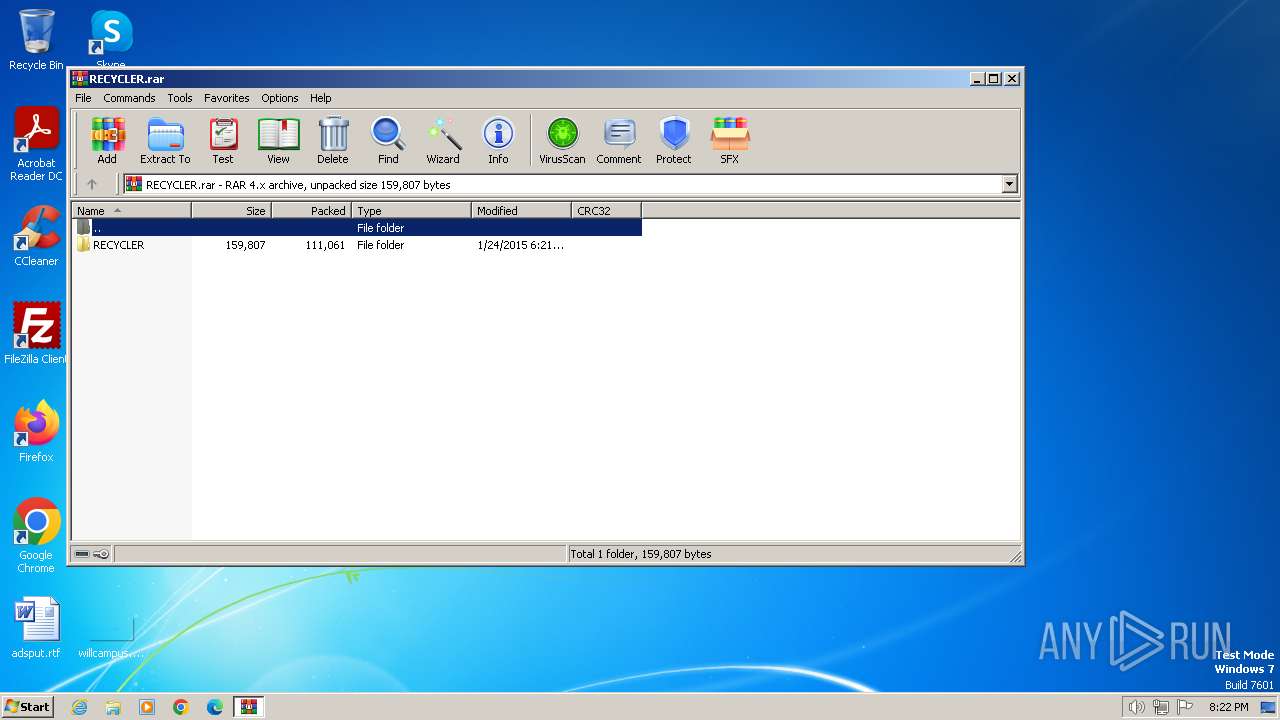
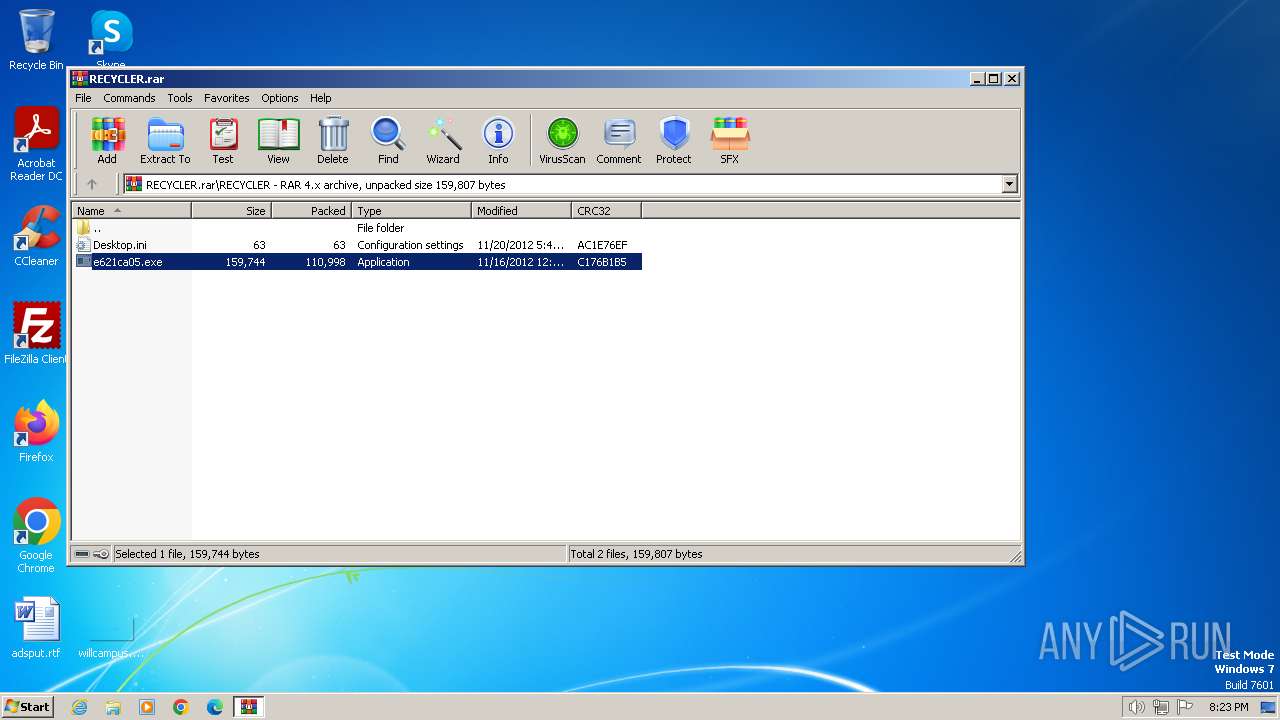
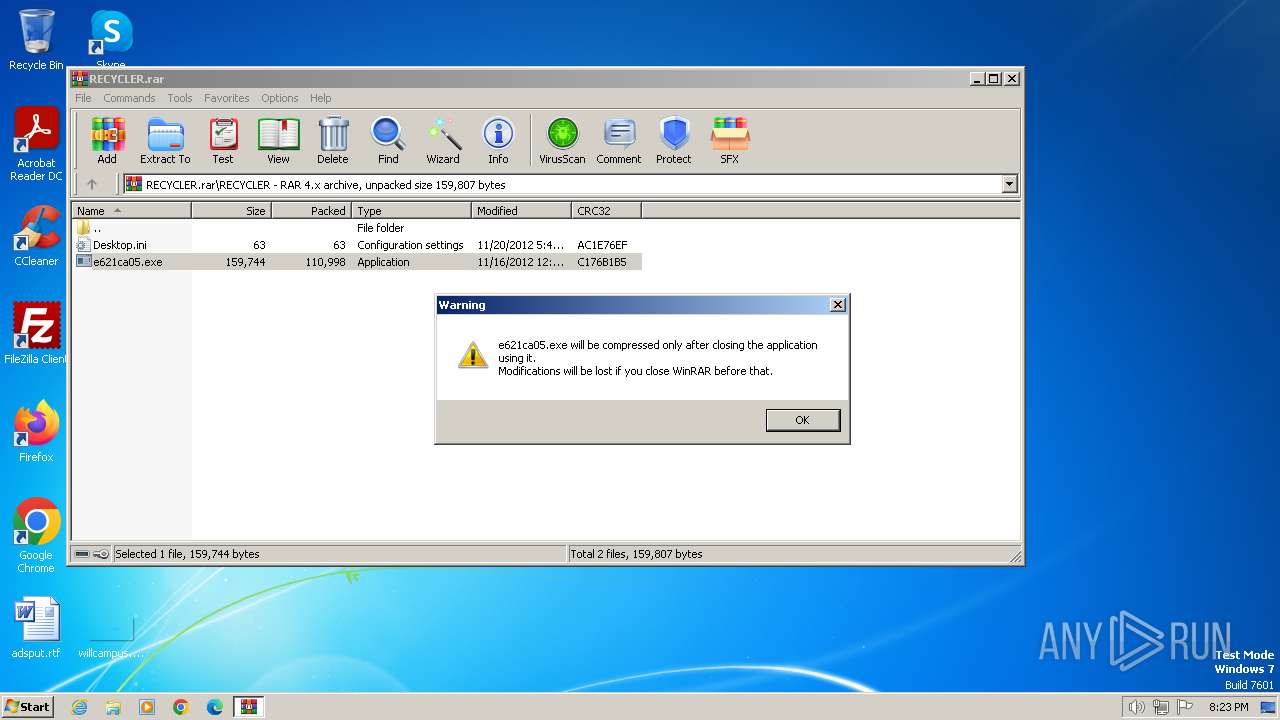
| File name: | RECYCLER.rar |
| Full analysis: | https://app.any.run/tasks/bd922d71-f1d3-412a-bb35-076876c52348 |
| Verdict: | Malicious activity |
| Analysis date: | June 23, 2024, 19:22:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | C39D52F2733504271B2AF8396345C9D7 |
| SHA1: | 26BDCB32B9CA34508566BF727DC08697DDAA71A3 |
| SHA256: | 0E8B35C4D6214660201BDD2BC26599AE63E37E37EBE3E6FAB70A7CC8FBFAA7FE |
| SSDEEP: | 3072:+iXyNwGyqkA3WJsNaDQyo//+t82B85pC7lrPnWvB:+kyNwGuqaDQR//yt8DChreJ |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3380)
Application was injected by another process
- dwm.exe (PID: 460)
- taskeng.exe (PID: 280)
- explorer.exe (PID: 1296)
- ctfmon.exe (PID: 1032)
Runs injected code in another process
- e621ca05.exe (PID: 3264)
Connects to the CnC server
- explorer.exe (PID: 1296)
Changes the autorun value in the registry
- explorer.exe (PID: 1296)
SUSPICIOUS
Starts application from unusual location
- WinRAR.exe (PID: 3380)
- e621ca05.exe (PID: 3264)
- e621ca05.exe (PID: 3280)
- explorer.exe (PID: 1296)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3380)
Application launched itself
- e621ca05.exe (PID: 3280)
Write to the desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 3380)
Executable content was dropped or overwritten
- explorer.exe (PID: 1296)
Connects to unusual port
- explorer.exe (PID: 1296)
INFO
Checks supported languages
- e621ca05.exe (PID: 3280)
- e621ca05.exe (PID: 3264)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3380)
Reads the computer name
- e621ca05.exe (PID: 3264)
Creates files or folders in the user directory
- explorer.exe (PID: 1296)
Drops the executable file immediately after the start
- explorer.exe (PID: 1296)
Reads the Internet Settings
- explorer.exe (PID: 1296)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1296)
Checks proxy server information
- explorer.exe (PID: 1296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 104 |
|---|---|
| UncompressedSize: | 63 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2012:11:20 17:43:58 |
| PackingMethod: | Stored |
| ArchivedFileName: | RECYCLER\Desktop.ini |
Total processes
41
Monitored processes
7
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | taskeng.exe {8F81F50F-8A56-43F4-81CA-1E996579EDDB} | C:\Windows\System32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 460 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1032 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1296 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3264 | C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.39455\RECYCLER\e621ca05.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.39455\RECYCLER\e621ca05.exe | — | e621ca05.exe | |||||||||||
User: admin Company: Abrilabr Integrity Level: MEDIUM Description: Abrilabr Exit code: 0 Version: 9.04.5464 Modules
| |||||||||||||||
| 3280 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.39455\RECYCLER\e621ca05.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.39455\RECYCLER\e621ca05.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Abrilabr Integrity Level: MEDIUM Description: Abrilabr Exit code: 0 Version: 9.04.5464 Modules
| |||||||||||||||
| 3380 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\RECYCLER.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 933
Read events
3 864
Write events
56
Delete events
13
Modification events
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1296) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (1296) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RECYCLER.rar | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
2
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1296 | explorer.exe | C:\Users\admin\AppData\Roaming\Zeeoen.exe | executable | |
MD5:5BCE8B2DFB5E9532520B0206915CF9CC | SHA256:424BEA1E8B83ABFEDB6F58783405ECEAD18F120560D762BCC99A703648D16E9E | |||
| 3380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.39455\RECYCLER\Desktop.ini | ini | |
MD5:E783BDD20A976EAEAAE1FF4624487420 | SHA256:2F65FA9C7ED712F493782ABF91467F869419A2F8B5ADF23B44019C08190FA3F3 | |||
| 3380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.39455\RECYCLER\e621ca05.exe | executable | |
MD5:5BCE8B2DFB5E9532520B0206915CF9CC | SHA256:424BEA1E8B83ABFEDB6F58783405ECEAD18F120560D762BCC99A703648D16E9E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
17
Threats
93
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 2.17.197.241:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.17.198.153:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.219.240.231:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 2.17.197.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67a3611ec3c0260d | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1296 | explorer.exe | 199.2.137.21:1887 | f0001.info | MICROSOFT-CORP-AS | US | whitelisted |
1372 | svchost.exe | 2.17.197.241:80 | ctldl.windowsupdate.com | Akamai International B.V. | BE | unknown |
1372 | svchost.exe | 2.17.198.153:80 | crl.microsoft.com | Akamai International B.V. | BE | unknown |
1372 | svchost.exe | 23.219.240.231:80 | www.microsoft.com | AKAMAI-AS | US | unknown |
1060 | svchost.exe | 2.17.197.240:80 | ctldl.windowsupdate.com | Akamai International B.V. | BE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.wipmania.com |
| unknown |
dns.msftncsi.com |
| shared |
f0001.info |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
f0010.info |
| unknown |
f0100.info |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Reply Sinkhole - Microsoft - 199.2.137.0/24 |
1060 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Reply Sinkhole - Microsoft - 199.2.137.0/24 |
1296 | explorer.exe | Misc activity | ET INFO IRC Nick change on non-standard port |
1296 | explorer.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS IRC - NICK and 3 Letter Country Code |
1296 | explorer.exe | A Network Trojan was detected | ET MALWARE Likely Bot Nick in IRC (USA +..) |
1296 | explorer.exe | A Network Trojan was detected | ET MALWARE Likely Bot Nick in IRC (Country Code ISO 3166-1 alpha-3) |
1296 | explorer.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS IRC - NICK and Possible Windows XP/7 |
1296 | explorer.exe | A Network Trojan was detected | ET MALWARE Backdoor.Win32.Dorkbot.AR Join IRC channel |
1296 | explorer.exe | Misc activity | ET CHAT IRC USER Off-port Likely bot with 0 0 colon checkin |
1060 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Reply Sinkhole - Microsoft - 199.2.137.0/24 |
19 ETPRO signatures available at the full report