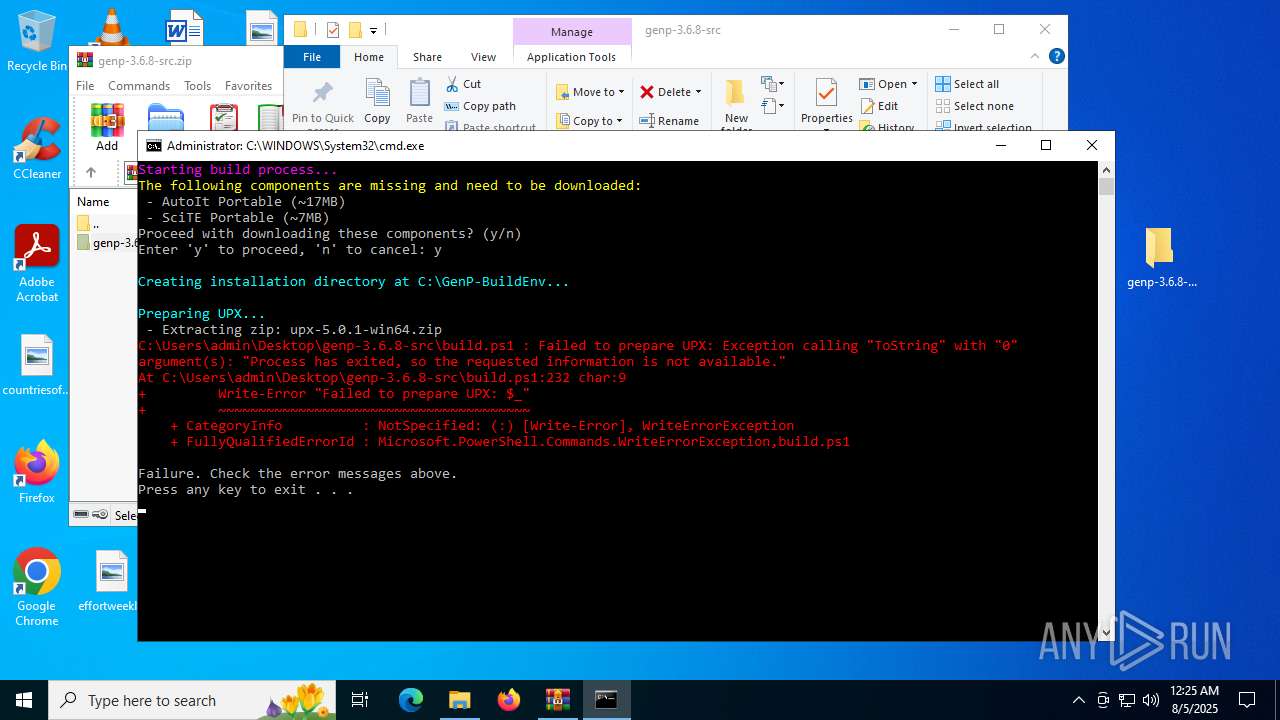
| File name: | genp-3.6.8-src.zip |
| Full analysis: | https://app.any.run/tasks/35ecfc39-8704-4b67-a961-f607a3c77fee |
| Verdict: | Malicious activity |
| Analysis date: | August 05, 2025, 00:24:06 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | E3A46339C44CFC17D386B2AB8BAA8F71 |
| SHA1: | 6FFE8CDAB5E575FB09599F1048378780F51F6D5F |
| SHA256: | 0D7BA3F043EA5CDCE1B74F7386413888F8D2DA59D97427FD2F68B4D702107F04 |
| SSDEEP: | 49152:pd/DzjdDsB5Rrn5mqUEPP84LRUvaflJ5/w1p6C1tGSB3CLlXTlBKcLs:p1D1c5Rrn4qxPLlEIlLRC1tJUs |
MALICIOUS
Generic archive extractor
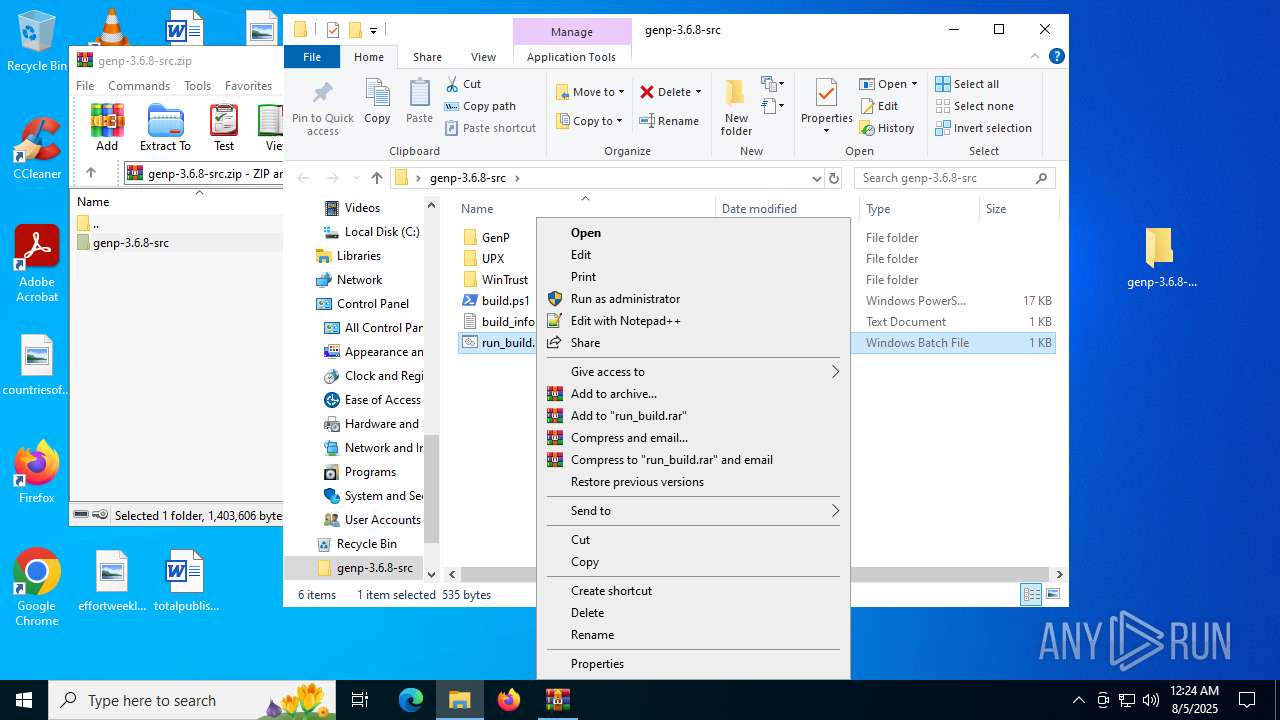
- WinRAR.exe (PID: 3576)
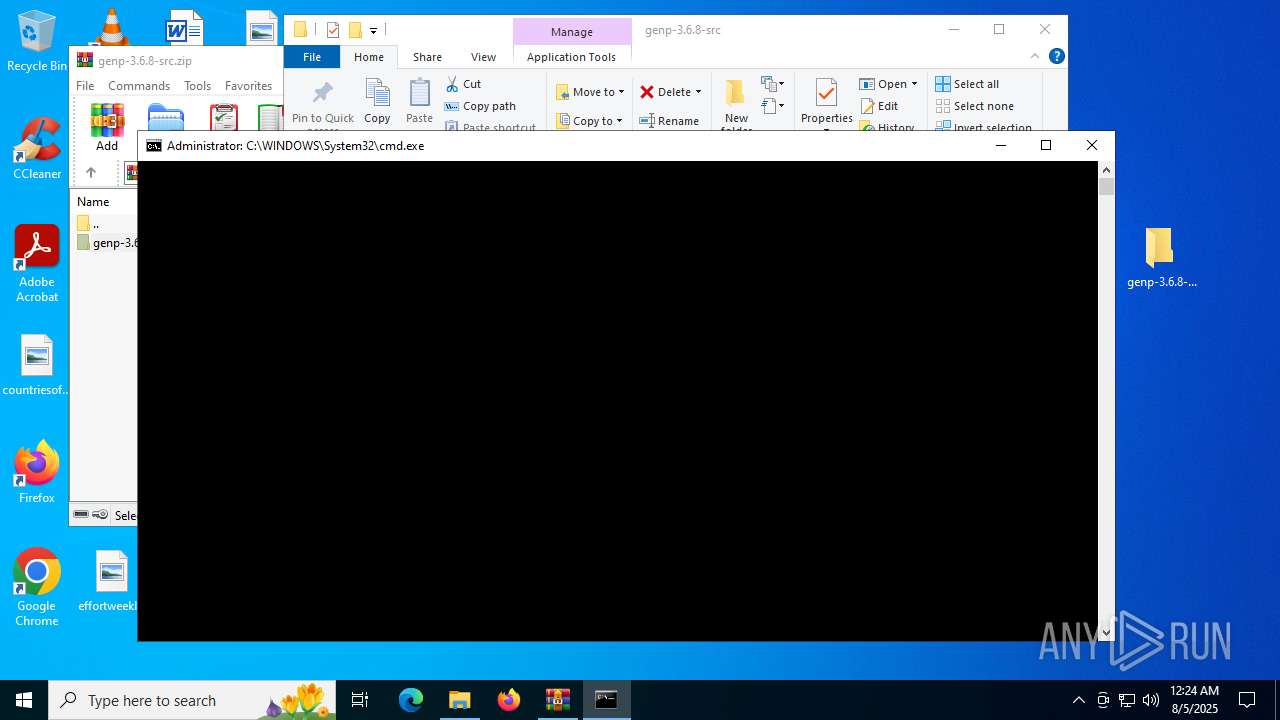
Bypass execution policy to execute commands
- powershell.exe (PID: 6304)
Changes powershell execution policy (Bypass)
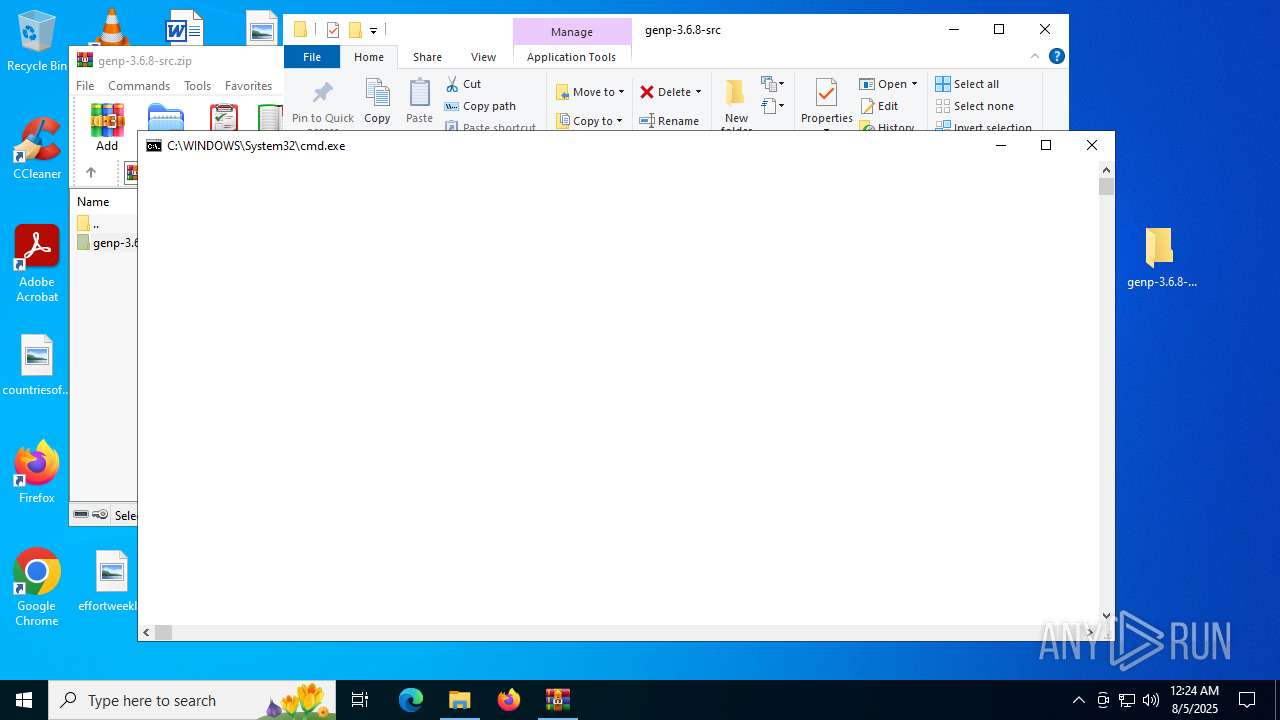
- cmd.exe (PID: 2400)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3576)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 2400)
- net.exe (PID: 1204)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2400)
The process executes Powershell scripts
- cmd.exe (PID: 2400)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 6304)
Executable content was dropped or overwritten
- tar.exe (PID: 2040)
The process executes via Task Scheduler
- updater.exe (PID: 6676)
Application launched itself
- updater.exe (PID: 6676)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3576)
Manual execution by a user
- cmd.exe (PID: 2400)
The sample compiled with english language support
- WinRAR.exe (PID: 3576)
- tar.exe (PID: 2040)
Checks supported languages
- tar.exe (PID: 2040)
- updater.exe (PID: 6676)
- updater.exe (PID: 5684)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6304)
Reads the computer name
- updater.exe (PID: 6676)
Process checks whether UAC notifications are on
- updater.exe (PID: 6676)
Reads the software policy settings
- slui.exe (PID: 2348)
Checks proxy server information
- slui.exe (PID: 2348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:08:04 19:57:08 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | genp-3.6.8-src/ |
Total processes
156
Monitored processes
12
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
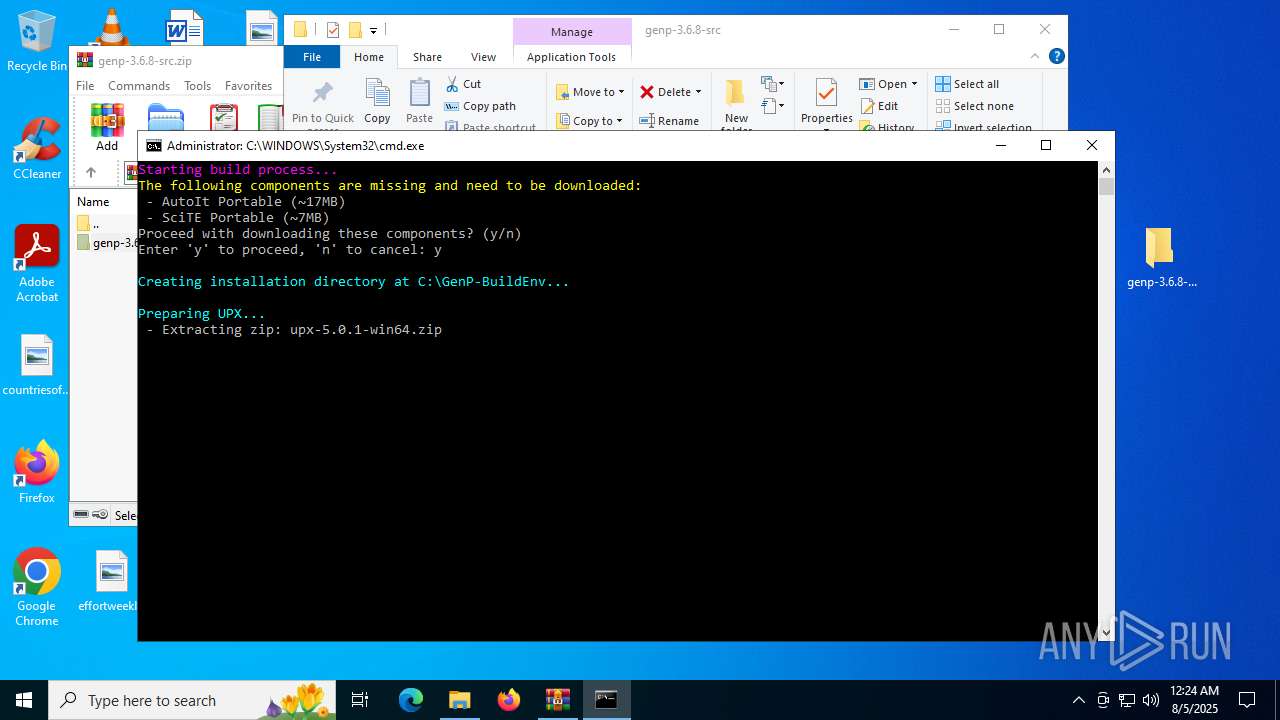
| 2040 | "C:\WINDOWS\system32\tar.exe" -xf "C:\Users\admin\Desktop\genp-3.6.8-src\UPX\upx-5.0.1-win64.zip" -C "C:\Users\admin\Desktop\genp-3.6.8-src\UPX" | C:\Windows\System32\tar.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: bsdtar archive tool Exit code: 0 Version: 3.5.2 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2348 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2400 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\genp-3.6.8-src\run_build.