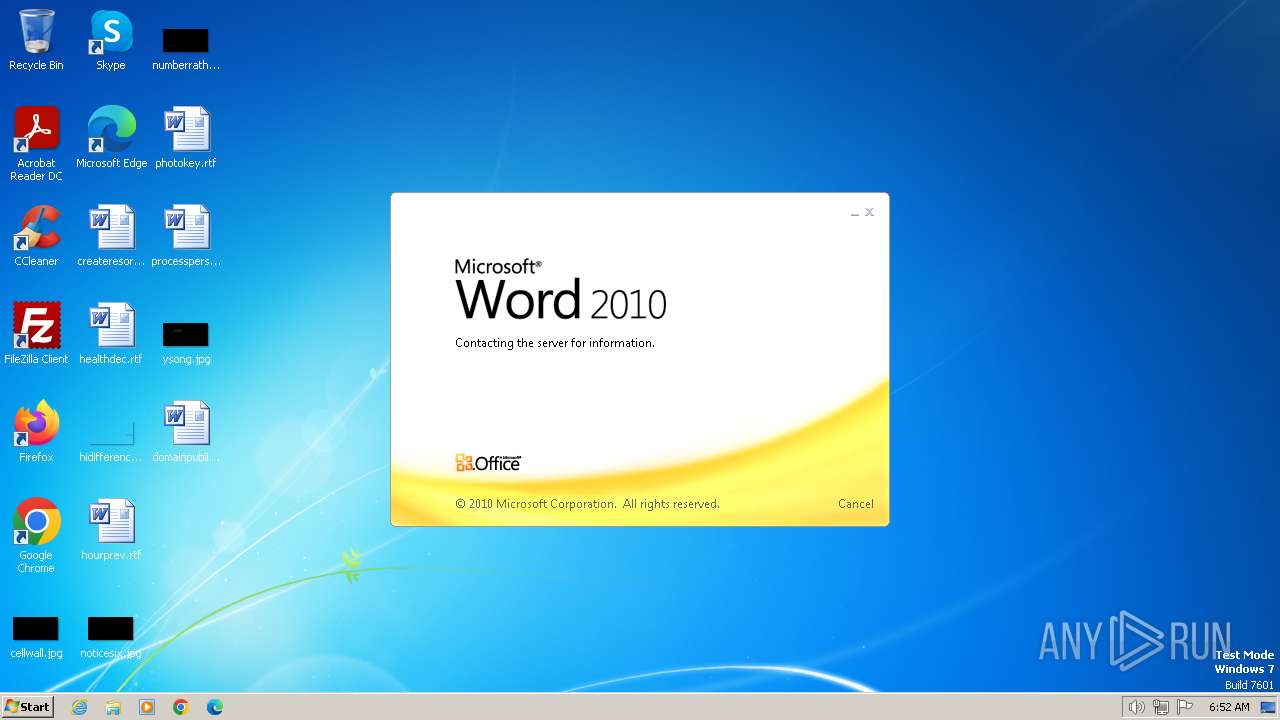
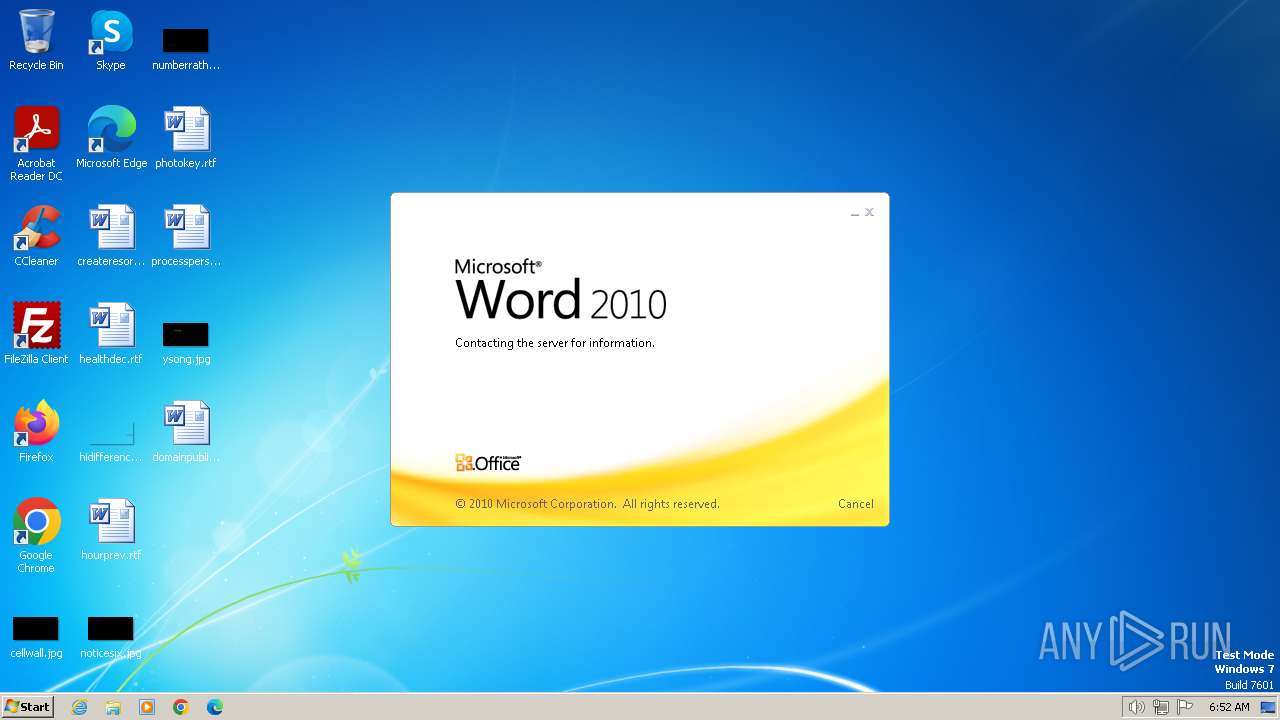
Connection from MS Office application
- WINWORD.EXE (PID: 3768)
CVE-2017-0199 detected
- WINWORD.EXE (PID: 3768)
SUSPICIOUS
Non-standard symbols in registry
- WINWORD.EXE (PID: 3768)
Connects to the server without a host name
- WINWORD.EXE (PID: 3768)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:04:17 16:20:40 |
| ZipCRC: | 0x7fcf3406 |
| ZipCompressedSize: | 365 |
| ZipUncompressedSize: | 1460 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 2 minutes |
| Pages: | 1 |
| Words: | 28 |
| Characters: | 165 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | Grizli777 |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 192 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 12 |
| Keywords: | - |
| LastModifiedBy: | 91974 |
| RevisionNumber: | 10 |
| CreateDate: | 2023:11:10 01:33:00Z |
| ModifyDate: | 2024:04:14 23:35:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | 91974 |
| Description: | - |
Total processes
37
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3768 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\DETAILS INFORMATION.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
3 008
Read events
2 931
Write events
63
Delete events
14
Modification events
| (PID) Process: | (3768) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 52= |
Value: 35323D00B80E0000010000000000000000000000 | |||
| (PID) Process: | (3768) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3768) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3768) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3768) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3768) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3768) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3768) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3768) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3768) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
6
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVREE15.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | — | |
MD5:— | SHA256:— | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{F6EBC15C-6065-4C67-8CD2-FCE27EB52E8A} | — | |
MD5:— | SHA256:— | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:07CC75372FBB97F6154479ACA014528D | SHA256:2D612B7DAC9AE659F7554516F42F8FB699605052B759075EA6E16105848F4BA7 | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{08767243-4F3C-433C-9DEC-1F8192CB8D54} | binary | |
MD5:342EE594290F2E52ADAC3C394BF78A01 | SHA256:C8E8CEBC79954E6DB96D52E2DAEF3E7CD482D0161AE804AA4709E867FAED8D76 | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-{730CFE41-C6D6-43AF-A5F4-C49E75101E41}.FSD | binary | |
MD5:9BAF52B1F56E8799119C95EEFCF5D98A | SHA256:BA107658EC7D57AD3C05623B9908C44CFBFC93F85BCC5D2356693061317D2398 | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{A8EB299A-B16E-4350-BF51-5F1C556B8035}.FSD | binary | |
MD5:122B3ED64AB885C4B19B68747EFCC118 | SHA256:B5B5404CE87DABB03879000CFECC8668D26F1CF0D61E849FF69195F65E6EBAB2 | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSF-{0E1EEE64-E8C6-4E2A-9759-63CF07FD8988}.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:EB5EF6B8DB15FBBEE4828751D570F4F7 | SHA256:8ABD019E45F17D58C272C4ACDBCBE0DB0A99B9806C2059B3B48D870B499BA22A | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$TAILS INFORMATION.docx | pgc | |
MD5:34C263268E77C1E9E88EED53A6165B37 | SHA256:21A50F73F82B6B8D7B1555AD75F2A09A47670BD8063857CF7C347BFF42127B96 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
7
DNS requests
2
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
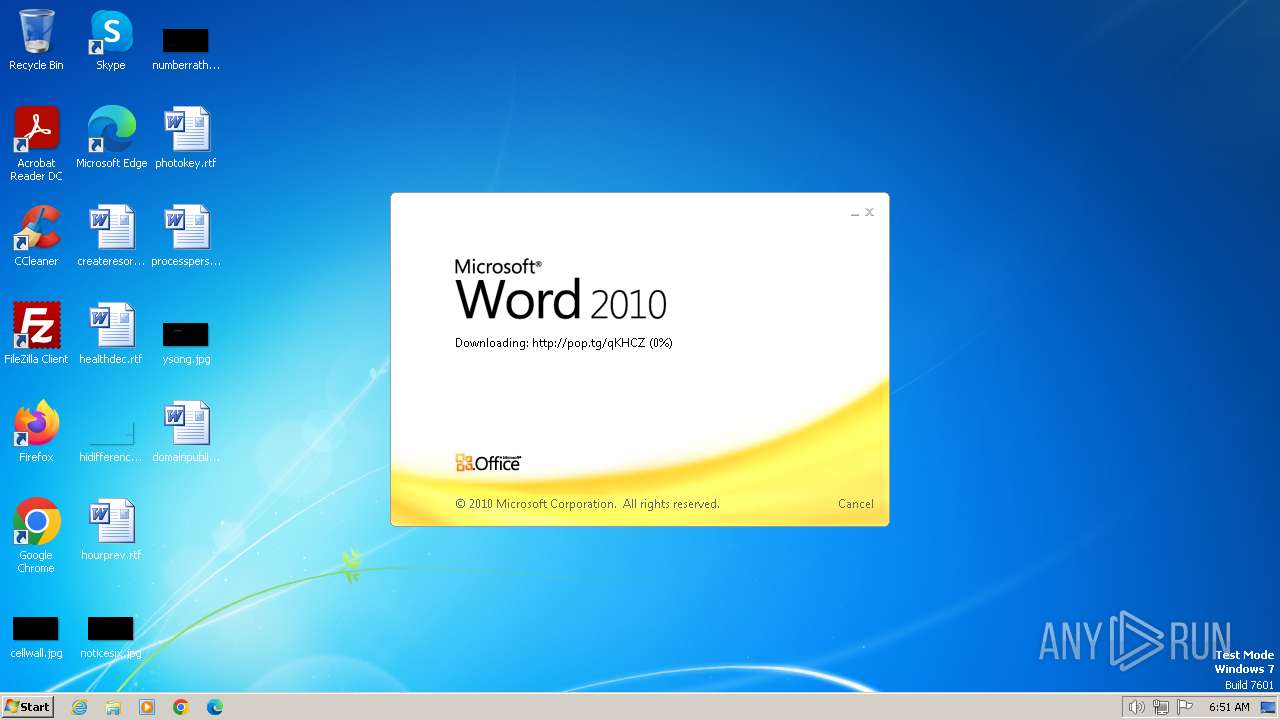
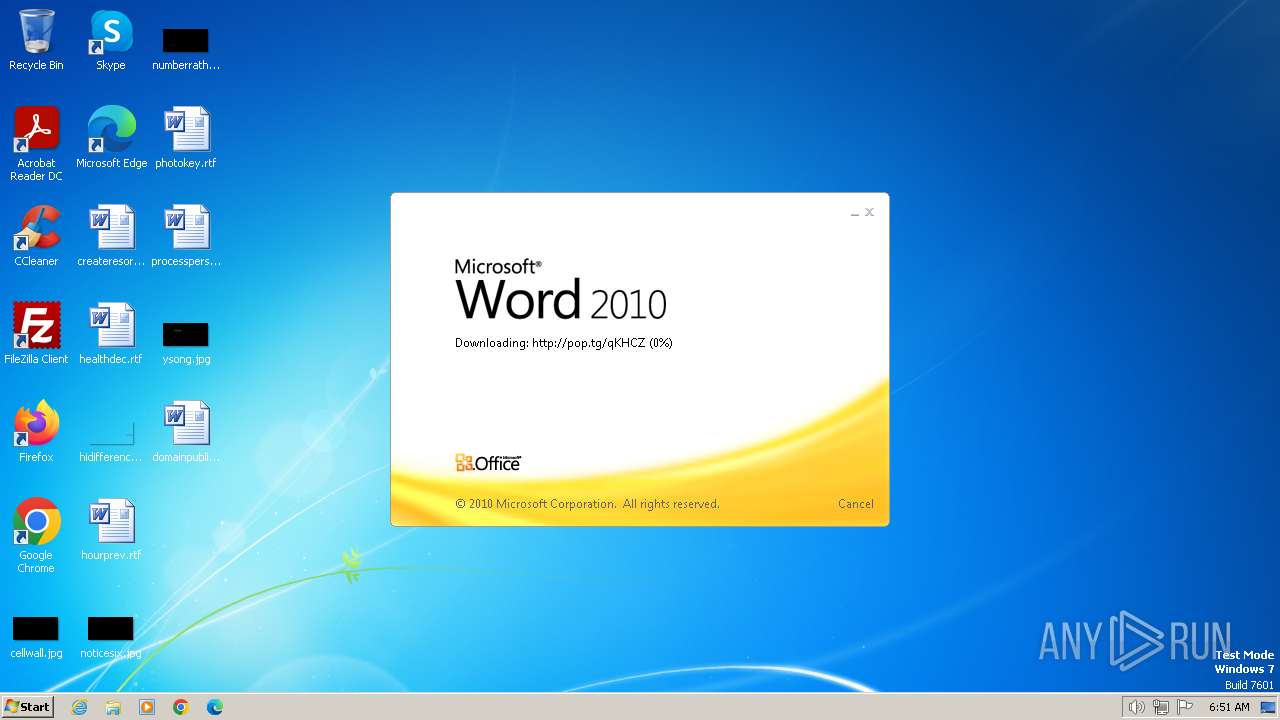
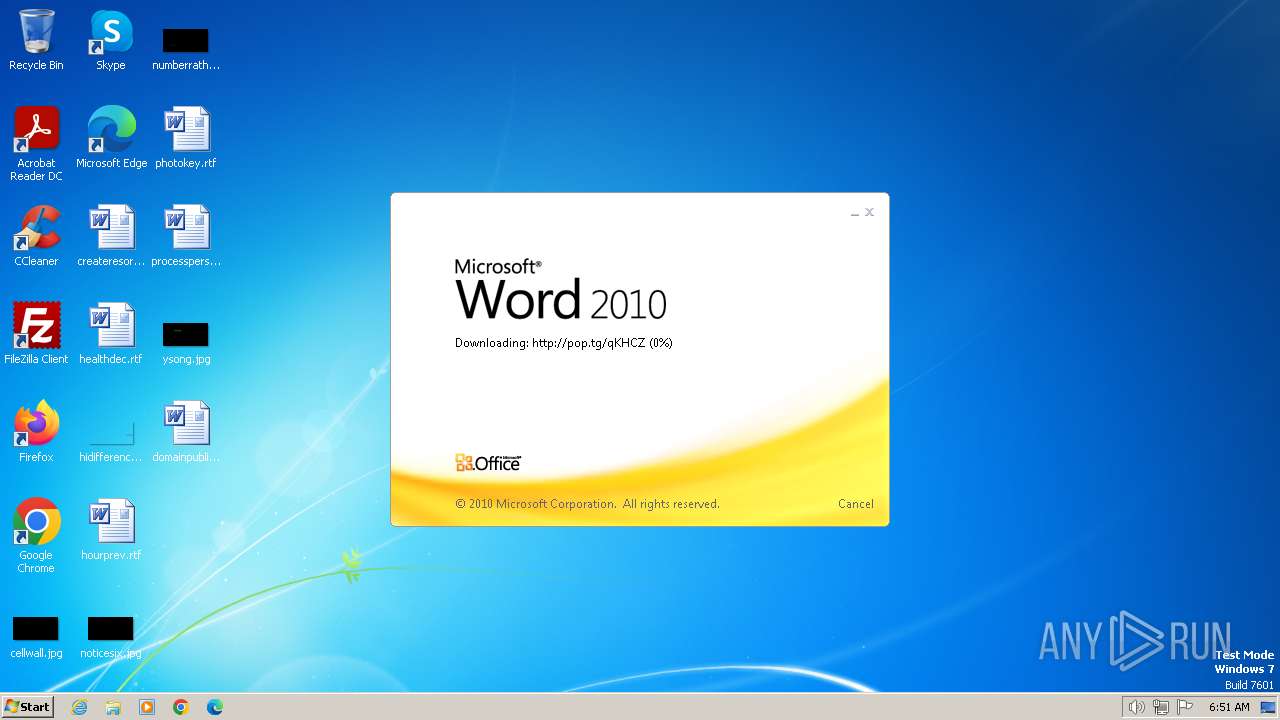
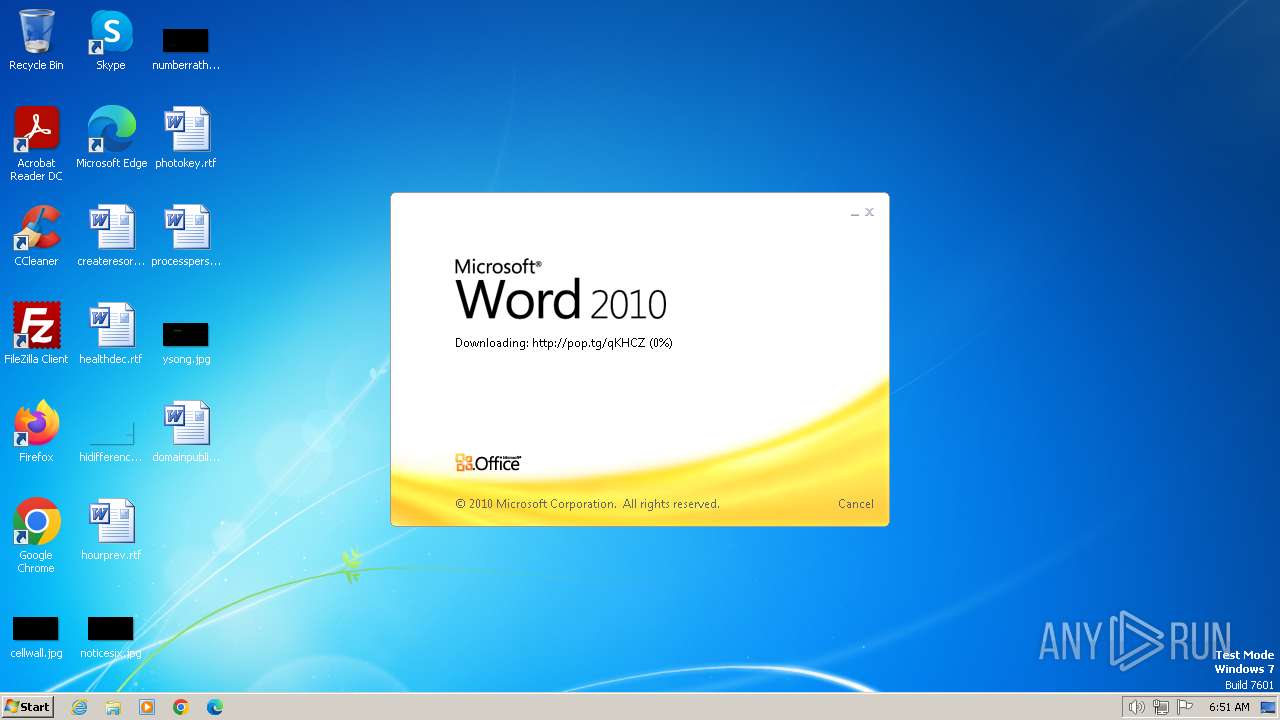
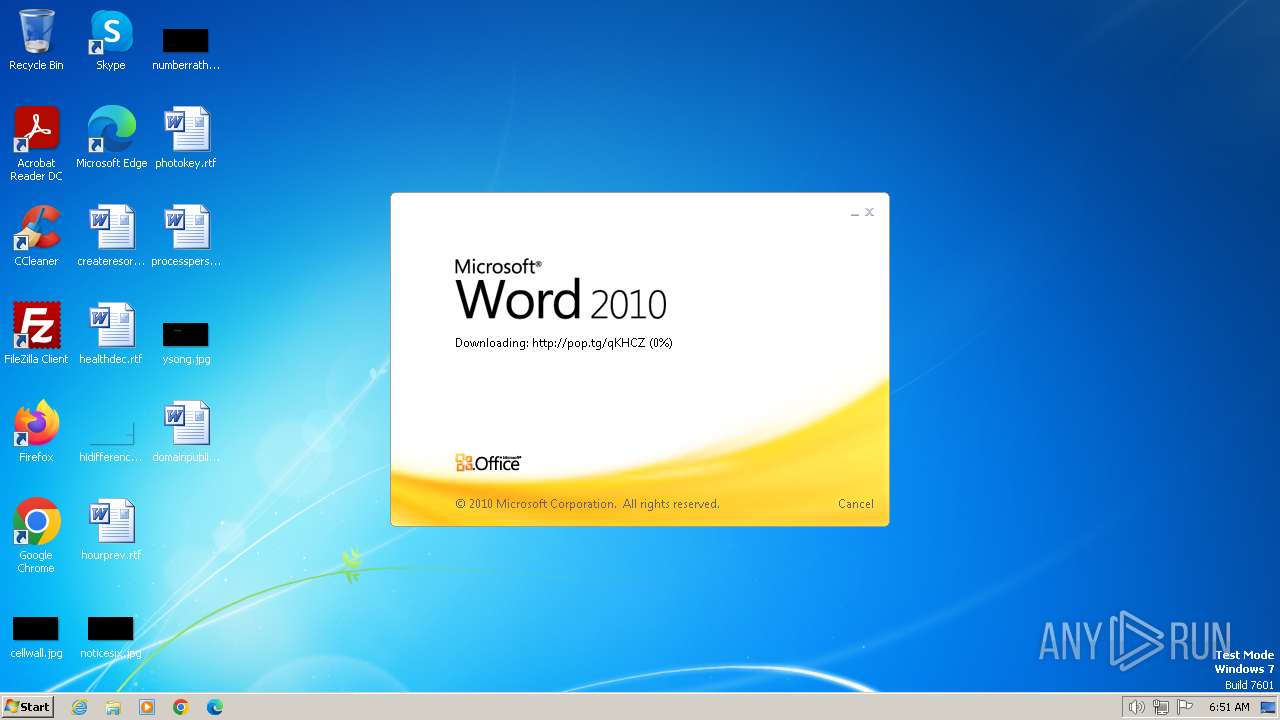
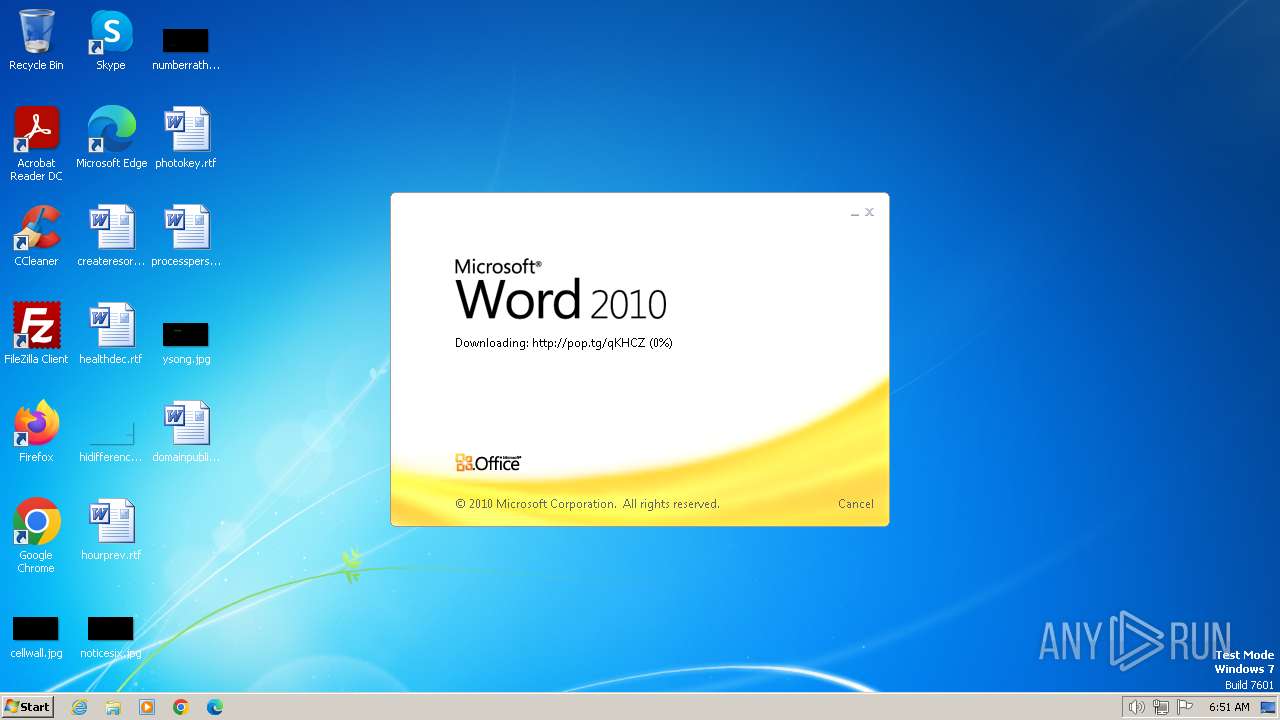
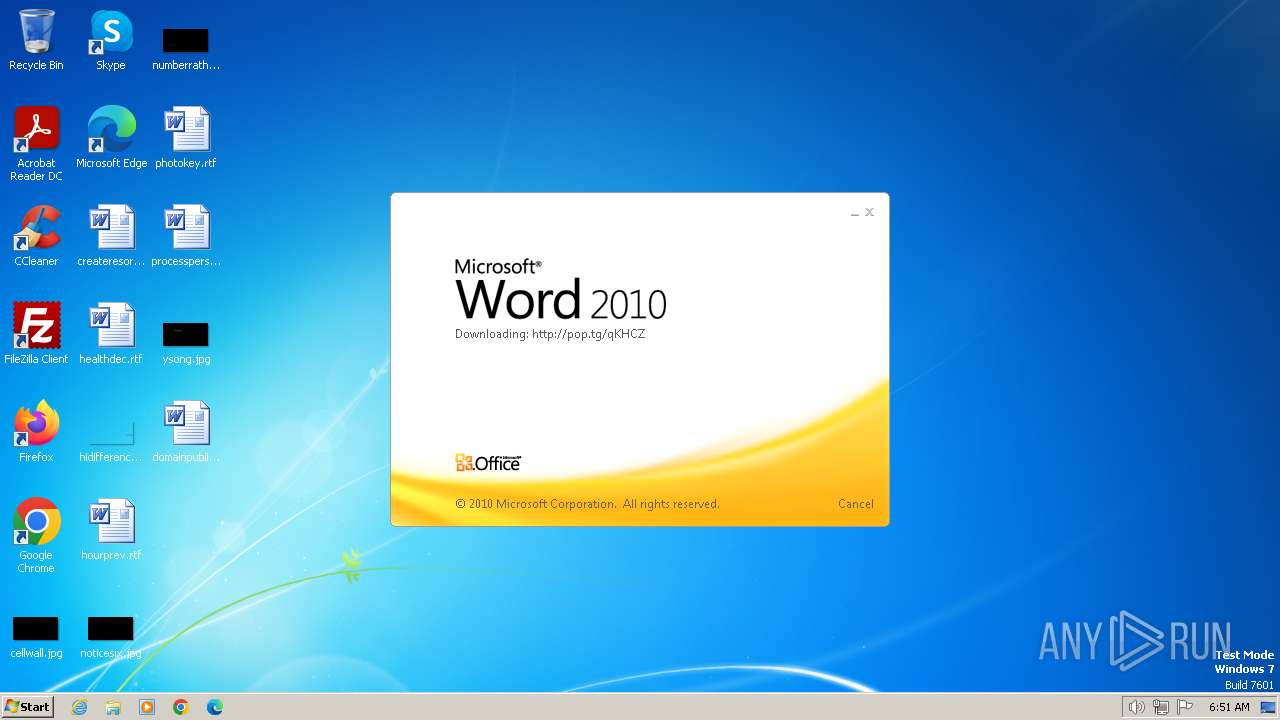
3768 | WINWORD.EXE | OPTIONS | 204 | 104.21.15.201:80 | http://pop.tg/ | unknown | — | — | unknown |
3768 | WINWORD.EXE | HEAD | 204 | 172.67.206.230:80 | http://pop.tg/qKHCZ | unknown | — | — | unknown |
828 | svchost.exe | OPTIONS | 204 | 104.21.15.201:80 | http://pop.tg/ | unknown | — | — | unknown |
828 | svchost.exe | PROPFIND | 404 | 104.21.15.201:80 | http://pop.tg/ | unknown | — | — | unknown |
828 | svchost.exe | PROPFIND | 404 | 104.21.15.201:80 | http://pop.tg/ | unknown | — | — | unknown |
3768 | WINWORD.EXE | GET | 302 | 104.21.15.201:80 | http://pop.tg/qKHCZ | unknown | — | — | unknown |
3768 | WINWORD.EXE | GET | — | 23.95.60.75:80 | http://23.95.60.75/80/hnm/ireallywantakissfrommywifesheisverybeautifulgirlwhoilovealotsheisreallybeautifulgirleveriseenshe___ismybabygirlmylove.doc | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
3768 | WINWORD.EXE | 104.21.15.201:80 | pop.tg | CLOUDFLARENET | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3768 | WINWORD.EXE | 172.67.206.230:80 | pop.tg | CLOUDFLARENET | US | unknown |
828 | svchost.exe | 104.21.15.201:80 | pop.tg | CLOUDFLARENET | — | unknown |
3768 | WINWORD.EXE | 23.95.60.75:80 | — | AS-COLOCROSSING | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pop.tg |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET USER_AGENTS Microsoft Office Existence Discovery User-Agent |
— | — | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
— | — | Potentially Bad Traffic | ET HUNTING Microsoft Office User-Agent Requesting A Doc File |