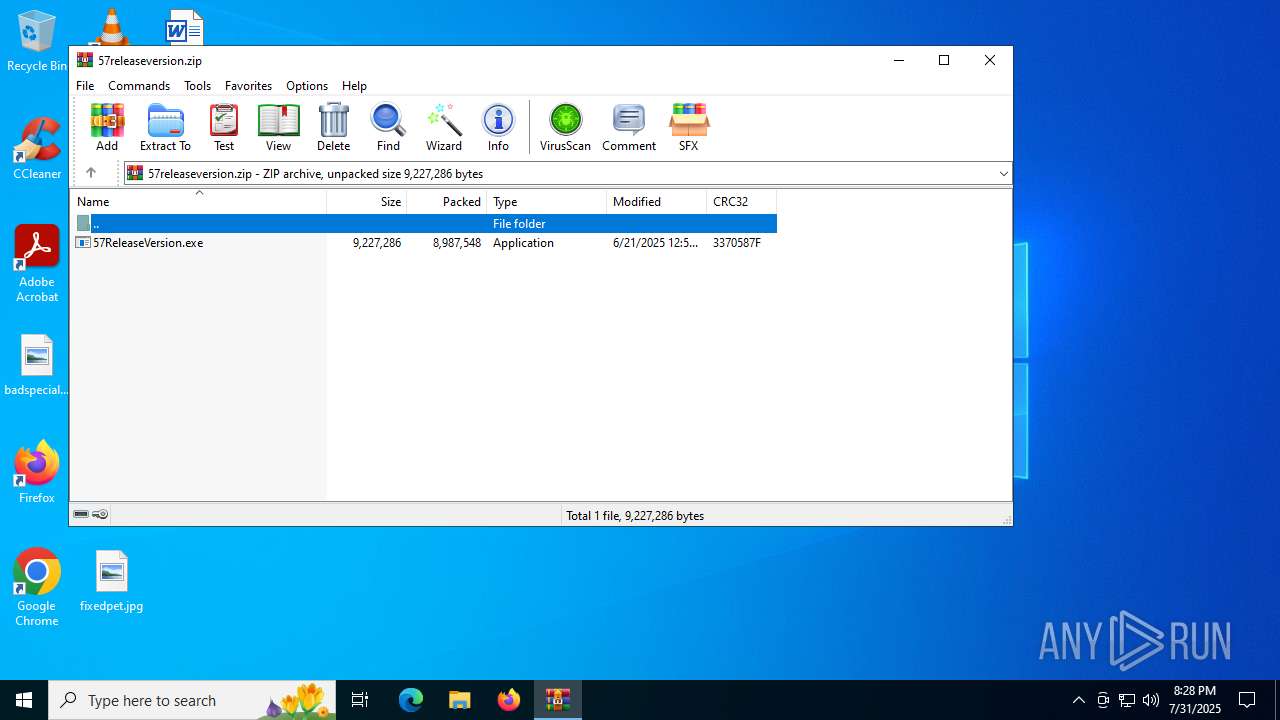
| File name: | 57releaseversion.zip |
| Full analysis: | https://app.any.run/tasks/8ba5e54b-f3f7-4941-8321-8744914d1fbf |
| Verdict: | Malicious activity |
| Analysis date: | July 31, 2025, 20:28:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 2FCDDC4603979A9B877F37C9B627BC53 |
| SHA1: | 8DB75D0907793E59232DBFB9A3532921F78334DD |
| SHA256: | 0D67E7BD97C870A2477AE3CD0C769267536707310112D85C69454AF892741A68 |
| SSDEEP: | 98304:R8k13Er/CbuScsXXnV/9EhAZE9Gq1Kklvm1Li5Zn/0lcUXI3+rl8OcPEZVItSv1D:5qcggDACD |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4724)
SUSPICIOUS
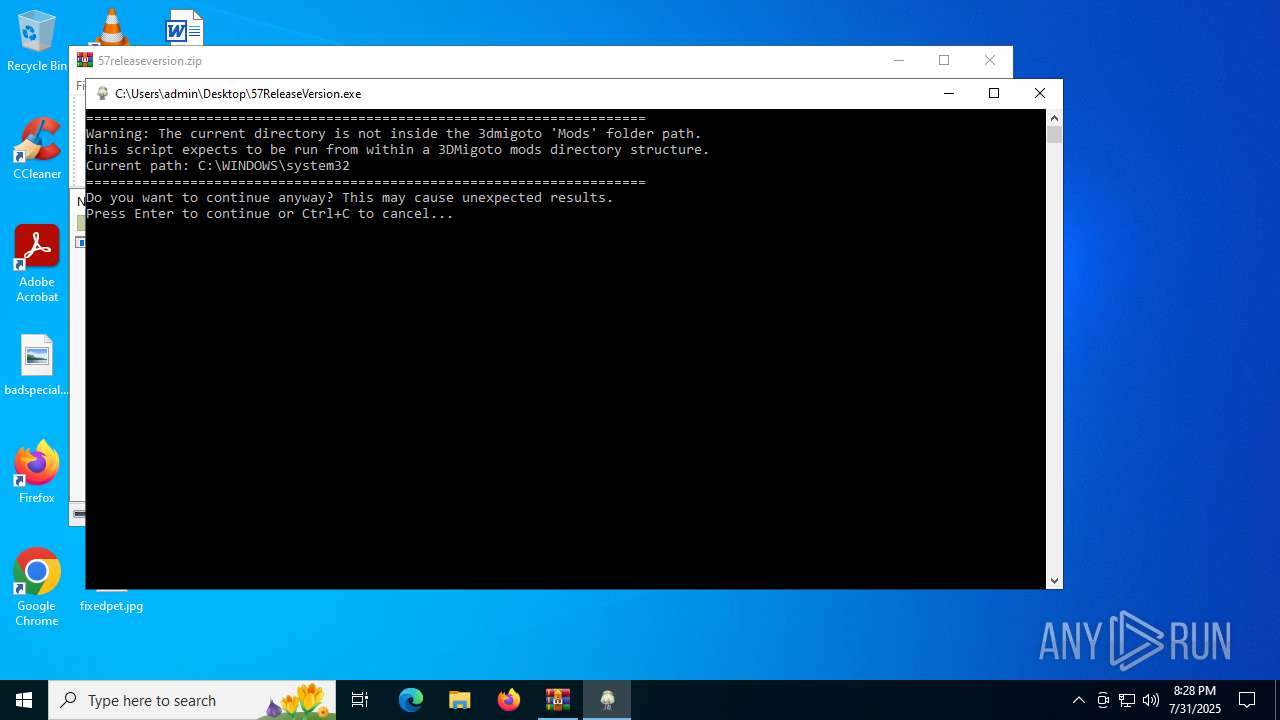
Process drops legitimate windows executable
- 57ReleaseVersion.exe (PID: 6224)
Process drops python dynamic module
- 57ReleaseVersion.exe (PID: 6224)
Executable content was dropped or overwritten
- 57ReleaseVersion.exe (PID: 6224)
Application launched itself
- 57ReleaseVersion.exe (PID: 6224)
Loads Python modules
- 57ReleaseVersion.exe (PID: 5248)
The process drops C-runtime libraries
- 57ReleaseVersion.exe (PID: 6224)
INFO
Checks supported languages
- 57ReleaseVersion.exe (PID: 6224)
- 57ReleaseVersion.exe (PID: 5248)
Manual execution by a user
- 57ReleaseVersion.exe (PID: 6224)
The sample compiled with english language support
- 57ReleaseVersion.exe (PID: 6224)
Create files in a temporary directory
- 57ReleaseVersion.exe (PID: 6224)
PyInstaller has been detected (YARA)
- 57ReleaseVersion.exe (PID: 6224)
- 57ReleaseVersion.exe (PID: 5248)
Checks proxy server information
- slui.exe (PID: 4160)
Reads the software policy settings
- slui.exe (PID: 4160)
Reads the computer name
- 57ReleaseVersion.exe (PID: 6224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:21 00:58:44 |
| ZipCRC: | 0x3370587f |
| ZipCompressedSize: | 8987548 |
| ZipUncompressedSize: | 9227286 |
| ZipFileName: | 57ReleaseVersion.exe |
Total processes
138
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4160 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\57releaseversion.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5248 | "C:\Users\admin\Desktop\57ReleaseVersion.exe" | C:\Users\admin\Desktop\57ReleaseVersion.exe | — | 57ReleaseVersion.exe | |||||||||||
User: admin Company: AGMG Discord Integrity Level: MEDIUM Description: GI Mods Fixer Version: 1.0.0.0 Modules
| |||||||||||||||
| 6224 | "C:\Users\admin\Desktop\57ReleaseVersion.exe" | C:\Users\admin\Desktop\57ReleaseVersion.exe | explorer.exe | ||||||||||||
User: admin Company: AGMG Discord Integrity Level: MEDIUM Description: GI Mods Fixer Version: 1.0.0.0 Modules
| |||||||||||||||
| 6668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 57ReleaseVersion.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 974
Read events
4 966
Write events
8
Delete events
0
Modification events
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\57releaseversion.zip | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
57
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6224 | 57ReleaseVersion.exe | C:\Users\admin\AppData\Local\Temp\_MEI62242\_hashlib.pyd | executable | |
MD5:EEDB6D834D96A3DFFFFB1F65B5F7E5BE | SHA256:79C4CDE23397B9A35B54A3C2298B3C7A844454F4387CB0693F15E4FACD227DD2 | |||
| 6224 | 57ReleaseVersion.exe | C:\Users\admin\AppData\Local\Temp\_MEI62242\_multiprocessing.pyd | executable | |
MD5:A4281E383EF82C482C8BDA50504BE04A | SHA256:467B0FEF42D70B55ABF41D817DFF7631FAEEF84DCE64F8AADB5690A22808D40C | |||
| 6224 | 57ReleaseVersion.exe | C:\Users\admin\AppData\Local\Temp\_MEI62242\_bz2.pyd | executable | |
MD5:223FD6748CAE86E8C2D5618085C768AC | SHA256:F81DC49EAC5ECC528E628175ADD2FF6BDA695A93EA76671D7187155AA6326ABB | |||
| 6224 | 57ReleaseVersion.exe | C:\Users\admin\AppData\Local\Temp\_MEI62242\_queue.pyd | executable | |
MD5:6E0CB85DC94E351474D7625F63E49B22 | SHA256:3F57F29ABD86D4DC8F4CA6C3F190EBB57D429143D98F0636FF5117E08ED81F9B | |||
| 6224 | 57ReleaseVersion.exe | C:\Users\admin\AppData\Local\Temp\_MEI62242\_ctypes.pyd | executable | |
MD5:BBD5533FC875A4A075097A7C6ABA865E | SHA256:BE9828A877E412B48D75ADDC4553D2D2A60AE762A3551F9731B50CAE7D65B570 | |||
| 6224 | 57ReleaseVersion.exe | C:\Users\admin\AppData\Local\Temp\_MEI62242\_ssl.pyd | executable | |
MD5:5B9B3F978D07E5A9D701F832463FC29D | SHA256:D568B3C99BF0FC35A1F3C5F66B4A9D3B67E23A1D3CF0A4D30499D924D805F5AA | |||
| 6224 | 57ReleaseVersion.exe | C:\Users\admin\AppData\Local\Temp\_MEI62242\_lzma.pyd | executable | |
MD5:05E8B2C429AFF98B3AE6ADC842FB56A3 | SHA256:A6E2A5BB7A33AD9054F178786A031A46EA560FAEEF1FB96259331500AAE9154C | |||
| 6224 | 57ReleaseVersion.exe | C:\Users\admin\AppData\Local\Temp\_MEI62242\_socket.pyd | executable | |
MD5:DC06F8D5508BE059EAE9E29D5BA7E9EC | SHA256:7DAFF6AA3851A913ED97995702A5DFB8A27CB7CF00FB496597BE777228D7564A | |||
| 6224 | 57ReleaseVersion.exe | C:\Users\admin\AppData\Local\Temp\_MEI62242\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
| 6224 | 57ReleaseVersion.exe | C:\Users\admin\AppData\Local\Temp\_MEI62242\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:1BEBD9B65ED18B680F7E39BEF09FE6CE | SHA256:E756F6970905657CF73ECB3F57BAE55A67BE29AFA75AE4D16046B0F7229708EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
51
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SIHClient.exe | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.165.164.15:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
5368 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5368 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5968 | RUXIMICS.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.32.76:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5968 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.32:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.32:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5968 | RUXIMICS.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |