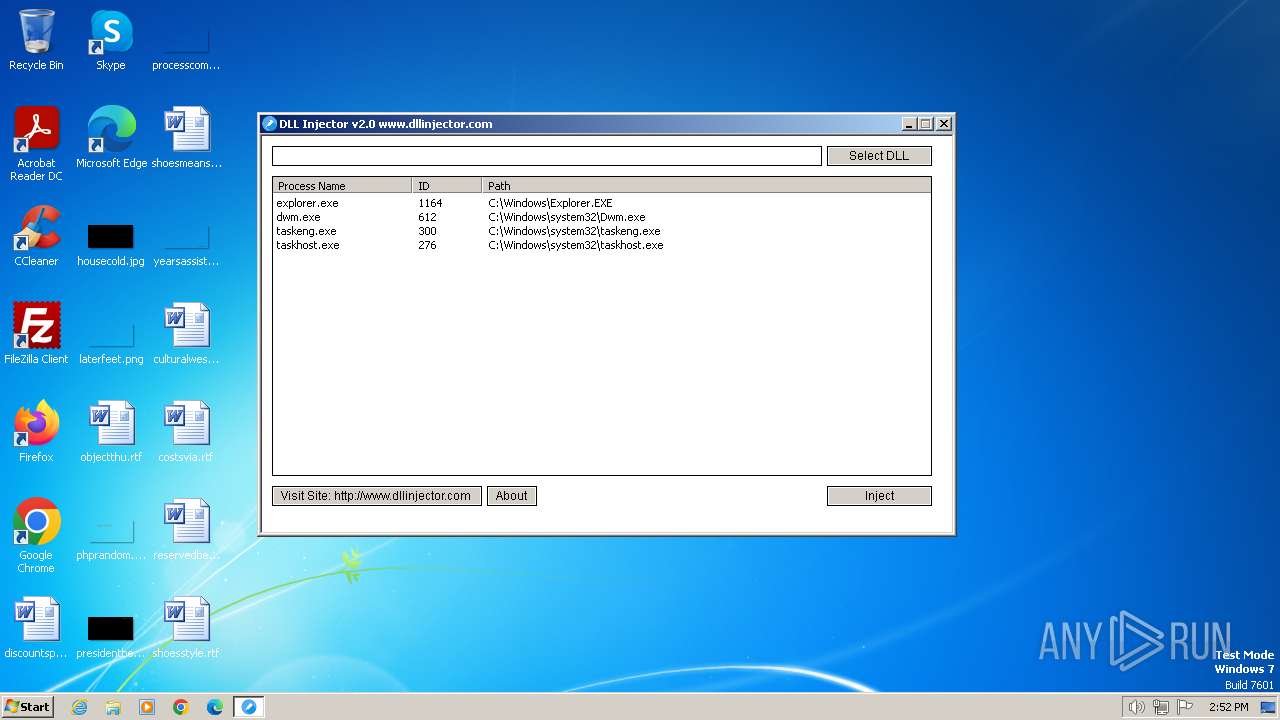
| File name: | DLLInjector v2.exe |
| Full analysis: | https://app.any.run/tasks/d908fb34-eca1-47fc-b385-967321aa1f73 |
| Verdict: | Malicious activity |
| Analysis date: | April 20, 2024, 13:52:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0A5A1030BEBA8CBA4F283A0636231EE1 |
| SHA1: | EFCD77F4FEA4D5CFEC707F9EE936E027B92BB696 |
| SHA256: | 0DB7DDDD89FC145AB250C69C543A0B0CCC5BCE53D017F2FAF63D9A115A011D26 |
| SSDEEP: | 12288:x+tVsdFFKO0aEDNlLq4pmiv6sZZ1IXLcyc57iSCu6A9zH6uQ:30aEDNZq4pmiysH+XkiSCuv9zH6D |
MALICIOUS
Drops the executable file immediately after the start
- DLLInjector v2.exe (PID: 3768)
SUSPICIOUS
Reads the Internet Settings
- DLLInjector v2.exe (PID: 3768)
Reads security settings of Internet Explorer
- DLLInjector v2.exe (PID: 3768)
Checks Windows Trust Settings
- DLLInjector v2.exe (PID: 3768)
Reads settings of System Certificates
- DLLInjector v2.exe (PID: 3768)
INFO
Checks proxy server information
- DLLInjector v2.exe (PID: 3768)
Checks supported languages
- DLLInjector v2.exe (PID: 3768)
Reads the computer name
- DLLInjector v2.exe (PID: 3768)
Reads the machine GUID from the registry
- DLLInjector v2.exe (PID: 3768)
Creates files or folders in the user directory
- DLLInjector v2.exe (PID: 3768)
Create files in a temporary directory
- DLLInjector v2.exe (PID: 3768)
Reads the software policy settings
- DLLInjector v2.exe (PID: 3768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:12:05 16:41:44+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 441344 |
| InitializedDataSize: | 208896 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x34aff |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Dutch |
| CharacterSet: | Unicode |
| CompanyName: | AN Soft |
| FileDescription: | DLL Injector |
| FileVersion: | 2.0.0.0 |
| InternalName: | DLL Injector |
| LegalCopyright: | Copyright (C) 2017 |
| OriginalFileName: | DLLInjector.exe |
| ProductName: | DLL Injector |
| ProductVersion: | 2.0.0.0 |
Total processes
35
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3768 | "C:\Users\admin\AppData\Local\Temp\DLLInjector v2.exe" | C:\Users\admin\AppData\Local\Temp\DLLInjector v2.exe | explorer.exe | ||||||||||||
User: admin Company: AN Soft Integrity Level: MEDIUM Description: DLL Injector Version: 2.0.0.0 Modules
| |||||||||||||||
Total events
5 554
Read events
5 514
Write events
34
Delete events
6
Modification events
| (PID) Process: | (3768) DLLInjector v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3768) DLLInjector v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3768) DLLInjector v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3768) DLLInjector v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3768) DLLInjector v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3768) DLLInjector v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (3768) DLLInjector v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (3768) DLLInjector v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (3768) DLLInjector v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (3768) DLLInjector v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3768 | DLLInjector v2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | — | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
| 3768 | DLLInjector v2.exe | C:\Users\admin\AppData\Roaming\dll 2.0\log.txt | binary | |
MD5:336D5EBC5436534E61D16E63DDFCA327 | SHA256:— | |||
| 3768 | DLLInjector v2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:E9FC3304ADE050D2F42F0B5ADF0ACD92 | SHA256:76B363516D72A2B1FF930D4B7BF23C10510F32E39FB58D13A96F09E1C6F2912A | |||
| 3768 | DLLInjector v2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:F4968C0CCB9B834766F0D01F6FA1EA91 | SHA256:2FB2096765D3989D2660C49E09900CBFE51F395F47790C18C5525789D1000C9B | |||
| 3768 | DLLInjector v2.exe | C:\Users\admin\AppData\Local\Temp\CabEE92.tmp | — | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
| 3768 | DLLInjector v2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1B1495DD322A24490E2BF2FAABAE1C61 | binary | |
MD5:EFEEA575BB28566B18B45EA835554AC3 | SHA256:FCA842FAAACF6BD3ED6025284113846F4BFC48A9E33FC5867AD212CC911FF179 | |||
| 3768 | DLLInjector v2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\readweb[1].htm | html | |
MD5:0104C301C5E02BD6148B8703D19B3A73 | SHA256:446A6087825FA73EADB045E5A2E9E2ADF7DF241B571228187728191D961DDA1F | |||
| 3768 | DLLInjector v2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:BF619C3F14786393C13BA698F9DDEC61 | SHA256:3498D7C6CD8A199F505DAF5ABADA892330C767D491F2DA97CC0ACEB6F4869FF0 | |||
| 3768 | DLLInjector v2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3768 | DLLInjector v2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\readweb[1].htm | binary | |
MD5:336D5EBC5436534E61D16E63DDFCA327 | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
8
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3768 | DLLInjector v2.exe | GET | 301 | 188.114.96.3:80 | http://www.dllinjector.com/readweb.php?version=2.0 | unknown | — | — | unknown |
3768 | DLLInjector v2.exe | GET | 200 | 23.35.209.170:80 | http://x2.c.lencr.org/ | unknown | — | — | unknown |
1080 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0351668c06fee42b | unknown | — | — | unknown |
3768 | DLLInjector v2.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ba8b3774ef5e1024 | unknown | — | — | unknown |
3768 | DLLInjector v2.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0eaddb710dec913c | unknown | — | — | unknown |
3768 | DLLInjector v2.exe | GET | 200 | 23.35.209.170:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
3768 | DLLInjector v2.exe | 188.114.96.3:80 | www.dllinjector.com | CLOUDFLARENET | NL | unknown |
3768 | DLLInjector v2.exe | 188.114.96.3:443 | www.dllinjector.com | CLOUDFLARENET | NL | unknown |
3768 | DLLInjector v2.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3768 | DLLInjector v2.exe | 23.35.209.170:80 | x1.c.lencr.org | AKAMAI-AS | CA | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dllinjector.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
Threats
Process | Message |
|---|---|
DLLInjector v2.exe | Created folder |