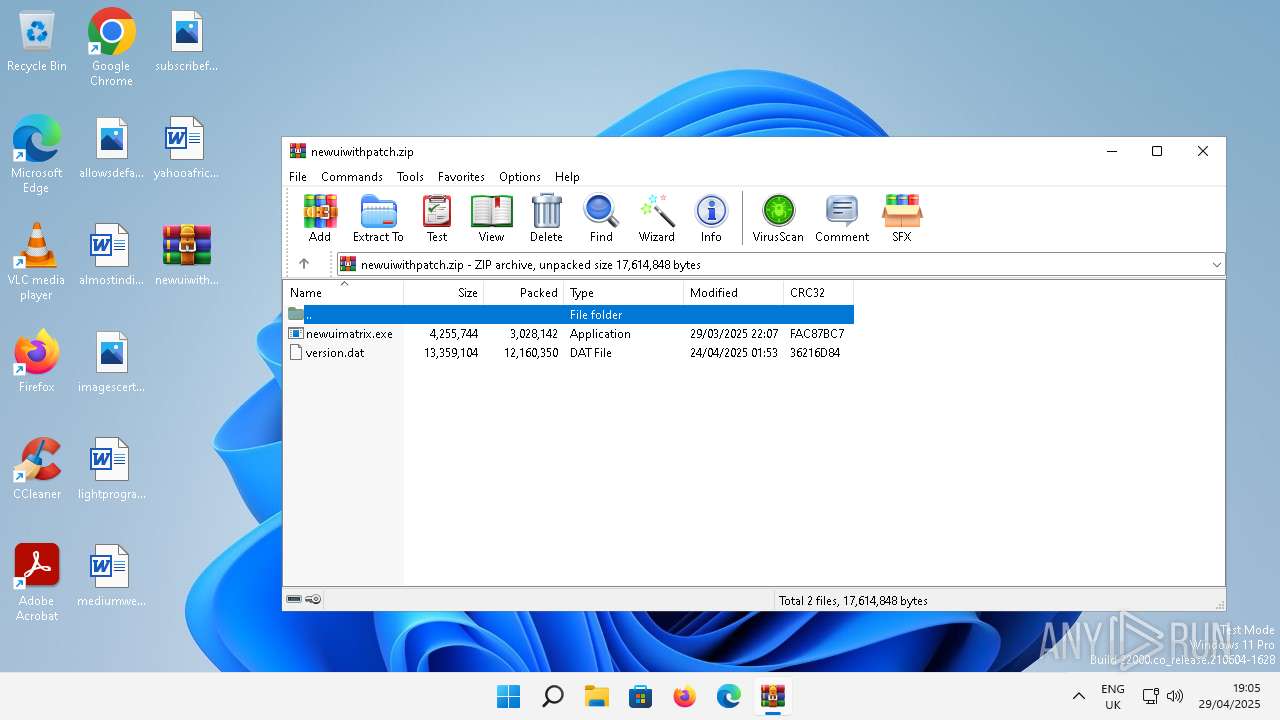
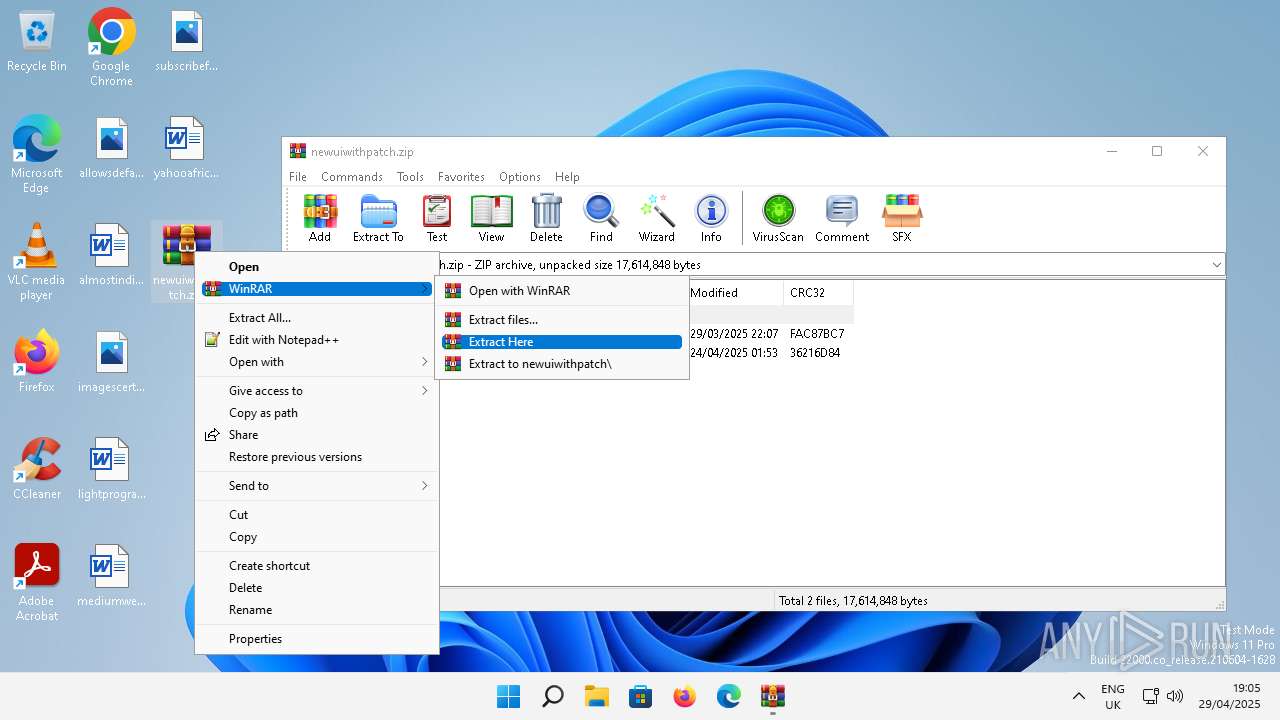
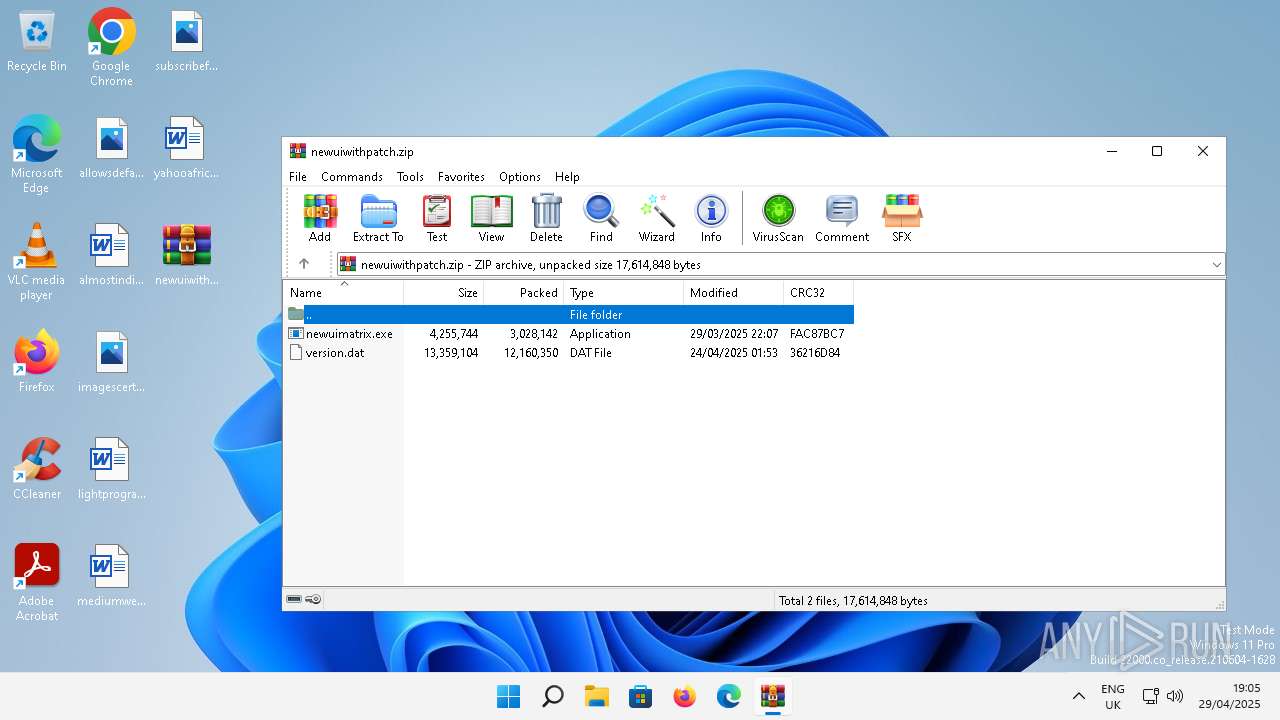
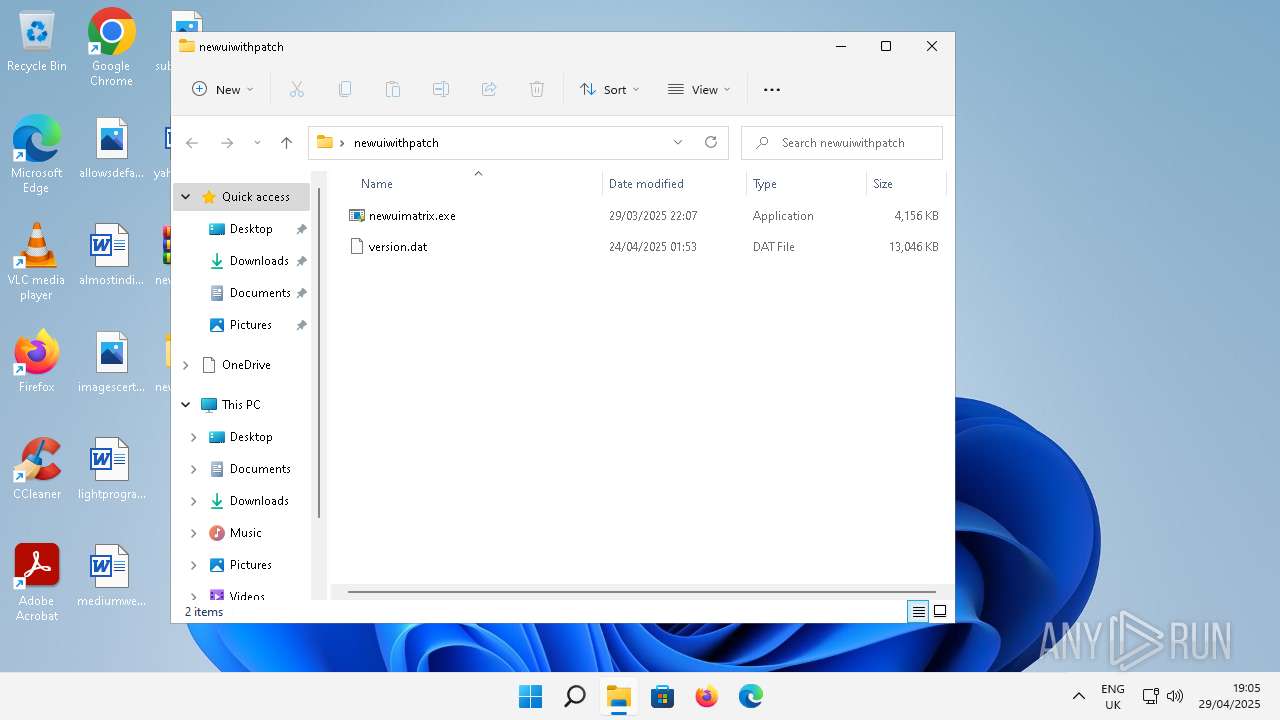
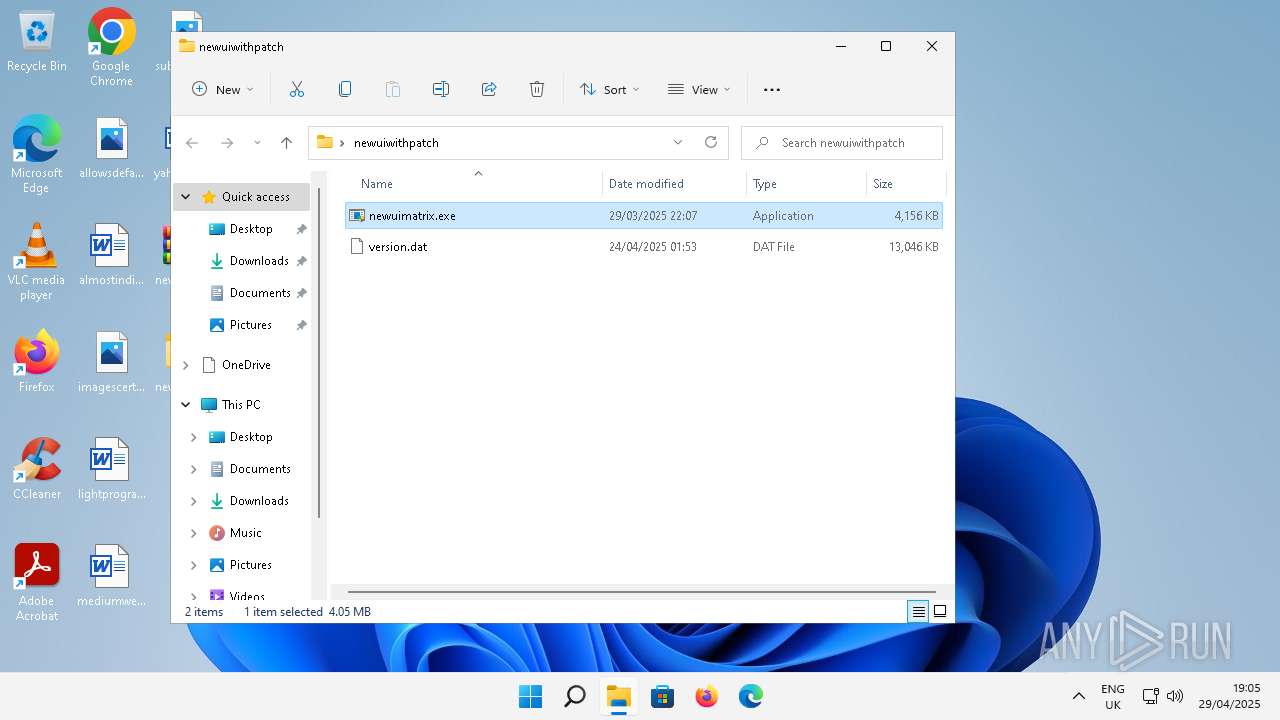
| File name: | newuiwithpatch.zip |
| Full analysis: | https://app.any.run/tasks/8ec22cc1-7039-432a-905d-c8bfa0132311 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 18:04:49 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | CCC8BB14BBF88719D2BE73C2BE1A57FA |
| SHA1: | DEFEDB164C2C867D654D4CDC00FFEBA1AEF0D12A |
| SHA256: | 0D7D0DA1690C2598908FFA2E4C18FEE754A8E2257BDBD21292B1AF92C75B0A20 |
| SSDEEP: | 98304:QespGrfoJNw0w+fSuGnds0vNQ1vctwOzmB0zhUvbvEWXHUMwCM583PCWKMcgMo8u:pPFzhDaDf1QMMIfRbqs0FkxL |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5956)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- dllhost.exe (PID: 1108)
INFO
Manual execution by a user
- WinRAR.exe (PID: 1832)
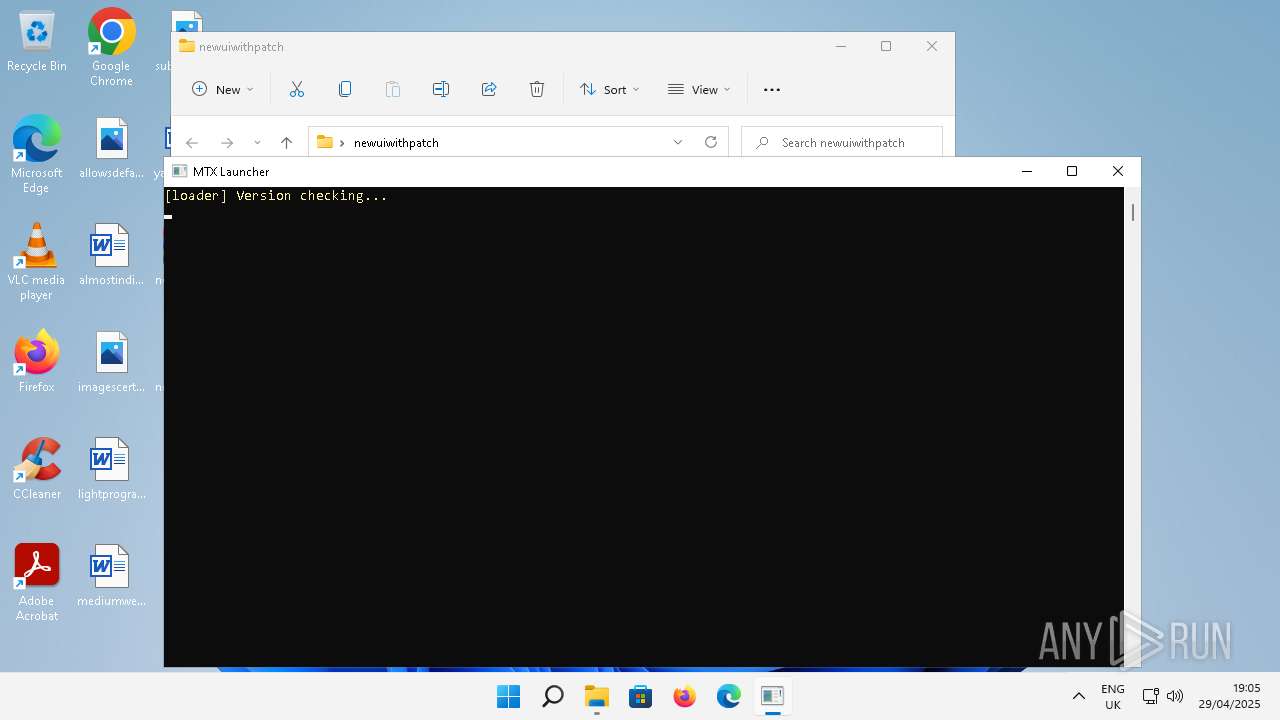
- newuimatrix.exe (PID: 5116)
- newuimatrix.exe (PID: 6124)
Checks supported languages
- newuimatrix.exe (PID: 6124)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:24 07:53:14 |
| ZipCRC: | 0x36216d84 |
| ZipCompressedSize: | 12160350 |
| ZipUncompressedSize: | 13359104 |
| ZipFileName: | version.dat |
Total processes
114
Monitored processes
7
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1108 | "C:\Windows\system32\DllHost.exe" /Processid:{B41DB860-64E4-11D2-9906-E49FADC173CA} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1832 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\newuiwithpatch.zip" C:\Users\admin\Desktop\newuiwithpatch\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2268 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | newuimatrix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | "C:\Users\admin\Desktop\newuiwithpatch\newuimatrix.exe" | C:\Users\admin\Desktop\newuiwithpatch\newuimatrix.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5524 | C:\Windows\System32\rundll32.exe C:\Windows\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5956 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\newuiwithpatch.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6124 | "C:\Users\admin\Desktop\newuiwithpatch\newuimatrix.exe" | C:\Users\admin\Desktop\newuiwithpatch\newuimatrix.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
1 888
Read events
1 862
Write events
26
Delete events
0
Modification events
| (PID) Process: | (5956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\newuiwithpatch.zip | |||
| (PID) Process: | (5956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1832 | WinRAR.exe | C:\Users\admin\Desktop\newuiwithpatch\version.dat | — | |
MD5:— | SHA256:— | |||
| 1832 | WinRAR.exe | C:\Users\admin\Desktop\newuiwithpatch\newuimatrix.exe | executable | |
MD5:49B79A318C7CF4BCF6C3F44D0ED260F9 | SHA256:887B773172839A3149DF2E67E8F6746A1BEAEF05C98718F525089F82D4EB15FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
31
DNS requests
13
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 23.212.222.21:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | unknown |
1660 | smartscreen.exe | GET | 200 | 208.89.74.17:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1559d00c0af7827b | unknown | — | — | whitelisted |
1352 | svchost.exe | GET | 200 | 184.24.77.24:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?4c1c53e3976db8c9 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?0cde1ba27ffa6121 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?e3701e10c494692d | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?cb47fcaae7c714cf | unknown | — | — | whitelisted |
4960 | svchost.exe | POST | 403 | 23.213.166.81:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | whitelisted |
4960 | svchost.exe | POST | 403 | 23.213.166.81:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | whitelisted |
4960 | svchost.exe | POST | 403 | 23.213.166.81:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1352 | svchost.exe | 184.24.77.24:80 | — | Akamai International B.V. | DE | unknown |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2276 | svchost.exe | 23.212.222.21:443 | fs.microsoft.com | AKAMAI-AS | AU | whitelisted |
1660 | smartscreen.exe | 20.56.187.20:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1660 | smartscreen.exe | 208.89.74.17:80 | ctldl.windowsupdate.com | — | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1188 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6124 | newuimatrix.exe | 109.123.234.188:9999 | — | — | — | unknown |
2988 | OfficeClickToRun.exe | 104.208.16.92:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2768 | svchost.exe | 23.50.131.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |