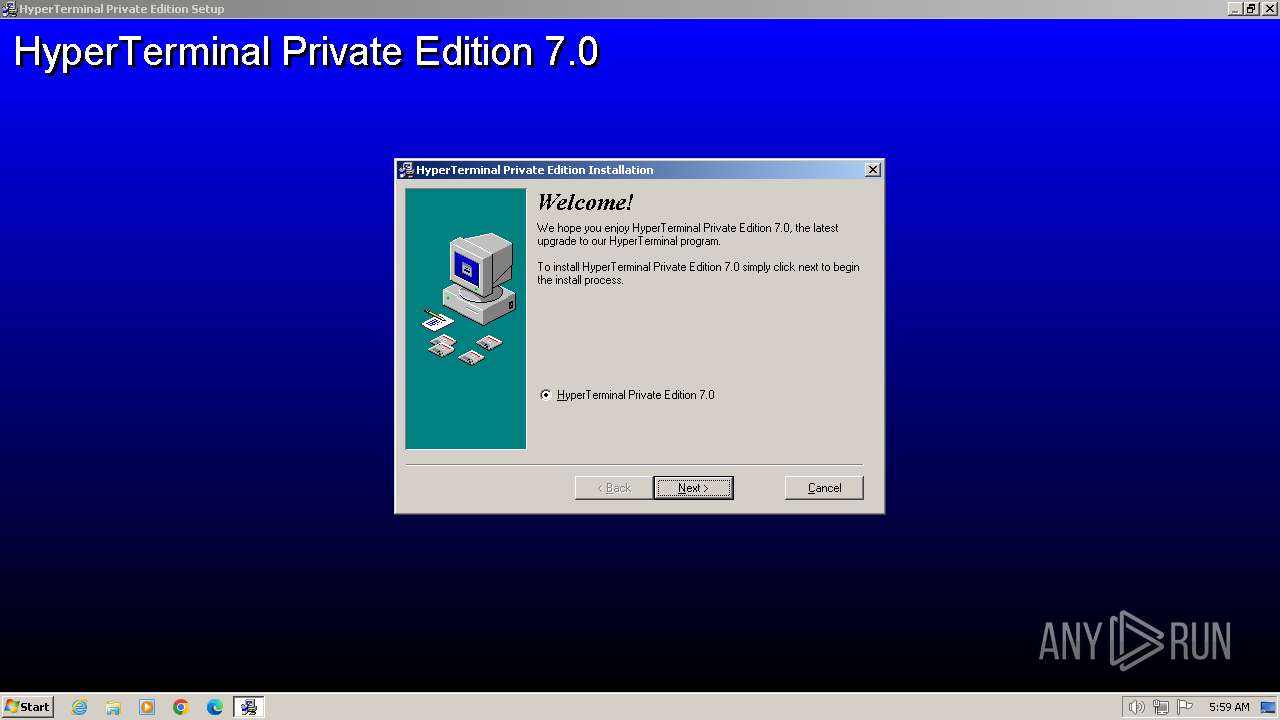
| File name: | htpe7.exe |
| Full analysis: | https://app.any.run/tasks/b71f0c6d-85b7-4df7-b85f-e725b598f37a |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2024, 04:59:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 29A0694490619235ADE01FFC130865FF |
| SHA1: | FC0C4AD65E13694F9AF4CA8A800EE1931DFC83AC |
| SHA256: | 0E1B2ED27B426A09A35E60E8D79413C6FEE4E98646FEFCA8F7AA319A2A493180 |
| SSDEEP: | 98304:VVm1Q9leql9qEPG6cq0U4NSjCmJfh71NOkY3LVtliPUNWoTHZ9mSmadGoGy9woo2:LmwpesJaOOZiJd89 |
MALICIOUS
Drops the executable file immediately after the start
- htpe7.exe (PID: 3708)
- vcredist_x86.exe (PID: 1476)
- msiexec.exe (PID: 1324)
Creates a writable file in the system directory
- htpe7.exe (PID: 3708)
SUSPICIOUS
Executable content was dropped or overwritten
- htpe7.exe (PID: 3708)
- vcredist_x86.exe (PID: 1476)
Executes as Windows Service
- VSSVC.exe (PID: 3100)
Searches for installed software
- htpe7.exe (PID: 3708)
- dllhost.exe (PID: 3484)
Process drops legitimate windows executable
- htpe7.exe (PID: 3708)
- vcredist_x86.exe (PID: 1476)
- msiexec.exe (PID: 1324)
Reads security settings of Internet Explorer
- htpe7.exe (PID: 3708)
Reads the Internet Settings
- htpe7.exe (PID: 3708)
Checks Windows Trust Settings
- msiexec.exe (PID: 1324)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1324)
The process drops C-runtime libraries
- msiexec.exe (PID: 1324)
Creates file in the systems drive root
- msiexec.exe (PID: 1324)
Uses ICACLS.EXE to modify access control lists
- htpe7.exe (PID: 3708)
Creates a software uninstall entry
- htpe7.exe (PID: 3708)
Creates/Modifies COM task schedule object
- htpe7.exe (PID: 3708)
INFO
Create files in a temporary directory
- htpe7.exe (PID: 3708)
- msiexec.exe (PID: 1324)
- install.exe (PID: 2544)
Reads the computer name
- htpe7.exe (PID: 3708)
- vcredist_x86.exe (PID: 1476)
- install.exe (PID: 2544)
- msiexec.exe (PID: 1324)
- HyperTrm.exe (PID: 2064)
Checks supported languages
- htpe7.exe (PID: 3708)
- vcredist_x86.exe (PID: 1476)
- msiexec.exe (PID: 1324)
- install.exe (PID: 2544)
- HyperTrm.exe (PID: 2064)
- HyperTrm.exe (PID: 1524)
Reads the machine GUID from the registry
- htpe7.exe (PID: 3708)
- vcredist_x86.exe (PID: 1476)
- msiexec.exe (PID: 1324)
- install.exe (PID: 2544)
- HyperTrm.exe (PID: 1524)
- HyperTrm.exe (PID: 2064)
Creates files in the program directory
- htpe7.exe (PID: 3708)
- HyperTrm.exe (PID: 1524)
Reads Environment values
- vcredist_x86.exe (PID: 1476)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1324)
Reads the software policy settings
- msiexec.exe (PID: 1324)
Manual execution by a user
- HyperTrm.exe (PID: 2064)
Disables trace logs
- HyperTrm.exe (PID: 2064)
Creates a software uninstall entry
- msiexec.exe (PID: 1324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Wise Installer executable (91.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (5.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2001:08:13 17:13:38+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, Removable run from swap |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 8704 |
| InitializedDataSize: | 5632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21af |
| OSVersion: | 4 |
| ImageVersion: | 4 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.0.0.0 |
| ProductVersionNumber: | 7.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Hilgraeve, Inc. |
| FileDescription: | HyperTerminal Private Edition |
| FileVersion: | 7 |
| LegalCopyright: | Copyright © 2001 Hilgraeve Inc. |
Total processes
58
Monitored processes
11
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1144 | "C:\Windows\System32\cacls.exe" "C:\Program Files\HyperTerminal" /E /G Users:F | C:\Windows\System32\cacls.exe | — | htpe7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1324 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1476 | "C:\PROGRA~1\HYPERT~1\VCREDI~1.EXE" /q:a | C:\Program Files\HyperTerminal\vcredist_x86.exe | htpe7.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2008 Redistributable Setup Exit code: 0 Version: 9.0.21022.08 Modules
| |||||||||||||||
| 1524 | "C:\PROGRA~1\HYPERT~1\HyperTrm.exe" -initializeTrial | C:\Program Files\HyperTerminal\HyperTrm.exe | — | htpe7.exe | |||||||||||
User: admin Company: Hilgraeve, Inc. Integrity Level: HIGH Description: HyperTerminal Applet Exit code: 0 Version: 7.03 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\HyperTerminal\HyperTrm.exe" | C:\Program Files\HyperTerminal\HyperTrm.exe | — | explorer.exe | |||||||||||
User: admin Company: Hilgraeve, Inc. Integrity Level: MEDIUM Description: HyperTerminal Applet Version: 7.03 Modules
| |||||||||||||||
| 2544 | c:\ae5def1464470c7d237436feebdf7c\.\install.exe /q:a | C:\ae5def1464470c7d237436feebdf7c\install.exe | — | vcredist_x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: External Installer Exit code: 0 Version: 9.0.21022.8 built by: RTM Modules
| |||||||||||||||
| 2692 | "C:\Windows\System32\cacls.exe" hg_dbh.lic /E /G Users:W | C:\Windows\System32\cacls.exe | — | htpe7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3100 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3392 | "C:\Users\admin\AppData\Local\Temp\htpe7.exe" | C:\Users\admin\AppData\Local\Temp\htpe7.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3484 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
10 710
Read events
10 304
Write events
394
Delete events
12
Modification events
| (PID) Process: | (3708) htpe7.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000C200EEBF4EC8DA017C0E0000840C0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) htpe7.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000C200EEBF4EC8DA017C0E0000840C0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) htpe7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (3708) htpe7.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000D495A5C04EC8DA017C0E0000840C0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3708) htpe7.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D495A5C04EC8DA017C0E0000580C0000E803000001000000000000000000000066EF61B9348D3440AF7C12AC64267B680000000000000000 | |||
| (PID) Process: | (3100) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000003C1FAFC04EC8DA011C0C00002C080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3100) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000003C1FAFC04EC8DA011C0C0000240B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3100) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000003C1FAFC04EC8DA011C0C0000800B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3100) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000003C1FAFC04EC8DA011C0C0000140A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3100) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000009681B1C04EC8DA011C0C00002C080000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
62
Suspicious files
39
Text files
45
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3484 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3484 | dllhost.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:86B27C54EAF449D0248125B99EC3812E | SHA256:5F36245AC7187EF0754EA46E60544639463706ADA5D516C0963A192B4784091F | |||
| 1476 | vcredist_x86.exe | C:\ae5def1464470c7d237436feebdf7c\install.res.1042.dll | executable | |
MD5:0D4FB4095EA49C1EC89B9E8DB0B936A3 | SHA256:7D86F3BA0232C2AC4B4FCE96E4CEBB23700312A032D5D0DB988EC6B358BE1686 | |||
| 3708 | htpe7.exe | C:\Users\admin\AppData\Local\Temp\GLME472.tmp | executable | |
MD5:A8108D3E40849B61FDDFACF36E520395 | SHA256:84C6507FE457D6A882F643908423A3E42EE1170218D18C53366AE6FBD627FF36 | |||
| 3708 | htpe7.exe | C:\Users\admin\AppData\Local\Temp\~GLH0000.TMP | executable | |
MD5:9DA8F742593D4BBCA708B90725282AE2 | SHA256:E362A9815527869E0F71FDF766A1C3648E307145DEFDA7A5279914E522BCB57C | |||
| 3708 | htpe7.exe | C:\Program Files\HyperTerminal\~GLH0001.TMP | executable | |
MD5:B936F0F378B9A35489353E878154E899 | SHA256:C6A7E484F4D84883BC1205BCCEA3114C0521025712922298EDE9B2A1CD632357 | |||
| 1476 | vcredist_x86.exe | C:\ae5def1464470c7d237436feebdf7c\vc_red.msi | executable | |
MD5:E0951D3CB1038EB2D2B2B2F336E1AB32 | SHA256:507AC60E145057764F13CF1AD5366A7E15DDC0DA5CC22216F69E3482697D5E88 | |||
| 1476 | vcredist_x86.exe | C:\ae5def1464470c7d237436feebdf7c\vc_red.cab | compressed | |
MD5:E10F2F6E6379E9185F71AEC1421F37B4 | SHA256:9681BCFD73C610EB6A9538D872C1E7844548FCA341F22FB66CCADB4D78530B4D | |||
| 1476 | vcredist_x86.exe | C:\ae5def1464470c7d237436feebdf7c\install.exe | executable | |
MD5:520A6D1CBCC9CF642C625FE814C93C58 | SHA256:08966CE743AA1CBED0874933E104EF7B913188ECD8F0C679F7D8378516C51DA2 | |||
| 1476 | vcredist_x86.exe | C:\ae5def1464470c7d237436feebdf7c\install.res.1040.dll | executable | |
MD5:6310AB8FC9E3DBEE80592FC453A34FEE | SHA256:7774F2436C96A70B0CDC8176883EE7A4614353F17AD61BFBD5A8D7A1906483D3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 2.16.100.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 2.19.126.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f69642324cc87bd | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 52.140.118.28:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IN | unknown |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 2.16.100.168:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
1372 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
1060 | svchost.exe | 2.19.126.163:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |