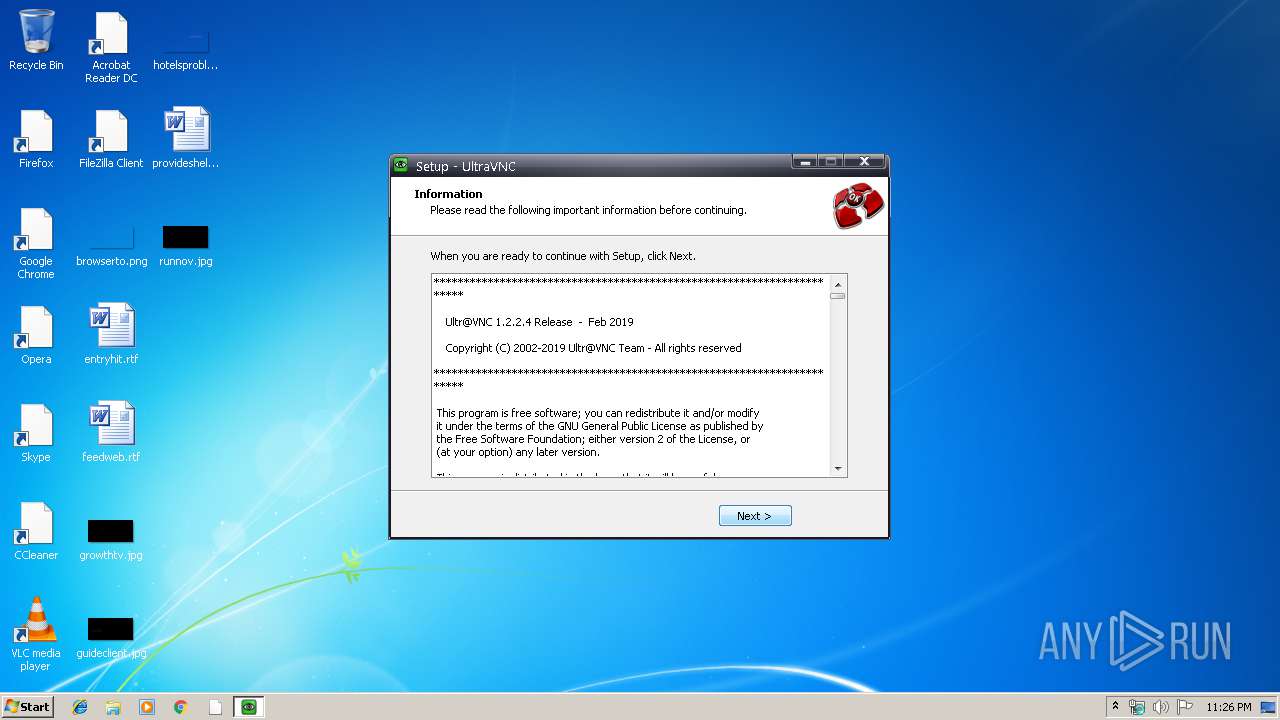
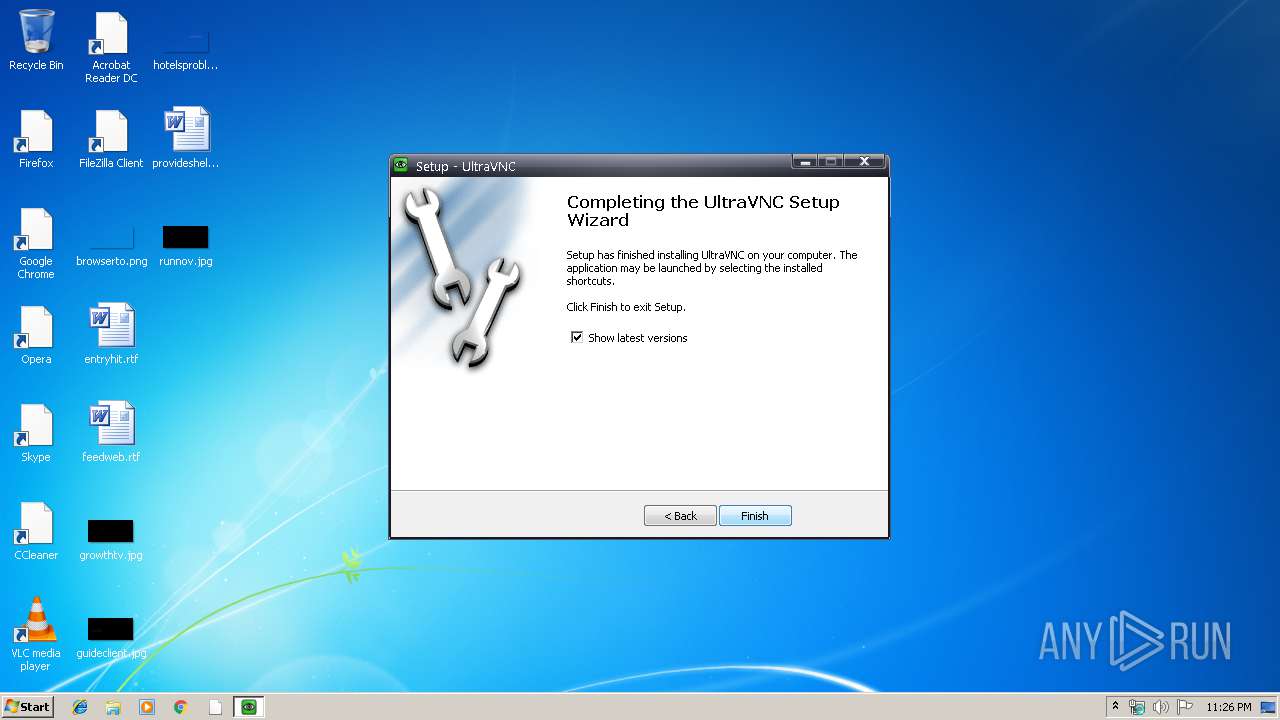
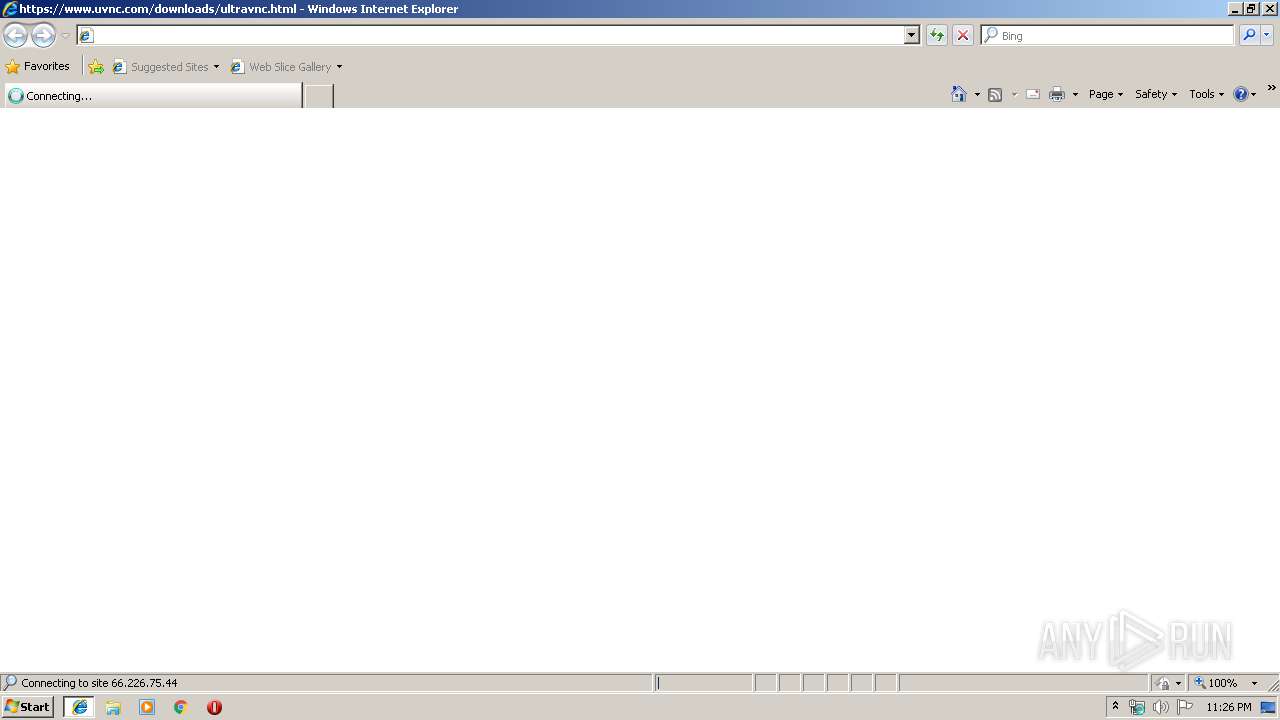
| URL: | https://www.uvnc.eu/download/1224/UltraVNC_1_2_24_X86_Setup.exe |
| Full analysis: | https://app.any.run/tasks/8ce38364-2ab7-4914-ad53-a132c4551644 |
| Verdict: | Suspicious activity |
| Analysis date: | August 22, 2019, 22:26:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 64D25F254DD46E6BFDC81D822FB24C7D |
| SHA1: | 0132DECD4E29AAD07E23ACFB7A543DBAA46F1257 |
| SHA256: | 0D717E702A7DE0A9156AFF735B9768B74F0ECC30E31B65111502A6C28377B861 |
| SSDEEP: | 3:N8DSLcGLARkUxfXarl6MRAvA:2OLcGLcxfX/MRQA |
MALICIOUS
Application was dropped or rewritten from another process
- UltraVNC_1_2_24_X86_Setup[1].exe (PID: 504)
- setcad.exe (PID: 1428)
- setpasswd.exe (PID: 3508)
- UltraVNC_1_2_24_X86_Setup[1].exe (PID: 3416)
- vncviewer.exe (PID: 2876)
SUSPICIOUS
Executable content was dropped or overwritten
- UltraVNC_1_2_24_X86_Setup[1].exe (PID: 504)
- iexplore.exe (PID: 3812)
- iexplore.exe (PID: 3520)
- UltraVNC_1_2_24_X86_Setup[1].tmp (PID: 4052)
- UltraVNC_1_2_24_X86_Setup[1].exe (PID: 3416)
Uses NETSH.EXE for network configuration
- UltraVNC_1_2_24_X86_Setup[1].tmp (PID: 4052)
Starts Internet Explorer
- UltraVNC_1_2_24_X86_Setup[1].tmp (PID: 3376)
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3588)
Creates files in the user directory
- vncviewer.exe (PID: 2876)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3812)
- iexplore.exe (PID: 3120)
Changes internet zones settings
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 2208)
Application was dropped or rewritten from another process
- UltraVNC_1_2_24_X86_Setup[1].tmp (PID: 3376)
- UltraVNC_1_2_24_X86_Setup[1].tmp (PID: 4052)
Creates files in the user directory
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 3812)
- iexplore.exe (PID: 3120)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3588)
Application launched itself
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 2208)
Loads dropped or rewritten executable
- UltraVNC_1_2_24_X86_Setup[1].tmp (PID: 4052)
Creates files in the program directory
- UltraVNC_1_2_24_X86_Setup[1].tmp (PID: 4052)
Reads internet explorer settings
- iexplore.exe (PID: 3120)
Reads settings of System Certificates
- iexplore.exe (PID: 2208)
Manual execution by user
- vncviewer.exe (PID: 2876)
Changes settings of System certificates
- iexplore.exe (PID: 2208)
Creates a software uninstall entry
- UltraVNC_1_2_24_X86_Setup[1].tmp (PID: 4052)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
57
Monitored processes
16
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\UltraVNC_1_2_24_X86_Setup[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\UltraVNC_1_2_24_X86_Setup[1].exe | iexplore.exe | ||||||||||||
User: admin Company: uvnc bvba Integrity Level: MEDIUM Description: UltraVNC Setup Exit code: 0 Version: 1.2.2.4 Modules
| |||||||||||||||
| 1428 | "C:\Program Files\uvnc bvba\UltraVNC\setcad.exe" | C:\Program Files\uvnc bvba\UltraVNC\setcad.exe | — | UltraVNC_1_2_24_X86_Setup[1].tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2208 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | UltraVNC_1_2_24_X86_Setup[1].tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2404 | "C:\Windows\system32\netsh" firewall add allowedprogram "C:\Program Files\uvnc bvba\UltraVNC\winvnc.exe" "winvnc.exe" ENABLE ALL | C:\Windows\system32\netsh.exe | — | UltraVNC_1_2_24_X86_Setup[1].tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2524 | "C:\Windows\system32\netsh" firewall add portopening TCP 5800 vnc5800 | C:\Windows\system32\netsh.exe | — | UltraVNC_1_2_24_X86_Setup[1].tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2864 | "C:\Windows\system32\netsh" firewall add portopening TCP 5900 vnc5900 | C:\Windows\system32\netsh.exe | — | UltraVNC_1_2_24_X86_Setup[1].tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
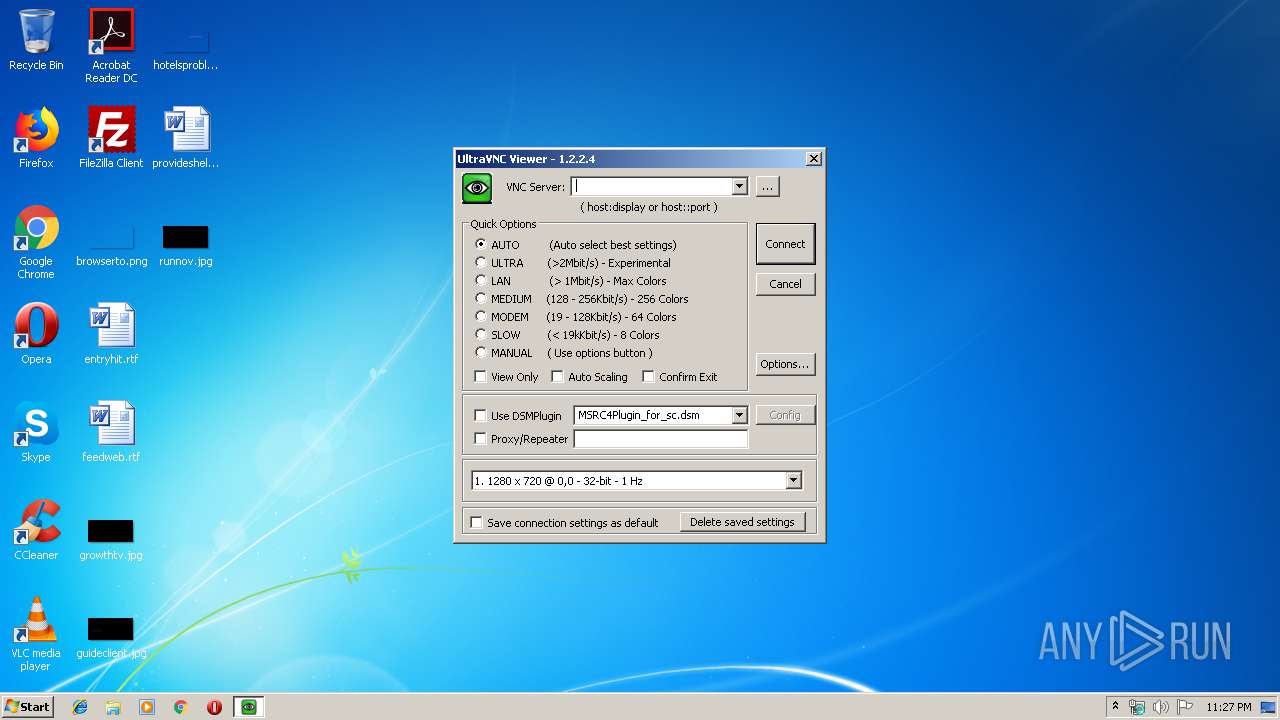
| 2876 | "C:\Program Files\uvnc bvba\UltraVNC\vncviewer.exe" | C:\Program Files\uvnc bvba\UltraVNC\vncviewer.exe | explorer.exe | ||||||||||||
User: admin Company: UltraVNC Integrity Level: MEDIUM Description: VNCViewer Exit code: 0 Version: 1.2.2.4 Modules
| |||||||||||||||
| 3120 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2208 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3304 | "C:\Windows\system32\netsh" firewall add allowedprogram "C:\Program Files\uvnc