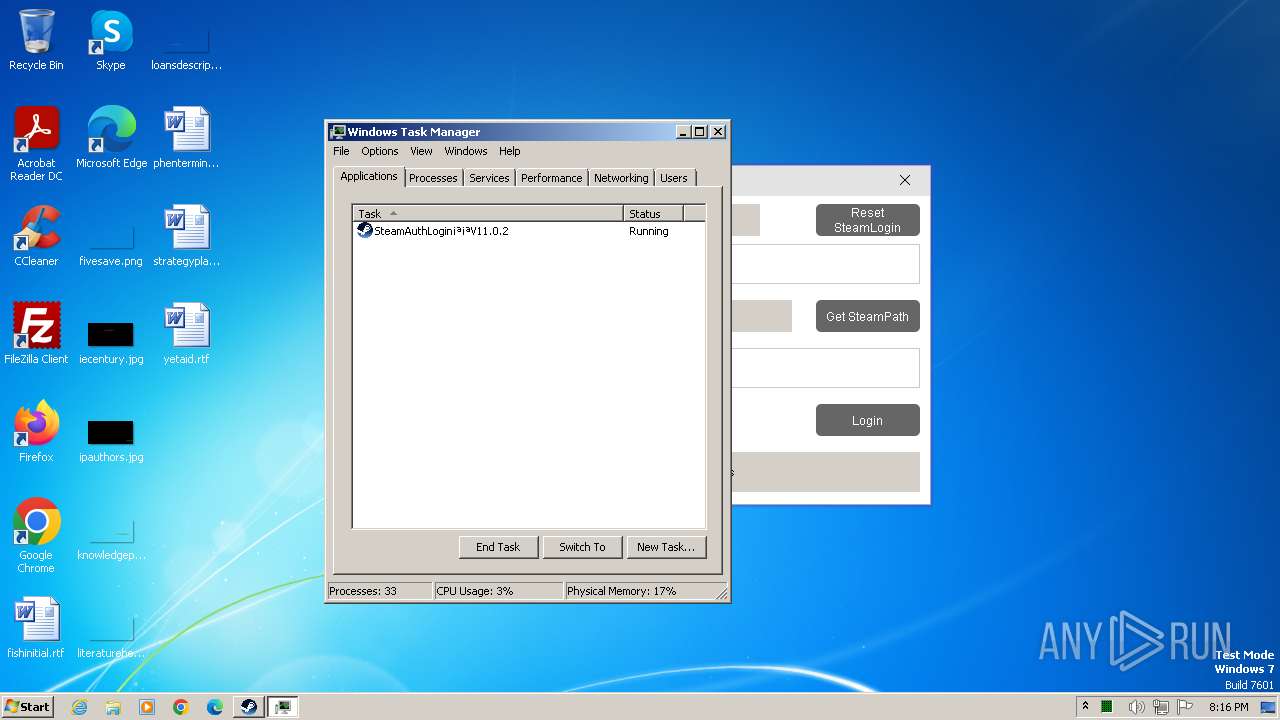
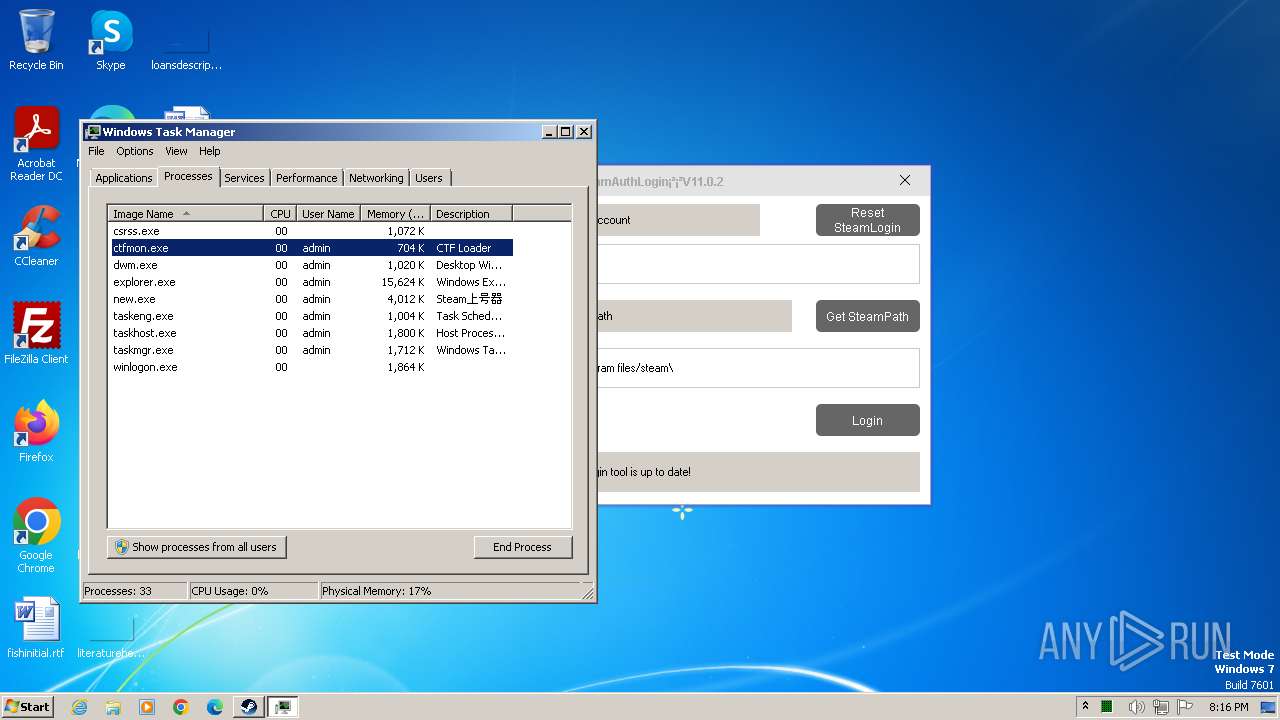
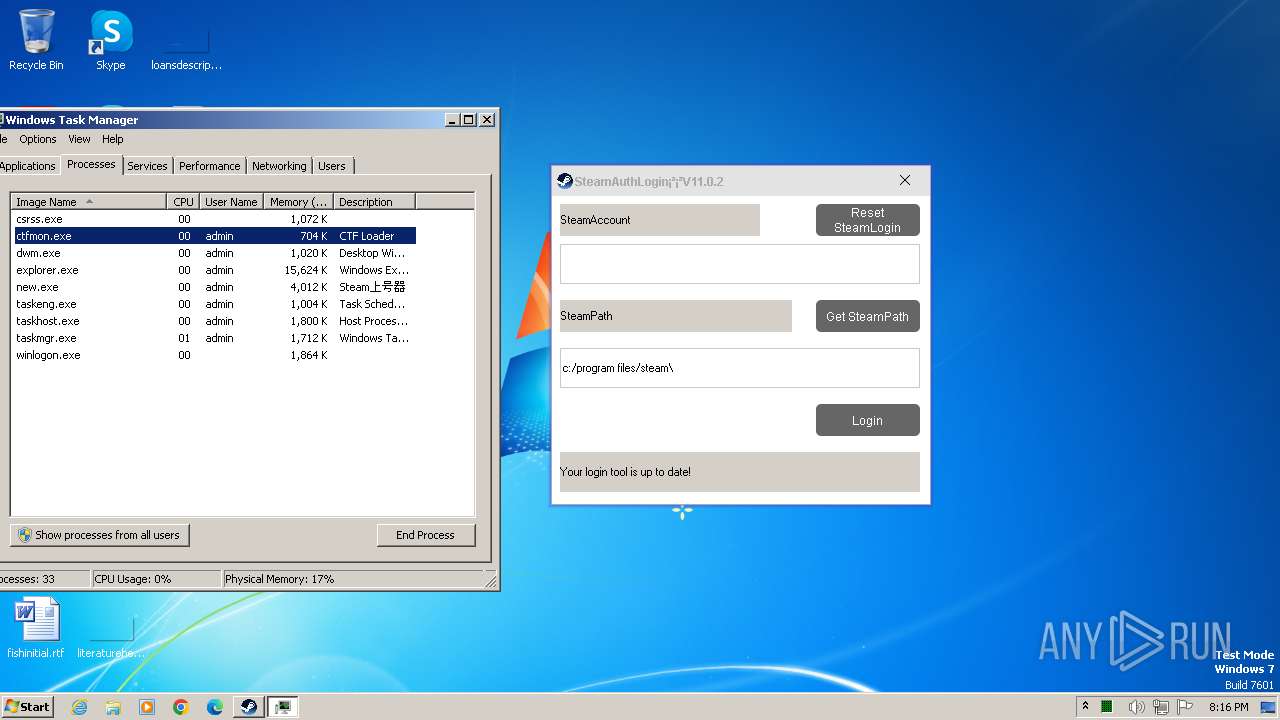
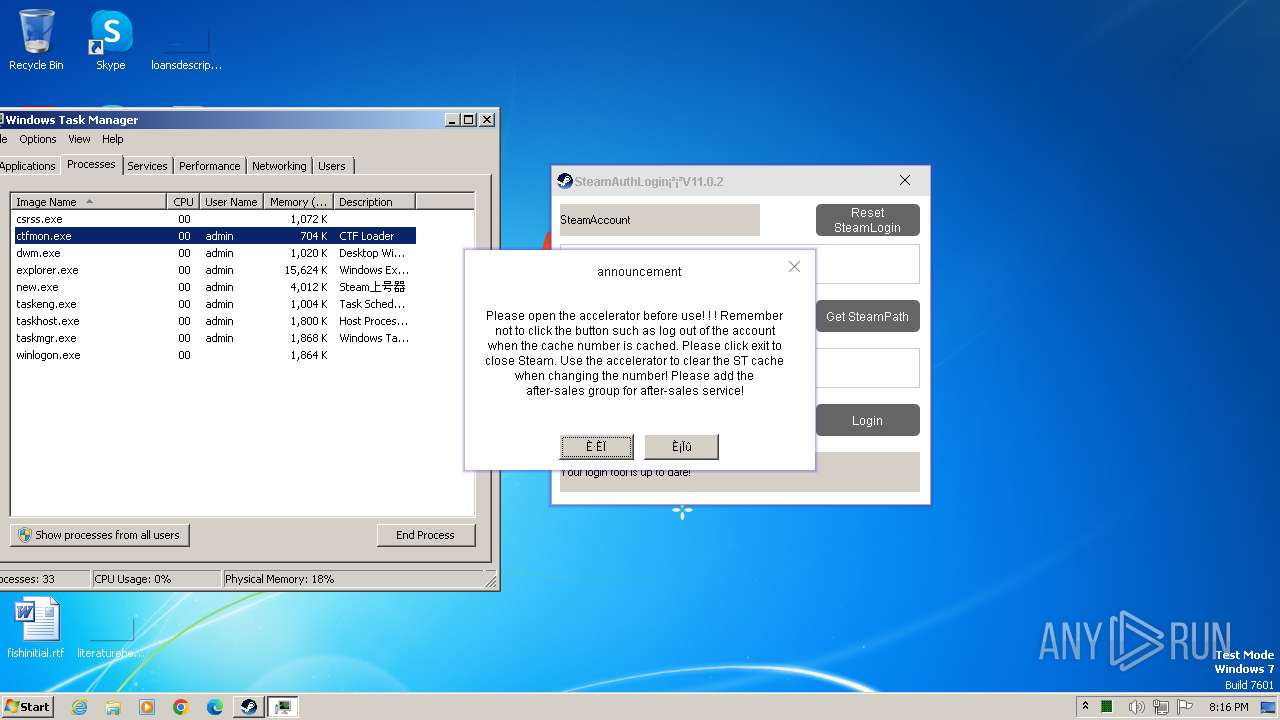
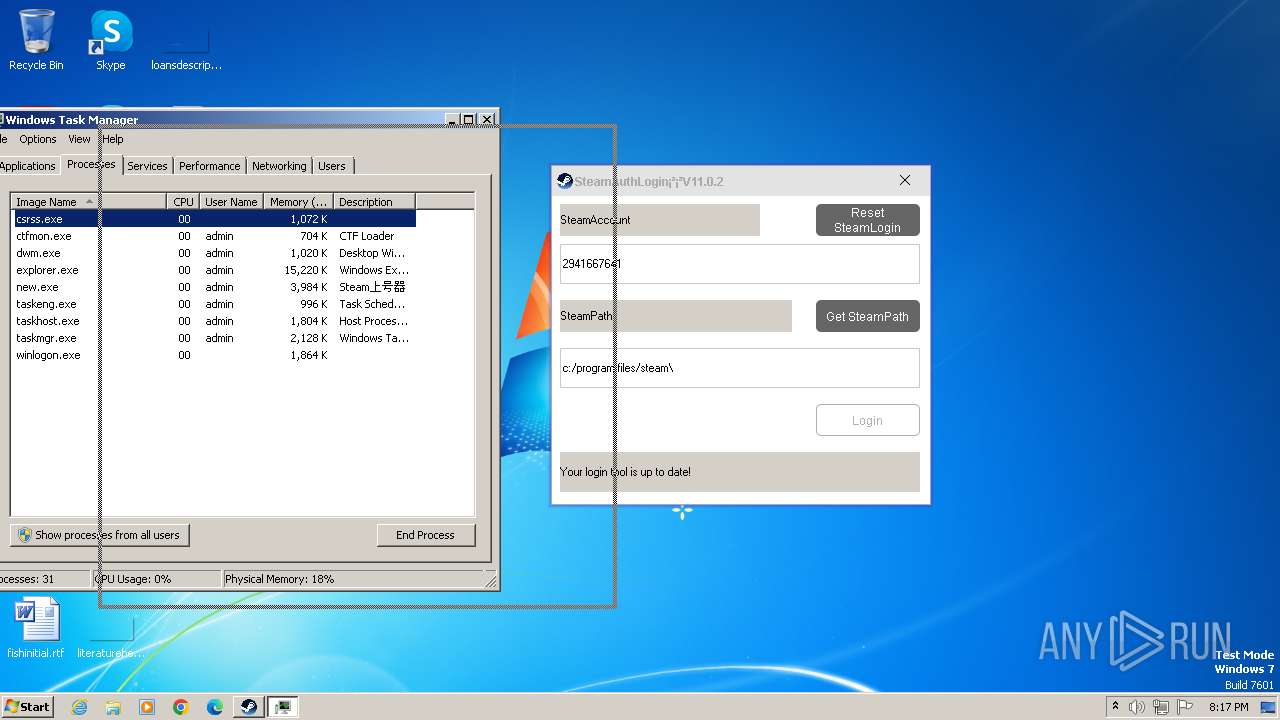
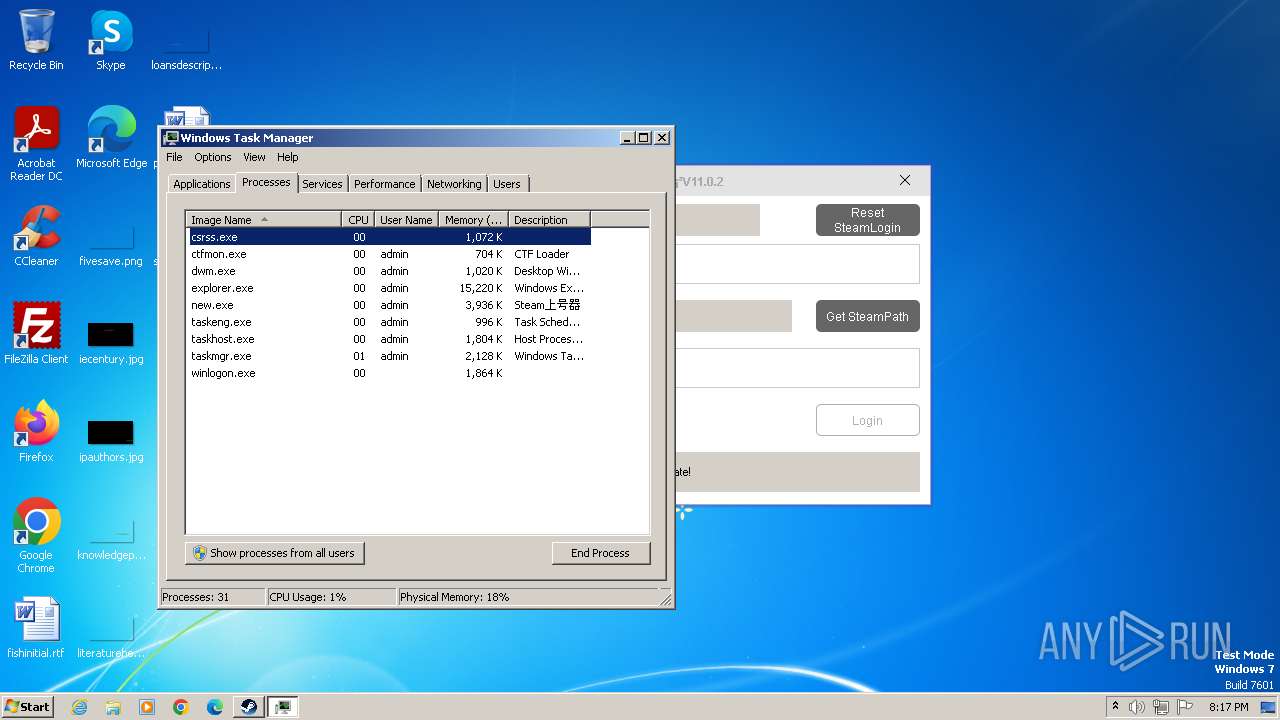
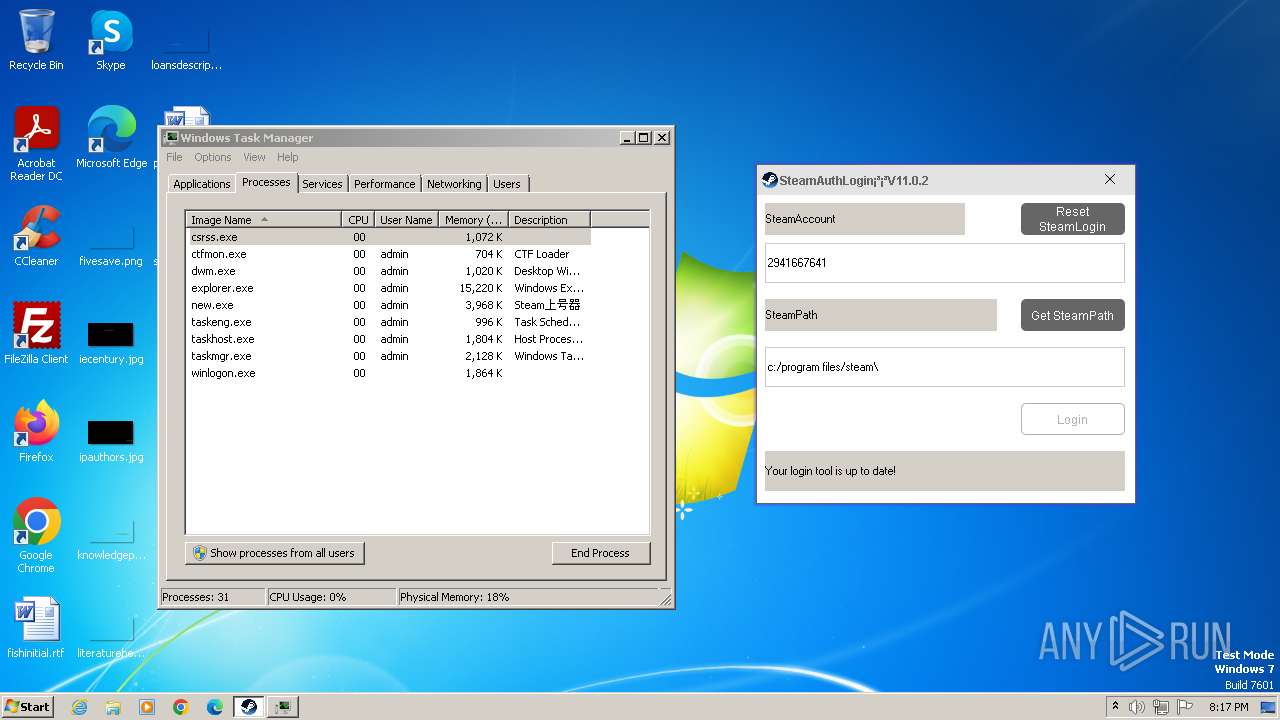
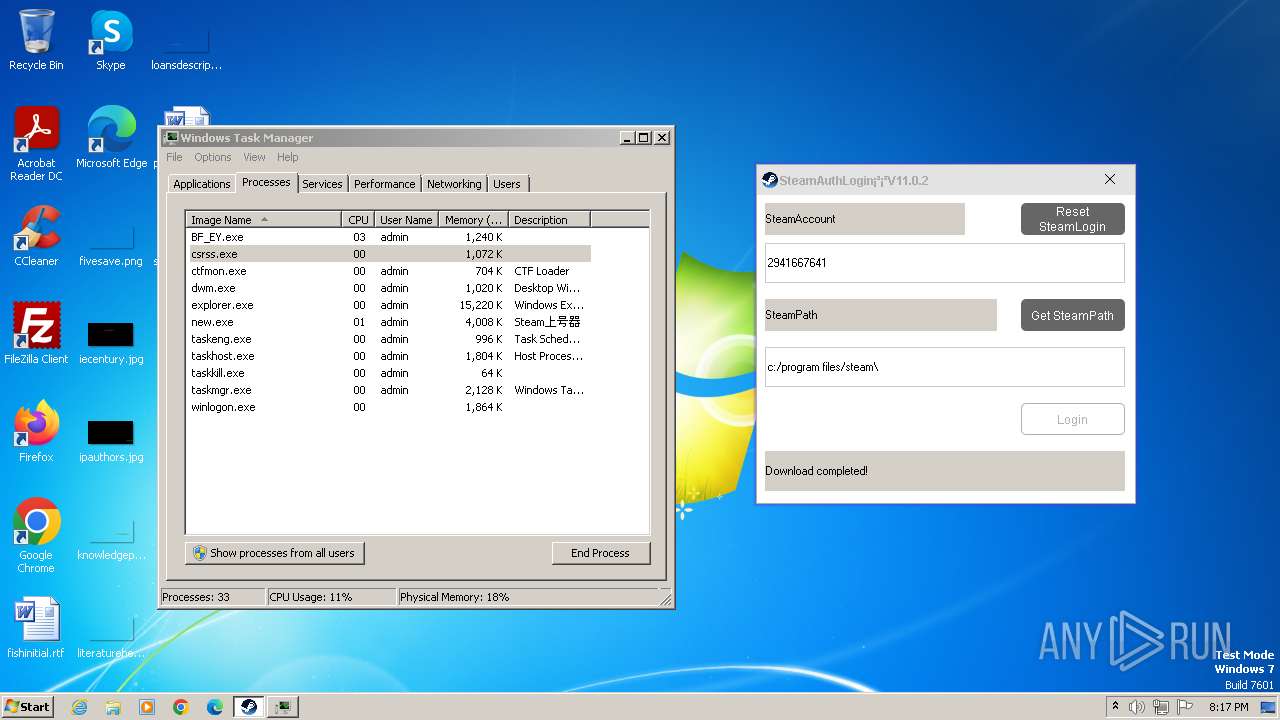
| File name: | new.exe |
| Full analysis: | https://app.any.run/tasks/b808a917-f89d-4538-b805-ac677cc48063 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2024, 19:15:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | DE0DB8BF33AA9887C471A08E5389F0A7 |
| SHA1: | 4F62F40AF655F23946A25E14AEC74104EC11DBB4 |
| SHA256: | 0D9F8727750389AA03656CEDC6A0A472B5530020961A2B9977FECCE67B7D7D5A |
| SSDEEP: | 98304:knk3y8E74s2FHOkSrSN5Bf1kM3pXdcm8ISRS25VZVV0xZb3T9pBq9RCD:tAw |
MALICIOUS
Drops the executable file immediately after the start
- new.exe (PID: 4084)
SUSPICIOUS
Reads the Internet Settings
- new.exe (PID: 4084)
Reads security settings of Internet Explorer
- new.exe (PID: 4084)
Executable content was dropped or overwritten
- new.exe (PID: 4084)
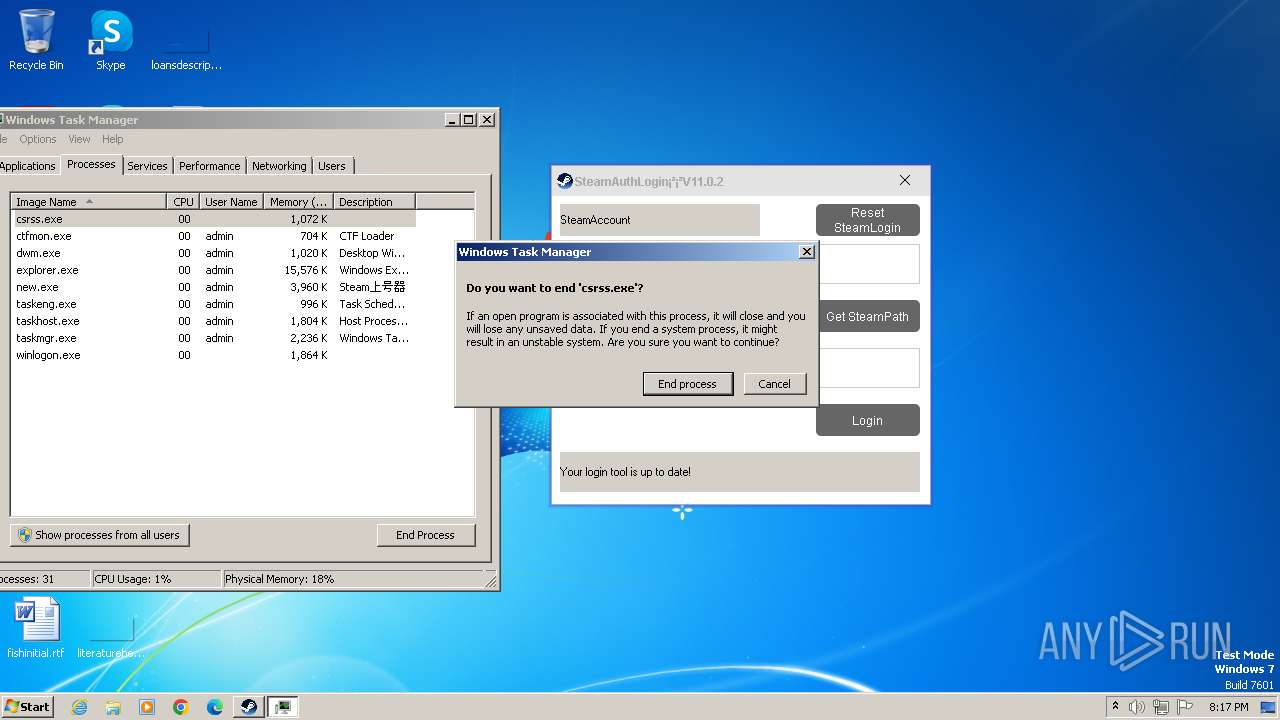
