| download: | /hanks445/CVE-2024-38063/raw/main/CVE-2024-38143%20poc.exe |
| Full analysis: | https://app.any.run/tasks/8e54cdeb-935a-4260-a571-dc137a218f70 |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2024, 12:15:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0C5A47D387A5EC1BDB9B4BCBEF89DC79 |
| SHA1: | FD9117FA7B4A12875655AE574FF207FA1A0E3AA8 |
| SHA256: | 0DFA551E2B12AF0991714A3E5BE26C9A4C00F7663F065DBF4D8B84C9ABC7B97A |
| SSDEEP: | 98304:2rqpPiR0LJI03XMAEbV6ggvpot5hOKZhlmi3WYll6+rS3bqij5ELAdEYDMaQ9+S0:DS6dtYOGG |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 7060)
- dllhost.exe (PID: 2572)
Creates or modifies Windows services
- winver.exe (PID: 2044)
SUSPICIOUS
Executable content was dropped or overwritten
- 8e54cdeb-935a-4260-a571-dc137a218f70.exe (PID: 6260)
- BNZY1O1PB.exe (PID: 1128)
- 3dsystem.exe (PID: 6940)
- winver.exe (PID: 2044)
Executes application which crashes
- 8e54cdeb-935a-4260-a571-dc137a218f70.exe (PID: 6260)
Creates file in the systems drive root
- explorer.exe (PID: 6796)
Drops the executable file immediately after the start
- 8e54cdeb-935a-4260-a571-dc137a218f70.exe (PID: 6260)
- BNZY1O1PB.exe (PID: 1128)
- 3dsystem.exe (PID: 6940)
The process creates files with name similar to system file names
- BNZY1O1PB.exe (PID: 1128)
Executes as Windows Service
- DirectX.exe (PID: 1356)
- DirectX.exe (PID: 3700)
Connects to unusual port
- iexplore.exe (PID: 5112)
- 3dsystem.exe (PID: 6940)
- winver.exe (PID: 2044)
- BNZY1O1PB.exe (PID: 1248)
- iexplore.exe (PID: 6592)
- BNZY1O1PB.exe (PID: 1128)
Likely accesses (executes) a file from the Public directory
- notepad.exe (PID: 7076)
INFO
Checks supported languages
- 8e54cdeb-935a-4260-a571-dc137a218f70.exe (PID: 6260)
- BNZY1O1PB.exe (PID: 1128)
- DirectX.exe (PID: 6912)
- 3dsystem.exe (PID: 6940)
- DirectX.exe (PID: 1356)
- iexplore.exe (PID: 5112)
- 3dsystem.exe (PID: 6156)
- DirectX.exe (PID: 3700)
- DirectX.exe (PID: 5796)
- iexplore.exe (PID: 6592)
- TextInputHost.exe (PID: 6912)
- BNZY1O1PB.exe (PID: 1248)
Reads the computer name
- BNZY1O1PB.exe (PID: 1128)
- 8e54cdeb-935a-4260-a571-dc137a218f70.exe (PID: 6260)
- 3dsystem.exe (PID: 6940)
- DirectX.exe (PID: 1356)
- iexplore.exe (PID: 5112)
- DirectX.exe (PID: 6912)
- BNZY1O1PB.exe (PID: 1248)
- 3dsystem.exe (PID: 6156)
- DirectX.exe (PID: 3700)
- DirectX.exe (PID: 5796)
- iexplore.exe (PID: 6592)
- TextInputHost.exe (PID: 6912)
Reads security settings of Internet Explorer
- explorer.exe (PID: 6796)
- dllhost.exe (PID: 7060)
- winver.exe (PID: 2044)
- dllhost.exe (PID: 2572)
Creates files in the program directory
- 3dsystem.exe (PID: 6940)
- winver.exe (PID: 2044)
Reads the machine GUID from the registry
- BNZY1O1PB.exe (PID: 1128)
- 3dsystem.exe (PID: 6940)
- 3dsystem.exe (PID: 6156)
- BNZY1O1PB.exe (PID: 1248)
Checks proxy server information
- WerFault.exe (PID: 7048)
Reads the software policy settings
- WerFault.exe (PID: 7048)
Creates files or folders in the user directory
- WerFault.exe (PID: 7048)
Manual execution by a user
- notepad.exe (PID: 7076)
- BNZY1O1PB.exe (PID: 1248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:11:11 03:37:53+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 2303488 |
| InitializedDataSize: | 705536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x152ea3 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.1.1031 |
| ProductVersionNumber: | 2.0.1.1031 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | 360.cn |
| FileDescription: | 看图 |
| FileVersion: | 2.0.1.1031 |
| InternalName: | 360AblumViewer |
| LegalCopyright: | (C) 360.cn Inc., All Rights Reserved. |
| OriginalFileName: | 360AblumViewer.exe |
| ProductName: | 看图 |
| ProductVersion: | 2.0.1.1031 |
Total processes
146
Monitored processes
21
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
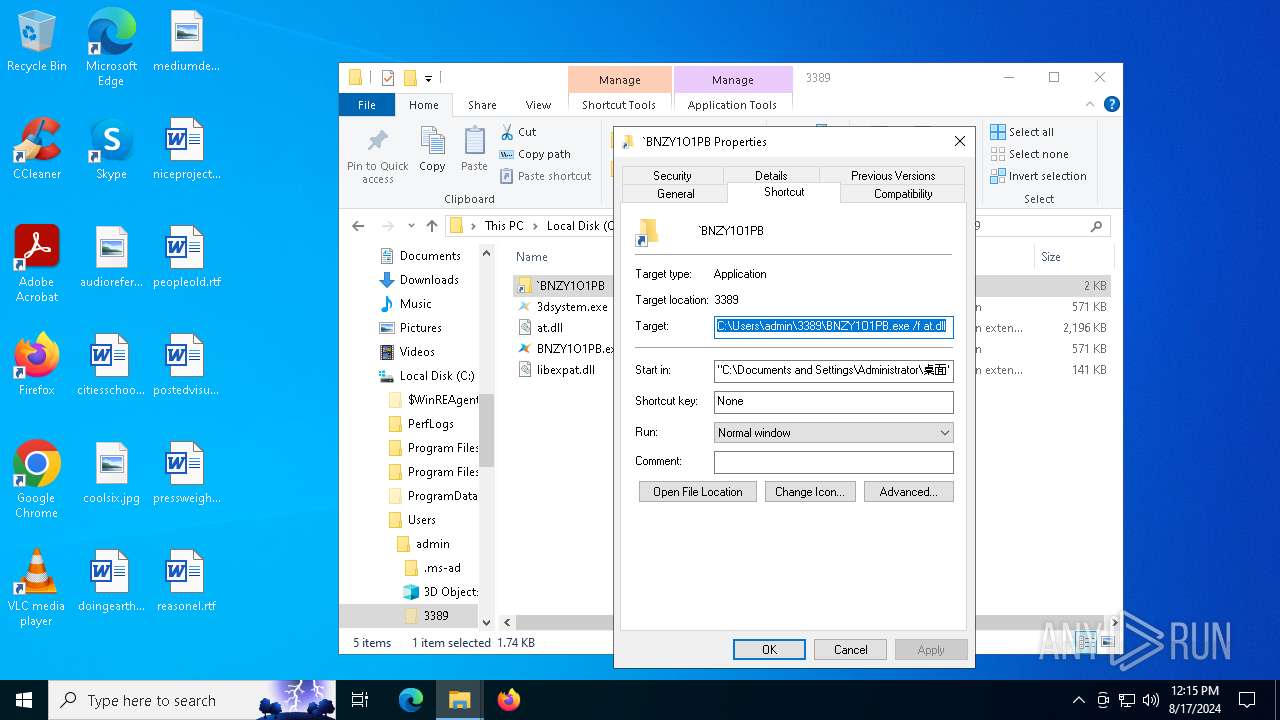
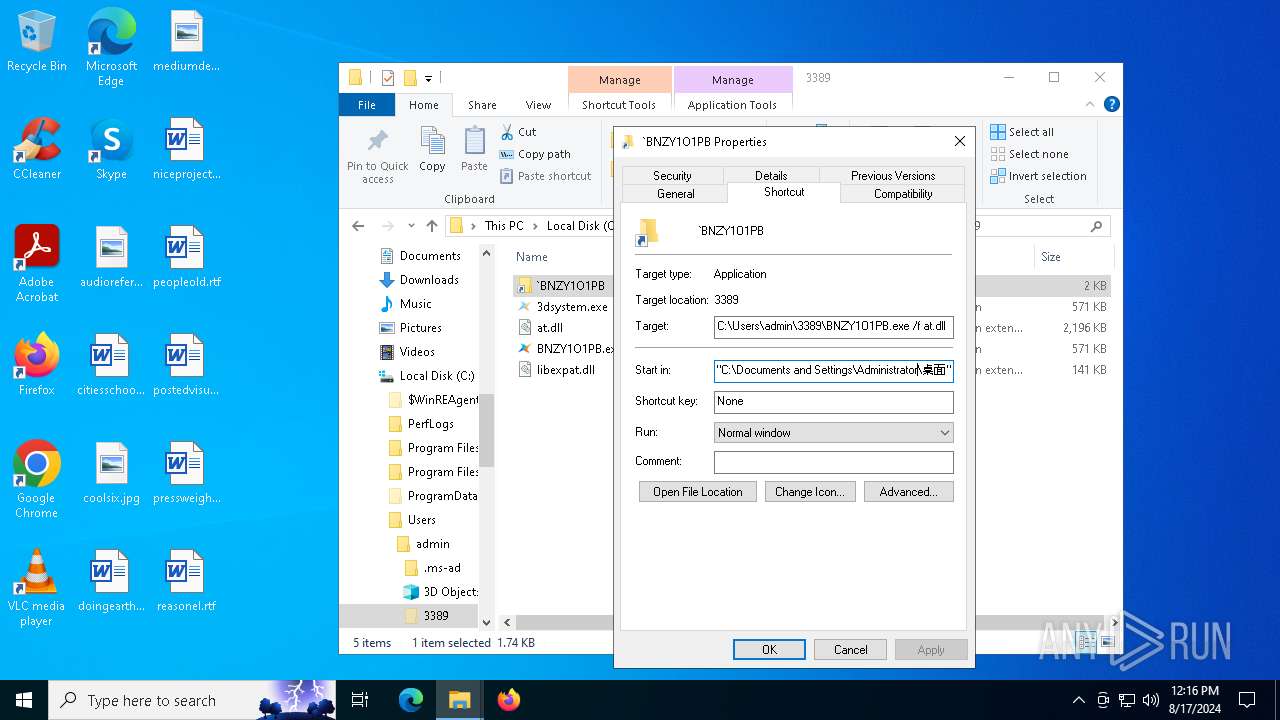
| 1128 | "C:\Users\admin\3389\BNZY1O1PB.exe" /f at.dll | C:\Users\admin\3389\BNZY1O1PB.exe | explorer.exe | ||||||||||||
User: admin Company: 深圳市迅雷网络技术有限公司 Integrity Level: MEDIUM Description: 迅雷游戏 Exit code: 0 Version: 1.0.0.32 Modules
| |||||||||||||||
| 1248 | "C:\Users\admin\3389\BNZY1O1PB.exe" /f at.dll | C:\Users\admin\3389\BNZY1O1PB.exe | explorer.exe | ||||||||||||
User: admin Company: 深圳市迅雷网络技术有限公司 Integrity Level: MEDIUM Description: 迅雷游戏 Exit code: 0 Version: 1.0.0.32 Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Thunder\DirectX.exe" /f at.dll | C:\Program Files\Thunder\DirectX.exe | — | services.exe | |||||||||||
User: SYSTEM Company: 深圳市迅雷网络技术有限公司 Integrity Level: SYSTEM Description: 迅雷游戏 Exit code: 0 Version: 1.0.0.32 Modules
| |||||||||||||||
| 2044 | /f at.dll | C:\Windows\SysWOW64\winver.exe | iexplore.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Version Reporter Applet Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2572 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3700 | "C:\Program Files\Thunder\DirectX.exe" /f at.dll | C:\Program Files\Thunder\DirectX.exe | — | services.exe | |||||||||||
User: SYSTEM Company: 深圳市迅雷网络技术有限公司 Integrity Level: SYSTEM Description: 迅雷游戏 Exit code: 0 Version: 1.0.0.32 Modules
| |||||||||||||||
| 5112 | /f at.dll | C:\Program Files (x86)\Internet Explorer\iexplore.exe | DirectX.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5796 | "C:\Program Files\Thunder\DirectX.exe" /f at.dll | C:\Program Files\Thunder\DirectX.exe | — | dllhost.exe | |||||||||||
User: admin Company: 深圳市迅雷网络技术有限公司 Integrity Level: HIGH Description: 迅雷游戏 Exit code: 0 Version: 1.0.0.32 Modules
| |||||||||||||||
| 6156 | "C:\Users\admin\3389\3dsystem.exe" /f at.dll | C:\Users\admin\3389\3dsystem.exe | — | dllhost.exe | |||||||||||
User: admin Company: 深圳市迅雷网络技术有限公司 Integrity Level: HIGH Description: 迅雷游戏 Exit code: 0 Version: 1.0.0.32 Modules
| |||||||||||||||
Total events
33 086
Read events
33 010
Write events
75
Delete events
1
Modification events
| (PID) Process: | (6796) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6796) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E0000000F000000000000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6796) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0400000006000000050000000100000008000000020000000C0000000B0000000A00000009000000070000000000000003000000FFFFFFFF | |||
| (PID) Process: | (6796) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (6796) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | MinimizedStateTabletModeOff |
Value: 0 | |||
| (PID) Process: | (6796) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | QatItems |
Value: 3C7369713A637573746F6D554920786D6C6E733A7369713D22687474703A2F2F736368656D61732E6D6963726F736F66742E636F6D2F77696E646F77732F323030392F726962626F6E2F716174223E3C7369713A726962626F6E206D696E696D697A65643D2266616C7365223E3C7369713A71617420706F736974696F6E3D2230223E3C7369713A736861726564436F6E74726F6C733E3C7369713A636F6E74726F6C206964513D227369713A3136313238222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3136313239222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333532222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333834222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333336222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333537222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C2F7369713A736861726564436F6E74726F6C733E3C2F7369713A7161743E3C2F7369713A726962626F6E3E3C2F7369713A637573746F6D55493E | |||
| (PID) Process: | (6796) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar\ShellBrowser |
| Operation: | write | Name: | ITBar7Layout |
Value: 13000000000000000000000020000000100000000000000001000000010700005E01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6796) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0\4\0 |
| Operation: | write | Name: | 2 |
Value: 4E003100000000001159EB6112003333383900003A0009000400EFBE1159EB611159EB612E000000695D050000000A00000000000000000000000000000043AB74003300330038003900000014000000 | |||
| (PID) Process: | (6796) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0\4\0\2 |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (6796) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0\4\0 |
| Operation: | write | Name: | MRUListEx |
Value: 020000000000000001000000FFFFFFFF | |||
Executable files
8
Suspicious files
9
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7048 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_8e54cdeb-935a-42_59f3ca8bda1e3a3444e2b7ae69807715857e4528_561dae5f_f0d71382-d135-4b38-a982-53f0b9d5c519\Report.wer | — | |
MD5:— | SHA256:— | |||
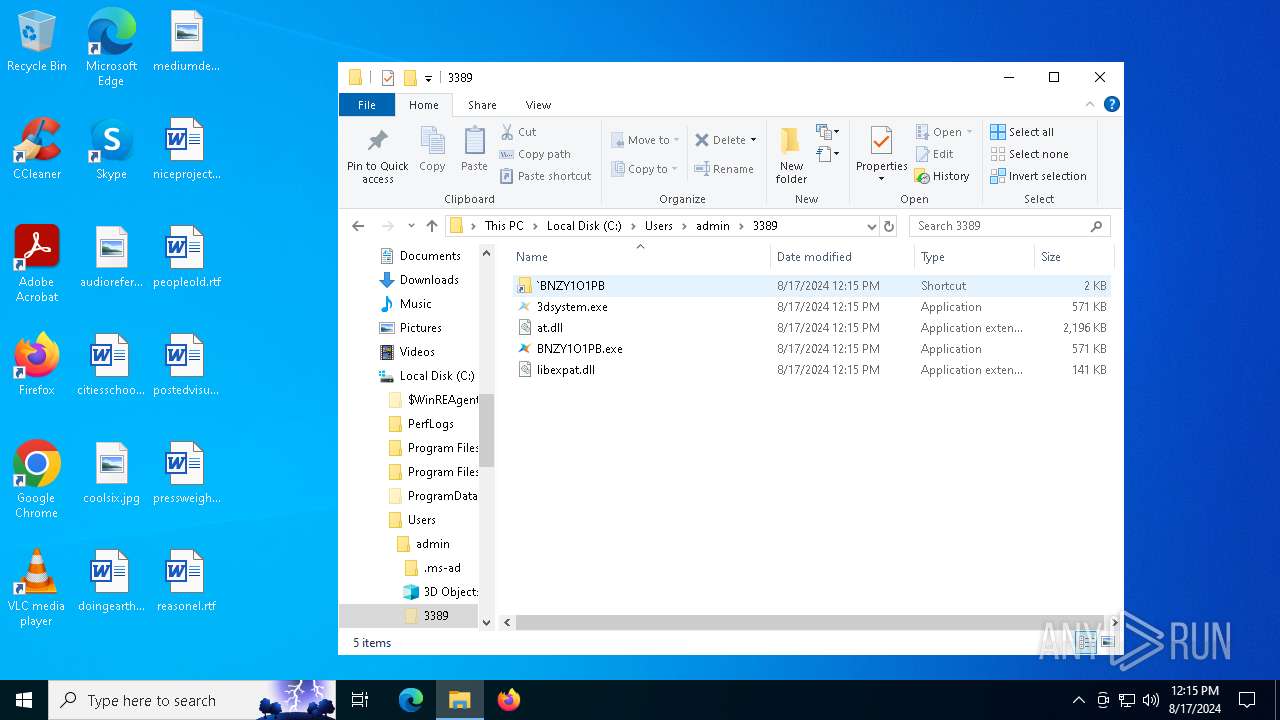
| 6260 | 8e54cdeb-935a-4260-a571-dc137a218f70.exe | C:\Users\admin\3389\at.dll | binary | |
MD5:4D203806F4AE0355B490BA538794A686 | SHA256:5DAF973EB400FC29AE151AEF633DED1097C9F30575DB222879D903A9BE5C1D61 | |||
| 1128 | BNZY1O1PB.exe | C:\Users\admin\3389\3dsystem.exe | executable | |
MD5:BA7BA700C39C576330F18819E075D6BE | SHA256:13675A7BC3274837F9E53C192646180B98B57AC9CDC675FC67C2CF2BF14DF053 | |||
| 6260 | 8e54cdeb-935a-4260-a571-dc137a218f70.exe | C:\Users\admin\3389\`BNZY1O1PB.lnk | lnk | |
MD5:7BAF62423146BC11132FBFC178835889 | SHA256:E6F4C233DC0D83E1CE2C4E133076D94C8B771840FF1FBD450BD7FC888165D182 | |||
| 6940 | 3dsystem.exe | C:\Program Files\Thunder\at.dll | binary | |
MD5:4D203806F4AE0355B490BA538794A686 | SHA256:5DAF973EB400FC29AE151AEF633DED1097C9F30575DB222879D903A9BE5C1D61 | |||
| 6940 | 3dsystem.exe | C:\Program Files\Thunder\DirectX.exe | executable | |
MD5:BA7BA700C39C576330F18819E075D6BE | SHA256:13675A7BC3274837F9E53C192646180B98B57AC9CDC675FC67C2CF2BF14DF053 | |||
| 7048 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER941F.tmp.xml | xml | |
MD5:8F5EAE102C211A97A6406ADFCE55266A | SHA256:6BB92DD6E205BDFF43DDFFFFE7679B25CDAE591CC748B39828A00BE477BED346 | |||
| 7048 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB64A9EBEDF48D3895381D5B7D80743D | SHA256:EA21D495930AD76F267A33A0F593DBF0C7EA75E457FCAE49A29DAAD8BD920F42 | |||
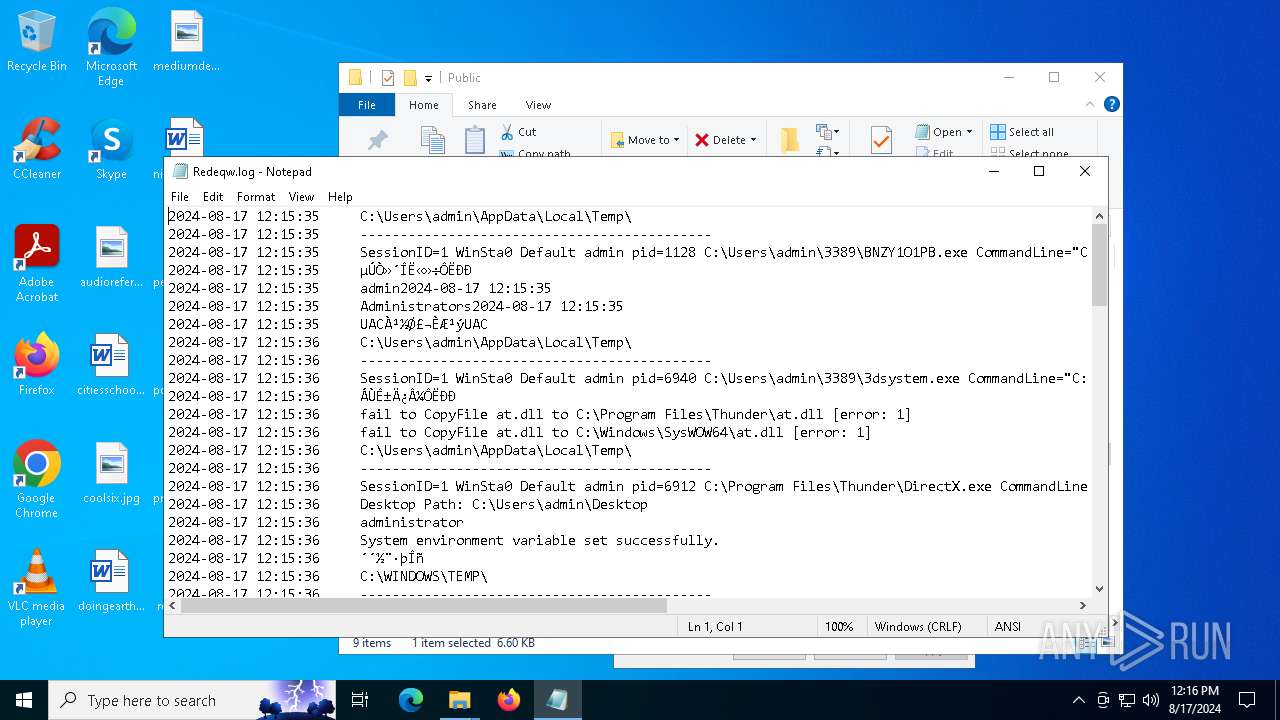
| 1128 | BNZY1O1PB.exe | C:\Users\Public\Redeqw.log | text | |
MD5:44010B589AA75C70A728E82C1D2EE8DB | SHA256:AC05A1CB3EDFD277F999312620231F94FB644EC222CD84218DA17C0D66EAEDA4 | |||
| 7048 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER93F0.tmp.WERInternalMetadata.xml | xml | |
MD5:18BD6475B3AD836C676853276F108519 | SHA256:9A37EC3157111806E639AB39CF7D0E128576E2E135BC51A308E05F3E072D28D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
56
DNS requests
18
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6396 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7052 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6332 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2044 | winver.exe | GET | 200 | 113.31.111.142:80 | http://www.cip.cc/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4016 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6308 | backgroundTaskHost.exe | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | unknown |
6332 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
abc.masktable.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2044 | winver.exe | Generic Protocol Command Decode | SURICATA HTTP Request line incomplete |