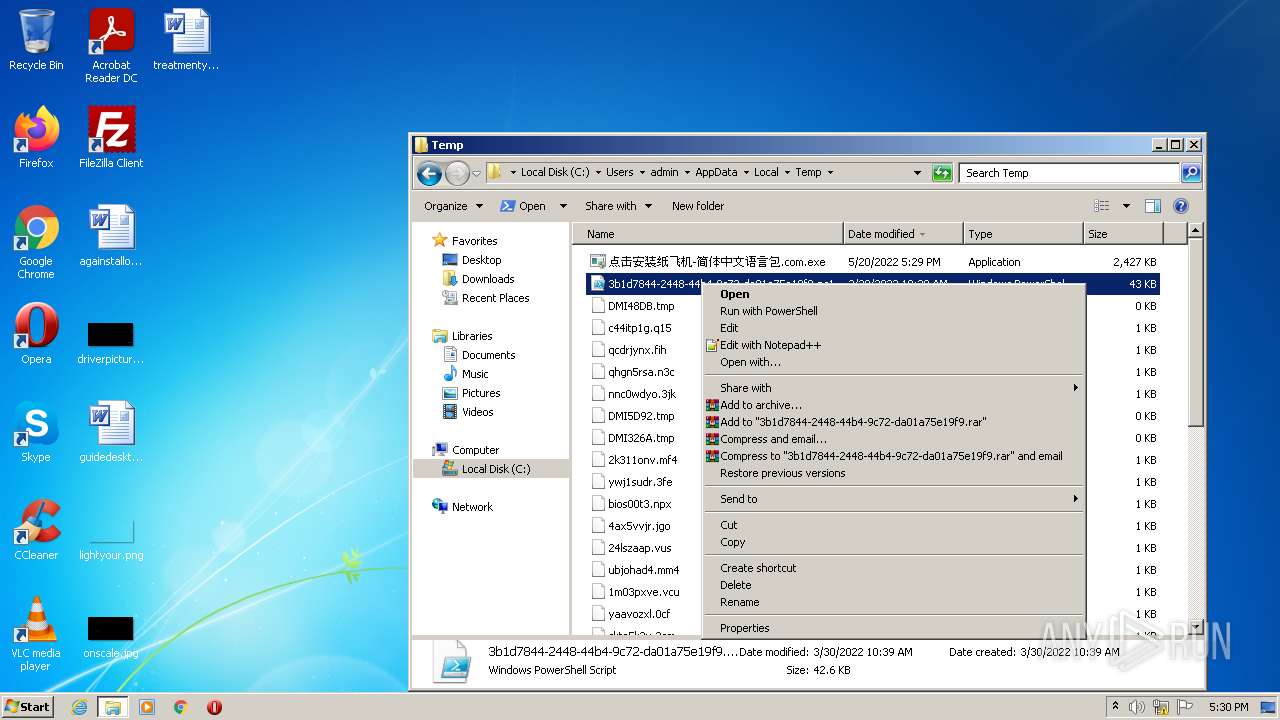
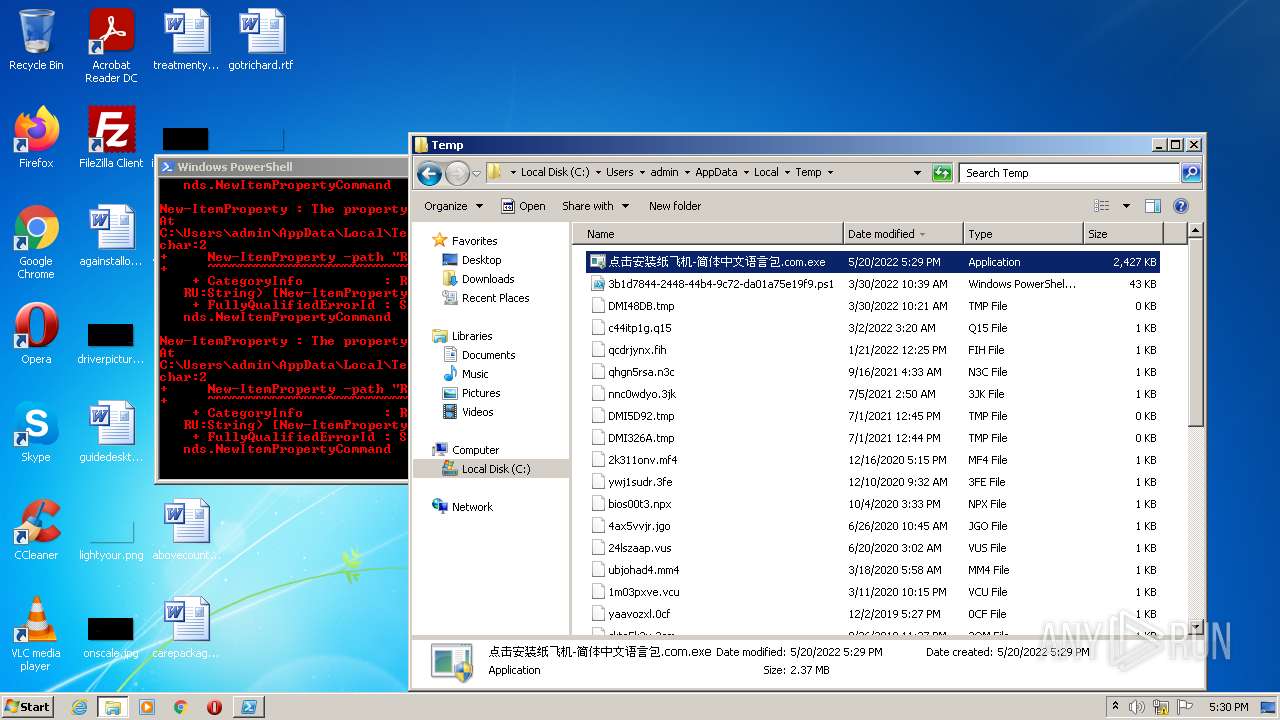
| File name: | 点击安装纸飞机-简体中文语言包.com |
| Full analysis: | https://app.any.run/tasks/0d804a4d-4c96-4ee0-b0be-cdc8a076f2f5 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 16:29:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 392CA1E33128E8BA6FE1417D5CF5569D |
| SHA1: | BAA7421C8394690736A436E036EB17C70D9B070D |
| SHA256: | 0E405E90943AA08BC9BA0F487D63D6EF1D2A1EDFB938C874D0285C3B5EDC3CAB |
| SSDEEP: | 49152:yu/pYQ+jPw/cfm9WDoQzmBo4xaKldv19I227pq0IwAfplRmf3aTzsV8sa7qCj8SW:HYQ+jPwNYhzmBo44Kldv1wq0IwCplRmw |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the computer name
- 点击安装纸飞机-简体中文语言包.com.exe (PID: 3748)
- powershell.exe (PID: 2088)
Checks supported languages
- 点击安装纸飞机-简体中文语言包.com.exe (PID: 3748)
- powershell.exe (PID: 2088)
Reads the date of Windows installation
- powershell.exe (PID: 2088)
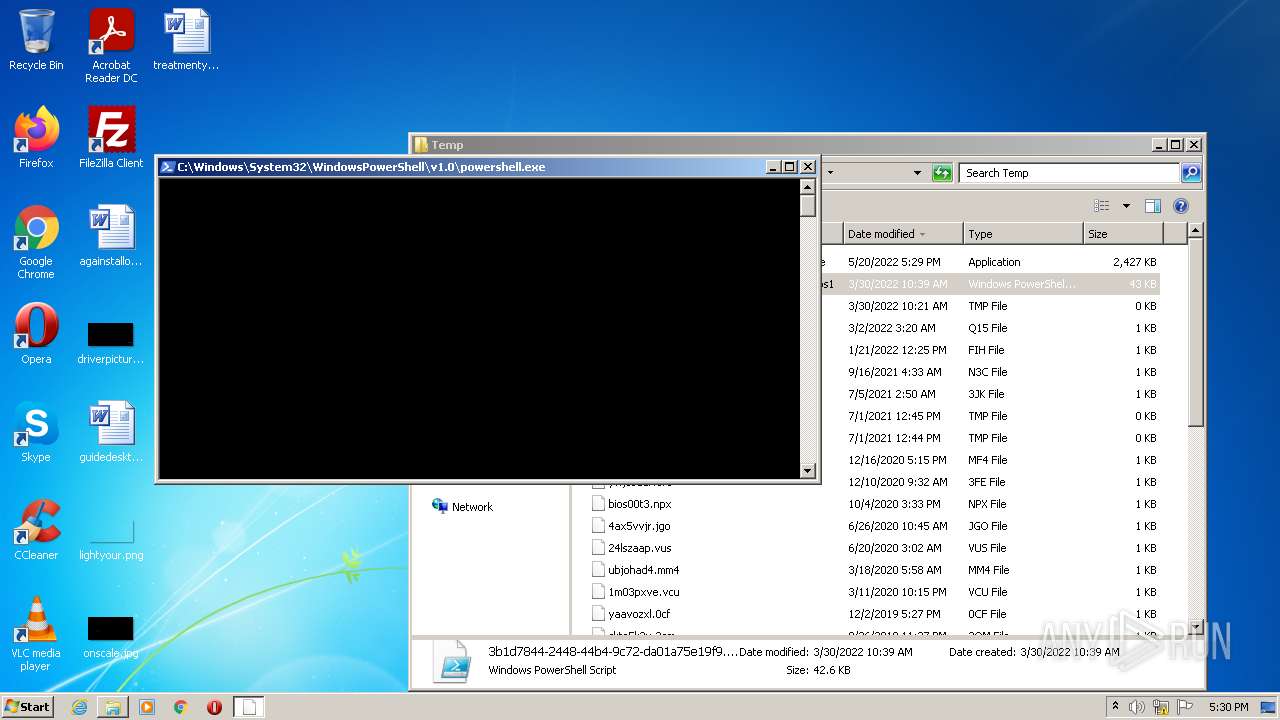
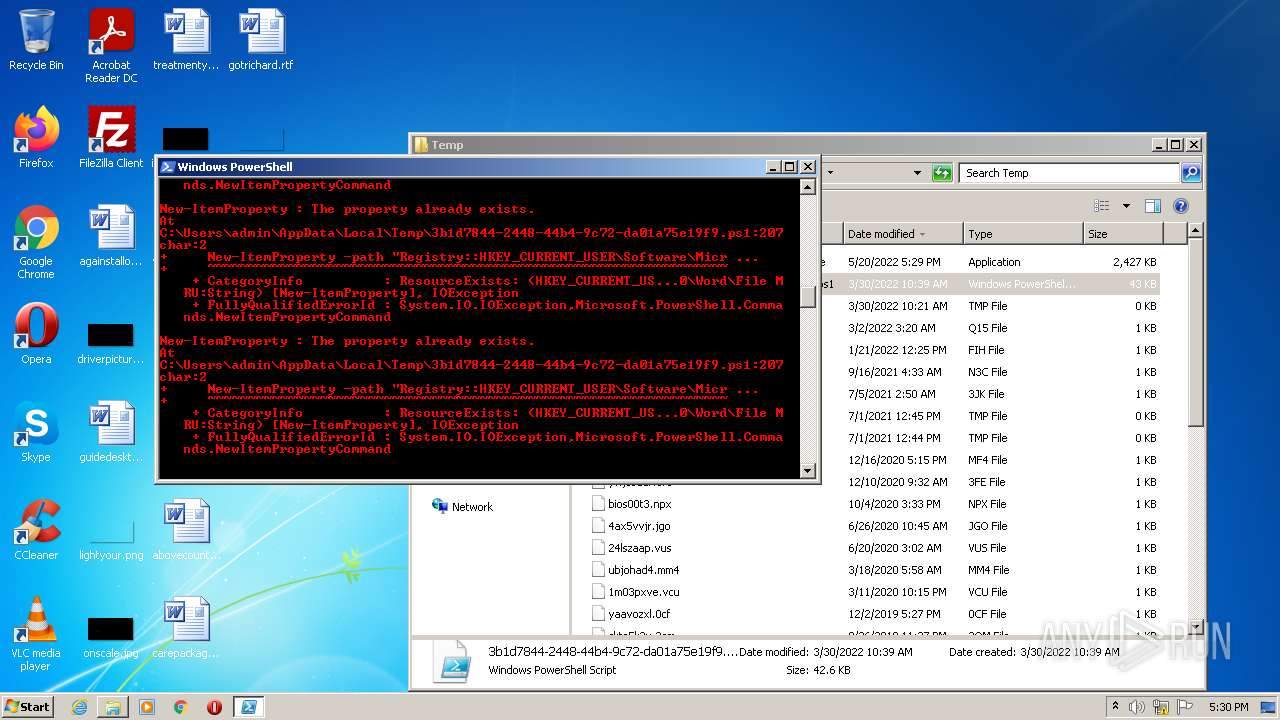
Executes PowerShell scripts
- powershell.exe (PID: 2088)
Creates files in the user directory
- powershell.exe (PID: 2088)
INFO
Manual execution by user
- powershell.exe (PID: 2088)
- firefox.exe (PID: 684)
- 点击安装纸飞机-简体中文语言包.com.exe (PID: 2084)
Checks Windows Trust Settings
- powershell.exe (PID: 2088)
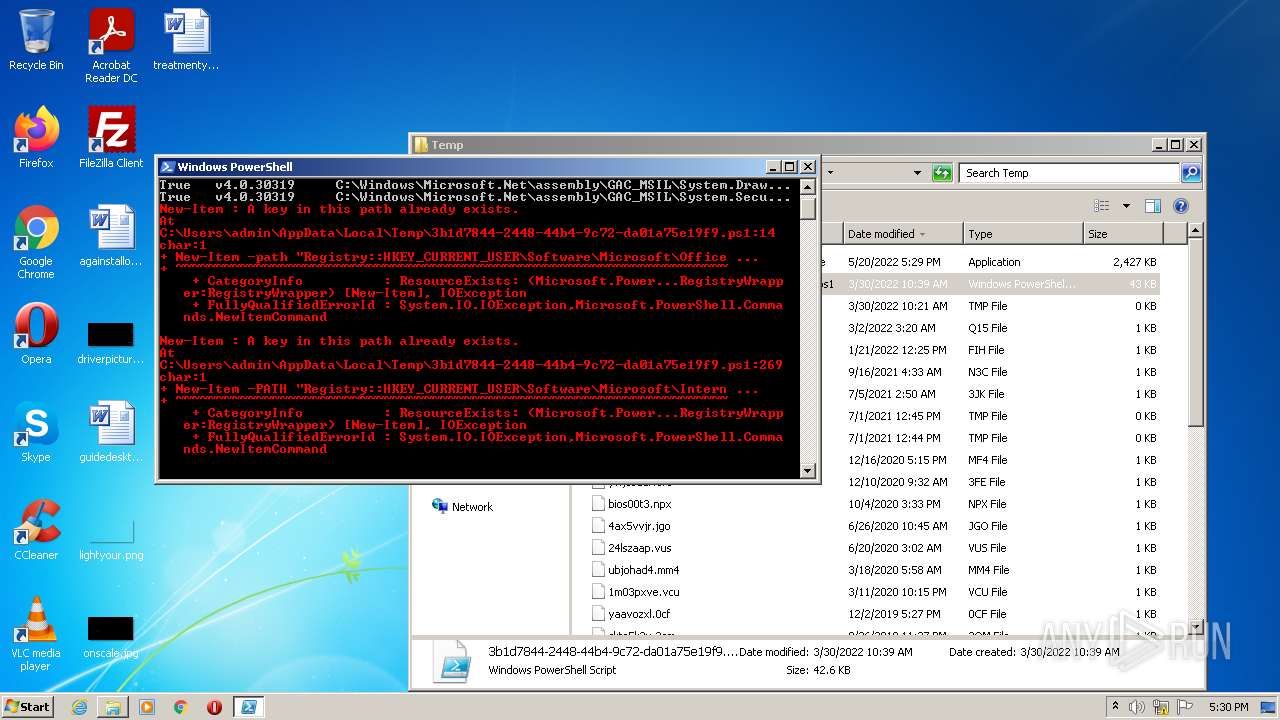
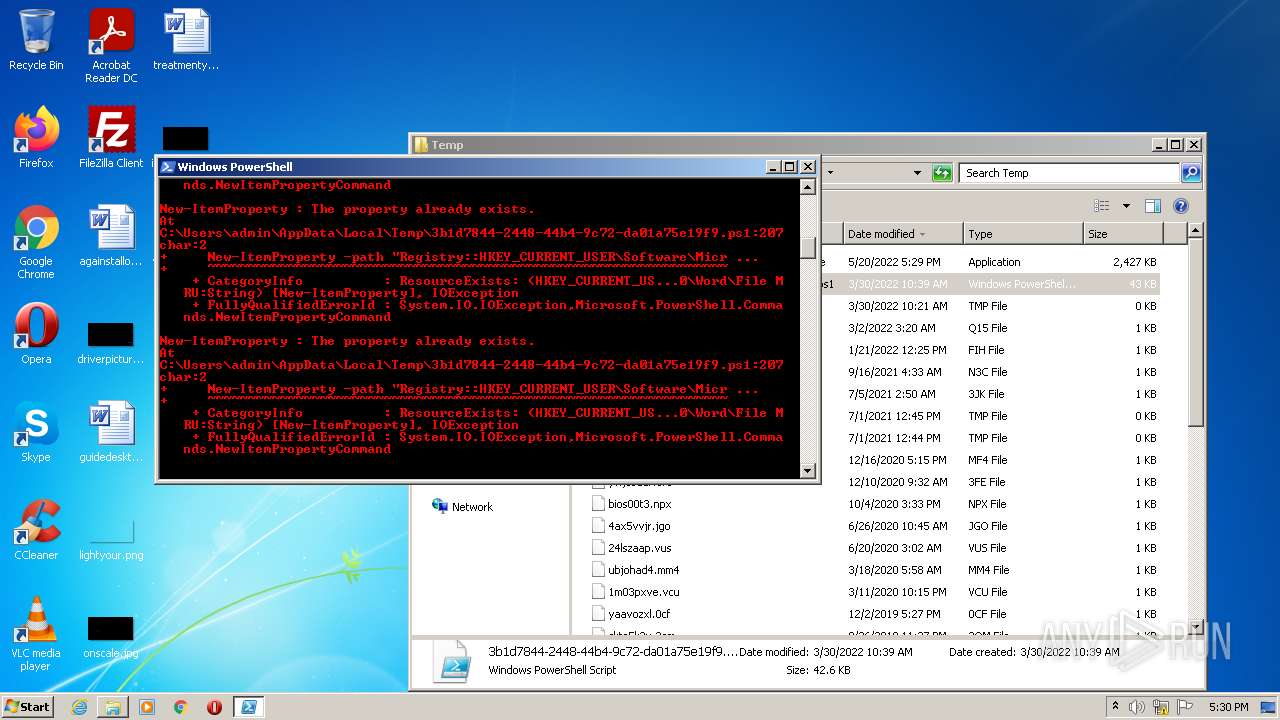
Reads Microsoft Office registry keys
- powershell.exe (PID: 2088)
Application launched itself
- firefox.exe (PID: 684)
- firefox.exe (PID: 1124)
Checks supported languages
- firefox.exe (PID: 684)
- firefox.exe (PID: 1124)
- firefox.exe (PID: 3140)
Reads the computer name
- firefox.exe (PID: 1124)
- firefox.exe (PID: 3140)
Reads CPU info
- firefox.exe (PID: 1124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (16.9) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (15) |
| .exe | | | Win32 Executable (generic) (2.4) |
| .exe | | | Generic Win/DOS Executable (1) |
EXIF
EXE
| ProductVersion: | 1.0.0.1 |
|---|---|
| ProductName: | TODO: <产品名> |
| OriginalFileName: | zh-cnv55.exe |
| LegalCopyright: | Copyright (C) 2022 |
| InternalName: | zh-cnv55.exe |
| FileVersion: | 1.0.0.1 |
| FileDescription: | TODO: <文件说明> |
| CompanyName: | TODO: <公司名> |
| CharacterSet: | Unicode |
| LanguageCode: | Unknown (000F) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.1 |
| FileVersionNumber: | 1.0.0.1 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x135d14 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 1067520 |
| CodeSize: | 1416704 |
| LinkerVersion: | 10 |
| PEType: | PE32 |
| TimeStamp: | 2022:05:20 04:55:32+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 20-May-2022 02:55:32 |
| Detected languages: |
|
| CompanyName: | TODO: <公司名> |
| FileDescription: | TODO: <文件说明> |
| FileVersion: | 1.0.0.1 |
| InternalName: | zh-cnv55.exe |
| LegalCopyright: | Copyright (C) 2022 |
| OriginalFilename: | zh-cnv55.exe |
| ProductName: | TODO: <产品名> |
| ProductVersion: | 1.0.0.1 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 20-May-2022 02:55:32 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00159D4A | 0x00159E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.5079 |
.rdata | 0x0015B000 | 0x000455AE | 0x00045600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.99238 |
.data | 0x001A1000 | 0x0000F9BC | 0x00008200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.92675 |
.rsrc | 0x001B1000 | 0x0008D918 | 0x0008DA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.98741 |
.reloc | 0x0023F000 | 0x00029718 | 0x00029800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.02634 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.05194 | 866 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 2.74274 | 180 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
3 | 2.34038 | 308 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
4 | 2.34004 | 308 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
5 | 2.51649 | 308 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
6 | 2.45401 | 308 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
7 | 0.38158 | 34 | Latin 1 / Western European | Chinese - PRC | RT_STRING |
8 | 2.34505 | 308 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
9 | 2.34864 | 308 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
10 | 2.31114 | 308 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
IMM32.dll |
KERNEL32.dll |
MSIMG32.dll |
OLEACC.dll |
OLEAUT32.dll |
SHELL32.dll |
Total processes
49
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1124 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2084 | "C:\Users\admin\AppData\Local\Temp\点击安装纸飞机-简体中文语言包.com.exe" | C:\Users\admin\AppData\Local\Temp\点击安装纸飞机-简体中文语言包.com.exe | — | Explorer.EXE | |||||||||||
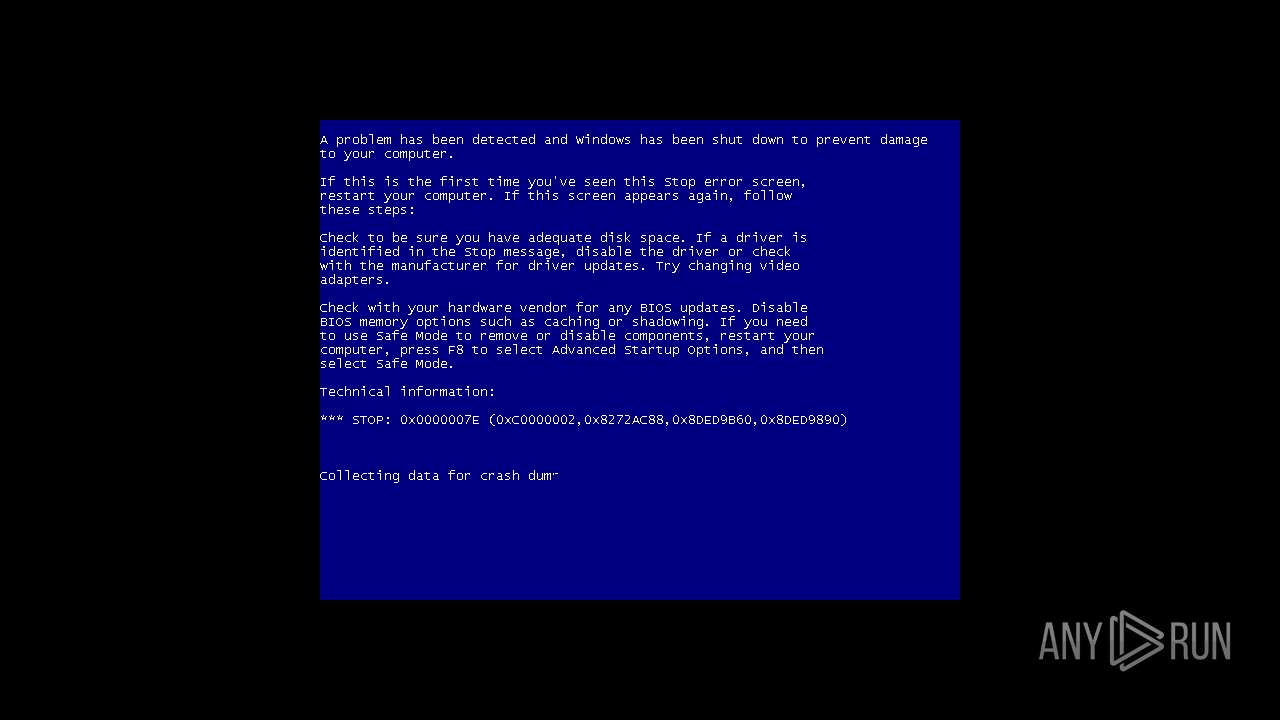
User: admin Company: TODO: <公司名> Integrity Level: MEDIUM Description: TODO: <文件说明> Exit code: 3221226540 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2088 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\AppData\Local\Temp\3b1d7844-2448-44b4-9c72-da01a75e19f9.ps1" "-Command" "if((Get-ExecutionPolicy ) -ne AllSigned) { Set-ExecutionPolicy -Scope Process Bypass }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\AppData\Local\Temp\点击安装纸飞机-简体中文语言包.com.exe" | C:\Users\admin\AppData\Local\Temp\点击安装纸飞机-简体中文语言包.com.exe | — | Explorer.EXE | |||||||||||
User: admin Company: TODO: <公司名> Integrity Level: MEDIUM Description: TODO: <文件说明> Exit code: 3221226540 Version: 1.0.0.1 Modules
| |||||||||||||||
| 3140 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1124.0.119330745\1889524912" -parentBuildID 20201112153044 -prefsHandle 1100 -prefMapHandle 860 -prefsLen 1 -prefMapSize 238726 -appdir "C:\Program Files\Mozilla Firefox\browser" - 1124 "\\.\pipe\gecko-crash-server-pipe.1124" 1188 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 3748 | "C:\Users\admin\AppData\Local\Temp\点击安装纸飞机-简体中文语言包.com.exe" | C:\Users\admin\AppData\Local\Temp\点击安装纸飞机-简体中文语言包.com.exe | Explorer.EXE | ||||||||||||
User: admin Company: TODO: <公司名> Integrity Level: HIGH Description: TODO: <文件说明> Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
3 816
Read events
3 745
Write events
71
Delete events
0
Modification events
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\IntelliForms\Storage2 |
| Operation: | write | Name: | 8B1BFEF64249C5001CB3BCB1810F164C2B20AB1F2D |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000B4C3BC0BD7C4D14FA00B123D5E6EF7FB0000000002000000000010660000000100002000000001CF37F5544E7DEE37A78F841E630A4274493F024CA0ED41F93352C87A1D3C21000000000E8000000002000020000000D85050EF69444837624AB5EA37B123D8F2921B3FDA0E4B8037F07C9913A5398D900000007B80F02C23331E96A875DE895938C3F459EF618864D8CE094ED7706E49F80D1836F0FA1993EB007213D3B26B3FEE6F5FB48DE16F7089050B4D50C908163CA6D4D72FC3C3D0E6B1F39D7AE6DDD69E6C3EFFE94690EA0FEFF4E285DC499D5D136B0FEBDAFB864E24A4DC2FF9EFFFC56E65F5C0E3622DEC456C30A336E1F570C67A267FE1B353994989268977A15D29468140000000297174344D59CC4F41057559D66CB817C72A1E079F33C04136B57A8952075CF1E3055DC6AB735F4BFB17993D6C3BB2586D3973257DA7126F078B18C35392C867 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\IntelliForms\Storage2 |
| Operation: | write | Name: | 2D50F97810C80E64C8DB6DC48F2302DEDD8A138AA2 |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000B4C3BC0BD7C4D14FA00B123D5E6EF7FB00000000020000000000106600000001000020000000D6B74CE0E0AB37F0767A5703FD5227BFEC99EE5CB5371327CB3DCA2A7BA1F950000000000E8000000002000020000000A0703CB25C5BCBA1C7A0A9B277119C6EFAFF44C031B1EAFFE2D3045A8D814BA0900000003B42DDC444C168E826BCD62A9754EF4A86A331DE776F7C50214C2C1E34EFA94930D4AD4C85BE2DCC7F6B0E0339DDA6372628656452BB324114D30701B505A20D156874150F8EC7498B15C445895F358C16DABB114E3636AAB32BC2177FED3BCF4F8863AA60645B6AA5D36208899AB3B2E1A69667FC5DF7DD0A705CD6712E9CE8100A4B08CD9B6B7D765A3231FCE1C40D40000000E288D46B2CEDF8E2A6D4A741DEEA128C2D1C48A76436E69592922B1E5BD9930A0FF6927631B53D4E933125BE45CAE69ECDF53811499445D58F2C71AF64F1DA29 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\IntelliForms\Storage2 |
| Operation: | write | Name: | 0768C3934AE3F30784DD58C1E8931D5CAEE0B41DB9 |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000B4C3BC0BD7C4D14FA00B123D5E6EF7FB0000000002000000000010660000000100002000000048CF9B79D127D00D5CE50EEF548E087EBC91CC54709D5DFA91DBFE32EF5058AA000000000E8000000002000020000000597633C6C135BFDFA5210141FA17761A499116150E179BD78730305C68A0BE4A900000004ACABF3A8BE2866F04AA9D06AFF76A0E37CEFB5FD4E359067986854B7D6423393892CA0E3D59FF6C8C47F5E5FF768CEE253D253656F67F70EF366AD9F3C49546AABB90932AB0A53E6CB1F34751F11A3F106EAD4CEA36C631D5208E5CE663545B08ABD16A78E757BAB9BAC28CD03A8D77A678366EAD20E0A12E05E1D52062194AACB61CCD8D95C2410FC537DFE90FE97C40000000334E3844CDDDA37E1E788937756BC7BF2B7C2706AB246602FE0423DE644DCC75C255A28C3B1F5B600C1D426DDFB5FB69BEBF1E50AC98C41E848D95F40F5D8FE5 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\IntelliForms\Storage2 |
| Operation: | write | Name: | FE04CF6903375EE3F5094A46A9393F4FFAEF2427E7 |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000B4C3BC0BD7C4D14FA00B123D5E6EF7FB00000000020000000000106600000001000020000000BD9D96051FAB316EFA36C4AA0B81F198E062B3E482CF69BDC7BF0D22D3D02A24000000000E80000000020000200000003185C923B2BBDA14670BB7C9EA77351FCDFD7D3845467EE863A882ED32D8670490000000817697B51BE2AA9FF2F60E79F2E5977BB626227C68C3B489D298C1236A4AFF0AB143490BDCF7D49FBCEBCABE6EC027C87831F56B55110F48B20B2FFBEC92DB9C3BD9E4E2ABA89C64EC408A21D15114E29204D4E25E4226005A063A8B57B21EF65C8C0BB46A7E89165A069C1764EF56358DAA7FB733281258C918ABE1D5560858CE8E275DA1BE93695F544EA4177BD71E4000000088FB16D6ED62FBC942808046890411A340F7A23C29A5E65C23A2A15271F9C9FB812BF4F5AB3A24C7A18C839987664B8E014E8EB87F33D5EC8FE25FCDBE205822 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\IntelliForms\Storage2 |
| Operation: | write | Name: | A8E38E656BA0A386DD7A47E98467AD11339C6E0F2E |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000B4C3BC0BD7C4D14FA00B123D5E6EF7FB000000000200000000001066000000010000200000007D624E80070BB0C720F6AC4C971FAF6E1686832809777BFD9D9562AC9A933C6D000000000E8000000002000020000000846B4CFF93093DFE78276F770F00740BA906C0AB71A47D5BB3AF347060EE087190000000E511D7C2A9DEBDD2B71496B4AF9197EB8BB1B82A219BADE3DBDA23DE7B2315E2D9CF4A5497B70574736D7172517EE3722AE2BBC2FFD776C0F19CF06E15FEF6816EB665D79061C08B73D09E1C039E26FB576BC5DD8298610501087F694CD9C5A2015C79284A9A04655F4F27235069A756542FBA30A434755EFEFDC8504DA511DEBF5650F767AB836EFC8D8774882A356F40000000DB3E131B1A43EED76F59A71CC115BD5E49AF54BE3CF34AD47C15A57EA135B31DF868FFE7067BD8B3D6E153AEB5145D27F7F80518784C62C0C7F1F6AB576F003A | |||
Executable files
0
Suspicious files
29
Text files
30
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF103c6e.TMP | binary | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\L9NMNXUAR3XPCHBK6N4K.temp | binary | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\Desktop\valuesunderstanding.png | image | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\Desktop\initialinvolved.jpg | image | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\Desktop\innchris.jpg | image | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\valuesunderstanding.png.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\Desktop\restaurantstheir.jpg | image | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\innchris.jpg.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\4ships4r.2u1.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report