| File name: | 0dd9d9638a59b6fbab792b7781962571b653c44ebae3d9b8351937ec71f0af8b.rtf |
| Full analysis: | https://app.any.run/tasks/18c7c7d3-bf6b-4d82-8517-682b680033f6 |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2020, 02:29:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, unknown version |
| MD5: | FEF12D62A3B2FBF1D3BE1F0C71AE393E |
| SHA1: | DE54DEE3FBA472B898CE4BB3304D0DD89D17D34C |
| SHA256: | 0DD9D9638A59B6FBAB792B7781962571B653C44EBAE3D9B8351937EC71F0AF8B |
| SSDEEP: | 6144:IMmXjOiZgF4ax5vC3KkpSHOKlwK5EkNub1S4Vw0:IV+F4ax5q37MeK5bGw4Z |
MALICIOUS
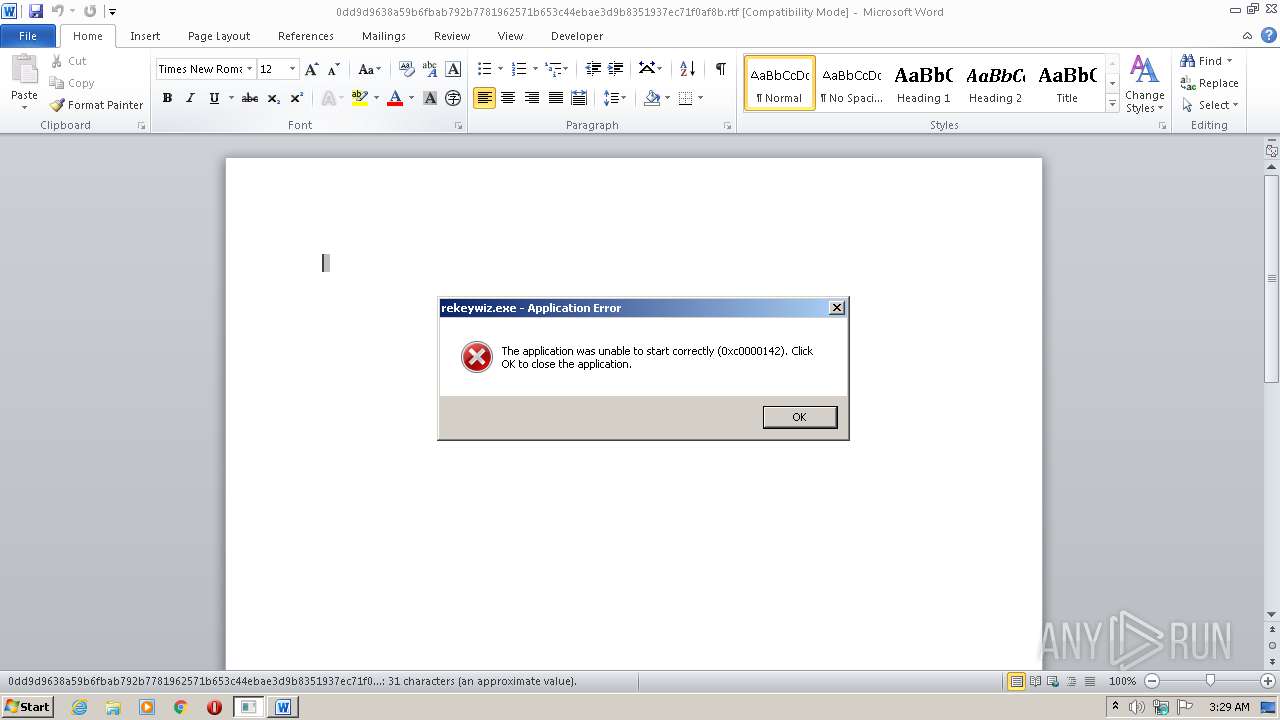
Application was dropped or rewritten from another process
- rekeywiz.exe (PID: 2068)
Changes the autorun value in the registry
- EQNEDT32.EXE (PID: 1340)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 1340)
SUSPICIOUS
Executed via COM
- EQNEDT32.EXE (PID: 1340)
Creates files in the program directory
- EQNEDT32.EXE (PID: 1340)
Reads internet explorer settings
- EQNEDT32.EXE (PID: 1340)
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 1340)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 956)
Creates files in the user directory
- WINWORD.EXE (PID: 956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
36
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\0dd9d9638a59b6fbab792b7781962571b653c44ebae3d9b8351937ec71f0af8b.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1340 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 2068 | "C:\ProgramData\DnsFiles\rekeywiz.exe" | C:\ProgramData\DnsFiles\rekeywiz.exe | — | EQNEDT32.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: EFS REKEY wizard Exit code: 3221225794 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 626
Read events
964
Write events
538
Delete events
124
Modification events
| (PID) Process: | (956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | vx4 |
Value: 76783400BC030000010000000000000000000000 | |||
| (PID) Process: | (956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
1
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA0D6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 956 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1340 | EQNEDT32.EXE | C:\ProgramData\DnsFiles\RaG3Oo.tmp | binary | |
MD5:— | SHA256:— | |||
| 1340 | EQNEDT32.EXE | C:\ProgramData\DnsFiles\Duser.dll | executable | |
MD5:— | SHA256:— | |||
| 956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$d9d9638a59b6fbab792b7781962571b653c44ebae3d9b8351937ec71f0af8b.rtf | pgc | |
MD5:— | SHA256:— | |||
| 956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\1.a | text | |
MD5:— | SHA256:— | |||
| 1340 | EQNEDT32.EXE | C:\ProgramData\DnsFiles\rekeywiz.exe.config | xml | |
MD5:— | SHA256:— | |||
| 1340 | EQNEDT32.EXE | C:\ProgramData\DnsFiles\rekeywiz.exe | executable | |
MD5:082ED4A73761682F897EA1D7F4529F69 | SHA256:FA86B5BC5343CA92C235304B8DCBCF4188C6BE7D4621C625564BEBD5326ED850 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report