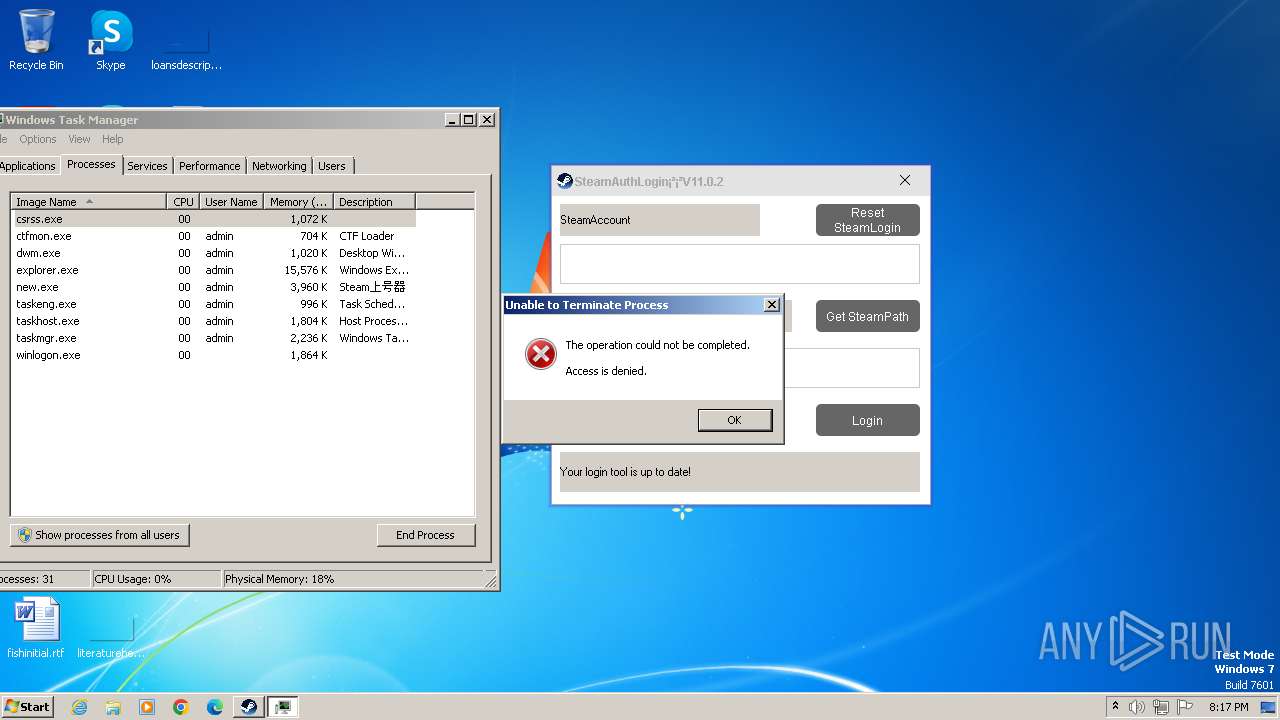
Uses TASKKILL.EXE to kill process
- BF_EY.exe (PID: 1660)
INFO
Creates files or folders in the user directory
- new.exe (PID: 4084)
- BF_EY.exe (PID: 1660)
Reads the machine GUID from the registry
- new.exe (PID: 4084)
Checks supported languages
- new.exe (PID: 4084)
- BF_EY.exe (PID: 1660)
- wmpnscfg.exe (PID: 336)
Checks proxy server information
- new.exe (PID: 4084)
Create files in a temporary directory
- new.exe (PID: 4084)
Manual execution by a user
- wmpnscfg.exe (PID: 336)
- taskmgr.exe (PID: 2204)
Reads the computer name
- wmpnscfg.exe (PID: 336)
- BF_EY.exe (PID: 1660)
- new.exe (PID: 4084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (24.4) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.6) |
| .exe | | | UPX compressed Win32 Executable (21.2) |
| .exe | | | Win32 EXE Yoda's Crypter (20.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:04:27 11:56:53+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 757760 |
| InitializedDataSize: | 1957888 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x99a9b |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.2.0 |
| ProductVersionNumber: | 11.0.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 11.0.2.0 |
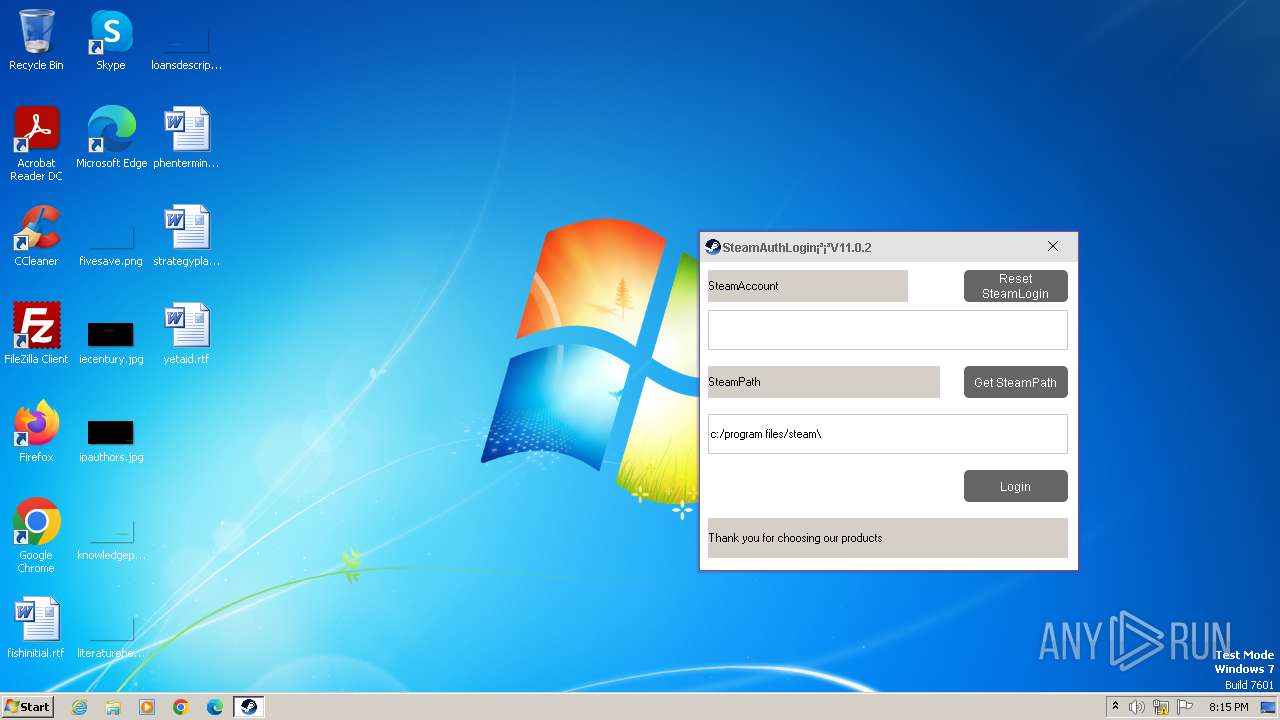
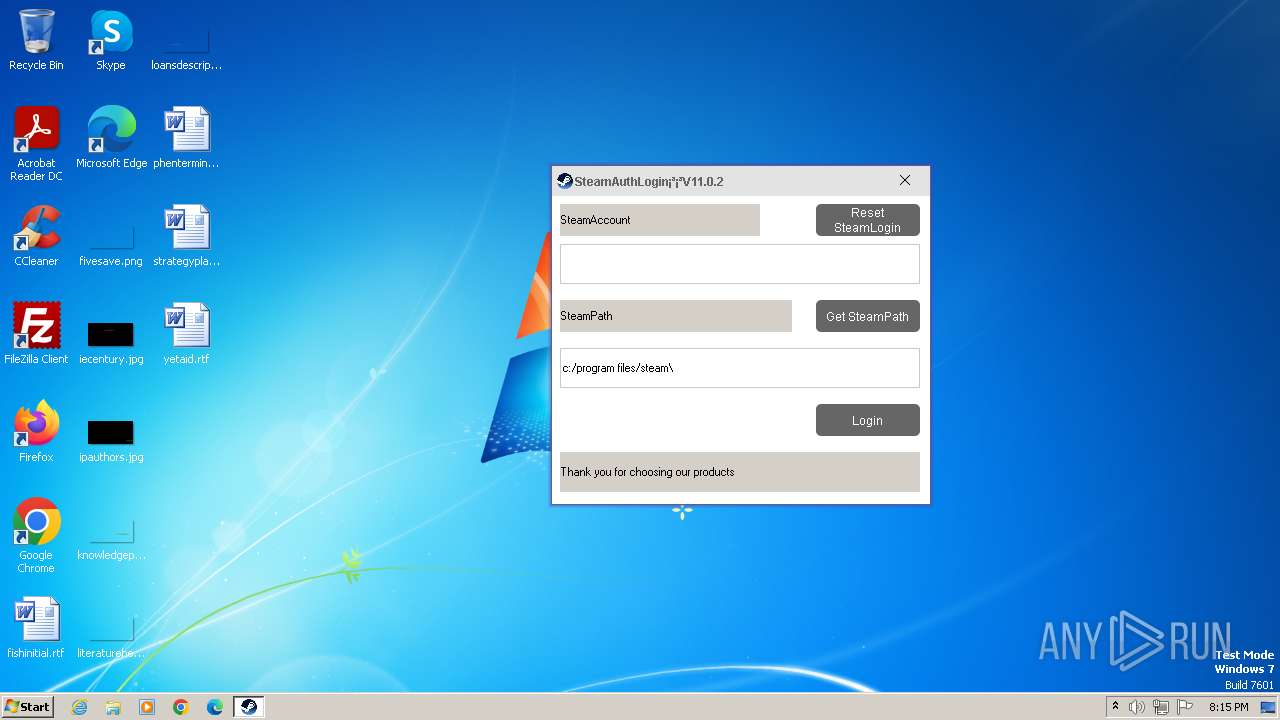
| FileDescription: | Steam上号器 |
| ProductName: | Steam上号器.纯 |
| ProductVersion: | 11.0.2.0 |
| CompanyName: | 北方帝国@NorthGod |
| LegalCopyright: | 北方帝国@NorthGod |
| Comments: | Steam上号器 |
Total processes
45
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 336 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1588 | taskkill /f /im steam.exe | C:\Windows\System32\taskkill.exe | — | BF_EY.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1660 | C:\Users\admin\AppData\Local\Temp\\BF_EY.exe | C:\Users\admin\AppData\Local\Temp\BF_EY.exe | — | new.exe | |||||||||||
User: admin Integrity Level: HIGH Description: 只用于学习交流使用,请勿用于其他非法用途,否则后果自负! Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1788 | taskkill /f /im steamwebhelper.exe | C:\Windows\System32\taskkill.exe | — | BF_EY.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2204 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\AppData\Local\Temp\new.exe" | C:\Users\admin\AppData\Local\Temp\new.exe | — | explorer.exe | |||||||||||
User: admin Company: 北方帝国@NorthGod Integrity Level: MEDIUM Description: Steam上号器 Exit code: 3221226540 Version: 11.0.2.0 Modules
| |||||||||||||||
| 4084 | "C:\Users\admin\AppData\Local\Temp\new.exe" | C:\Users\admin\AppData\Local\Temp\new.exe | explorer.exe | ||||||||||||
User: admin Company: 北方帝国@NorthGod Integrity Level: HIGH Description: Steam上号器 Exit code: 0 Version: 11.0.2.0 Modules
| |||||||||||||||
Total events
1 271
Read events
1 243
Write events
22
Delete events
6
Modification events
| (PID) Process: | (4084) new.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Multimedia\DrawDib |
| Operation: | write | Name: | vga.drv 1280x720x32(BGR 0) |
Value: 31,31,31,31 | |||
| (PID) Process: | (4084) new.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4084) new.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (4084) new.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (4084) new.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (4084) new.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (4084) new.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4084) new.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4084) new.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4084) new.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
1
Suspicious files
1
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4084 | new.exe | C:\Users\admin\AppData\Local\Temp\BF_EY.exe | executable | |
MD5:9BE9BAEF8F5BDDB382889AEB190B341C | SHA256:3FCB28D168674E3FCC8D388914A54B49A6A49F254081A4827B121C3E38565E45 | |||
| 4084 | new.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\checkConnect[1].htm | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1660 | BF_EY.exe | C:\Users\admin\AppData\Local\Steam\local.vdf | text | |
MD5:C6FADC9922F45F1B10D095A4DE9DB208 | SHA256:63A12AFE6C86FFD8B27A368963F899678AF62C9387589A7AD4E02815A6AE578F | |||
| 4084 | new.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\versionSoftware[1].htm | text | |
MD5:7E079D9DDC5717367F8799EDECDC02D5 | SHA256:2C59C0411D8AD175FE066C2FA4B0AF8F072A0D8973D3E9FA910FB3542BBE8BA9 | |||
| 4084 | new.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\getAnnouncement[1].htm | text | |
MD5:BC1C0CB672469C260A96FF15C828A95E | SHA256:0B233222F22F77A73C8408F59CF4AE2AC8A95C2FC7313C4900B599CF2D746F1D | |||
| 4084 | new.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\ey[1].htm | text | |
MD5:7CCD70CABA7EAFF5BF577C81FE6FCB34 | SHA256:9745CC514697104ED3510D779CB9E7DB7CCA145D43455BE1A1F0704764E7CBB4 | |||
| 4084 | new.exe | C:\Users\admin\AppData\Roaming\config.ini | text | |
MD5:C6997AC281FD6DF0E8E19314E0E68919 | SHA256:CAD17921A1BF361C639E53A830AFA1A9462BE2EC401F67FD6BB90528A85CDBFA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
12
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4084 | new.exe | HEAD | 200 | 103.235.46.40:80 | http://www.baidu.com/ | unknown | — | — | unknown |
4084 | new.exe | HEAD | 200 | 103.235.46.40:80 | http://www.baidu.com/ | unknown | — | — | unknown |
4084 | new.exe | GET | 200 | 18.141.225.24:80 | http://steam.authorization.ink/checkConnect?sign=9b18c2be162d9db5d8b3cc09d9c01d51&t=1717182942 | unknown | — | — | unknown |
4084 | new.exe | GET | 200 | 36.110.213.227:80 | http://elephant.browser.360.cn/?t=translate&i=%E6%82%A8%E7%9A%84%E4%B8%8A%E5%8F%B7%E5%99%A8%E5%B7%B2%E6%98%AF%E6%9C%80%E6%96%B0%EF%BC%81&type=AUTO&doctype=text&xmlVersion=1.1&keyfrom=360se&m=youdao | unknown | — | — | unknown |
4084 | new.exe | GET | 200 | 18.141.225.24:80 | http://steam.authorization.ink/versionSoftware?sign=1b69b61490f79d1166d8f617653e5a51&t=1717182965 | unknown | — | — | unknown |
4084 | new.exe | HEAD | 200 | 103.235.46.40:80 | http://www.baidu.com/ | unknown | — | — | unknown |
4084 | new.exe | GET | 200 | 18.141.225.24:80 | http://steam.authorization.ink/getAnnouncement?sign=c8c015410391d836bec178796005bbe9&t=1717182968 | unknown | — | — | unknown |
4084 | new.exe | GET | 200 | 36.110.213.227:80 | http://elephant.browser.360.cn/?t=translate&i=%E4%BD%BF%E7%94%A8%E5%89%8D%E8%AF%B7%E5%85%88%E6%89%93%E5%BC%80%E5%8A%A0%E9%80%9F%E5%99%A8%EF%BC%81%EF%BC%81%EF%BC%81%E7%BC%93%E5%AD%98%E5%8F%B7%E5%88%87%E8%AE%B0%E4%B8%8D%E5%8F%AF%E7%82%B9%E5%87%BB%E6%B3%A8%E9%94%80%E8%B4%A6%E6%88%B7%E7%AD%89%E6%8C%89%E9%92%AE%EF%BC%8C%E5%85%B3%E9%97%AD%53%74%65%61%6D%E8%AF%B7%E7%82%B9%E5%87%BB%E9%80%80%E5%87%BA%EF%BC%8C%E6%8D%A2%E5%8F%B7%E7%94%A8%E4%B8%8A%E5%8F%B7%E5%99%A8%E6%B8%85%E9%99%A4%53%54%E7%BC%93%E5%AD%98%EF%BC%81%E5%94%AE%E5%90%8E%E8%AF%B7%E5%8A%A0%E5%94%AE%E5%90%8E%E7%BE%A4%EF%BC%81&type=AUTO&doctype=text&xmlVersion=1.1&keyfrom=360se&m=youdao | unknown | — | — | unknown |
4084 | new.exe | GET | 200 | 36.110.213.227:80 | http://elephant.browser.360.cn/?t=translate&i=%E4%B8%8B%E8%BD%BD%E5%AE%8C%E6%88%90%EF%BC%81&type=AUTO&doctype=text&xmlVersion=1.1&keyfrom=360se&m=youdao | unknown | — | — | unknown |
4084 | new.exe | GET | 200 | 18.141.225.24:80 | http://steam.authorization.ink/download/ey?sign=79780446757eebd2f4db62d49e14ad01&t=1717183056&userName=2941667641 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4084 | new.exe | 103.235.46.40:80 | www.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | malicious |
4084 | new.exe | 18.141.225.24:80 | steam.authorization.ink | AMAZON-02 | SG | unknown |
4084 | new.exe | 36.110.213.227:80 | elephant.browser.360.cn | IDC, China Telecommunications Corporation | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.baidu.com |
| whitelisted |
steam.authorization.ink |
| unknown |
elephant.browser.360.cn |
| unknown |