| URL: | https://www.apponic.com/ |
| Full analysis: | https://app.any.run/tasks/091e9a6f-86f4-4f51-ac6c-c8dbc4a4cb13 |
| Verdict: | Malicious activity |
| Analysis date: | April 03, 2024, 18:07:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C1046B23ECCE54841230A505E041D014 |
| SHA1: | 011162140533F8B80AFCA0C8887D50E2533B93D6 |
| SHA256: | 0D680113D0DB121810A3EEB87DE29898620F976A20B43A7B5732F7079EFB2FA7 |
| SSDEEP: | 3:N8DSLEZGZ3:2OLE4Z3 |
MALICIOUS
Actions looks like stealing of personal data
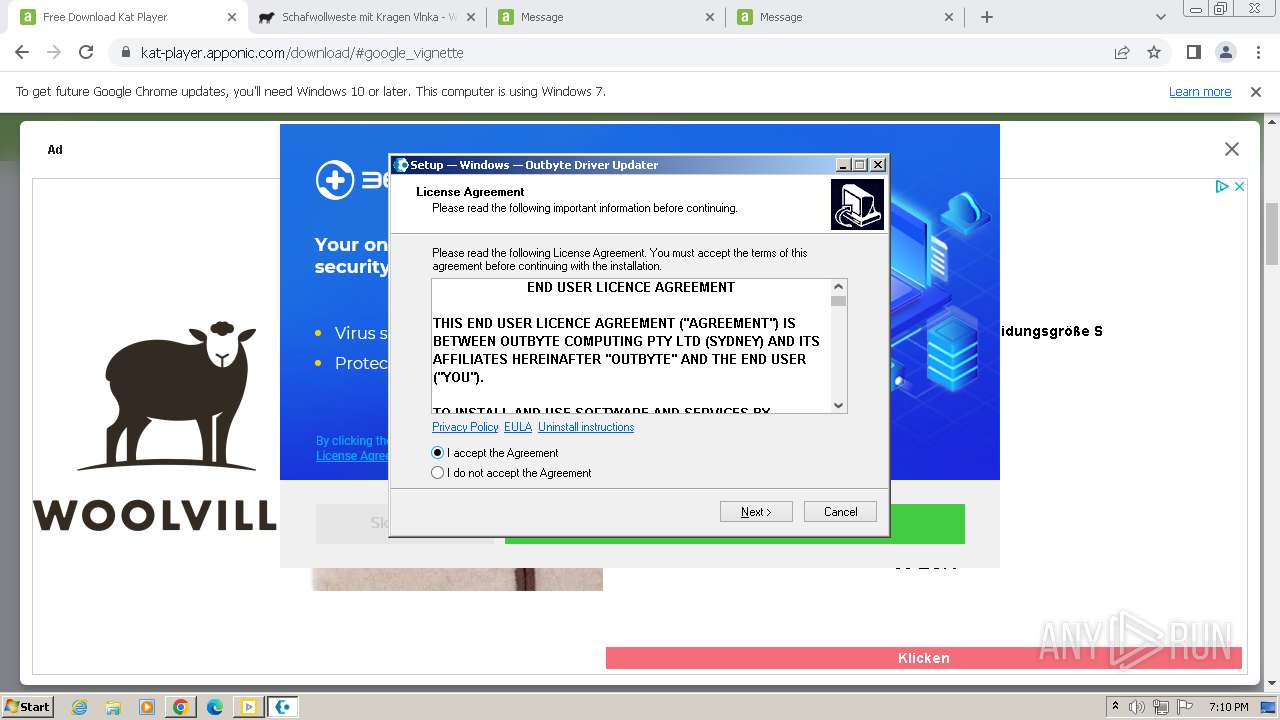
- PixelSee_id4078696id.exe (PID: 392)
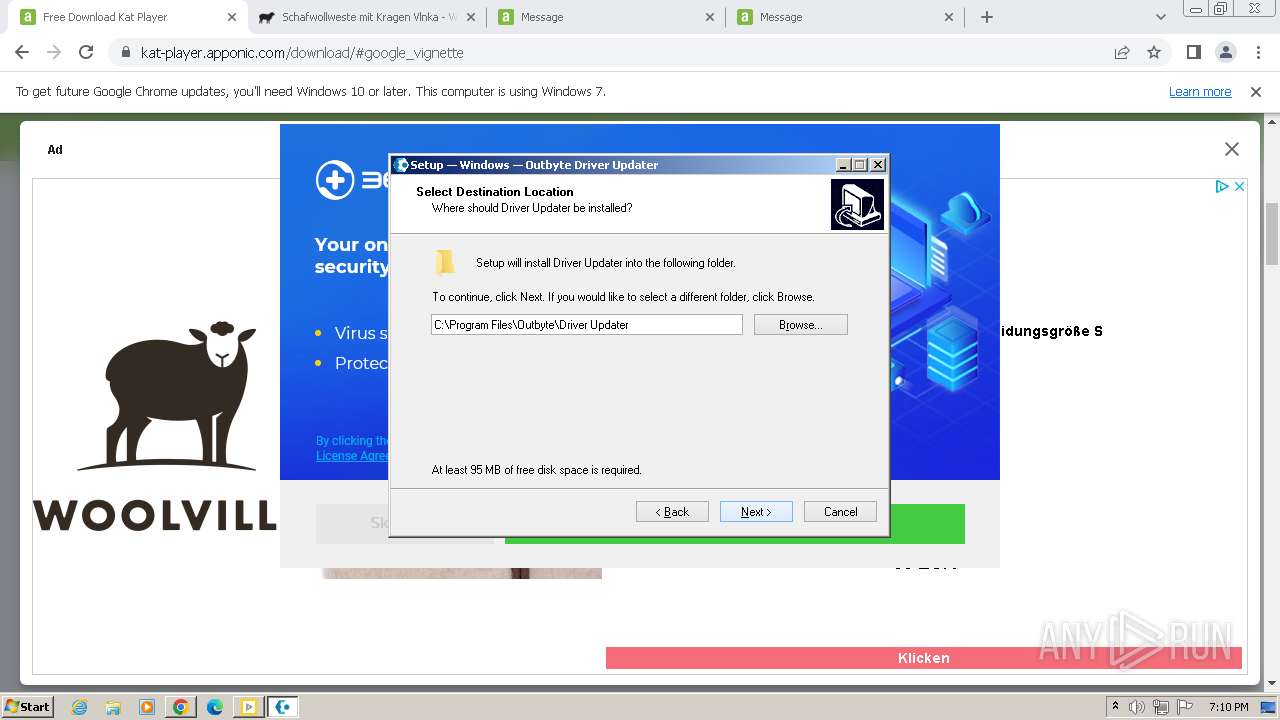
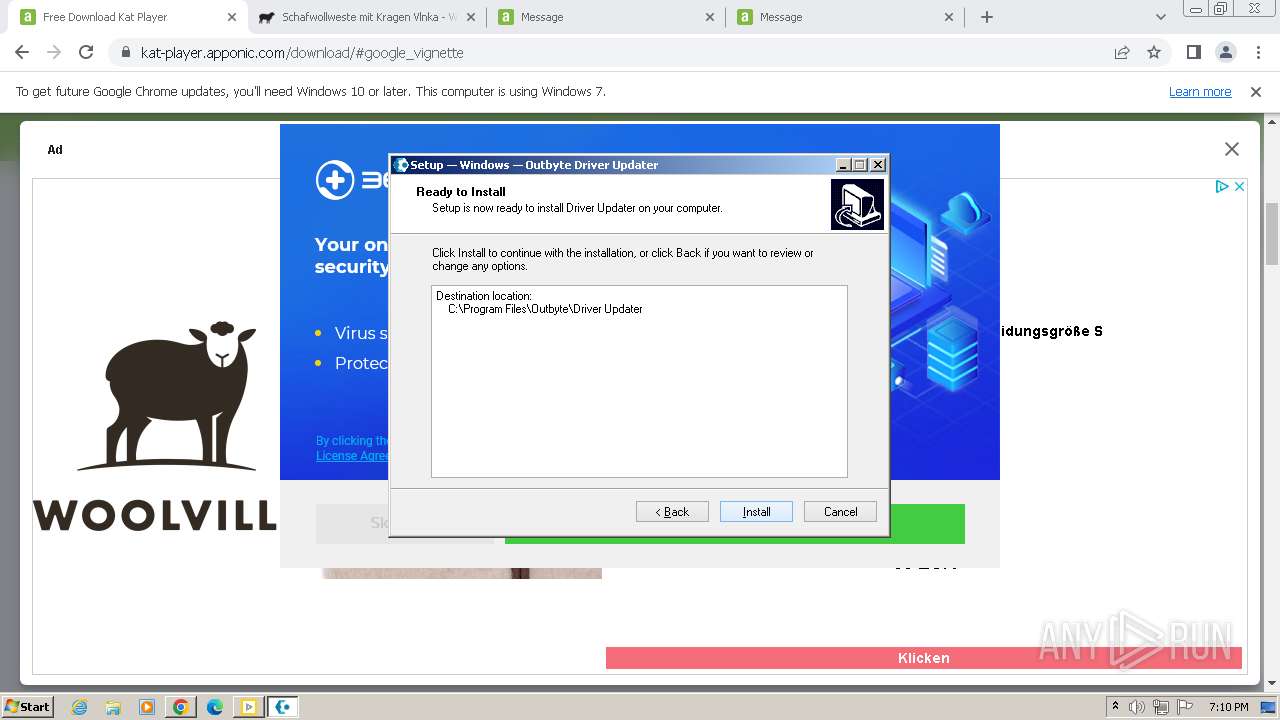
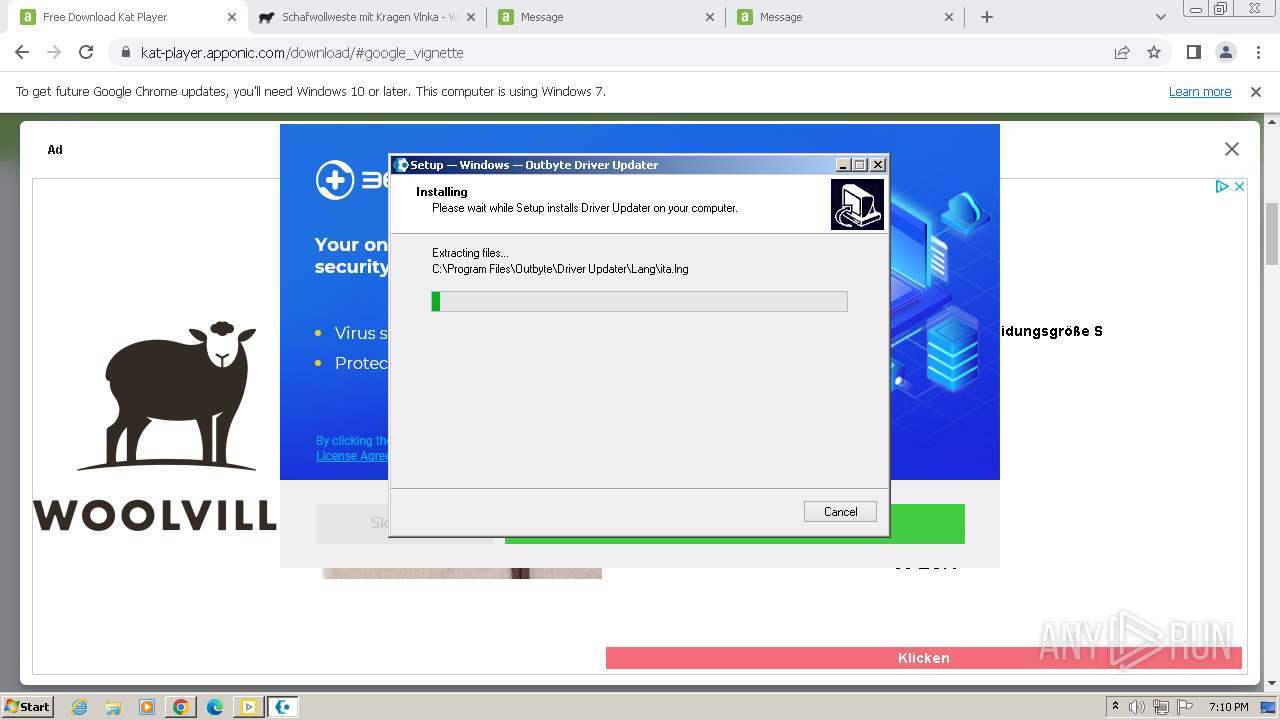
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
- setup_filerecovery.tmp (PID: 6100)
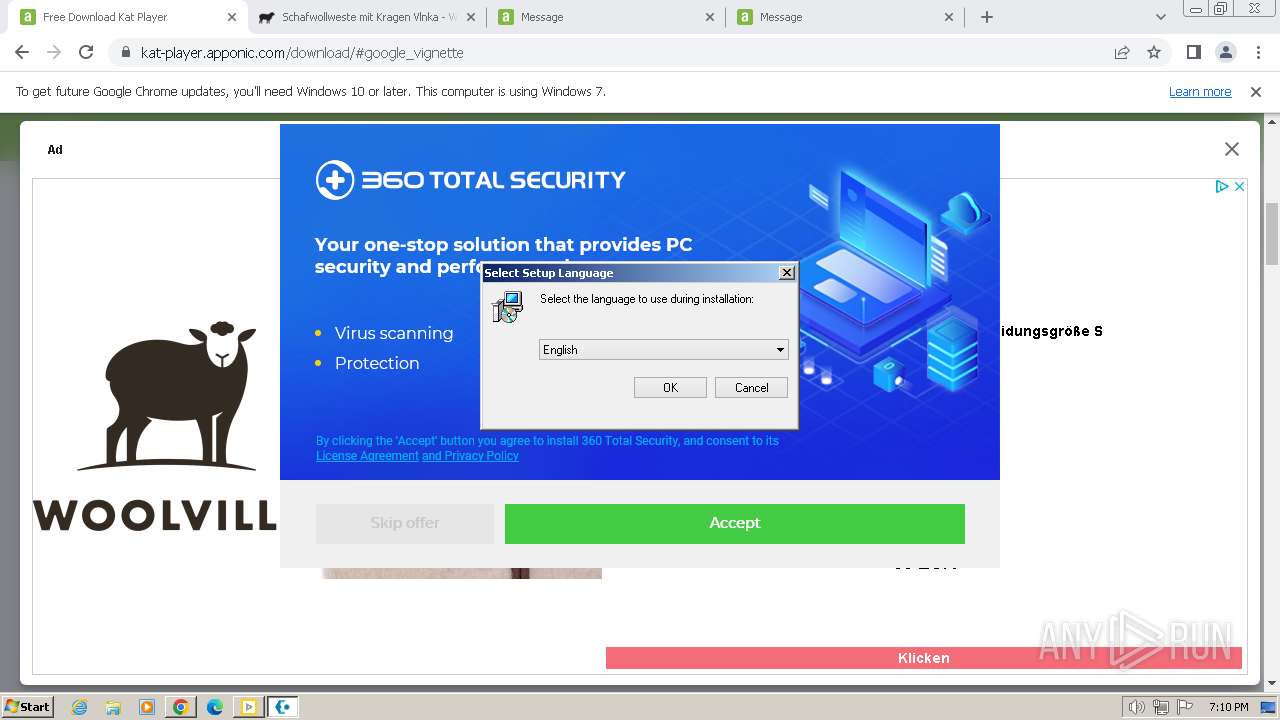
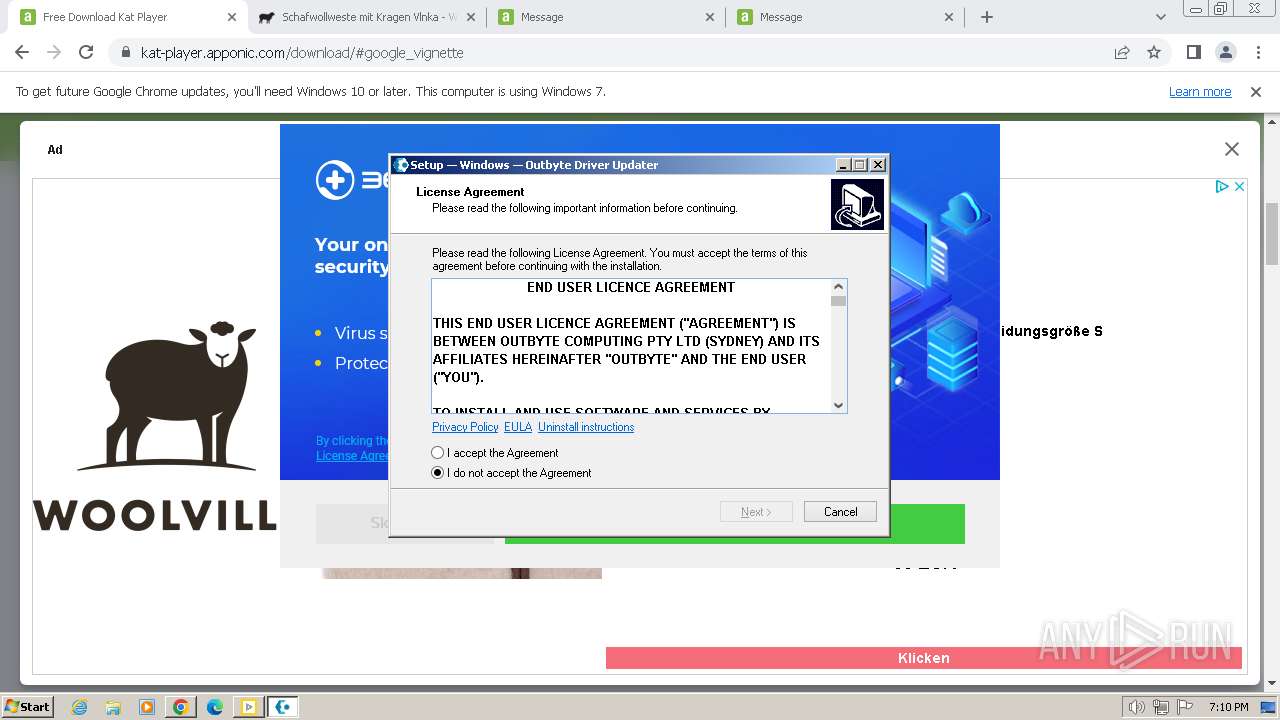
Drops the executable file immediately after the start
- Windows-outbyte-driver-updater.exe (PID: 3684)
- lum_inst.tmp (PID: 3596)
- PixelSee_id4078696id.exe (PID: 392)
- lum_inst.exe (PID: 2088)
- luminati-m-controller.exe (PID: 2100)
- net_updater32.exe (PID: 3452)
- Installer.exe (PID: 1848)
- DriverUpdater.exe (PID: 4664)
- luminati-m-controller.exe (PID: 5392)
- setup_filerecovery.exe (PID: 6092)
- setup_filerecovery.tmp (PID: 6100)
Creates a writable file in the system directory
- net_updater32.exe (PID: 3452)
Changes the autorun value in the registry
- pixelsee.exe (PID: 3768)
Steals credentials from Web Browsers
- DriverUpdater.exe (PID: 3888)
- setup_filerecovery.tmp (PID: 6100)
- taskhost.exe (PID: 3920)
Registers / Runs the DLL via REGSVR32.EXE
- DriverUpdater.exe (PID: 4664)
SUSPICIOUS
Reads the Internet Settings
- PixelSee_id4078696id.exe (PID: 392)
- Windows-outbyte-driver-updater.exe (PID: 3684)
- Installer.exe (PID: 1848)
- lum_inst.tmp (PID: 3596)
- luminati-m-controller.exe (PID: 2100)
- pixelsee.exe (PID: 3768)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
- luminati-m-controller.exe (PID: 5392)
- setup_filerecovery.tmp (PID: 6100)
- taskhost.exe (PID: 3920)
Reads security settings of Internet Explorer
- PixelSee_id4078696id.exe (PID: 392)
- Installer.exe (PID: 1848)
- lum_inst.tmp (PID: 3596)
- luminati-m-controller.exe (PID: 2100)
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
- setup_filerecovery.tmp (PID: 6100)
Reads Microsoft Outlook installation path
- PixelSee_id4078696id.exe (PID: 392)
Reads Internet Explorer settings
- PixelSee_id4078696id.exe (PID: 392)
Process drops legitimate windows executable
- PixelSee_id4078696id.exe (PID: 392)
- luminati-m-controller.exe (PID: 2100)
Checks Windows Trust Settings
- Installer.exe (PID: 1848)
- net_updater32.exe (PID: 3452)
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
Reads settings of System Certificates
- Installer.exe (PID: 1848)
- luminati-m-controller.exe (PID: 2100)
- net_updater32.exe (PID: 2536)
- DriverUpdater.exe (PID: 3888)
- pixelsee.exe (PID: 3768)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
The process drops C-runtime libraries
- PixelSee_id4078696id.exe (PID: 392)
- luminati-m-controller.exe (PID: 2100)
Reads the Windows owner or organization settings
- Installer.exe (PID: 1848)
- lum_inst.tmp (PID: 3596)
- setup_filerecovery.tmp (PID: 6100)
Reads the BIOS version
- Installer.exe (PID: 1848)
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
- setup_filerecovery.tmp (PID: 6100)
Creates a software uninstall entry
- PixelSee_id4078696id.exe (PID: 392)
- Installer.exe (PID: 1848)
Adds/modifies Windows certificates
- luminati-m-controller.exe (PID: 2100)
- Installer.exe (PID: 1848)
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
Detected use of alternative data streams (AltDS)
- luminati-m-controller.exe (PID: 2100)
- net_updater32.exe (PID: 3452)
- luminati-m-controller.exe (PID: 5392)
Non-standard symbols in registry
- lum_inst.tmp (PID: 3596)
- DriverUpdater.exe (PID: 3888)
- setup_filerecovery.tmp (PID: 6100)
Executes as Windows Service
- net_updater32.exe (PID: 3452)
- ServiceHelper.Agent.exe (PID: 3588)
- VSSVC.exe (PID: 4248)
- taskhost.exe (PID: 3920)
Process drops SQLite DLL files
- Installer.exe (PID: 1848)
- setup_filerecovery.tmp (PID: 6100)
Uses NETSH.EXE to add a firewall rule or allowed programs
- PixelSee_id4078696id.exe (PID: 392)
Searches for installed software
- dllhost.exe (PID: 4216)
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 4876)
Mutex name with non-standard characters
- DriverUpdater.exe (PID: 4664)
INFO
Drops the executable file immediately after the start
- chrome.exe (PID: 3500)
The process uses the downloaded file
- chrome.exe (PID: 2172)
- chrome.exe (PID: 3500)
- chrome.exe (PID: 1028)
Checks supported languages
- PixelSee_id4078696id.exe (PID: 392)
- wmpnscfg.exe (PID: 3656)
- Windows-outbyte-driver-updater.exe (PID: 3684)
- Installer.exe (PID: 1848)
- lum_inst.exe (PID: 2088)
- luminati-m-controller.exe (PID: 2100)
- lum_inst.tmp (PID: 3596)
- test_wpf.exe (PID: 2032)
- net_updater32.exe (PID: 2536)
- net_updater32.exe (PID: 3452)
- test_wpf.exe (PID: 2296)
- idle_report.exe (PID: 2784)
- brightdata.exe (PID: 1880)
- ServiceHelper.Agent.exe (PID: 3924)
- ServiceHelper.Agent.exe (PID: 3588)
- pixelsee.exe (PID: 3768)
- pixelsee_crashpad_handler.exe (PID: 2068)
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
- idle_report.exe (PID: 5260)
- luminati-m-controller.exe (PID: 5392)
- idle_report.exe (PID: 5792)
- test_wpf.exe (PID: 5408)
- setup_filerecovery.exe (PID: 6092)
- reader.exe (PID: 6120)
- setup_filerecovery.tmp (PID: 6100)
Reads the computer name
- PixelSee_id4078696id.exe (PID: 392)
- wmpnscfg.exe (PID: 3656)
- Windows-outbyte-driver-updater.exe (PID: 3684)
- Installer.exe (PID: 1848)
- lum_inst.tmp (PID: 3596)
- test_wpf.exe (PID: 2032)
- luminati-m-controller.exe (PID: 2100)
- net_updater32.exe (PID: 2536)
- net_updater32.exe (PID: 3452)
- test_wpf.exe (PID: 2296)
- idle_report.exe (PID: 2784)
- brightdata.exe (PID: 1880)
- ServiceHelper.Agent.exe (PID: 3924)
- ServiceHelper.Agent.exe (PID: 3588)
- pixelsee.exe (PID: 3768)
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
- idle_report.exe (PID: 5260)
- luminati-m-controller.exe (PID: 5392)
- idle_report.exe (PID: 5792)
- test_wpf.exe (PID: 5408)
- setup_filerecovery.tmp (PID: 6100)
Checks proxy server information
- PixelSee_id4078696id.exe (PID: 392)
- Windows-outbyte-driver-updater.exe (PID: 3684)
- Installer.exe (PID: 1848)
- luminati-m-controller.exe (PID: 2100)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
- setup_filerecovery.tmp (PID: 6100)
Create files in a temporary directory
- PixelSee_id4078696id.exe (PID: 392)
- Windows-outbyte-driver-updater.exe (PID: 3684)
- lum_inst.exe (PID: 2088)
- Installer.exe (PID: 1848)
- setup_filerecovery.exe (PID: 6092)
- setup_filerecovery.tmp (PID: 6100)
Reads the machine GUID from the registry
- PixelSee_id4078696id.exe (PID: 392)
- Installer.exe (PID: 1848)
- luminati-m-controller.exe (PID: 2100)
- test_wpf.exe (PID: 2032)
- net_updater32.exe (PID: 2536)
- net_updater32.exe (PID: 3452)
- test_wpf.exe (PID: 2296)
- idle_report.exe (PID: 2784)
- brightdata.exe (PID: 1880)
- pixelsee.exe (PID: 3768)
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
- idle_report.exe (PID: 5260)
- luminati-m-controller.exe (PID: 5392)
- test_wpf.exe (PID: 5408)
- idle_report.exe (PID: 5792)
- setup_filerecovery.tmp (PID: 6100)
Manual execution by a user
- wmpnscfg.exe (PID: 3656)
- explorer.exe (PID: 5640)
Process checks computer location settings
- Windows-outbyte-driver-updater.exe (PID: 3684)
- Installer.exe (PID: 1848)
- luminati-m-controller.exe (PID: 2100)
- net_updater32.exe (PID: 3452)
- DriverUpdater.exe (PID: 4664)
- luminati-m-controller.exe (PID: 5392)
- setup_filerecovery.tmp (PID: 6100)
Application launched itself
- chrome.exe (PID: 3500)
Creates files in the program directory
- Installer.exe (PID: 1848)
- luminati-m-controller.exe (PID: 2100)
- net_updater32.exe (PID: 2536)
- net_updater32.exe (PID: 3452)
- brightdata.exe (PID: 1880)
- DriverUpdater.exe (PID: 3888)
- CustomDllSurrogate.x32.exe (PID: 4892)
- DriverUpdater.exe (PID: 4664)
- luminati-m-controller.exe (PID: 5392)
- setup_filerecovery.tmp (PID: 6100)
Reads the software policy settings
- Installer.exe (PID: 1848)
- luminati-m-controller.exe (PID: 2100)
- net_updater32.exe (PID: 2536)
- net_updater32.exe (PID: 3452)
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
Reads Windows Product ID
- Installer.exe (PID: 1848)
- DriverUpdater.exe (PID: 3888)
- DriverUpdater.exe (PID: 4664)
- setup_filerecovery.tmp (PID: 6100)
Creates files or folders in the user directory
- Installer.exe (PID: 1848)
- PixelSee_id4078696id.exe (PID: 392)
- luminati-m-controller.exe (PID: 2100)
- pixelsee.exe (PID: 3768)
- pixelsee_crashpad_handler.exe (PID: 2068)
- DriverUpdater.exe (PID: 4664)
- CustomDllSurrogate.x32.exe (PID: 4892)
- taskhost.exe (PID: 3920)
Reads Environment values
- luminati-m-controller.exe (PID: 2100)
- net_updater32.exe (PID: 3452)
- brightdata.exe (PID: 1880)
- pixelsee.exe (PID: 3768)
- luminati-m-controller.exe (PID: 5392)
Reads Microsoft Office registry keys
- DriverUpdater.exe (PID: 4664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
172
Monitored processes
111
Malicious processes
19
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=54 --mojo-platform-channel-handle=5212 --field-trial-handle=1168,i,10976330724926442215,11423318362585401399,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
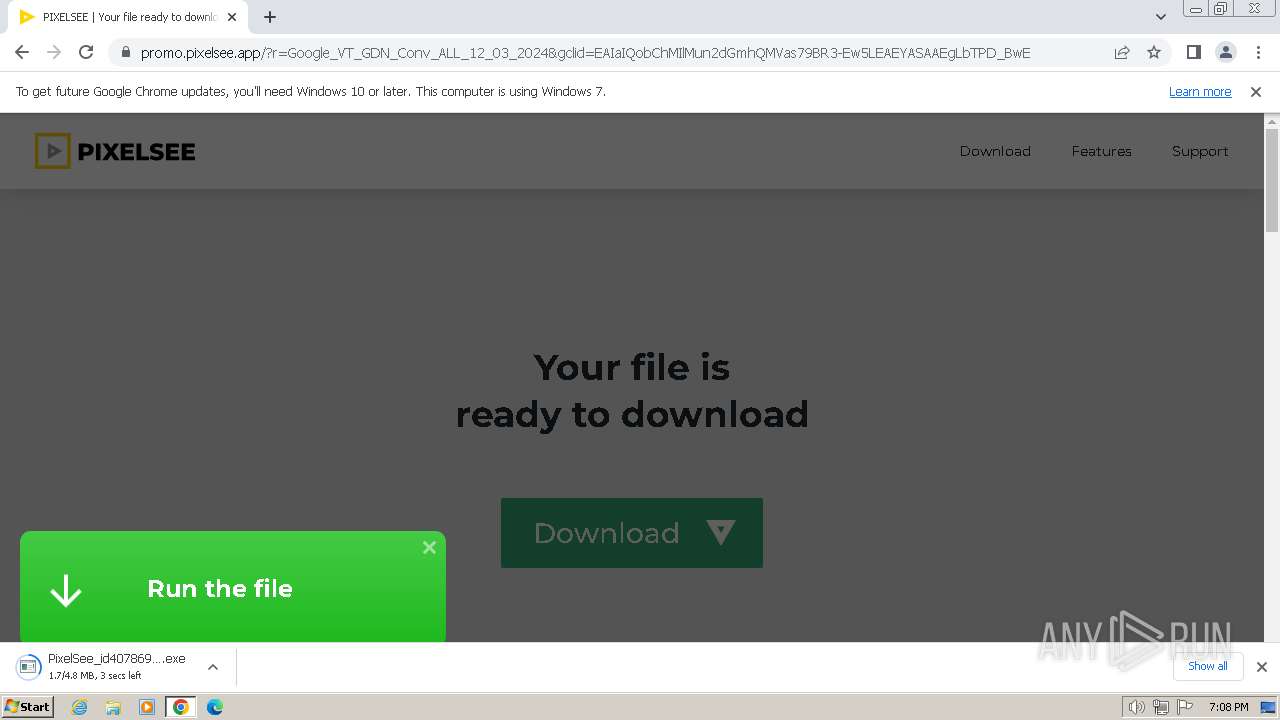
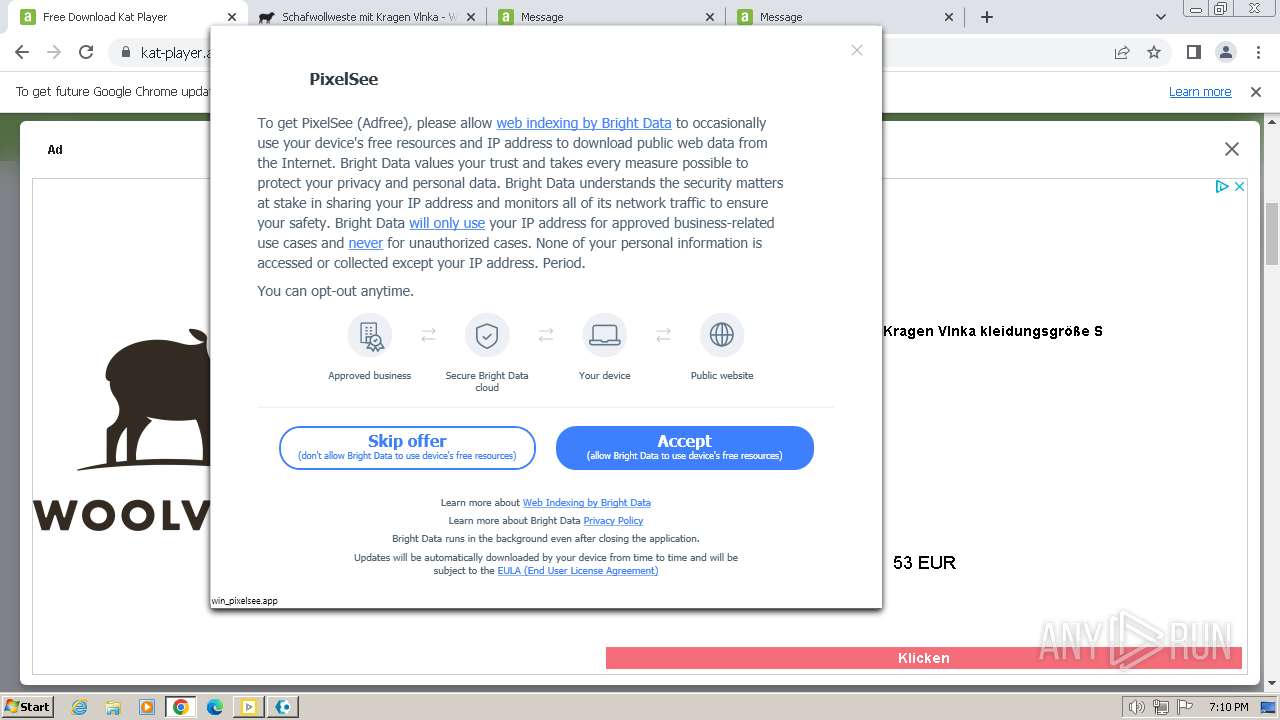
| 392 | "C:\Users\admin\Downloads\PixelSee_id4078696id.exe" | C:\Users\admin\Downloads\PixelSee_id4078696id.exe | chrome.exe | ||||||||||||
User: admin Company: SIA Circle Solutions Integrity Level: HIGH Description: PixelSee Player Installer Version: 14.0.0.0 Modules
| |||||||||||||||
| 548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=44 --mojo-platform-channel-handle=3528 --field-trial-handle=1168,i,10976330724926442215,11423318362585401399,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3940 --field-trial-handle=1168,i,10976330724926442215,11423318362585401399,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=828 --field-trial-handle=1168,i,10976330724926442215,11423318362585401399,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=3724 --field-trial-handle=1168,i,10976330724926442215,11423318362585401399,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=72 --mojo-platform-channel-handle=4880 --field-trial-handle=1168,i,10976330724926442215,11423318362585401399,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 844 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3128 --field-trial-handle=1168,i,10976330724926442215,11423318362585401399,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=43 --mojo-platform-channel-handle=4696 --field-trial-handle=1168,i,10976330724926442215,11423318362585401399,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --mojo-platform-channel-handle=3960 --field-trial-handle=1168,i,10976330724926442215,11423318362585401399,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
126 329
Read events
124 963
Write events
1 182
Delete events
184
Modification events
| (PID) Process: | (3500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3500) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
575
Suspicious files
175
Text files
182
Unknown types
286
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:— | SHA256:— | |||
| 3500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:— | SHA256:— | |||
| 3500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 3500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF182872.TMP | text | |
MD5:— | SHA256:— | |||
| 3500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF182872.TMP | text | |
MD5:— | SHA256:— | |||
| 3500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF182872.TMP | — | |
MD5:— | SHA256:— | |||
| 3500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\03de5d0b-6db9-43fc-bacb-b99bf66fa746.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
425
DNS requests
540
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
1848 | Installer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAsllCLO2YEqFaBOmVKKDvo%3D | unknown | — | — | unknown |
1848 | Installer.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
1848 | Installer.exe | GET | 304 | 23.36.163.20:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8e10cd7dea406758 | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
956 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertGlobalG2TLSRSASHA2562020CA1-1.crt | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
956 | chrome.exe | 142.251.166.84:443 | accounts.google.com | GOOGLE | US | unknown |
3500 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
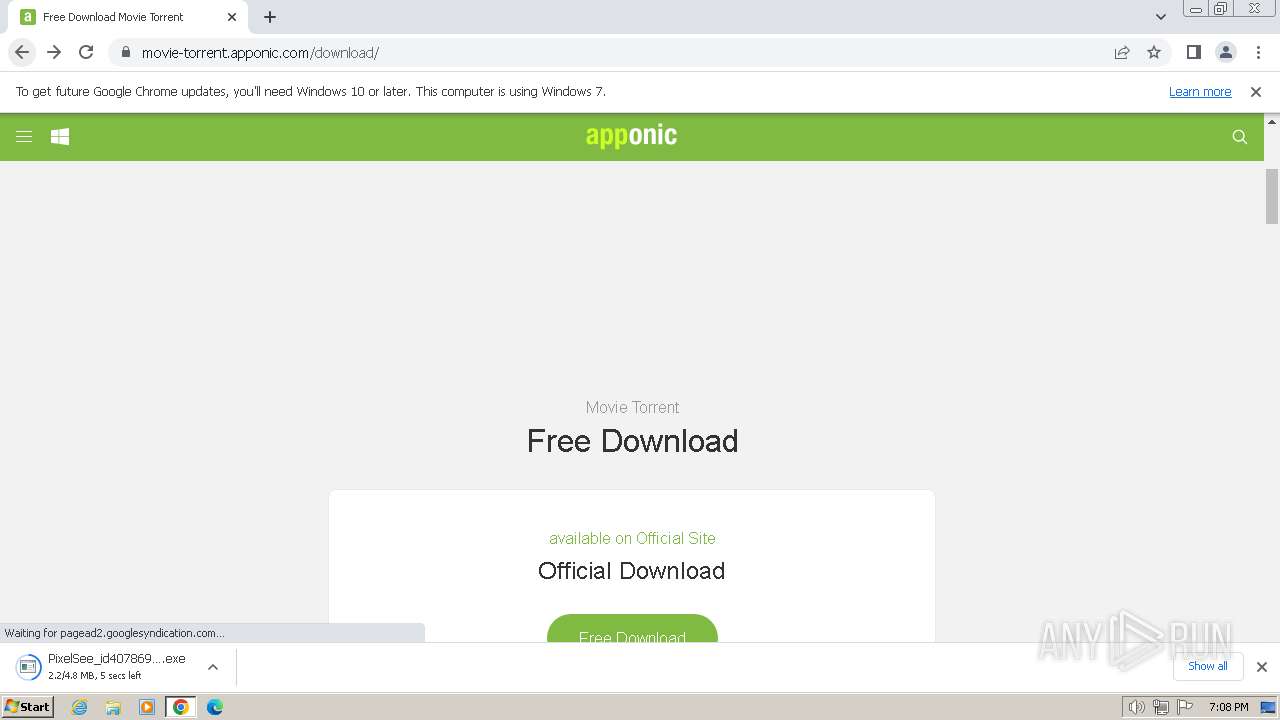
956 | chrome.exe | 66.206.12.122:443 | www.apponic.com | HVC-AS | US | unknown |
956 | chrome.exe | 142.250.185.194:443 | pagead2.googlesyndication.com | GOOGLE | US | unknown |
956 | chrome.exe | 142.250.186.131:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
956 | chrome.exe | 13.225.78.65:443 | cdn.apponic.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
www.apponic.com |
| malicious |
cdn.apponic.com |
| shared |
img.apponic.com |
| unknown |
pagead2.googlesyndication.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
tpc.googlesyndication.com |
| whitelisted |
www.googletagservices.com |
| whitelisted |
adservice.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
956 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
3452 | net_updater32.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
Process | Message |
|---|---|
pixelsee.exe | QWindowsEGLStaticContext::create: Could not initialize EGL display: error 0x3001
|
pixelsee.exe | QWindowsEGLStaticContext::create: When using ANGLE, check if d3dcompiler_4x.dll is available
|
pixelsee.exe | > __thiscall Application::Application(int &,char *[])
|
pixelsee.exe | os version: "6.1.7601v" __ os name: "Windows 7 Version 6.1 (Build 7601: SP 1)"
|
pixelsee.exe | > int __thiscall Application::exec(void)
|
pixelsee.exe | > __thiscall PixelseeSettings::PixelseeSettings(void)
|
pixelsee.exe | INSTALL ID: "" _ OLD ID: ""
|
pixelsee.exe | reseller - "" installId ""
|
pixelsee.exe | > void __thiscall PixelseeSettings::flushSettings(void)
|
pixelsee.exe | main libvlc debug: VLC media player - 3.0.16 Vetinari
|