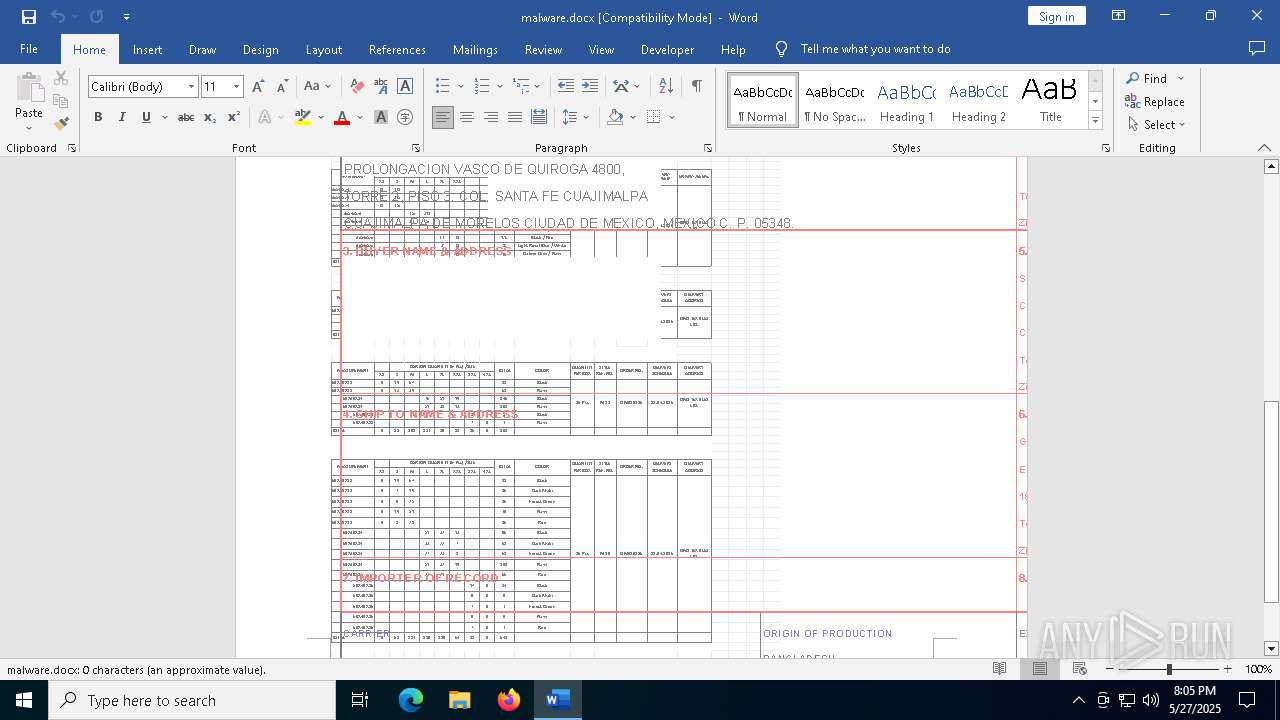
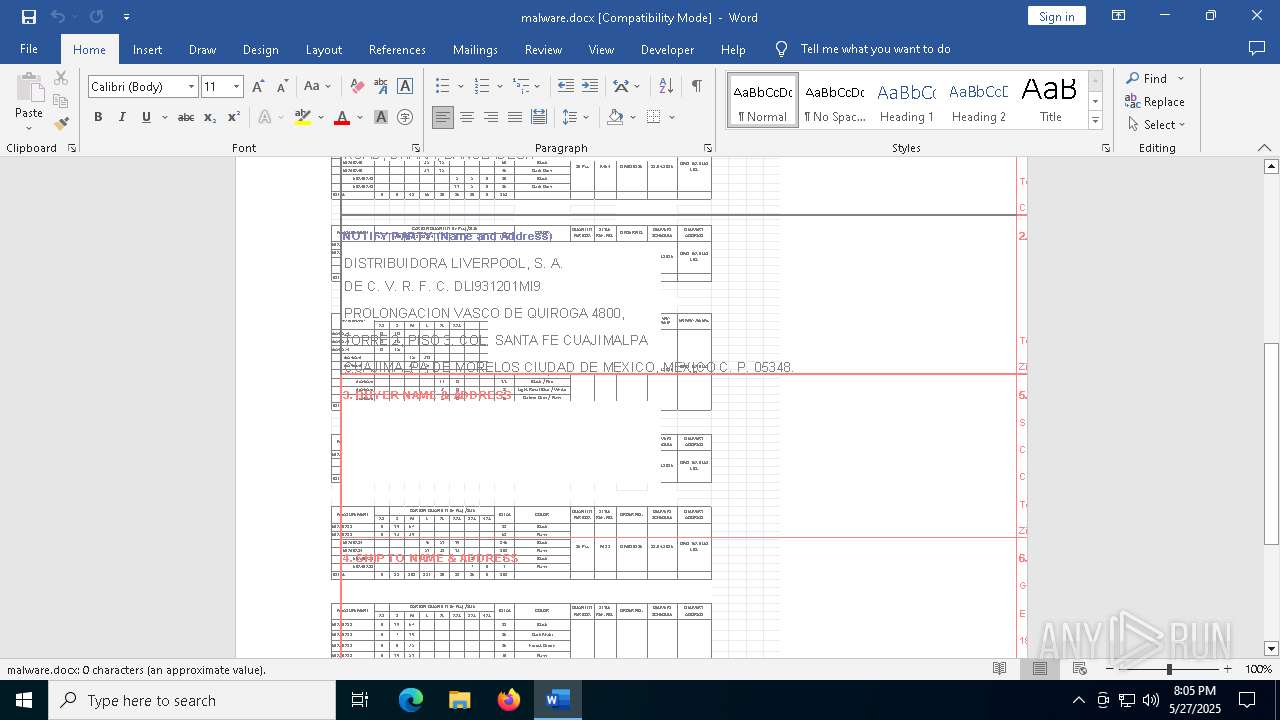
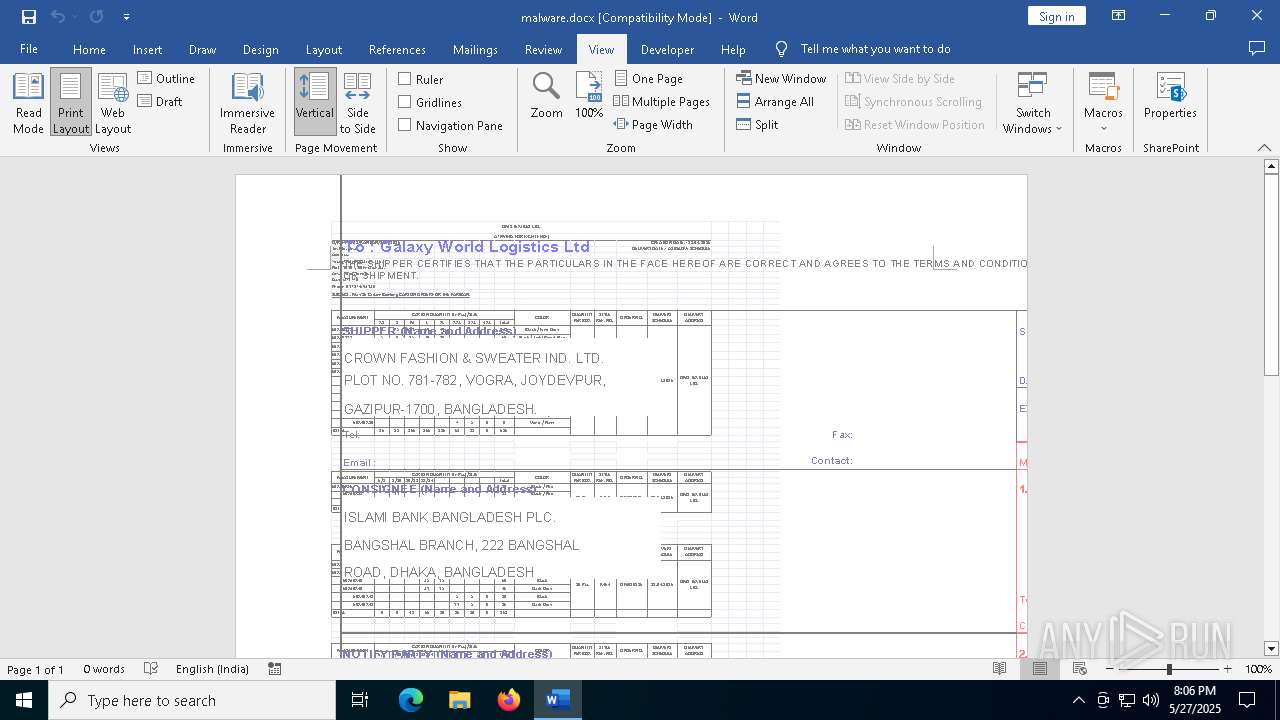
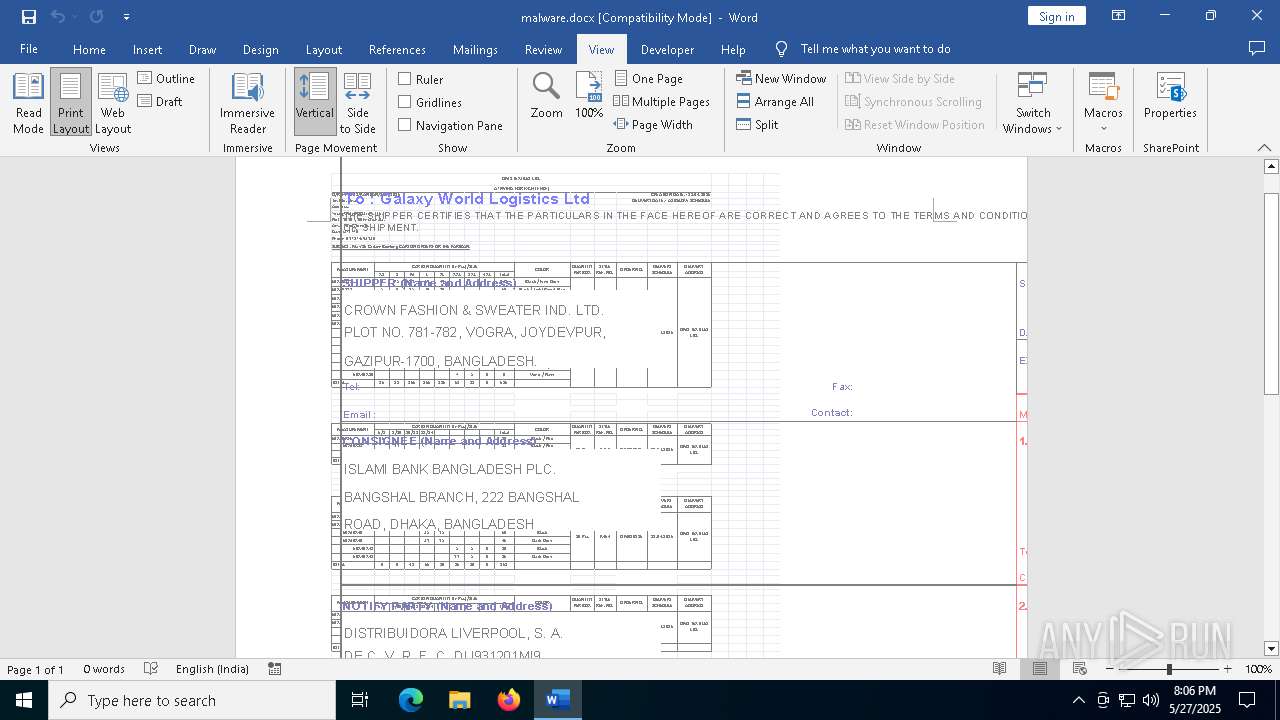
| File name: | malware.docx |
| Full analysis: | https://app.any.run/tasks/0ef2f622-e410-4f75-9bc3-407a12c095bc |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 20:05:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | CA820A526E7F4BB5D6BB6ACE7DF155B2 |
| SHA1: | 6AB81D9C8F19D628D254950DCEDDFE420F832A6E |
| SHA256: | 0E36739707CFD78EFE2B675B3F9F68E370C55C7DE967752A73EAEB7A8CCB54B8 |
| SSDEEP: | 6144:Gergf0v3lHTdHDLZg6CxCNDqipLTHWh7MA7gAj3zv:s0PlHTd/ZQCoYLTH1ggWDv |
MALICIOUS
EXPLOIT has been detected (SURICATA)
- WINWORD.EXE (PID: 2244)
SUSPICIOUS
Connects to the server without a host name
- WINWORD.EXE (PID: 2244)
INFO
Reads the time zone
- WINWORD.EXE (PID: 2244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:27 13:04:60 |
| ZipCRC: | 0x309c932b |
| ZipCompressedSize: | 443 |
| ZipUncompressedSize: | 2568 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | Grizli777 |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 12 |
| Keywords: | - |
| LastModifiedBy: | 91974 |
| RevisionNumber: | 2 |
| CreateDate: | 2025:05:18 17:03:00Z |
| ModifyDate: | 2025:05:18 17:04:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | 91974 |
| Description: | - |
Total processes
139
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2244 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\malware.docx /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7720 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7764 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7892 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "1E7E0D53-0CCE-4E81-BAEB-1BFB4291BD82" "7968302C-B24E-4D35-AE6D-B989F5F924DF" "2244" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
17 274
Read events
16 146
Write events
1 032
Delete events
96
Modification events
| (PID) Process: | (2244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (2244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | &o) |
Value: 漦)ࣄ | |||
| (PID) Process: | (2244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Word\AddinsData\Genko.Connect12 |
| Operation: | write | Name: | LoadCount |
Value: 5 | |||
| (PID) Process: | (2244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | FilePath |
Value: officeclient.microsoft.com\4D3449CC-40BF-4016-A2F5-51A1281B62E5 | |||
| (PID) Process: | (2244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | StartDate |
Value: 50C24BA842CFDB01 | |||
| (PID) Process: | (2244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | EndDate |
Value: 5082B5D20BD0DB01 | |||
| (PID) Process: | (2244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\AddInLoadTimes |
| Operation: | write | Name: | Genko.Connect12 |
Value: 040000009D0000002F0000003F0000001000000000000000 | |||
| (PID) Process: | (2244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | bo) |
Value: 潢)ࣄ | |||
| (PID) Process: | (2244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\2244 |
| Operation: | write | Name: | 0 |
Value: 0B0E102CB44152599A3F4AA08706B14D7A4B97230046D186EEBEAAE8F3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DA200C2190000C50E8908C91003783634C511C411D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (2244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | -p) |
Value: 2D702900C40800000600000001000000C7DF58A842CFDB016E000000020000005E0000000400000063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C006C006F00630061006C005C00740065006D0070005C006D0061006C0077006100720065002E0064006F0063007800000000000000 | |||
Executable files
0
Suspicious files
113
Text files
50
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\4D3449CC-40BF-4016-A2F5-51A1281B62E5 | xml | |
MD5:0F7D23769BD54D1F21CCD1C567D0BE7D | SHA256:EEE1F8C091006AC568CEBEB5D9E8CC65E5F4396605712C78AF184EBEE9D04686 | |||
| 2244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 2244 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D3E33CAF35AFD67E2FD49D09E15909B5_04EECEE476F0EB29549174232867253B | der | |
MD5:325FC5ED32A5ACAA441807891170A567 | SHA256:BDF4746C553F76E0CF0C3DE73AD6EB981E64734FD134045B0D2E3258FA7A4922 | |||
| 2244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$alware.docx | pgc | |
MD5:34B7FFF76A5BFFA428180AB29A1F346F | SHA256:D856C97769C4A66469EF751C3AEA4DE3A11339F1EF43A217F738686DCA7E6548 | |||
| 2244 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:38D76B3178E469C2CA647D9CC1D8A224 | SHA256:E3BBDD9E37F05701211CDFCF2EBED28CB769A349EF766FE5B4CE889EE3D3A555 | |||
| 2244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:AB207B9279737B1A7A6446DB96E2F57E | SHA256:9A04622E3BE47F23F7E4AF217B07ED9763C0AFD2613D2FAFCF9A740925F1B027 | |||
| 2244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:402A83D123EB9B0E2678AA6AE0F07900 | SHA256:DF395D5536EE310E747AE880AD743D2FDC702A56414D93DC7D4262CCF7420451 | |||
| 2244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:B5038306CF25CBA362EACC40A969E52A | SHA256:133079071E86CB987AB7EA1ED3B143595D23DCC9D4AFBA7834A58AE8F7ADD807 | |||
| 2244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{F4CB243F-FC68-4B48-A062-168805A76FFC}.tmp | smt | |
MD5:830FBF83999E052538EAF156AB6ECB17 | SHA256:D5098A2CEAE815DB29CD53C76F85240C95DC4D2E3FEDDD71D628617064C29869 | |||
| 2244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\CE8B14F9.doc | text | |
MD5:9FEC8CF2A72C853744F3CACEC08D7454 | SHA256:CEB372BB4B79E14AF6090665BD36E42E7A38F1E7B13BAF964CFC9250222012DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
67
DNS requests
28
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2244 | WINWORD.EXE | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
2244 | WINWORD.EXE | GET | 200 | 184.24.77.52:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgY6qspBkOcnB576yeW36W0Y1A%3D%3D | unknown | — | — | whitelisted |
2244 | WINWORD.EXE | HEAD | 200 | 107.172.132.32:80 | http://107.172.132.32/700/bgv/seethebestthingswithnicepersongivengoodthingsforhim______seethebestthingswithnicepersongivengoodthingsforhim________seethebestthingswithnicepersongivengoodthingsforhim.doc | unknown | — | — | unknown |
2244 | WINWORD.EXE | GET | 200 | 107.172.132.32:80 | http://107.172.132.32/700/bgv/seethebestthingswithnicepersongivengoodthingsforhim______seethebestthingswithnicepersongivengoodthingsforhim________seethebestthingswithnicepersongivengoodthingsforhim.doc | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2244 | WINWORD.EXE | HEAD | 200 | 107.172.132.32:80 | http://107.172.132.32/700/bgv/seethebestthingswithnicepersongivengoodthingsforhim______seethebestthingswithnicepersongivengoodthingsforhim________seethebestthingswithnicepersongivengoodthingsforhim.doc | unknown | — | — | unknown |
2244 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1196 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5796 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2244 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
2244 | WINWORD.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2244 | WINWORD.EXE | 2.16.10.163:443 | omex.cdn.office.net | Akamai International B.V. | AT | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
short.udon-morishige.com |
| unknown |
x1.c.lencr.org |
| whitelisted |
r11.o.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2244 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
2244 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
2244 | WINWORD.EXE | Potentially Bad Traffic | ET HUNTING Microsoft Office User-Agent Requesting A Doc File |
2244 | WINWORD.EXE | Misc Attack | EXPLOIT [ANY.RUN] Obfuscated RTF document including the CLSID of the Equation Editor (CVE-2017-11882) |
2244 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
2244 | WINWORD.EXE | Misc activity | ET USER_AGENTS Microsoft Office Existence Discovery User-Agent |