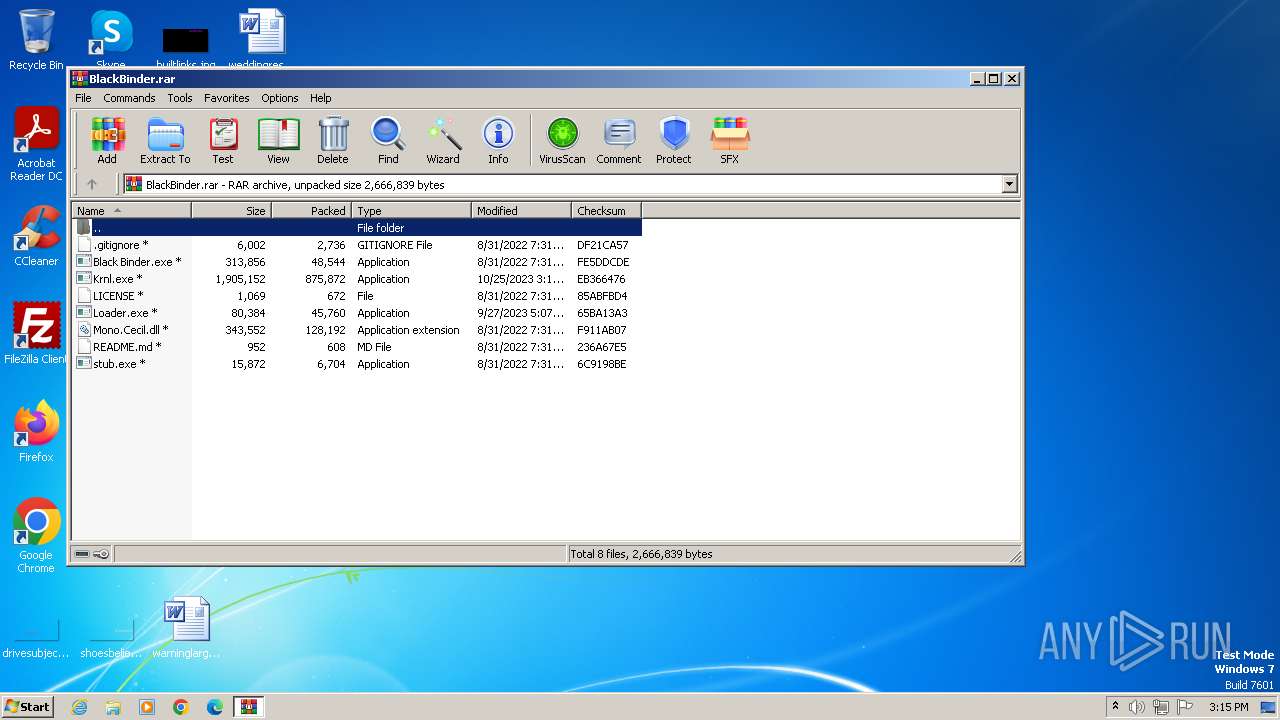
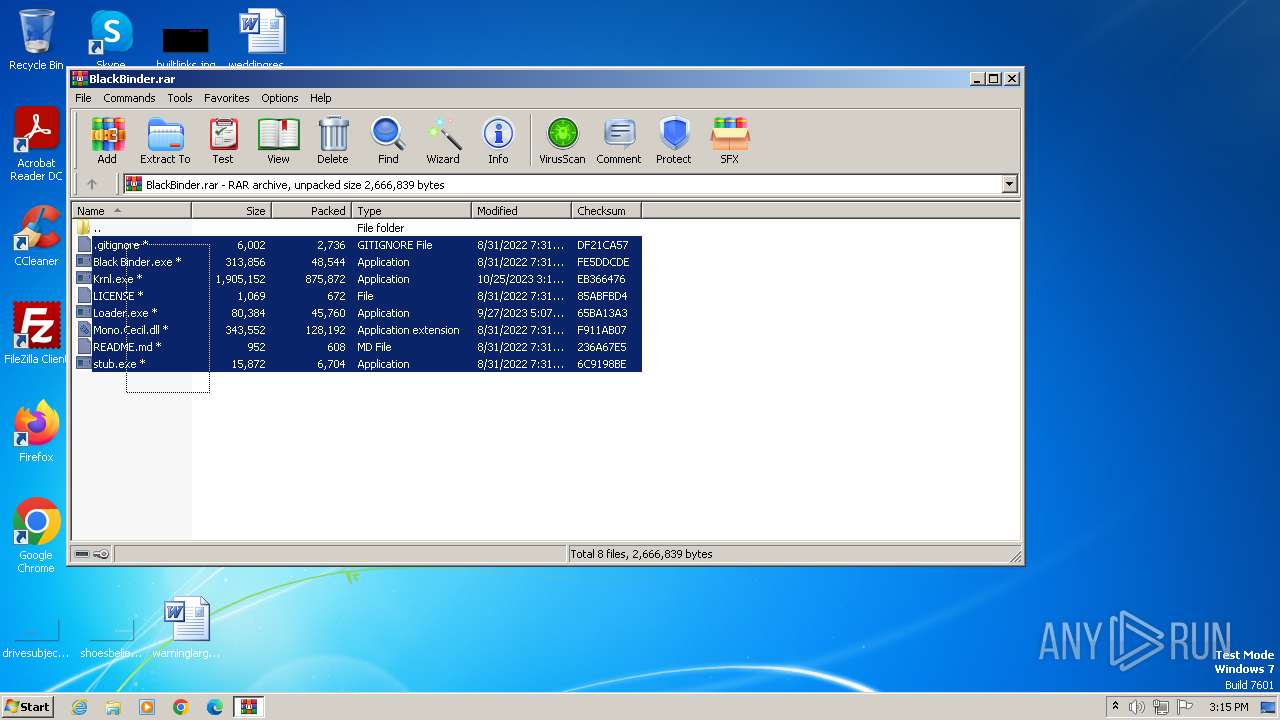
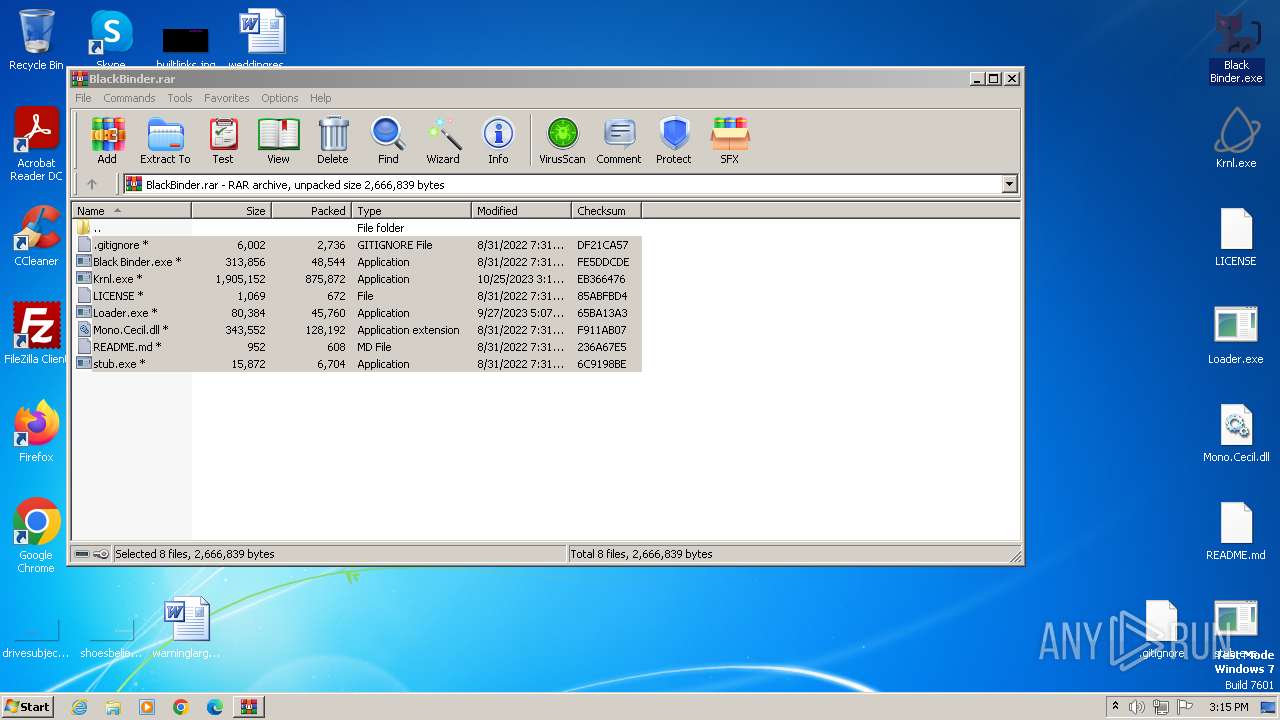
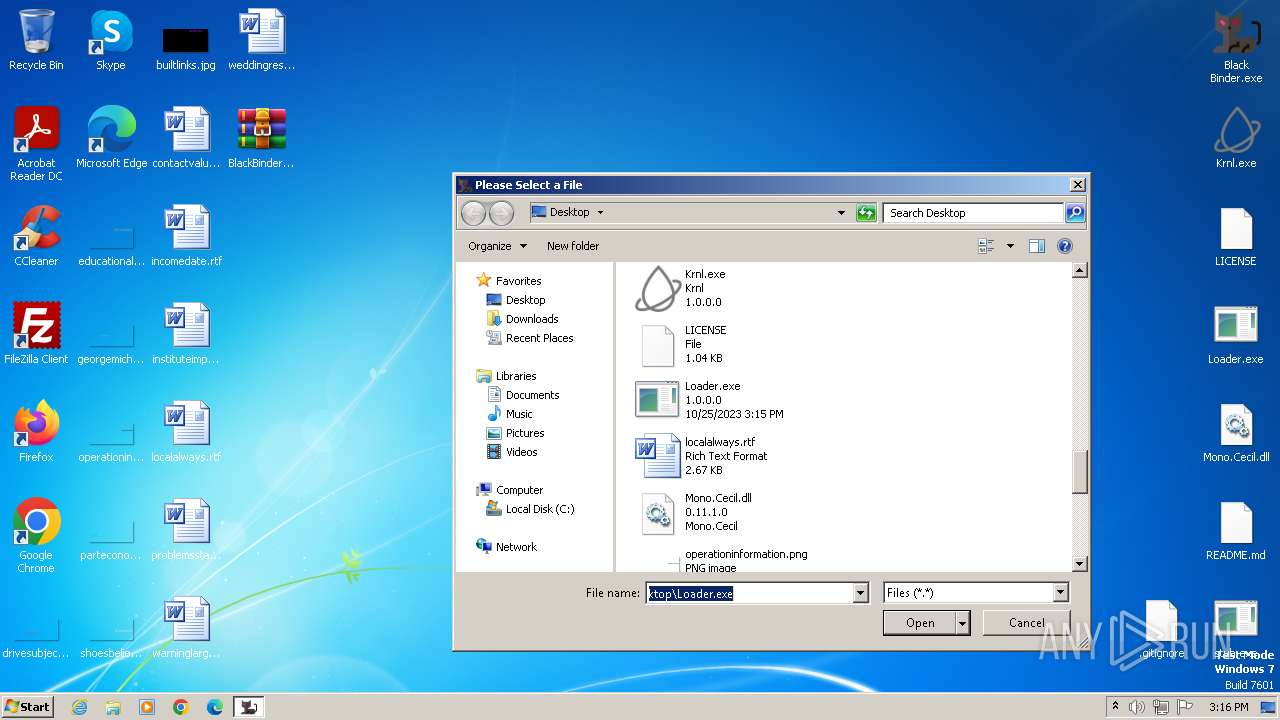
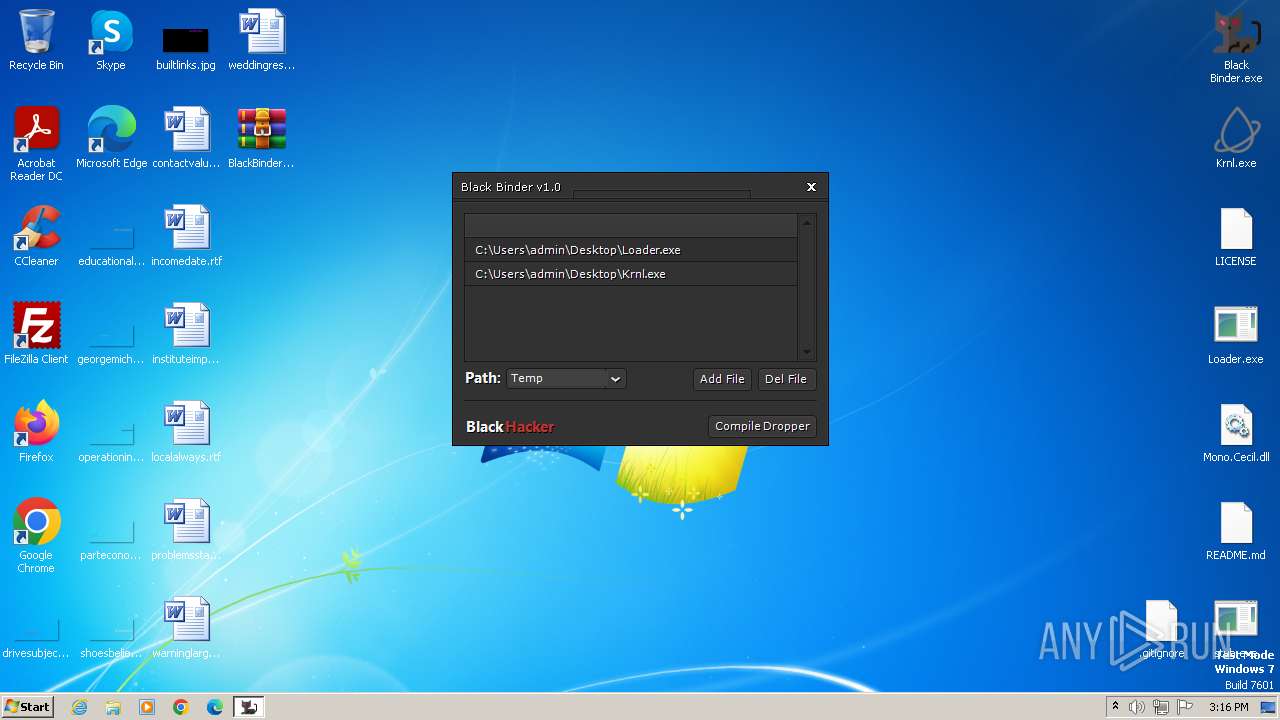
| File name: | BlackBinder.rar |
| Full analysis: | https://app.any.run/tasks/86dca439-68cc-4d8f-82f0-41200a51c729 |
| Verdict: | Malicious activity |
| Threats: | XWorm is a remote access trojan (RAT) sold as a malware-as-a-service. It possesses an extensive hacking toolset and is capable of gathering private information and files from the infected computer, hijacking MetaMask and Telegram accounts, and tracking user activity. XWorm is typically delivered to victims' computers through multi-stage attacks that start with phishing emails. |
| Analysis date: | October 25, 2023, 14:15:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 146FF770E5ECC133150F729E5E5A4FC3 |
| SHA1: | F831F1A200DB95920D81C1D5DEEABC85F9E1579E |
| SHA256: | 0E24F077983A481266C3F040D8055926E6F690B342D533677E47549C8BF9DC1E |
| SSDEEP: | 49152:kcm/mRiH4pRYYvsX5l/QQsB3cT43ldxqVlksTzWAVY1bi8GztaIxEVn95qBFR8Gp:D5RiH3YvspSQsP3ldoXOAabi8TQsne0c |
MALICIOUS
Application was dropped or rewritten from another process
- Black Binder.exe (PID: 3756)
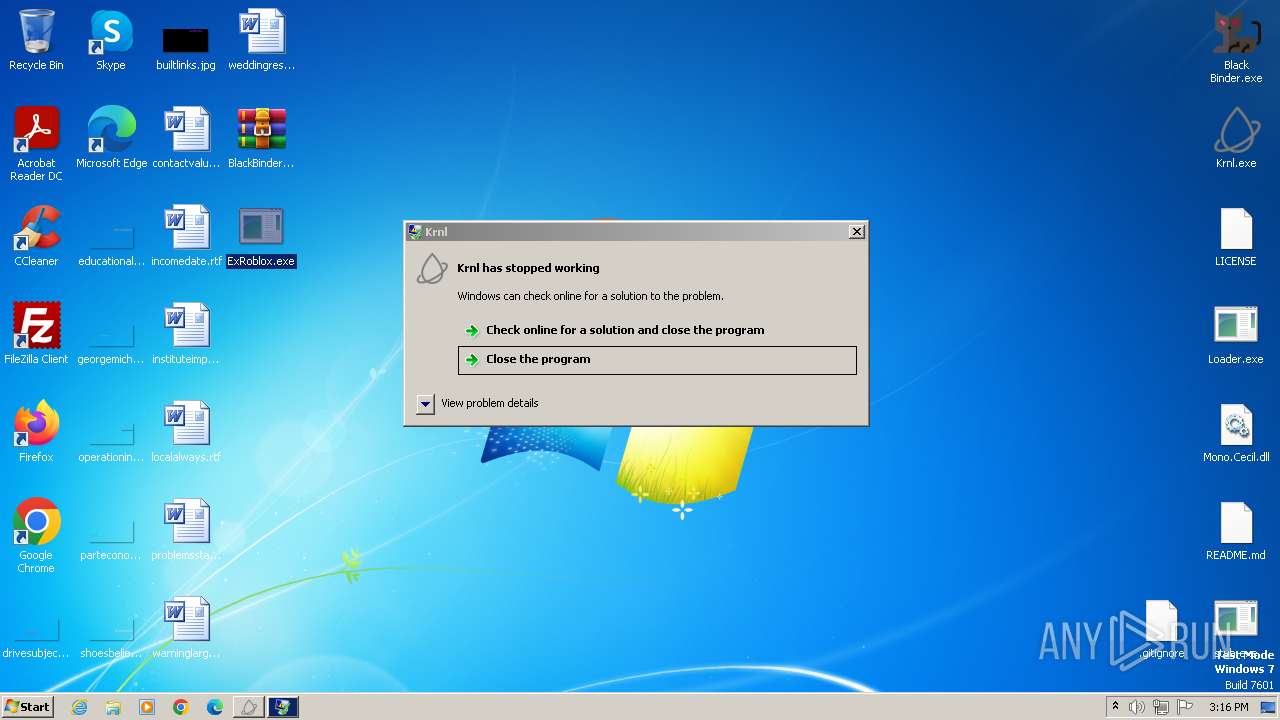
- ExRoblox.exe (PID: 3056)
- Krnl.exe (PID: 3568)
- Loader.exe (PID: 2552)
- Loader.exe (PID: 2040)
Drops the executable file immediately after the start
- Black Binder.exe (PID: 3756)
- ExRoblox.exe (PID: 3056)
Loads dropped or rewritten executable
- Black Binder.exe (PID: 3756)
XWORM has been detected (YARA)
- Loader.exe (PID: 2040)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3852)
- explorer.exe (PID: 1400)
- Black Binder.exe (PID: 3756)
Reads the Internet Settings
- Krnl.exe (PID: 3568)
- Loader.exe (PID: 2552)
- Loader.exe (PID: 2040)
- ExRoblox.exe (PID: 3056)
- Black Binder.exe (PID: 3756)
Checks for external IP
- Loader.exe (PID: 2552)
- Loader.exe (PID: 2040)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3852)
- explorer.exe (PID: 1400)
Reads the Internet Settings
- explorer.exe (PID: 1400)
Manual execution by a user
- Black Binder.exe (PID: 3756)
- Loader.exe (PID: 2040)
- ExRoblox.exe (PID: 3056)
Checks supported languages
- Black Binder.exe (PID: 3756)
- Krnl.exe (PID: 3568)
- Loader.exe (PID: 2552)
- Loader.exe (PID: 2040)
- ExRoblox.exe (PID: 3056)
Reads the computer name
- Black Binder.exe (PID: 3756)
- ExRoblox.exe (PID: 3056)
- Loader.exe (PID: 2552)
- Krnl.exe (PID: 3568)
- Loader.exe (PID: 2040)
Reads the machine GUID from the registry
- Black Binder.exe (PID: 3756)
- Loader.exe (PID: 2552)
- Krnl.exe (PID: 3568)
- ExRoblox.exe (PID: 3056)
- Loader.exe (PID: 2040)
Create files in a temporary directory
- ExRoblox.exe (PID: 3056)
Reads Environment values
- Loader.exe (PID: 2552)
- Loader.exe (PID: 2040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(2040) Loader.exe
C2swezy.ddns.net:5555
Keys
AES!#Swezy--:CX/Slave*s/.c-YX%&
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameUSB Driver.exe
Mutexc5PuxEH0SRKALzzl
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
54
Monitored processes
10
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 1400 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\Desktop\Loader.exe" | C:\Users\admin\Desktop\Loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 2148734499 Version: 1.0.0.0 Modules
XWorm(PID) Process(2040) Loader.exe C2swezy.ddns.net:5555 Keys AES!#Swezy--:CX/Slave*s/.c-YX%& Options Splitter<Xwormmm> Sleep time3 USB drop nameUSB Driver.exe Mutexc5PuxEH0SRKALzzl | |||||||||||||||
| 2552 | "C:\Users\admin\AppData\Local\Temp\Loader.exe" | C:\Users\admin\AppData\Local\Temp\Loader.exe | ExRoblox.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 2148734499 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2760 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\System32\wisptis.exe | — | Krnl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3024 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\System32\wisptis.exe | — | Krnl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3056 | "C:\Users\admin\Desktop\ExRoblox.exe" | C:\Users\admin\Desktop\ExRoblox.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Update Assistant Exit code: 0 Version: 10.0.18362.1 Modules
| |||||||||||||||
| 3568 | "C:\Users\admin\AppData\Local\Temp\Krnl.exe" | C:\Users\admin\AppData\Local\Temp\Krnl.exe | ExRoblox.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Krnl Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3756 | "C:\Users\admin\Desktop\Black Binder.exe" | C:\Users\admin\Desktop\Black Binder.exe | — | explorer.exe | |||||||||||
User: admin Company: DarkSoftwareCo - Black.Hacker Integrity Level: MEDIUM Description: Black Binder Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3852 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\BlackBinder.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
8 778
Read events
8 614
Write events
154
Delete events
10
Modification events
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1400) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs |
| Operation: | write | Name: | MRUListEx |
Value: 020000001E0000001D0000001C0000001B0000001A000000000000001900000003000000180000001600000017000000150000001400000013000000120000000F00000011000000100000000E0000000D0000000C0000000B0000000A00000009000000080000000700000006000000050000000400000001000000FFFFFFFF | |||
| (PID) Process: | (1400) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000F6D6788197A75D498472ACE88906AC8D0000000002000000000010660000000100002000000048832D3FD0459F35F292D4F0571B992C6EB9F500D4ED7BC3B99927FC5331D217000000000E80000000020000200000003EFBFF3AEC091353AF9E58D48DF2D06E9D1BDED94E4937159293C20E513DDF0F3000000087034FE3522EDDAC6E83C331CAE7E3CB92B187260C4DAD8D1C31F9039AB30BE9E56E6C6EE2A54DD7C0FCB3257D6FF55F4000000040B806FFF8B32ABD66EABA7F35A86503B0F300E1B9A976FC4B3F6328F133A31ACB461ADFC86BE84974CB3AD9119C225504F24589D1CDC1655DA54BABE9CEF265 | |||
Executable files
13
Suspicious files
3
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3852.33406\Black Binder.exe | executable | |
MD5:4D7E55F77003562C0A8080AD90A79BA1 | SHA256:345AED87AAA0E1D81963292F063C366366B6CF6A514D3D4F80FECAAAE09B5990 | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3852.33406\.gitignore | text | |
MD5:F626BDF2AC91B3951D8438B3E3872353 | SHA256:9842F442B12E86B03ACD67CD83923F4FFA95FB72F546B6C13EF2269D770F57E7 | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3852.33406\Mono.Cecil.dll | executable | |
MD5:CB79DD472AE13EF082326ECC0C7891C5 | SHA256:5B39CAF5C7E489336A1C9585CFA89ADFA12682887B799CC3E21E10CE9484E57D | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3852.33406\stub.exe | executable | |
MD5:E315DE9918567F55E083CD3965F6B64B | SHA256:FA6D3E9933444F46A82325FD0E470101F1297879E9656BF64B5406EEB7584E77 | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3852.33406\LICENSE | text | |
MD5:9552AAF077A44CDAD5382D31601FE7B4 | SHA256:EB1F071507EBC686B0A7723590C731670F2817B722238FCED63C0CC24020FCB9 | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3852.33406\README.md | text | |
MD5:0087C23ABB2DC8BC9C33F148F889345B | SHA256:3045A9CC1219778F76A11CBFD966D4D7479D59ECA2DA4AABA7D1FF3629742E6B | |||
| 1400 | explorer.exe | C:\Users\admin\Desktop\.gitignore | text | |
MD5:F626BDF2AC91B3951D8438B3E3872353 | SHA256:9842F442B12E86B03ACD67CD83923F4FFA95FB72F546B6C13EF2269D770F57E7 | |||
| 1400 | explorer.exe | C:\Users\admin\Desktop\LICENSE | text | |
MD5:9552AAF077A44CDAD5382D31601FE7B4 | SHA256:EB1F071507EBC686B0A7723590C731670F2817B722238FCED63C0CC24020FCB9 | |||
| 1400 | explorer.exe | C:\Users\admin\Desktop\Loader.exe | executable | |
MD5:F6B303FDE168E6EC5DB1BCFB3493C0DD | SHA256:B849A7C7B17B978A2B1AE1F704F41CA3FEC114E15B7C7818FF0F23B53039A9BF | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3852.33406\Loader.exe | executable | |
MD5:F6B303FDE168E6EC5DB1BCFB3493C0DD | SHA256:B849A7C7B17B978A2B1AE1F704F41CA3FEC114E15B7C7818FF0F23B53039A9BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
2
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2552 | Loader.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | text | 5 b | unknown |
2040 | Loader.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | text | 5 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2552 | Loader.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
2040 | Loader.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
2040 | Loader.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2040 | Loader.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
2040 | Loader.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
Process | Message |
|---|---|
Loader.exe | CLR: Managed code called FailFast without specifying a reason.
|
Loader.exe | CLR: Managed code called FailFast without specifying a reason.
|