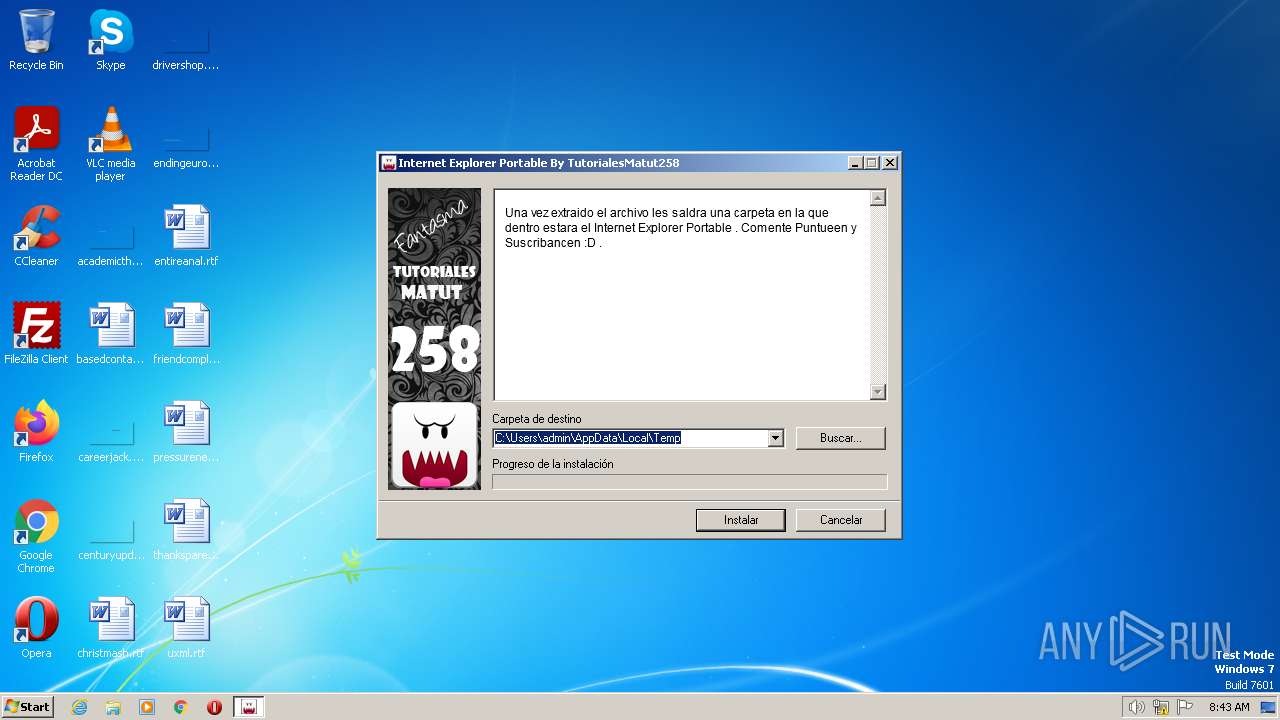
| File name: | Internet Explorer Portable By TutorialesMatut258.exe |
| Full analysis: | https://app.any.run/tasks/f48f8565-7a7a-4046-936d-8c20f0feaae6 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2023, 07:43:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6467A8CFD36D8F5BE1D93A70756650E3 |
| SHA1: | B9BA8A931BB3247ED2DCC8C1B043E6DE62E1DB7E |
| SHA256: | 0EA1AF923F15D14AA268F4556F0879CDD7B090C94589720AF93ED3D3F9DC80B8 |
| SSDEEP: | 49152:Q83FNRTCE2/tQb3IsKMJia64WuQ4axKFXwhF0HkifdC:R72/tHMJiayuQkwh8kifdC |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
Executable content was dropped or overwritten
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
Reads Microsoft Outlook installation path
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
Reads Internet Explorer settings
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
Creates executable files that already exist in Windows
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
INFO
Checks supported languages
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
Reads the computer name
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
Checks proxy server information
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
The process checks LSA protection
- explorer.exe (PID: 2756)
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
Reads the machine GUID from the registry
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
Create files in a temporary directory
- Internet Explorer Portable By TutorialesMatut258.exe (PID: 3988)
Manual execution by a user
- explorer.exe (PID: 2756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.8) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x1000 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 218112 |
| CodeSize: | 81920 |
| LinkerVersion: | 5 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| TimeStamp: | 2007:09:20 12:34:46+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 20-Sep-2007 12:34:46 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000200 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 20-Sep-2007 12:34:46 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00014000 | 0x00013800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.46548 |
.data | 0x00015000 | 0x00007000 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.90968 |
.idata | 0x0001C000 | 0x00001000 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.12446 |
.rsrc | 0x0001D000 | 0x00033930 | 0x00033A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.683 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.06643 | 831 | Latin 1 / Western European | Russian - Russia | RT_MANIFEST |
2 | 3.37095 | 296 | Latin 1 / Western European | Process Default Language | RT_ICON |
3 | 5.81329 | 3752 | Latin 1 / Western European | Process Default Language | RT_ICON |
4 | 6.39217 | 2216 | Latin 1 / Western European | Process Default Language | RT_ICON |
5 | 5.47785 | 1384 | Latin 1 / Western European | Process Default Language | RT_ICON |
6 | 7.88292 | 50469 | Latin 1 / Western European | Process Default Language | RT_ICON |
7 | 3.24143 | 556 | Latin 1 / Western European | Russian - Russia | RT_STRING |
8 | 3.28574 | 946 | Latin 1 / Western European | Russian - Russia | RT_STRING |
9 | 3.04375 | 530 | Latin 1 / Western European | Russian - Russia | RT_STRING |
10 | 3.15563 | 638 | Latin 1 / Western European | Russian - Russia | RT_STRING |
Imports
ADVAPI32.DLL |
COMCTL32.DLL |
COMDLG32.DLL |
GDI32.DLL |
KERNEL32.DLL |
OLE32.DLL |
SHELL32.DLL |
USER32.DLL |
Total processes
39
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2756 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3988 | "C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258.exe" | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
628
Read events
614
Write events
14
Delete events
0
Modification events
| (PID) Process: | (3988) Internet Explorer Portable By TutorialesMatut258.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3988) Internet Explorer Portable By TutorialesMatut258.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3988) Internet Explorer Portable By TutorialesMatut258.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3988) Internet Explorer Portable By TutorialesMatut258.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3988) Internet Explorer Portable By TutorialesMatut258.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3988) Internet Explorer Portable By TutorialesMatut258.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3988) Internet Explorer Portable By TutorialesMatut258.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003E010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3988) Internet Explorer Portable By TutorialesMatut258.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3988) Internet Explorer Portable By TutorialesMatut258.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
39
Suspicious files
0
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3988 | Internet Explorer Portable By TutorialesMatut258.exe | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258\Connection Wizard\icwres.dll | executable | |
MD5:76C820E626ADB0AD4AA942DA2DE08CDB | SHA256:BFB0FFC0D966097207023D8B94F8E47C9320AABCFF9FF81AEB6EFC2EAA96B6E8 | |||
| 3988 | Internet Explorer Portable By TutorialesMatut258.exe | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258\Connection Wizard\icwconn.dll | executable | |
MD5:84299BB8BD1902C02D36D09D6CA84225 | SHA256:96B1AA826485E444BF62B8ADAAD947762C45A0686794D18CB414786AD47A68C2 | |||
| 3988 | Internet Explorer Portable By TutorialesMatut258.exe | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258\Connection Wizard\icwx25b.dun | text | |
MD5:779A172DB0088470AD8C66C9D8136ED4 | SHA256:4080B596083F2071ECD0F094CBDFD29B2344F8FE362AD20E67FF2F233BB777FD | |||
| 3988 | Internet Explorer Portable By TutorialesMatut258.exe | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258\Connection Wizard\icwutil.dll | executable | |
MD5:6B60CB4ADC4F9756AB926FECA838DA67 | SHA256:D655FDD0994AB058D7DFA39944518825F4FDFB9B068A0FC084D730DFB3E7D5DB | |||
| 3988 | Internet Explorer Portable By TutorialesMatut258.exe | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258\Connection Wizard\state.icw | text | |
MD5:30ADDB5CFF3344CFF7CA3672DF3643FB | SHA256:65513950DF22B22B72657698939743427E753F817A4B0918F34679AE3AB16088 | |||
| 3988 | Internet Explorer Portable By TutorialesMatut258.exe | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258\Connection Wizard\isignup.exe | executable | |
MD5:9F3D815ADA743771C4B5931012D828F6 | SHA256:E7DCEE3643EFDA68830727672488B8755E94A98D0083CF8BB8B95D4CA8071FAF | |||
| 3988 | Internet Explorer Portable By TutorialesMatut258.exe | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258\Connection Wizard\icwx25c.dun | text | |
MD5:AB240A378BC06BD2F0EBF4D3F16923EA | SHA256:31DB40DC1AD522807F95F0F90236C47AC1D7E7E6DBCDC6ED2BEB6271B76DA695 | |||
| 3988 | Internet Explorer Portable By TutorialesMatut258.exe | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258\Connection Wizard\icwtutor.exe | executable | |
MD5:2AC323944743808A30253497A92B1488 | SHA256:1327EA7CCBF9E88D1B2C7B2620624972733BF780F30FC8F1A33082E74F8D8C66 | |||
| 3988 | Internet Explorer Portable By TutorialesMatut258.exe | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258\Connection Wizard\inetwiz.exe | executable | |
MD5:2B25A6F80B102520DCF9E338B448C328 | SHA256:8D74215E14CE7B68138AEAE7CC159BA3208C01375E3E4BE4958288568304B189 | |||
| 3988 | Internet Explorer Portable By TutorialesMatut258.exe | C:\Users\admin\AppData\Local\Temp\Internet Explorer Portable By TutorialesMatut258\Connection Wizard\phone.icw | text | |
MD5:78EE68E61BF9AFE6A1096558FEC1D79B | SHA256:FA0C00D72529F524E6CEF9237C564F43E08F71D12AC56D1DAD755A80E43D9D79 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3252 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |