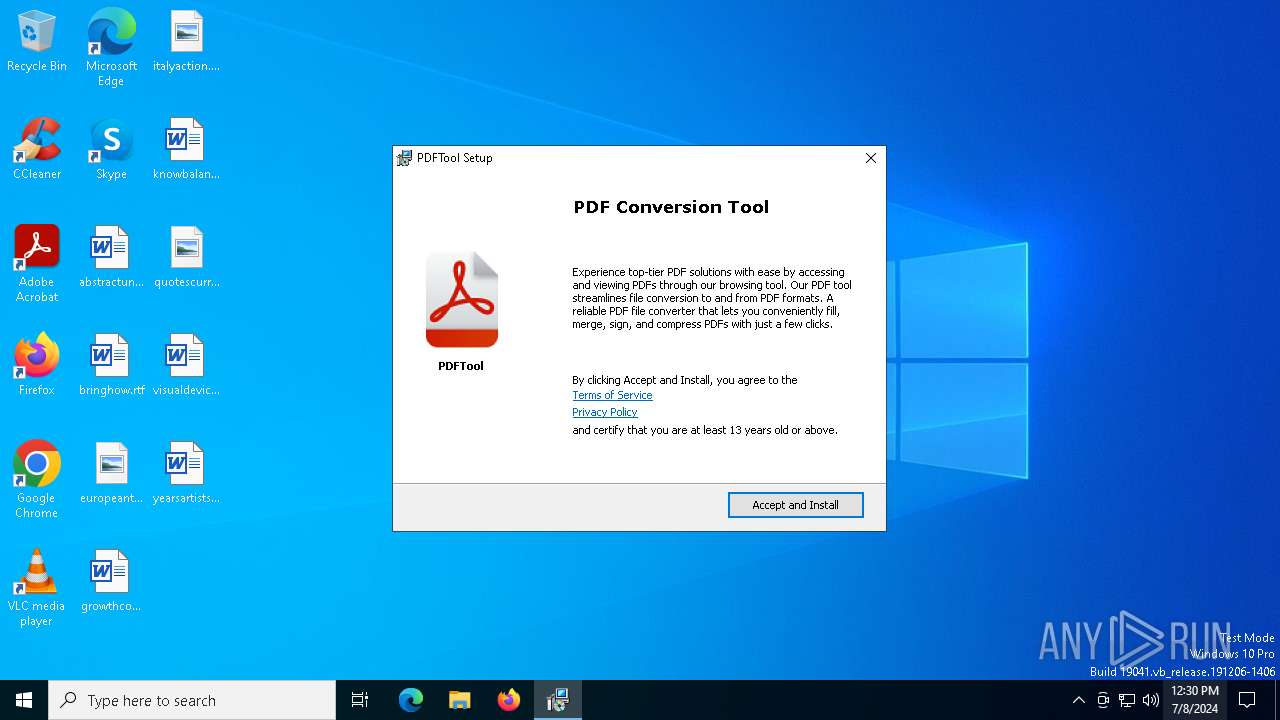
| File name: | PDFTool-v3.2.1233.0_50146512.msi |
| Full analysis: | https://app.any.run/tasks/249dc6ee-5156-43aa-acfe-887a09f5bbe2 |
| Verdict: | Malicious activity |
| Analysis date: | July 08, 2024, 12:29:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: PDFTool, Author: PDFTool, Keywords: Installer, MSI, Database, Comments: A base dados do instalador contm a lgica e os dados necessrios para instalar o PDFTool., Create Time/Date: Tue Jun 11 00:43:18 2024, Name of Creating Application: PDFTool, Security: 0, Template: ;1033, Last Saved By: ;1046, Revision Number: {FDB85B32-9B81-43D8-8670-E0B3CC28C504}3.2.1233.0;{FDB85B32-9B81-43D8-8670-E0B3CC28C504}3.2.1233.0;{A0D9FBCF-6C79-4E3B-B7A0-54DCC675BD69}, Number of Pages: 450, Number of Characters: 63 |
| MD5: | 615BE873A5FF5041D9D376F1B28B0695 |
| SHA1: | 1CB3DFCA3A92AF9E6BEAB6C38EE47DC32203F5C2 |
| SHA256: | 0DBC1C15CEFBCD850388CC9A31B690CC1254B9E724F9CD8CD9165E775DF48307 |
| SSDEEP: | 98304:N9ISoMSpkCN/2W4x0xaAW9BvOqPgBGs8fck3JrOrSLDunNurEQsIN9j6x4XWPUIJ:DR |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 6044)
- msiexec.exe (PID: 6936)
- msiexec.exe (PID: 7020)
Bypass execution policy to execute commands
- powershell.exe (PID: 6952)
- powershell.exe (PID: 1764)
Changes the autorun value in the registry
- msiexec.exe (PID: 7020)
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 6936)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 5240)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7020)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 6936)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 6936)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 6936)
The process executes Powershell scripts
- msiexec.exe (PID: 6936)
Process drops legitimate windows executable
- msiexec.exe (PID: 7020)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6936)
- msiexec.exe (PID: 7068)
Checks Windows Trust Settings
- msiexec.exe (PID: 6936)
- msiexec.exe (PID: 7020)
Node.exe was dropped
- msiexec.exe (PID: 6936)
Reads the date of Windows installation
- msiexec.exe (PID: 7068)
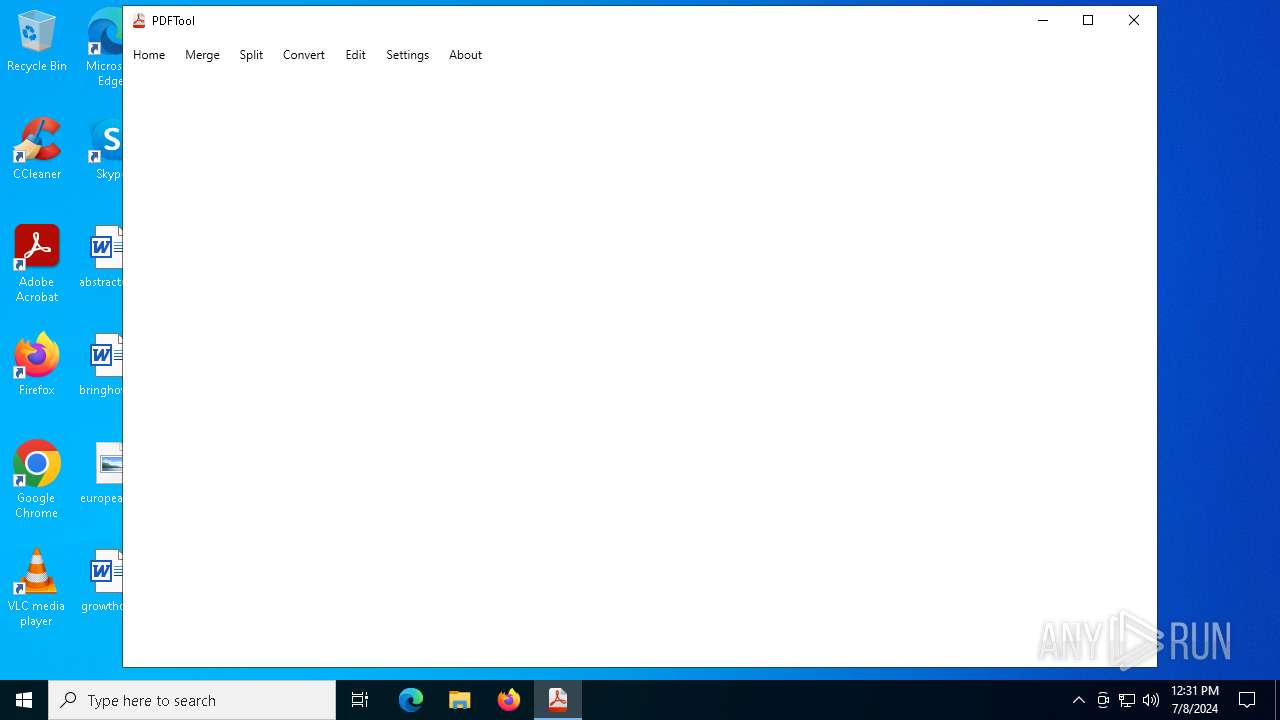
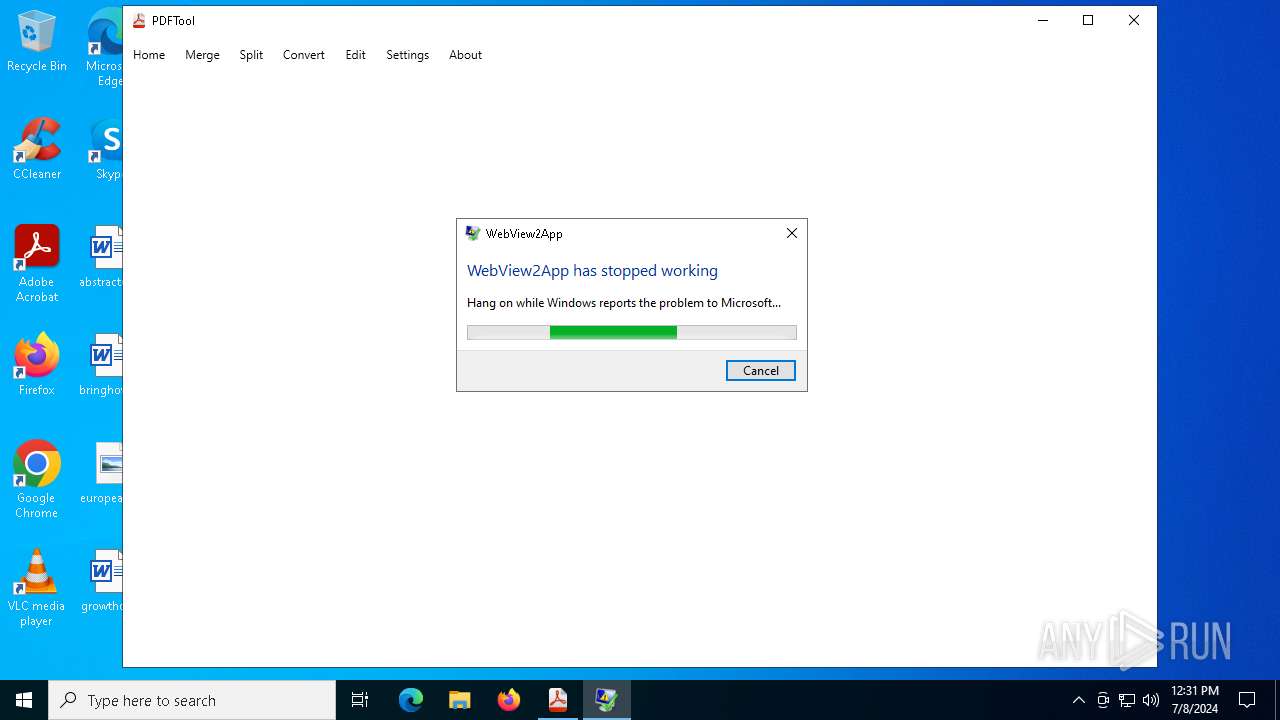
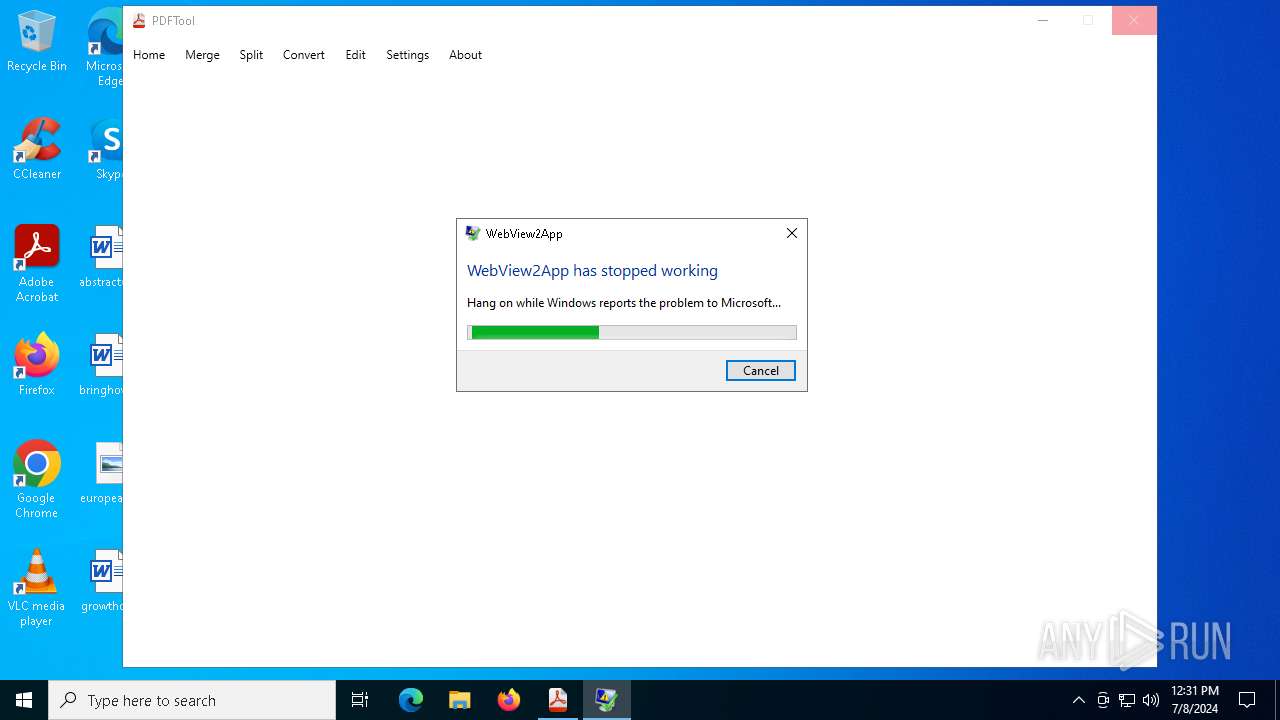
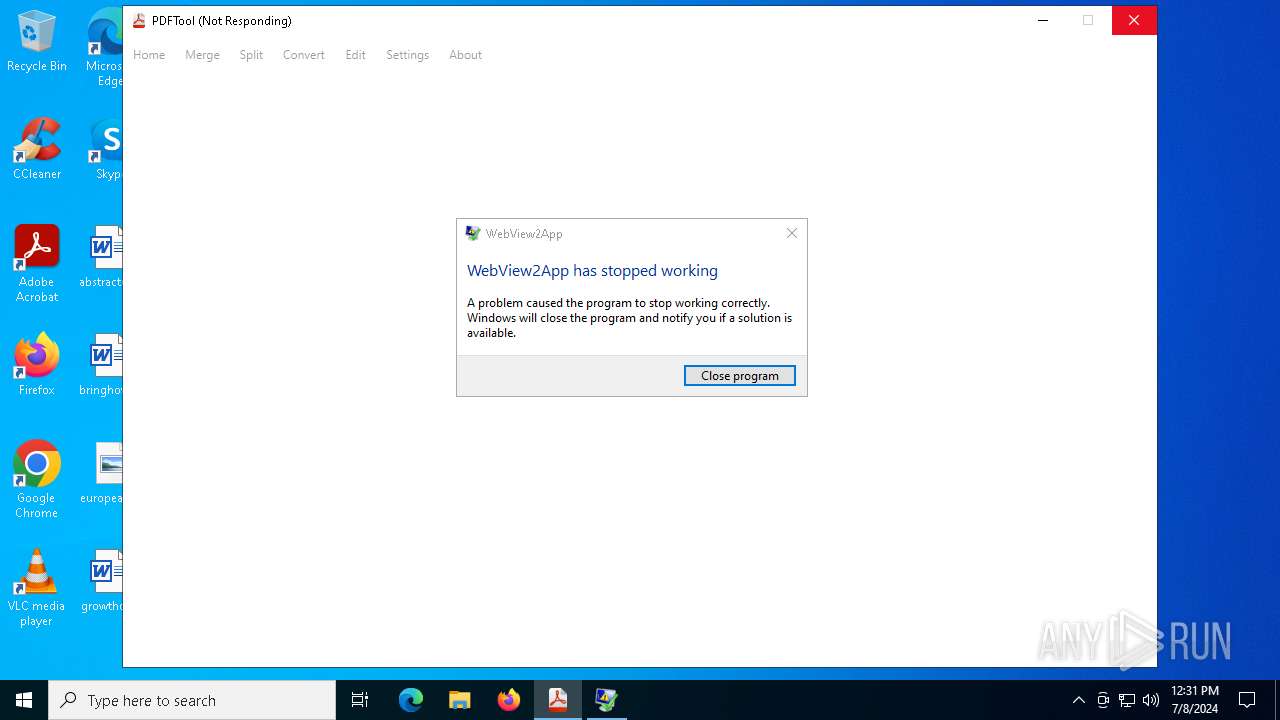
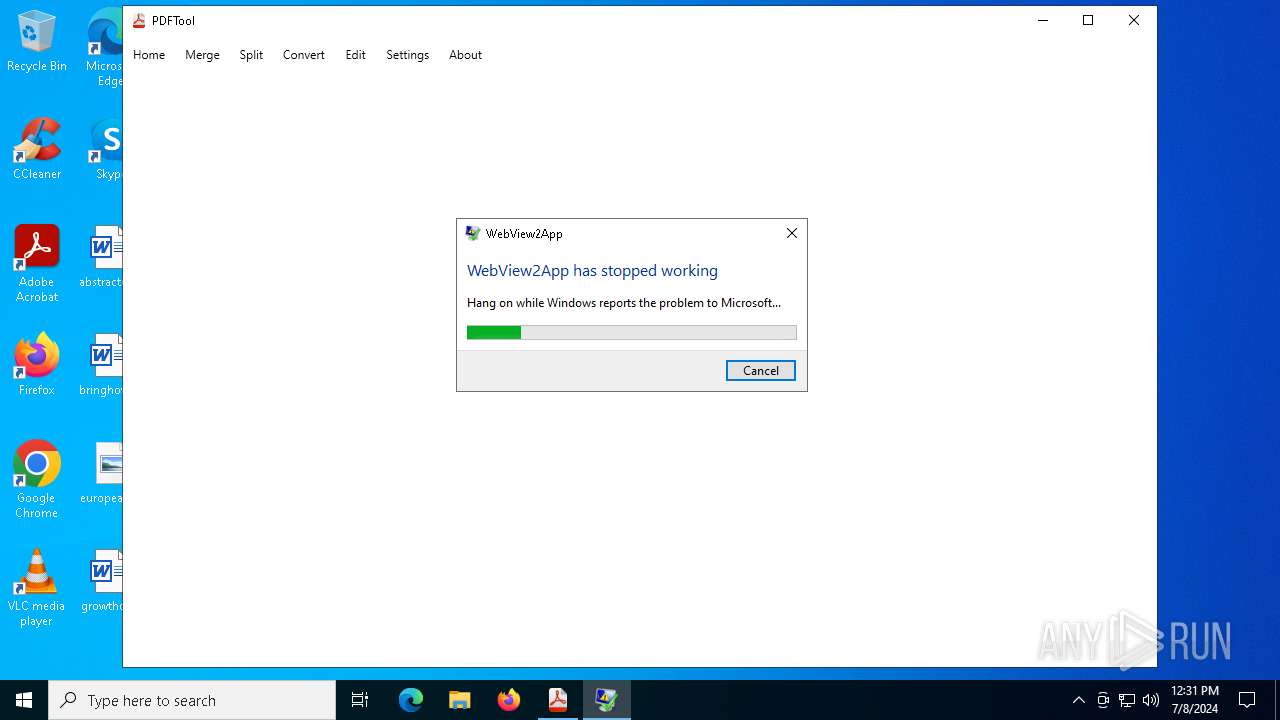
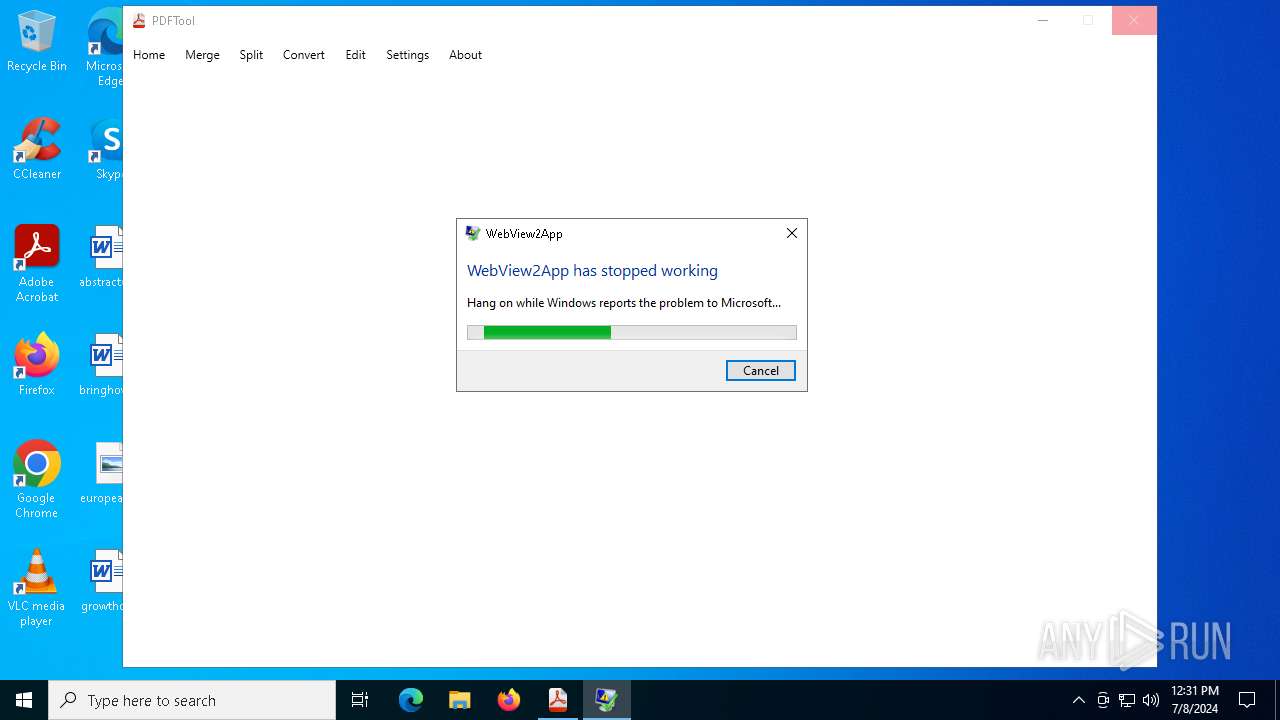
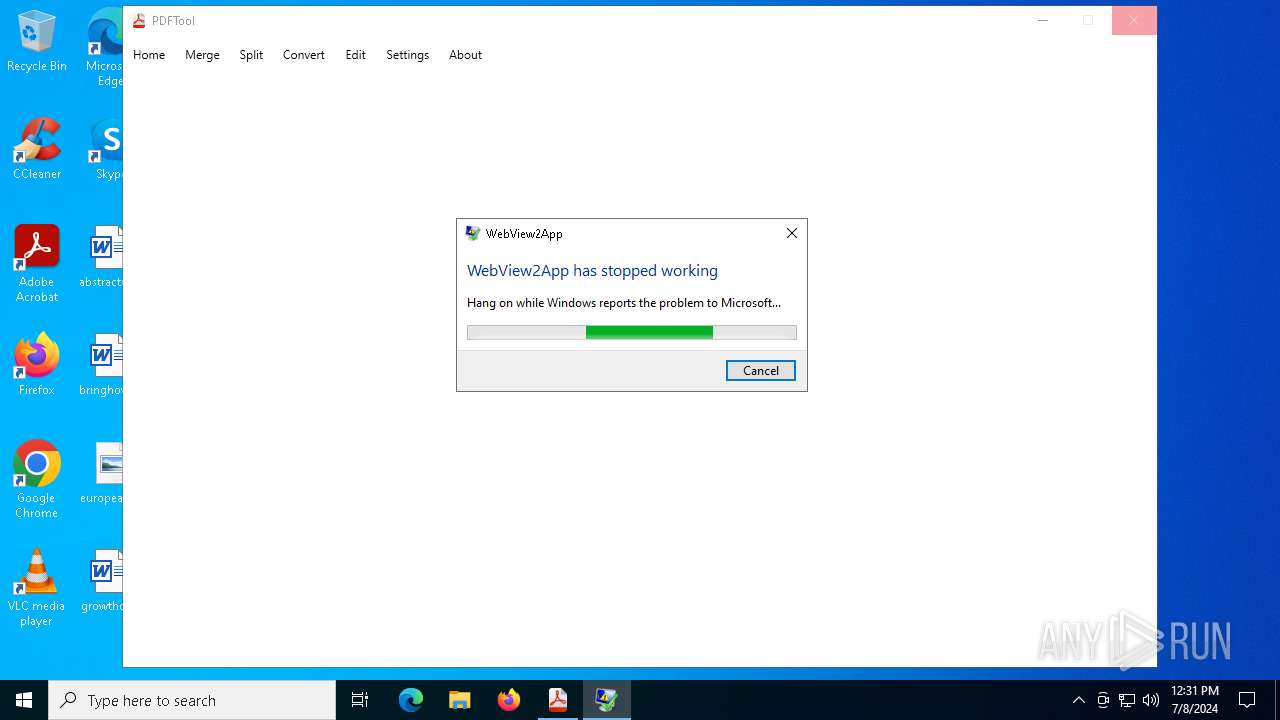
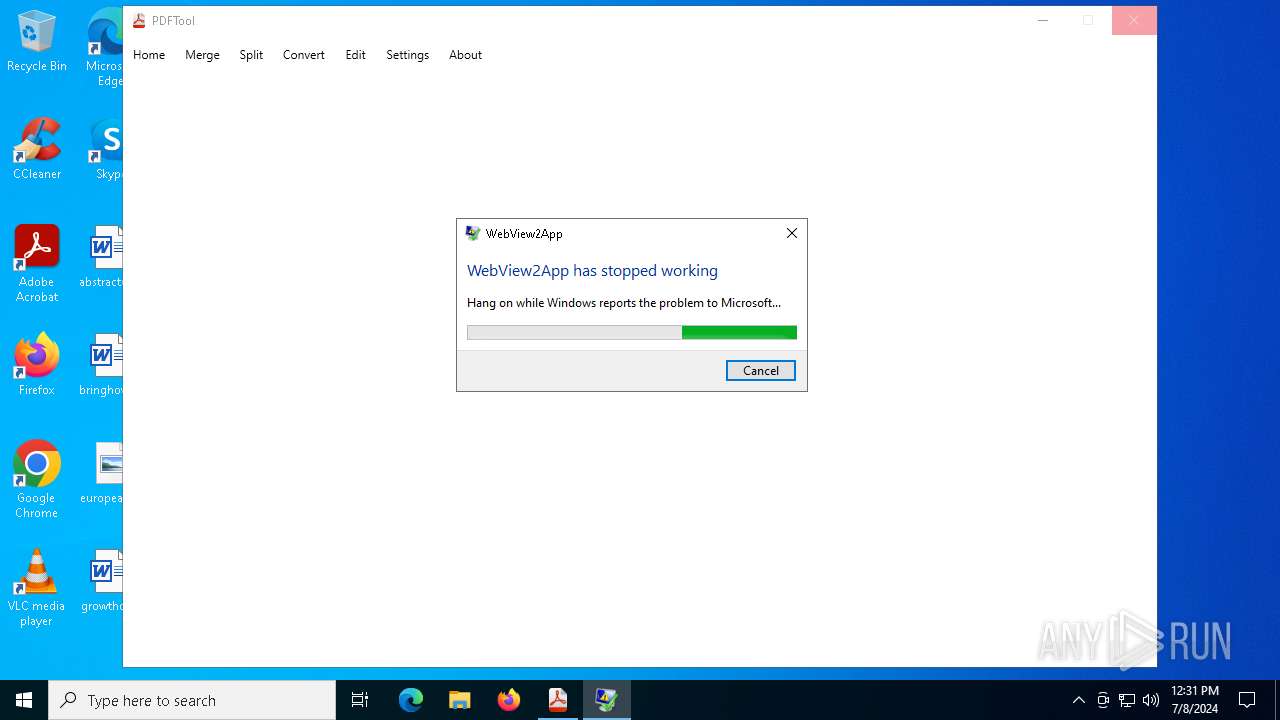
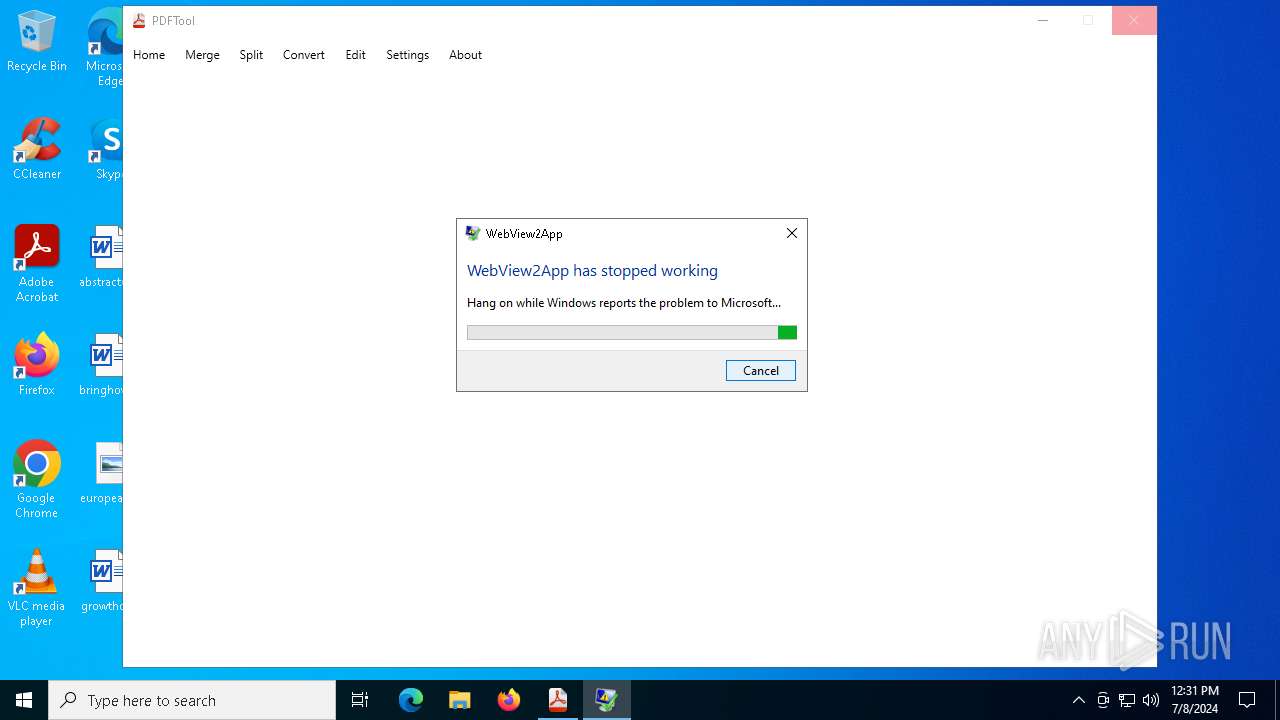
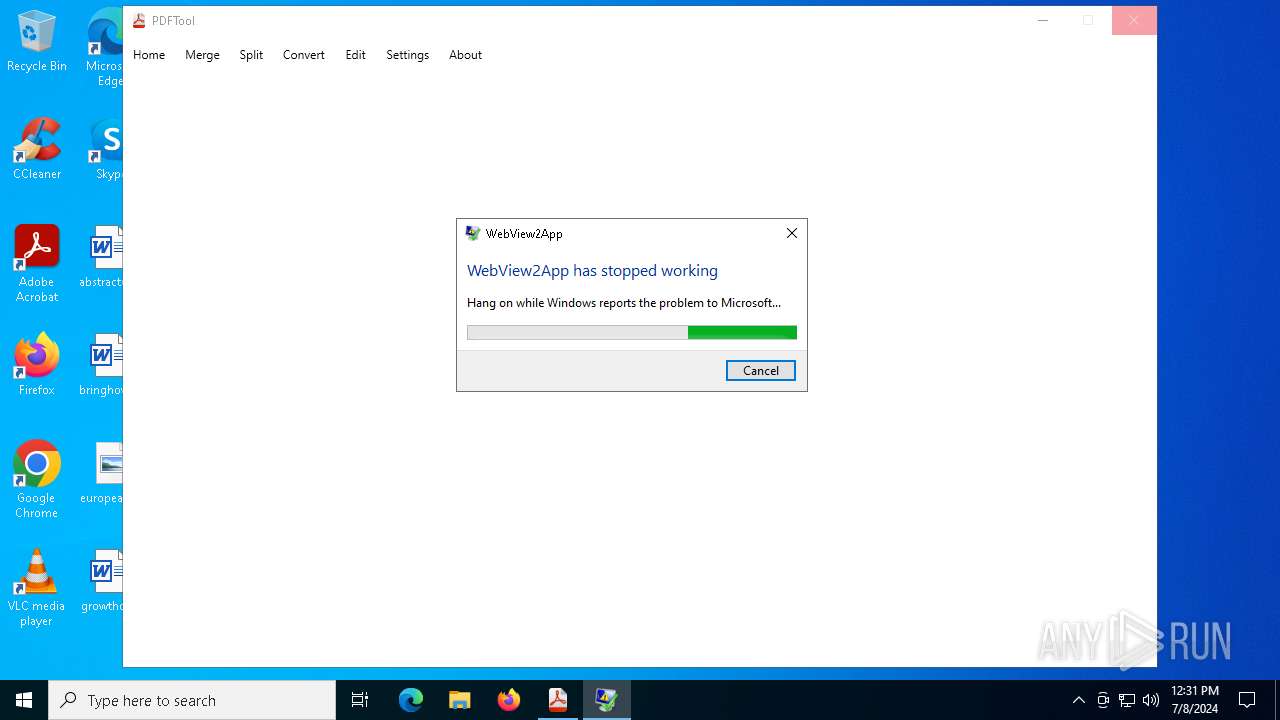
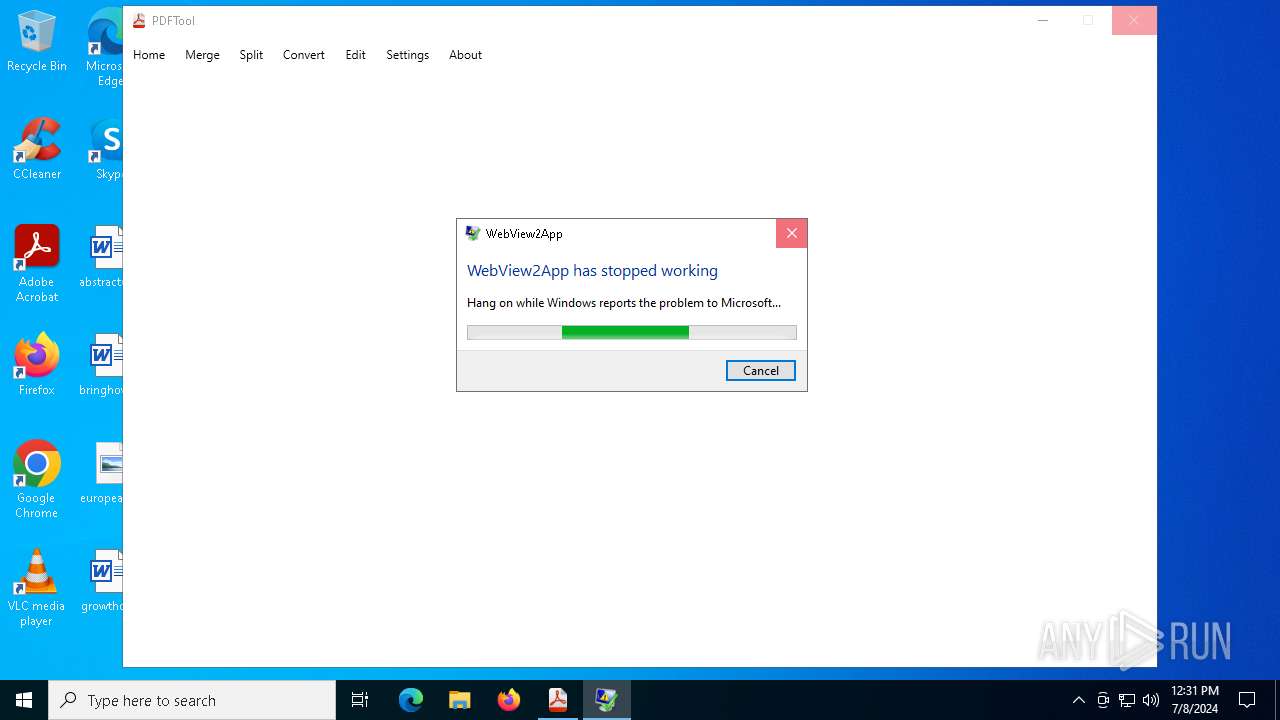
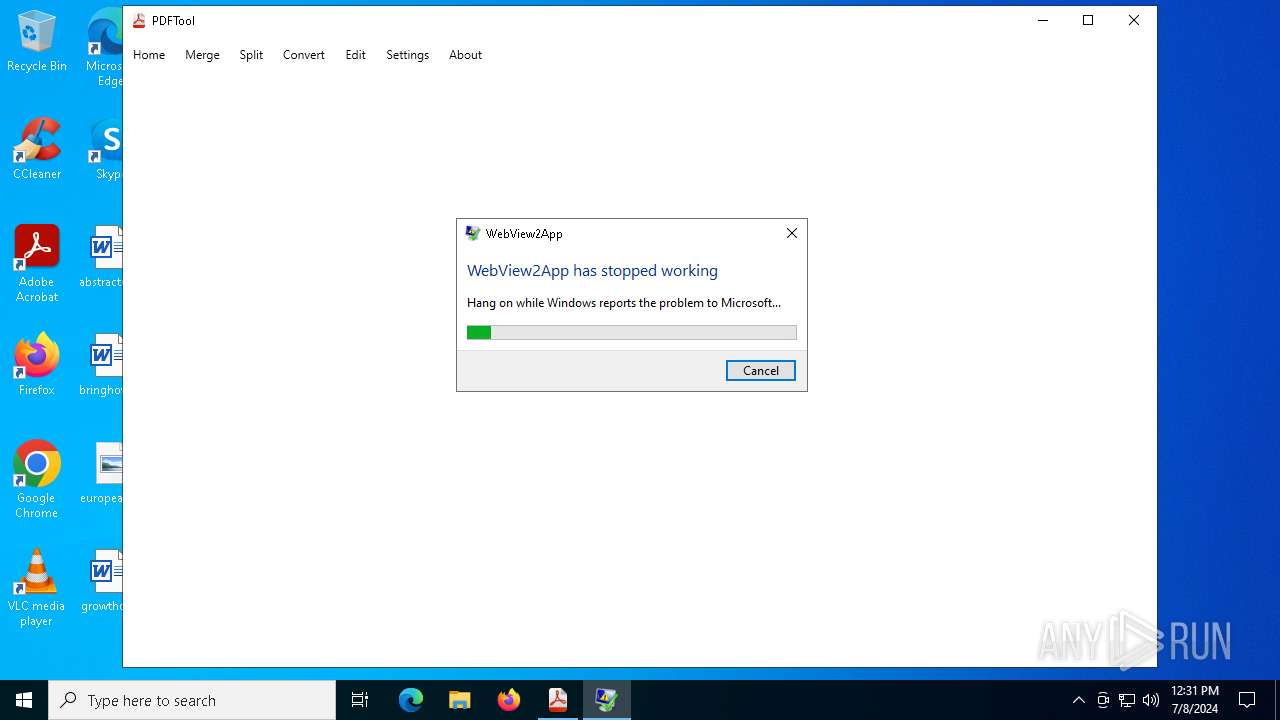
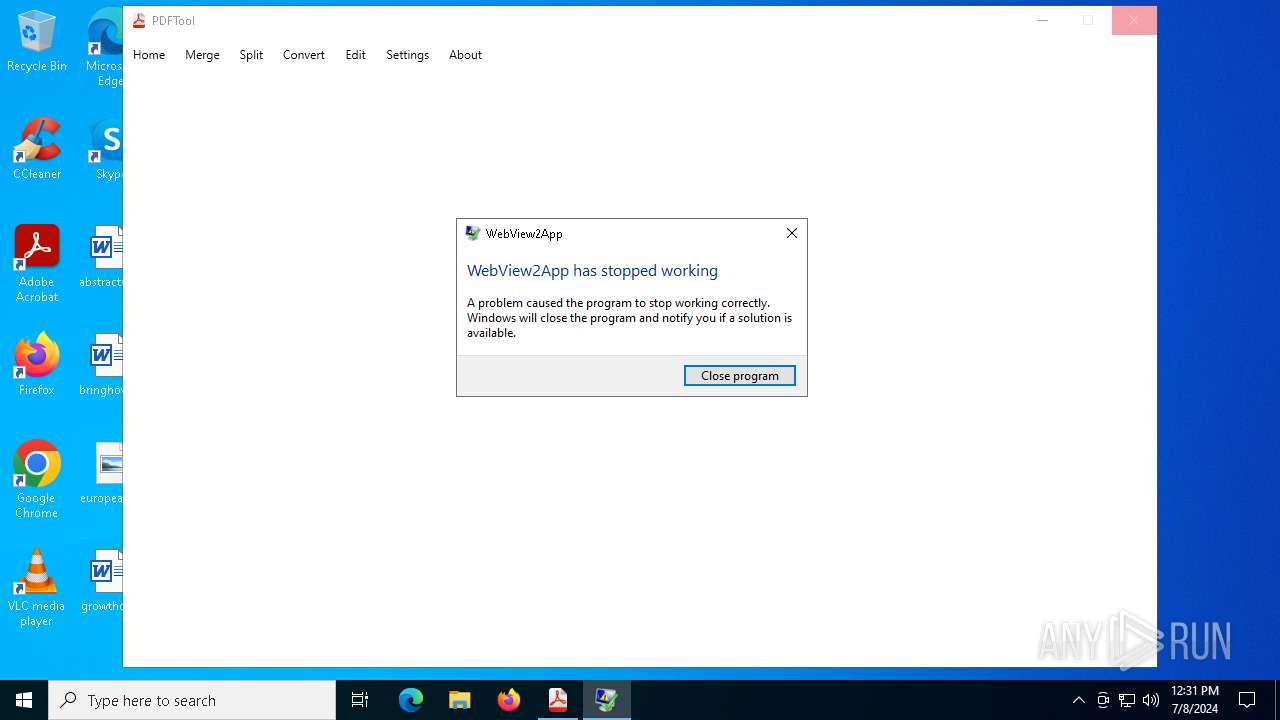
Executes application which crashes
- PDFTool.exe (PID: 6356)
- PDFTool.exe (PID: 7164)
- PDFTool.exe (PID: 5624)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6044)
- powershell.exe (PID: 6952)
- powershell.exe (PID: 1764)
Reads the computer name
- msiexec.exe (PID: 6936)
- msiexec.exe (PID: 7020)
- msiexec.exe (PID: 7068)
- PDFTool.exe (PID: 7164)
- PDFTool.exe (PID: 6356)
- PDFTool.exe (PID: 5624)
Checks proxy server information
- msiexec.exe (PID: 6044)
- powershell.exe (PID: 6952)
- msiexec.exe (PID: 6936)
- powershell.exe (PID: 1764)
- WerFault.exe (PID: 1132)
- WerFault.exe (PID: 2568)
- WerFault.exe (PID: 6928)
Creates files or folders in the user directory
- msiexec.exe (PID: 6044)
- msiexec.exe (PID: 7020)
- msiexec.exe (PID: 6936)
- WerFault.exe (PID: 2568)
- WerFault.exe (PID: 1132)
- WerFault.exe (PID: 6928)
Checks supported languages
- msiexec.exe (PID: 7020)
- msiexec.exe (PID: 7068)
- PDFTool.exe (PID: 6356)
- PDFTool.exe (PID: 7164)
- msiexec.exe (PID: 6936)
- PDFTool.exe (PID: 5624)
Reads the software policy settings
- msiexec.exe (PID: 6044)
- msiexec.exe (PID: 7020)
- powershell.exe (PID: 6952)
- powershell.exe (PID: 1764)
- msiexec.exe (PID: 6936)
- WerFault.exe (PID: 1132)
- WerFault.exe (PID: 2568)
- WerFault.exe (PID: 6928)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6044)
- msiexec.exe (PID: 7020)
- msiexec.exe (PID: 6936)
Reads Environment values
- msiexec.exe (PID: 7068)
- msiexec.exe (PID: 6936)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7020)
- msiexec.exe (PID: 6936)
- PDFTool.exe (PID: 6356)
- PDFTool.exe (PID: 7164)
- PDFTool.exe (PID: 5624)
Create files in a temporary directory
- msiexec.exe (PID: 6936)
- powershell.exe (PID: 6952)
- powershell.exe (PID: 1764)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6952)
- powershell.exe (PID: 1764)
Disables trace logs
- powershell.exe (PID: 6952)
- powershell.exe (PID: 1764)
Creates a software uninstall entry
- msiexec.exe (PID: 7020)
Process checks computer location settings
- msiexec.exe (PID: 7068)
Manual execution by a user
- PDFTool.exe (PID: 5624)
- PDFTool.exe (PID: 7164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {031EEC89-8030-412F-8ECA-FA0060F08B61} |
| Words: | 10 |
| Subject: | PDFTool |
| Author: | PDFTool |
| LastModifiedBy: | - |
| Software: | PDFTool |
| Template: | ;1033,1046,3082,1055 |
| Comments: | PDFTool 3.2.1233.0 |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2024:06:11 00:43:40 |
| ModifyDate: | 2024:06:11 00:43:40 |
| LastPrinted: | 2024:06:11 00:43:40 |
| Pages: | 450 |
| Characters: | 63 |
Total processes
155
Monitored processes
17
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1132 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6356 -s 1776 | C:\Windows\SysWOW64\WerFault.exe | PDFTool.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\PDFTool\pssC407.ps1" -propFile "C:\Users\admin\AppData\Local\PDFTool\msiC3F5.txt" -scriptFile "C:\Users\admin\AppData\Local\PDFTool\scrC3F6.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\PDFTool\scrC3F7.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2568 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7164 -s 1752 | C:\Windows\SysWOW64\WerFault.exe | PDFTool.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5624 | "C:\Users\admin\AppData\Local\PDFTool\PDFTool.exe" | C:\Users\admin\AppData\Local\PDFTool\PDFTool.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WebView2App Exit code: 3762504530 Version: 3.2.1233.0 Modules
| |||||||||||||||
| 6044 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\PDFTool-v3.2.1233.0_50146512.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6356 | "C:\Users\admin\AppData\Local\PDFTool\PDFTool.exe" /register | C:\Users\admin\AppData\Local\PDFTool\PDFTool.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WebView2App Exit code: 3762504530 Version: 3.2.1233.0 Modules
| |||||||||||||||
| 6528 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
49 890
Read events
49 529
Write events
338
Delete events
23
Modification events
| (PID) Process: | (7020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000000039E39932D1DA016C1B000008000000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000000039E39932D1DA016C1B000008000000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000002FC32A9A32D1DA016C1B000008000000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000002FC32A9A32D1DA016C1B000008000000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000F0262D9A32D1DA016C1B000008000000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000067F0319A32D1DA016C1B000008000000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (7020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000007879B79A32D1DA016C1B000008000000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000076DCB99A32D1DA016C1B000090140000E80300000100000000000000000000002FABBA91C45EDD40BC7A581D42F7C99000000000000000000000000000000000 | |||
| (PID) Process: | (5240) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000001BEFBE9A32D1DA0178140000900A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
30
Suspicious files
44
Text files
32
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7020 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7020 | msiexec.exe | C:\WINDOWS\Installer\1d6e3d.msi | — | |
MD5:— | SHA256:— | |||
| 6936 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msi715A.txt | — | |
MD5:— | SHA256:— | |||
| 6936 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scr715B.ps1 | — | |
MD5:— | SHA256:— | |||
| 6936 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scr715C.txt | — | |
MD5:— | SHA256:— | |||
| 6936 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss716D.ps1 | — | |
MD5:— | SHA256:— | |||
| 6044 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI840.tmp | executable | |
MD5:D0C9613582605F3793FDAD7279DE428B | SHA256:8BD84F1156EBDFA44AFAAC8A4579BA56A8C7513E3D51E00822167EA144923726 | |||
| 6044 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\357F04AD41BCF5FE18FCB69F60C6680F_4B24743B8F91CE797D24B8FCFCA3C262 | binary | |
MD5:2D89C64721E32118DC8A086172A4BB23 | SHA256:6A439D09A7F3B3BA1C0B707CED9C435E6759FAAA1B596C137E0BAF1854D38F30 | |||
| 6044 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:47F17DDBF05C7709A1BBC05FC0B62551 | SHA256:030043B77B2245A95808435EF53EA8F74D601278D8B5FA880C0743300AEB1B24 | |||
| 6044 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\357F04AD41BCF5FE18FCB69F60C6680F_4B24743B8F91CE797D24B8FCFCA3C262 | binary | |
MD5:AD7EE1277F562DC247A85BAA9B5E9A66 | SHA256:1B384406E036B668E2483F1A67AC0A2EFD61792B9B4450422747484507F0F93F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
75
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6044 | msiexec.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | unknown |
4632 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
6044 | msiexec.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDEXkmCboMU2WPdtTtg%3D%3D | unknown | — | — | unknown |
6952 | powershell.exe | POST | 200 | 18.173.206.161:80 | http://d25xn4y1w1xf3s.cloudfront.net/ | unknown | — | — | unknown |
6308 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
6936 | msiexec.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
4720 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6308 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1764 | powershell.exe | POST | 200 | 18.173.206.161:80 | http://d25xn4y1w1xf3s.cloudfront.net/ | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4656 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4632 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6044 | msiexec.exe | 146.75.122.133:80 | ocsp.globalsign.com | FASTLY | US | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1060 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 52.111.243.30:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4632 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3776 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.globalsign.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
d25xn4y1w1xf3s.cloudfront.net |
| unknown |
dn0diw4x4ljz4.cloudfront.net |
| unknown |
Threats
Process | Message |
|---|---|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|