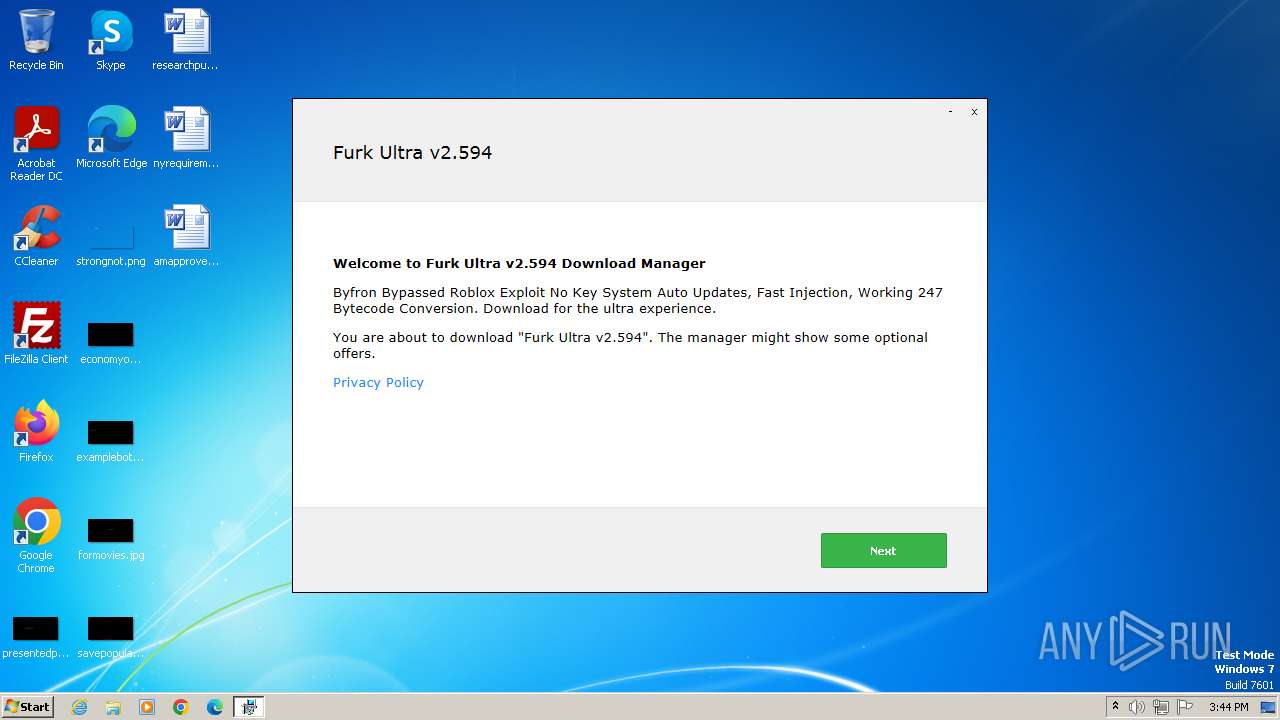
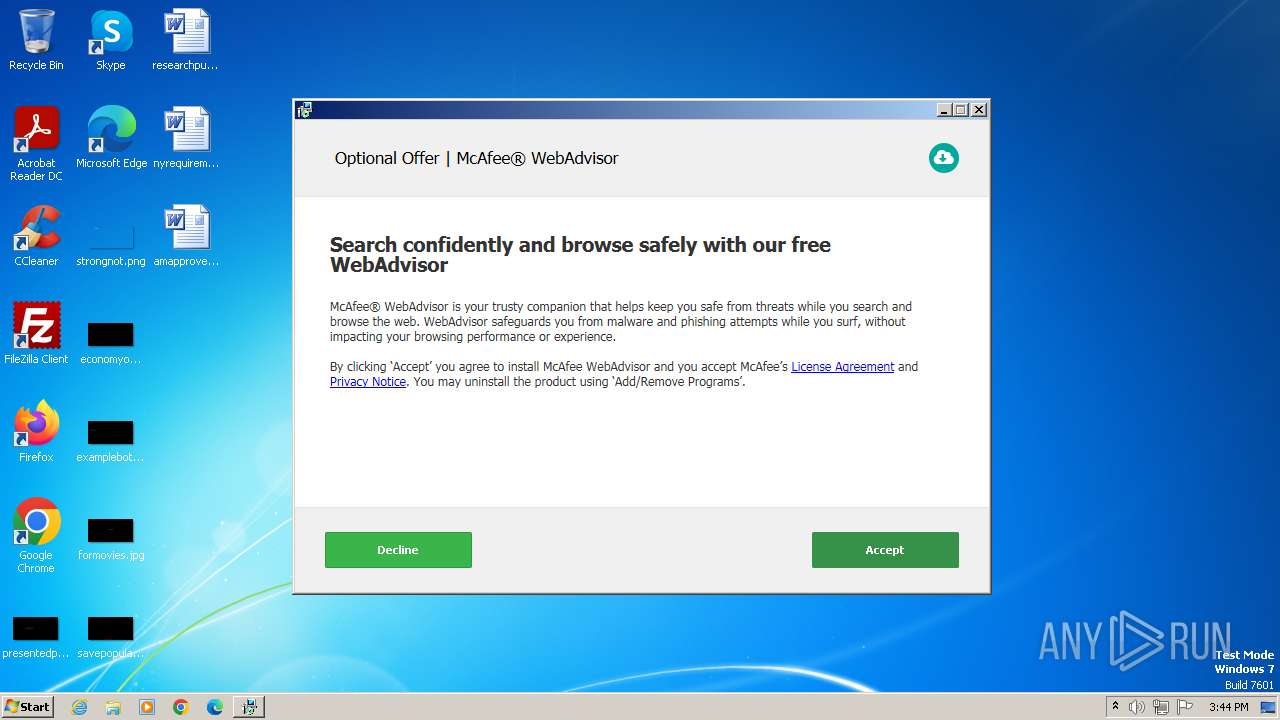
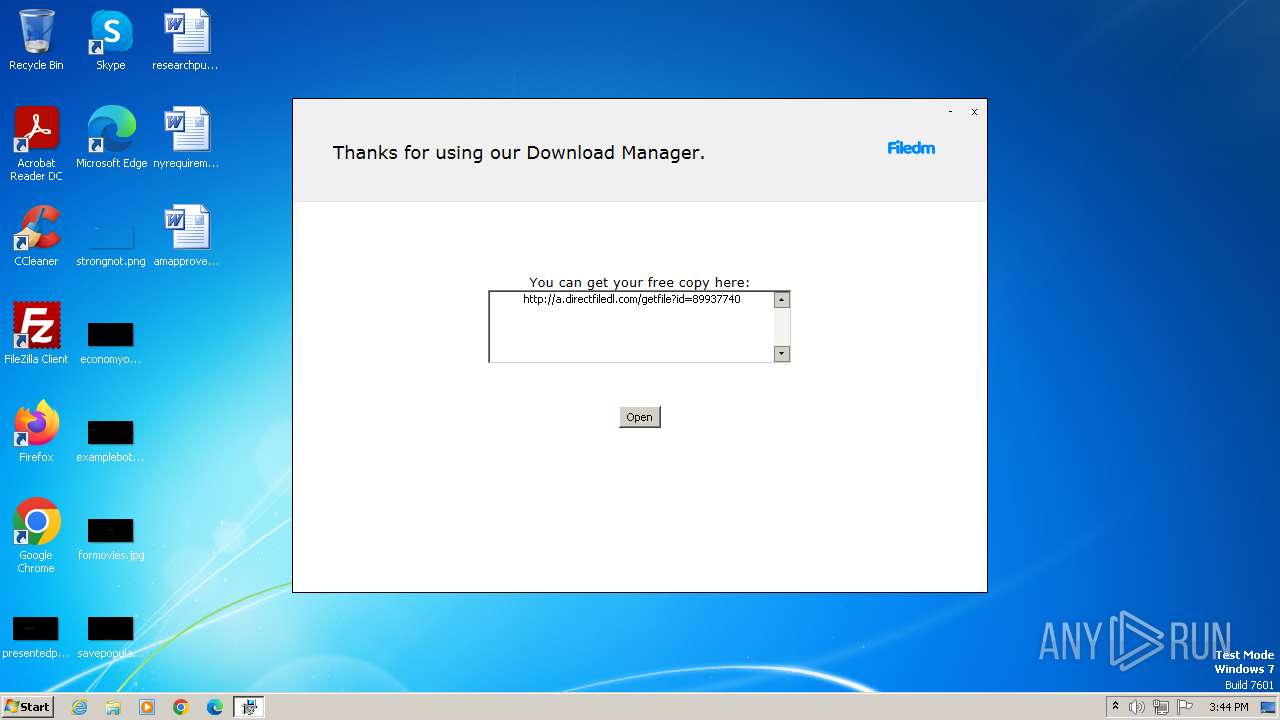
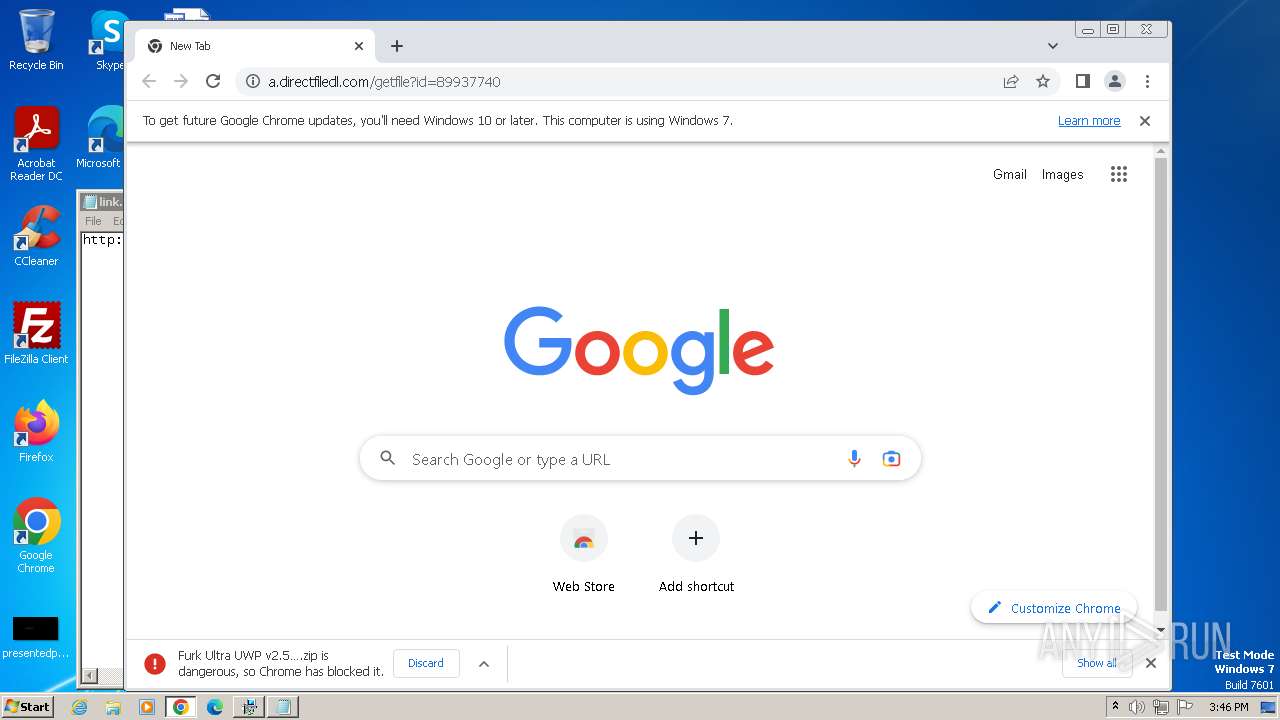
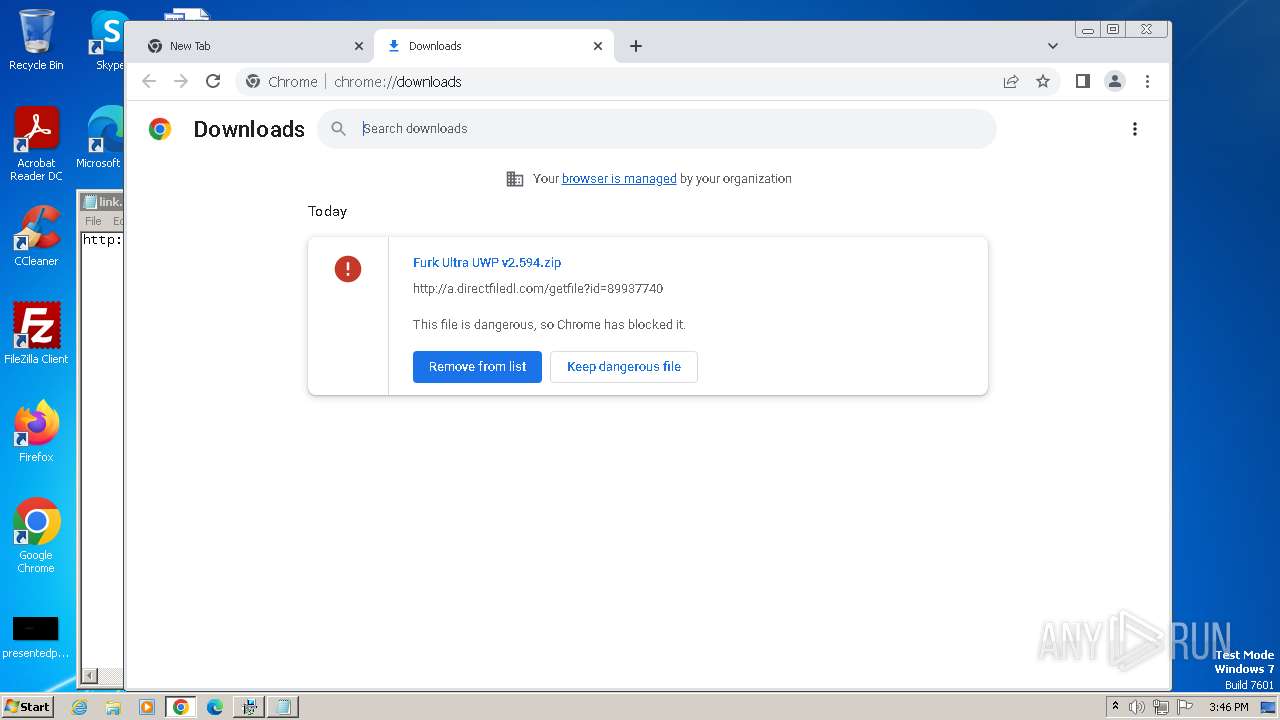
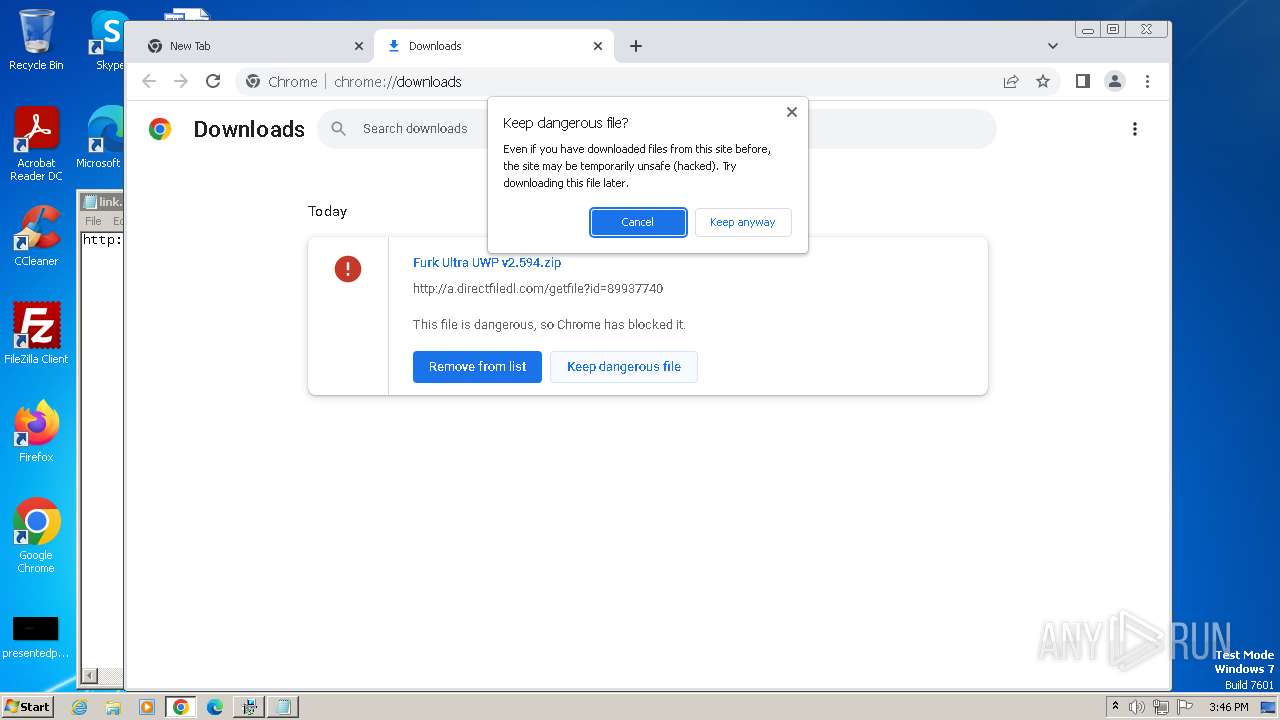
| File name: | Furk Ultra v2.594_89937740.exe |
| Full analysis: | https://app.any.run/tasks/d3d12c2a-08eb-4454-9bae-a46c128a0a98 |
| Verdict: | Malicious activity |
| Analysis date: | October 21, 2023, 14:43:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | ADD9D682DB94CBB7917E49FE0A654115 |
| SHA1: | 0EFB3270EFFCF3D776935E6F76AC040EAF529BC0 |
| SHA256: | 0DB6C42DCE6E6D5DF074FF2EA90A99036CB06EE886270370B39F6E6283CE2B9B |
| SSDEEP: | 98304:xnHYVCPMKWzFaABrApQ04by+l1y69vZNI0rG0I5mln9MiYC846WxC3jwPz6jk+p1:LyX2iB |
MALICIOUS
Application was dropped or rewritten from another process
- setup89937740.exe (PID: 1648)
- setup89937740.exe (PID: 1836)
- OfferInstaller.exe (PID: 2880)
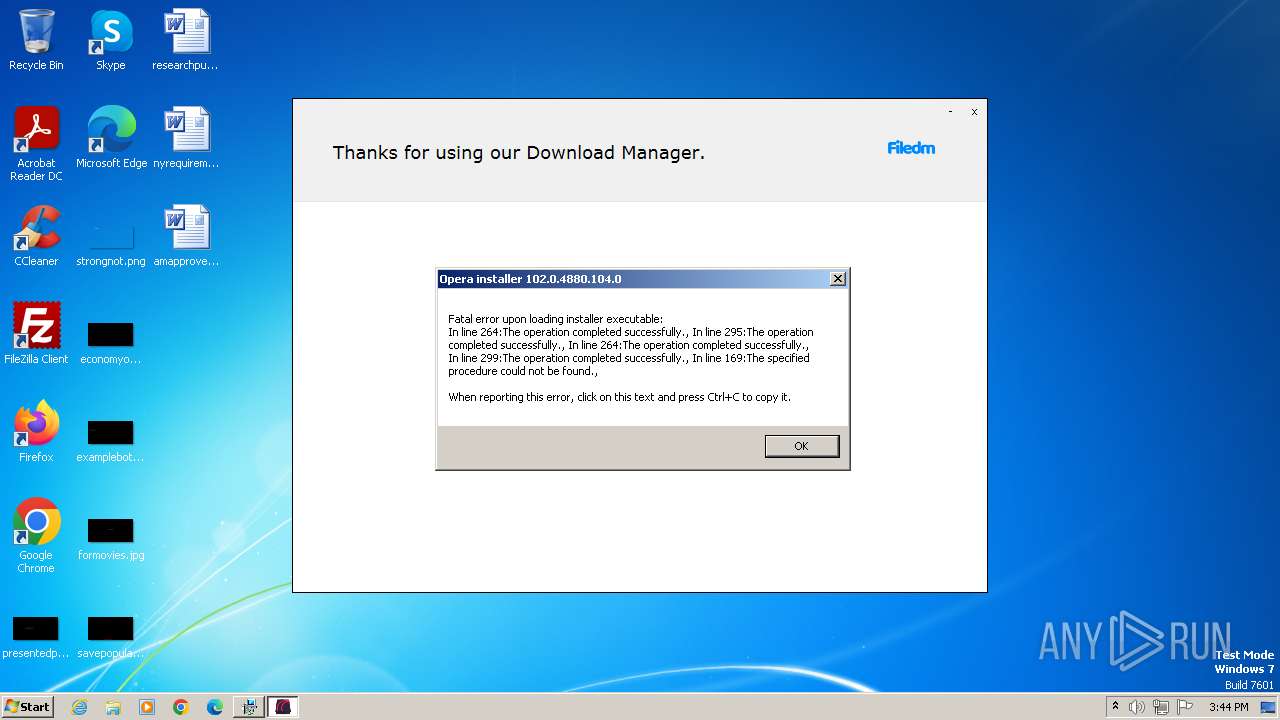
- OperaGX.exe (PID: 1024)
- FurkUltra.exe (PID: 2852)
Drops the executable file immediately after the start
- Furk Ultra v2.594_89937740.exe (PID: 1740)
- setup89937740.exe (PID: 1648)
- OperaGX.exe (PID: 1024)
Actions looks like stealing of personal data
- setup89937740.exe (PID: 1648)
- OfferInstaller.exe (PID: 2880)
Loads dropped or rewritten executable
- OfferInstaller.exe (PID: 2880)
- setup89937740.exe (PID: 1836)
- setup89937740.exe (PID: 1648)
SUSPICIOUS
Reads the Internet Settings
- setup89937740.exe (PID: 1648)
- Furk Ultra v2.594_89937740.exe (PID: 1740)
- setup89937740.exe (PID: 1836)
- OfferInstaller.exe (PID: 2880)
Reads settings of System Certificates
- Furk Ultra v2.594_89937740.exe (PID: 1740)
- setup89937740.exe (PID: 1648)
- OfferInstaller.exe (PID: 2880)
The process drops C-runtime libraries
- setup89937740.exe (PID: 1648)
Process drops legitimate windows executable
- setup89937740.exe (PID: 1648)
- chrome.exe (PID: 1868)
- WinRAR.exe (PID: 2628)
Checks Windows Trust Settings
- Furk Ultra v2.594_89937740.exe (PID: 1740)
- setup89937740.exe (PID: 1648)
Reads the Windows owner or organization settings
- setup89937740.exe (PID: 1648)
- OfferInstaller.exe (PID: 2880)
Reads security settings of Internet Explorer
- setup89937740.exe (PID: 1648)
- Furk Ultra v2.594_89937740.exe (PID: 1740)
Searches for installed software
- setup89937740.exe (PID: 1648)
Adds/modifies Windows certificates
- Furk Ultra v2.594_89937740.exe (PID: 1740)
Starts CMD.EXE for commands execution
- setup89937740.exe (PID: 1648)
- OfferInstaller.exe (PID: 2880)
Executing commands from a ".bat" file
- setup89937740.exe (PID: 1648)
- OfferInstaller.exe (PID: 2880)
Get information on the list of running processes
- cmd.exe (PID: 3420)
- cmd.exe (PID: 3800)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3420)
- cmd.exe (PID: 3800)
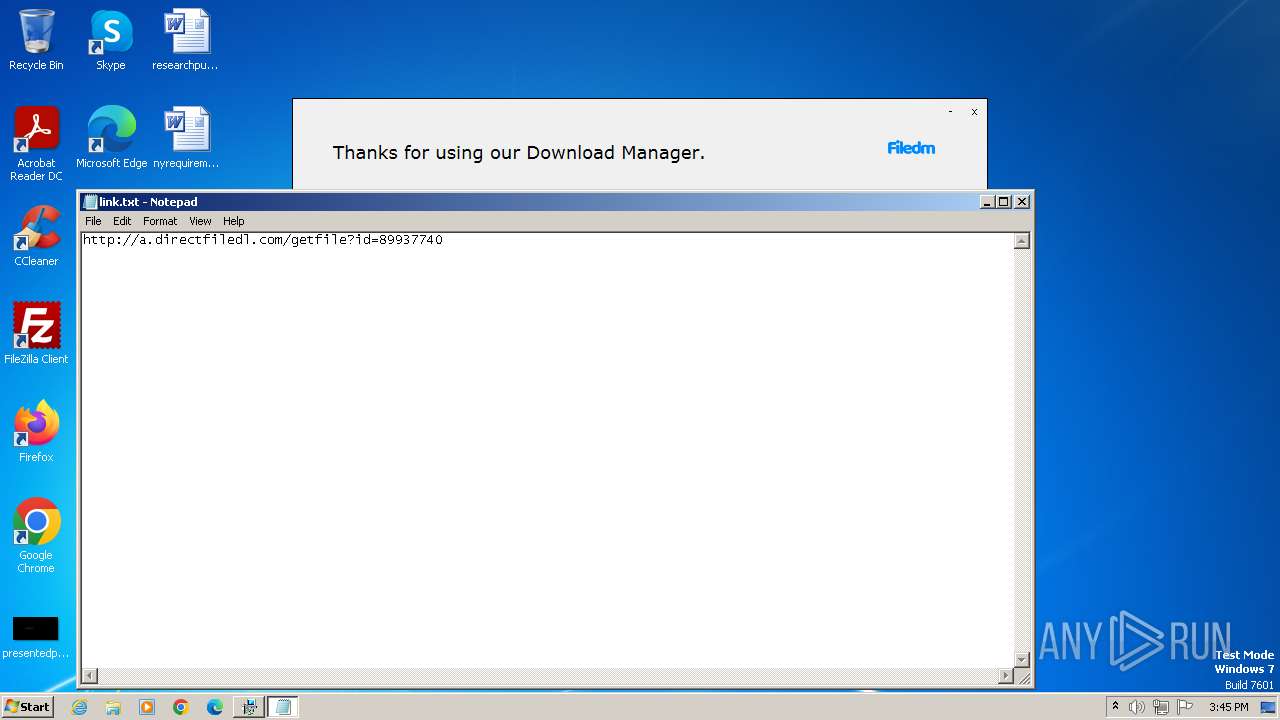
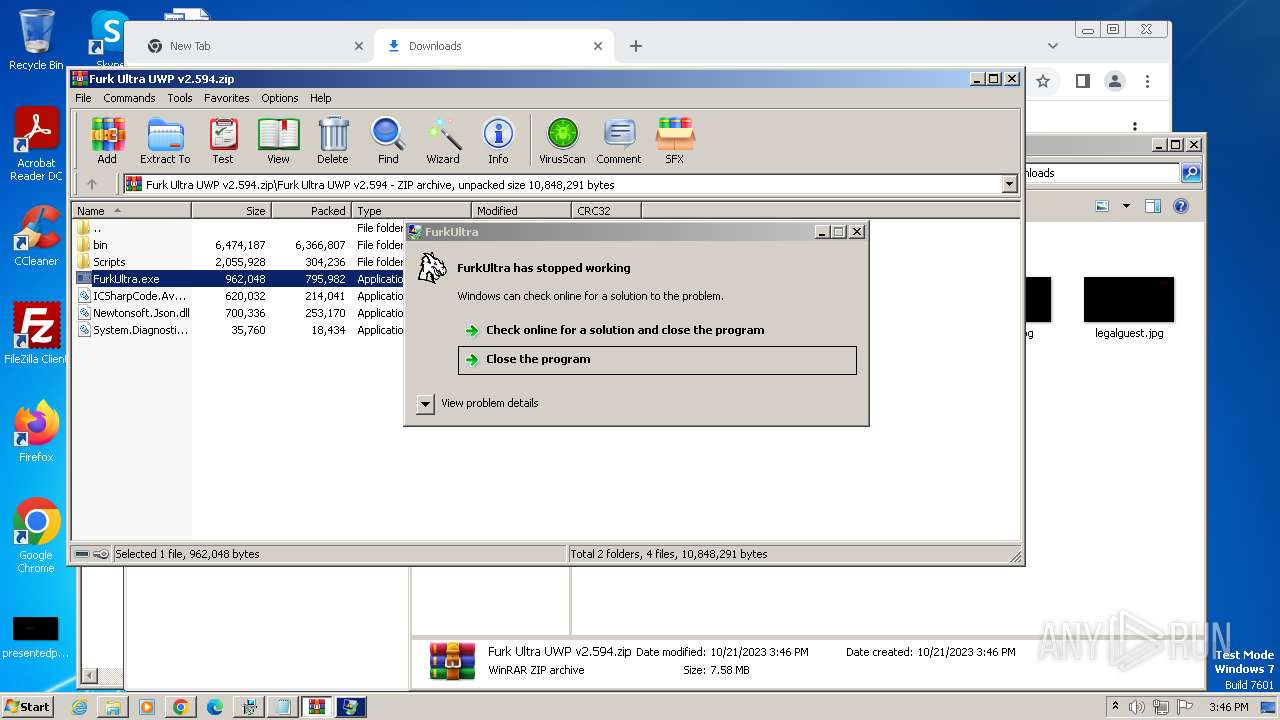
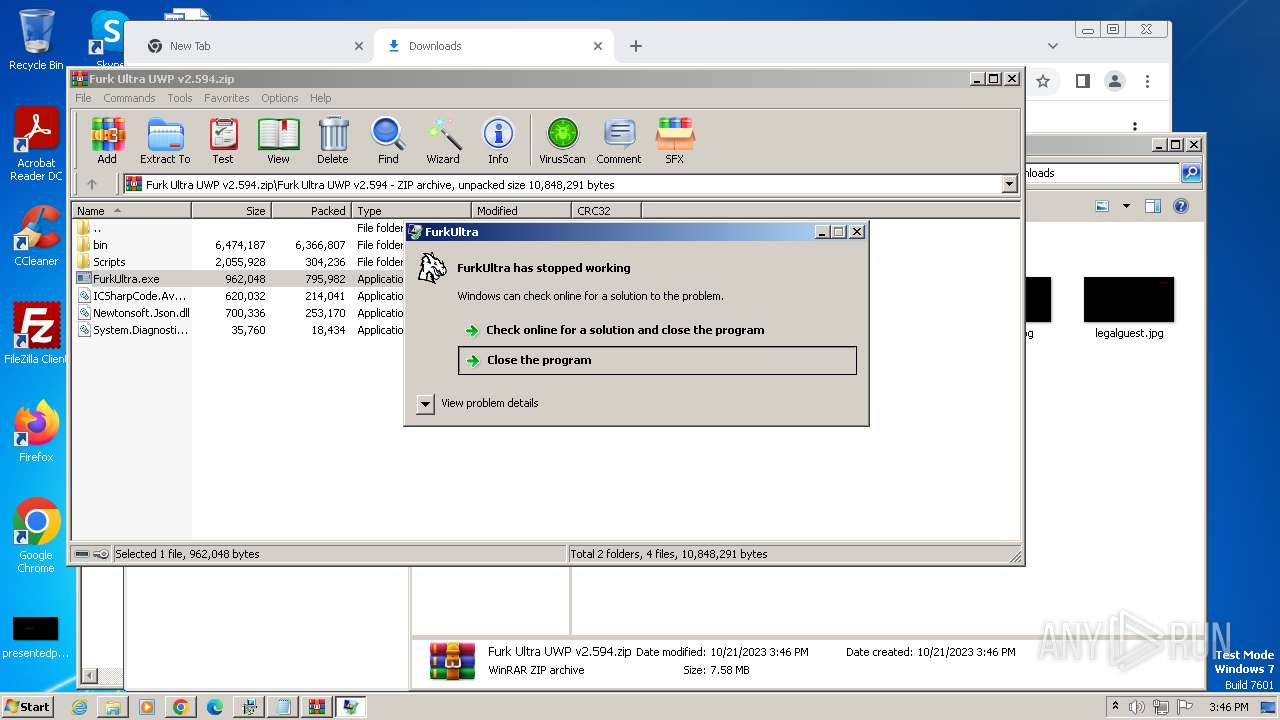
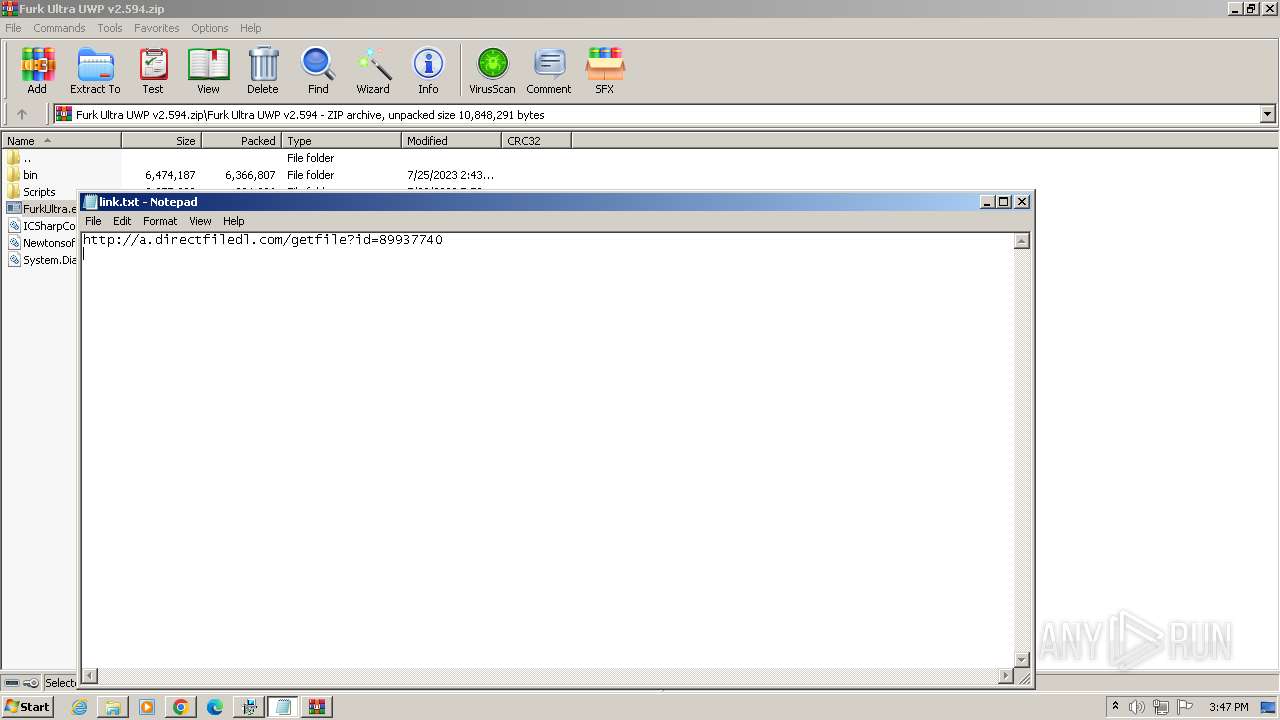
Start notepad (likely ransomware note)
- Furk Ultra v2.594_89937740.exe (PID: 1740)
INFO
Checks supported languages
- Furk Ultra v2.594_89937740.exe (PID: 1740)
- setup89937740.exe (PID: 1648)
- setup89937740.exe (PID: 1836)
- OfferInstaller.exe (PID: 2880)
- OperaGX.exe (PID: 1024)
- FurkUltra.exe (PID: 2852)
Reads the machine GUID from the registry
- Furk Ultra v2.594_89937740.exe (PID: 1740)
- setup89937740.exe (PID: 1648)
- OfferInstaller.exe (PID: 2880)
- setup89937740.exe (PID: 1836)
- FurkUltra.exe (PID: 2852)
Creates files or folders in the user directory
- Furk Ultra v2.594_89937740.exe (PID: 1740)
- setup89937740.exe (PID: 1648)
- OperaGX.exe (PID: 1024)
- OfferInstaller.exe (PID: 2880)
Create files in a temporary directory
- setup89937740.exe (PID: 1648)
- Furk Ultra v2.594_89937740.exe (PID: 1740)
- setup89937740.exe (PID: 1836)
- OfferInstaller.exe (PID: 2880)
- OperaGX.exe (PID: 1024)
Reads Environment values
- setup89937740.exe (PID: 1648)
- OfferInstaller.exe (PID: 2880)
Checks proxy server information
- Furk Ultra v2.594_89937740.exe (PID: 1740)
Reads the computer name
- Furk Ultra v2.594_89937740.exe (PID: 1740)
- setup89937740.exe (PID: 1836)
- OfferInstaller.exe (PID: 2880)
- FurkUltra.exe (PID: 2852)
- setup89937740.exe (PID: 1648)
Reads product name
- setup89937740.exe (PID: 1648)
- OfferInstaller.exe (PID: 2880)
Manual execution by a user
- chrome.exe (PID: 2448)
- WinRAR.exe (PID: 2628)
The process uses the downloaded file
- chrome.exe (PID: 2600)
- chrome.exe (PID: 2064)
- chrome.exe (PID: 444)
- WinRAR.exe (PID: 2628)
- chrome.exe (PID: 3656)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2628)
- chrome.exe (PID: 1868)
Application launched itself
- chrome.exe (PID: 2448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:09 12:14:48+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.22 |
| CodeSize: | 4244480 |
| InitializedDataSize: | 5623808 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3816aa |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Download Manager |
| FileVersion: | 1 |
| InternalName: | Download Manager |
| LegalCopyright: | Download Manager |
| OriginalFileName: | Download Manager |
| ProductName: | Download Manager |
| ProductVersion: | 1 |
Total processes
96
Monitored processes
49
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3892 --field-trial-handle=1120,i,5867323215290942352,14806160184954738593,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3884 --field-trial-handle=1120,i,5867323215290942352,14806160184954738593,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 448 | tasklist /FI "PID eq 2880" /fo csv | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | find /I "2880" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
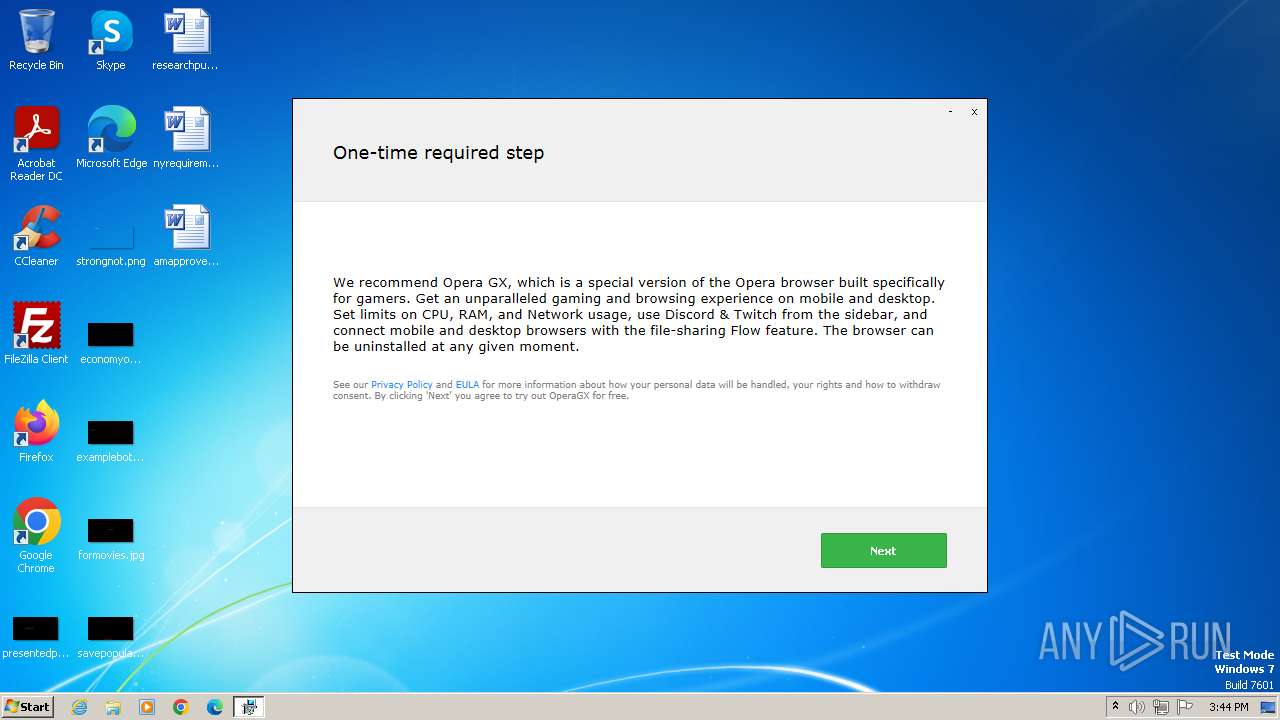
| 1024 | C:\Users\admin\AppData\Local\OperaGX.exe --silent --allusers=0 | C:\Users\admin\AppData\Local\OperaGX.exe | — | Furk Ultra v2.594_89937740.exe | |||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera GX Installer Exit code: 2 Version: 102.0.4880.104 Modules
| |||||||||||||||
| 1124 | timeout 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6bb18b38,0x6bb18b48,0x6bb18b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1248 | timeout 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1408 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\link.txt | C:\Windows\System32\notepad.exe | — | Furk Ultra v2.594_89937740.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3632 --field-trial-handle=1120,i,5867323215290942352,14806160184954738593,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
26 993
Read events
26 760
Write events
232
Delete events
1
Modification events
| (PID) Process: | (1740) Furk Ultra v2.594_89937740.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1740) Furk Ultra v2.594_89937740.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000056010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1740) Furk Ultra v2.594_89937740.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1740) Furk Ultra v2.594_89937740.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1740) Furk Ultra v2.594_89937740.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1740) Furk Ultra v2.594_89937740.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1740) Furk Ultra v2.594_89937740.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1740) Furk Ultra v2.594_89937740.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1740) Furk Ultra v2.594_89937740.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1648) setup89937740.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager |
| Operation: | write | Name: | PendingFileRenameOperations |
Value: \??\C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\ServiceHide.dll | |||
Executable files
35
Suspicious files
112
Text files
73
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1740 | Furk Ultra v2.594_89937740.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:B552995DC23E6C80AADB6B2B2FEBEF08 | SHA256:0A03F2F47BFA8D8EF90501FEDB78246AB7952D0C3AF6017B3EE7126F2CAFF151 | |||
| 1740 | Furk Ultra v2.594_89937740.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:058E86D8602DDC8E298B7F20A9C84350 | SHA256:464E4E508D639C25FCEC9AD61AD5030A7384065BDA9D57094BE9F8D48216DA87 | |||
| 1740 | Furk Ultra v2.594_89937740.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:4DE5EE392D9664DF2CF6E5ED9C46D850 | SHA256:65474CA04C80788ABD7E1E4B435028B7023B54F10862128A820322E6DA7CD395 | |||
| 1740 | Furk Ultra v2.594_89937740.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1740 | Furk Ultra v2.594_89937740.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0D55D68DC09266D5B02DD35BD366A02_4D644F80CF310B2FF24E334E93454439 | binary | |
MD5:47C2835A53872CD9C41C1A1F1552732D | SHA256:36DD6197860358EF95D8C74A2C2A414CEE66784BFD4ED6839943FB0B76E6C578 | |||
| 1740 | Furk Ultra v2.594_89937740.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\service[1].htm | text | |
MD5:8AFAD19C27FF5550895A17BD98BDE331 | SHA256:53961393AB9544FC6A2D4EF6E44CADAA4813E2E736BB90187DF0D569BD99B565 | |||
| 1648 | setup89937740.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\SciterWrapper.dll | executable | |
MD5:105A9E404F7AC841C46380063CC27F50 | SHA256:69FE749457218EC9A765F9AAC74CAF6D4F73084CF5175D3FD1E4F345AF8B3B8B | |||
| 1648 | setup89937740.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\GenericSetup.LastScreen.dll | executable | |
MD5:6E001F8D0EE4F09A6673A9E8168836B6 | SHA256:6A30F9C604C4012D1D2E1BA075213C378AFB1BFCB94276DE7995ED7BBF492859 | |||
| 1648 | setup89937740.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\ServiceHide.dll | executable | |
MD5:72990C7E32EE6C811EA3D2EA64523234 | SHA256:E77E0B4F2762F76A3EAAADF5A3138A35EC06ECE80EDC4B3396DE7A601F8DA1B3 | |||
| 1648 | setup89937740.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\H2OServices.dll | executable | |
MD5:6DF226BDA27D26CE4523B80DBF57A9EA | SHA256:17D737175D50EEE97AC1C77DB415FE25CC3C7A3871B65B93CC3FAD63808A9ABC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
45
DNS requests
47
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | — | — | unknown |
1740 | Furk Ultra v2.594_89937740.exe | GET | 200 | 23.212.210.158:80 | http://x2.c.lencr.org/ | unknown | binary | 300 b | unknown |
1740 | Furk Ultra v2.594_89937740.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/s/gts1d4/fBhj9wRXMMA/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEGMmYrCWCX4LCfKe4VeZo4Q%3D | unknown | binary | 471 b | unknown |
1740 | Furk Ultra v2.594_89937740.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1517bce33054eae9 | unknown | compressed | 4.66 Kb | unknown |
1740 | Furk Ultra v2.594_89937740.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1740 | Furk Ultra v2.594_89937740.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
1740 | Furk Ultra v2.594_89937740.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/s/gts1d4/1vrh9NNoW7c/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICECZq1D8gJj36CpLkn2hSfVA%3D | unknown | binary | 471 b | unknown |
1740 | Furk Ultra v2.594_89937740.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | unknown | binary | 724 b | unknown |
1740 | Furk Ultra v2.594_89937740.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?b9af2ce623240281 | unknown | compressed | 61.6 Kb | unknown |
1740 | Furk Ultra v2.594_89937740.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1740 | Furk Ultra v2.594_89937740.exe | 35.190.60.70:443 | www.dlsft.com | GOOGLE | US | whitelisted |
1740 | Furk Ultra v2.594_89937740.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1740 | Furk Ultra v2.594_89937740.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1648 | setup89937740.exe | 104.17.9.52:443 | flow.lavasoft.com | CLOUDFLARENET | — | shared |
1648 | setup89937740.exe | 104.18.68.73:443 | sos.adaware.com | CLOUDFLARENET | — | unknown |
1740 | Furk Ultra v2.594_89937740.exe | 188.114.97.3:443 | filedm.com | CLOUDFLARENET | NL | unknown |
1740 | Furk Ultra v2.594_89937740.exe | 23.212.210.158:80 | x1.c.lencr.org | AKAMAI-AS | AU | unknown |
1648 | setup89937740.exe | 69.192.161.107:443 | package.avira.com | AKAMAI-AS | DE | unknown |
1648 | setup89937740.exe | 18.245.86.53:443 | download.enigmasoftware.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dlsft.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.google.com |
| whitelisted |
flow.lavasoft.com |
| whitelisted |
sos.adaware.com |
| whitelisted |
dlsft.com |
| unknown |
filedm.com |
| malicious |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
Threats
5 ETPRO signatures available at the full report
Process | Message |
|---|---|
setup89937740.exe | at sciter:init-script.tis
|
setup89937740.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|
setup89937740.exe | Error: File not found - sciterwrapper:console.tis
|
setup89937740.exe | |
setup89937740.exe | |
setup89937740.exe | |
setup89937740.exe | at sciter:init-script.tis
|
setup89937740.exe | Error: File not found - sciterwrapper:console.tis
|
setup89937740.exe | |
setup89937740.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|