bvba\UltraVNC\vncviewer.exe" "vncviewer.exe" ENABLE ALL | C:\Windows\system32\netsh.exe | — | UltraVNC_1_2_24_X86_Setup[1].tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3376 | "C:\Users\admin\AppData\Local\Temp\is-BOLOS.tmp\UltraVNC_1_2_24_X86_Setup[1].tmp" /SL5="$301C0,2361186,350720,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\UltraVNC_1_2_24_X86_Setup[1].exe" | C:\Users\admin\AppData\Local\Temp\is-BOLOS.tmp\UltraVNC_1_2_24_X86_Setup[1].tmp | — | UltraVNC_1_2_24_X86_Setup[1].exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
1 871
Read events
1 530
Write events
330
Delete events
11
Modification events
| (PID) Process: | (3520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {DCB91157-C52B-11E9-B86F-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30708000400160016001A001400C900 | |||
Executable files
30
Suspicious files
4
Text files
37
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3520 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3520 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3812 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@www.uvnc[1].txt | — | |
MD5:— | SHA256:— | |||
| 3520 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF79924C744FF381AB.TMP | — | |
MD5:— | SHA256:— | |||
| 3812 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3520 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF1457AB3642677085.TMP | — | |
MD5:— | SHA256:— | |||
| 3520 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{DCB91157-C52B-11E9-B86F-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3812 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@www.uvnc[2].txt | text | |
MD5:— | SHA256:— | |||
| 3520 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{DCB91158-C52B-11E9-B86F-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3520 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019082220190823\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
13
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
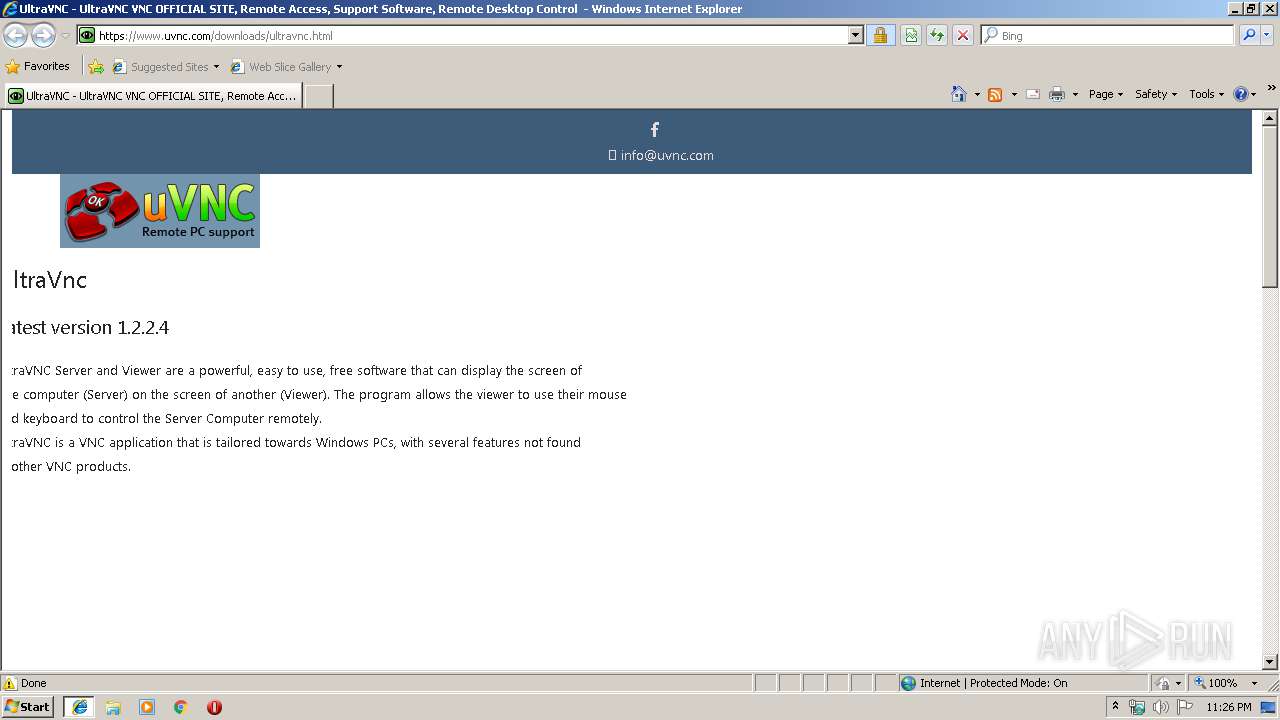
3120 | iexplore.exe | GET | 302 | 66.226.75.44:80 | http://www.uvnc.com/downloads/ultravnc.html | US | html | 228 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3812 | iexplore.exe | 213.186.33.4:443 | www.uvnc.eu | OVH SAS | FR | malicious |
3120 | iexplore.exe | 66.226.75.44:80 | www.uvnc.com | Codero | US | suspicious |
3520 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3120 | iexplore.exe | 216.58.207.72:443 | ssl.google-analytics.com | Google Inc. | US | whitelisted |
3120 | iexplore.exe | 66.226.75.44:443 | www.uvnc.com | Codero | US | suspicious |
2208 | iexplore.exe | 66.226.75.44:443 | www.uvnc.com | Codero | US | suspicious |
3120 | iexplore.exe | 172.217.23.162:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.uvnc.eu |
| malicious |
www.uvnc.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
ssl.google-analytics.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vncviewer.exe | socket error 10061
|