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2980 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3576 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\genp-3.6.8-src.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tar.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5684 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=134.0.6985.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x298,0x29c,0x2a0,0x274,0x2a4,0x111c460,0x111c46c,0x111c478 | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 6304 | powershell.exe -ExecutionPolicy Bypass -File "C:\Users\admin\Desktop\genp-3.6.8-src\build.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 192
Read events
7 184
Write events
8
Delete events
0
Modification events
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\genp-3.6.8-src.zip | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
3
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
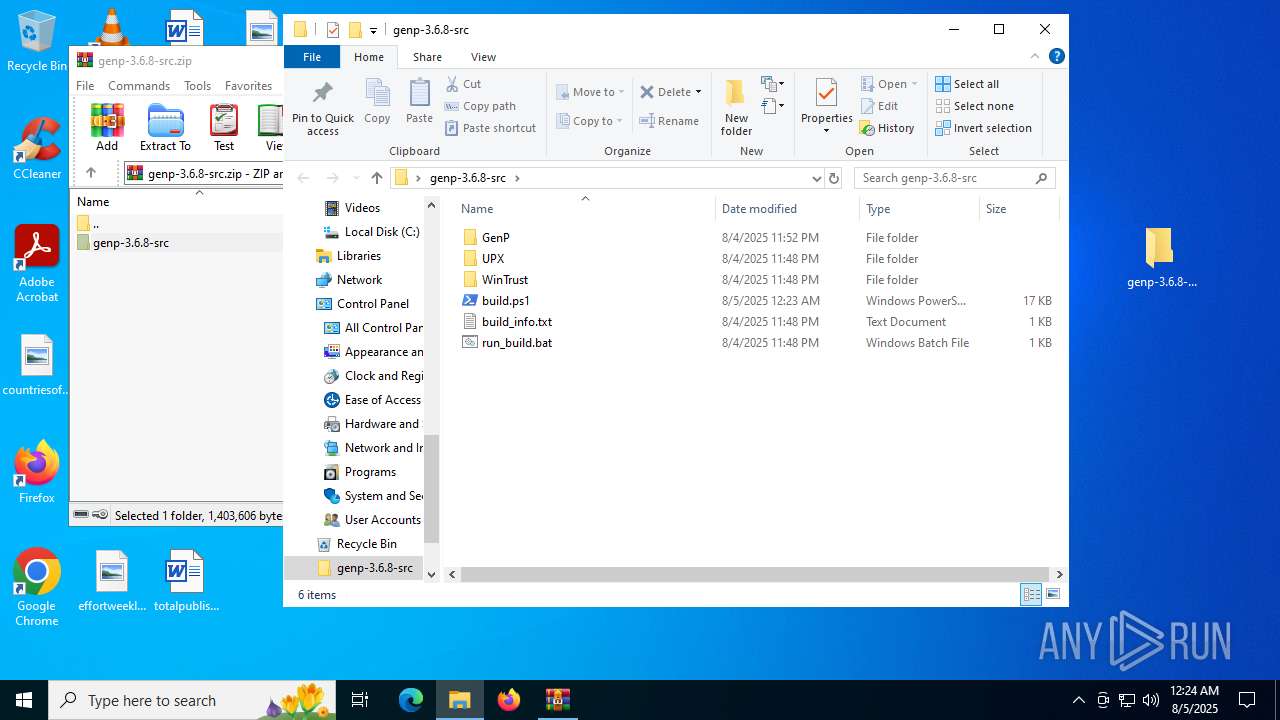
| 3576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3576.26433\genp-3.6.8-src\build.ps1 | text | |
MD5:3D359DAB743AD2B4BC9DA1371664C08A | SHA256:4376B2647326C8FCD92C90542DC278E5B6D96D469FF27814428C083CC82A2F9C | |||
| 3576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3576.26433\genp-3.6.8-src\GenP\GenP-3.6.8.au3 | binary | |
MD5:3A9CE1010E5C5DF4D7809DCFCAF1402A | SHA256:B5B99933A6898FA4DA516AB3797DADE30B77D04F08877FE3E98CC6D19FDA1444 | |||
| 3576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3576.26433\genp-3.6.8-src\GenP\config.ini | text | |
MD5:9E9E253A5B55B1C3E7406C95A90AAE58 | SHA256:A712B27B3327D95A09AE7EE08672DF63B2A84731EAD829124CA4D0EF4B75F130 | |||
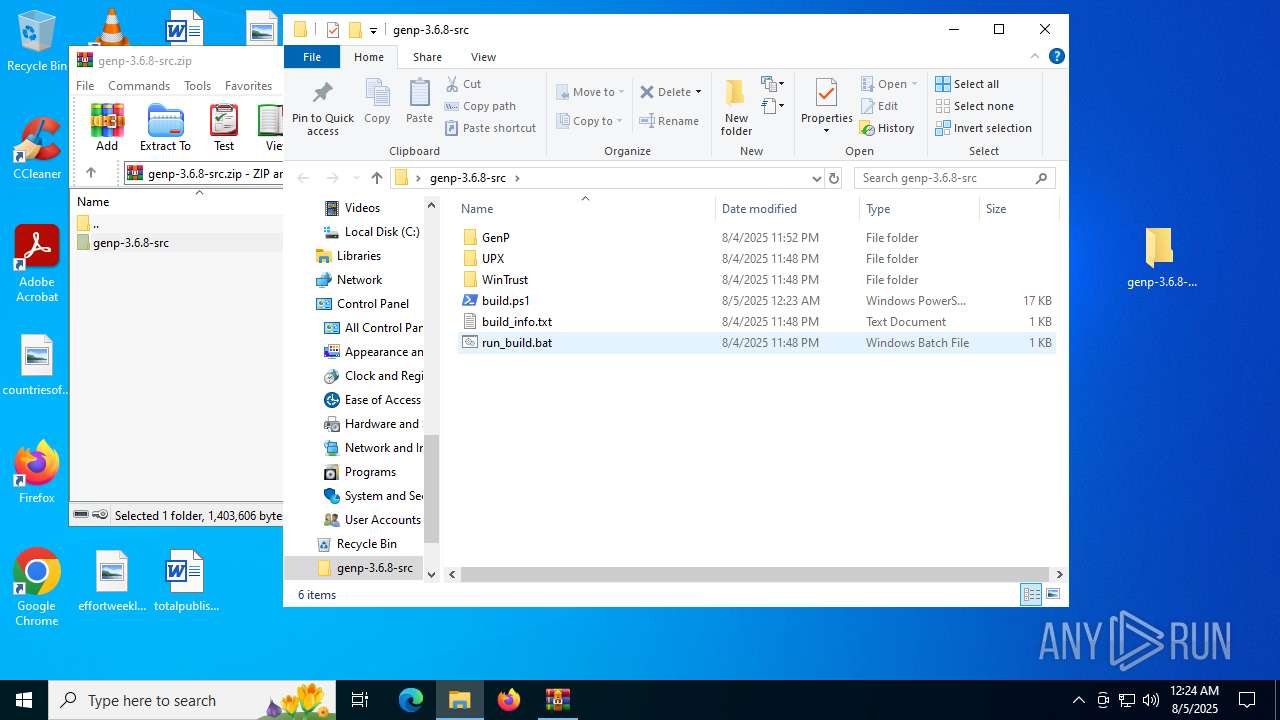
| 3576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3576.26433\genp-3.6.8-src\run_build.bat | text | |
MD5:2A1B445614F030C40FB92204611C1034 | SHA256:E89150350B8B4D6957C180B8C044F367CDEA8D0D0B71C8F59DCA8F9EC99A2BE5 | |||
| 3576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3576.26433\genp-3.6.8-src\WinTrust\patch_wintrust.ps1 | text | |
MD5:4C1563EB08376A1FC0979A18C1DF28FC | SHA256:A73B572BBF1DDBF7D9F5A03EA5ECF9E2C296ECBEFBC60104656F21644B20B2F2 | |||
| 3576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3576.26433\genp-3.6.8-src\build_info.txt | text | |
MD5:FE91D47527E7EC9024F4D263A5884DE5 | SHA256:5BFF34F3B20E7489574185A1F3C1263221FFB5E1BAC4449D25520432678A8B42 | |||
| 2040 | tar.exe | C:\Users\admin\Desktop\genp-3.6.8-src\UPX\upx-5.0.1-win64\upx-doc.txt | text | |
MD5:2B20CF0D043C8B5C0FC0F27AECEF750D | SHA256:CDFBF5D3955DA09942C1993D8E9049EA47709765CAE5DDF134E8BF0856A28435 | |||
| 2040 | tar.exe | C:\Users\admin\Desktop\genp-3.6.8-src\UPX\upx-5.0.1-win64\README | text | |
MD5:F658702644480C07BDDB594457F8EB3C | SHA256:A68FE2B3FE48F4FD67B2924019ABE41CD1749AD025C43F265269B011D40AD830 | |||
| 2040 | tar.exe | C:\Users\admin\Desktop\genp-3.6.8-src\UPX\upx-5.0.1-win64\upx-doc.html | xml | |
MD5:CC0164496A03755DDCBC2A8F29DD5B90 | SHA256:F308BA932CFE33DA54B33B21CCEF83F073AB1A208BEE54A5B6FA22963E7F663F | |||
| 2040 | tar.exe | C:\Users\admin\Desktop\genp-3.6.8-src\UPX\upx-5.0.1-win64\LICENSE | text | |
MD5:353753597AA110E0DED3508408C6374A | SHA256:905D4A66D5324E154D976BBF88829D4D9263815A2B97CC40954F06D4A23C28EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
29
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 193.108.153.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4032 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1740 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1740 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5884 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4172 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 193.108.153.158:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4032 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |