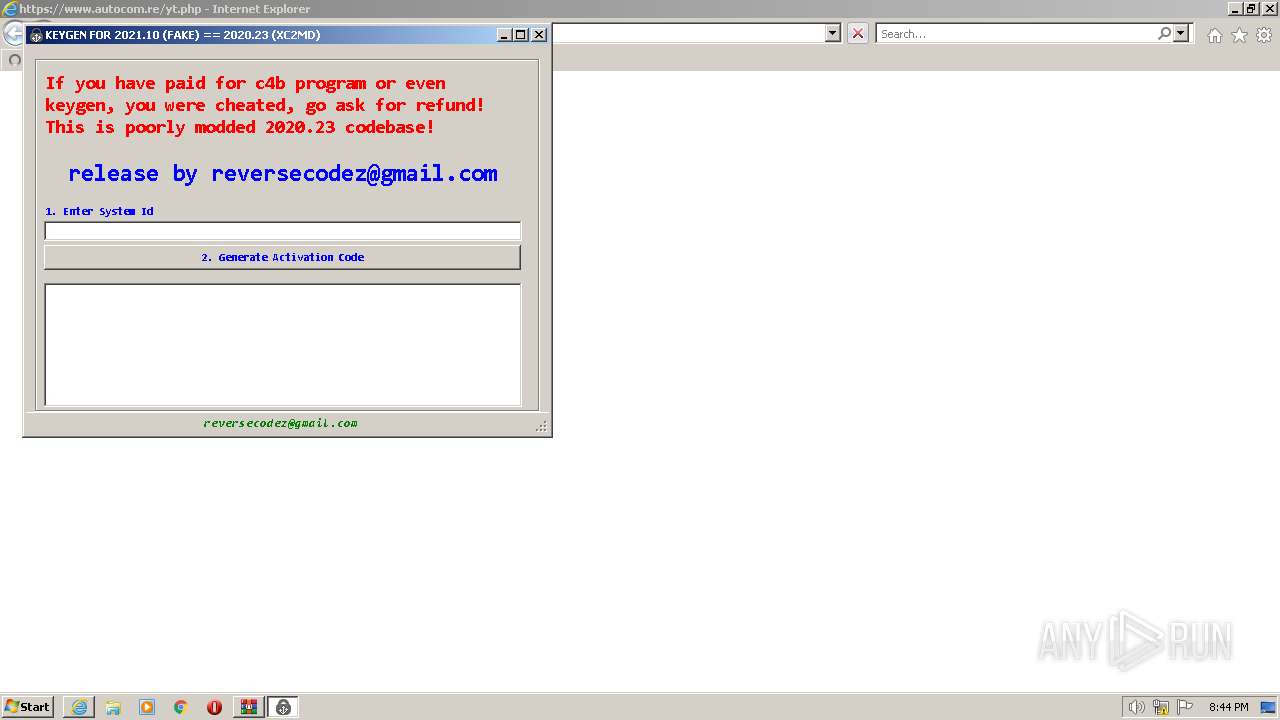
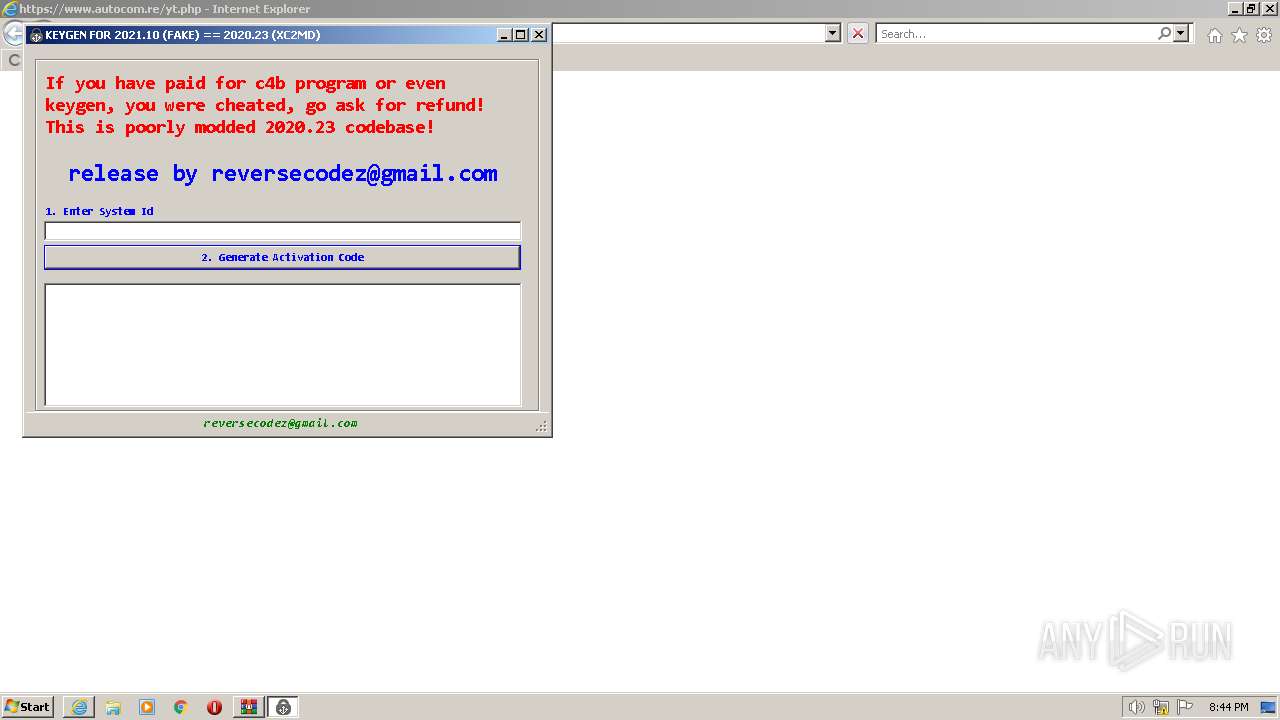
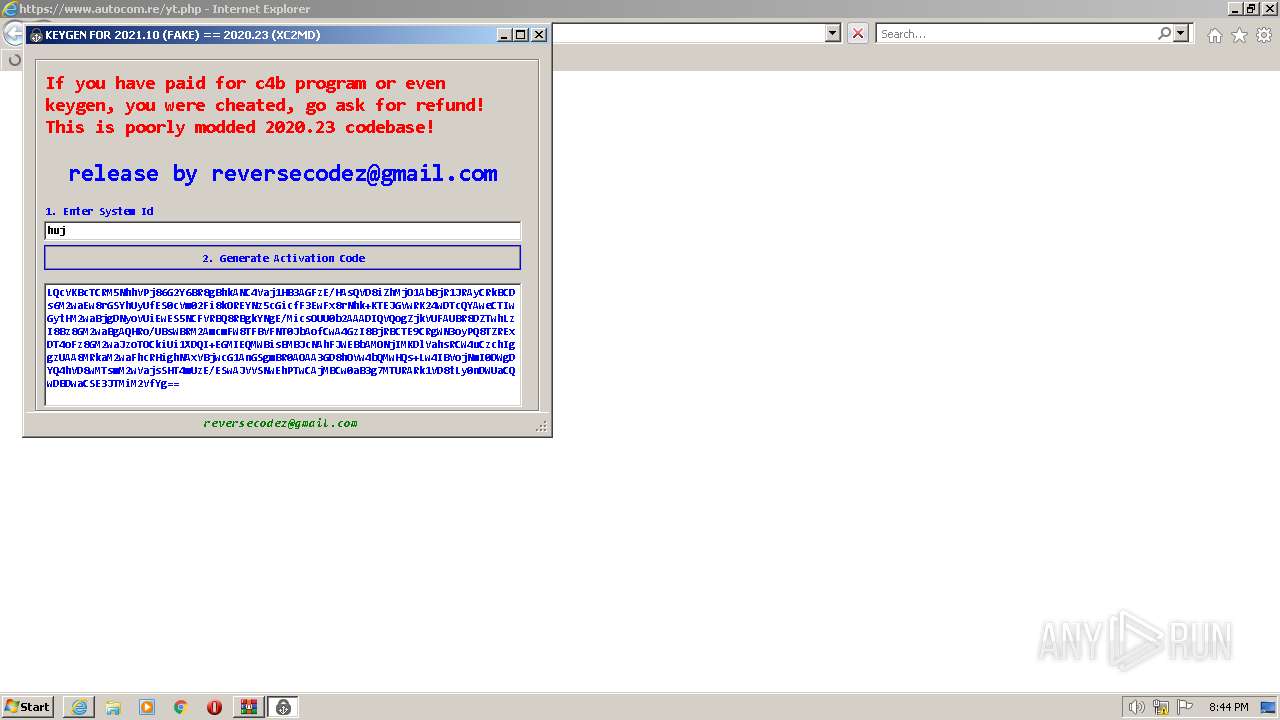
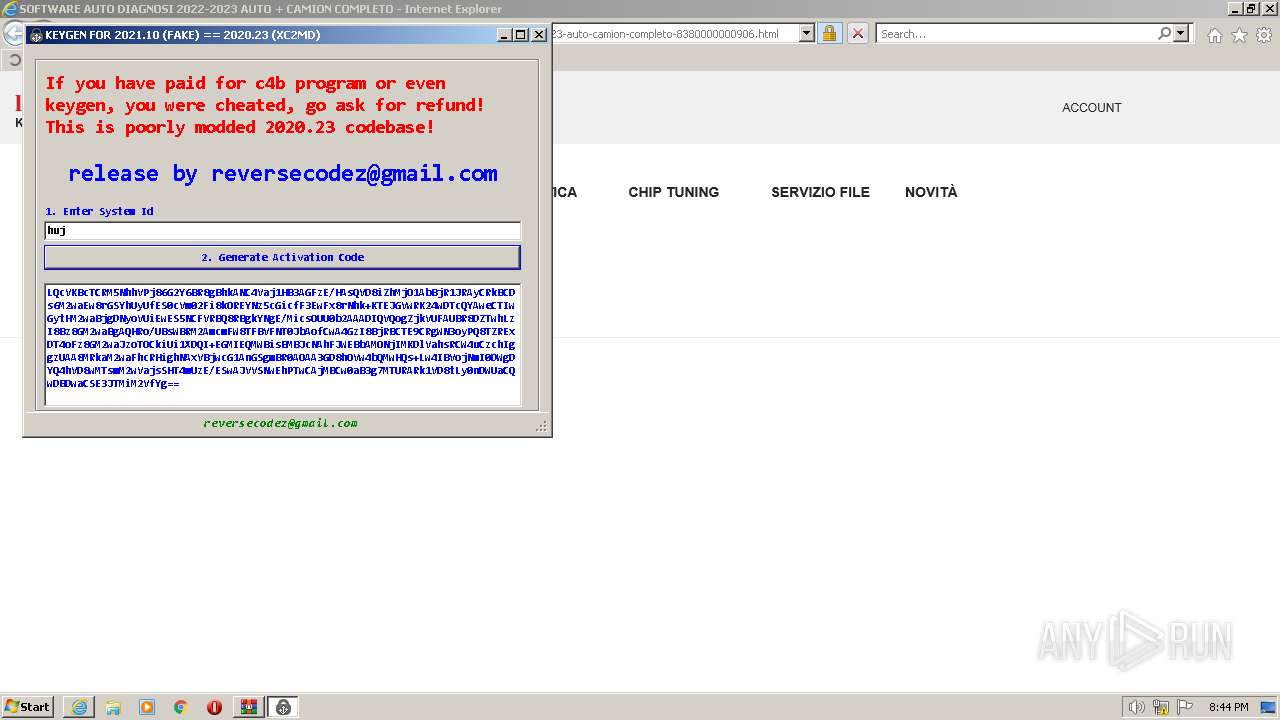
| File name: | Keygen_For_Fake_2021_11_by_ReverseCodez.rar |
| Full analysis: | https://app.any.run/tasks/8afb8580-0840-45fe-a91a-2bf4b8cc29a1 |
| Verdict: | Malicious activity |
| Analysis date: | May 28, 2023, 19:44:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 89C1142CA760197306B87A1EA4FF8488 |
| SHA1: | 0EC9213E12975550333729ECCC03CBE9CE44ED53 |
| SHA256: | 0DD4434FE34DE41C317A14592A1B6A3DCC4EB7450125CFA6F843CADDFB2337FA |
| SSDEEP: | 3072:9sqC6TsuOXZXeFO23iaq78IIM2bBjEIRUA:JsukZXeFUF70M2bmIRUA |
MALICIOUS
Application was dropped or rewritten from another process
- Keygen_For_Fake_2021_11_by_ReverseCodez.exe (PID: 2476)
SUSPICIOUS
Reads the Internet Settings
- Keygen_For_Fake_2021_11_by_ReverseCodez.exe (PID: 2476)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4092)
Checks supported languages
- Keygen_For_Fake_2021_11_by_ReverseCodez.exe (PID: 2476)
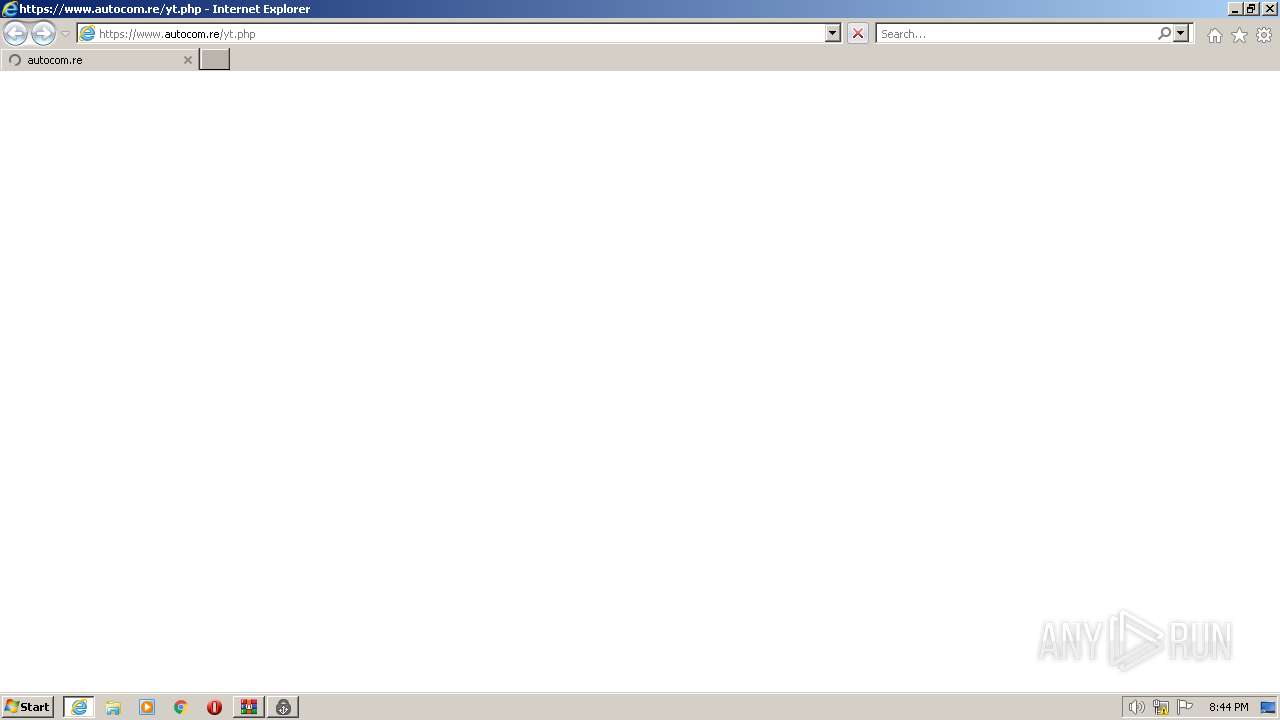
Application launched itself
- iexplore.exe (PID: 820)
Reads the computer name
- Keygen_For_Fake_2021_11_by_ReverseCodez.exe (PID: 2476)
Create files in a temporary directory
- iexplore.exe (PID: 820)
- iexplore.exe (PID: 3120)
Reads the machine GUID from the registry
- Keygen_For_Fake_2021_11_by_ReverseCodez.exe (PID: 2476)
The process checks LSA protection
- Keygen_For_Fake_2021_11_by_ReverseCodez.exe (PID: 2476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
40
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 820 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.autocom.re/yt.php | C:\Program Files\Internet Explorer\iexplore.exe | Keygen_For_Fake_2021_11_by_ReverseCodez.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2476 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4092.5472\Keygen_For_Fake_2021_11_by_ReverseCodez.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4092.5472\Keygen_For_Fake_2021_11_by_ReverseCodez.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Keygen Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3120 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:820 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4092 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Keygen_For_Fake_2021_11_by_ReverseCodez.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
19 872
Read events
19 763
Write events
107
Delete events
2
Modification events
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
1
Suspicious files
63
Text files
165
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 3120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:1A2016CD7D68A14413530A182AF83C00 | SHA256:25C1C7F25C1AB3757C853A00FC92EB9CFC0A5CA89A3D610B09158EBA93D940DA | |||
| 3120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:D0BB1C217D93885FFFCC276A6B48C7FC | SHA256:0DD90A9D99ADDACBDF8D911D5AB69D15A90450B919898D378EE0E75DF6EE48DF | |||
| 4092 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4092.5472\Keygen_For_Fake_2021_11_by_ReverseCodez.exe | executable | |
MD5:6DA69B8791C12096042659EFCCA980C5 | SHA256:27FACA387D9A8E5C7E43366B3EB4E0E108C9BC1BBFADE960A7A41EB134F0EAE0 | |||
| 3120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:89609EDE8EFA46F94DA6FAD064FFF2F2 | SHA256:D43C5CD9708313EEF3A678F538B8DEDFD0678D17491F8EB5E00B6A2B776C9649 | |||
| 3120 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1U66W33T.txt | text | |
MD5:56A4FE22DAA00E426F42FCD51D077530 | SHA256:A0EA18812A3DEEDEBCB9469FBFC02AC2FB6081E81709D0B21FB38998CF4AEB2B | |||
| 3120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:3AC860860707BAAF32469FA7CC7C0192 | SHA256:D015145D551ECD14916270EFAD773BBC9FD57FAD2228D2C24559F696C961D904 | |||
| 820 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:BE5E6FFE0CEF71E84AA5445537FD611A | SHA256:99989DDB05AC43D7AA3B6857E63985B38B3123D939814A374A11762026775FA3 | |||
| 3120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6993ED1A32879B8A1ECFCC601881358F | binary | |
MD5:A0D548F37209280F0E6A3EF2138CA960 | SHA256:AA83E697BEFC64E738191C0237E6FC7F1E204FB14AAE9C6588E1D33DB1319C4F | |||
| 3120 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\OU8K5KCT.txt | text | |
MD5:F797FFEF22AC62E11C080A30C7756B24 | SHA256:DD203FE7A12C7F4A32A82C78C73B5E45DFFC027A9D23F6F5C362F239557A992D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
78
DNS requests
32
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3120 | iexplore.exe | GET | — | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCKJOyu2maNfwq1WudyH8eI | US | — | — | whitelisted |
3120 | iexplore.exe | GET | — | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHzBdM78nb12Iemmn%2F8ya%2B0%3D | US | — | — | whitelisted |
3120 | iexplore.exe | GET | — | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCf4d%2FNemnDwxJHGtU61rL9 | US | — | — | whitelisted |
3120 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC8BvJrfo6wqwnyfQ7FZgF1 | US | der | 472 b | whitelisted |
3120 | iexplore.exe | GET | 200 | 23.201.254.55:80 | http://x1.c.lencr.org/ | CH | der | 717 b | whitelisted |
3120 | iexplore.exe | GET | 200 | 67.26.81.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1aa3e47269e0af79 | US | compressed | 4.70 Kb | whitelisted |
3120 | iexplore.exe | GET | 200 | 2.16.241.15:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgRMi9LcSgOIgf8ZGsUoFqtiNg%3D%3D | unknown | binary | 503 b | shared |
3120 | iexplore.exe | GET | 200 | 23.201.254.55:80 | http://r3.i.lencr.org/ | CH | der | 1.28 Kb | whitelisted |
3120 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | binary | 1.41 Kb | whitelisted |
3120 | iexplore.exe | GET | 200 | 18.66.92.70:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | binary | 1.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3616 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3120 | iexplore.exe | 103.163.187.150:443 | www.autocom.re | SpeedyPage Ltd | GB | suspicious |
3120 | iexplore.exe | 67.26.81.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
820 | iexplore.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | suspicious |
3120 | iexplore.exe | 2.16.241.15:80 | r3.o.lencr.org | Akamai International B.V. | DE | suspicious |
3120 | iexplore.exe | 86.105.14.24:443 | www.universaltuning.it | IT.Gate S.p.A. | IT | unknown |
3120 | iexplore.exe | 23.201.254.55:80 | r3.i.lencr.org | AKAMAI-AS | CH | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.autocom.re |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
r3.i.lencr.org |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
www.universaltuning.it |
| unknown |
ocsp.digicert.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1076 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |