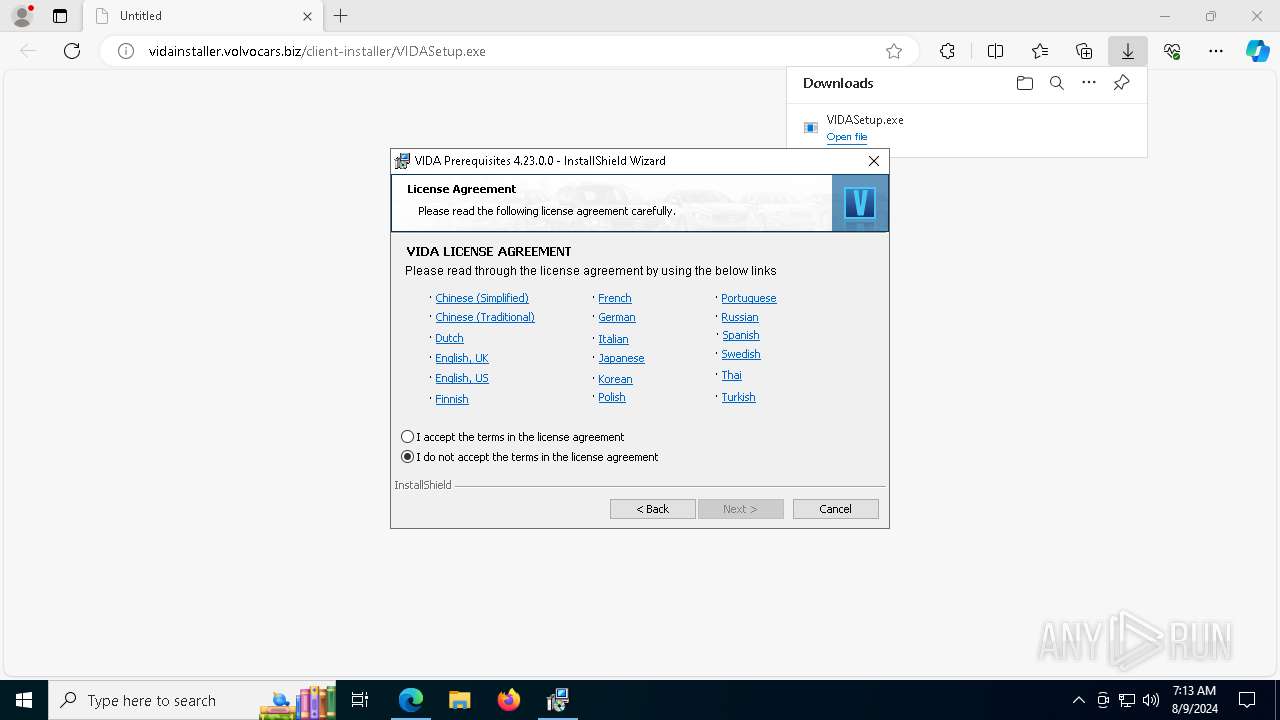
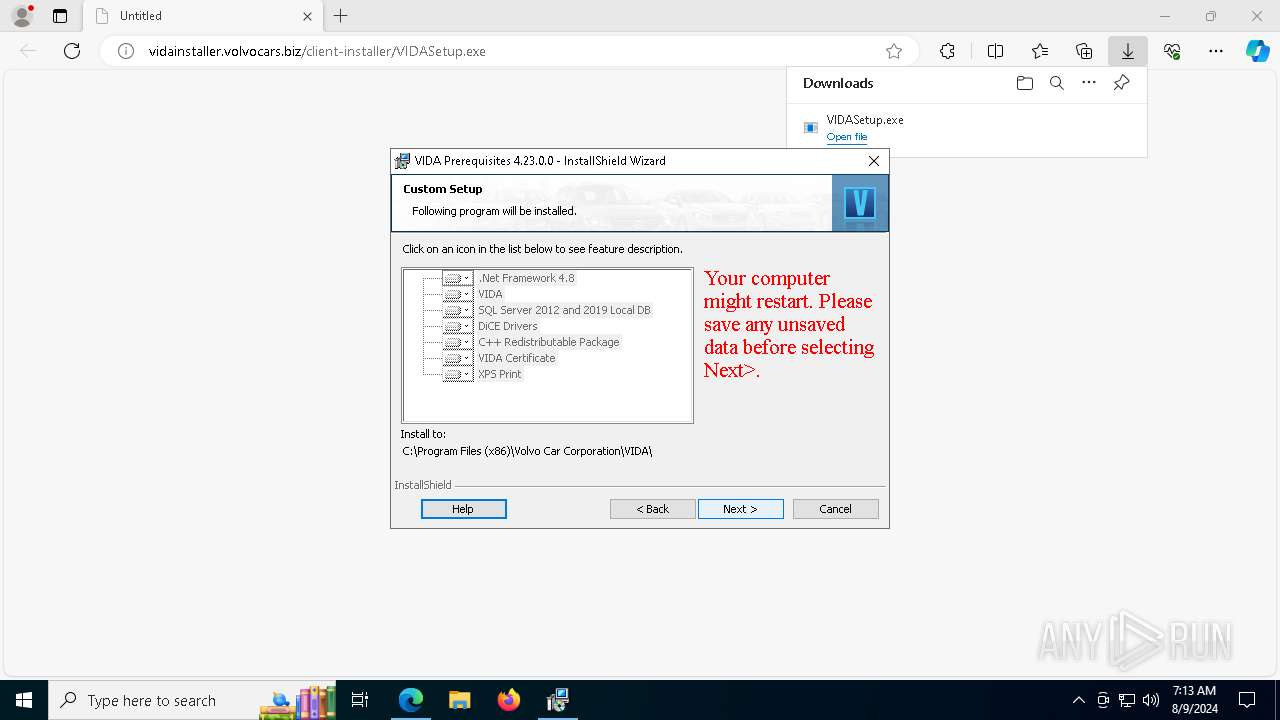
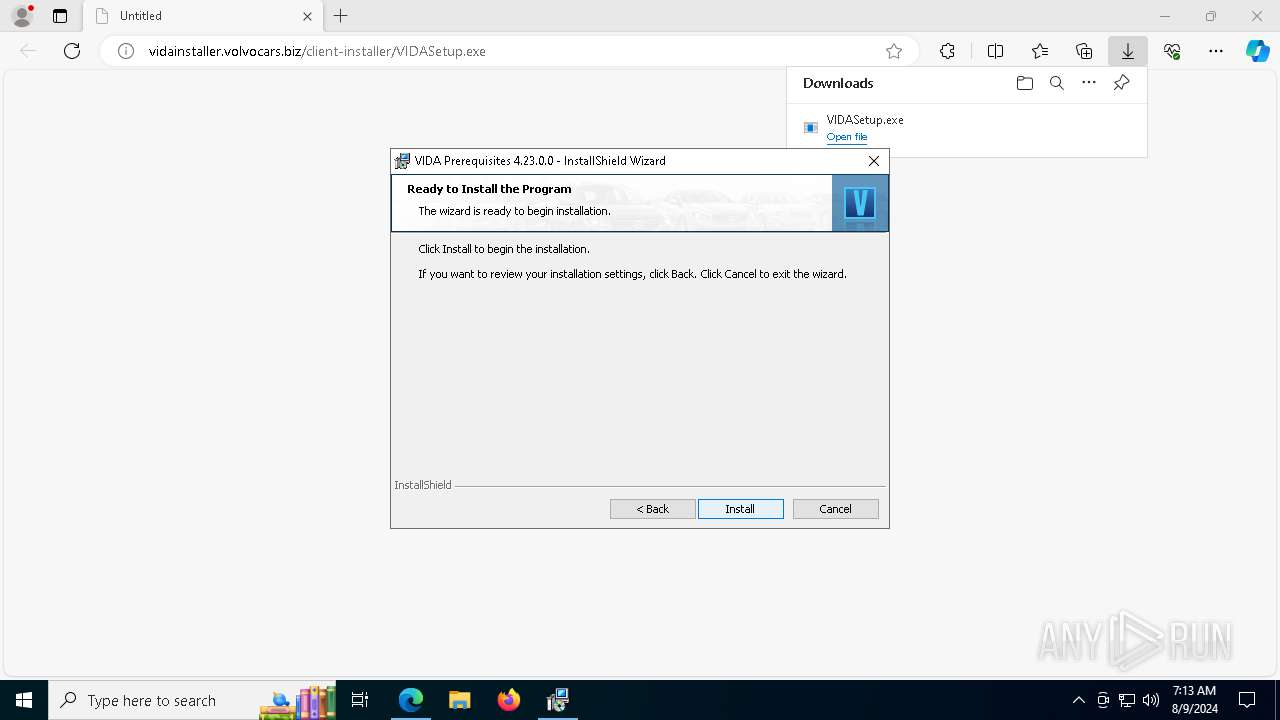
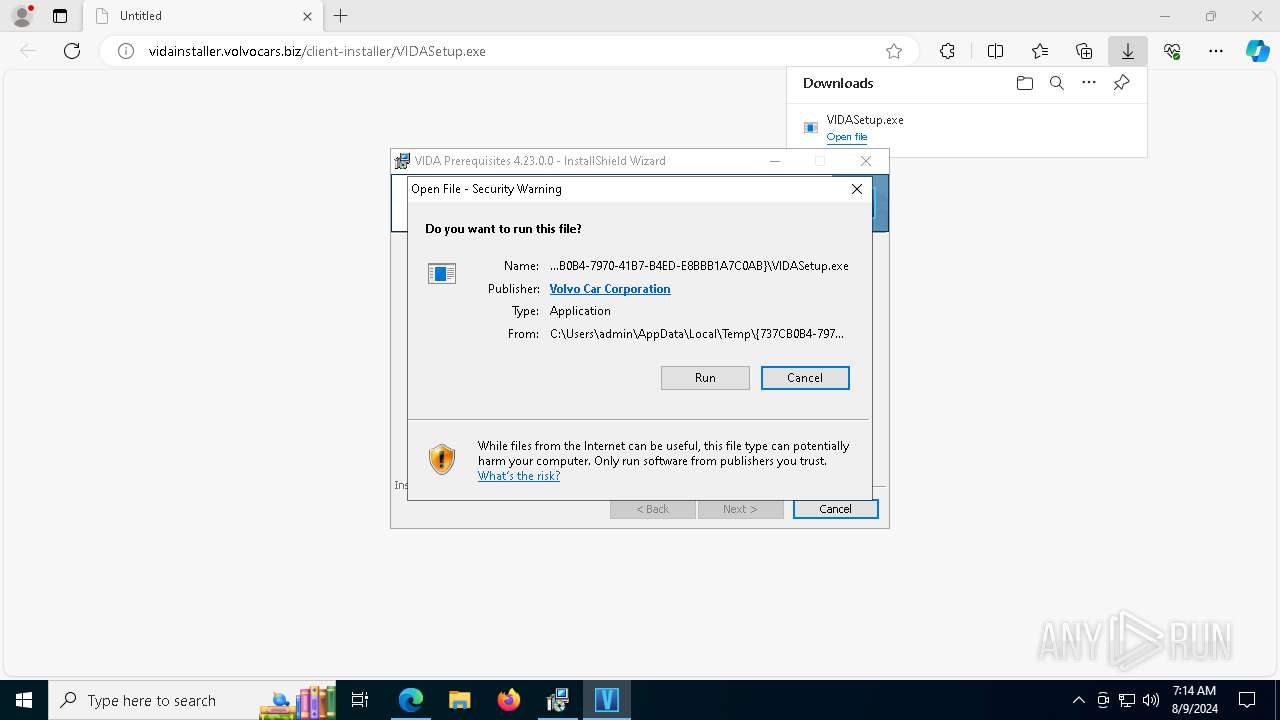
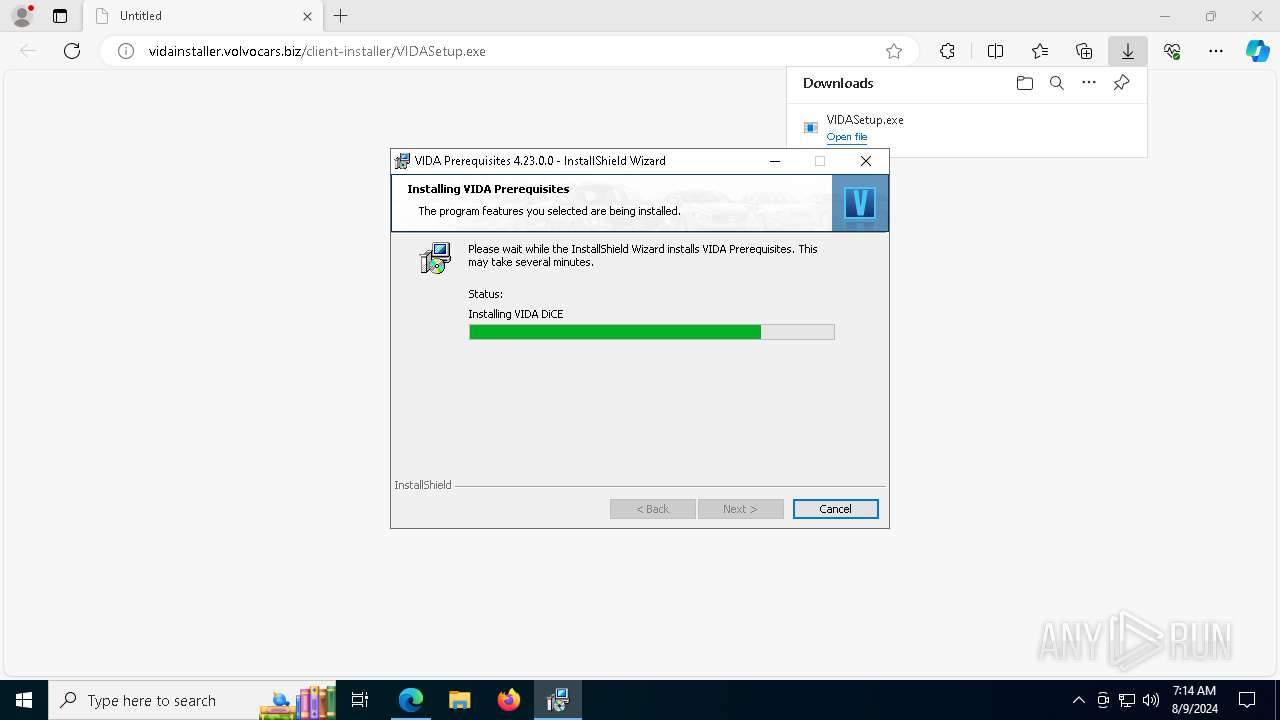
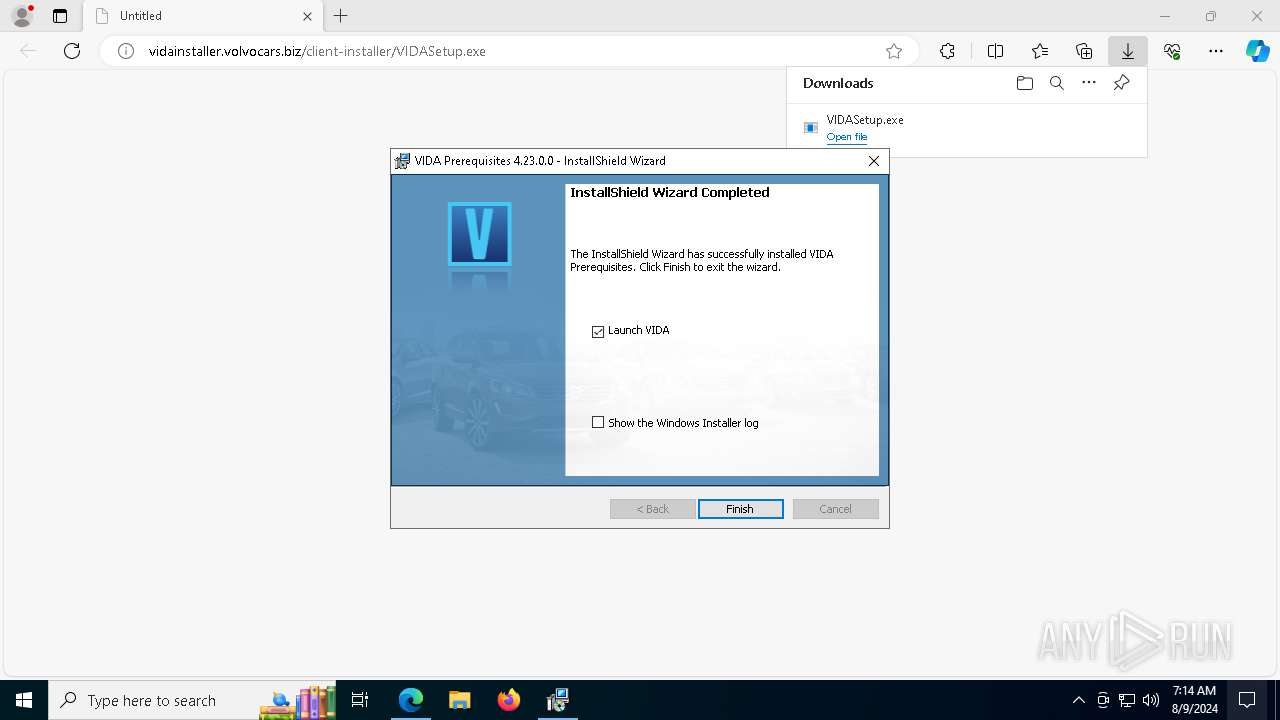
| URL: | http://vidainstaller.volvocars.biz/client-installer/VIDASetup.exe |
| Full analysis: | https://app.any.run/tasks/f3ded902-5b3e-4bd1-9a38-cf2473d0672d |
| Verdict: | Malicious activity |
| Analysis date: | August 09, 2024, 07:11:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 1766BA229C27EE0FE03637DE78440C8C |
| SHA1: | 377CFECFD7F34AC866DC0F15E0DB170DA7CC447B |
| SHA256: | 0EA7CCC28E09BBB1BCC830083C5077C87A27E10FBCD9D6E06C9BE16DBEF1271F |
| SSDEEP: | 3:N1KIhYJOXLeiVXgXKJRAL4A:CI+OXLXVwXsAL4A |
MALICIOUS
Creates a new registry key or changes the value of an existing one (SCRIPT)
- msiexec.exe (PID: 5492)
Gets path to any of the special folders (SCRIPT)
- msiexec.exe (PID: 1076)
Changes the autorun value in the registry
- VIDASetup.exe (PID: 8132)
Run PowerShell with an invisible window
- powershell.exe (PID: 7612)
SUSPICIOUS
Reads security settings of Internet Explorer
- cookie_exporter.exe (PID: 7520)
- msiexec.exe (PID: 1076)
- VIDASetup.exe (PID: 8132)
- VidaClientAppLauncher.exe (PID: 7616)
Starts itself from another location
- VIDASetup.exe (PID: 1140)
- VIDASetup.exe (PID: 6256)
Executable content was dropped or overwritten
- VIDASetup.exe (PID: 460)
- VIDASetup.exe (PID: 8132)
- SetupDiCE.exe (PID: 1048)
- drvinst.exe (PID: 7720)
- VIDASetup.exe (PID: 6652)
Likely accesses (executes) a file from the Public directory
- msiexec.exe (PID: 6540)
- msiexec.exe (PID: 8168)
Writes binary data to a Stream object (SCRIPT)
- msiexec.exe (PID: 5492)
- msiexec.exe (PID: 1076)
Runs shell command (SCRIPT)
- msiexec.exe (PID: 5492)
- msiexec.exe (PID: 1076)
Creates FileSystem object to access computer's file system (SCRIPT)
- msiexec.exe (PID: 5492)
- msiexec.exe (PID: 1076)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 1076)
- VIDASetup.exe (PID: 8132)
- cmd.exe (PID: 7472)
- VIDASetup.exe (PID: 460)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 1216)
- cmd.exe (PID: 3876)
- cmd.exe (PID: 7876)
- cmd.exe (PID: 7180)
- cmd.exe (PID: 7276)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 7176)
- cmd.exe (PID: 8168)
- cmd.exe (PID: 7252)
- cmd.exe (PID: 7232)
Reads the date of Windows installation
- msiexec.exe (PID: 1076)
- VIDASetup.exe (PID: 8132)
Accesses Windows installation date via WMI (SCRIPT)
- msiexec.exe (PID: 1076)
Accesses WMI object display name (SCRIPT)
- msiexec.exe (PID: 1076)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 7440)
Executes as Windows Service
- sqlwriter.exe (PID: 2388)
- VSSVC.exe (PID: 7528)
Process drops legitimate windows executable
- msiexec.exe (PID: 7440)
- SetupDiCE.exe (PID: 1048)
- drvinst.exe (PID: 7720)
- msiexec.exe (PID: 7404)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7440)
Drops the executable file immediately after the start
- msiexec.exe (PID: 7440)
- VIDASetup.exe (PID: 8132)
- SetupDiCE.exe (PID: 1048)
- msiexec.exe (PID: 7404)
- drvinst.exe (PID: 7720)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6856)
The process drops C-runtime libraries
- msiexec.exe (PID: 7440)
Adds/modifies Windows certificates
- powershell.exe (PID: 7612)
- SetupDiCE.exe (PID: 1048)
- VIDASetup.exe (PID: 8132)
Executing commands from a ".bat" file
- VIDASetup.exe (PID: 8132)
Application launched itself
- cmd.exe (PID: 7472)
- VIDASetup.exe (PID: 8132)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 7440)
- drvinst.exe (PID: 7720)
Creates files in the driver directory
- msiexec.exe (PID: 7404)
- drvinst.exe (PID: 7720)
Checks Windows Trust Settings
- drvinst.exe (PID: 7720)
- VIDASetup.exe (PID: 8132)
The process deletes folder without confirmation
- VIDASetup.exe (PID: 8132)
- VIDASetup.exe (PID: 460)
INFO
Reads Microsoft Office registry keys
- msedge.exe (PID: 6596)
Application launched itself
- msedge.exe (PID: 6596)
- msiexec.exe (PID: 7440)
Reads Environment values
- cookie_exporter.exe (PID: 7520)
- msiexec.exe (PID: 5492)
- msiexec.exe (PID: 1076)
- identity_helper.exe (PID: 1812)
- VidaClientAppLauncher.exe (PID: 7616)
Checks supported languages
- cookie_exporter.exe (PID: 7520)
- VIDASetup.exe (PID: 1140)
- VIDASetup.exe (PID: 460)
- msiexec.exe (PID: 7440)
- msiexec.exe (PID: 1076)
- msiexec.exe (PID: 5492)
- VIDASetup.exe (PID: 6256)
- VIDASetup.exe (PID: 8132)
- msiexec.exe (PID: 7260)
- sqlwriter.exe (PID: 2388)
- identity_helper.exe (PID: 1812)
- msiexec.exe (PID: 6432)
- msiexec.exe (PID: 7796)
- msiexec.exe (PID: 7232)
- SetupDiCE.exe (PID: 1048)
- msiexec.exe (PID: 7192)
- msiexec.exe (PID: 7404)
- drvinst.exe (PID: 7720)
- VIDASetup.exe (PID: 6652)
- VidaClientAppLauncher.exe (PID: 7616)
The process uses the downloaded file
- msedge.exe (PID: 6596)
- msedge.exe (PID: 7216)
- VIDASetup.exe (PID: 1140)
- VIDASetup.exe (PID: 6256)
- VIDASetup.exe (PID: 8132)
Checks proxy server information
- cookie_exporter.exe (PID: 7520)
- VIDASetup.exe (PID: 8132)
- VidaClientAppLauncher.exe (PID: 7616)
Reads the computer name
- cookie_exporter.exe (PID: 7520)
- VIDASetup.exe (PID: 1140)
- VIDASetup.exe (PID: 460)
- msiexec.exe (PID: 1076)
- msiexec.exe (PID: 7440)
- msiexec.exe (PID: 5492)
- VIDASetup.exe (PID: 8132)
- VIDASetup.exe (PID: 6256)
- msiexec.exe (PID: 7260)
- msiexec.exe (PID: 6432)
- sqlwriter.exe (PID: 2388)
- identity_helper.exe (PID: 1812)
- msiexec.exe (PID: 7796)
- msiexec.exe (PID: 7232)
- SetupDiCE.exe (PID: 1048)
- msiexec.exe (PID: 7192)
- drvinst.exe (PID: 7720)
- msiexec.exe (PID: 7404)
- VidaClientAppLauncher.exe (PID: 7616)
- VIDASetup.exe (PID: 6652)
Create files in a temporary directory
- VIDASetup.exe (PID: 1140)
- VIDASetup.exe (PID: 460)
- msiexec.exe (PID: 1076)
- VIDASetup.exe (PID: 8132)
- VIDASetup.exe (PID: 6256)
- SetupDiCE.exe (PID: 1048)
- VIDASetup.exe (PID: 6652)
- VidaClientAppLauncher.exe (PID: 7616)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6540)
- msedge.exe (PID: 6596)
- msiexec.exe (PID: 7440)
- msiexec.exe (PID: 7404)
Process checks computer location settings
- msiexec.exe (PID: 1076)
- VIDASetup.exe (PID: 8132)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7440)
- msiexec.exe (PID: 7404)
- drvinst.exe (PID: 7720)
- VIDASetup.exe (PID: 8132)
- VidaClientAppLauncher.exe (PID: 7616)
Creates files in the program directory
- sqlwriter.exe (PID: 2388)
Creates a software uninstall entry
- msiexec.exe (PID: 7440)
- msiexec.exe (PID: 7404)
Reads the software policy settings
- msiexec.exe (PID: 7404)
- drvinst.exe (PID: 7720)
- VIDASetup.exe (PID: 8132)
- VidaClientAppLauncher.exe (PID: 7616)
Adds/modifies Windows certificates
- drvinst.exe (PID: 7720)
Creates files or folders in the user directory
- VIDASetup.exe (PID: 8132)
Disables trace logs
- VidaClientAppLauncher.exe (PID: 7616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
257
Monitored processes
108
Malicious processes
6
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 460 | C:\Users\admin\AppData\Local\Temp\{7F193364-EB1B-4B1F-A125-84D24B57F062}\VIDASetup.exe /q"C:\Users\admin\Downloads\VIDASetup.exe" /tempdisk1folder"C:\Users\admin\AppData\Local\Temp\{7F193364-EB1B-4B1F-A125-84D24B57F062}" /IS_temp | C:\Users\admin\AppData\Local\Temp\{7F193364-EB1B-4B1F-A125-84D24B57F062}\VIDASetup.exe | VIDASetup.exe | ||||||||||||
User: admin Company: Volvo Car Corporation Integrity Level: HIGH Description: Setup Launcher Unicode Exit code: 0 Version: 4.23.0.0 Modules
| |||||||||||||||
| 888 | netsh advfirewall firewall delete rule name=VIDA_PEERCOM_TCP | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | "C:\Users\admin\AppData\Local\Temp\{737CB0B4-7970-41B7-B4ED-E8BBB1A7C0AB}\{A7DD6D06-28D0-45B8-BEBB-F3A4EE46F0EE}\SetupDiCE.exe" | C:\Users\admin\AppData\Local\Temp\{737CB0B4-7970-41B7-B4ED-E8BBB1A7C0AB}\{A7DD6D06-28D0-45B8-BEBB-F3A4EE46F0EE}\SetupDiCE.exe | VIDASetup.exe | ||||||||||||
User: admin Company: SETEK AB Integrity Level: HIGH Description: DiCE Setup Exit code: 0 Version: 7, 0, 0, 1 Modules
| |||||||||||||||
| 1048 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | C:\Windows\syswow64\MsiExec.exe -Embedding 623046F574277EB1520E41601BB21A85 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | "C:\Users\admin\Downloads\VIDASetup.exe" | C:\Users\admin\Downloads\VIDASetup.exe | msedge.exe | ||||||||||||
User: admin Company: Volvo Car Corporation Integrity Level: HIGH Description: Setup Launcher Unicode Exit code: 0 Version: 4.23.0.0 Modules
| |||||||||||||||
| 1184 | "C:\WINDOWS\system32\cmd.exe" /c rmdir /s /q "C:\Users\admin\AppData\Local\Temp\{737CB0B4-7970-41B7-B4ED-E8BBB1A7C0AB}" | C:\Windows\SysWOW64\cmd.exe | — | VIDASetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | "C:\Windows\SysWOW64\cmd.exe" /c netsh advfirewall firewall delete rule name=vida.desktop.exe | C:\Windows\SysWOW64\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6484 --field-trial-handle=2320,i,2393411682612155965,5256227625519689537,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1920 | netsh advfirewall firewall add rule name=VIDA_PEERCOM_UDP dir=in action=allow enable=yes protocol=UDP localport=24200 | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
73 095
Read events
68 348
Write events
4 660
Delete events
87
Modification events
| (PID) Process: | (6436) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (6436) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (6436) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (6436) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (6436) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (6436) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31124011 | |||
| (PID) Process: | (6436) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6436) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6436) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6436) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
358
Suspicious files
336
Text files
217
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6596 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFe54d2.TMP | — | |
MD5:— | SHA256:— | |||
| 6596 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RFe54d2.TMP | — | |
MD5:— | SHA256:— | |||
| 6596 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFe54e2.TMP | — | |
MD5:— | SHA256:— | |||
| 6596 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6596 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6596 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6596 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFe54e2.TMP | — | |
MD5:— | SHA256:— | |||
| 6596 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFe54e2.TMP | — | |
MD5:— | SHA256:— | |||
| 6596 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6596 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
91
DNS requests
71
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4436 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4436 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6372 | svchost.exe | HEAD | 200 | 23.48.23.5:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e456c896-44a6-416b-bdf2-a332bb03a659?P1=1723465174&P2=404&P3=2&P4=bg0hXMJ8i3OMChxzRVWy64Q1hORr3ddRnPSzHJmoeXSlAfd%2bZfhT8FixJH6BoVtQIRn34Kus%2fEcfrYiGEkzhVg%3d%3d | unknown | — | — | whitelisted |
7832 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7876 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6372 | svchost.exe | GET | 206 | 23.48.23.5:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e456c896-44a6-416b-bdf2-a332bb03a659?P1=1723465174&P2=404&P3=2&P4=bg0hXMJ8i3OMChxzRVWy64Q1hORr3ddRnPSzHJmoeXSlAfd%2bZfhT8FixJH6BoVtQIRn34Kus%2fEcfrYiGEkzhVg%3d%3d | unknown | — | — | whitelisted |
6372 | svchost.exe | GET | 206 | 23.48.23.5:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e456c896-44a6-416b-bdf2-a332bb03a659?P1=1723465174&P2=404&P3=2&P4=bg0hXMJ8i3OMChxzRVWy64Q1hORr3ddRnPSzHJmoeXSlAfd%2bZfhT8FixJH6BoVtQIRn34Kus%2fEcfrYiGEkzhVg%3d%3d | unknown | — | — | whitelisted |
6372 | svchost.exe | GET | 206 | 23.48.23.5:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e456c896-44a6-416b-bdf2-a332bb03a659?P1=1723465174&P2=404&P3=2&P4=bg0hXMJ8i3OMChxzRVWy64Q1hORr3ddRnPSzHJmoeXSlAfd%2bZfhT8FixJH6BoVtQIRn34Kus%2fEcfrYiGEkzhVg%3d%3d | unknown | — | — | whitelisted |
6372 | svchost.exe | GET | 206 | 23.48.23.5:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e456c896-44a6-416b-bdf2-a332bb03a659?P1=1723465174&P2=404&P3=2&P4=bg0hXMJ8i3OMChxzRVWy64Q1hORr3ddRnPSzHJmoeXSlAfd%2bZfhT8FixJH6BoVtQIRn34Kus%2fEcfrYiGEkzhVg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4100 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2472 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6832 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6596 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6832 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6832 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6832 | msedge.exe | 13.107.246.67:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
vidainstaller.volvocars.biz |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |