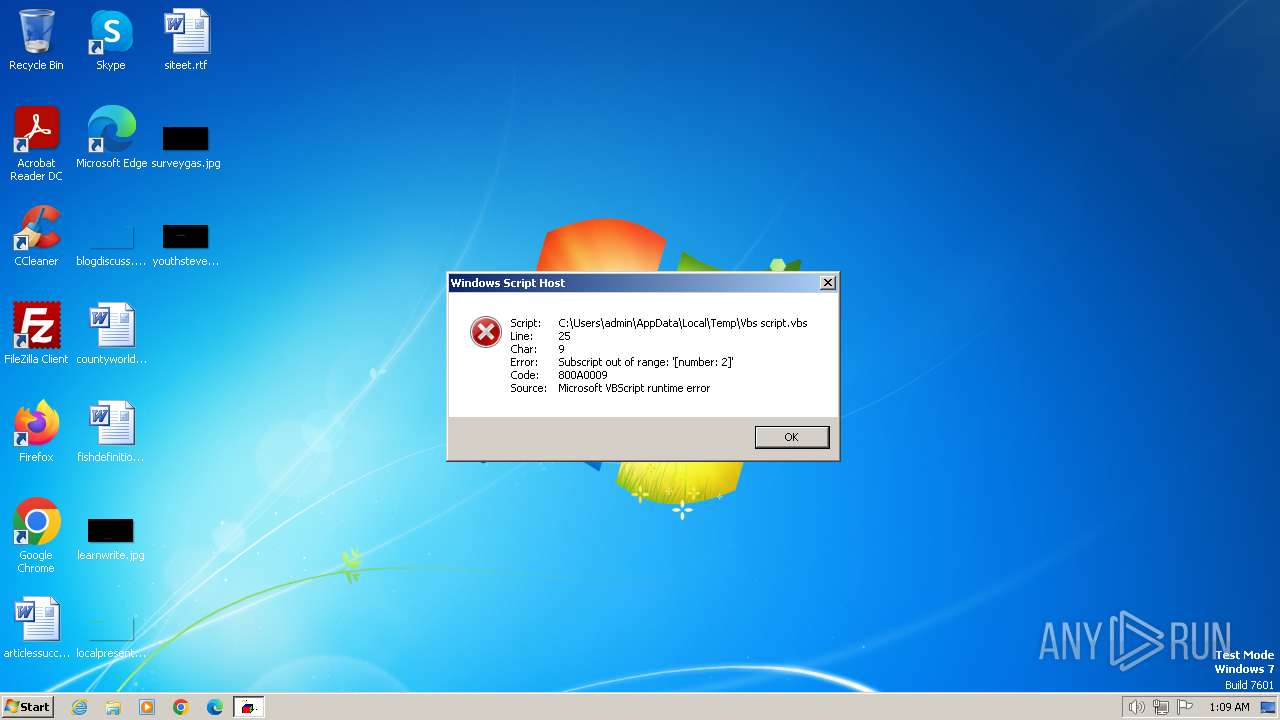
| File name: | Vbs script.vbs |
| Full analysis: | https://app.any.run/tasks/808ce525-b3e8-4880-8dae-80c4dc9c3dba |
| Verdict: | Malicious activity |
| Analysis date: | July 03, 2024, 00:09:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | BC0145B8D4943E8AD13BCFB2D5DAD6F2 |
| SHA1: | 3295E08F7F35AA996C63FEAB8A7D635CBECF3026 |
| SHA256: | 0E6ACBA97219E768A81479A92EF7DAD5A09E3AA4BC9F66651D5E1C27B53B5D8F |
| SSDEEP: | 192:KmODlriLKlfUPwXmy2JtfQdUlp8YOB2i4q6PA1bYsm9Eg3Raw:KmOjlX0nfQwOBEL3Raw |
MALICIOUS
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 3368)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 3368)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 3368)
SUSPICIOUS
Adds/modifies Windows certificates
- wscript.exe (PID: 3368)
Reads the Internet Settings
- wscript.exe (PID: 3368)
INFO
Checks proxy server information
- wscript.exe (PID: 3368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3368 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Vbs script.vbs" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
4 302
Read events
4 211
Write events
68
Delete events
23
Modification events
| (PID) Process: | (3368) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3368) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3368) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3368) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3368) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3368) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (3368) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (3368) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (3368) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (3368) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
5
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3368 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\close[1].htm | html | |
MD5:196CFACAFFB725C92C6D5D4F16289E92 | SHA256:3CD343B356E21807BA2D17E5DE1FE01756EC53BCC76699572E78B0BEFBE5AC6F | |||
| 3368 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8FE92D2CB8EA6728AE5EEF539C967F86 | binary | |
MD5:CC4770AD758C9DDB3BD12497F84C3FAE | SHA256:6A386D28D7A6483F293FC0395732A81B9A2B8270A042D9830E90567B46A3EFBA | |||
| 3368 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:DB64389F667D07BB9516BE87CD572A6E | SHA256:86C877C7FF71CB3AC5ECEF16B14794EFA0DA802C699A40D4EF56EDC0191DD867 | |||
| 3368 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8FE92D2CB8EA6728AE5EEF539C967F86 | binary | |
MD5:F535AD02C3DE4E02308046F891209255 | SHA256:2F0A5BFDA58FCC431CEAF1DA2BBB3A95133734790008A09B8435E5CC7B8D5B8C | |||
| 3368 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:CB9C886943FAD3F70F4CAD18F1618D01 | SHA256:18B6017B9D25A1AB174BCD684195B4B39CDC788E244D073366AEA8375E605059 | |||
| 3368 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
16
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3368 | wscript.exe | GET | 304 | 2.16.164.72:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e8c072ac380ebd16 | unknown | — | — | unknown |
3368 | wscript.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
3368 | wscript.exe | GET | 200 | 95.101.54.114:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgNivXFw%2FpfMOs9enpp0%2Fa21dQ%3D%3D | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 173.222.108.210:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67a3611ec3c0260d | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3368 | wscript.exe | 208.109.234.63:443 | 63.234.109.208.host.secureserver.net | AS-26496-GO-DADDY-COM-LLC | US | unknown |
1372 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3368 | wscript.exe | 2.16.164.72:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
3368 | wscript.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
3368 | wscript.exe | 95.101.54.114:80 | r11.o.lencr.org | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
63.234.109.208.host.secureserver.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r11.o.lencr.org |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |