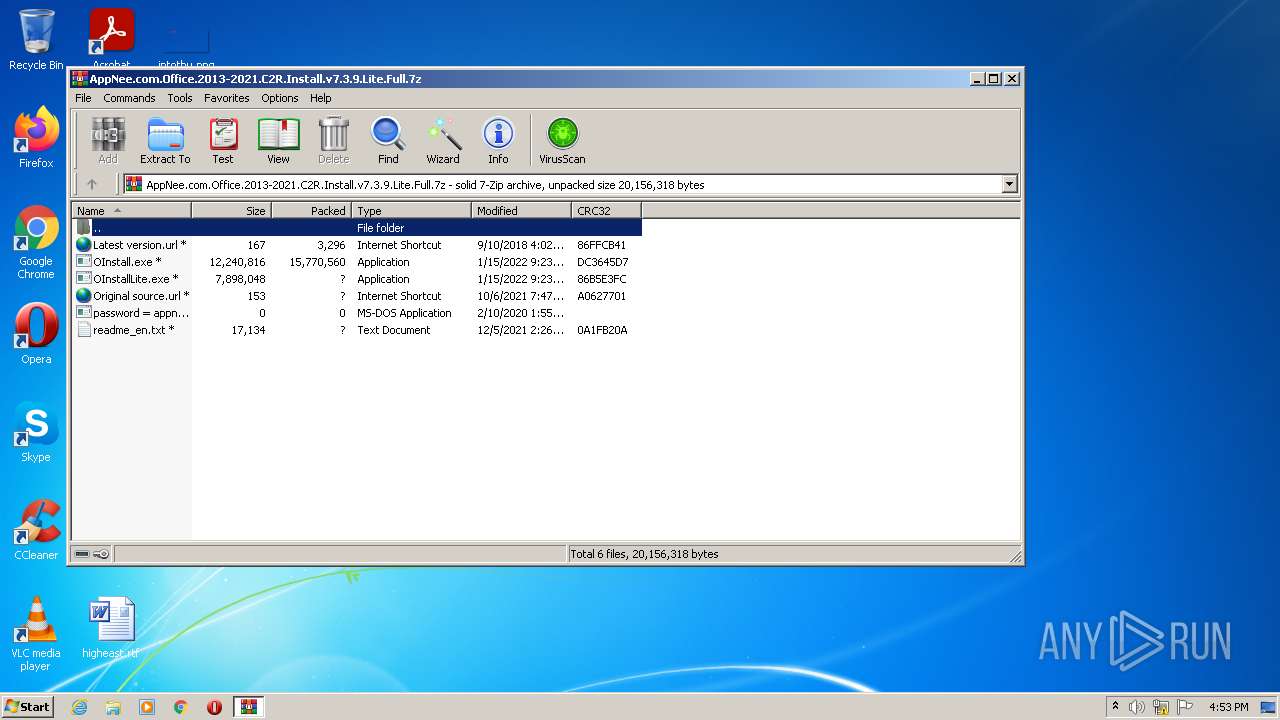
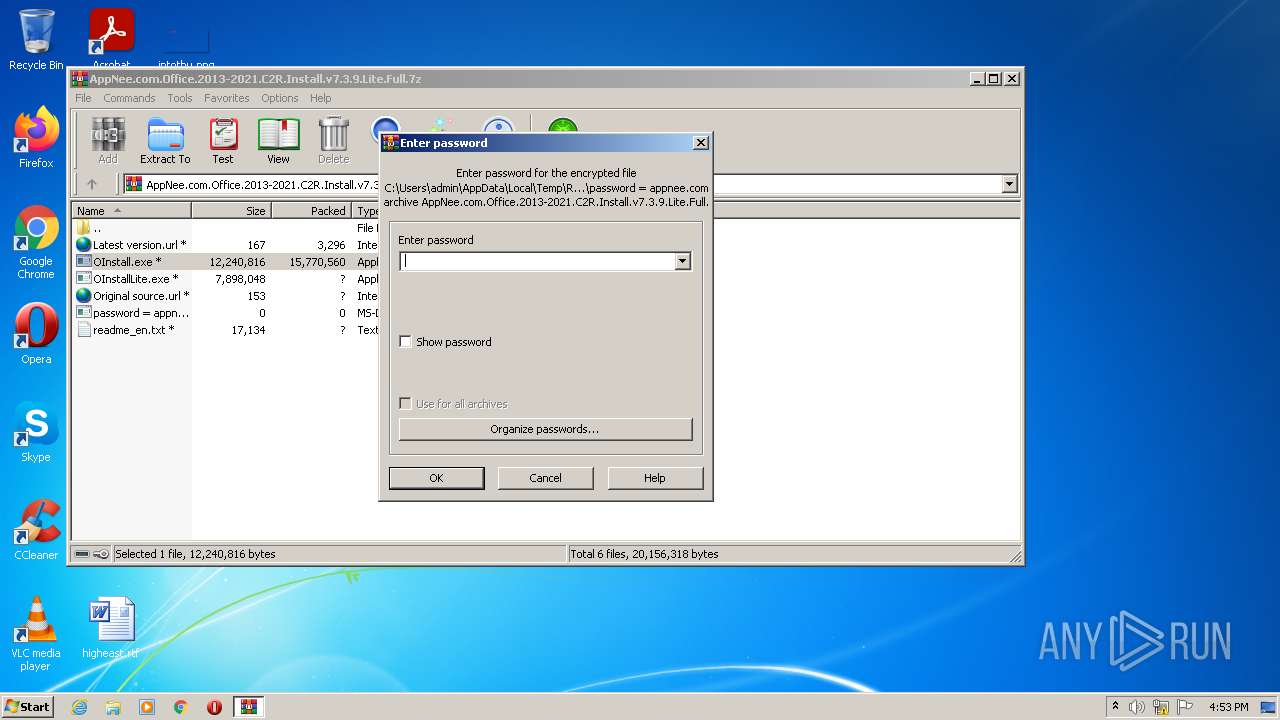
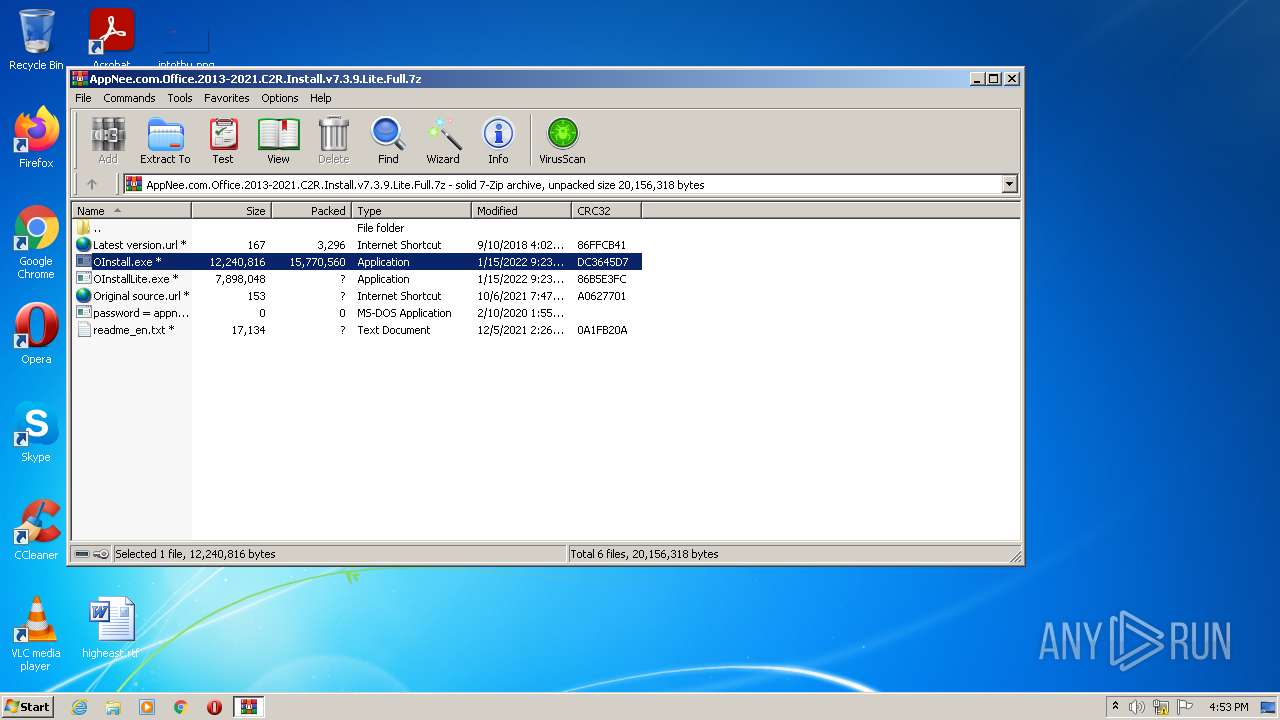
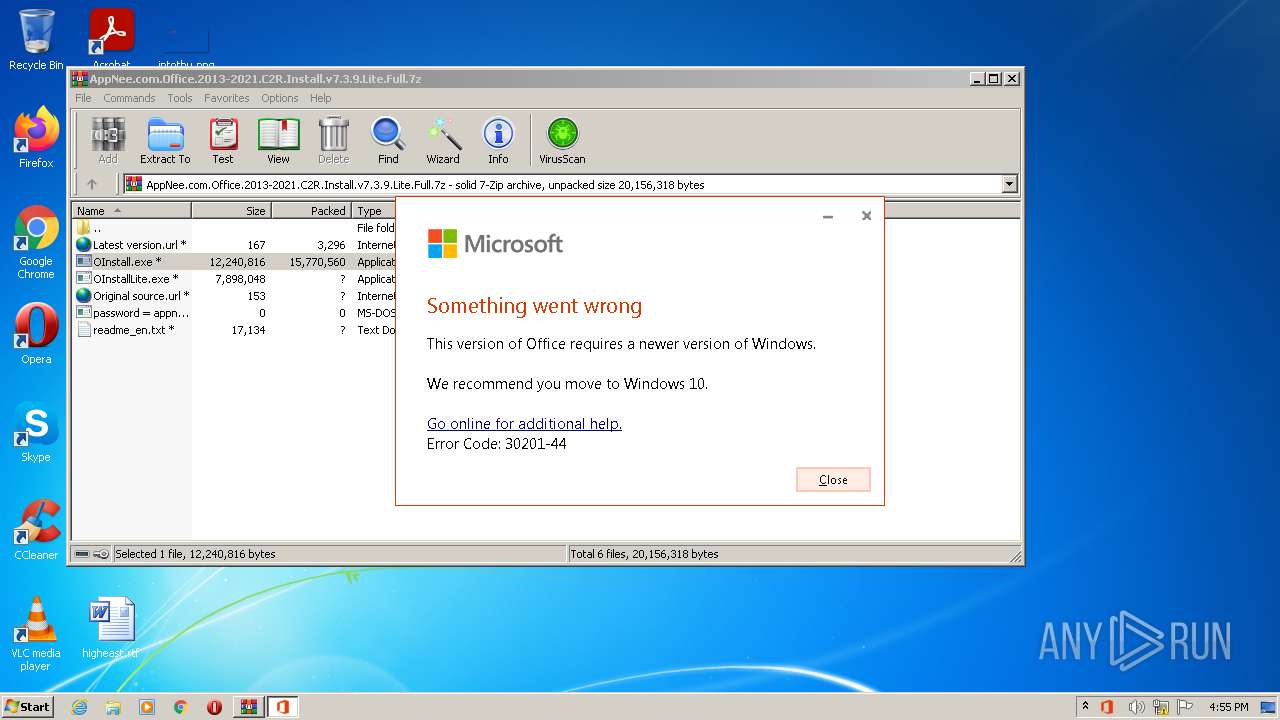
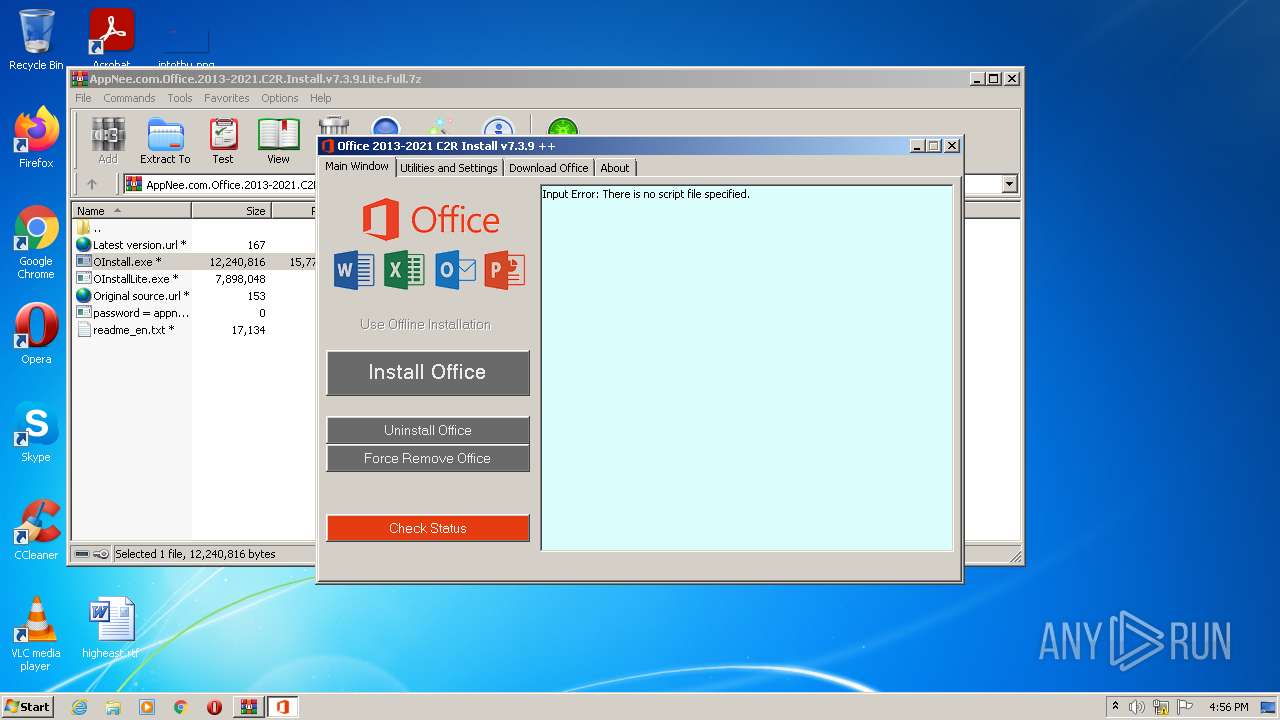
| File name: | AppNee.com.Office.2013-2021.C2R.Install.v7.3.9.Lite.Full.7z |
| Full analysis: | https://app.any.run/tasks/1d8db937-9555-48e5-ac16-744f74e76d17 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 16:53:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A0DDEE5E11429E74CE5FADD7AFEB7108 |
| SHA1: | FEE7C64C98FC7133C6BDE7310BCBB5CA671B0A50 |
| SHA256: | 0DBFDF325766C93565CA3AD87B31E51D0C0FEDD99022E740AFFD48E03F6A88B3 |
| SSDEEP: | 393216:aAj81cvH39gwzff/RQoXeZQPjgEiGOvZRvr79:LSwTwmgFGY5R |
MALICIOUS
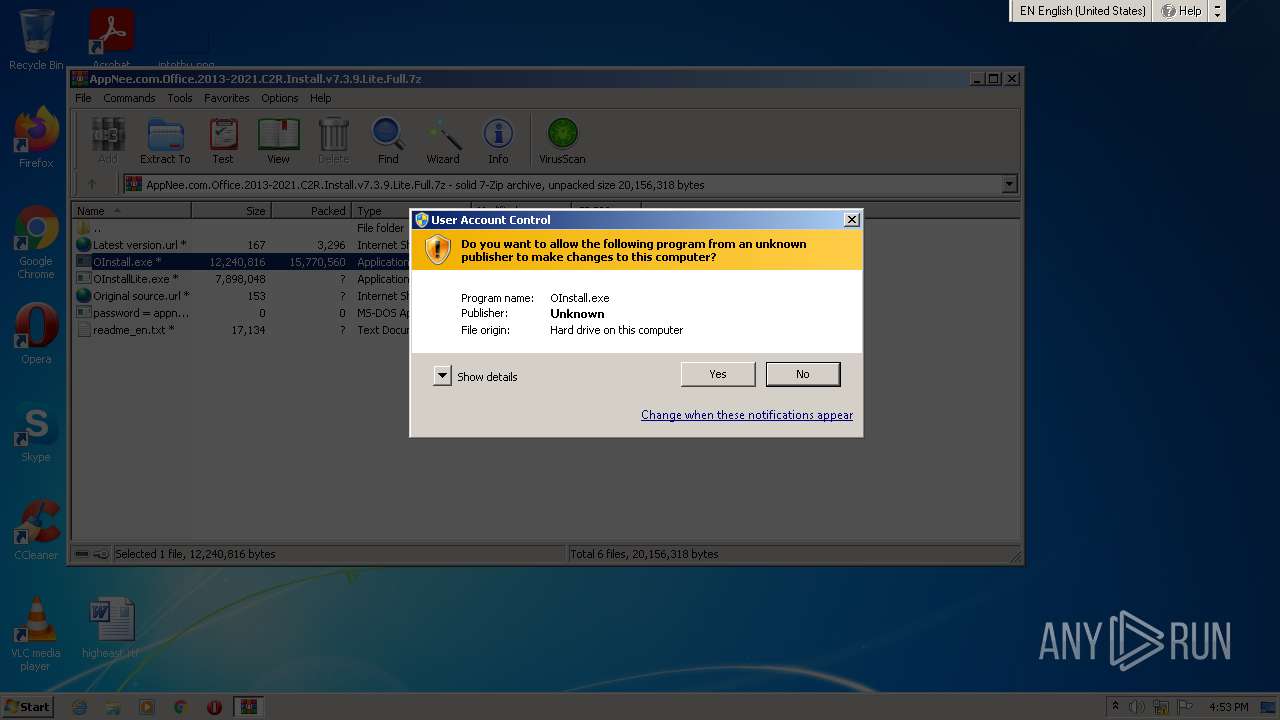
Application was dropped or rewritten from another process
- OInstall.exe (PID: 2700)
- OInstall.exe (PID: 2356)
- files.dat (PID: 2920)
- OfficeClickToRun.exe (PID: 188)
- OfficeClickToRun.exe (PID: 3848)
Drops executable file immediately after starts
- OInstall.exe (PID: 2700)
- files.dat (PID: 2920)
- OfficeClickToRun.exe (PID: 3848)
Loads dropped or rewritten executable
- OfficeClickToRun.exe (PID: 188)
- OfficeClickToRun.exe (PID: 3848)
Changes settings of System certificates
- OfficeClickToRun.exe (PID: 3848)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 4076)
- OInstall.exe (PID: 2700)
- cmd.exe (PID: 2768)
- files.dat (PID: 2920)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 904)
- powershell.exe (PID: 3400)
- powershell.exe (PID: 3768)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 528)
- powershell.exe (PID: 480)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1312)
- OfficeClickToRun.exe (PID: 3848)
- OfficeClickToRun.exe (PID: 188)
- cmd.exe (PID: 3376)
- cmd.exe (PID: 2524)
- cmd.exe (PID: 684)
- cmd.exe (PID: 3248)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 2748)
- cmd.exe (PID: 188)
- cscript.exe (PID: 2228)
- cmd.exe (PID: 2844)
Reads the computer name
- WinRAR.exe (PID: 4076)
- OInstall.exe (PID: 2700)
- powershell.exe (PID: 3400)
- powershell.exe (PID: 904)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 528)
- powershell.exe (PID: 480)
- powershell.exe (PID: 3768)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 1312)
- powershell.exe (PID: 3332)
- OfficeClickToRun.exe (PID: 188)
- OfficeClickToRun.exe (PID: 3848)
- cscript.exe (PID: 2228)
Reads Environment values
- OInstall.exe (PID: 2700)
- powershell.exe (PID: 904)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 528)
- powershell.exe (PID: 1312)
- powershell.exe (PID: 3332)
- OfficeClickToRun.exe (PID: 188)
- OfficeClickToRun.exe (PID: 3848)
Executable content was dropped or overwritten
- OInstall.exe (PID: 2700)
- files.dat (PID: 2920)
- WinRAR.exe (PID: 4076)
- expand.exe (PID: 3888)
- OfficeClickToRun.exe (PID: 3848)
Starts application with an unusual extension
- cmd.exe (PID: 2768)
Drops a file that was compiled in debug mode
- OInstall.exe (PID: 2700)
- files.dat (PID: 2920)
- expand.exe (PID: 3888)
- OfficeClickToRun.exe (PID: 3848)
Drops a file with a compile date too recent
- OInstall.exe (PID: 2700)
- WinRAR.exe (PID: 4076)
- expand.exe (PID: 3888)
- OfficeClickToRun.exe (PID: 3848)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 2700)
Executes PowerShell scripts
- OInstall.exe (PID: 2700)
Uses REG.EXE to modify Windows registry
- OInstall.exe (PID: 2700)
- cmd.exe (PID: 3248)
- cmd.exe (PID: 2524)
- cmd.exe (PID: 684)
- cmd.exe (PID: 3376)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 2748)
- cmd.exe (PID: 2844)
Drops a file with too old compile date
- expand.exe (PID: 3888)
Creates a directory in Program Files
- expand.exe (PID: 2708)
- OInstall.exe (PID: 2700)
- expand.exe (PID: 3888)
- OfficeClickToRun.exe (PID: 3848)
Creates files in the program directory
- expand.exe (PID: 2708)
- OfficeClickToRun.exe (PID: 3848)
- expand.exe (PID: 3888)
Creates files in the Windows directory
- OfficeClickToRun.exe (PID: 3848)
Executed as Windows Service
- OfficeClickToRun.exe (PID: 3848)
Adds / modifies Windows certificates
- OfficeClickToRun.exe (PID: 3848)
Removes files from Windows directory
- OfficeClickToRun.exe (PID: 3848)
Executes scripts
- cmd.exe (PID: 188)
INFO
Checks Windows Trust Settings
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3400)
- powershell.exe (PID: 904)
- powershell.exe (PID: 3768)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 528)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 1312)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 480)
- OfficeClickToRun.exe (PID: 3848)
Checks supported languages
- expand.exe (PID: 3416)
- expand.exe (PID: 3876)
- expand.exe (PID: 3372)
- reg.exe (PID: 2576)
- expand.exe (PID: 3704)
- expand.exe (PID: 3888)
- expand.exe (PID: 2708)
- reg.exe (PID: 1252)
- reg.exe (PID: 1148)
- reg.exe (PID: 976)
- reg.exe (PID: 2936)
- reg.exe (PID: 1708)
- reg.exe (PID: 2576)
- reg.exe (PID: 2864)
Dropped object may contain Bitcoin addresses
- expand.exe (PID: 3416)
Reads settings of System Certificates
- OfficeClickToRun.exe (PID: 3848)
- OfficeClickToRun.exe (PID: 188)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 188)
- OfficeClickToRun.exe (PID: 3848)
- reg.exe (PID: 1148)
- reg.exe (PID: 1252)
- reg.exe (PID: 2864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
104
Monitored processes
40
Malicious processes
5
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
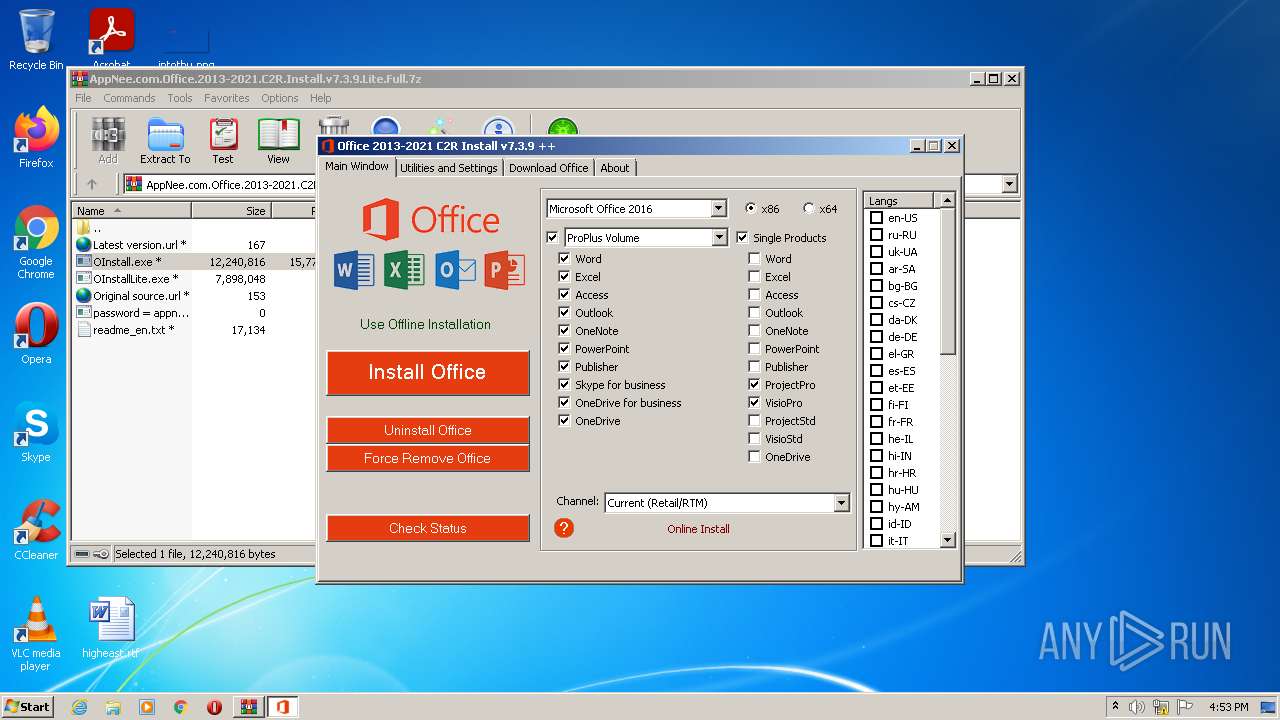
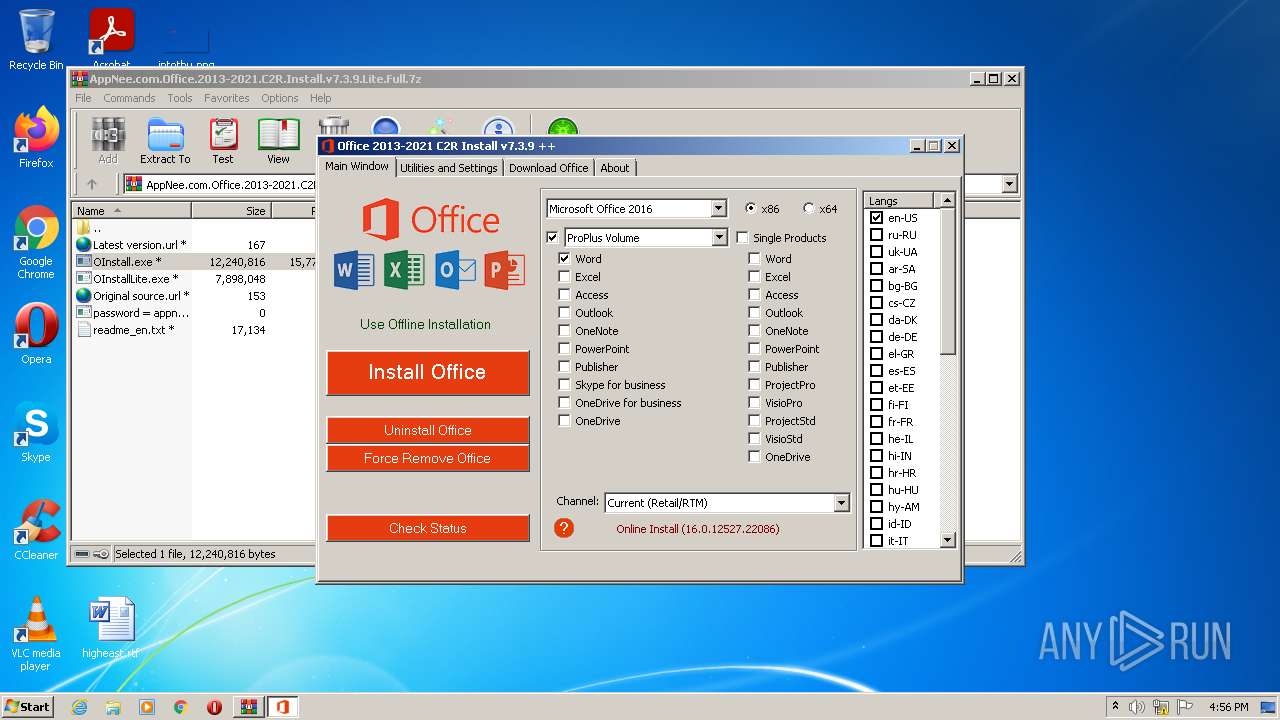
| 188 | "C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe" deliverymechanism=492350f6-3a01-4f97-b9c0-c7c6ddf67d60 platform=x86 productreleaseid=none culture=en-us defaultplatform=False lcid=1033 b= storeid= forceupgrade=True piniconstotaskbar=False pidkeys=XQNVK-8JYDB-WJ9W3-YJ8YR-WFG99 forceappshutdown=True autoactivate=1 productstoadd=ProPlusVolume.16_en-us_x-none scenario=unknown updatesenabled.16=True acceptalleulas.16=True cdnbaseurl.16=http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 version.16=16.0.14729.20260 mediatype.16=CDN baseurl.16=http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 sourcetype.16=CDN displaylevel=True uninstallpreviousversion=True ProPlusVolume.excludedapps.16=excel,access,publisher,groove,lync,onenote,outlook,powerpoint,onedrive,teams | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Click-to-Run (SxS) Exit code: 17004 Version: 16.0.14729.20228 Modules
| |||||||||||||||
| 188 | "C:\Windows\System32\cmd.exe" /D /c cscript.exe "" /dstatus //NoLogo | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 480 | "powershell" -command "& { Get-Content C:\Users\admin\AppData\Local\Temp\over771349\VersionDescriptor.xml | Set-Content -Encoding ASCII v32.txt } | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 528 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab', 'C:\Users\admin\AppData\Local\Temp\over771349\v32.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 684 | "C:\Windows\System32\cmd.exe" /D /c reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration" /f /v "UpdateUrl" /t REG_SZ /d http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 904 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab', 'C:\Users\admin\AppData\Local\Temp\over373465\v32.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 976 | reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration" /f /v "UpdateUrl" /t REG_SZ /d http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1148 | reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration" /f /v "AudienceId" /t REG_SZ /d 492350f6-3a01-4f97-b9c0-c7c6ddf67d60 | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1252 | reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration" /f /v "CDNBaseUrl" /t REG_SZ /d http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1312 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/16.0.14729.20260/i320.cab', 'C:\Users\admin\AppData\Local\Temp\over771349\i320.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
18 232
Read events
17 935
Write events
284
Delete events
13
Modification events
| (PID) Process: | (4076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4076) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (4076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AppNee.com.Office.2013-2021.C2R.Install.v7.3.9.Lite.Full.7z | |||
| (PID) Process: | (4076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
220
Suspicious files
35
Text files
40
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4076 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4076.37965\Latest version.url | url | |
MD5:— | SHA256:— | |||
| 4076 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4076.37965\Original source.url | url | |
MD5:— | SHA256:— | |||
| 4076 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4076.37965\readme_en.txt | text | |
MD5:— | SHA256:— | |||
| 3068 | powershell.exe | C:\Users\admin\AppData\Local\Temp\over699146\v32.cab | compressed | |
MD5:— | SHA256:— | |||
| 3416 | expand.exe | C:\Users\admin\AppData\Local\Temp\over699146\$dpx$.tmp\d954e76c9b75124b8331360160294bf9.tmp | xml | |
MD5:— | SHA256:— | |||
| 3416 | expand.exe | C:\Users\admin\AppData\Local\Temp\over699146\VersionDescriptor.xml | xml | |
MD5:— | SHA256:— | |||
| 3416 | expand.exe | C:\Windows\Logs\DPX\setupact.log | text | |
MD5:— | SHA256:— | |||
| 4076 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4076.37965\OInstall.exe | executable | |
MD5:0C56F6A26E937CB8A2B938F3501668B3 | SHA256:BB9316912AC3C5155D2EBB5FE1D8B569EE2913E342C6603ACB72F10E3FC2AA71 | |||
| 2700 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4076.37965\files\files.dat | executable | |
MD5:55D21B2C272A5D6B9F54FA9ED82BF9EB | SHA256:7A1C82E264258470D14CA345EA1A9B6FC34FA19B393A92077A01BE5F1AD08F47 | |||
| 2920 | files.dat | C:\Users\admin\AppData\Local\Temp\Rar$EXb4076.37965\files\Uninstall.xml | text | |
MD5:364F86F97324EA82FE0D142CD01CF6DD | SHA256:09D5B42140BAB13165BA97FBD0E77792304C3C93555BE02C3DCE21A7A69C66DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
26
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
904 | powershell.exe | GET | 301 | 104.107.160.60:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | US | — | — | whitelisted |
3068 | powershell.exe | GET | 301 | 104.107.160.60:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | US | — | — | whitelisted |
3504 | powershell.exe | GET | 301 | 104.107.160.60:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | US | — | — | whitelisted |
528 | powershell.exe | GET | 301 | 104.107.160.60:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | US | — | — | whitelisted |
1312 | powershell.exe | GET | 301 | 104.107.160.60:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/16.0.14729.20260/i320.cab | US | — | — | whitelisted |
3332 | powershell.exe | GET | 301 | 23.53.168.85:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/16.0.14729.20260/i321033.cab | NL | — | — | whitelisted |
904 | powershell.exe | GET | 200 | 23.32.238.209:80 | http://officecdn.microsoft.com.edgesuite.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | US | compressed | 10.8 Kb | whitelisted |
1932 | svchost.exe | GET | 200 | 2.18.233.62:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | der | 814 b | whitelisted |
3504 | powershell.exe | GET | 200 | 23.32.238.209:80 | http://officecdn.microsoft.com.edgesuite.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | US | compressed | 10.8 Kb | whitelisted |
528 | powershell.exe | GET | 200 | 23.32.238.208:80 | http://officecdn.microsoft.com.edgesuite.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | US | compressed | 10.8 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3068 | powershell.exe | 104.107.160.60:80 | officecdn.microsoft.com | GTT Communications Inc. | US | unknown |
904 | powershell.exe | 104.107.160.60:80 | officecdn.microsoft.com | GTT Communications Inc. | US | unknown |
3504 | powershell.exe | 104.107.160.60:80 | officecdn.microsoft.com | GTT Communications Inc. | US | unknown |
528 | powershell.exe | 104.107.160.60:80 | officecdn.microsoft.com | GTT Communications Inc. | US | unknown |
528 | powershell.exe | 23.32.238.208:80 | officecdn.microsoft.com.edgesuite.net | XO Communications | US | unknown |
1312 | powershell.exe | 104.107.160.60:80 | officecdn.microsoft.com | GTT Communications Inc. | US | unknown |
1312 | powershell.exe | 23.32.238.208:80 | officecdn.microsoft.com.edgesuite.net | XO Communications | US | unknown |
3332 | powershell.exe | 23.53.168.85:80 | officecdn.microsoft.com | Akamai Technologies, Inc. | NL | unknown |
3332 | powershell.exe | 2.16.106.171:80 | officecdn.microsoft.com.edgesuite.net | Akamai International B.V. | — | whitelisted |
3848 | OfficeClickToRun.exe | 52.113.194.132:443 | ecs.office.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officecdn.microsoft.com |
| whitelisted |
officecdn.microsoft.com.edgesuite.net |
| whitelisted |
ecs.office.com |
| whitelisted |
vortex-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |