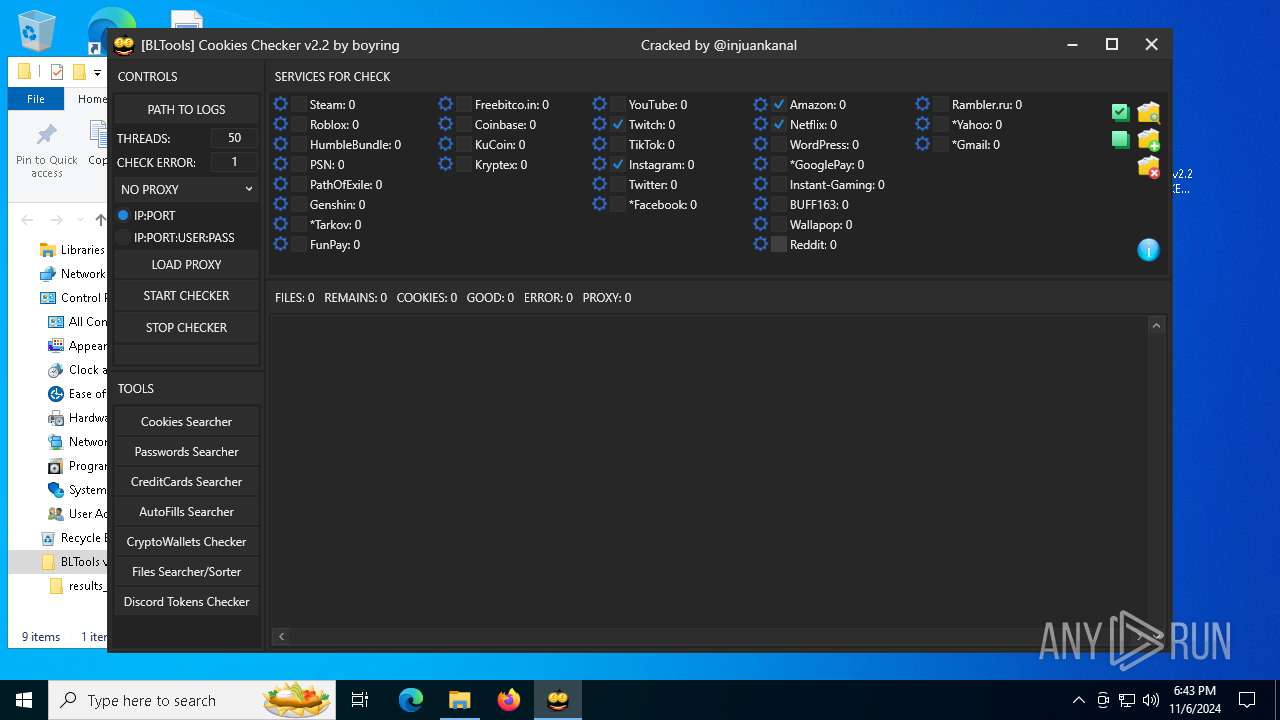
| File name: | BLTools v2.2 [CRACKED BY INJUAN].rar |
| Full analysis: | https://app.any.run/tasks/a0aa6899-d282-43bf-8b11-d3be6bbb6986 |
| Verdict: | Malicious activity |
| Analysis date: | November 06, 2024, 18:42:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C780503429C3389B9049EB08AAEC2FA5 |
| SHA1: | 8A1C8694A1FF23C2773727BE0CC9A027FE8C0D29 |
| SHA256: | 0DAF92DCC7243CB9BF76F7BDB48FA1FD028CF7FEF8B305D26E5EEFFED5E98C8A |
| SSDEEP: | 98304:fYhtVAlKJ/sRiHXnZkjBvYz9CfprfdN7aCS09JIQyFkXk0Ehkjqlvt4VSRmCj/eK:K3gHxNWdHbtzTmK5J |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- BLTools-v2.2.exe (PID: 6260)
Executable content was dropped or overwritten
- BLTools-v2.2.exe (PID: 6260)
Checks for external IP
- svchost.exe (PID: 2172)
- BLTools-v2.2.exe (PID: 7056)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6424)
Manual execution by a user
- BLTools-v2.2.exe (PID: 6260)
- BLTools-v2.2.exe (PID: 5652)
- BLTools-v2.2.exe (PID: 6680)
.NET Reactor protector has been detected
- BLTools-v2.2.exe (PID: 7056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 114615 |
| UncompressedSize: | 367616 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | BLTools v2.2 [CRACKED BY INJUAN]/AlphaFS.dll |
Total processes
141
Monitored processes
10
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1576 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2360 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
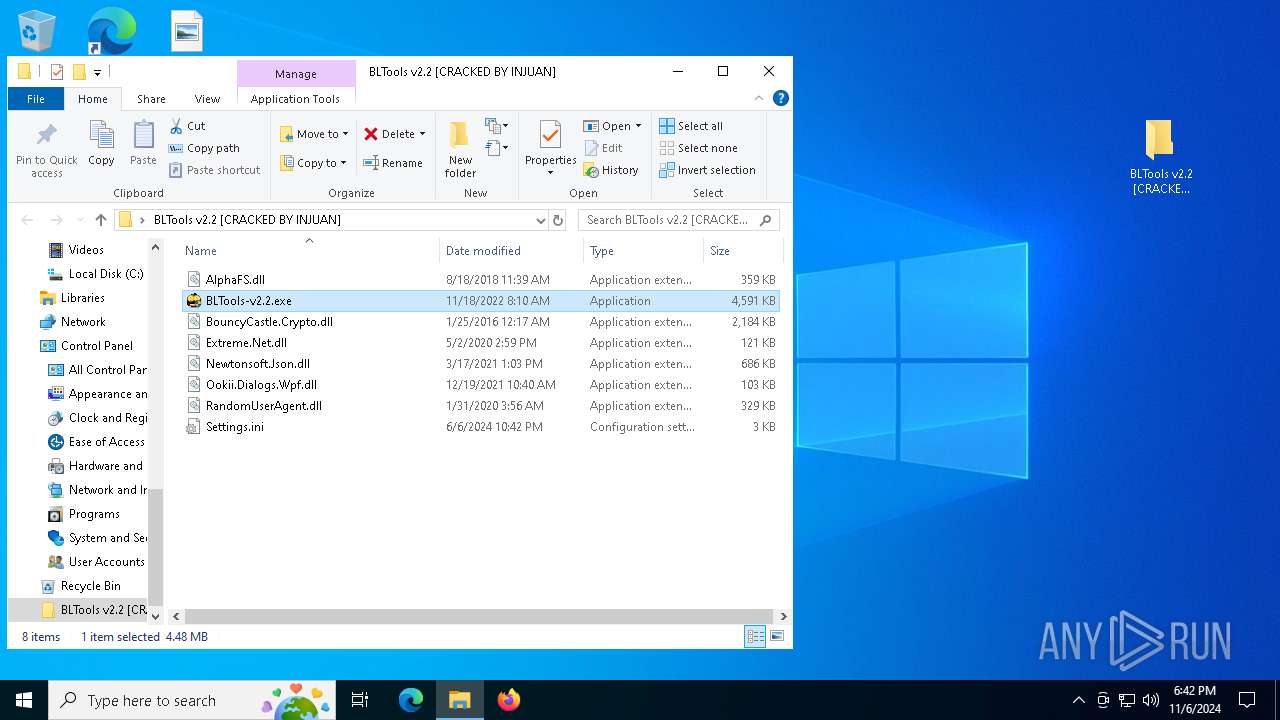
| 5652 | "C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools-v2.2.exe" | C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools-v2.2.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Exit code: 3221226540 Version: 2.2.0.0 Modules
| |||||||||||||||
| 6260 | "C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools-v2.2.exe" | C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools-v2.2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: BLTools Exit code: 0 Version: 2.2.0.0 Modules
| |||||||||||||||
| 6276 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6304 | "C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools v2.2.exe" | C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools v2.2.exe | BLTools-v2.2.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: BLTools Version: 2.2.0.0 Modules
| |||||||||||||||
| 6424 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN].rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6680 | "C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools-v2.2.exe" | C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools-v2.2.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Exit code: 3221226540 Version: 2.2.0.0 Modules
| |||||||||||||||
| 7056 | "C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools-v2.2.exe" | C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools-v2.2.exe | BLTools-v2.2.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: BLTools Exit code: 1 Version: 2.2.0.0 Modules
| |||||||||||||||
Total events
12 780
Read events
12 749
Write events
31
Delete events
0
Modification events
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN].rar | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
9
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6424.36769\BLTools v2.2 [CRACKED BY INJUAN]\BLTools v2.2.exe | executable | |
MD5:31B01CDAEBE52FE31F74CD083A18FB88 | SHA256:120B0DC2FEC8495FD608890CEE10CF68E8CE2B97561BB044C2CE28990F017716 | |||
| 6424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6424.36769\BLTools v2.2 [CRACKED BY INJUAN]\AlphaFS.dll | executable | |
MD5:F2F6F6798D306D6D7DF4267434B5C5F9 | SHA256:837F2CEAB6BBD9BC4BF076F1CB90B3158191888C3055DD2B78A1E23F1C3AAFDD | |||
| 6424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6424.36769\BLTools v2.2 [CRACKED BY INJUAN]\BLTools-v2.2.exe | executable | |
MD5:EF5EE302110F10993A991FD9A2350594 | SHA256:F368811F3BB071D6EE006731FE819A0B7D8CD7ED5FD8110AEB5CB0DA22A3A3A7 | |||
| 6424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6424.36769\BLTools v2.2 [CRACKED BY INJUAN]\Ookii.Dialogs.Wpf.dll | executable | |
MD5:932EBB3F9E7113071C6A17818342B7CC | SHA256:285AA8225732DDBCF211B1158BD6CFF8BF3ACBEEAB69617F4BE85862B7105AB5 | |||
| 6424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6424.36769\BLTools v2.2 [CRACKED BY INJUAN]\Settings.ini | text | |
MD5:D51D2C45B7DBC4686B46466761697496 | SHA256:253FED99A9FF0C33362D740DD7DFAE00F83D583212977F6E6103DAC3BB7788F8 | |||
| 6260 | BLTools-v2.2.exe | C:\Users\admin\Desktop\BLTools v2.2 [CRACKED BY INJUAN]\BLTools v2.2.exe | executable | |
MD5:31B01CDAEBE52FE31F74CD083A18FB88 | SHA256:120B0DC2FEC8495FD608890CEE10CF68E8CE2B97561BB044C2CE28990F017716 | |||
| 6424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6424.36769\BLTools v2.2 [CRACKED BY INJUAN]\Extreme.Net.dll | executable | |
MD5:F79F0E3A0361CAC000E2D3553753CD68 | SHA256:8A6518AB7419FBEC3AC9875BAA3AFB410AD1398C7AA622A09CD9084EC6CADFCD | |||
| 6424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6424.36769\BLTools v2.2 [CRACKED BY INJUAN]\BouncyCastle.Crypto.dll | executable | |
MD5:3CF6BF0E0A27F3665EDD6362D137E4CC | SHA256:1985B85BB44BE6C6EAF35E02EF11E23A890E809B8EC2E53210A4AD5A85B26C70 | |||
| 6304 | BLTools v2.2.exe | C:\Windows\System32\drivers\etc\hosts | text | |
MD5:85005F4D1BE0DFE6A3707DBCCFA635EA | SHA256:1C8E2765DECC6D1DB6FFA250BAF9926DEB4895ABC1A013233930CE7D9637AB5B | |||
| 6424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6424.36769\BLTools v2.2 [CRACKED BY INJUAN]\Newtonsoft.Json.dll | executable | |
MD5:081D9558BBB7ADCE142DA153B2D5577A | SHA256:B624949DF8B0E3A6153FDFB730A7C6F4990B6592EE0D922E1788433D276610F3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
45
DNS requests
29
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6180 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4088 | SIHClient.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4088 | SIHClient.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5984 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
6944 | svchost.exe | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | whitelisted |
6304 | BLTools v2.2.exe | 193.109.246.157:443 | bltools.moy.su | Compubyte Limited | RU | suspicious |
944 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
944 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
bltools.moy.su |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7056 | BLTools-v2.2.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (iplogger .com in TLS SNI) |
2172 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (iplogger .com in DNS lookup) |
1 ETPRO signatures available at the full report